| File name: | ATLauncher.exe |
| Full analysis: | https://app.any.run/tasks/580a78d4-5dc7-40b6-80ce-81025ebd20c0 |
| Verdict: | Malicious activity |
| Analysis date: | March 04, 2024, 20:02:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows |
| MD5: | F09A1D73ABC2F425F7544BBF7EA5AA42 |
| SHA1: | 40282F8210619ADECA62B4FC710F257072BD8F42 |
| SHA256: | 73BB616FC4FDAD4EE3BE7B449DE0D07F3769A2F5F0BE639F08E1867528C30106 |
| SSDEEP: | 98304:JS9gb3OpdC6RpCE5xDNelTy9rjlPFKK6mIBAMrqQPH8Fw44BbHwAhShCNmWnAyzx:4DlQMa+Ph+e8hYNVKC0iSG5d+ |
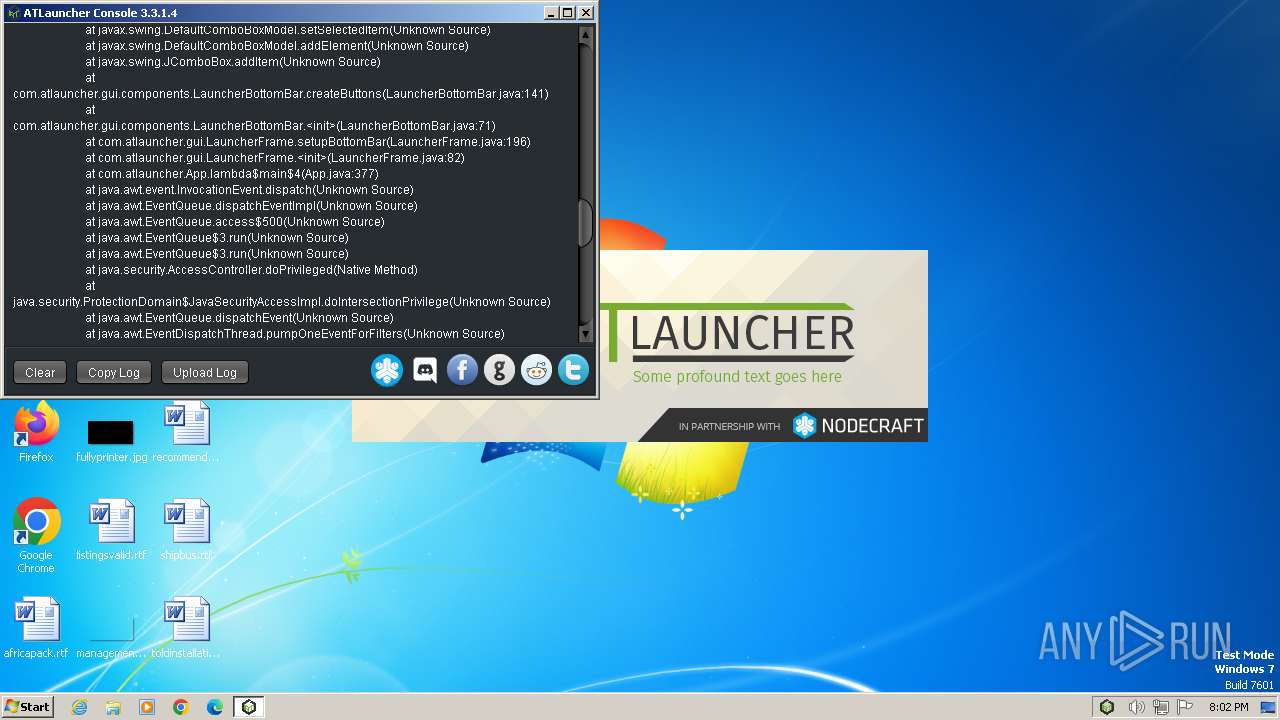
MALICIOUS
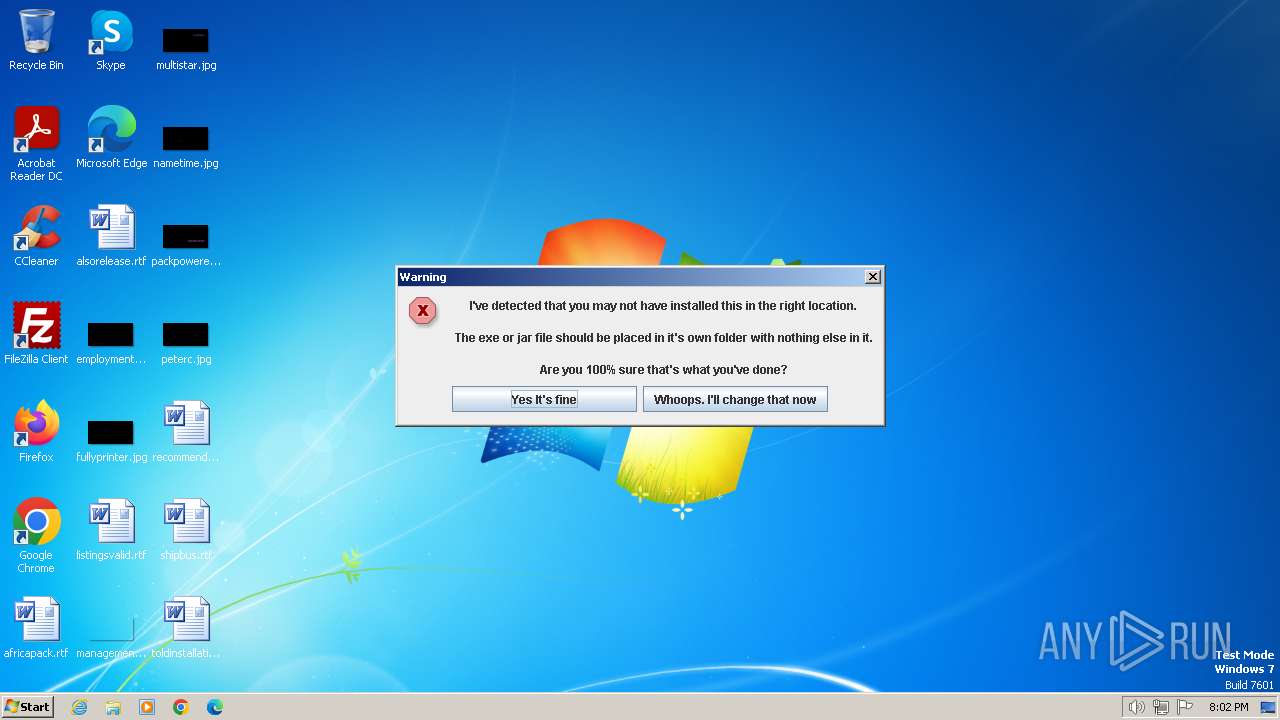
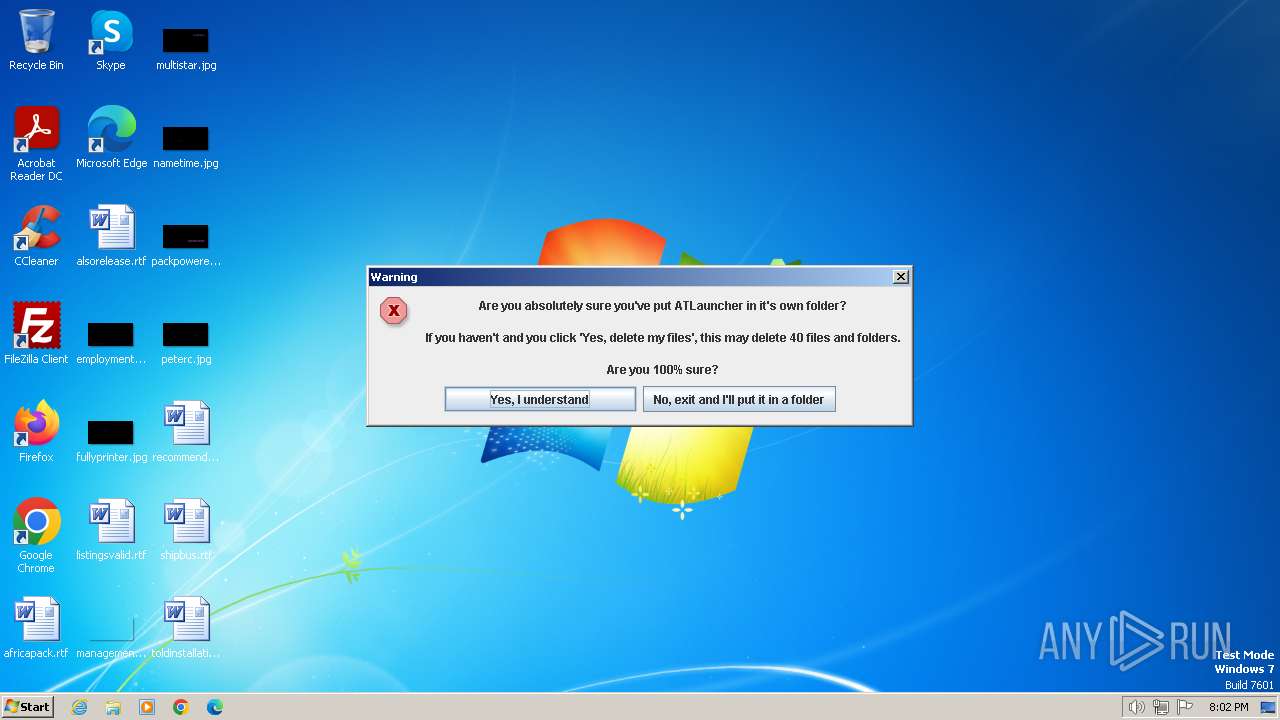
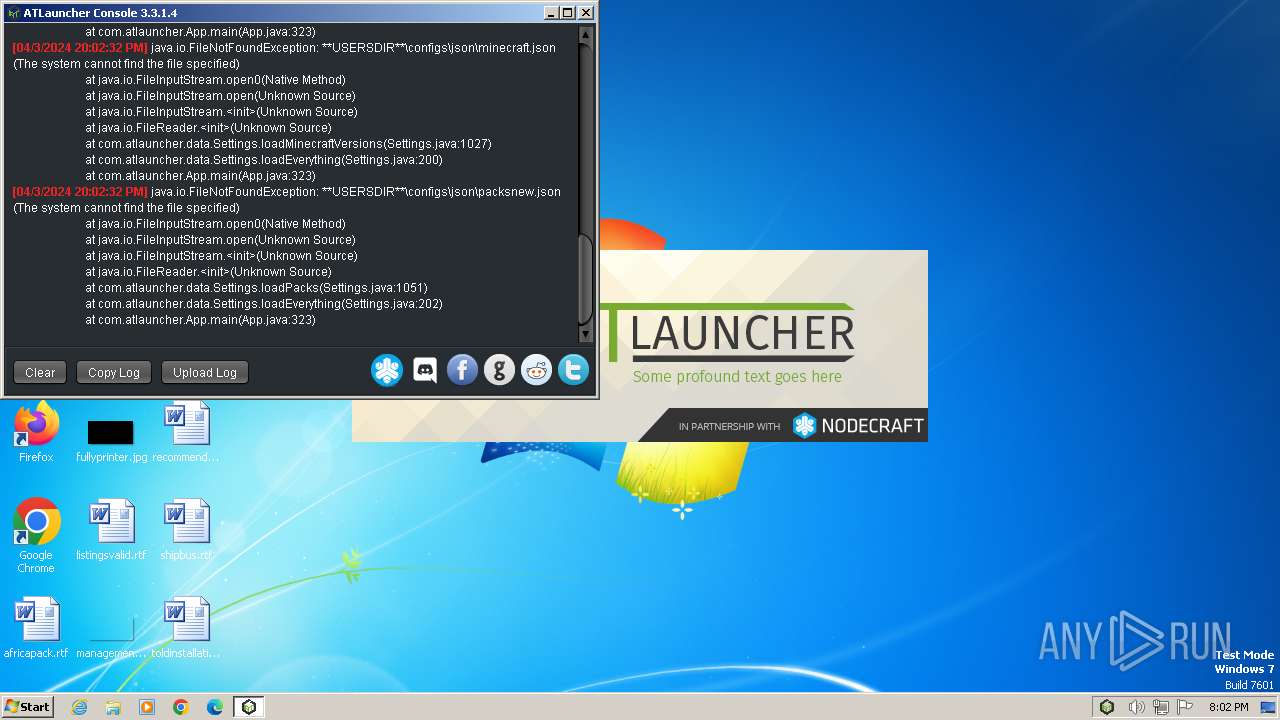
Drops the executable file immediately after the start
- ATLauncher.exe (PID: 1432)
- javaw.exe (PID: 3916)
Actions looks like stealing of personal data
- javaw.exe (PID: 3916)
SUSPICIOUS
Checks for Java to be installed
- ATLauncher.exe (PID: 1432)
- javaw.exe (PID: 3916)
Application launched itself
- javaw.exe (PID: 3916)
Executable content was dropped or overwritten
- javaw.exe (PID: 3916)
INFO
Checks supported languages
- javaw.exe (PID: 3916)
- ATLauncher.exe (PID: 1432)
- java.exe (PID: 3464)
- javaw.exe (PID: 3992)
Reads the machine GUID from the registry
- javaw.exe (PID: 3916)
Creates files in the program directory
- javaw.exe (PID: 3916)
Reads the computer name
- javaw.exe (PID: 3916)
Create files in a temporary directory
- javaw.exe (PID: 3916)
- java.exe (PID: 3464)
- javaw.exe (PID: 3992)
Creates files or folders in the user directory
- javaw.exe (PID: 3916)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:08:10 14:53:35+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 2.22 |
| CodeSize: | 19968 |
| InitializedDataSize: | 379392 |
| UninitializedDataSize: | 36864 |
| EntryPoint: | 0x1290 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.1 |
| ProductVersionNumber: | 0.0.0.1 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Windows NT |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | - |
| FileDescription: | ATLauncher |
| FileVersion: | unspecified |
| InternalName: | ATLauncher |
| LegalCopyright: | unknown |
| LegalTrademarks: | - |
| OriginalFileName: | ATLauncher-3.3.1.4.exe |
| ProductName: | ATLauncher |
| ProductVersion: | unspecified |
Total processes
45
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
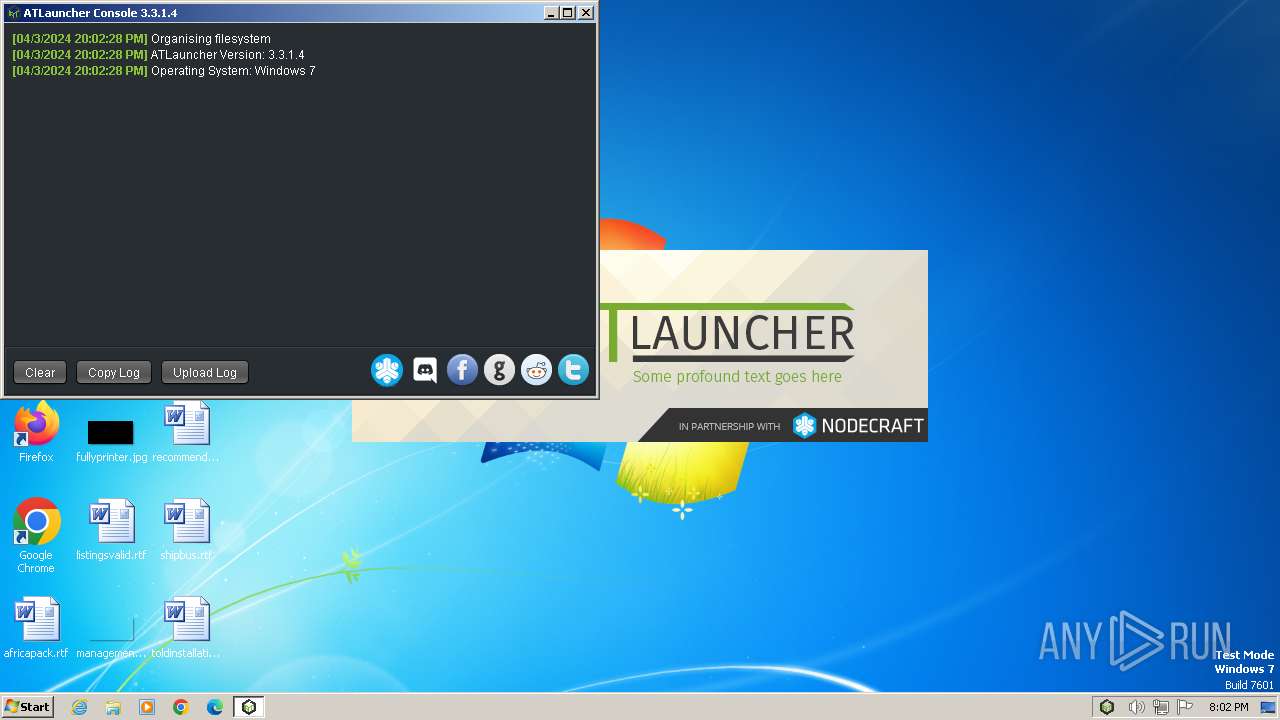
| 1432 | "C:\Users\admin\AppData\Local\Temp\ATLauncher.exe" | C:\Users\admin\AppData\Local\Temp\ATLauncher.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: ATLauncher Exit code: 0 Version: unspecified Modules
| |||||||||||||||
| 2488 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3464 | "C:\Program Files\Java\jre1.8.0_271\bin\java.exe" -version | C:\Program Files\Java\jre1.8.0_271\bin\java.exe | — | javaw.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 3736 | C:\Windows\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3916 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -Xms122m -Xmx1024m -Djna.nosys=true -classpath "C:\Users\admin\AppData\Local\Temp\ATLauncher.exe;lib\ATLauncher-3.3.1.4.jar;lib\authlib-1.5.21.jar;lib\gson-2.8.5.jar;lib\xz-1.8.jar;lib\base64-2.3.9.jar;lib\discord-rpc-1.6.2.jar;lib\jopt-simple-5.0.4.jar;lib\zt-zip-1.13.jar;lib\google-analytics-java-2.0.8.jar;lib\okhttp-4.0.1.jar;lib\sentry-1.7.24.jar;lib\gettext-lib-1.1.0.jar;lib\log4j-core-2.12.0.jar;lib\log4j-api-2.12.0.jar;lib\murmur-1.0.0.jar;lib\commons-lang3-3.9.jar;lib\guava-17.0.jar;lib\httpclient-4.5.9.jar;lib\commons-codec-1.11.jar;lib\jsr305-2.0.1.jar;lib\commons-io-2.4.jar;lib\jcl-over-slf4j-1.7.26.jar;lib\slf4j-api-1.7.26.jar;lib\okio-2.2.2.jar;lib\kotlin-stdlib-1.3.40.jar;lib\jackson-core-2.9.9.jar;lib\antlr4-runtime-4.7.2.jar;lib\kotlin-stdlib-common-1.3.40.jar;lib\annotations-13.0.jar;lib\httpcore-4.4.11.jar;lib\antlr4-annotations-4.7.2.jar" com.atlauncher.App | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | ATLauncher.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 3992 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw" -version | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | javaw.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
Total events
4 837
Read events
4 832
Write events
5
Delete events
0
Modification events
| (PID) Process: | (3916) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: javaw.exe | |||
| (PID) Process: | (3916) javaw.exe | Key: | HKEY_CLASSES_ROOT\discord-589393213723246592 |
| Operation: | write | Name: | URL Protocol |
Value: | |||
| (PID) Process: | (2488) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: DllHost.exe | |||
| (PID) Process: | (2488) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows Photo Viewer\Viewer |
| Operation: | write | Name: | MainWndPos |
Value: 6000000034000000A00400008002000000000000 | |||
Executable files
2
Suspicious files
0
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3916 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio2075295781685918579.tmp | image | |
MD5:57A31A42B8A13B28300789A085AD4E22 | SHA256:8F1D849195F570C81AA884C80417B1948883B63DB2DBC948254700FB111E266C | |||
| 3916 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio7838225028412075250.tmp | image | |
MD5:F4296034AFAB0DF957A87D611327F2F5 | SHA256:0FD6EE39CB2C3B590FBD621A82A4569BA7F5E3501AA1D335E1087563928FD50F | |||
| 3916 | javaw.exe | C:\Users\admin\AppData\Local\Temp\cache\journal.tmp | text | |
MD5:37E8E716E0E2F4A0B05CD9571D95B84D | SHA256:7080CB592D5149C858B206D3FD0D5E3E7D601F120AF00B2616BEE928EE1291CA | |||
| 3916 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio7938849149052596813.tmp | image | |
MD5:641424C14B17F9AE9DD08A5F7CCFF1B6 | SHA256:15A3967E51E7CE93C89B0703898E73CC32528A1BC4AED31E6E9AB5F50E987471 | |||
| 3916 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio7369240680393546689.tmp | image | |
MD5:83F562420E05BB9336A31F849574E258 | SHA256:33AFBDF1FEFF949B4BE7B8873A32DC0284CDEE894E1407982EF40DECE428B1CB | |||
| 3916 | javaw.exe | C:\Users\admin\AppData\Local\Temp\configs\ATLauncher.conf | text | |
MD5:632F2ACA627BC4D788F0D5FF0F21967B | SHA256:A3494E6AD4AC3DFC6D79687AF5AFE9522A37D701AE3B6A0C22F1FFA0A726F826 | |||
| 3916 | javaw.exe | C:\Users\admin\AppData\Local\Temp\discord-rpc\discord-rpc.dll | executable | |
MD5:B6FD682381B825D2CEBA5995C296DDE3 | SHA256:EF7404768C7183BDCE9E46666A121A89B77BE40060D0AEA4D67804CF0E5CE6D8 | |||
| 3916 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio4486507753149980475.tmp | image | |
MD5:57A31A42B8A13B28300789A085AD4E22 | SHA256:8F1D849195F570C81AA884C80417B1948883B63DB2DBC948254700FB111E266C | |||
| 3916 | javaw.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:E178ECC3A476A31FAFFC30612CA89FFA | SHA256:83E551EC0684E95D4E392431373EF12732F30B129F54D9069FD936C52B5BDC8D | |||
| 3916 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio8075605295004731670.tmp | image | |
MD5:57A31A42B8A13B28300789A085AD4E22 | SHA256:8F1D849195F570C81AA884C80417B1948883B63DB2DBC948254700FB111E266C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
17
DNS requests
4
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
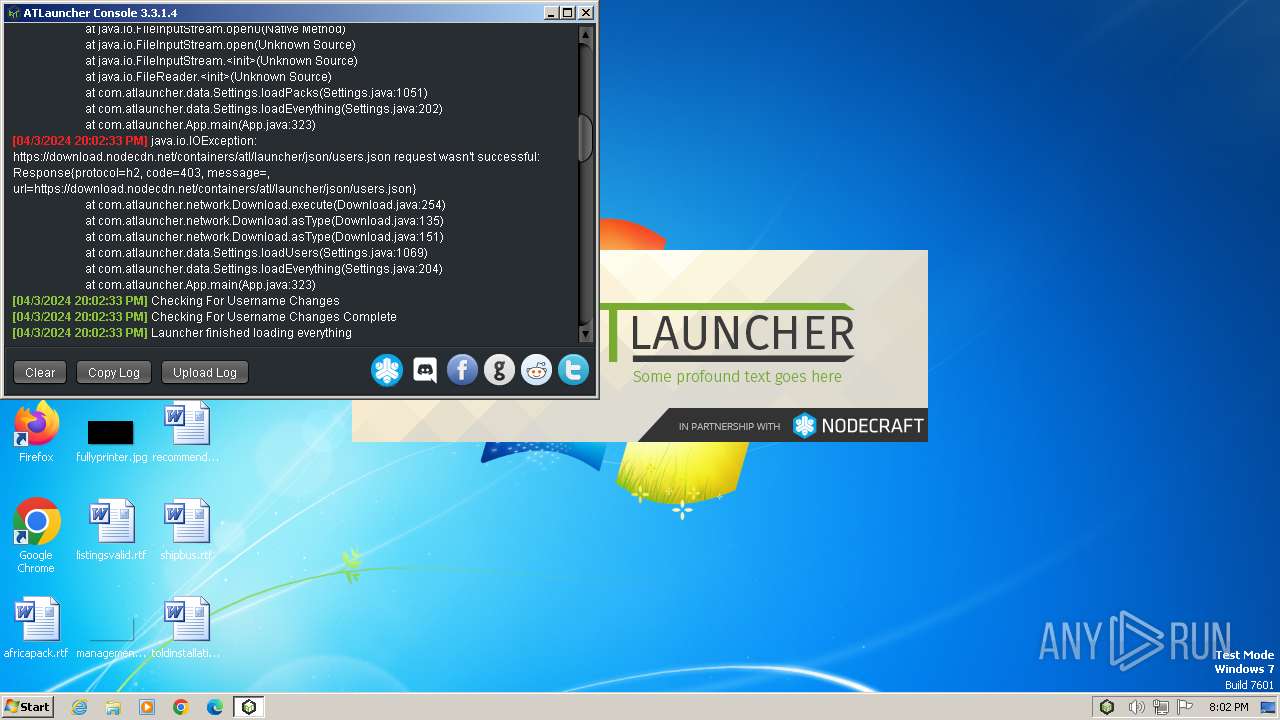
3916 | javaw.exe | 104.22.69.118:443 | download.nodecdn.net | CLOUDFLARENET | — | unknown |
3916 | javaw.exe | 35.186.247.156:443 | sentry.io | GOOGLE | US | unknown |
3916 | javaw.exe | 188.114.96.4:443 | api.atlauncher.com | CLOUDFLARENET | NL | unknown |
3916 | javaw.exe | 142.250.181.238:443 | www.google-analytics.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download.nodecdn.net |
| unknown |
sentry.io |
| whitelisted |
api.atlauncher.com |
| unknown |
www.google-analytics.com |
| whitelisted |