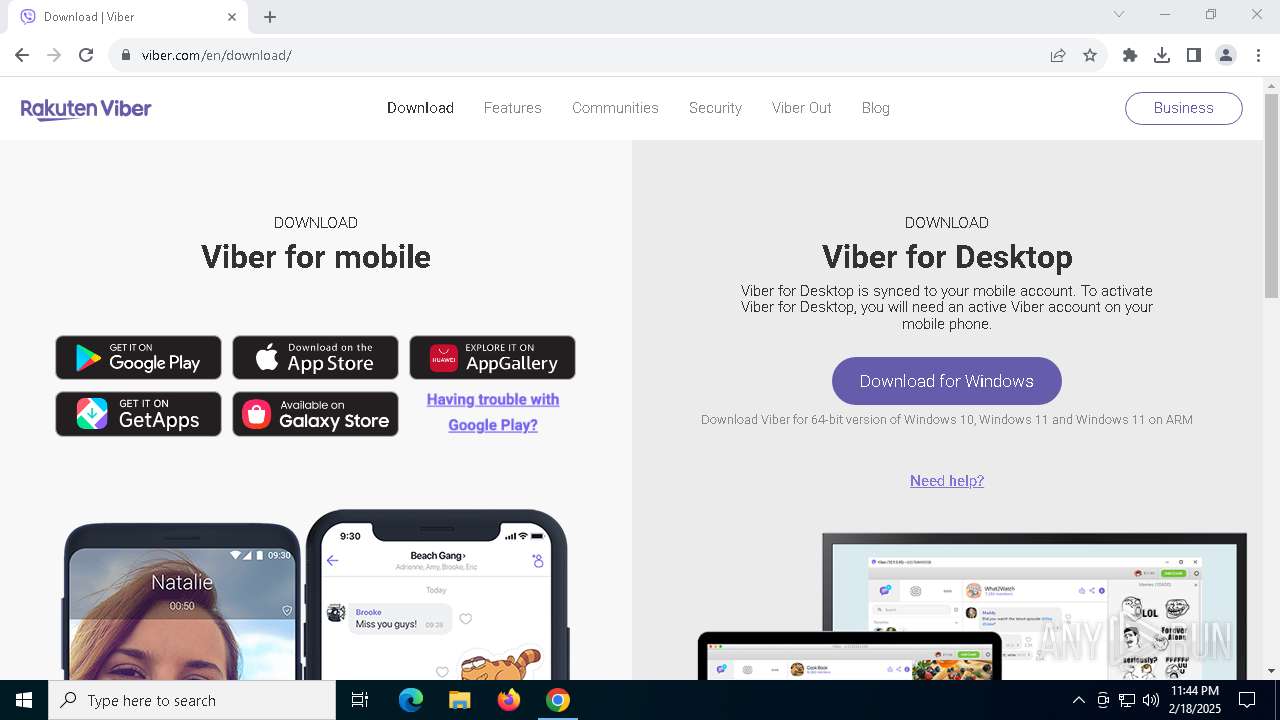
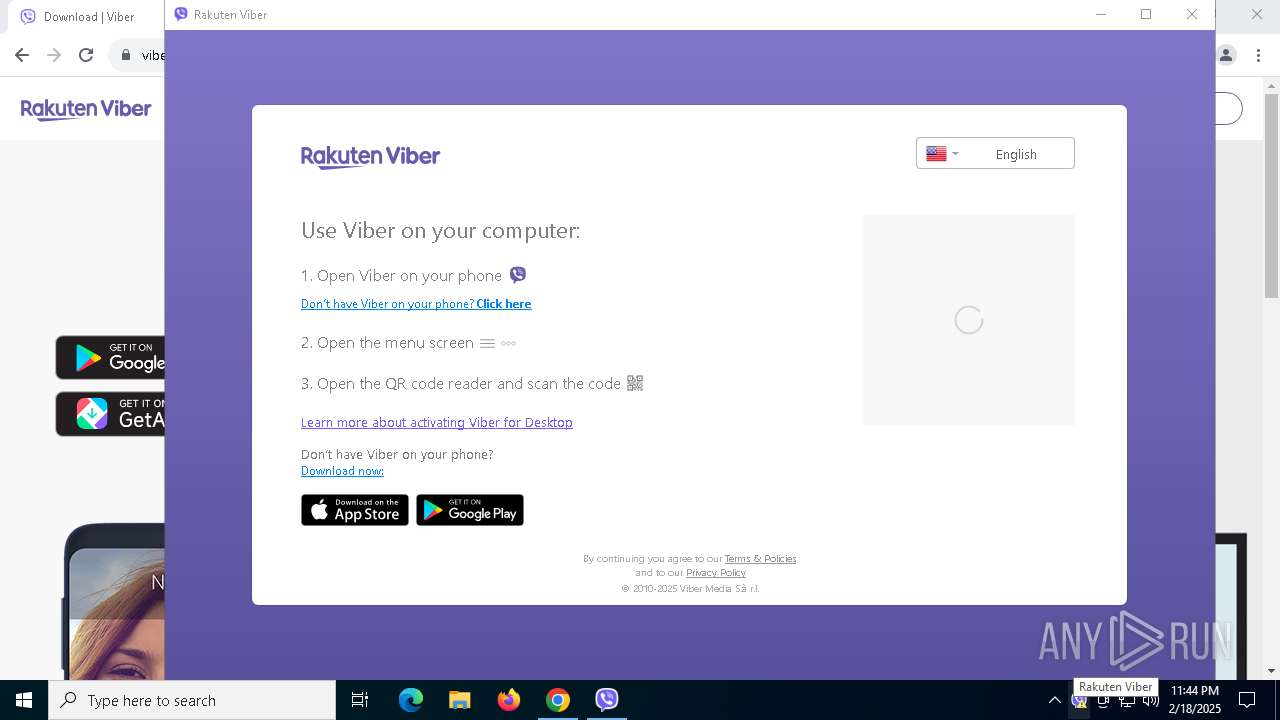
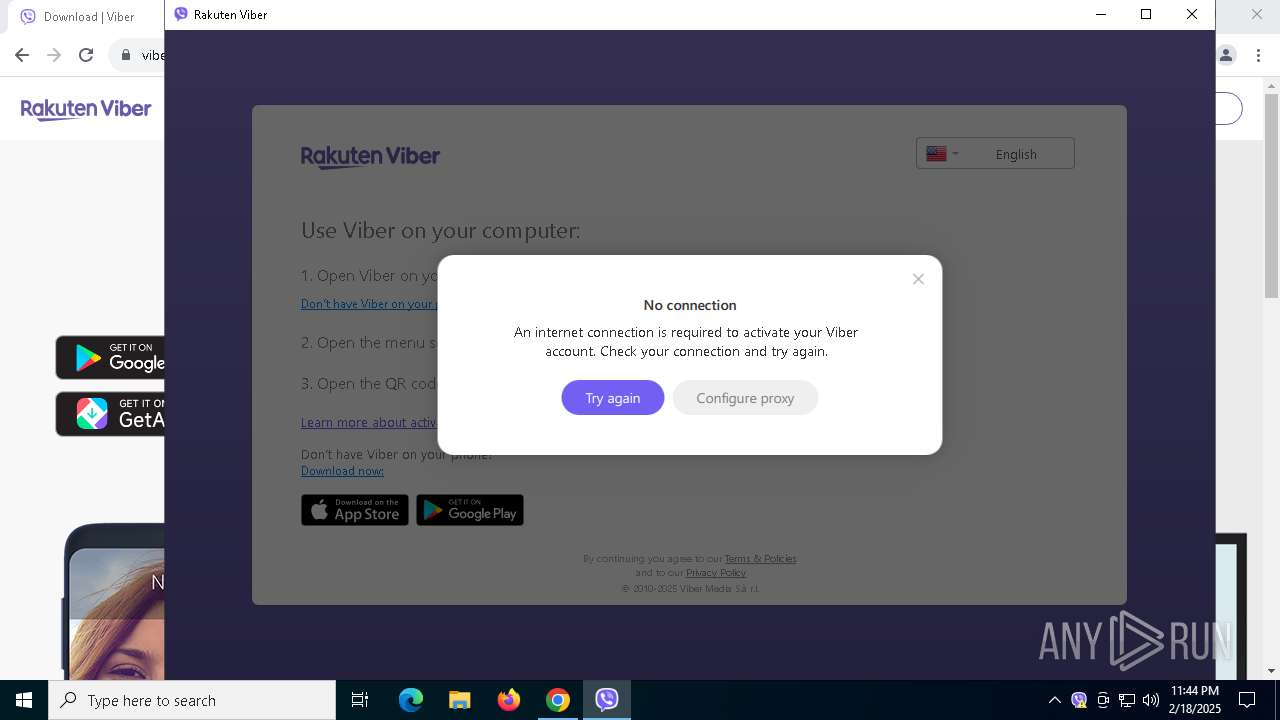
| URL: | viber.com |
| Full analysis: | https://app.any.run/tasks/314e7553-17c4-4778-a8cb-b05f98c75c05 |
| Verdict: | Malicious activity |
| Analysis date: | February 18, 2025, 23:43:01 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 20E3C346C1D64C1A5BC07D7550E8B0F1 |
| SHA1: | E337E1602220F7F7F2A256156A58BED43A2FEC0E |
| SHA256: | 73A64D400C07581C5293AB07BAFFCB462A5389D74F477998488E3A5F89A7609A |
| SSDEEP: | 3:iX:iX |
MALICIOUS
Changes the autorun value in the registry
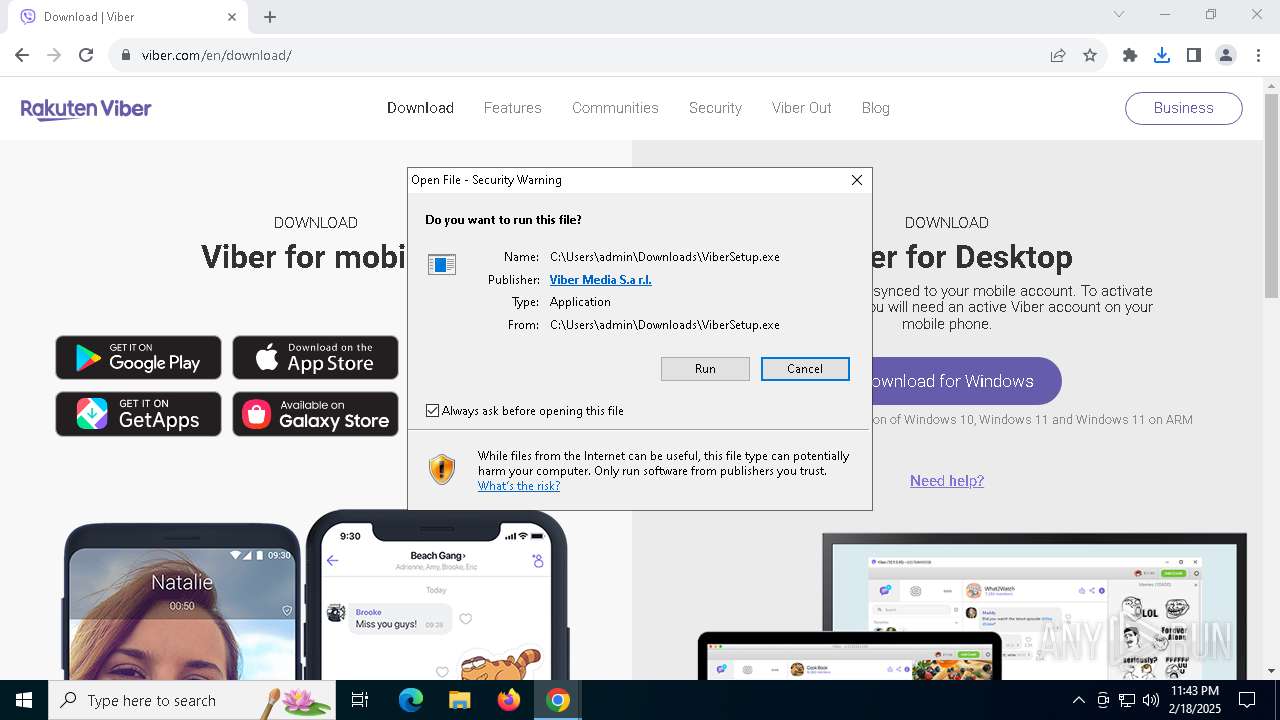
- ViberSetup.exe (PID: 6476)
- ie4uinit.exe (PID: 1172)
SUSPICIOUS
Process drops legitimate windows executable
- ViberSetup.exe (PID: 6476)
- msiexec.exe (PID: 5496)
Executable content was dropped or overwritten
- ViberSetup.exe (PID: 6476)
- rundll32.exe (PID: 2356)
Reads security settings of Internet Explorer
- ViberBA.exe (PID: 2612)
- ViberSetup.exe (PID: 6476)
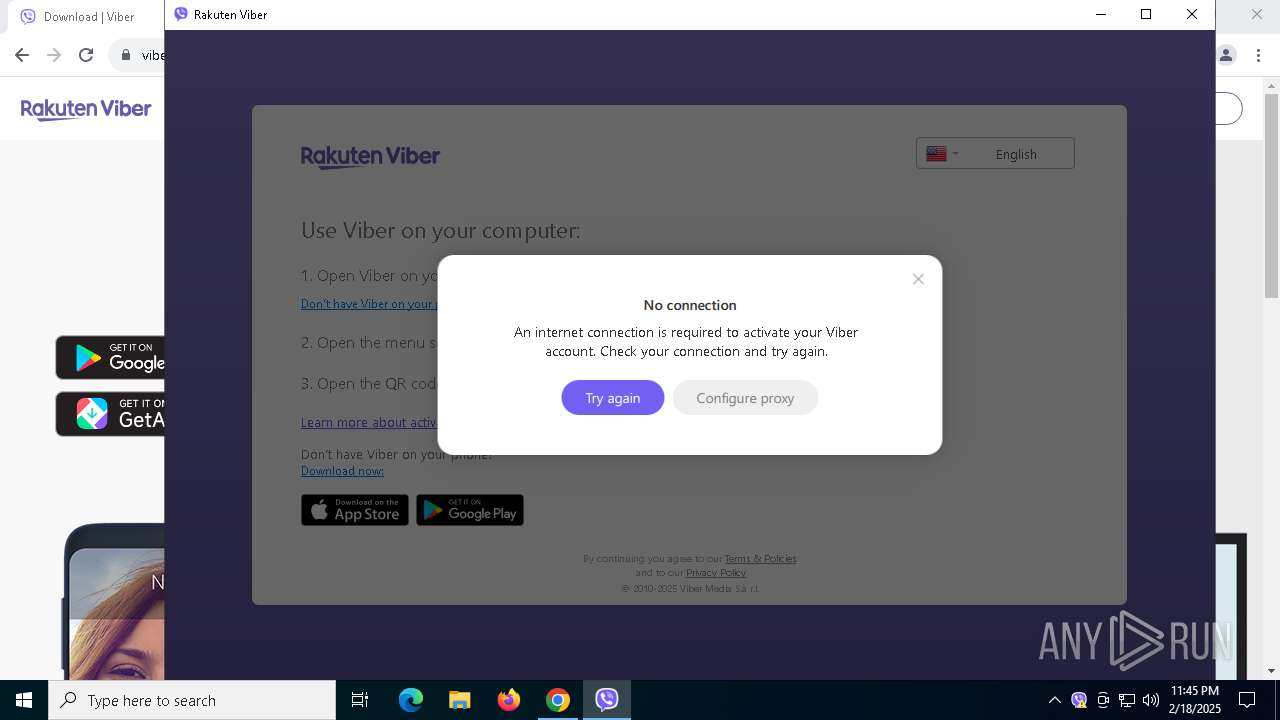
Checks for external IP
- ViberBA.exe (PID: 2612)
- Viber.exe (PID: 6912)
Creates a software uninstall entry
- ViberSetup.exe (PID: 6476)
Checks Windows Trust Settings
- ViberSetup.exe (PID: 6476)
- msiexec.exe (PID: 5496)
- ViberBA.exe (PID: 2612)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 5496)
The process drops C-runtime libraries
- msiexec.exe (PID: 5496)
Uses RUNDLL32.EXE to load library
- ie4uinit.exe (PID: 7020)
Detected use of alternative data streams (AltDS)
- Viber.exe (PID: 6912)
Searches for installed software
- ViberSetup.exe (PID: 6476)
INFO
Application launched itself
- chrome.exe (PID: 6300)
- msiexec.exe (PID: 5496)
Create files in a temporary directory
- ViberSetup.exe (PID: 6476)
- rundll32.exe (PID: 2356)
- Viber.exe (PID: 6912)
Checks supported languages
- ViberSetup.exe (PID: 6476)
- ViberBA.exe (PID: 2612)
- msiexec.exe (PID: 5496)
- msiexec.exe (PID: 2072)
- msiexec.exe (PID: 3076)
- Viber.exe (PID: 6912)
The sample compiled with english language support
- chrome.exe (PID: 6300)
- ViberSetup.exe (PID: 6476)
- msiexec.exe (PID: 5496)
Reads the computer name
- ViberBA.exe (PID: 2612)
- msiexec.exe (PID: 5496)
- msiexec.exe (PID: 2072)
- msiexec.exe (PID: 3076)
- Viber.exe (PID: 6912)
- ViberSetup.exe (PID: 6476)
Executable content was dropped or overwritten
- chrome.exe (PID: 6300)
- msiexec.exe (PID: 5496)
Creates files in the program directory
- ViberBA.exe (PID: 2612)
Reads the machine GUID from the registry
- ViberBA.exe (PID: 2612)
- ViberSetup.exe (PID: 6476)
- msiexec.exe (PID: 5496)
- Viber.exe (PID: 6912)
Creates files or folders in the user directory
- ViberBA.exe (PID: 2612)
- ViberSetup.exe (PID: 6476)
- msiexec.exe (PID: 5496)
- ie4uinit.exe (PID: 1172)
- Viber.exe (PID: 6912)
Disables trace logs
- ViberBA.exe (PID: 2612)
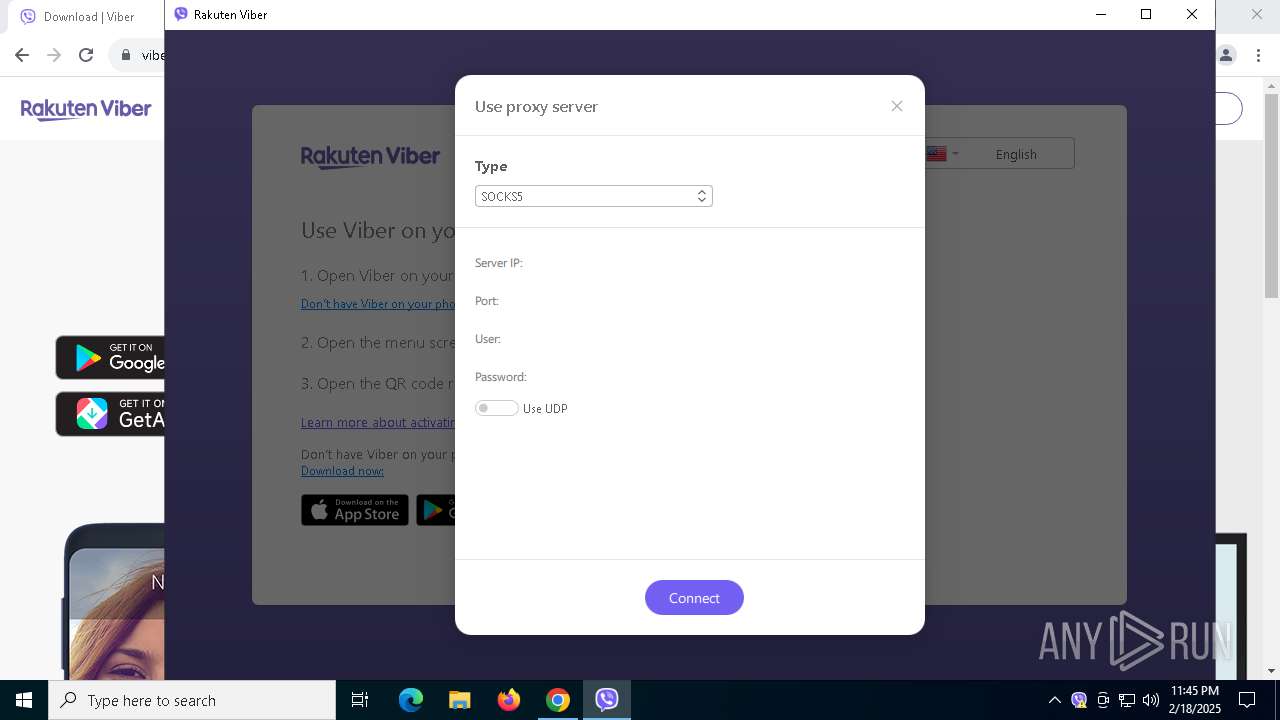
Checks proxy server information
- ViberBA.exe (PID: 2612)
- ViberSetup.exe (PID: 6476)
- Viber.exe (PID: 6912)
Reads the software policy settings
- ViberSetup.exe (PID: 6476)
- msiexec.exe (PID: 5496)
- Viber.exe (PID: 6912)
- ViberBA.exe (PID: 2612)
Creates a software uninstall entry
- msiexec.exe (PID: 5496)
Reads security settings of Internet Explorer
- ie4uinit.exe (PID: 7020)
- ie4uinit.exe (PID: 1172)
Reads Environment values
- msiexec.exe (PID: 5496)
- Viber.exe (PID: 6912)
Qt framework related mutex has been found
- Viber.exe (PID: 6912)
Process checks computer location settings
- Viber.exe (PID: 6912)
Reads the time zone
- Viber.exe (PID: 6912)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
158
Monitored processes
26
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1172 | ie4uinit.exe -show | C:\Windows\System32\ie4uinit.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IE Per-User Initialization Utility Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1520 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5956 --field-trial-handle=1928,i,2621669611468049676,1430057333326743047,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2072 | C:\Windows\syswow64\MsiExec.exe -Embedding B20F6EA09967606C3868633F0444AE07 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2356 | rundll32.exe "C:\WINDOWS\Installer\MSI6957.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1337953 2 ViberCustomActions!ViberCustomActions.KillViberCustomAction.KillViber | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2612 | "C:\Users\admin\AppData\Local\Temp\{5D6FB5F8-7D6A-4E95-92EC-0ED5E88C5C0D}\.ba\ViberBA.exe" -burn.ba.apiver 569705357157400576 -burn.ba.pipe BurnPipe.{20972129-2ABB-4A19-9406-8D749D825009} {B422A75C-D0B9-47D4-9FE4-F1777BC9BF95} | C:\Users\admin\AppData\Local\Temp\{5D6FB5F8-7D6A-4E95-92EC-0ED5E88C5C0D}\.ba\ViberBA.exe | ViberSetup.exe | ||||||||||||
User: admin Company: ViberBA Integrity Level: MEDIUM Description: ViberBA Exit code: 0 Version: 24.6.0.2 Modules
| |||||||||||||||
| 3076 | C:\Windows\System32\MsiExec.exe -Embedding 644ED889744CCA47F5304817F59E5699 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3140 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=860 --field-trial-handle=1928,i,2621669611468049676,1430057333326743047,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3876 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5296 --field-trial-handle=1928,i,2621669611468049676,1430057333326743047,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 4668 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4644 --field-trial-handle=1928,i,2621669611468049676,1430057333326743047,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 5032 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5328 --field-trial-handle=1928,i,2621669611468049676,1430057333326743047,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
45 963
Read events
45 386
Write events
554
Delete events
23
Modification events
| (PID) Process: | (6300) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6300) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6300) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6300) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6300) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (4668) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000918A02E75E82DB01 | |||
| (PID) Process: | (2612) ViberBA.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\ViberBA_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2612) ViberBA.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\ViberBA_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2612) ViberBA.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\ViberBA_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2612) ViberBA.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\ViberBA_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
Executable files
117
Suspicious files
386
Text files
64
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6300 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF13835c.TMP | — | |
MD5:— | SHA256:— | |||
| 6300 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6300 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF13836c.TMP | — | |
MD5:— | SHA256:— | |||
| 6300 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6300 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF13836c.TMP | — | |
MD5:— | SHA256:— | |||
| 6300 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF13836c.TMP | — | |
MD5:— | SHA256:— | |||
| 6300 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6300 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6300 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF13837b.TMP | — | |
MD5:— | SHA256:— | |||
| 6300 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
101
DNS requests
107
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5696 | svchost.exe | GET | 200 | 95.101.54.240:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5696 | svchost.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6300 | chrome.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
6300 | chrome.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
3076 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6300 | chrome.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAJP0xH3s%2BBMqM0zUi31yTc%3D | unknown | — | — | whitelisted |
3076 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2612 | ViberBA.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAsllCLO2YEqFaBOmVKKDvo%3D | unknown | — | — | whitelisted |
2612 | ViberBA.exe | GET | 200 | 184.30.131.245:80 | http://status.rapidssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRJiUKgT2m88fZ4nxc1Lu6M%2FjvkagQUDNtsgkkPSmcKuBTuesRIUojrVjgCEAnRuLsYFuF1BJh2h9x6leI%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 2.19.96.120:443 | — | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5696 | svchost.exe | 95.101.54.240:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5696 | svchost.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
6300 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6680 | chrome.exe | 104.85.28.109:80 | viber.com | AKAMAI-AS | FR | unknown |
6680 | chrome.exe | 104.85.28.109:443 | viber.com | AKAMAI-AS | FR | unknown |
6680 | chrome.exe | 108.177.127.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
viber.com |
| unknown |
accounts.google.com |
| whitelisted |
www.viber.com |
| whitelisted |
cdn.cookielaw.org |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
2612 | ViberBA.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
6912 | Viber.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |