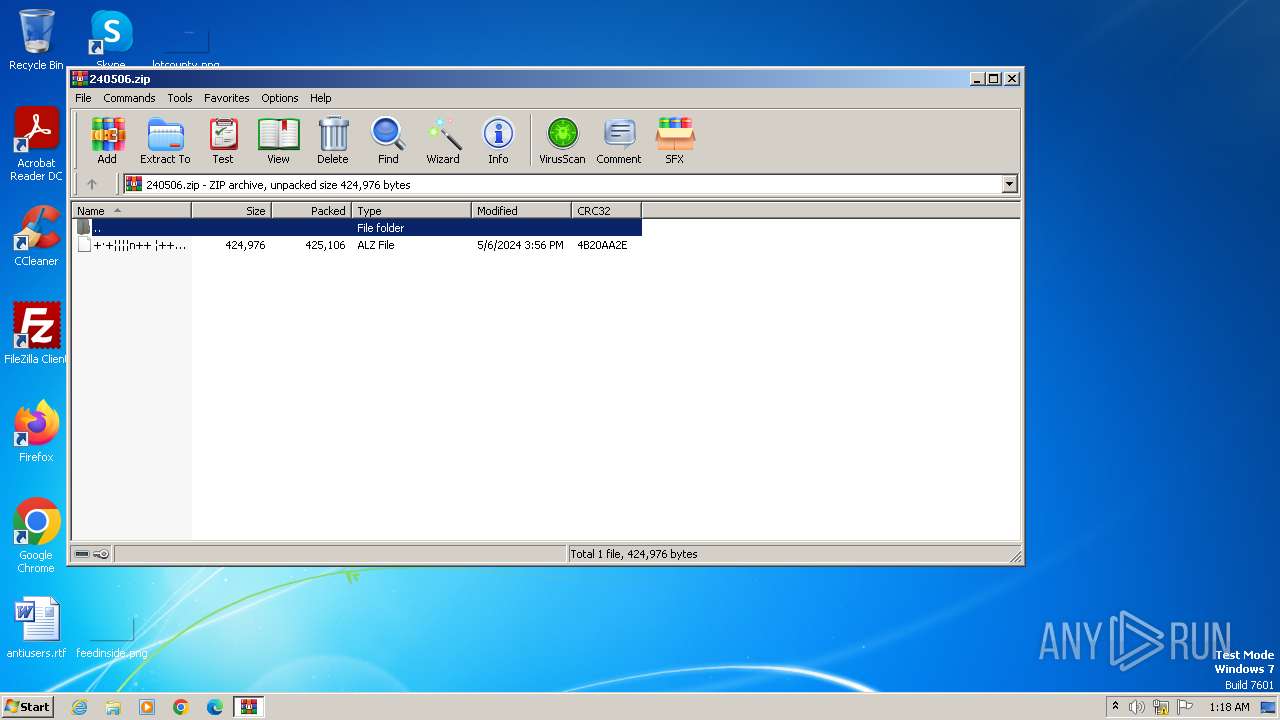
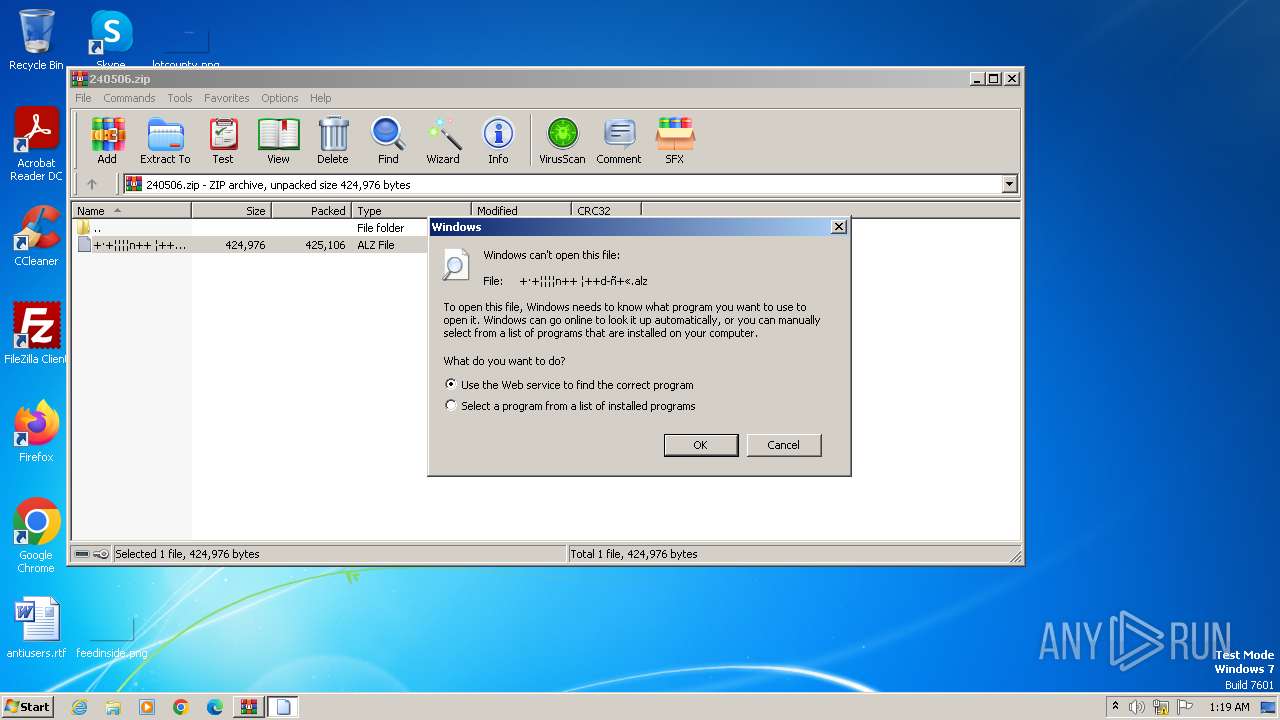
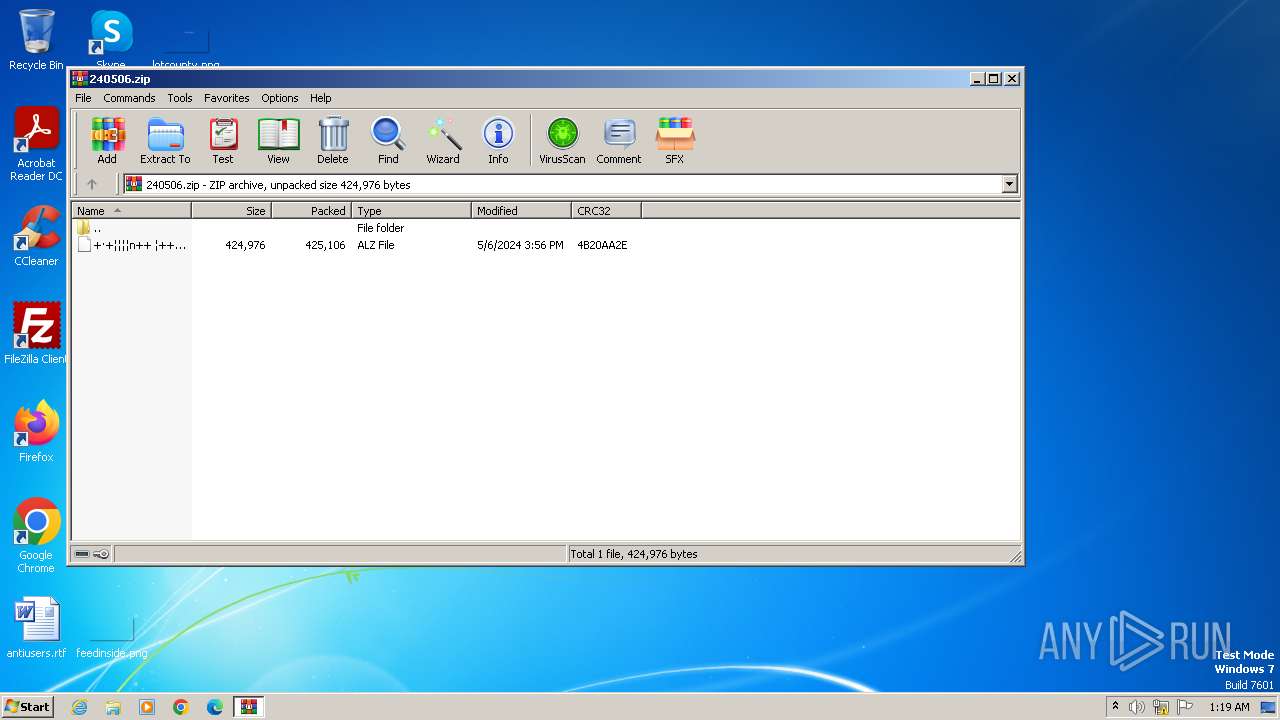
| File name: | 240506.zip |
| Full analysis: | https://app.any.run/tasks/b2c5be30-fa77-4231-aea9-59c8b4868126 |
| Verdict: | Malicious activity |
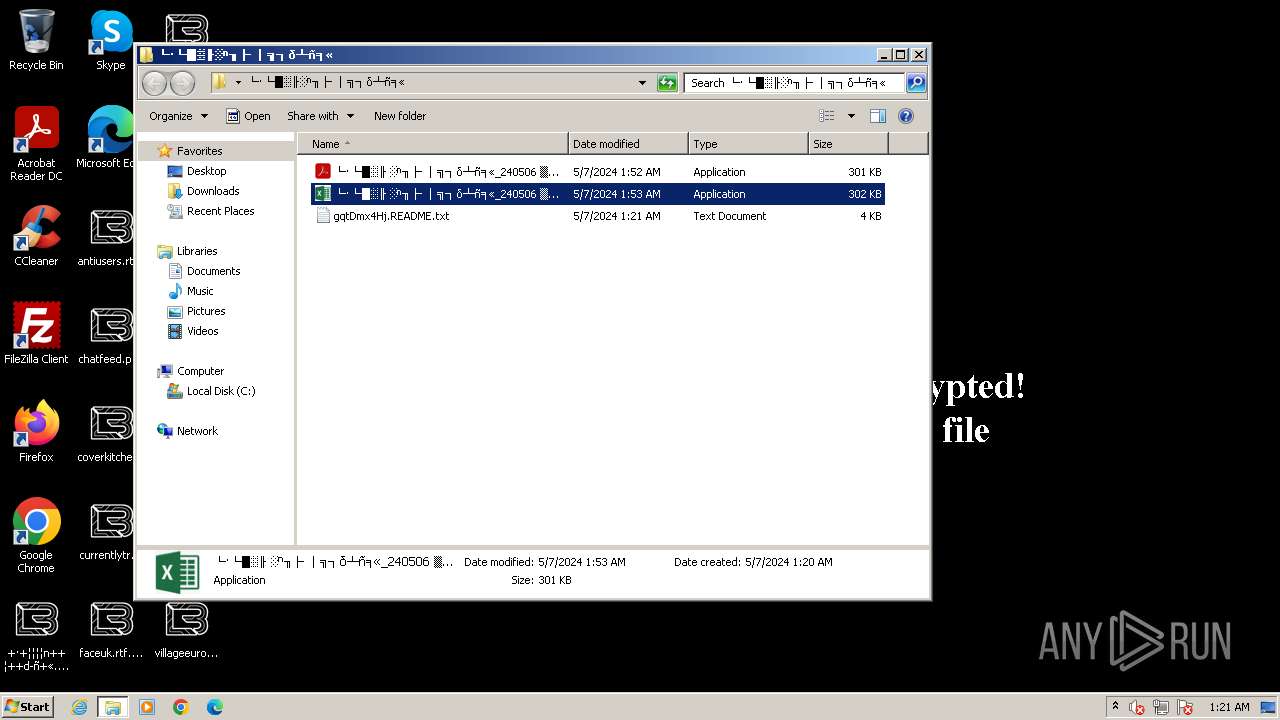
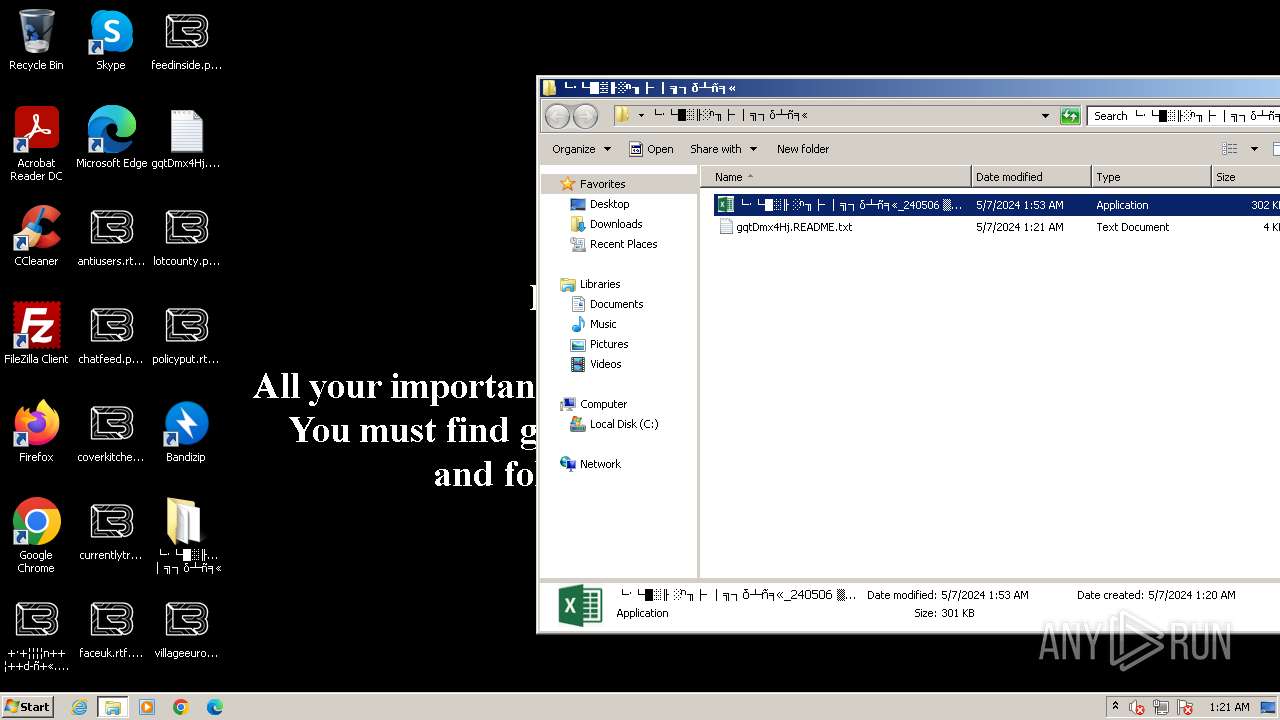
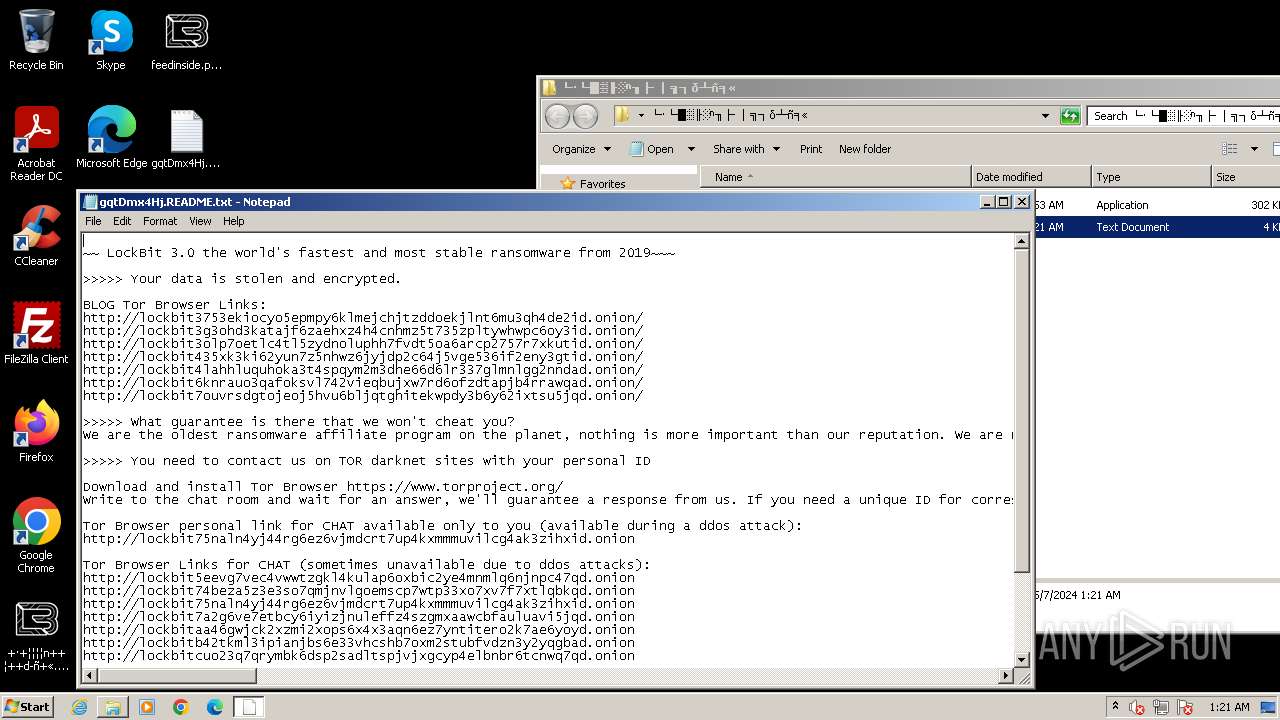
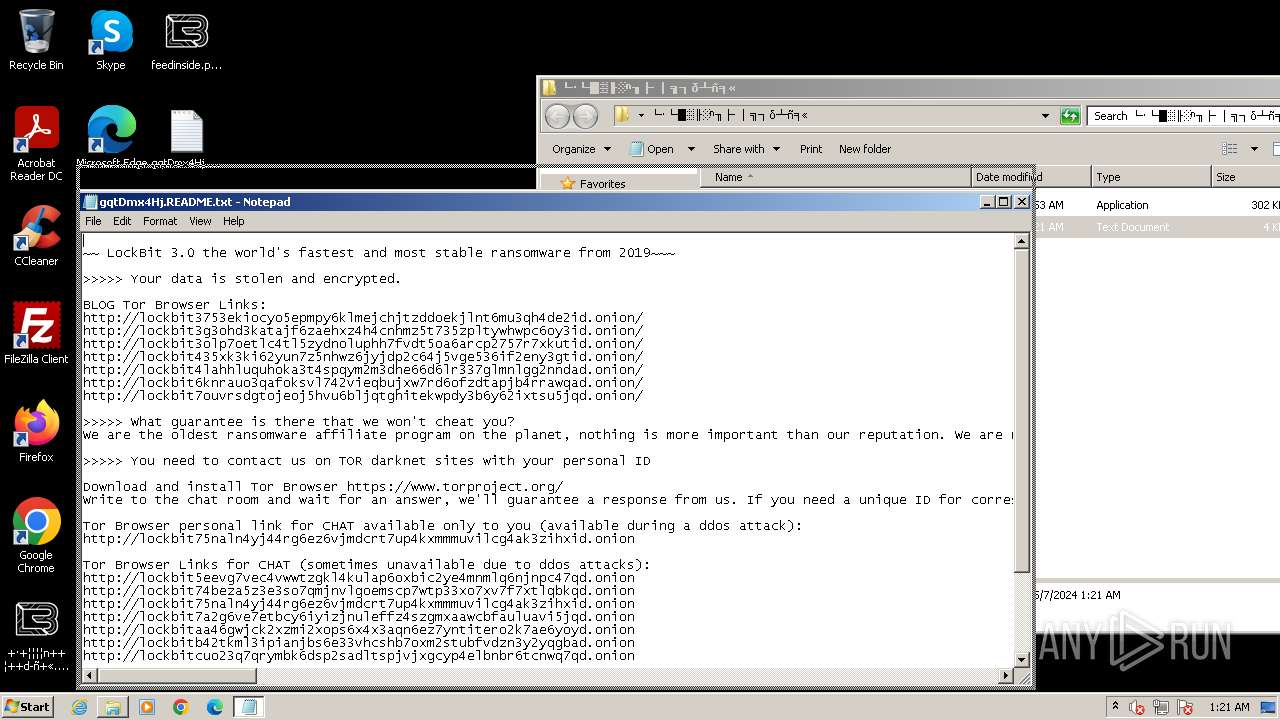
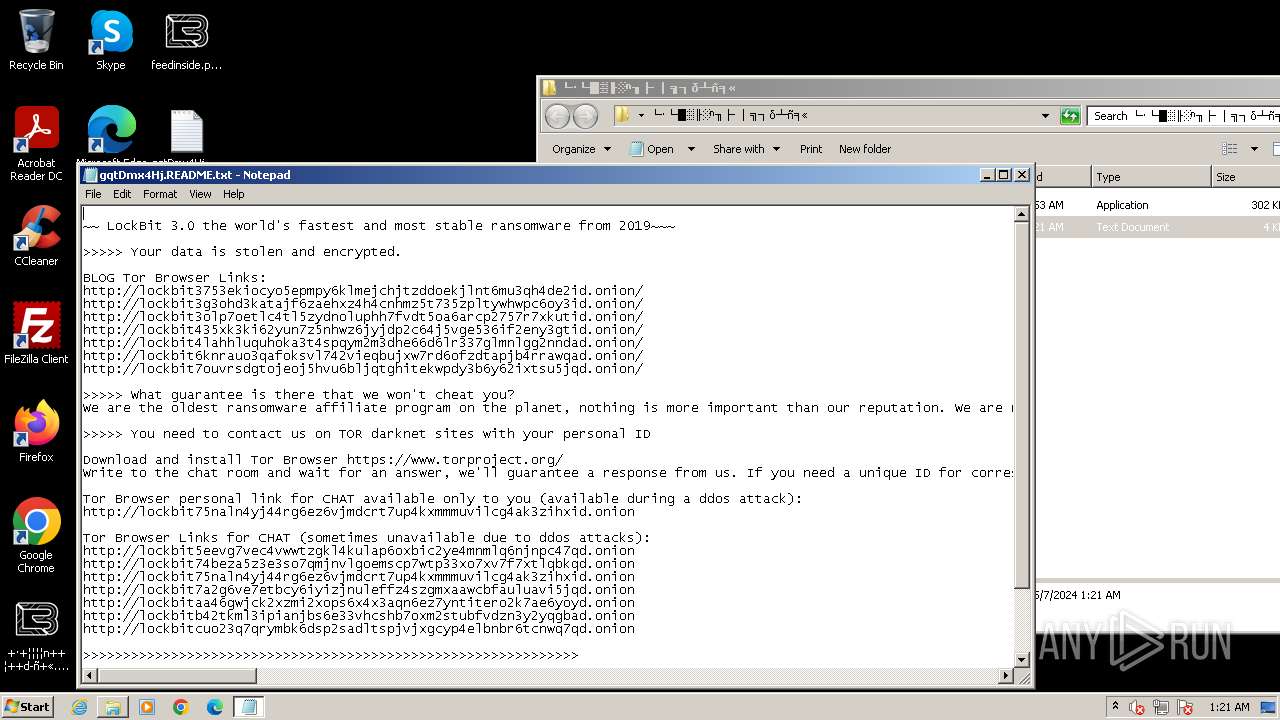
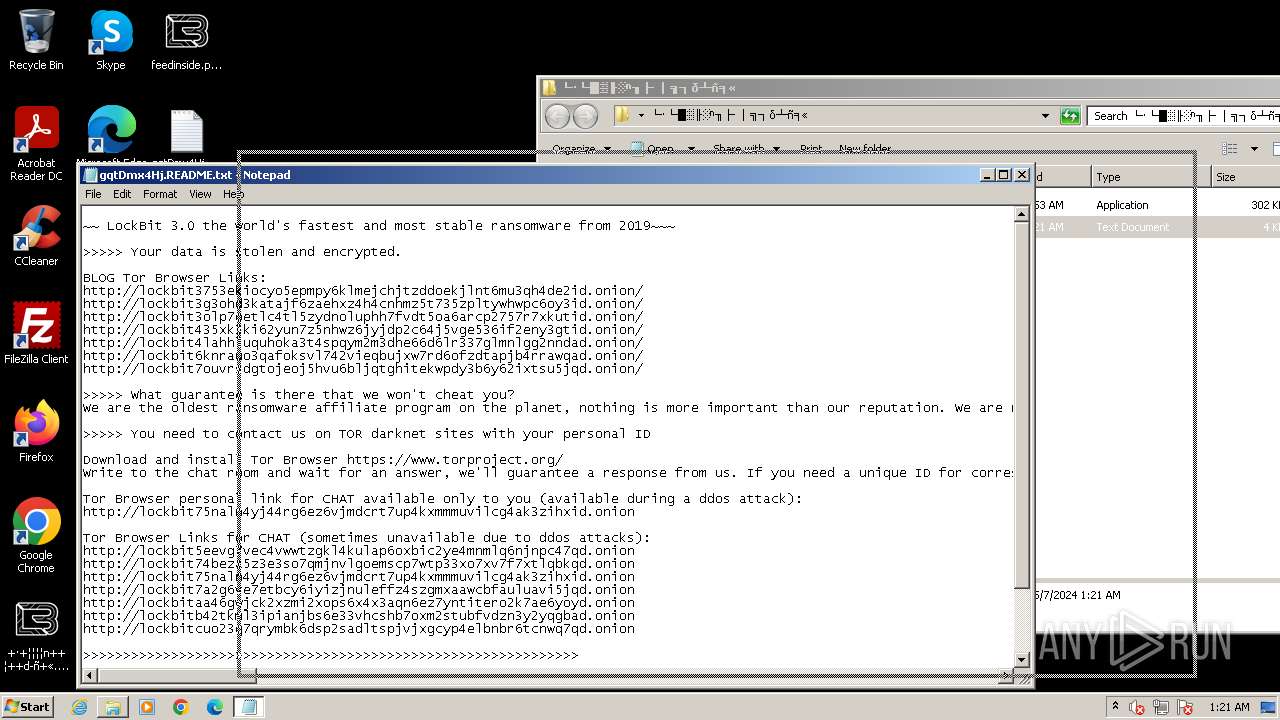
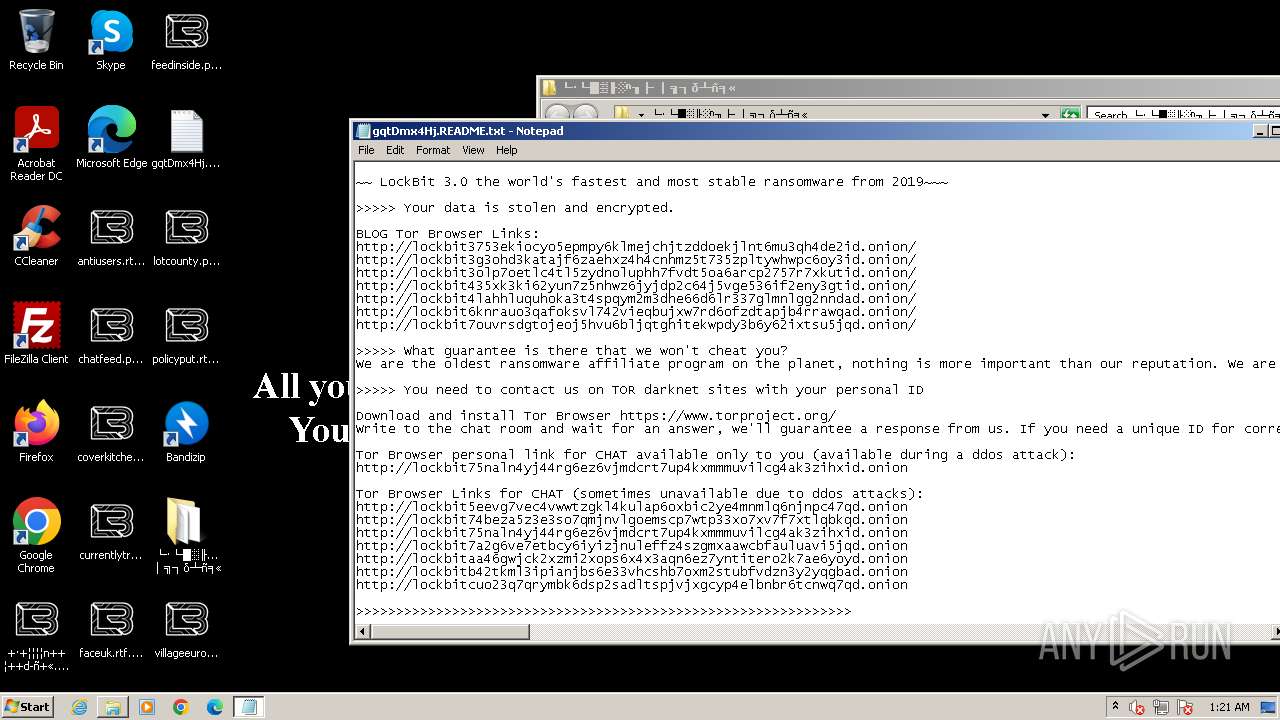
| Threats: | LockBit, a ransomware variant, encrypts data on infected machines, demanding a ransom payment for decryption. Used in targeted attacks, It's a significant risk to organizations. |
| Analysis date: | May 07, 2024, 00:18:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 973956538F251F5C3B5918B62568BE50 |
| SHA1: | 6EEE67E2DF80437CB802B1941F0EFB83A054BBDC |
| SHA256: | 73CB3B9CAD2DF48EFD839C2048A734B9B3D3F24604D024FE3AC2364687D9B6DD |
| SSDEEP: | 12288:ReM22BD1bpCWW6tus6PISp6dZ/Ws/SkVS77qDNsWG6:ReEB59CWW6tusCFp6dZ/JSkVGqDRG6 |
MALICIOUS
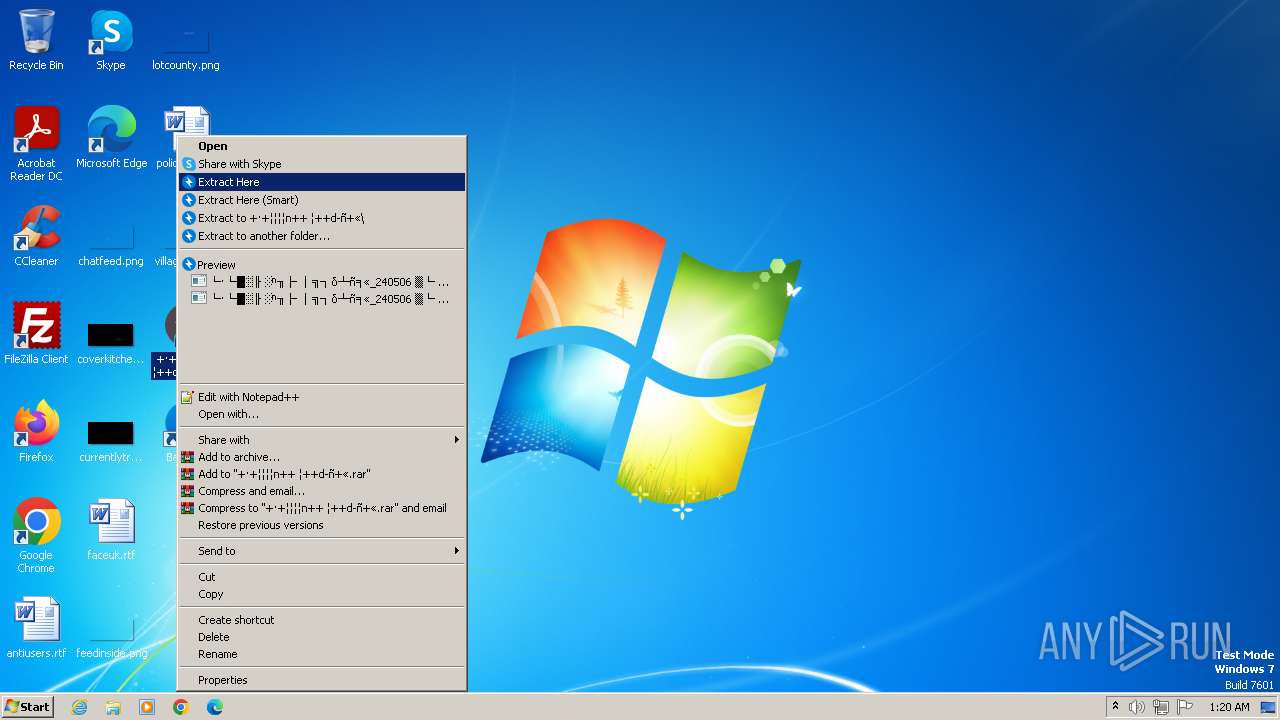
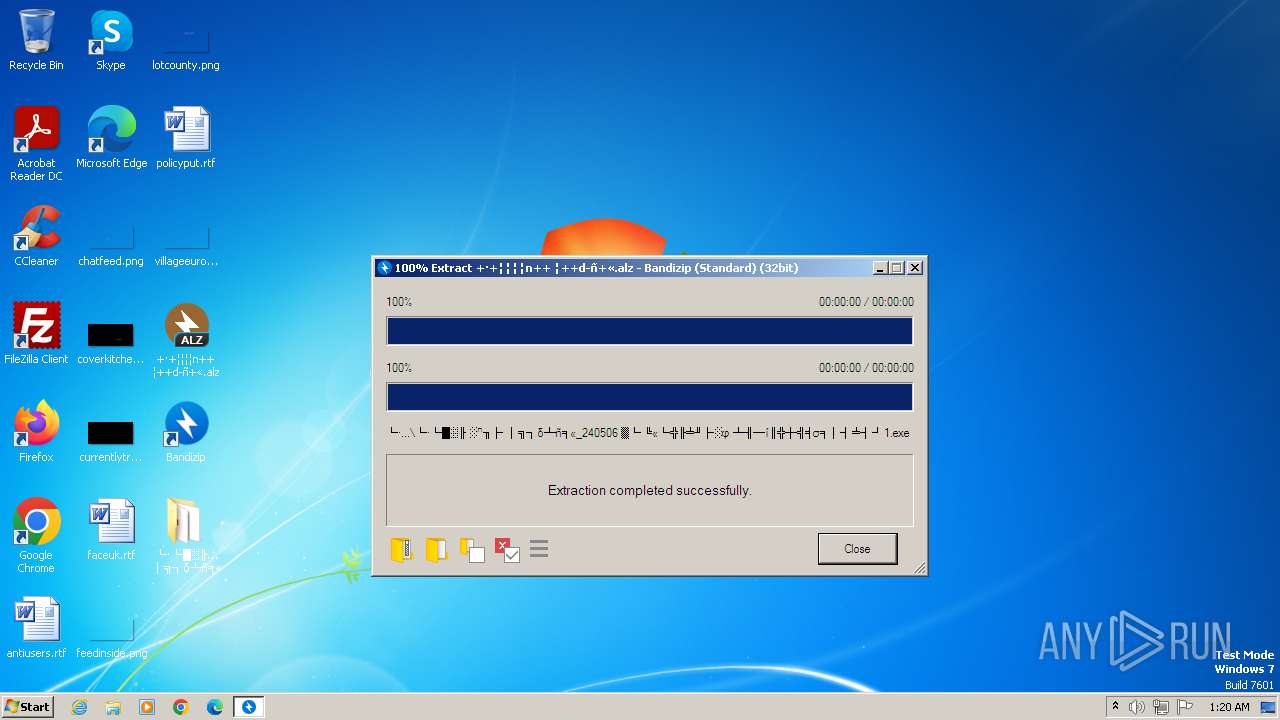
Drops the executable file immediately after the start
- BANDIZIP-SETUP-STD-ALL.EXE (PID: 3780)
- Bandizip.exe (PID: 3696)
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘.exe (PID: 2168)
Known privilege escalation attack
- dllhost.exe (PID: 2928)
Renames files like ransomware
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘.exe (PID: 2168)
[YARA] LockBit is detected
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘.exe (PID: 2168)
VIDAR has been detected (YARA)
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘1.exe (PID: 2280)
SUSPICIOUS
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 3980)
Reads security settings of Internet Explorer
- BANDIZIP-SETUP-STD-ALL.EXE (PID: 3780)
- Updater.exe (PID: 2712)
- Bandizip.exe (PID: 2700)
- Bandizip.exe (PID: 4088)
- Bandizip.exe (PID: 2812)
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘1.exe (PID: 2280)
Reads the Internet Settings
- BANDIZIP-SETUP-STD-ALL.EXE (PID: 3780)
- Bandizip.exe (PID: 2700)
- Updater.exe (PID: 2712)
- Bandizip.exe (PID: 4088)
- Bandizip.exe (PID: 2812)
- Bandizip.exe (PID: 2892)
- Bandizip.exe (PID: 3696)
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘1.exe (PID: 2280)
Checks Windows Trust Settings
- BANDIZIP-SETUP-STD-ALL.EXE (PID: 3780)
- Updater.exe (PID: 2712)
- Bandizip.exe (PID: 4088)
- Bandizip.exe (PID: 2812)
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘1.exe (PID: 2280)
Reads settings of System Certificates
- BANDIZIP-SETUP-STD-ALL.EXE (PID: 3780)
- Updater.exe (PID: 2712)
- Bandizip.exe (PID: 4088)
- Bandizip.exe (PID: 2812)
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘1.exe (PID: 2280)
Adds/modifies Windows certificates
- BANDIZIP-SETUP-STD-ALL.EXE (PID: 3780)
Changes Internet Explorer settings (feature browser emulation)
- RegDll.x86.exe (PID: 2104)
- RegDll.x86.exe (PID: 3508)
- RegDll.x86.exe (PID: 3136)
Executable content was dropped or overwritten
- BANDIZIP-SETUP-STD-ALL.EXE (PID: 3780)
- Bandizip.exe (PID: 3696)
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘.exe (PID: 2168)
Creates/Modifies COM task schedule object
- RegDll.x86.exe (PID: 4080)
Creates a software uninstall entry
- BANDIZIP-SETUP-STD-ALL.EXE (PID: 3780)
Reads Internet Explorer settings
- Updater.exe (PID: 2712)
Reads Microsoft Outlook installation path
- Updater.exe (PID: 2712)
Application launched itself
- Bandizip.exe (PID: 2700)
Write to the desktop.ini file (may be used to cloak folders)
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘.exe (PID: 2168)
Executes as Windows Service
- VSSVC.exe (PID: 2008)
Creates files like ransomware instruction
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘.exe (PID: 2168)
Connects to unusual port
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘1.exe (PID: 2280)
Changes the desktop background image
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘.exe (PID: 2168)
Starts application with an unusual extension
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘.exe (PID: 2168)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 664)
- rundll32.exe (PID: 1200)
- msedge.exe (PID: 1116)
- RegDll.x86.exe (PID: 3216)
- Bandizip.exe (PID: 2700)
- Bandizip.exe (PID: 2812)
- Bandizip.exe (PID: 3696)
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘.exe (PID: 3804)
- Bandizip.exe (PID: 2892)
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘1.exe (PID: 2280)
- notepad.exe (PID: 3056)
Application launched itself
- msedge.exe (PID: 1116)
Checks supported languages
- wmpnscfg.exe (PID: 664)
- BANDIZIP-SETUP-STD-ALL.EXE (PID: 3780)
- Bandizip.exe (PID: 3852)
- RegDll.x86.exe (PID: 3508)
- RegDll.x86.exe (PID: 3136)
- RegDll.x86.exe (PID: 2104)
- RegDll.x86.exe (PID: 4080)
- RegDll.x86.exe (PID: 2844)
- RegDll.x86.exe (PID: 3216)
- RegDll.x86.exe (PID: 2072)
- Bandizip.exe (PID: 3160)
- Bandizip.exe (PID: 2700)
- Updater.exe (PID: 2712)
- Bandizip.exe (PID: 4088)
- Bandizip.exe (PID: 2812)
- Bandizip.exe (PID: 3696)
- Bandizip.exe (PID: 2892)
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘.exe (PID: 3804)
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘.exe (PID: 2168)
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘1.exe (PID: 2280)
- B3F6.tmp (PID: 2972)
Reads the computer name
- wmpnscfg.exe (PID: 664)
- BANDIZIP-SETUP-STD-ALL.EXE (PID: 3780)
- RegDll.x86.exe (PID: 3216)
- Bandizip.exe (PID: 2700)
- Updater.exe (PID: 2712)
- Bandizip.exe (PID: 2812)
- Bandizip.exe (PID: 4088)
- Bandizip.exe (PID: 2892)
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘.exe (PID: 3804)
- Bandizip.exe (PID: 3696)
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘.exe (PID: 2168)
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘1.exe (PID: 2280)
Drops the executable file immediately after the start
- msedge.exe (PID: 1116)
- msedge.exe (PID: 1488)
Executable content was dropped or overwritten
- msedge.exe (PID: 1116)
- msedge.exe (PID: 1488)
The process uses the downloaded file
- msedge.exe (PID: 2432)
- msedge.exe (PID: 1116)
Reads the software policy settings
- BANDIZIP-SETUP-STD-ALL.EXE (PID: 3780)
- Updater.exe (PID: 2712)
- Bandizip.exe (PID: 4088)
- Bandizip.exe (PID: 2812)
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘1.exe (PID: 2280)
Reads the machine GUID from the registry
- BANDIZIP-SETUP-STD-ALL.EXE (PID: 3780)
- Updater.exe (PID: 2712)
- Bandizip.exe (PID: 4088)
- Bandizip.exe (PID: 2812)
- Bandizip.exe (PID: 2892)
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘.exe (PID: 3804)
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘.exe (PID: 2168)
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘1.exe (PID: 2280)
Checks proxy server information
- BANDIZIP-SETUP-STD-ALL.EXE (PID: 3780)
- Bandizip.exe (PID: 2700)
- Updater.exe (PID: 2712)
- Bandizip.exe (PID: 4088)
- Bandizip.exe (PID: 2812)
- Bandizip.exe (PID: 2892)
- Bandizip.exe (PID: 3696)
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘1.exe (PID: 2280)
Creates files or folders in the user directory
- BANDIZIP-SETUP-STD-ALL.EXE (PID: 3780)
- Updater.exe (PID: 2712)
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘1.exe (PID: 2280)
Creates files in the program directory
- BANDIZIP-SETUP-STD-ALL.EXE (PID: 3780)
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘.exe (PID: 2168)
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘1.exe (PID: 2280)
Checks transactions between databases Windows and Oracle
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘.exe (PID: 3804)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 2928)
Create files in a temporary directory
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘1.exe (PID: 2280)
Reads product name
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘1.exe (PID: 2280)
Reads Environment values
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘1.exe (PID: 2280)
Dropped object may contain TOR URL's
- └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘.exe (PID: 2168)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:05:06 15:56:46 |
| ZipCRC: | 0x4b20aa2e |
| ZipCompressedSize: | 425106 |
| ZipUncompressedSize: | 424976 |
| ZipFileName: | ???۱ǰ??? ????????.alz |
Total processes
113
Monitored processes
63
Malicious processes
10
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 112 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd8,0x6e6af598,0x6e6af5a8,0x6e6af5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 188 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1456 --field-trial-handle=1324,i,6138670470745489543,3374187927732427830,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 664 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 856 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4040 --field-trial-handle=1324,i,6138670470745489543,3374187927732427830,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 956 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3556 --field-trial-handle=1324,i,6138670470745489543,3374187927732427830,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1012 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3660 --field-trial-handle=1324,i,6138670470745489543,3374187927732427830,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1032 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=17 --mojo-platform-channel-handle=3356 --field-trial-handle=1324,i,6138670470745489543,3374187927732427830,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1060 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1188 --field-trial-handle=1324,i,6138670470745489543,3374187927732427830,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1116 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --profile-directory=Default | C:\Program Files\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
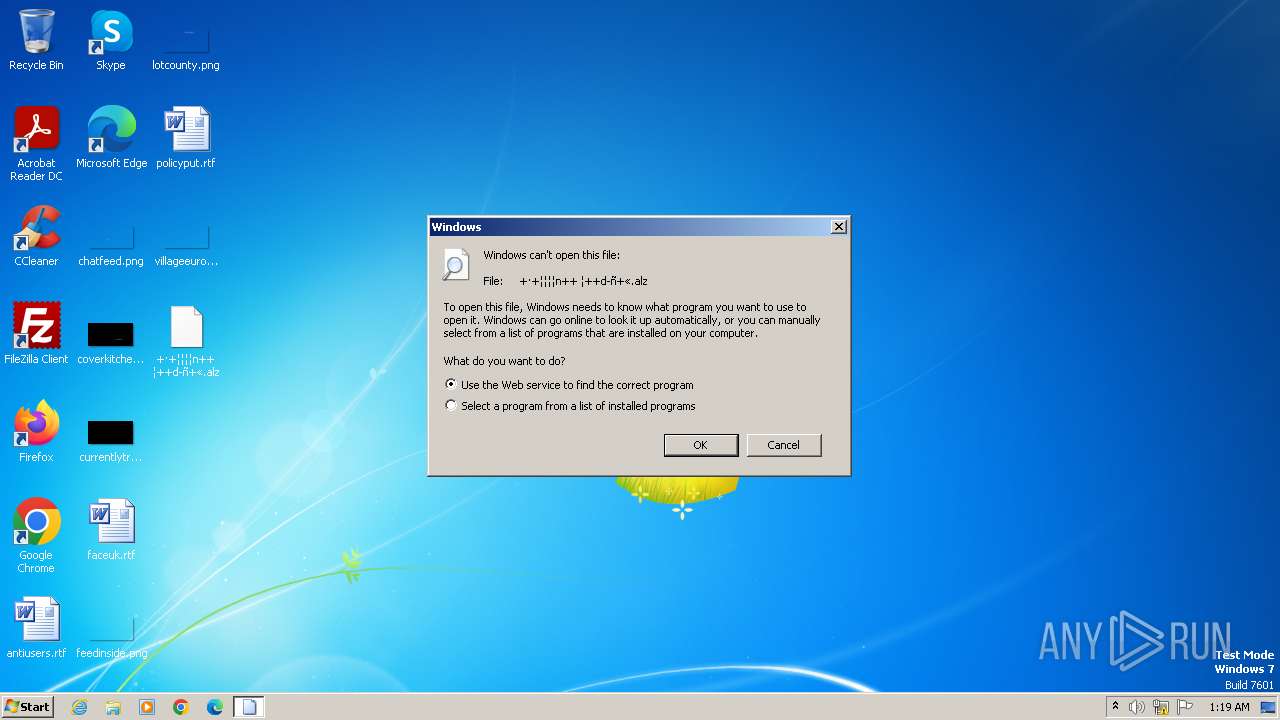
| 1200 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\+·+¦¦¦¦n++ ¦++d-ñ+«.alz | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
51 199
Read events
47 232
Write events
3 895
Delete events
72
Modification events
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\240506.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
47
Suspicious files
775
Text files
215
Unknown types
43
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1116 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\161b7fa1-e29c-4831-a911-ee066037a447.tmp | — | |
MD5:— | SHA256:— | |||
| 1116 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF11601e.TMP | — | |
MD5:— | SHA256:— | |||
| 1116 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1116 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF11606c.TMP | — | |
MD5:— | SHA256:— | |||
| 1116 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1116 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF116118.TMP | — | |
MD5:— | SHA256:— | |||
| 1116 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3980 | WinRAR.exe | C:\Users\admin\Desktop\+·+¦¦¦¦n++ ¦++d-ñ+«.alz | binary | |
MD5:86683A2C4F34FC8AD3C1EEF8B793B3F9 | SHA256:B7155C3AB8353DC1A792EBAC23E0FEF1D3F4F32879400614003693C21A5D1D41 | |||
| 1116 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | binary | |
MD5:A6EBC0D32A7B9304824D19DB63B4E37A | SHA256:E991057C2B1718A151C5FD06E1C153F57130D195454A1F94C8C4C20971697093 | |||
| 1116 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Session Storage\LOG.old | text | |
MD5:B2E1E436F8C0098B209AB866ADCDDEC4 | SHA256:6D137151132C6D0847E71AE0438348FB624F4AABFE26228B637153353A266035 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
107
DNS requests
128
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3780 | BANDIZIP-SETUP-STD-ALL.EXE | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?64d61d4d36924ad9 | unknown | — | — | unknown |
3780 | BANDIZIP-SETUP-STD-ALL.EXE | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEBuRJhVl1EslGbwM0iynBP4%3D | unknown | — | — | unknown |
3780 | BANDIZIP-SETUP-STD-ALL.EXE | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | unknown |
3780 | BANDIZIP-SETUP-STD-ALL.EXE | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | unknown |
2280 | └·└█▒╟ ░ⁿ╖├ │╗┐δ┴ñ╕«_240506 ▓└ ╚«└╬╟╧╜├░φ ┴╢─í║╬┼╣╡σ╕│┤╧┤┘1.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?d11ee5be6134aafc | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1116 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
1488 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1488 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1488 | msedge.exe | 204.79.197.203:443 | ntp.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1488 | msedge.exe | 2.17.147.131:443 | assets.msn.com | Akamai International B.V. | CZ | unknown |
1488 | msedge.exe | 18.244.18.38:443 | sb.scorecardresearch.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ntp.msn.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
assets.msn.com |
| whitelisted |
img-s-msn-com.akamaized.net |
| whitelisted |
sb.scorecardresearch.com |
| shared |
th.bing.com |
| whitelisted |
api.msn.com |
| whitelisted |
c.bing.com |
| whitelisted |
c.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1488 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |