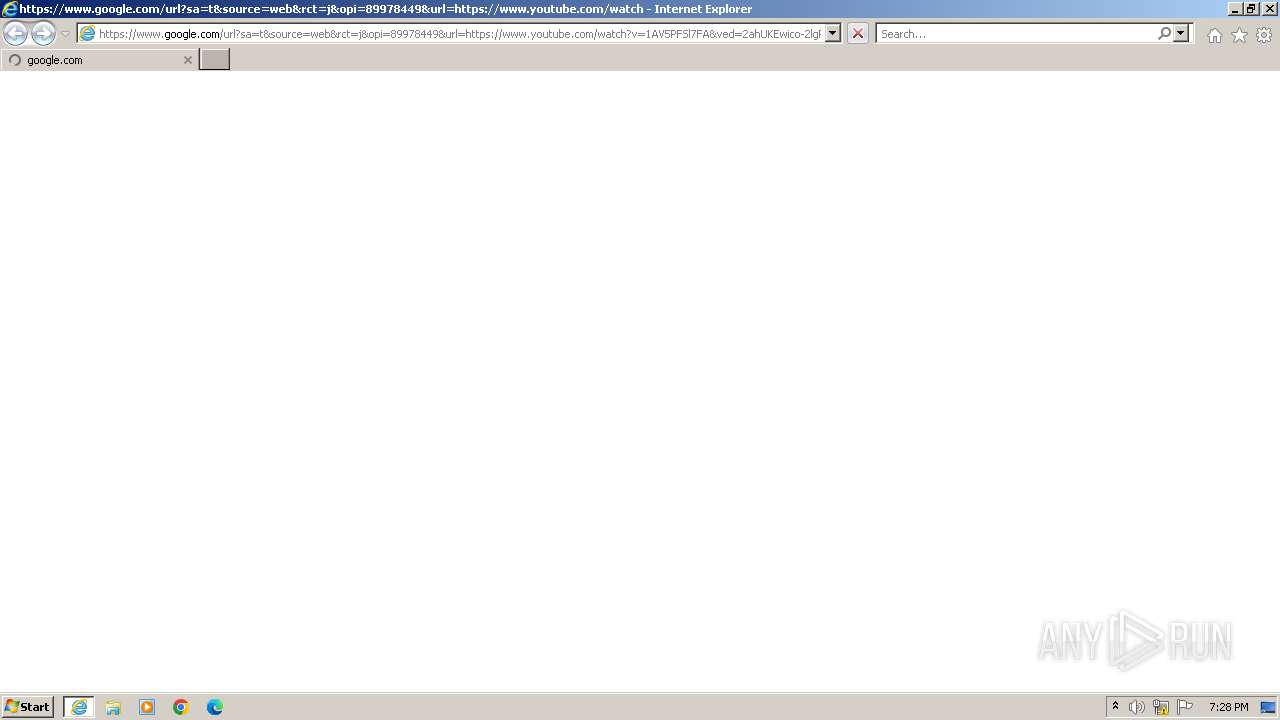
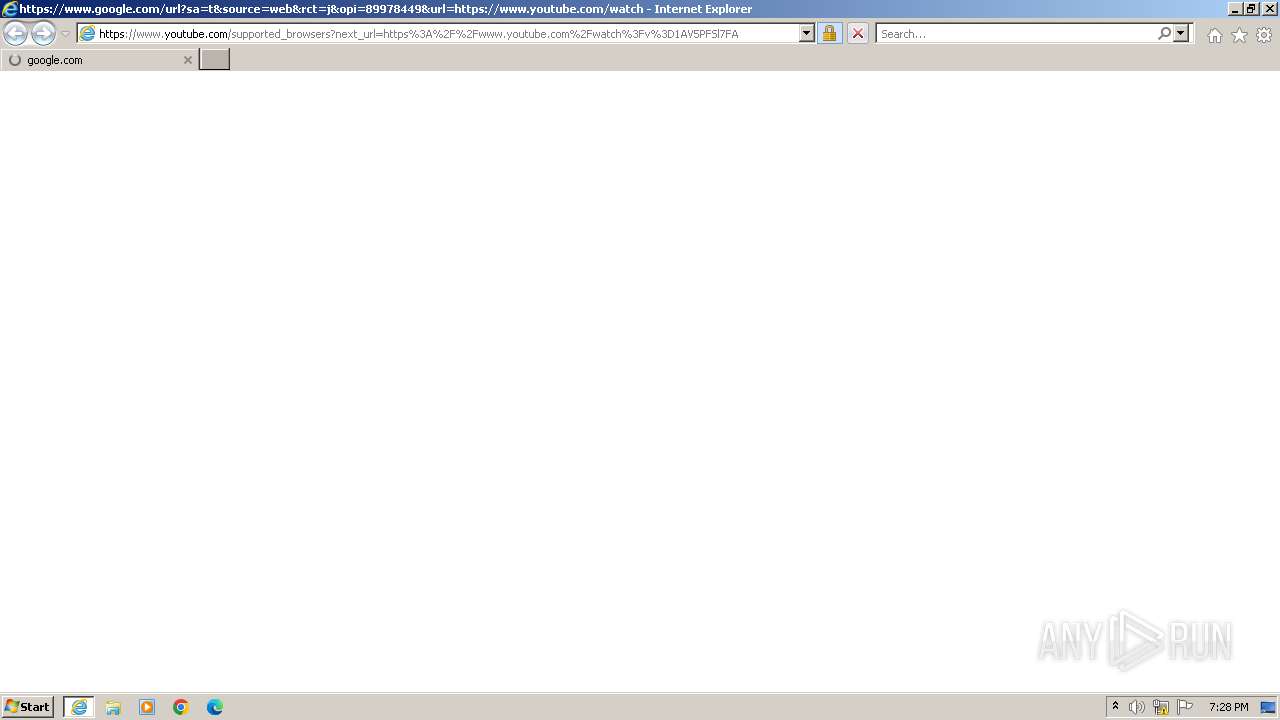
| URL: | https://www.google.com/url?sa=t&source=web&rct=j&opi=89978449&url=https://www.youtube.com/watch?v=1AV5PFSl7FA&ved=2ahUKEwico-2lgPOJAxXHxQIHHcx3LUIQjjh6BAgdEAE&usg=AOvVaw1eJKI-WL2lOl7pIb-HnEtH |
| Full analysis: | https://app.any.run/tasks/416c0611-2519-4479-9640-76e8a2f88220 |
| Verdict: | No threats detected |
| Analysis date: | November 23, 2024, 19:28:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 3232BE750F08FE682BB04ACC69C1B2F7 |
| SHA1: | 068CABD777ED6197861D29F25EE37751B7E9D863 |
| SHA256: | 73CFC1F98B050F3A14C914556F6DBEDCC873E3149676C2E4A6907E99B3A7C635 |
| SSDEEP: | 3:N8DSLI2sljXoW+PhIDNRRVYrSLUxGTKSEIY571jQTkYUNb3KrLtk/sGnkRQWALSM:2OLI2slQpUNRROGLUxGF5YXjQAvN+GTx |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 1836)
Executable content was dropped or overwritten
- iexplore.exe (PID: 848)
Manual execution by a user
- wmpnscfg.exe (PID: 3104)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
38
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 848 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1836 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1836 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.google.com/url?sa=t&source=web&rct=j&opi=89978449&url=https://www.youtube.com/watch?v=1AV5PFSl7FA&ved=2ahUKEwico-2lgPOJAxXHxQIHHcx3LUIQjjh6BAgdEAE&usg=AOvVaw1eJKI-WL2lOl7pIb-HnEtH" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3104 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
17 643
Read events
17 525
Write events
94
Delete events
24
Modification events
| (PID) Process: | (1836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (1836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31145437 | |||
| (PID) Process: | (1836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (1836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31145437 | |||
| (PID) Process: | (1836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1
Suspicious files
38
Text files
46
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 848 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:E8FEC8B860CA5D4DB095D7DF47D9A57A | SHA256:89A48189F75D88C99A690A7FF7D002880467093280D6A71D2CC2F1D170C3B6D1 | |||
| 848 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C02877841121CC45139CB51404116B25_16659210B029E2342348119FD8382C02 | binary | |
MD5:F447B2FB8B89840DD34F4D1A1586883D | SHA256:A53530B672FF9FE5B51391D31CECE26A95F0612356E2356F86BEE1EE0BE85EF7 | |||
| 848 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C02877841121CC45139CB51404116B25_16659210B029E2342348119FD8382C02 | der | |
MD5:8CA104C0E1E82BDB88A70B53FF53D537 | SHA256:20D2D35B1013E3DB6413AB4F30AE542CBA780F20B8B7FAF0BFDE77DA1880D155 | |||
| 848 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\yt_logo_rgb_light[1].png | image | |
MD5:D654F892F287A28026CD4D4DF56C29C8 | SHA256:FC6F5D8F32F13D5855840234DC1BFF5C91C35318EE2192D99B13EB3572F0BCA8 | |||
| 848 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\chrome[1].png | image | |
MD5:AC10B50494982BC75D03BD2D94E382F6 | SHA256:846A9B551E74F824FD7ACE3439A319B0C0803449E8CAEC9F16E2666E38A80EFD | |||
| 848 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\edgium[1].png | image | |
MD5:01010C21BDF1FC1D7F859071C4227529 | SHA256:6FB31ACDAF443A97183562571D52CE47DD44C1A8DCB4087338D77EA2617B286E | |||
| 848 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\4FA45AE1010E09657982D8D28B3BD38E_841DF67C840691A847835C0F760B4DC0 | der | |
MD5:329F56D3BC9C773B9CE4046A6BE42150 | SHA256:1755E57D23A732513F86579AC17EB08D871D83DAC0842A9E19B44D59AE6E0525 | |||
| 848 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\dinosaur[1].png | image | |
MD5:BDDA3FFD41C3527AD053E4AFB8CD9E1E | SHA256:1A9251DC3B3C064CFC5E2B90B6C7DC3C225F7017066DB2B77E49DAE90A94A399 | |||
| 848 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\4FA45AE1010E09657982D8D28B3BD38E_841DF67C840691A847835C0F760B4DC0 | binary | |
MD5:56378ED4BB016EC2F3D1219B47183206 | SHA256:8AAF78CCB840868014A4A01909FC25C865925156728C0C9228866872434D198B | |||
| 848 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\O37FWXR3.txt | text | |
MD5:C8A952E1BCA9CBAD53299649F2F52361 | SHA256:5602A3410150D1370068D5B8B6107B072B3630780D360EB4AE23987E48475DB2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
50
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
848 | iexplore.exe | GET | 304 | 84.201.210.20:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?651840a0ef66a591 | unknown | — | — | whitelisted |
848 | iexplore.exe | GET | 304 | 84.201.210.20:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3a75f9bdfde1ae8f | unknown | — | — | whitelisted |
848 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
848 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQCdnAM1WJ6jQhB6sJGT2Dti | unknown | — | — | whitelisted |
848 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
848 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://o.pki.goog/wr2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEEGoFYJ0C3qQCbRh5xcgwPQ%3D | unknown | — | — | whitelisted |
848 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQCm0zxQ5KDvqwpdQsrzXj3H | unknown | — | — | whitelisted |
848 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQDEGAgOcBEqfBC%2B1yioLDZa | unknown | — | — | whitelisted |
1836 | iexplore.exe | GET | 304 | 84.201.210.20:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9f379e501adbc710 | unknown | — | — | whitelisted |
1836 | iexplore.exe | GET | 304 | 84.201.210.20:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e5d569a6b1e21146 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
848 | iexplore.exe | 142.250.185.100:443 | www.google.com | GOOGLE | US | whitelisted |
848 | iexplore.exe | 84.201.210.20:80 | ctldl.windowsupdate.com | IP4NET Sp. z o.o. | PL | whitelisted |
848 | iexplore.exe | 142.250.186.67:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1108 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
848 | iexplore.exe | 216.58.206.78:443 | www.youtube.com | GOOGLE | US | whitelisted |
848 | iexplore.exe | 216.58.206.74:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
848 | iexplore.exe | 216.58.206.35:443 | fonts.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.google.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
c.pki.goog |
| whitelisted |
o.pki.goog |
| whitelisted |
www.youtube.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
api.bing.com |
| whitelisted |