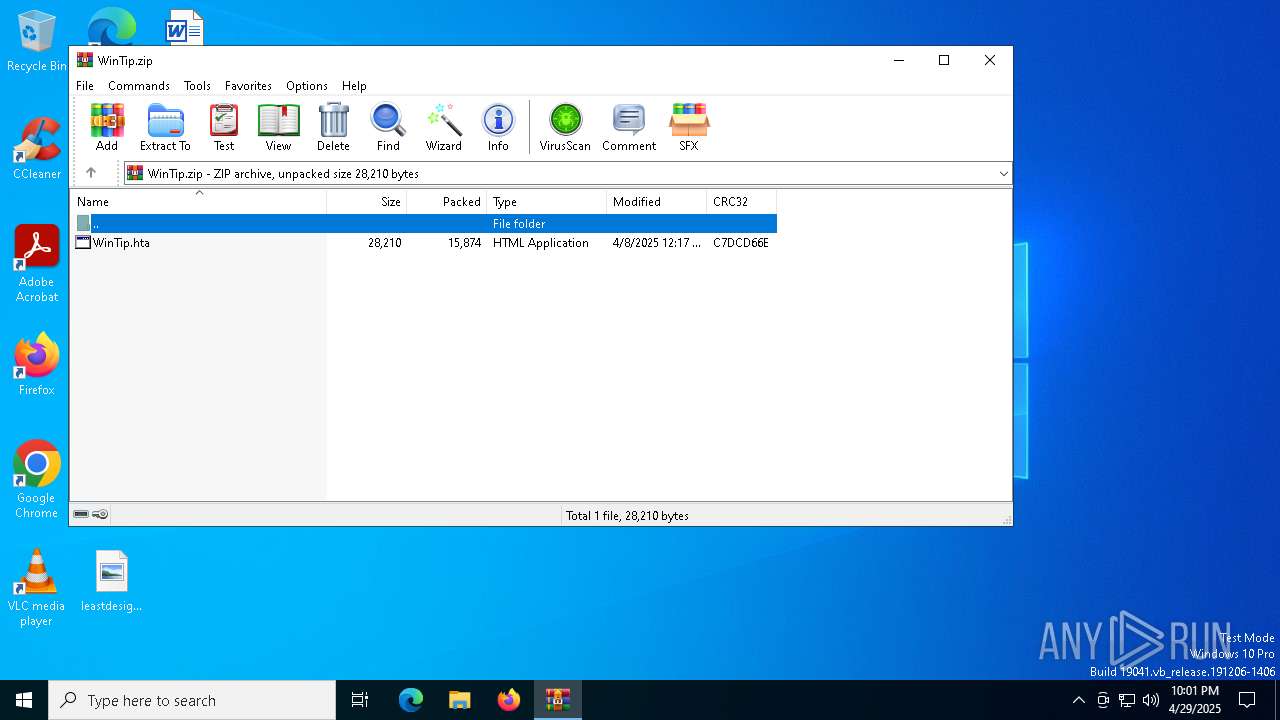
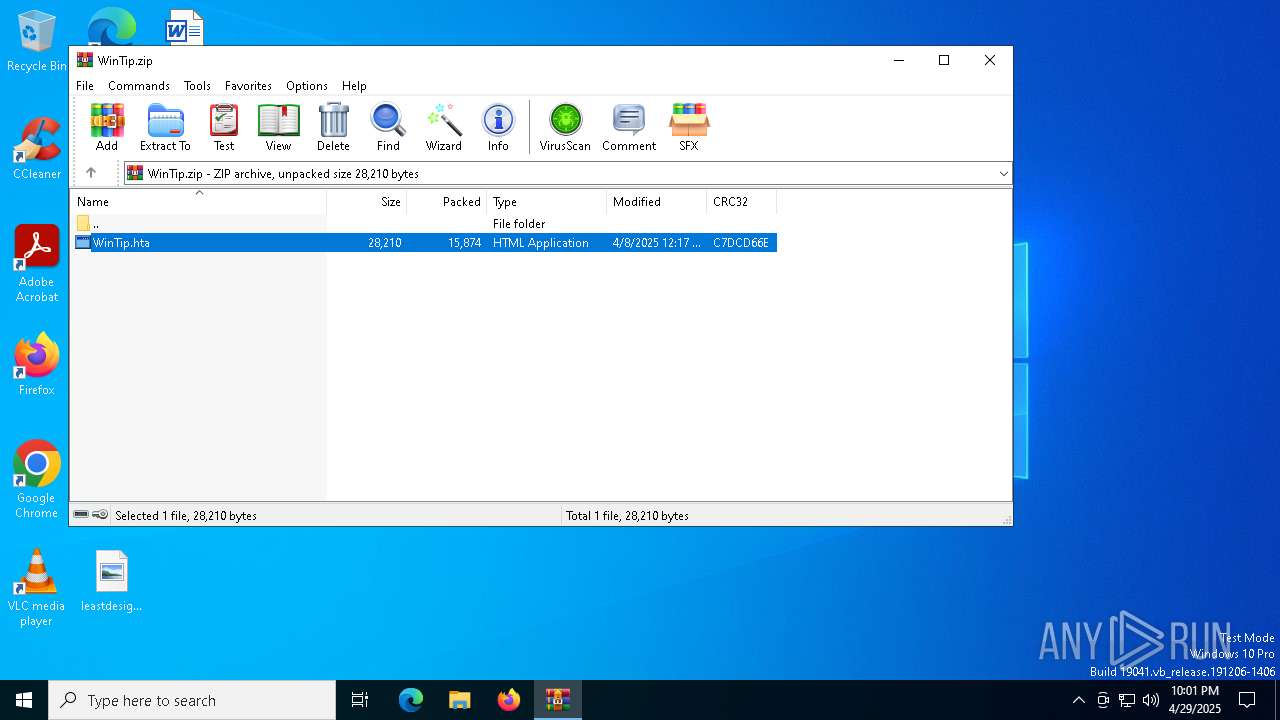
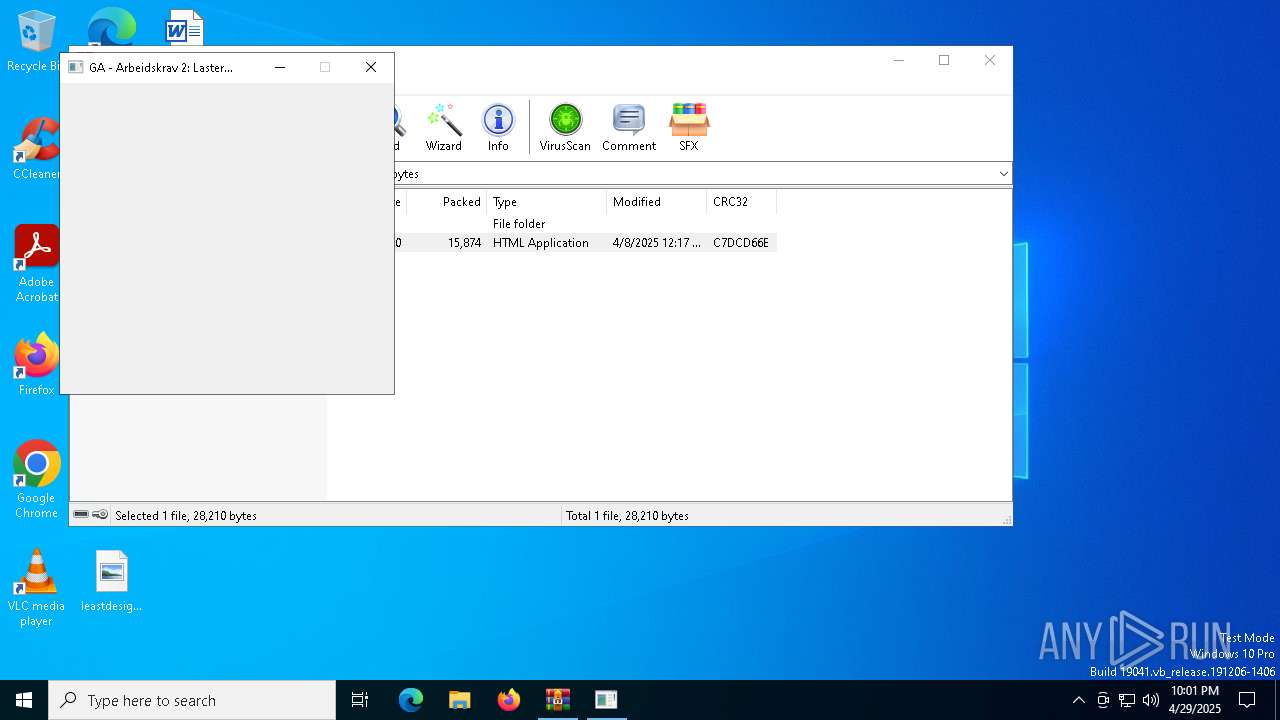
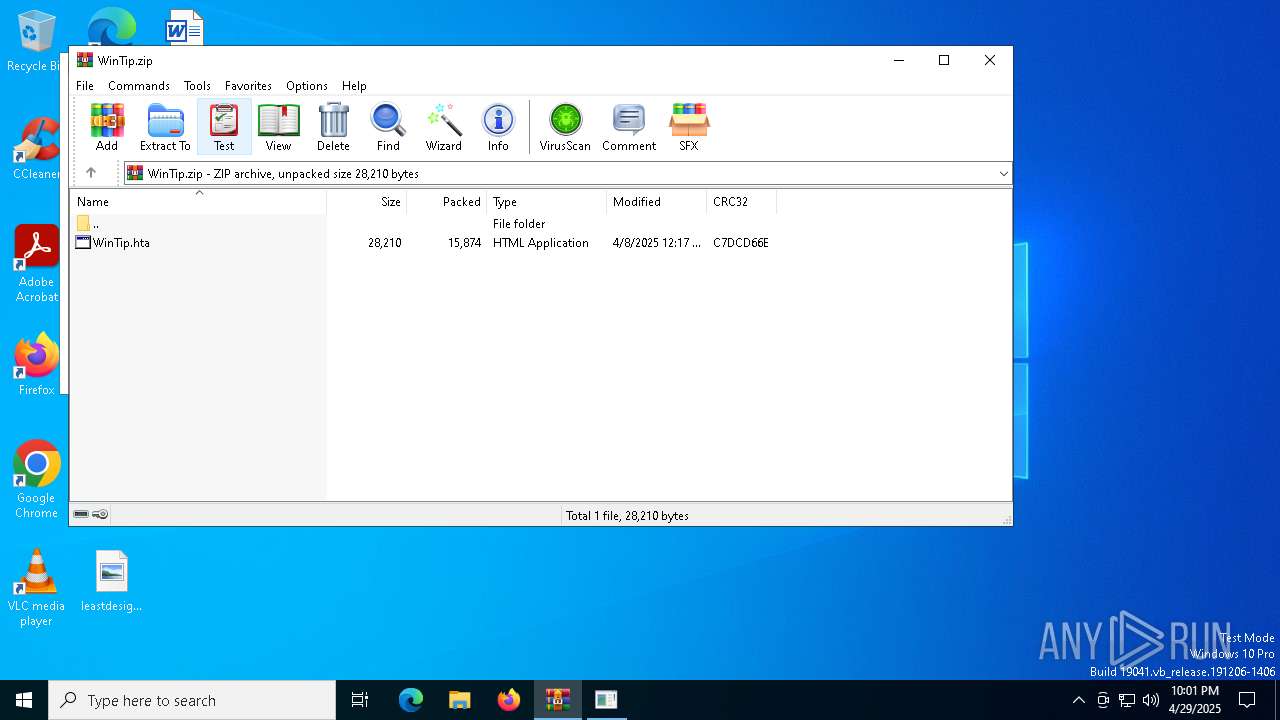
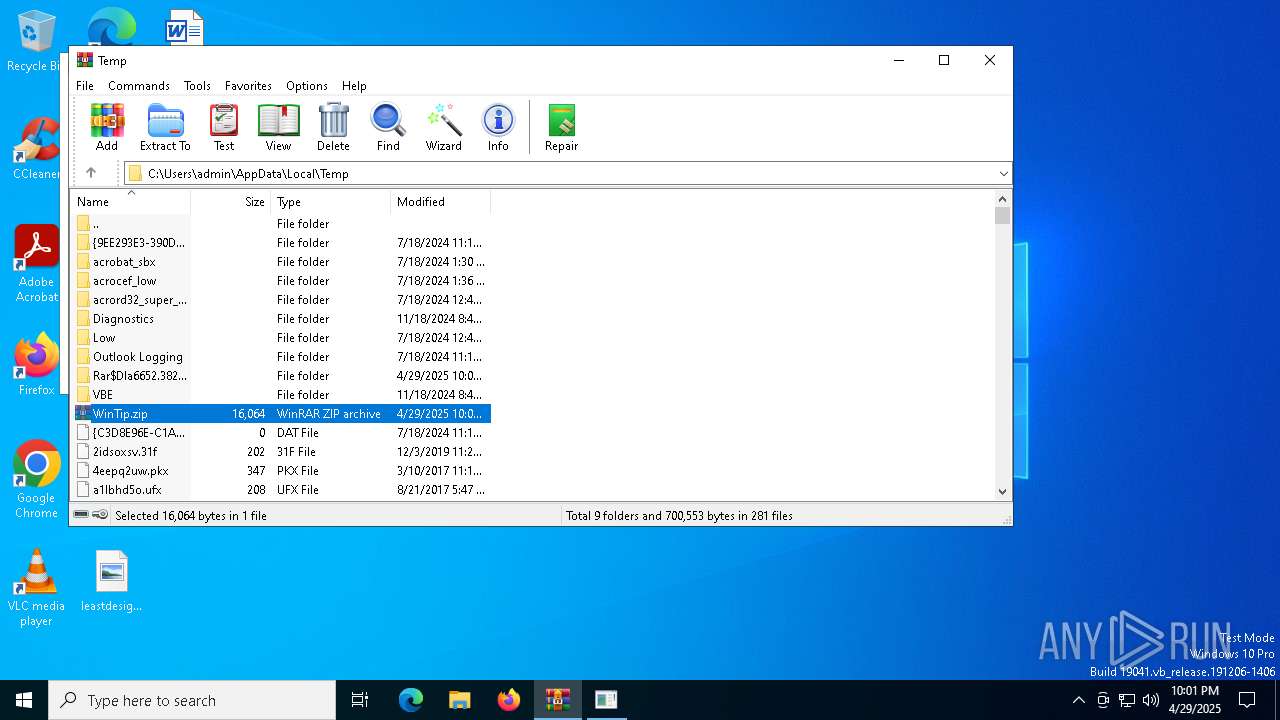
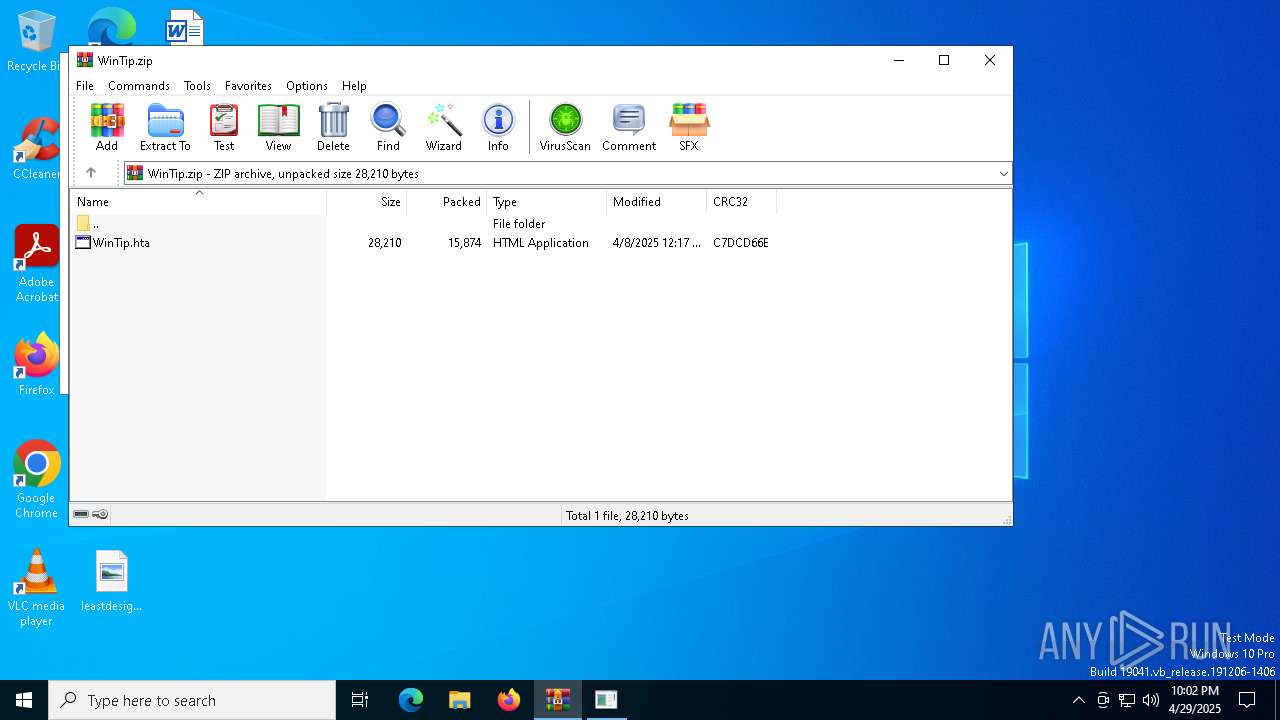
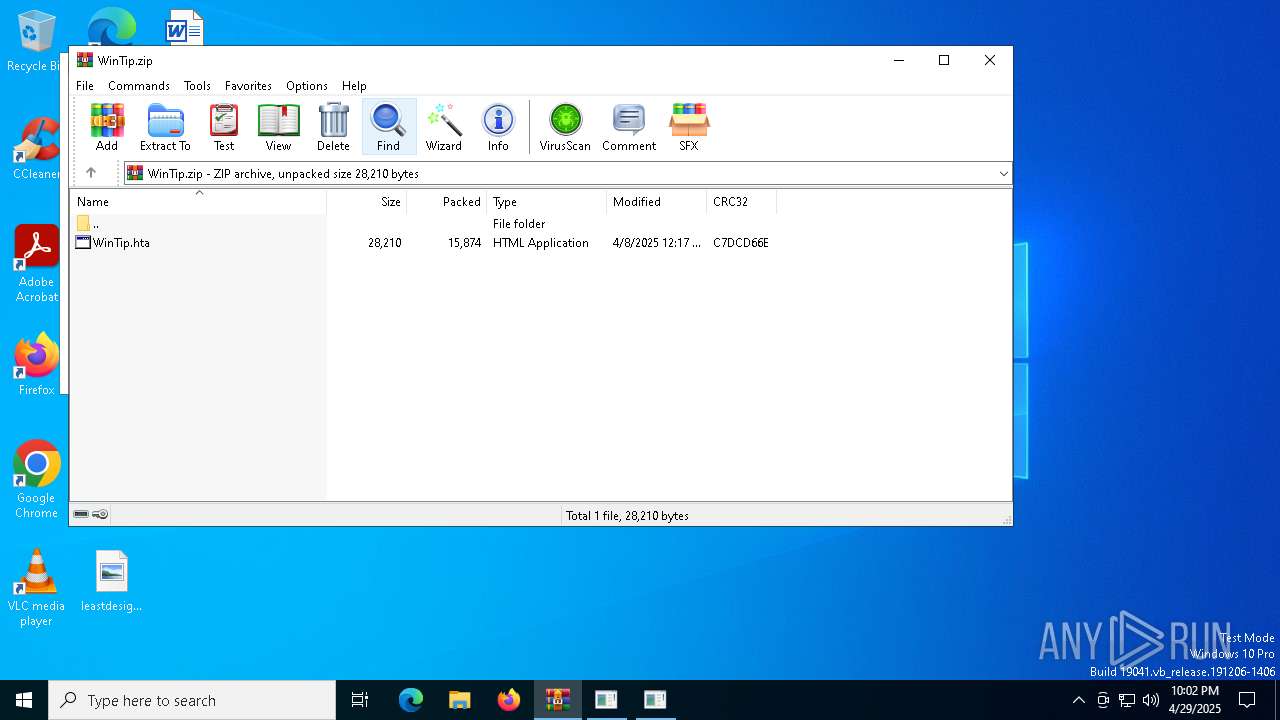
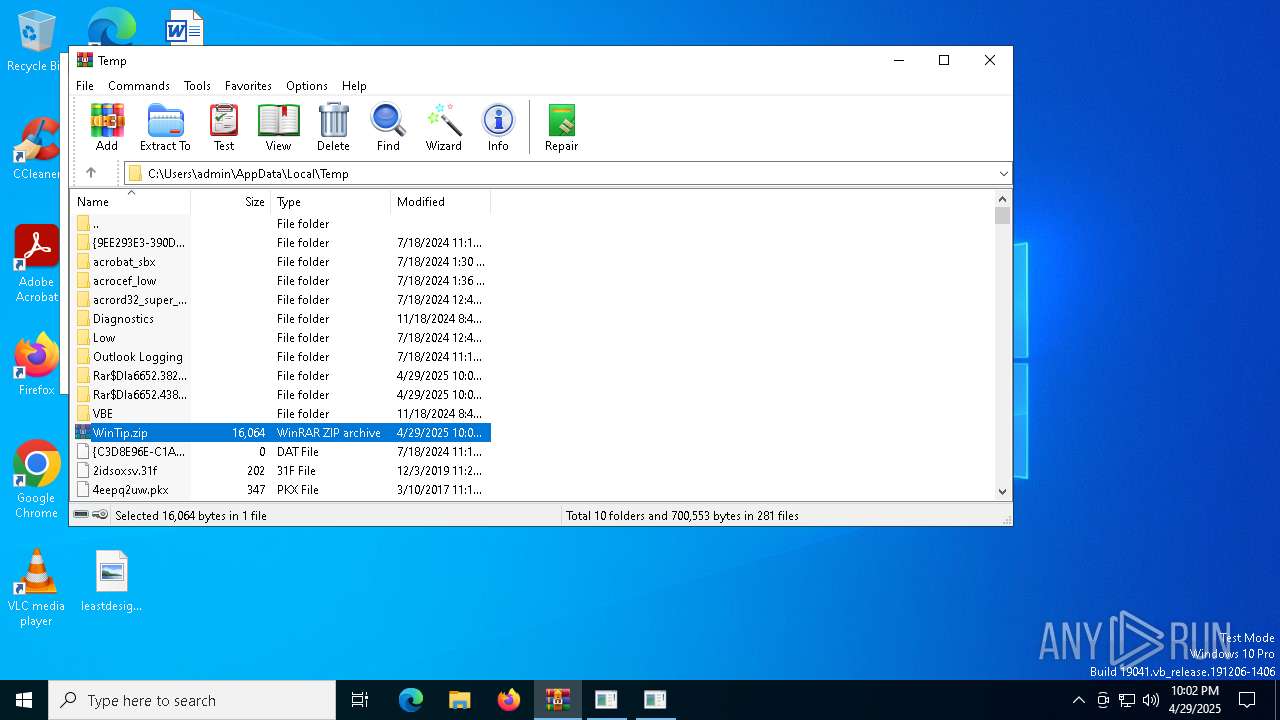
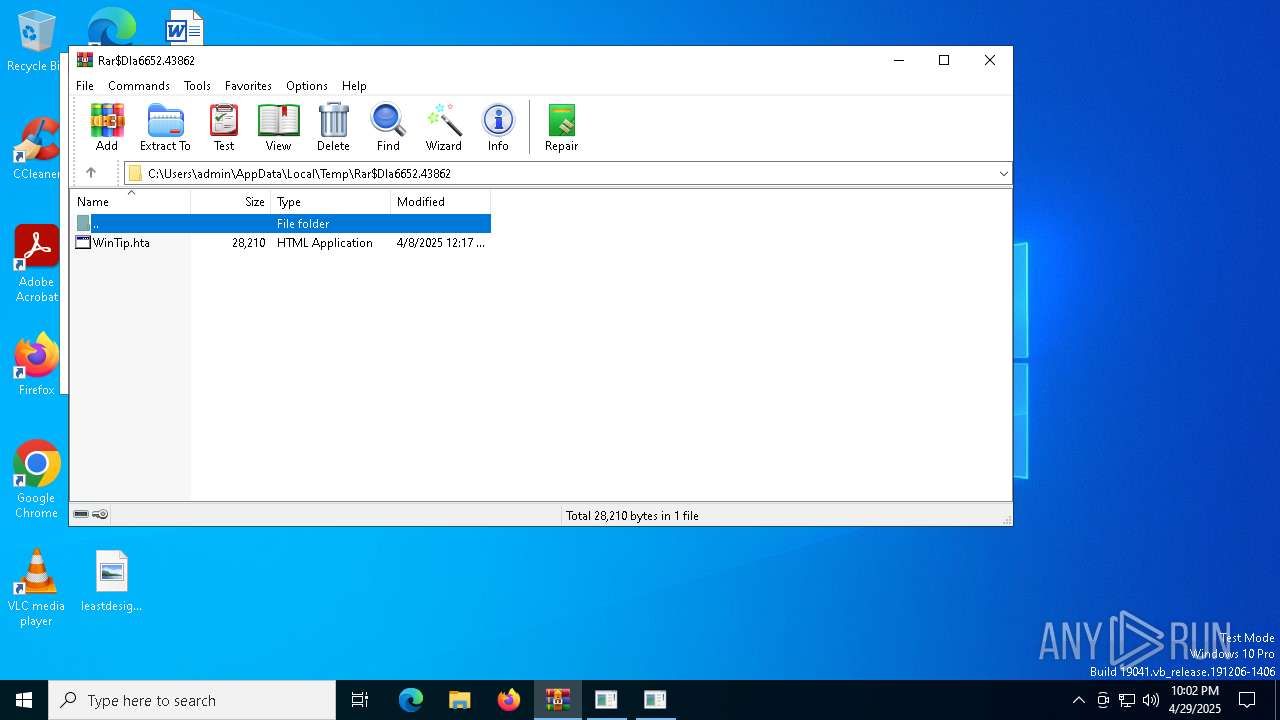
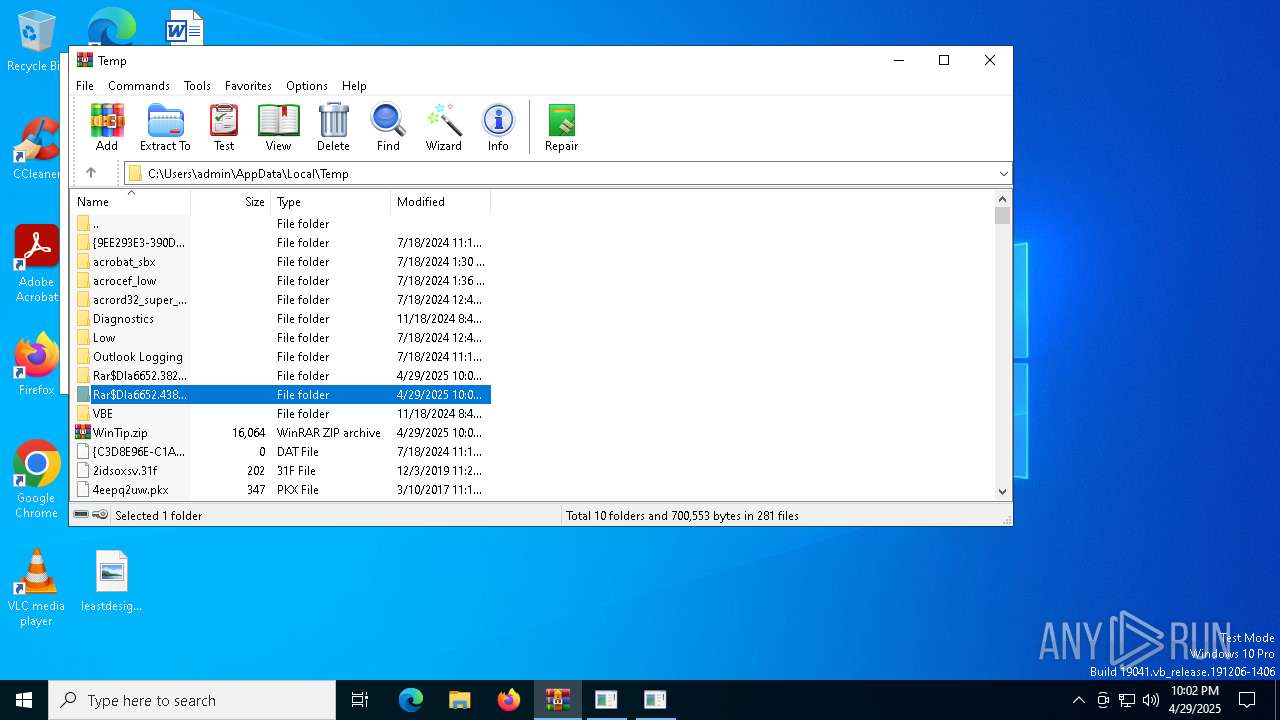
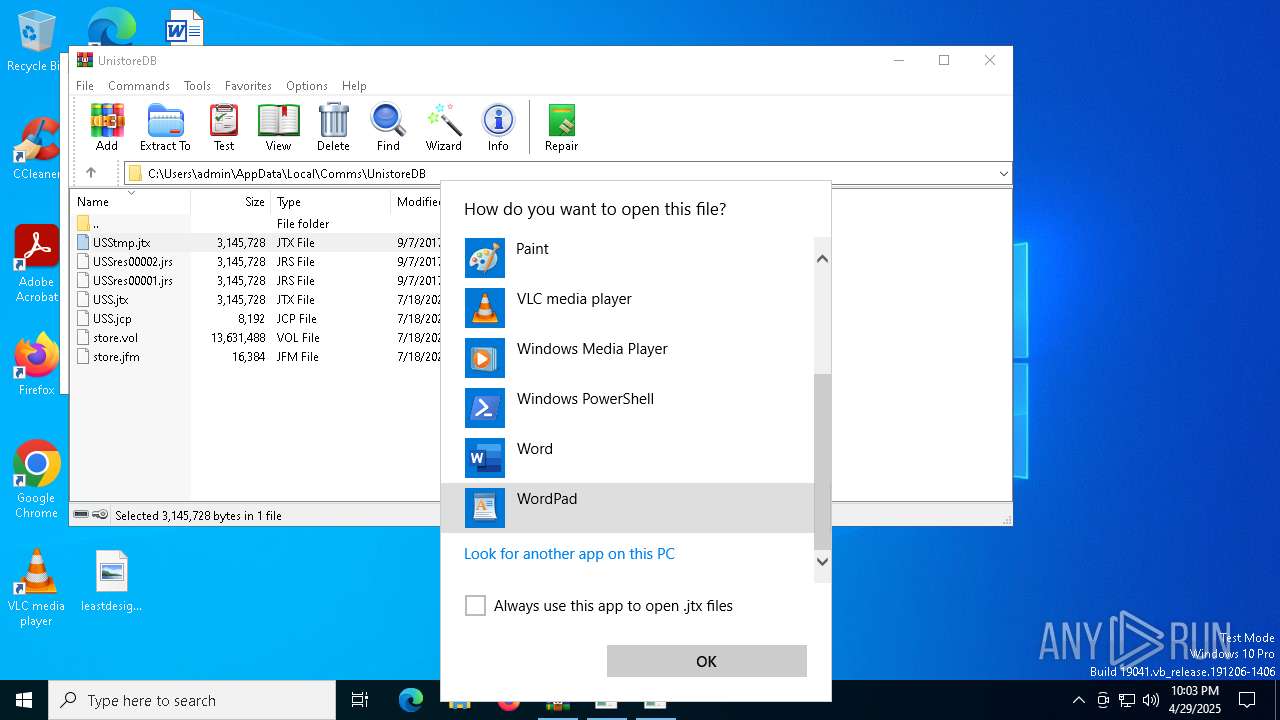
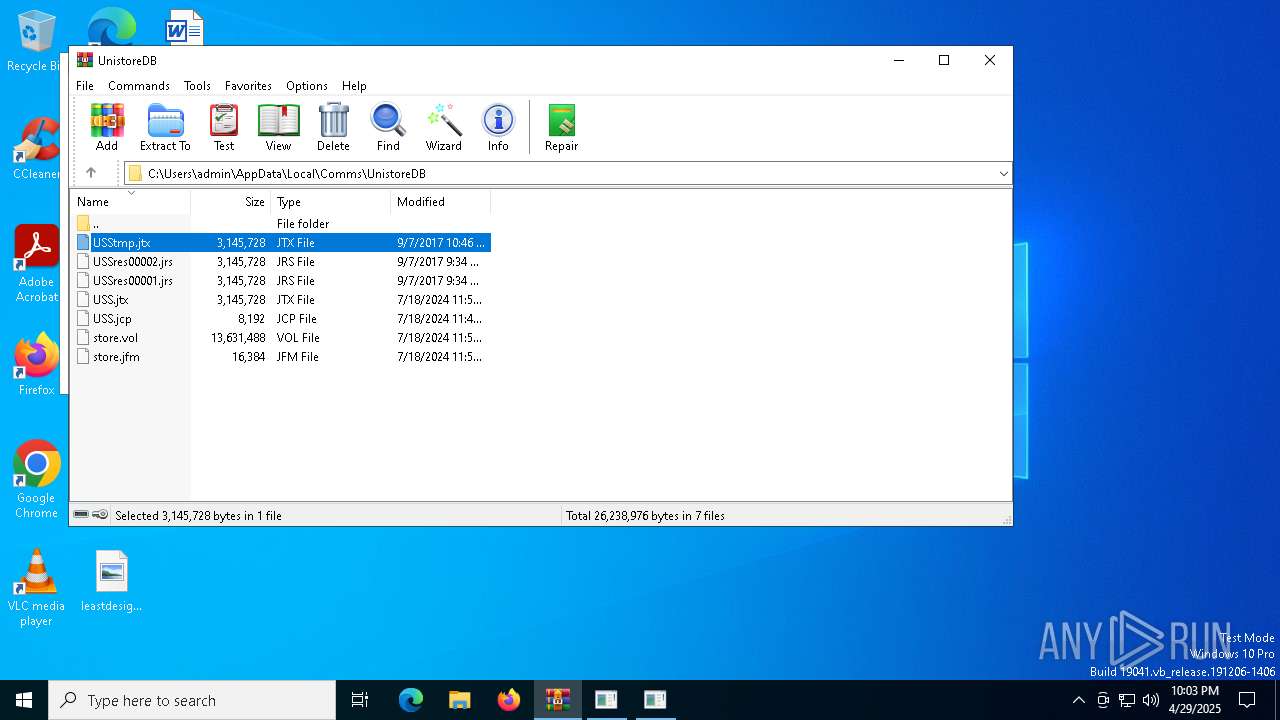
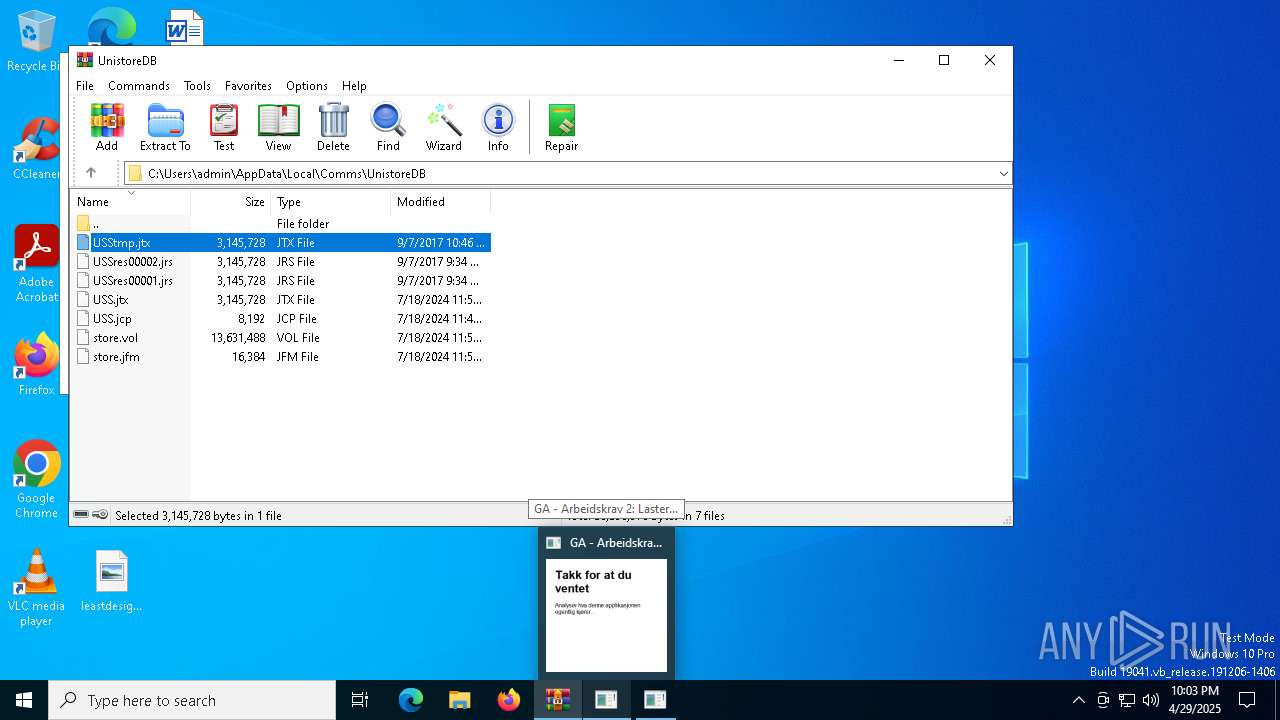
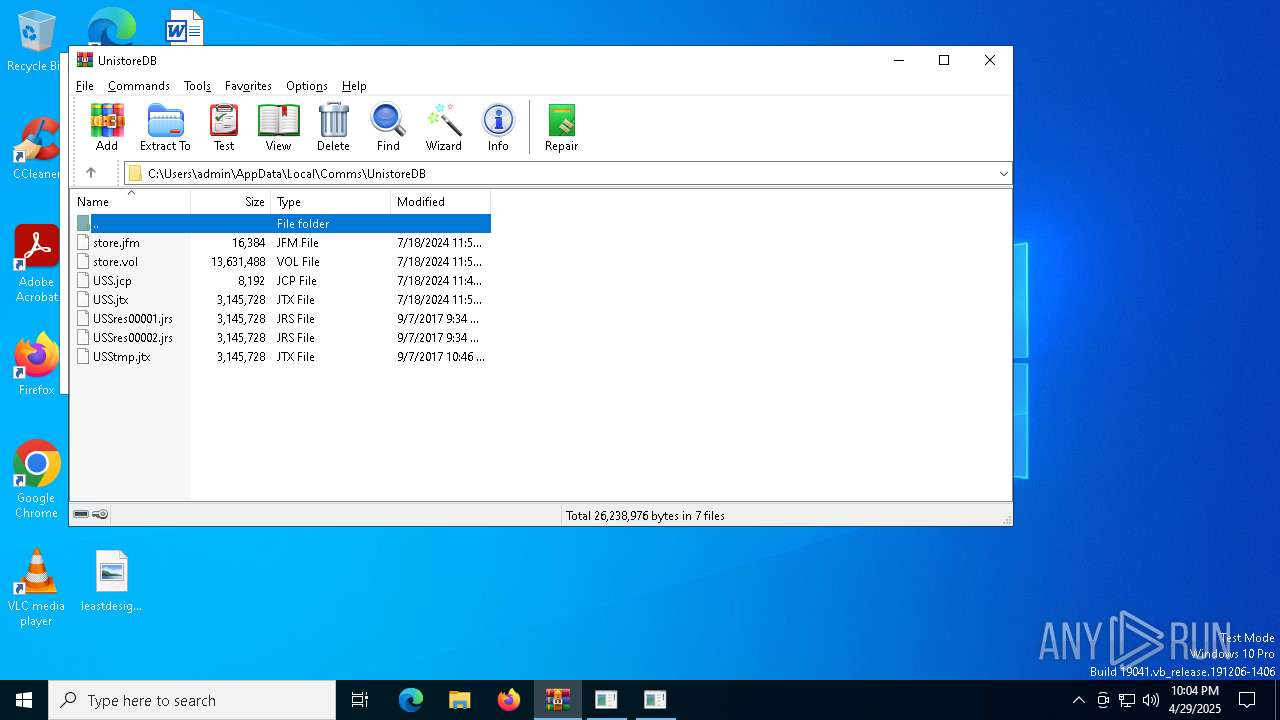
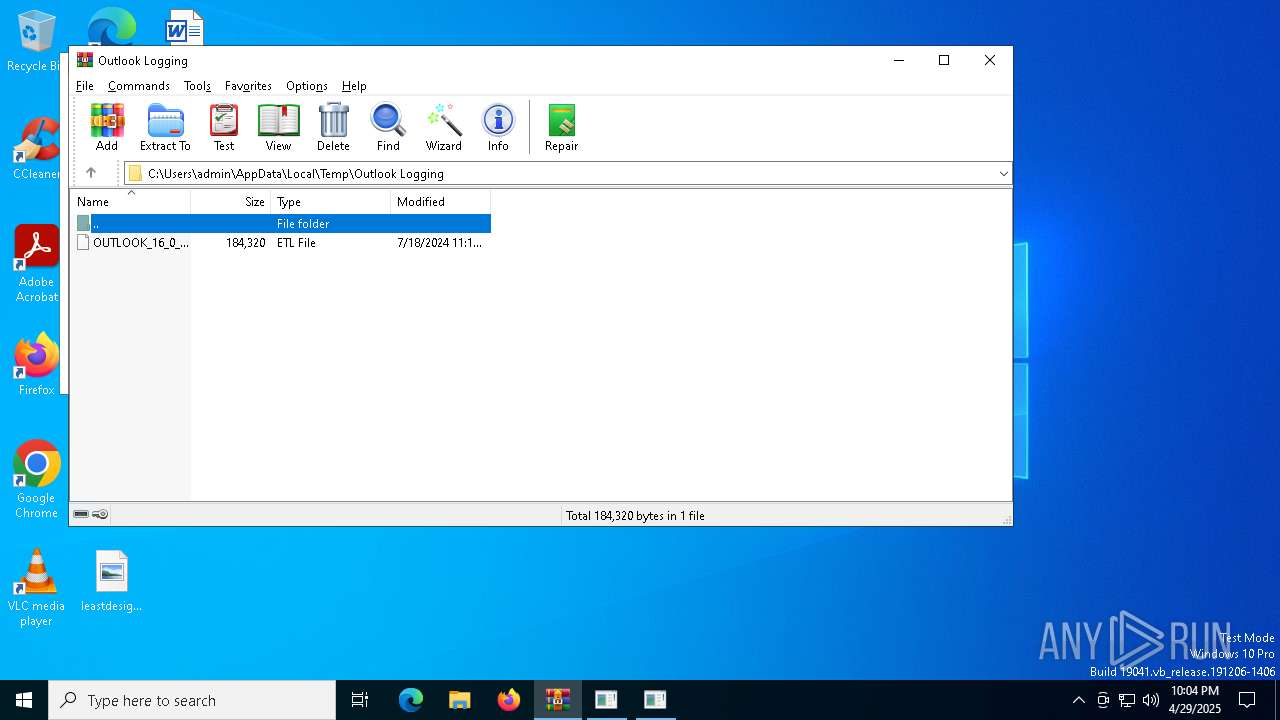
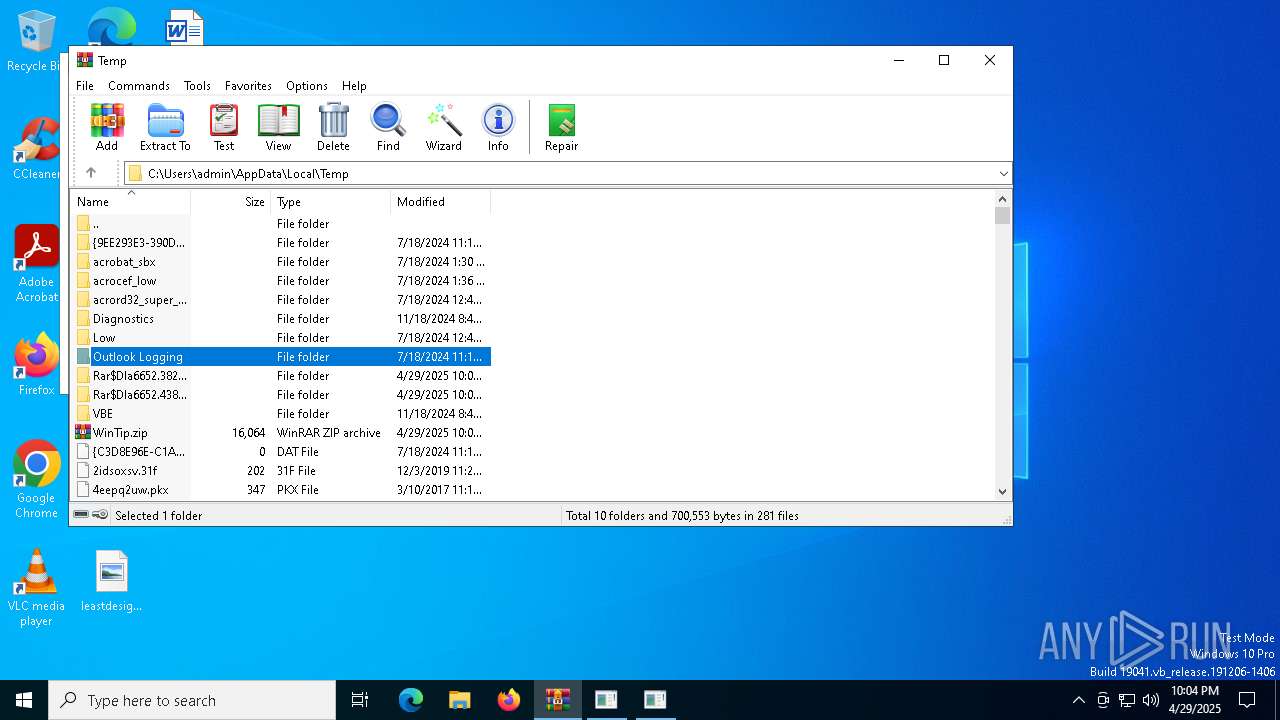
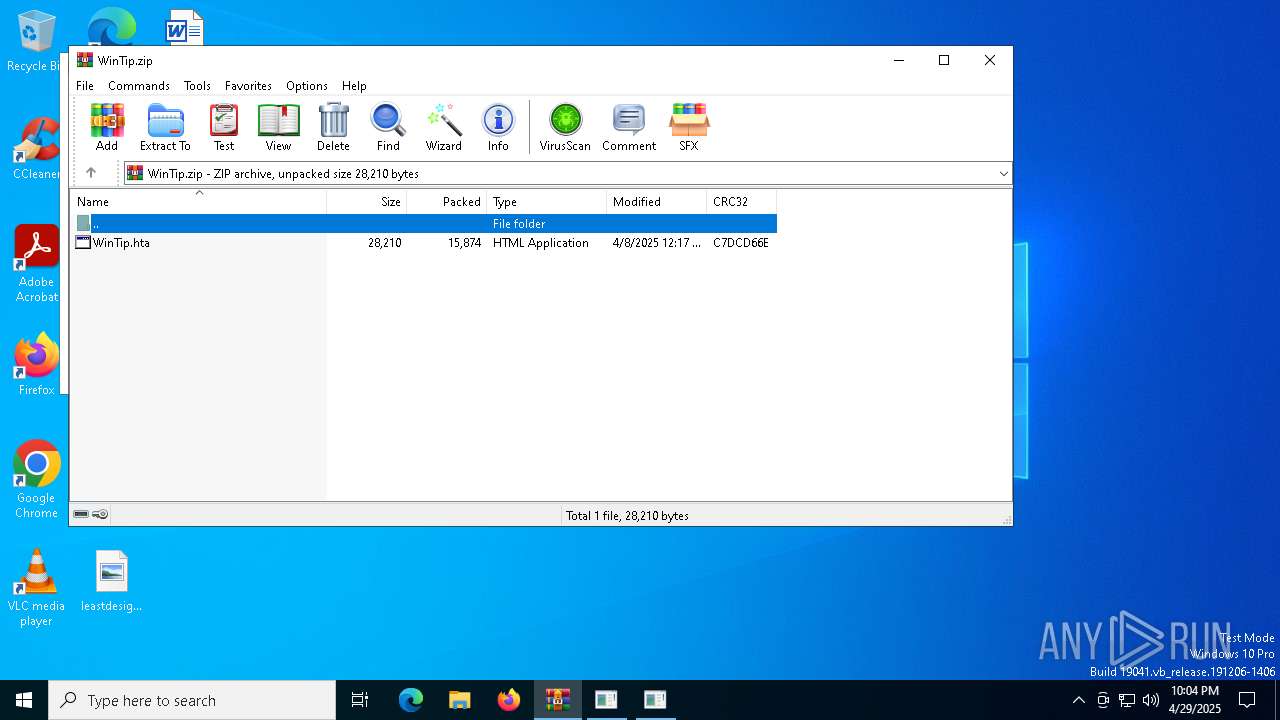
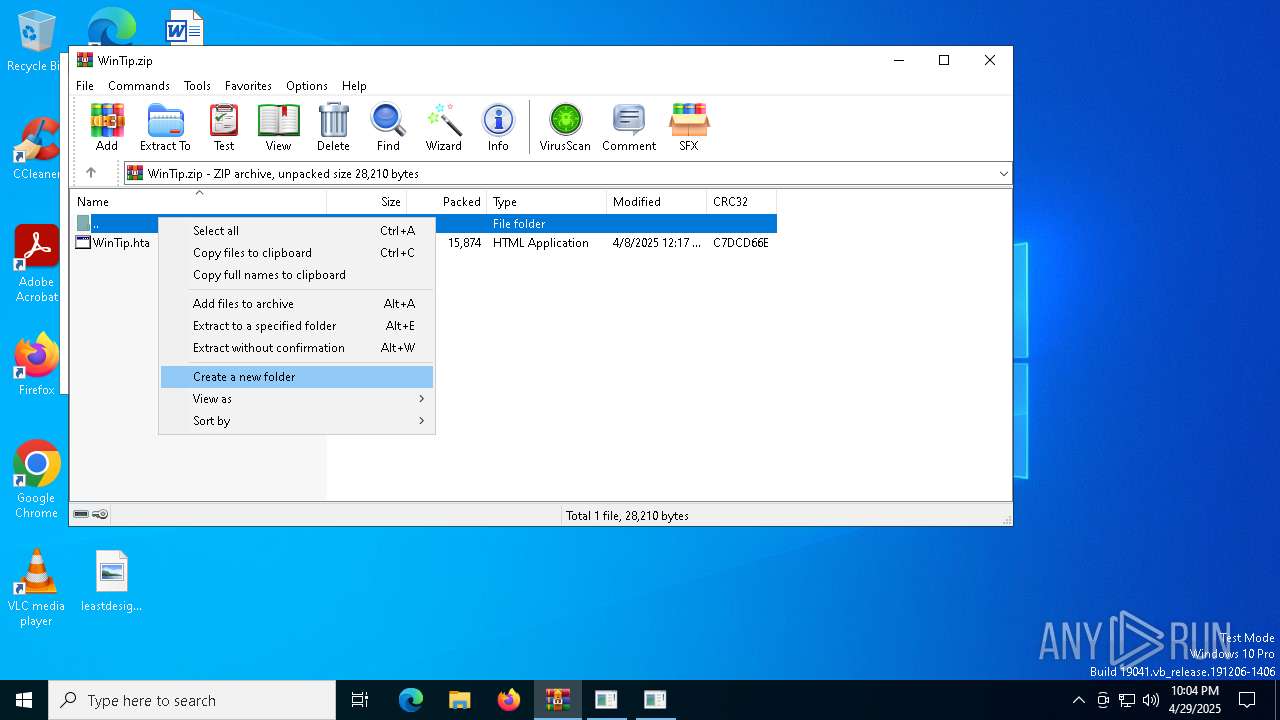
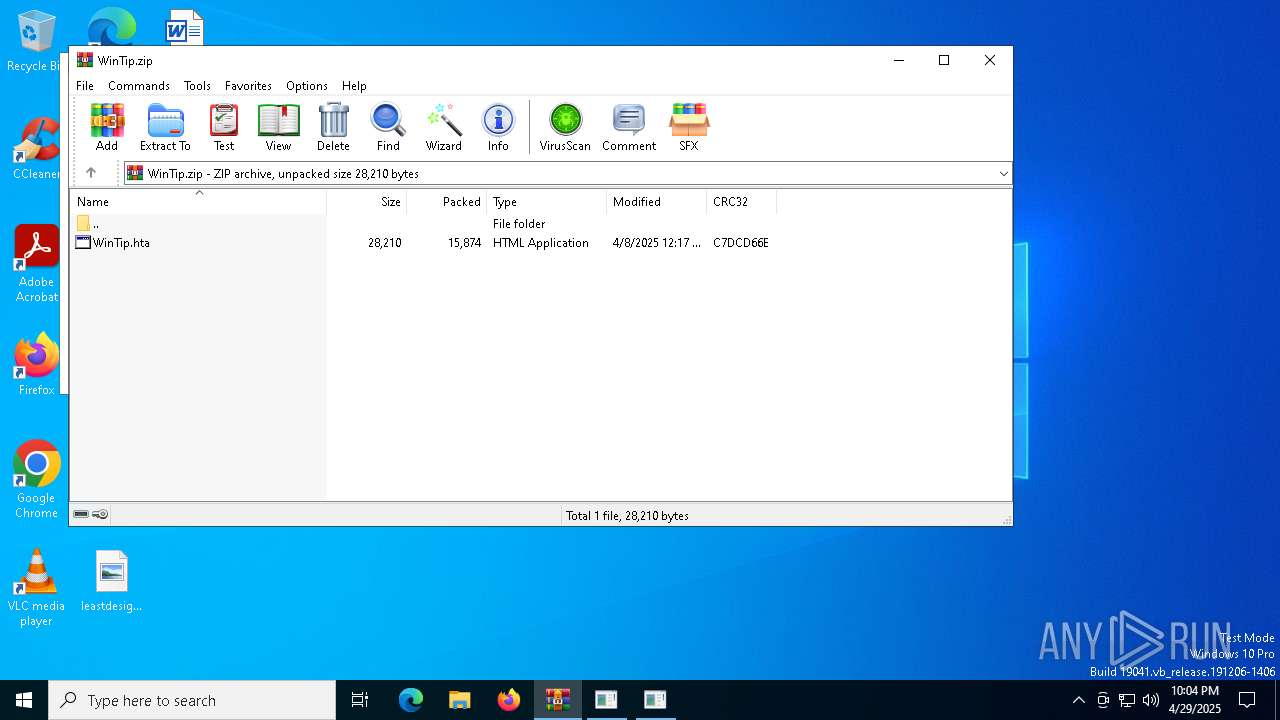
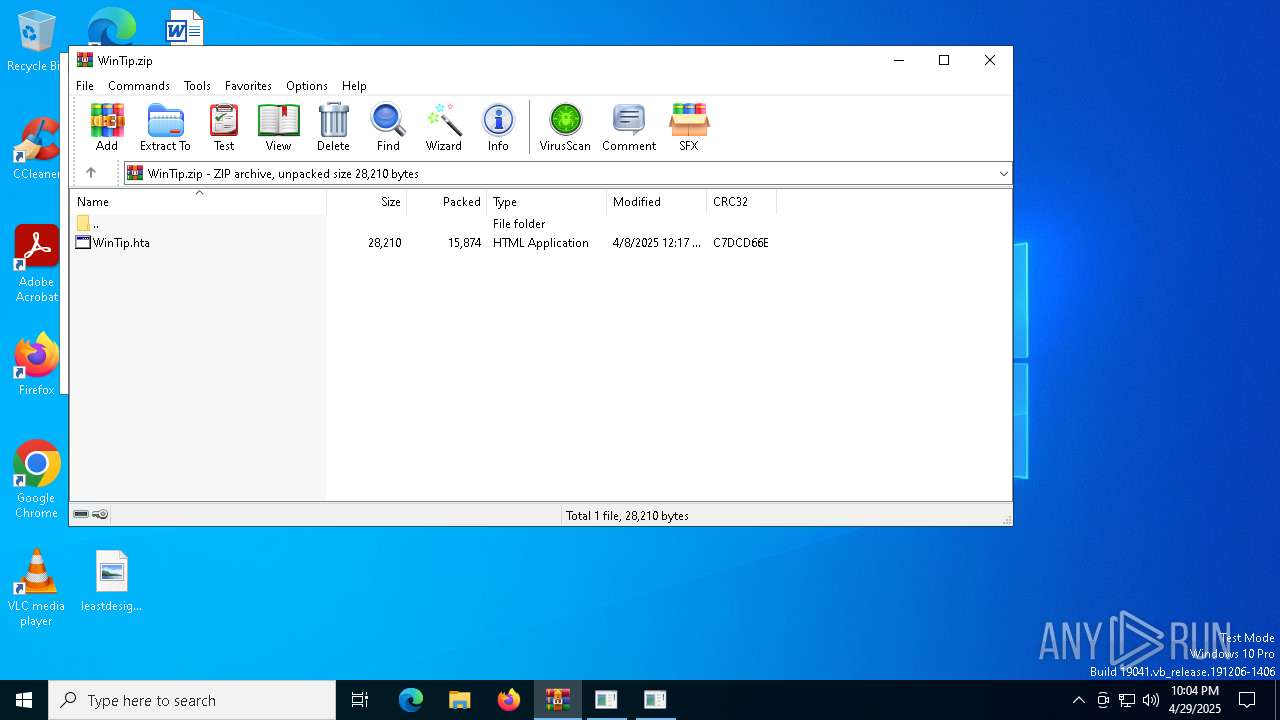
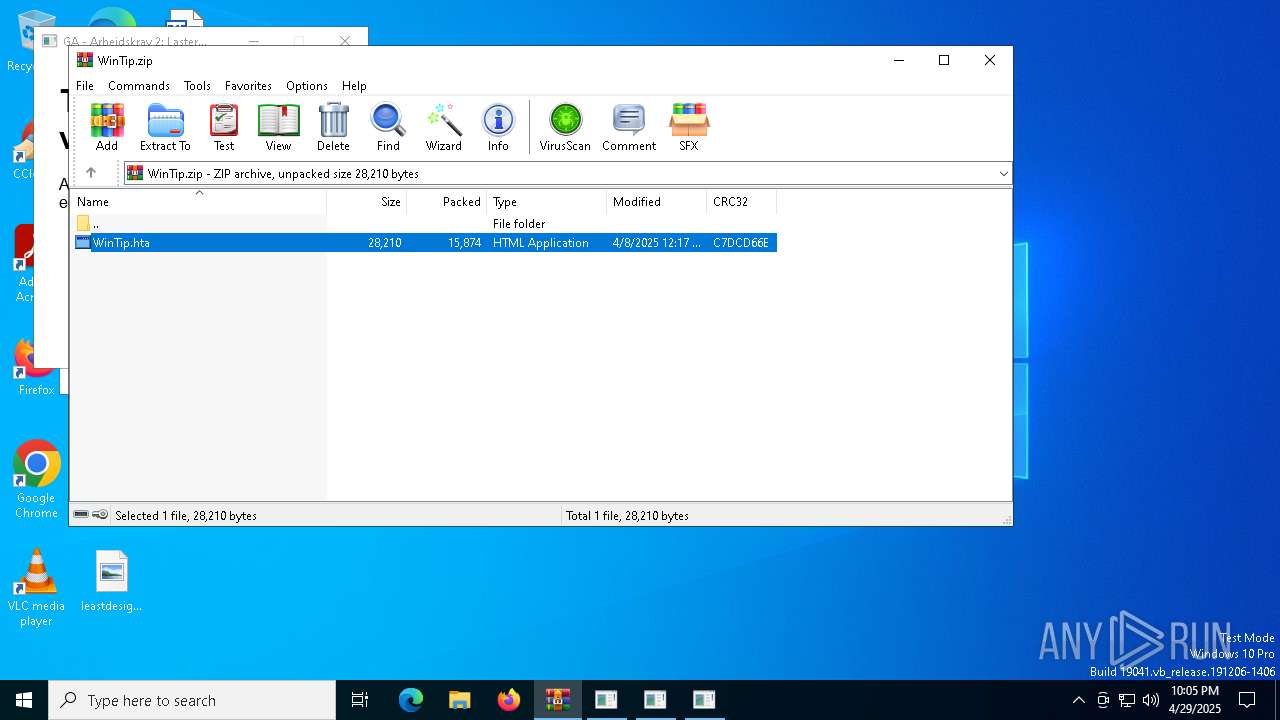
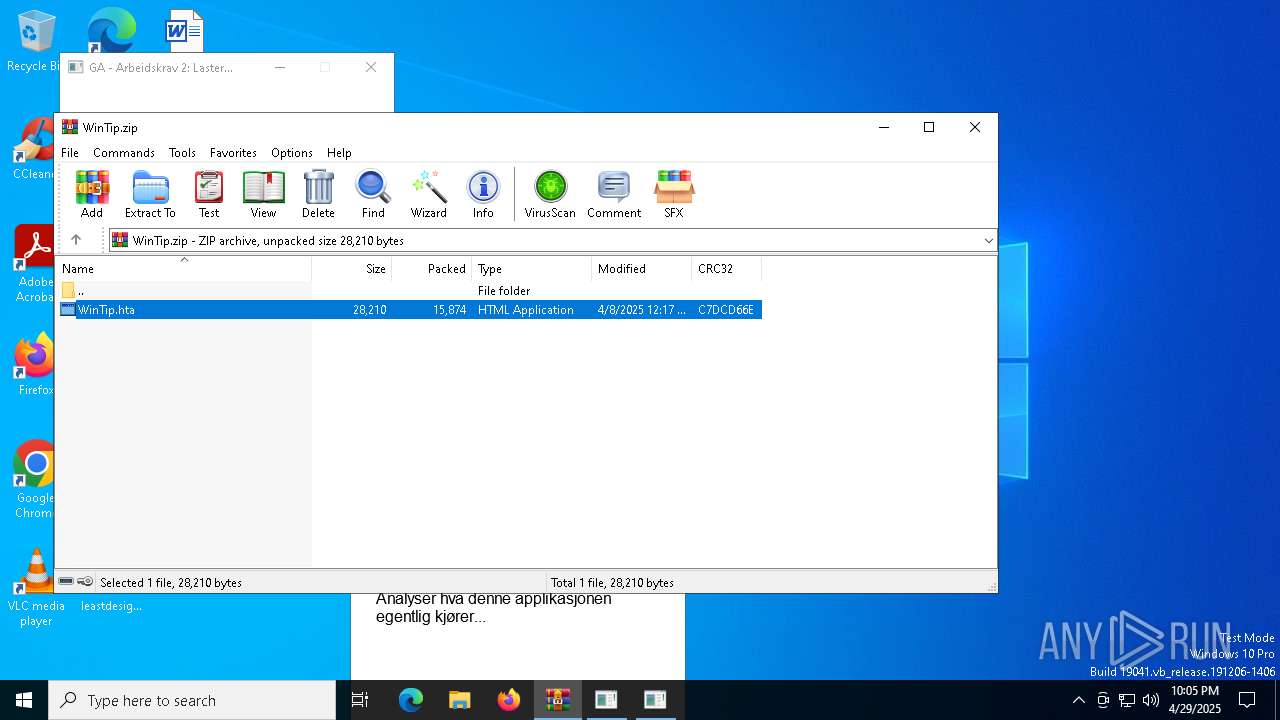
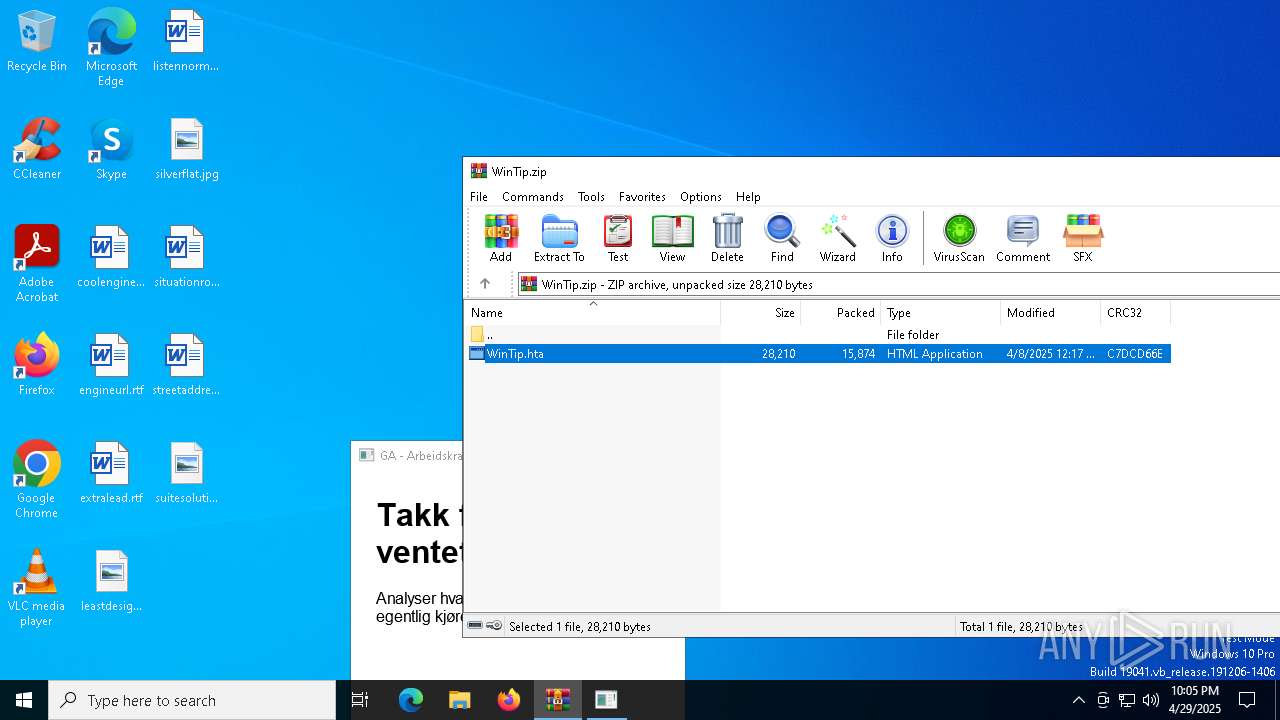
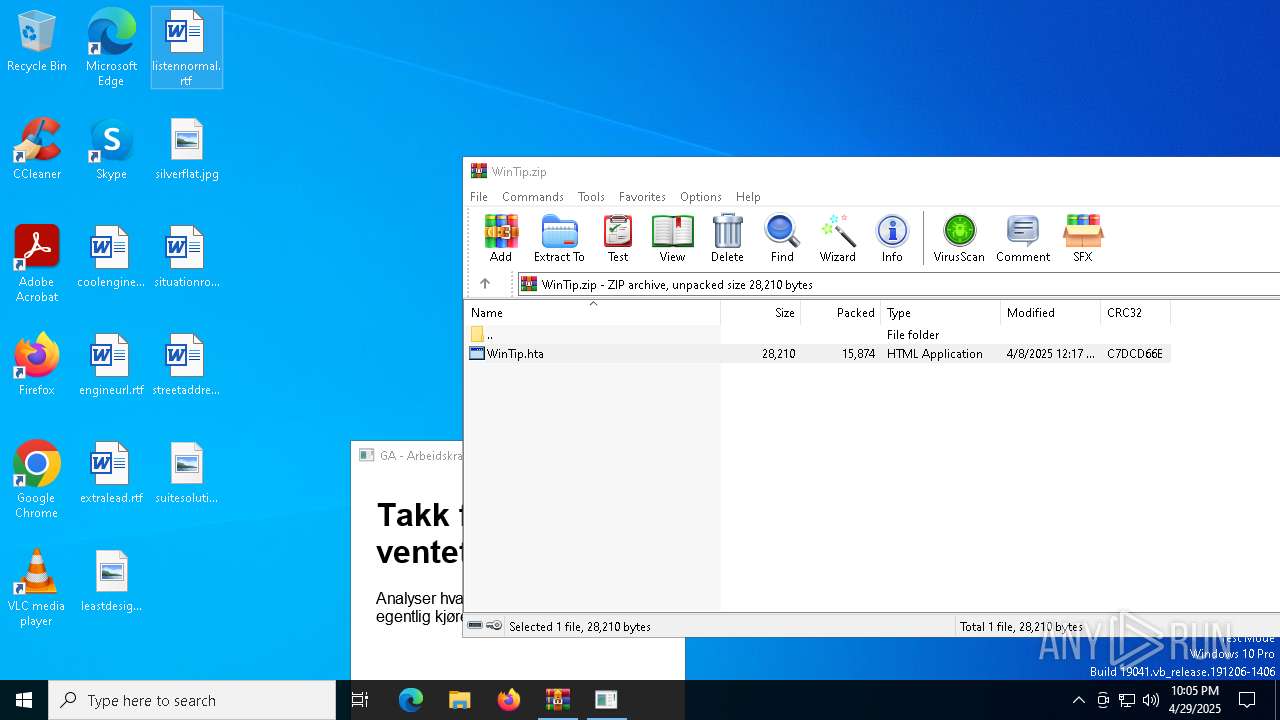
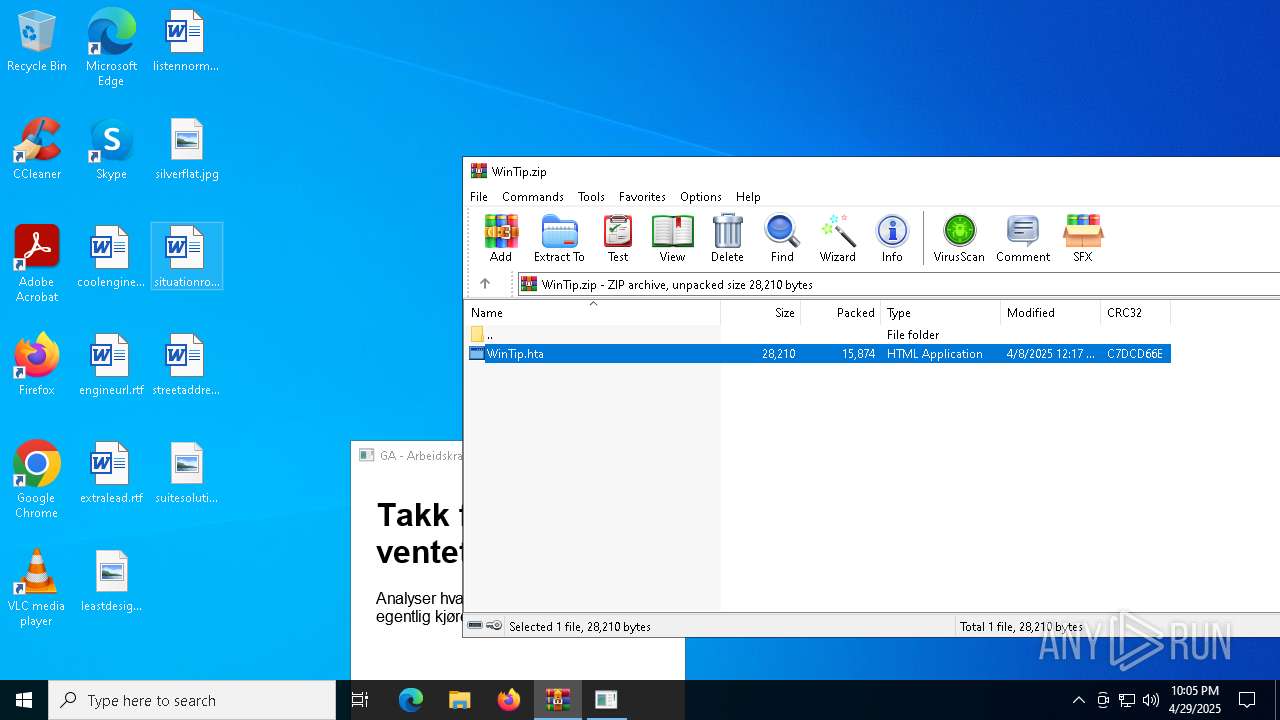
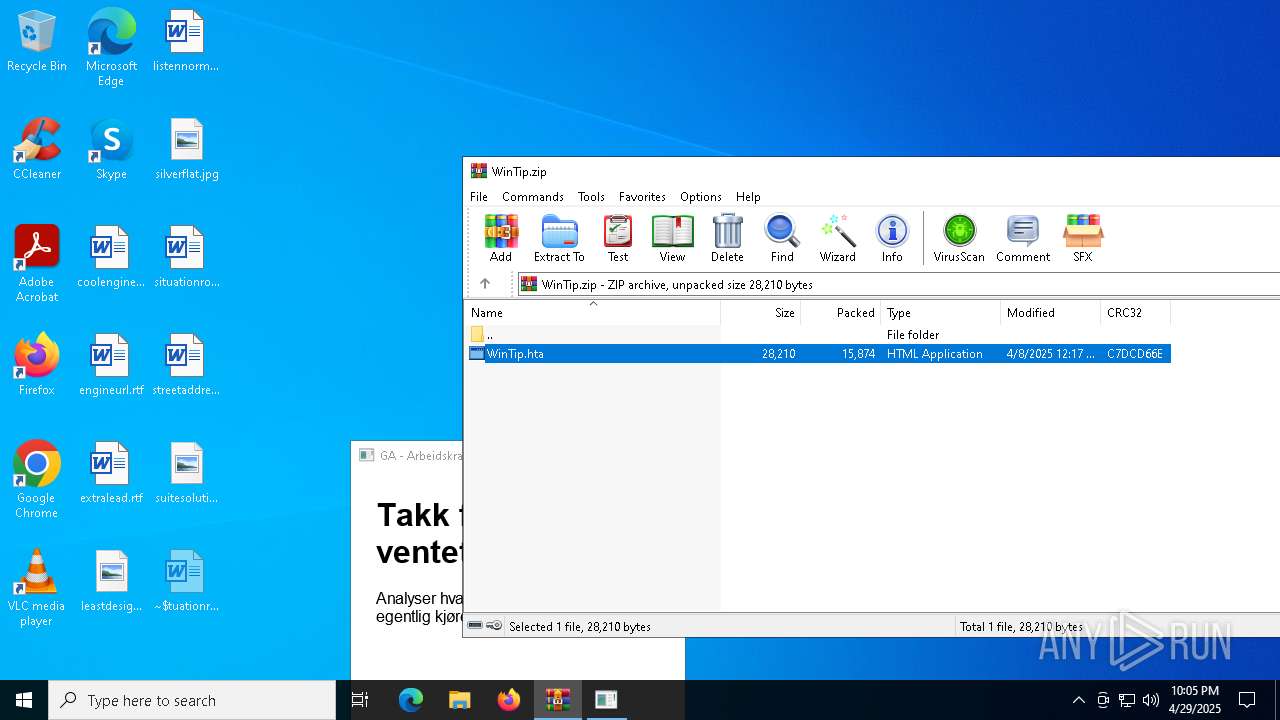
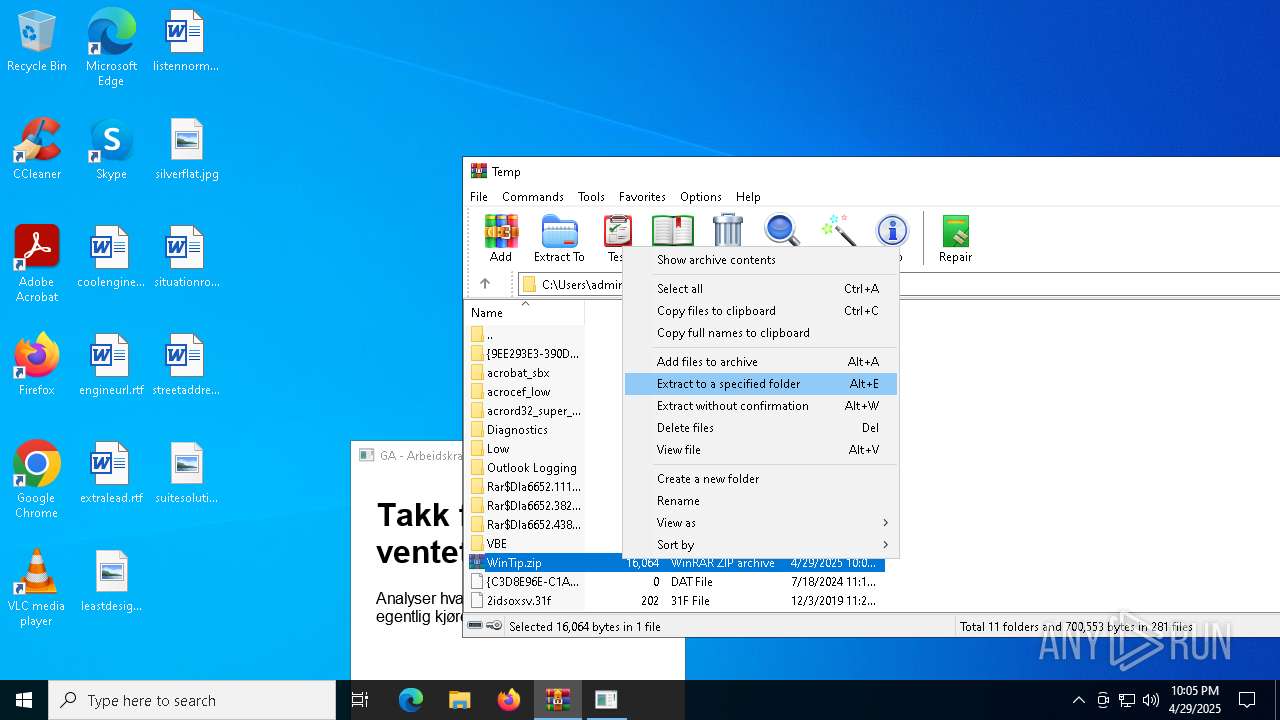
| File name: | WinTip.zip |
| Full analysis: | https://app.any.run/tasks/79170b16-2abc-4ba5-ab7d-e485223e9b5a |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 22:01:01 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 55CD1F0E70261AA23FC6FEF909B02AAF |
| SHA1: | 440767DCC0FBF4394173894D0A6F4405FDD4B485 |
| SHA256: | 73A9271A31246D91CC226718310AEE88FB3E74EB829232A5CC56B4BC6158A634 |
| SSDEEP: | 384:K+YAGRMzW+1SYiOvSdjUyqgnxomi1eMfWInTAcK+g74l34:K+YdRMF1SKvyUw/i1eMpAkgeI |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6652)
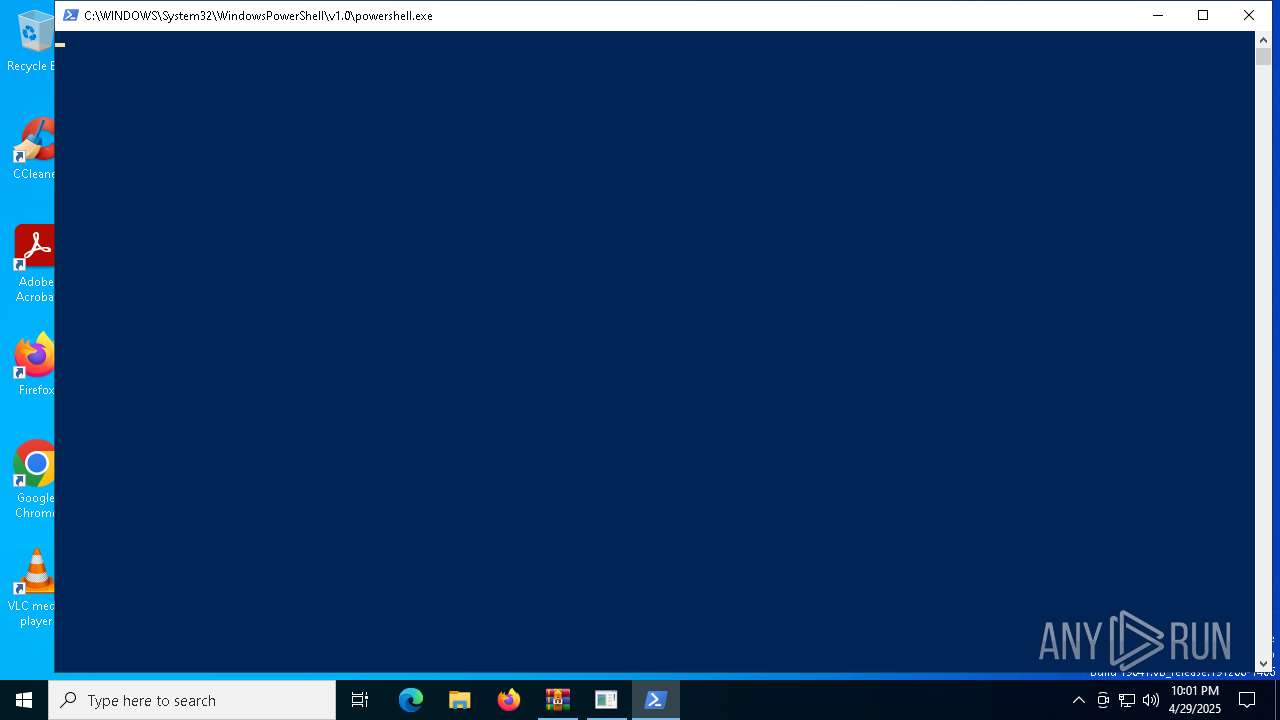
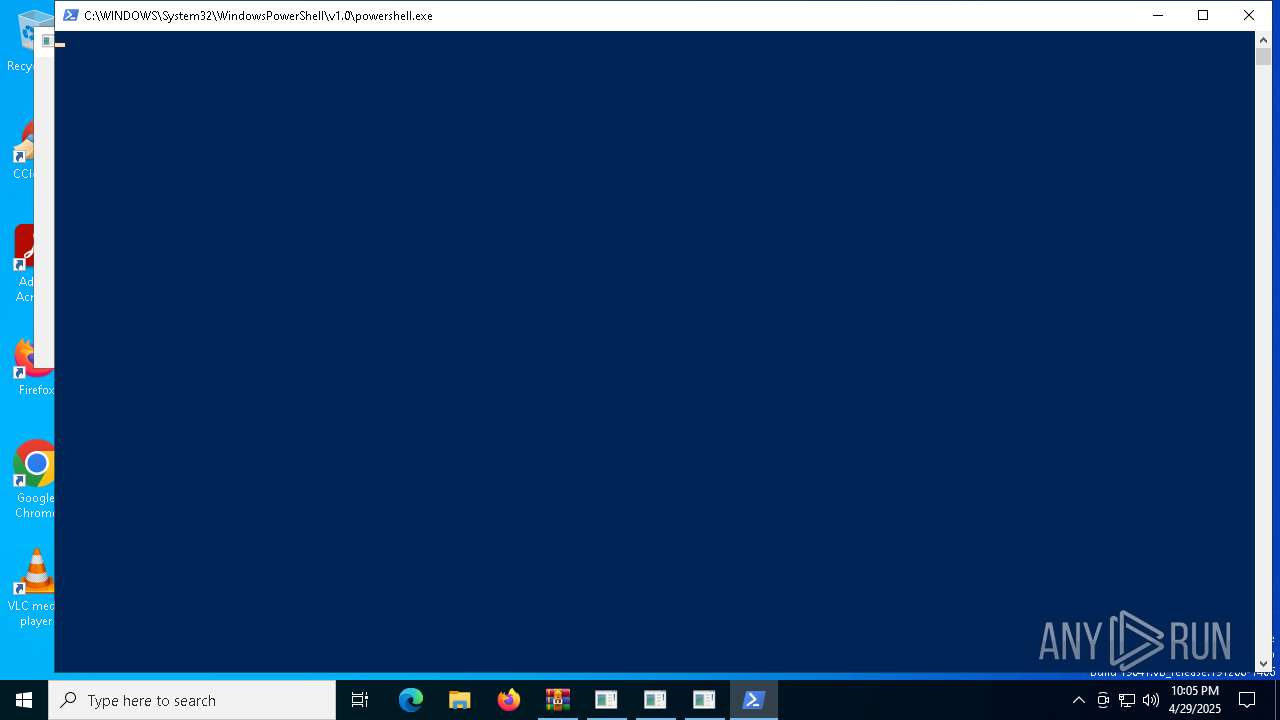
Bypass execution policy to execute commands
- powershell.exe (PID: 1676)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 4488)
Changes powershell execution policy (Bypass)
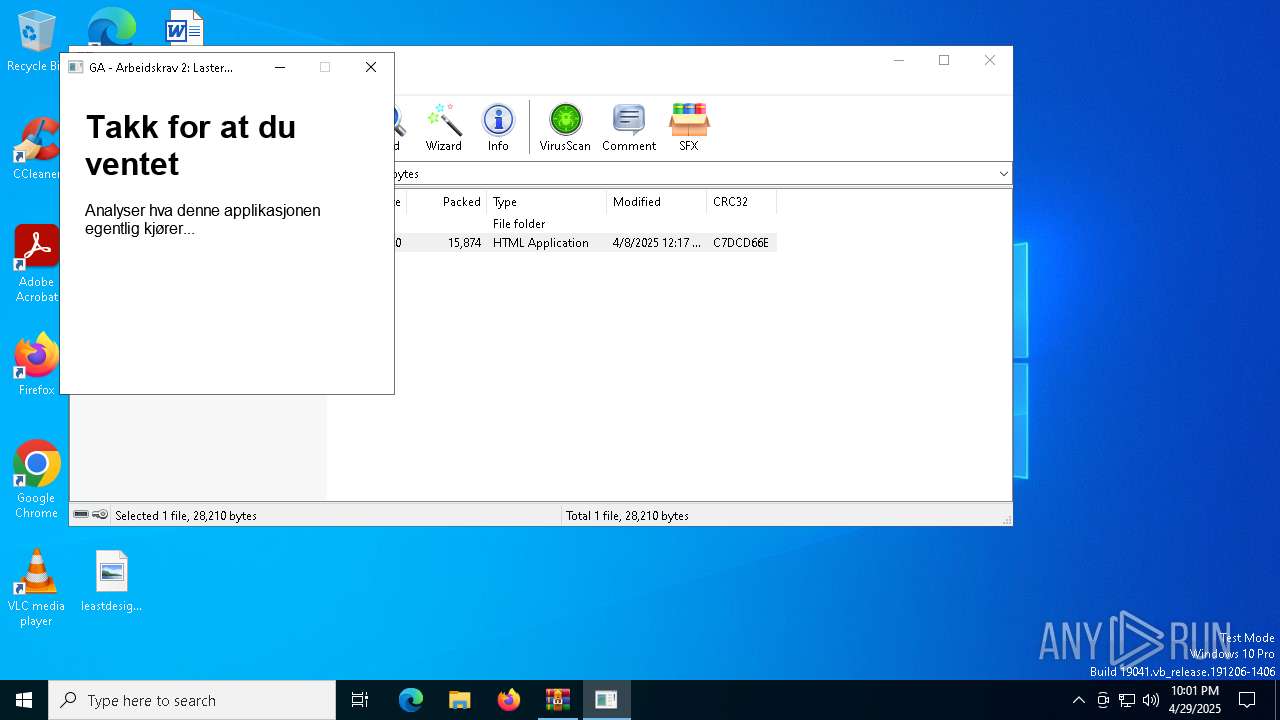
- mshta.exe (PID: 4920)
- mshta.exe (PID: 736)
- mshta.exe (PID: 2504)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 1676)
- powershell.exe (PID: 1512)
SUSPICIOUS
Identifying current user with WHOAMI command
- cmd.exe (PID: 2432)
- cmd.exe (PID: 4112)
- cmd.exe (PID: 1852)
Starts CMD.EXE for commands execution
- mshta.exe (PID: 4920)
- mshta.exe (PID: 736)
- mshta.exe (PID: 2504)
Possibly malicious use of IEX has been detected
- mshta.exe (PID: 4920)
- mshta.exe (PID: 736)
- mshta.exe (PID: 2504)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 4920)
- mshta.exe (PID: 736)
- mshta.exe (PID: 2504)
Probably download files using WebClient
- mshta.exe (PID: 4920)
- mshta.exe (PID: 736)
- mshta.exe (PID: 2504)
Uses NSLOOKUP.EXE to check DNS info
- powershell.exe (PID: 1676)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 4488)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 1676)
- powershell.exe (PID: 1512)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6652)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 6652)
- OpenWith.exe (PID: 4560)
- OpenWith.exe (PID: 6876)
- OpenWith.exe (PID: 5780)
Disables trace logs
- powershell.exe (PID: 1676)
- powershell.exe (PID: 1512)
Checks proxy server information
- powershell.exe (PID: 1676)
- powershell.exe (PID: 1512)
- slui.exe (PID: 1748)
Reads Internet Explorer settings
- mshta.exe (PID: 4920)
- mshta.exe (PID: 736)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1676)
- powershell.exe (PID: 1512)
Checks supported languages
- csc.exe (PID: 6800)
- csc.exe (PID: 1012)
Reads the machine GUID from the registry
- csc.exe (PID: 6800)
- csc.exe (PID: 1012)
Reads the software policy settings
- slui.exe (PID: 5936)
- slui.exe (PID: 1748)
Manual execution by a user
- WINWORD.EXE (PID: 1388)
- WINWORD.EXE (PID: 6960)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0008 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:08 14:17:32 |
| ZipCRC: | 0xc7dcd66e |
| ZipCompressedSize: | 15874 |
| ZipUncompressedSize: | 28210 |
| ZipFileName: | WinTip.hta |
Total processes
181
Monitored processes
41
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | "C:\Windows\SysWOW64\mshta.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa6652.43862\WinTip.hta" {1E460BD7-F1C3-4B2E-88BF-4E770A288AF5}{1E460BD7-F1C3-4B2E-88BF-4E770A288AF5} | C:\Windows\SysWOW64\mshta.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 780 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | "C:\WINDOWS\system32\nslookup.exe" -type=txt tz2.mojitoteam.no | C:\Windows\SysWOW64\nslookup.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: nslookup Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | "C:\WINDOWS\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /target:winexe /out:"C:\Users\admin\AppData\Local\Temp\timezone.exe" "C:\Users\admin\AppData\Local\Temp\timezone.cs" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 1 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1056 | "C:\WINDOWS\system32\nslookup.exe" -type=txt tz1.mojitoteam.no | C:\Windows\SysWOW64\nslookup.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: nslookup Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1188 | "C:\WINDOWS\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /target:winexe /out:"C:\Users\admin\AppData\Local\Temp\timezone.exe" "C:\Users\admin\AppData\Local\Temp\timezone.cs" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 1 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1300 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1388 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\listennormal.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
77 969
Read events
76 672
Write events
1 184
Delete events
113
Modification events
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\WinTip.zip | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.hta\OpenWithProgids |
| Operation: | write | Name: | htafile |
Value: | |||
| (PID) Process: | (4920) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Suspcious |
Value: C:\Users\admin\AppData\Local\Temp\carbon.hta | |||
Executable files
1
Suspicious files
42
Text files
18
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4920 | mshta.exe | C:\Users\admin\AppData\Local\Temp\carbon.hta | html | |
MD5:F56B2C29F093D1E3B196CD8029BEA8A8 | SHA256:752D5EDBC5B7D95A818B98A6035EC97EFD7C3965047A63A9C931A63F652BC954 | |||
| 1676 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_y1hjwv02.wub.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1676 | powershell.exe | C:\Users\admin\AppData\Local\Temp\timezone.cs | text | |
MD5:38520E3B29A6553032CFDA26261D45EC | SHA256:6BF46EC84A532FB48F9D3F0E80555D63675814E6219DCC8BF8CEF0A8B46BEF50 | |||
| 1388 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:6B96E94DF3C2C1E4FF3802741307ECDA | SHA256:9F16A8567BADD04EC8395A8E357CEE439C4566AC406F2D734752059AE5C7832B | |||
| 6652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6652.11135\WinTip.hta | html | |
MD5:F56B2C29F093D1E3B196CD8029BEA8A8 | SHA256:752D5EDBC5B7D95A818B98A6035EC97EFD7C3965047A63A9C931A63F652BC954 | |||
| 4488 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qutuxymx.yxb.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4488 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ln4jpdwj.knm.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1676 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_or5qhhaq.suq.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1676 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:863B5527572330FEB73B2B7A97D3B2D2 | SHA256:4C2F0F8360698D61B143A7A7D7D596561BFC6913A8DAD239E1CE8C1FEBDF5232 | |||
| 6652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6652.43862\WinTip.hta | html | |
MD5:F56B2C29F093D1E3B196CD8029BEA8A8 | SHA256:752D5EDBC5B7D95A818B98A6035EC97EFD7C3965047A63A9C931A63F652BC954 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
45
DNS requests
40
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.25:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5556 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5556 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1388 | WINWORD.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.216.77.25:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
1676 | powershell.exe | 195.159.29.35:443 | berg-henry.no | Globalconnect As | NO | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
berg-henry.no |
| unknown |
2.100.168.192.in-addr.arpa |
| whitelisted |
tz1.mojitoteam.no |
| unknown |