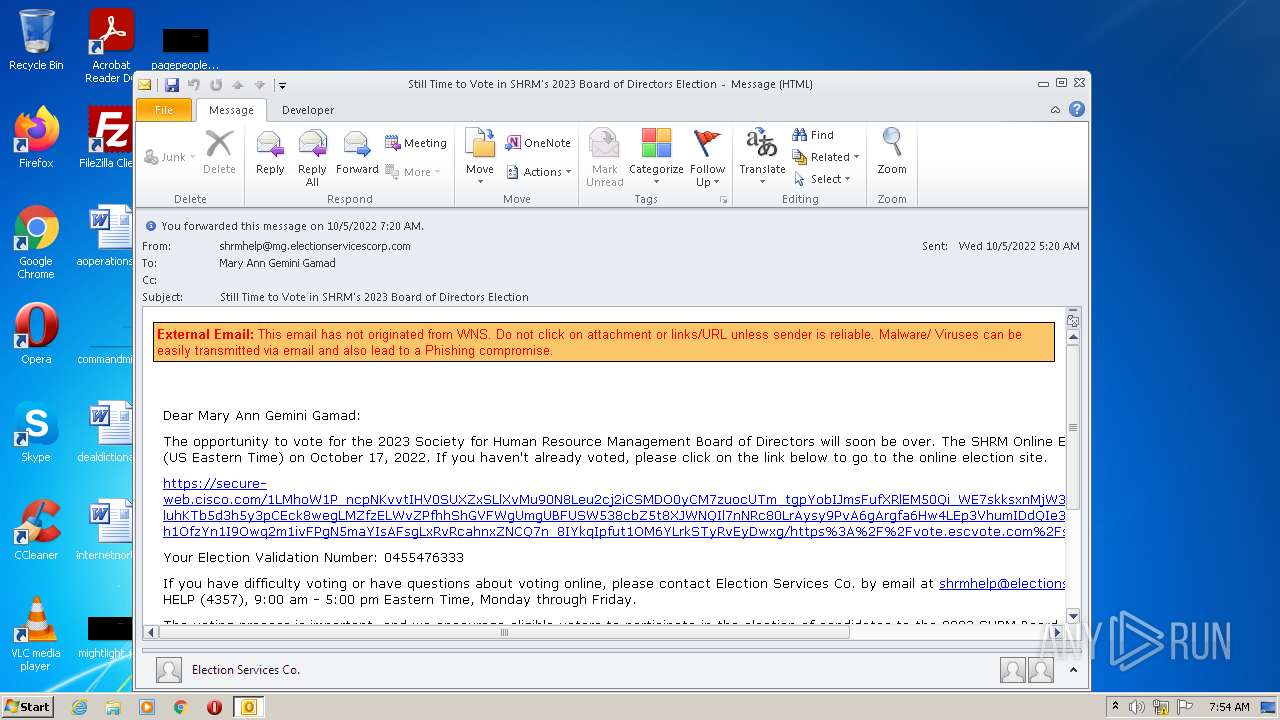
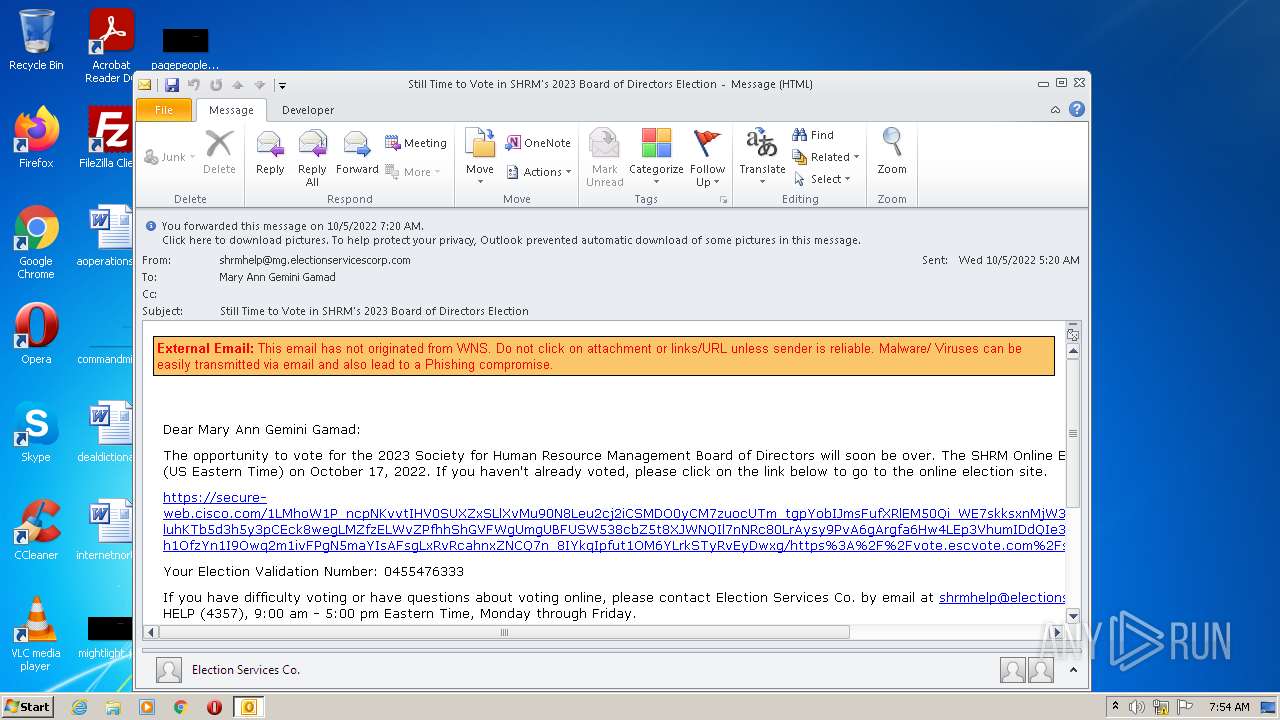
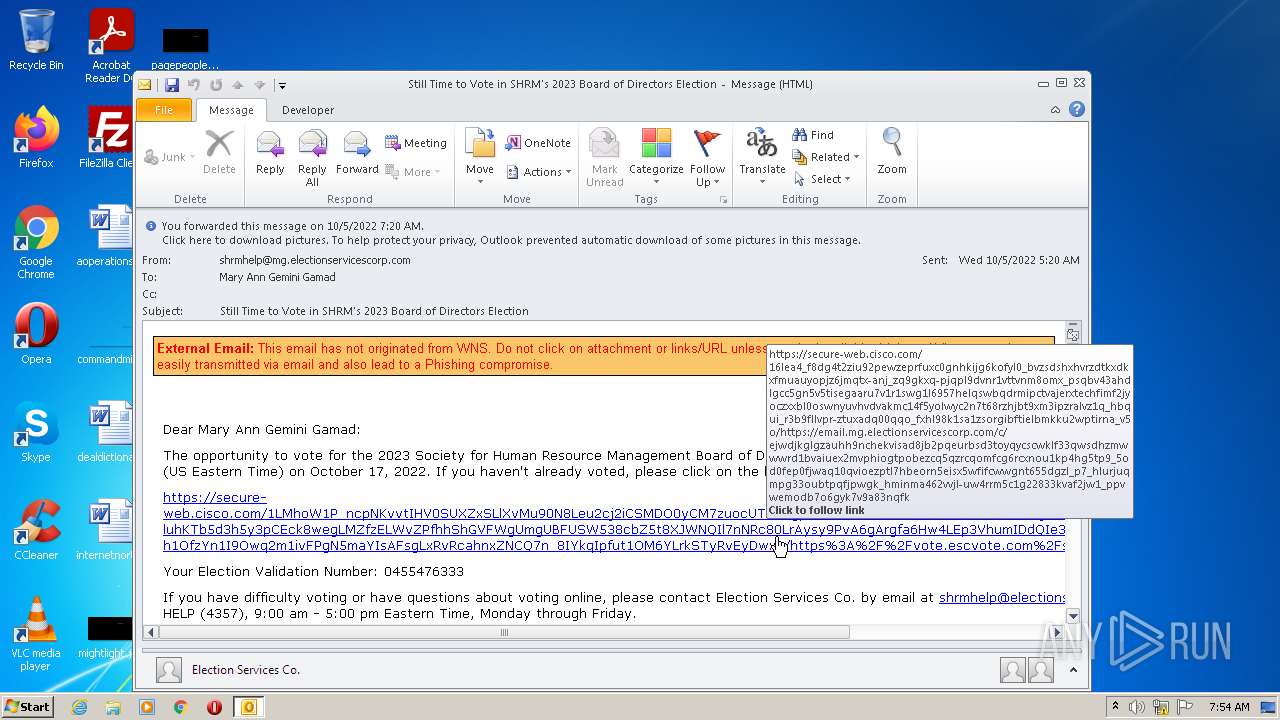
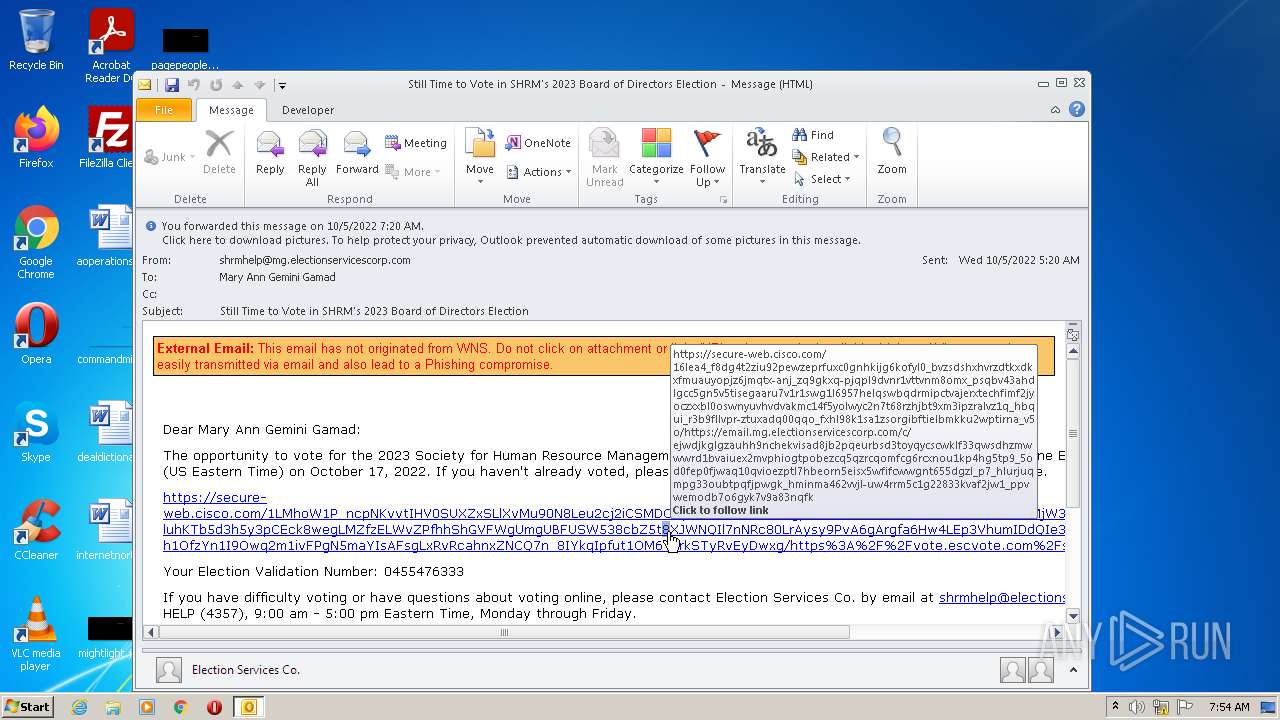
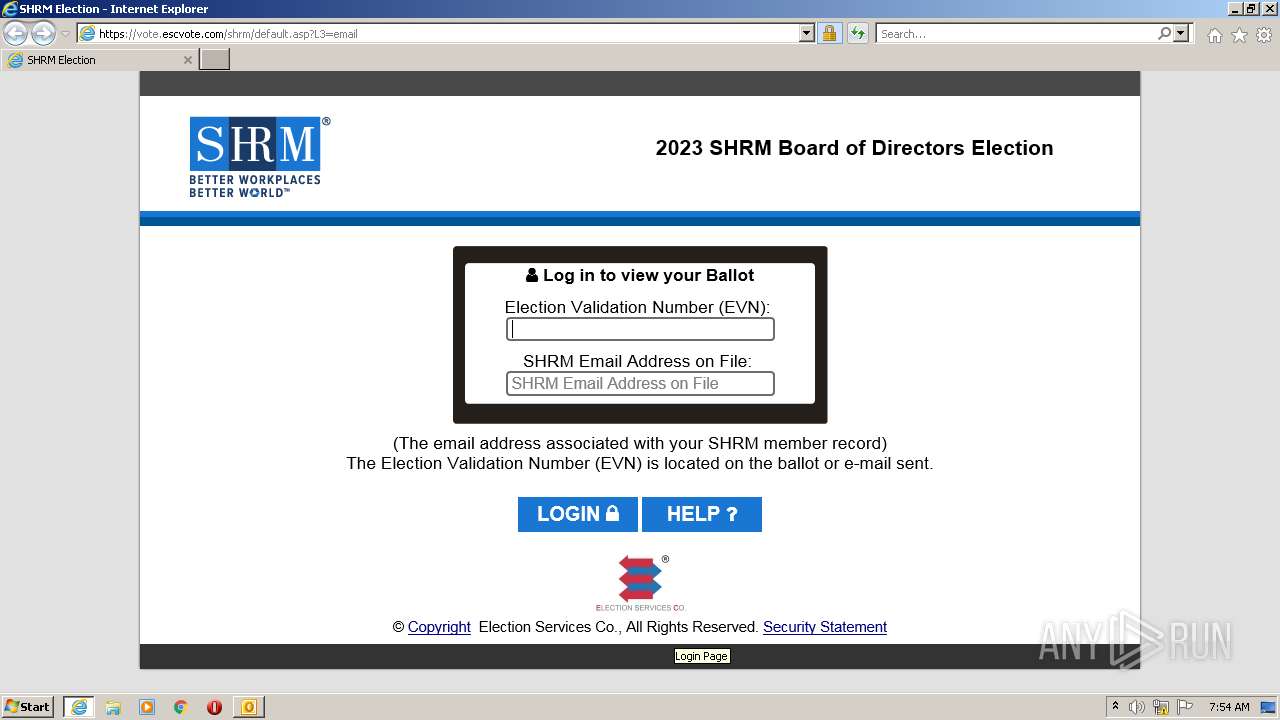
| File name: | Still Time to Vote in SHRM's 2023 Board of Directors Election.msg |
| Full analysis: | https://app.any.run/tasks/af644870-3f22-48a8-8c37-b434650e5598 |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2022, 06:54:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 014A849233CB8E1D0037E04FE3F9BBD9 |
| SHA1: | D0D04FE78CB4299726B44FF7B141CB0963ACC84D |
| SHA256: | 739E99416EF7CC31BCF33B737FAFC5AC312936404A55317C88BC4C3F4E06FDE9 |
| SSDEEP: | 768:dxo8k3+QsKOQkmMSdss4G4IhSna6fYOqQLJ2GsKJsK4UunFn6n4L0uWtWHYfboZ6:Lo8e+QBMS6G4IgJLxjunFn6n4L07 |
MALICIOUS
Saves itself using an automatic execution at the hidden registry location
- OUTLOOK.EXE (PID: 3492)
SUSPICIOUS
No suspicious indicators.INFO
Reads the machine GUID from the registry
- OUTLOOK.EXE (PID: 3492)
Creates files in the user directory
- OUTLOOK.EXE (PID: 3492)
Process checks LSA protection
- OUTLOOK.EXE (PID: 3492)
Application launched itself
- iexplore.exe (PID: 1068)
Starts Internet Explorer
- OUTLOOK.EXE (PID: 3492)
Searches for installed software
- OUTLOOK.EXE (PID: 3492)
Process checks computer location settings
- OUTLOOK.EXE (PID: 3492)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (45.3) |
|---|---|---|
| .oft | | | Outlook Form Template (26.5) |
Total processes
39
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 368 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1068 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1068 | "C:\Program Files\Internet Explorer\iexplore.exe" https://secure-web.cisco.com/16LEa4_f8dG4T2ZiU92PEwZEPRfuxc0gNhkIjg6kofYL0_BVZsdSHXhvRZdTKXDKXFmuAuyopjz6jmqTx-aNj_zQ9GkXq-PJqPl9Dvnr1VttVNM8Omx_psQBV43ahDlGCc5gN5V5TisEGaaru7v1r1swg1l6957HELqSwBqDrMIPCtVaJERXteCHFImF2JyOCZxXbL0oswNYUVHvDvakMC14f5YOLwYc2N7T68rZHJBt9xm3iPZralVZ1q_HBqUI_r3B9FLlVpR-zTUxADq00qQO_fxHl98k1Sa1zsorGIBFTIELbMkkU2wptIrNA_V5O/https%3A%2F%2Femail.mg.electionservicescorp.com%2Fc%2FeJwdjkGLgzAUhH9NchEkviSad8jB2pQeurBsD3tOYqyCscWkLf33qwsDHzMwwwRd1bVAIUEx2mvpHIOGTpobeZCq5QZRCQOmFcg6rCXnou1kp4hg5tp9_5oD0FEP0FjwAq10qvIoEZptL7hBeORN5eisx5wfifCWwGnT655DGZL_p7_HLUrjuqMPg33OubTpQfjpwgk_hminma462vVjl-UW4rRM5c1G22833kvaF2jW1_PPVwEMoDB7o6gYk7v9A83NQfk | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3492 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\Still Time to Vote in SHRM's 2023 Board of Directors Election.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
Total events
18 811
Read events
18 107
Write events
682
Delete events
22
Modification events
| (PID) Process: | (3492) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3492) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3492) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3492) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3492) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3492) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3492) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3492) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3492) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (3492) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
14
Text files
20
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3492 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRDAA6.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3492 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 3492 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3492 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 368 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\263821BCA2CBC5EA0B25012F05788322_41310C887E59D4EB5B8FD9D3DCA2C98D | der | |
MD5:— | SHA256:— | |||
| 368 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6CFED4E1A8866BE87BE17622BFB4D726_FBADB8F7FD7B56EE191ACF24A8989D94 | der | |
MD5:— | SHA256:— | |||
| 3492 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{AD3948A3-7DB0-44A1-8954-5521522870FE}\{1C306CB1-771E-4B4B-A902-86E897877F5B}.png | image | |
MD5:4C61C12EDBC453D7AE184976E95258E1 | SHA256:296526F9A716C1AA91BA5D6F69F0EB92FDF79C2CB2CFCF0CEB22B7CCBC27035F | |||
| 3492 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_Calendar_2_A3FB297080F3FB4AA65C0A4BBE94BBE5.dat | xml | |
MD5:B21ED3BD946332FF6EBC41A87776C6BB | SHA256:B1AAC4E817CD10670B785EF8E5523C4A883F44138E50486987DC73054A46F6F4 | |||
| 3492 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_AvailabilityOptions_2_A4EDC5162710C247B39D048F845726E0.dat | xml | |
MD5:EEAA832C12F20DE6AAAA9C7B77626E72 | SHA256:C4C9A90F2C961D9EE79CF08FBEE647ED7DE0202288E876C7BAAD00F4CA29CA16 | |||
| 3492 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_RssRule_2_5E70D1335FCD384FB729F220DC327292.dat | xml | |
MD5:D8B37ED0410FB241C283F72B76987F18 | SHA256:31E68049F6B7F21511E70CD7F2D95B9CF1354CF54603E8F47C1FC40F40B7A114 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
38
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1068 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
368 | iexplore.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQDjmTL5NIrO9%2B84JPrh00LV | US | der | 472 b | whitelisted |
368 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
1068 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
368 | iexplore.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 2.18 Kb | whitelisted |
368 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?ea718f22e19009e4 | US | compressed | 60.9 Kb | whitelisted |
368 | iexplore.exe | GET | 200 | 2.16.218.170:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgOjqBB9JdBmeefTHtyNP0RSdQ%3D%3D | unknown | der | 503 b | shared |
368 | iexplore.exe | GET | 200 | 23.45.105.185:80 | http://x1.c.lencr.org/ | NL | der | 717 b | whitelisted |
368 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?25375bf7f4064e9c | US | compressed | 60.9 Kb | whitelisted |
3492 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1068 | iexplore.exe | 204.79.197.200:443 | www.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3492 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
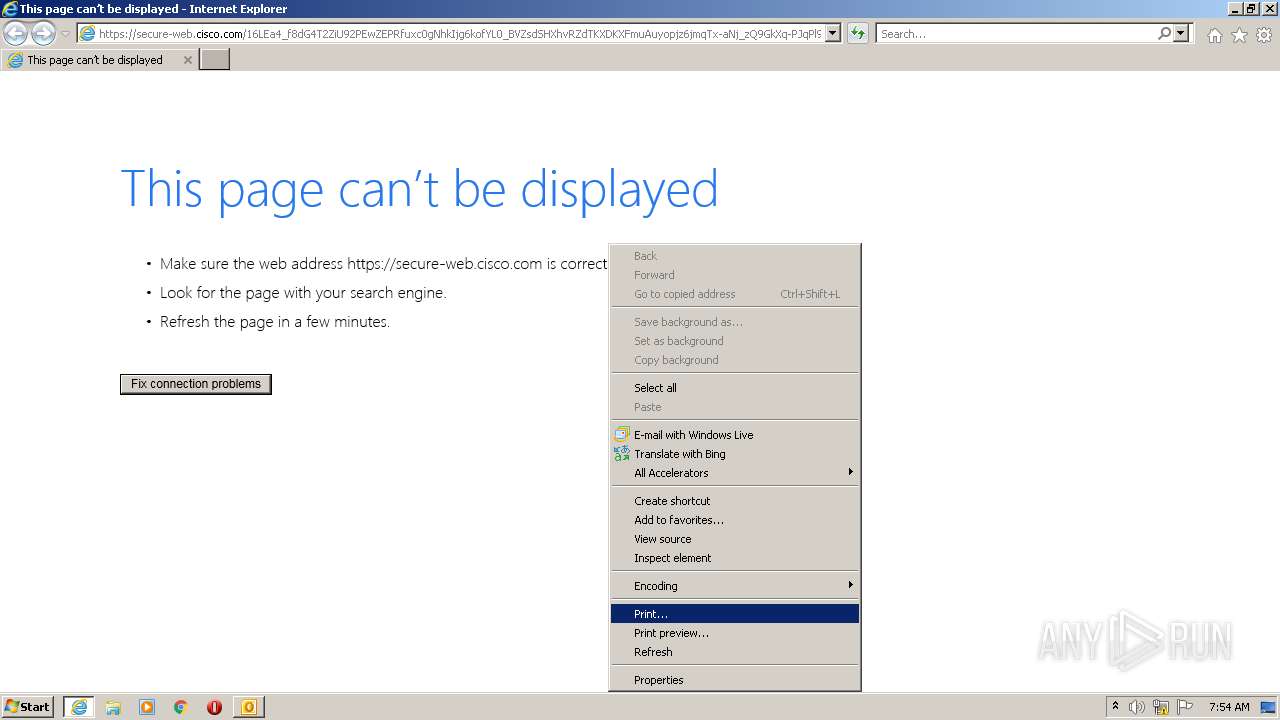
368 | iexplore.exe | 146.112.255.69:443 | secure-web.cisco.com | OPENDNS | US | suspicious |
— | — | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
1068 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
1068 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | EDGECAST | GB | whitelisted |
368 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
368 | iexplore.exe | 104.17.25.14:443 | cdnjs.cloudflare.com | CLOUDFLARENET | — | suspicious |
368 | iexplore.exe | 34.127.83.42:443 | email.mg.electionservicescorp.com | GOOGLE-CLOUD-PLATFORM | US | suspicious |
— | — | 93.184.220.29:80 | ocsp.digicert.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
secure-web.cisco.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
commercial.ocsp.identrust.com |
| whitelisted |
email.mg.electionservicescorp.com |
| suspicious |
ocsp.digicert.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |