| File name: | ________.js |
| Full analysis: | https://app.any.run/tasks/7a47dacb-d6ef-422f-bc13-dff883122d8c |
| Verdict: | Malicious activity |
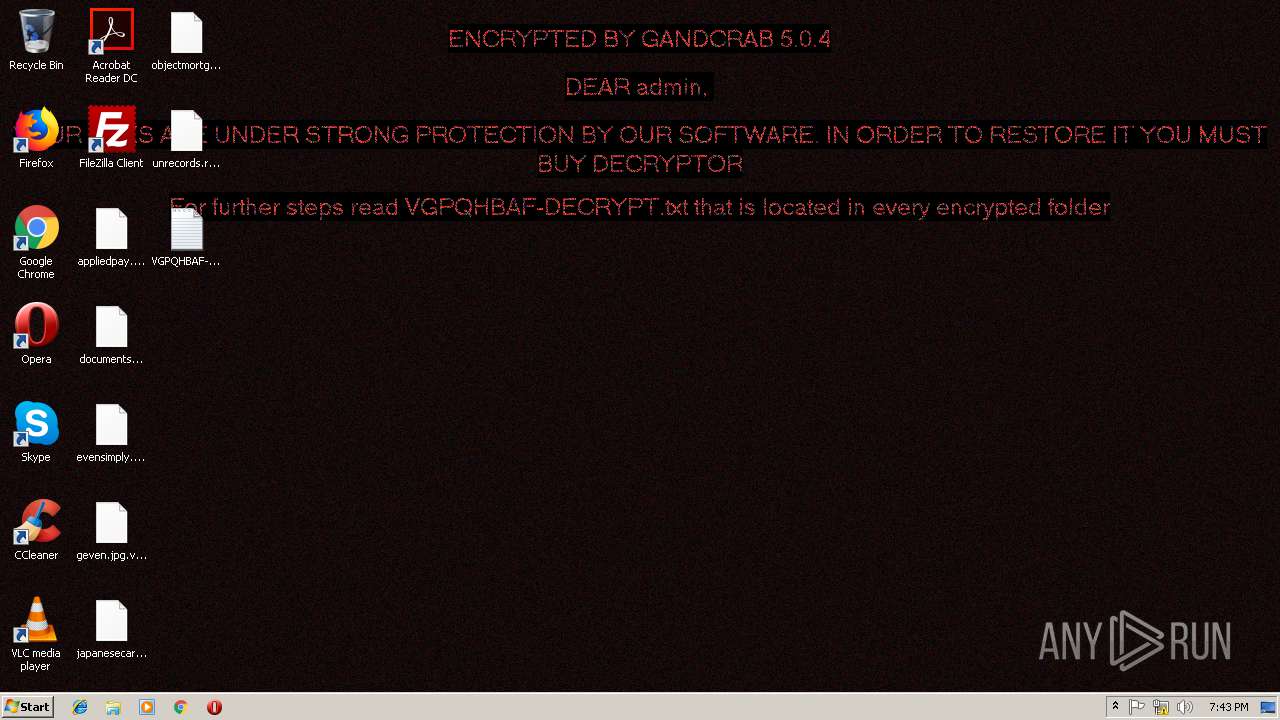
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | December 18, 2018, 19:42:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with CRLF line terminators |
| MD5: | E5C3CCAF61D0E1D1232F2A511AFD91E0 |
| SHA1: | 9686C2A1E066CA2DA50F6F33D359F835D6D74C6B |
| SHA256: | 73C52E33F3B5674AADBFF7ECDA954DA2BE358B003D0F49A83ABA84C16AF561F9 |
| SSDEEP: | 24576:a0Ew/XgLpnH7hIYEoluDWV/m2ja6R/WrPUyaytRMInw76ARzO89EePW5Qp40Pgar:g |
MALICIOUS
Dropped file may contain instructions of ransomware
- powershell.exe (PID: 2172)
Writes file to Word startup folder
- powershell.exe (PID: 2172)
Deletes shadow copies
- powershell.exe (PID: 2172)
GandCrab keys found
- powershell.exe (PID: 2172)
Renames files like Ransomware
- powershell.exe (PID: 2172)
Actions looks like stealing of personal data
- powershell.exe (PID: 2172)
Connects to CnC server
- powershell.exe (PID: 2172)
SUSPICIOUS
Creates files in the user directory
- WScript.exe (PID: 2876)
- powershell.exe (PID: 2172)
Executes PowerShell scripts
- WScript.exe (PID: 2876)
Reads the cookies of Mozilla Firefox
- powershell.exe (PID: 2172)
Creates files like Ransomware instruction
- powershell.exe (PID: 2172)
INFO
Reads settings of System Certificates
- powershell.exe (PID: 2172)
Dropped object may contain TOR URL's
- powershell.exe (PID: 2172)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
35
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2172 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass -Command "IEX (([System.IO.File]::ReadAllText('C:\Users\admin\AppData\Roaming\tnqalxuybs.log')).Replace('?',''));" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WScript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2764 | "C:\Windows\system32\wbem\wmic.exe" shadowcopy delete | C:\Windows\system32\wbem\wmic.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 2147749908 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2876 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\________.js" | C:\Windows\System32\WScript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
412
Read events
322
Write events
90
Delete events
0
Modification events
| (PID) Process: | (2876) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2876) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2172) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2172) powershell.exe | Key: | HKEY_CURRENT_USER\Software\ex_data\data |
| Operation: | write | Name: | ext |
Value: 2E00760067007000710068006200610066000000 | |||
| (PID) Process: | (2172) powershell.exe | Key: | HKEY_CURRENT_USER\Software\keys_data\data |
| Operation: | write | Name: | public |
Value: 0602000000A400005253413100080000010001001B604C7BCEDBA8F3CCCF837C75D0218DB31D2FB19B28E21D004E074139065AAFCBB6AAAF85CB99C040A5CDDE10B66EAC77C4717D1F8A2B914E69F5F1F094F27C282C9CB7424DCCE6A713AEB8AE4049F10B352C7D8AF4C2E62B6DA27054D69AAE7504C45042810CF6F78C131565932947B74D2559D9E202229E6508EA094DCB8DE1C06793180A3C2F89E715920D1827DFFF2E4A072FBE64F2B8884708E1B577496C09F7BBD575F2E8D726E3853570377DF4F51B9AEA2E14AC46CD75215498A37F671B1A5542B3422374B187B75698AE82530C3BD5DBCCE28DB0D884B7FEC8BD3080EC6F09B55072E0A9D67B0F82D1BEC6CE8C14BBB076A52523E56E128AC113E9 | |||
| (PID) Process: | (2172) powershell.exe | Key: | HKEY_CURRENT_USER\Software\keys_data\data |
| Operation: | write | Name: | private |
Value: 94040000C05C3F17AD625F93F6D10F52547EF01927F671D22D582E1268CA64951169BD9879563CB9771FE35642D314BFF0023F7D78D649C60063FE38017C13FD46F2FB40AFEA9408360E3DA75C98DA1B0FD35DCBB36B4F37855BEB5A2640D1A20A43ACC0B8911FF3B8C219E433356A824842E84C7F057B9F7E6BAFE17EC79E2345E6190CC228A7F015266514F4CC350E703EA173453E74F79ADAF51C6342B043F3DADA9DFA78AACF1FFE7387AD26A70A6E2AD12B8F84947F896ABD9614E17FACACF8BA7088F813448A89EE70A18D9745C68394259A5101DD498B9683B299E46628AD0750DE11893FFEF809D2809E849678C3A3EFB5EF4BC3E53D6BA6CF4718A5E2A62B8D829CFDD542D976965BFE348EF075607C5B6698F6AA5ABF4D0DC6111C9044D3E887B0F9660B52F307266A75DE8224E3882E336E73940B60A345223F51C5B2CED6EBFC4D48A12E8FD0CBC6776E113BC875C0276D7871AAB6C2DE61B7B0E134B813E929301B87C0085B9B4965F864EFC5A2BB0125DE75EA3C998628331F013D82D6105267B29351FB22517C676F29F3217E6CF83D41BAB3DA73A42C54A0E06366093F6BC482A8347260A2C2E3F96DF4FC5BA729D6F6EEAC9B86B598DCBCDF9636F97C94CD889E95B177818744D230ECB429C09282AB5EACBBCB644022AAE4781B77ACC0D8A8F7791F589D25BB243359FF388D927E73C8C6CF9146725F404536BC19C477993D46798CBF3F9C480EC074636A62F46F386D53CCD207A2EE7998ECAD4799A61ED8D90EF8A5CCF623E81AE2E01B0414BECDE8E0E738F3100093C9A1E949068F14EA89811E0D756438708D0ABE5A493782CA704B7F5881B211310FE8DB24059091CB6948B8B33A747C198D3F4D8C5F2AC7C7E26905680080CB23C58134496E8DBE48302BD21CE4BD049803C281F243488846735617D0808531B4F32CA8AF862F2E22954C3207074DA07CB683EC20A21365C241B7BACD1152931AA72DAC717993C5A15E29C4BFFE1518A769B8C08EF79EB37C90344B6EDC805D0E8B0B346FE599515AA5479A92F8C14E22ABF6C19E9B091C49427DA1BA71DAB139ED473854C35480BB920854C86E84F4BAC29063E46A6012118735BBFADD5EA2F7A77808B8B0AB868C4DD0D29D3EC3BC4A43D95DB4851AAD46118EACED8275D3E9C2450EBB0CA110734CCF5E40ED1E3DCFCAF878BAFEDF692158EA684EE849C819C604E8CAD74B31FD74EB44D4DFA7102DCEC7CF2BBF94762EF98770110C95AA116B53568105A8B624763375750416B9CDC71582E61AC75E81AD86568C05F61301CF39F9356CC7A3DF5C74F949B22825A4CC7C153B5FC7D8B4D6601B7FD5EB5DA035FABDFA346D793CFBCC416D1B832930A44006F5A0B87D7F2666F88127BDF9264AC3E12203D3CD5E74EE235181479F478079F5AA066232CD0D58EB7A6EA939863C502C41D06553E0147F2BB2A56BA4FFB0D98E004C0AED88C703157DE88173405D1F0E17FA0B2E9701975D91AA24C90B6B0AAE1EB721689801E7719A6C4257DF4B85DD1674A70099355DBBFFEBC4A9A8D97C395DBF8A7A6A71959C95C30518DFFC53E6406C6FAA708BE1BCB4082E47544609D1640E1B0C9689C3CEDC70C9D03A3DDFA1424A3E65023054F5F350327BFC8D2265FB5877DB4445E66B49ADC7C7CAD14A7DA554B89DA8475D050FB9C755CA9BF2A3C3F678BB0AEE280D49F2AFDC8AF5159A5A846477DA5E68A6877EBA5784036E43EF4A661F35C245C8A4A93AB47198C31A8B6B3440906A651E721B9565CD1CAEEFCD4DE15D81FE8EA34445FC8EB2B383B9EE46698D1D4C40EBB1B02CC64BA190555D75E59DBFAB4C25AF21D8402311A8437A20E8D0A5B00FC143B9F0C2213FAC639AE66392557B6778DF9B4F57B4FEBFD381B5A29BBA6661A571363A11D34649C18F03F6CC986FE9BDD576A8DBE94B83ACE976DE6ACAE5457C78502864EE39C33CDE20B239F8DA9948367CA5E7E7208AB1D447E4145CDD9609F2CACE2F763A06E938451ABC1A36F0A44639F48B52B750BB85265EC4B0CF495B8532B07D6F732B6A2BFB557320CA178DA1B939A871C2C4D9F3606442ED025AD2B0E8091732D669976834BB75B5574C7F88ABF49BAB5BC022AB48F21B7AF8566EF01F510B22CB4215A2109417CDAB9FC27E6465E3D4E725AF924BA4EC461D8E313B25F4F8858A328B3B84FC7E21837B982B2472259E61CC2467AF34CDBAF49655B3BCDED91B560A90F916D3F104428B1636CA113DDFDAA0D4C6AD073CCFB6890A6C3AE1AE8A5C67D71F01DD4029D7798D5A62F1F99DBAF7D9468E51908E70959C05865D465B6D354DBF01AC681DC243E5DE580F0671A5CDE1B0FB69CB27C6B238E249938D30A2AACB5C7D5B195B | |||
| (PID) Process: | (2172) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2172) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2172) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2172) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
0
Suspicious files
277
Text files
227
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2172 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\2B7SAGQGF5BPR1JLS6VH.temp | — | |
MD5:— | SHA256:— | |||
| 2172 | powershell.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | — | |
MD5:— | SHA256:— | |||
| 2172 | powershell.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\GlobData | — | |
MD5:— | SHA256:— | |||
| 2172 | powershell.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\GlobSettings | — | |
MD5:— | SHA256:— | |||
| 2172 | powershell.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\addressbook.acrodata | — | |
MD5:— | SHA256:— | |||
| 2172 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2172 | powershell.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\CRLCache\0FDED5CEB68C302B1CDB2BDDD9D0000E76539CB0.crl | — | |
MD5:— | SHA256:— | |||
| 2172 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF19a04d.TMP | binary | |
MD5:— | SHA256:— | |||
| 2172 | powershell.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\CRLCache\CE338828149963DCEA4CD26BB86F0363B4CA0BA5.crl | — | |
MD5:— | SHA256:— | |||
| 2172 | powershell.exe | C:\Users\admin\AppData\VGPQHBAF-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
82
TCP/UDP connections
143
DNS requests
66
Threats
38
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2172 | powershell.exe | GET | — | 217.26.53.161:80 | http://www.haargenau.biz/ | CH | — | — | malicious |
2172 | powershell.exe | GET | — | 136.243.13.215:80 | http://www.holzbock.biz/ | DE | — | — | suspicious |
2172 | powershell.exe | GET | 302 | 192.185.159.253:80 | http://www.pizcam.com/ | US | — | — | malicious |
2172 | powershell.exe | GET | 301 | 83.138.82.107:80 | http://www.swisswellness.com/ | DE | — | — | whitelisted |
2172 | powershell.exe | GET | — | 212.59.186.61:80 | http://www.hotelweisshorn.com/ | CH | — | — | malicious |
2172 | powershell.exe | GET | — | 78.46.77.98:80 | http://www.2mmotorsport.biz/ | DE | — | — | suspicious |
2172 | powershell.exe | GET | — | 83.166.138.7:80 | http://www.whitepod.com/ | CH | — | — | whitelisted |
2172 | powershell.exe | GET | 301 | 104.24.22.22:80 | http://www.belvedere-locarno.com/ | US | — | — | shared |
2172 | powershell.exe | GET | 301 | 80.244.187.247:80 | http://www.hotelfarinet.com/ | GB | — | — | malicious |
2172 | powershell.exe | GET | — | 217.26.53.37:80 | http://www.hrk-ramoz.com/ | CH | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2172 | powershell.exe | 78.46.77.98:80 | www.2mmotorsport.biz | Hetzner Online GmbH | DE | suspicious |
2172 | powershell.exe | 217.26.53.161:80 | www.haargenau.biz | Hostpoint AG | CH | malicious |
2172 | powershell.exe | 74.220.215.73:80 | www.bizziniinfissi.com | Unified Layer | US | malicious |
2172 | powershell.exe | 136.243.13.215:80 | www.holzbock.biz | Hetzner Online GmbH | DE | suspicious |
2172 | powershell.exe | 138.201.162.99:443 | www.fliptray.biz | Hetzner Online GmbH | DE | malicious |
2172 | powershell.exe | 138.201.162.99:80 | www.fliptray.biz | Hetzner Online GmbH | DE | malicious |
2172 | powershell.exe | 192.185.159.253:443 | www.pizcam.com | CyrusOne LLC | US | malicious |
2172 | powershell.exe | 192.185.159.253:80 | www.pizcam.com | CyrusOne LLC | US | malicious |
2172 | powershell.exe | 83.138.82.107:80 | www.swisswellness.com | hostNET Medien GmbH | DE | suspicious |
2172 | powershell.exe | 212.59.186.61:80 | www.hotelweisshorn.com | green.ch AG | CH | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.2mmotorsport.biz |
| unknown |
www.haargenau.biz |
| unknown |
www.bizziniinfissi.com |
| malicious |
www.holzbock.biz |
| unknown |
www.fliptray.biz |
| malicious |
www.pizcam.com |
| unknown |
www.swisswellness.com |
| whitelisted |
www.hotelweisshorn.com |
| unknown |
www.whitepod.com |
| whitelisted |
www.hardrockhoteldavos.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | powershell.exe | A Network Trojan was detected | ET TROJAN [eSentire] Win32/GandCrab v4/5 Ransomware CnC Activity |
2172 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
2172 | powershell.exe | A Network Trojan was detected | ET POLICY Data POST to an image file (jpg) |
2172 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
2172 | powershell.exe | A Network Trojan was detected | ET POLICY Data POST to an image file (gif) |
2172 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
2172 | powershell.exe | A Network Trojan was detected | ET POLICY Data POST to an image file (jpg) |
2172 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
2172 | powershell.exe | A Network Trojan was detected | ET POLICY Data POST to an image file (jpg) |
2172 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |