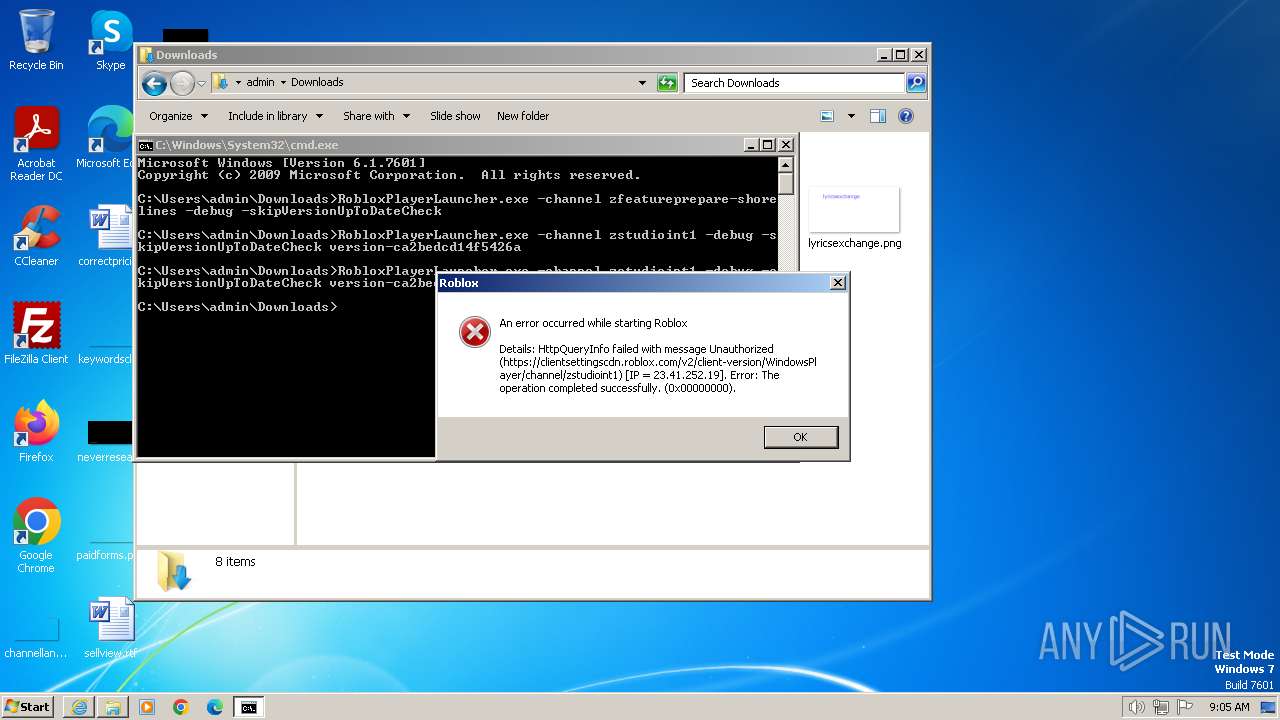
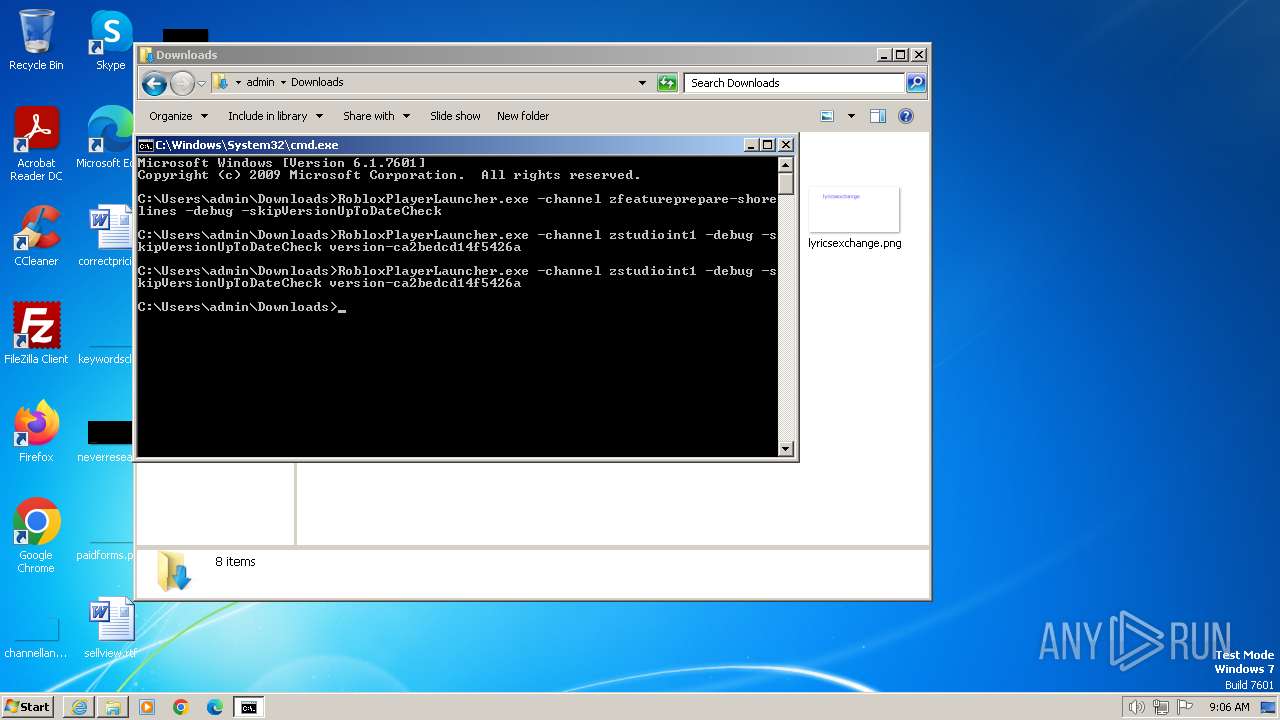
| URL: | https://setup.rbxcdn.com/Roblox.exe |
| Full analysis: | https://app.any.run/tasks/7bf626a2-3129-4a06-abf4-7b1370183eb4 |
| Verdict: | Malicious activity |
| Analysis date: | April 02, 2024, 08:01:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 8250106910DE4D6414EE3FBCED0F4D82 |
| SHA1: | 751BDB4E697D9F6C63A38D481A844F2C2264F8AE |
| SHA256: | 738D3D882771691A7DBAD8CC1E5BED652F0248FF885538220BF5BA71430BC229 |
| SSDEEP: | 3:N8NYDrkTn:2S/kT |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Internet Settings
- RobloxPlayerLauncher.exe (PID: 3800)
- RobloxPlayerLauncher.exe (PID: 296)
- RobloxPlayerLauncher.exe (PID: 3272)
- RobloxPlayerLauncher.exe (PID: 572)
- RobloxPlayerLauncher.exe (PID: 2880)
- RobloxPlayerLauncher.exe (PID: 3016)
Reads security settings of Internet Explorer
- RobloxPlayerLauncher.exe (PID: 3800)
- RobloxPlayerLauncher.exe (PID: 296)
- RobloxPlayerLauncher.exe (PID: 572)
- RobloxPlayerLauncher.exe (PID: 3272)
- RobloxPlayerLauncher.exe (PID: 2880)
- RobloxPlayerLauncher.exe (PID: 3016)
Checks Windows Trust Settings
- RobloxPlayerLauncher.exe (PID: 3800)
- RobloxPlayerLauncher.exe (PID: 296)
- RobloxPlayerLauncher.exe (PID: 572)
- RobloxPlayerLauncher.exe (PID: 3272)
- RobloxPlayerLauncher.exe (PID: 2880)
- RobloxPlayerLauncher.exe (PID: 3016)
Reads settings of System Certificates
- RobloxPlayerLauncher.exe (PID: 3800)
- RobloxPlayerLauncher.exe (PID: 296)
- RobloxPlayerLauncher.exe (PID: 3272)
- RobloxPlayerLauncher.exe (PID: 2880)
- RobloxPlayerLauncher.exe (PID: 572)
- RobloxPlayerLauncher.exe (PID: 3016)
Application launched itself
- RobloxPlayerLauncher.exe (PID: 3800)
- RobloxPlayerLauncher.exe (PID: 2880)
- RobloxPlayerLauncher.exe (PID: 3272)
INFO
Drops the executable file immediately after the start
- iexplore.exe (PID: 4000)
Application launched itself
- iexplore.exe (PID: 1836)
Modifies the phishing filter of IE
- iexplore.exe (PID: 1836)
Checks supported languages
- wmpnscfg.exe (PID: 3680)
- RobloxPlayerLauncher.exe (PID: 3800)
- RobloxPlayerLauncher.exe (PID: 296)
- RobloxPlayerLauncher.exe (PID: 3272)
- RobloxPlayerLauncher.exe (PID: 572)
- RobloxPlayerLauncher.exe (PID: 3016)
- RobloxPlayerLauncher.exe (PID: 2880)
Manual execution by a user
- wmpnscfg.exe (PID: 3680)
- explorer.exe (PID: 2148)
- cmd.exe (PID: 2244)
The process uses the downloaded file
- iexplore.exe (PID: 1836)
Reads the machine GUID from the registry
- RobloxPlayerLauncher.exe (PID: 3800)
- RobloxPlayerLauncher.exe (PID: 296)
- RobloxPlayerLauncher.exe (PID: 3272)
- RobloxPlayerLauncher.exe (PID: 572)
- RobloxPlayerLauncher.exe (PID: 2880)
- RobloxPlayerLauncher.exe (PID: 3016)
Reads the computer name
- wmpnscfg.exe (PID: 3680)
- RobloxPlayerLauncher.exe (PID: 3800)
- RobloxPlayerLauncher.exe (PID: 296)
- RobloxPlayerLauncher.exe (PID: 3272)
- RobloxPlayerLauncher.exe (PID: 572)
- RobloxPlayerLauncher.exe (PID: 2880)
- RobloxPlayerLauncher.exe (PID: 3016)
Create files in a temporary directory
- RobloxPlayerLauncher.exe (PID: 3800)
- RobloxPlayerLauncher.exe (PID: 296)
- RobloxPlayerLauncher.exe (PID: 3272)
- RobloxPlayerLauncher.exe (PID: 572)
- RobloxPlayerLauncher.exe (PID: 2880)
- RobloxPlayerLauncher.exe (PID: 3016)
Checks proxy server information
- RobloxPlayerLauncher.exe (PID: 3800)
- RobloxPlayerLauncher.exe (PID: 296)
- RobloxPlayerLauncher.exe (PID: 572)
- RobloxPlayerLauncher.exe (PID: 3272)
- RobloxPlayerLauncher.exe (PID: 2880)
- RobloxPlayerLauncher.exe (PID: 3016)
Reads the software policy settings
- RobloxPlayerLauncher.exe (PID: 3800)
- RobloxPlayerLauncher.exe (PID: 296)
- RobloxPlayerLauncher.exe (PID: 572)
- RobloxPlayerLauncher.exe (PID: 3272)
- RobloxPlayerLauncher.exe (PID: 2880)
- RobloxPlayerLauncher.exe (PID: 3016)
Creates files or folders in the user directory
- RobloxPlayerLauncher.exe (PID: 3800)
- RobloxPlayerLauncher.exe (PID: 296)
- RobloxPlayerLauncher.exe (PID: 3272)
- RobloxPlayerLauncher.exe (PID: 572)
- RobloxPlayerLauncher.exe (PID: 2880)
- RobloxPlayerLauncher.exe (PID: 3016)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
52
Monitored processes
11
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 296 | C:\Users\admin\Downloads\RobloxPlayerLauncher.exe --crashpad --no-rate-limit --database=C:\Users\admin\AppData\Local\Temp\crashpad_roblox --metrics-dir=C:\Users\admin\AppData\Local\Temp\crashpad_roblox --url=https://uploads.backtrace.rbx.com/post --annotation=RobloxChannel=zfeatureprepare-shorelines --annotation=RobloxGitHash=771b72f8e35b7c83e6a74bce1125195c9f128786 --annotation=UploadAttachmentKiloByteLimit=100 --annotation=UploadPercentage=100 --annotation=format=minidump --annotation=token=a2440b0bfdada85f34d79b43839f2b49ea6bba474bd7d126e844bc119271a1c3 --initial-client-data=0x598,0x59c,0x5a0,0x574,0x5a8,0x1db7948,0x1db7958,0x1db7968 | C:\Users\admin\Downloads\RobloxPlayerLauncher.exe | RobloxPlayerLauncher.exe | ||||||||||||
User: admin Company: Roblox Corporation Integrity Level: MEDIUM Description: Roblox Exit code: 0 Version: 1, 6, 0, 6180546 Modules
| |||||||||||||||
| 572 | C:\Users\admin\Downloads\RobloxPlayerLauncher.exe --crashpad --no-rate-limit --database=C:\Users\admin\AppData\Local\Temp\crashpad_roblox --metrics-dir=C:\Users\admin\AppData\Local\Temp\crashpad_roblox --url=https://uploads.backtrace.rbx.com/post --annotation=RobloxChannel=zstudioint1 --annotation=RobloxGitHash=771b72f8e35b7c83e6a74bce1125195c9f128786 --annotation=UploadAttachmentKiloByteLimit=100 --annotation=UploadPercentage=100 --annotation=format=minidump --annotation=token=a2440b0bfdada85f34d79b43839f2b49ea6bba474bd7d126e844bc119271a1c3 --initial-client-data=0x580,0x584,0x588,0x55c,0x590,0x1db7948,0x1db7958,0x1db7968 | C:\Users\admin\Downloads\RobloxPlayerLauncher.exe | RobloxPlayerLauncher.exe | ||||||||||||
User: admin Company: Roblox Corporation Integrity Level: MEDIUM Description: Roblox Exit code: 0 Version: 1, 6, 0, 6180546 Modules
| |||||||||||||||
| 1836 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://setup.rbxcdn.com/Roblox.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2148 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2244 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
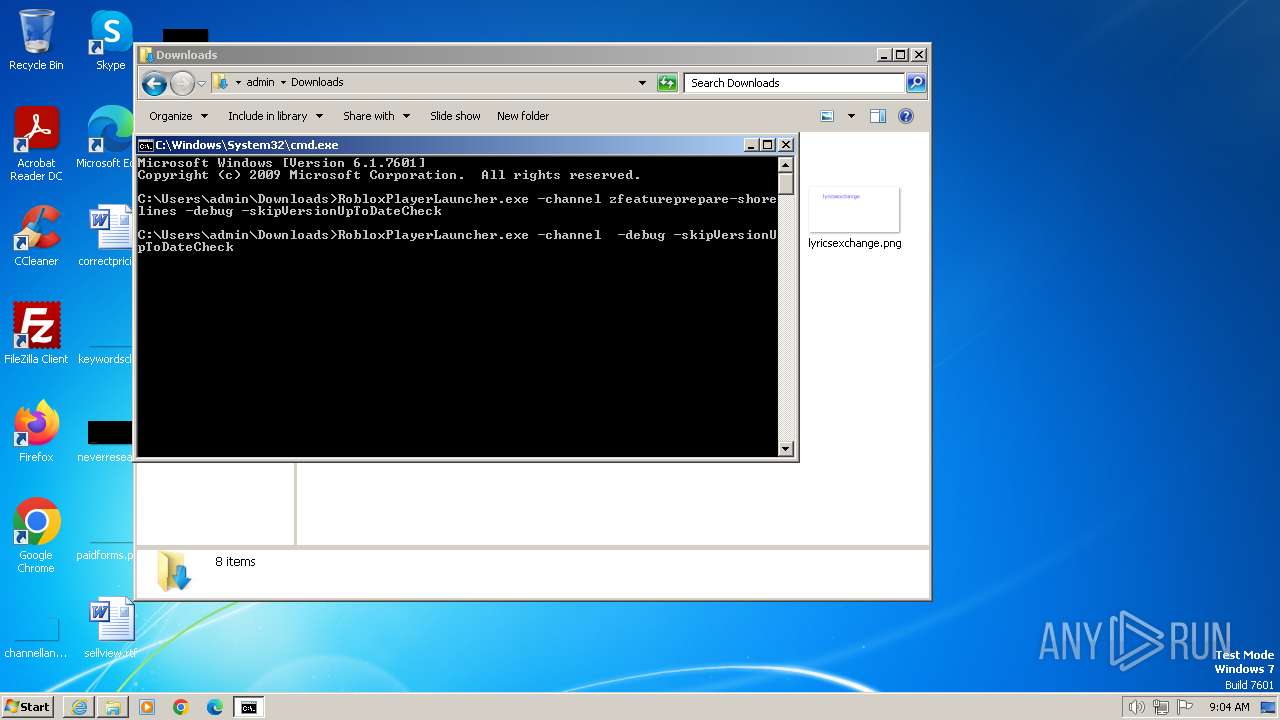
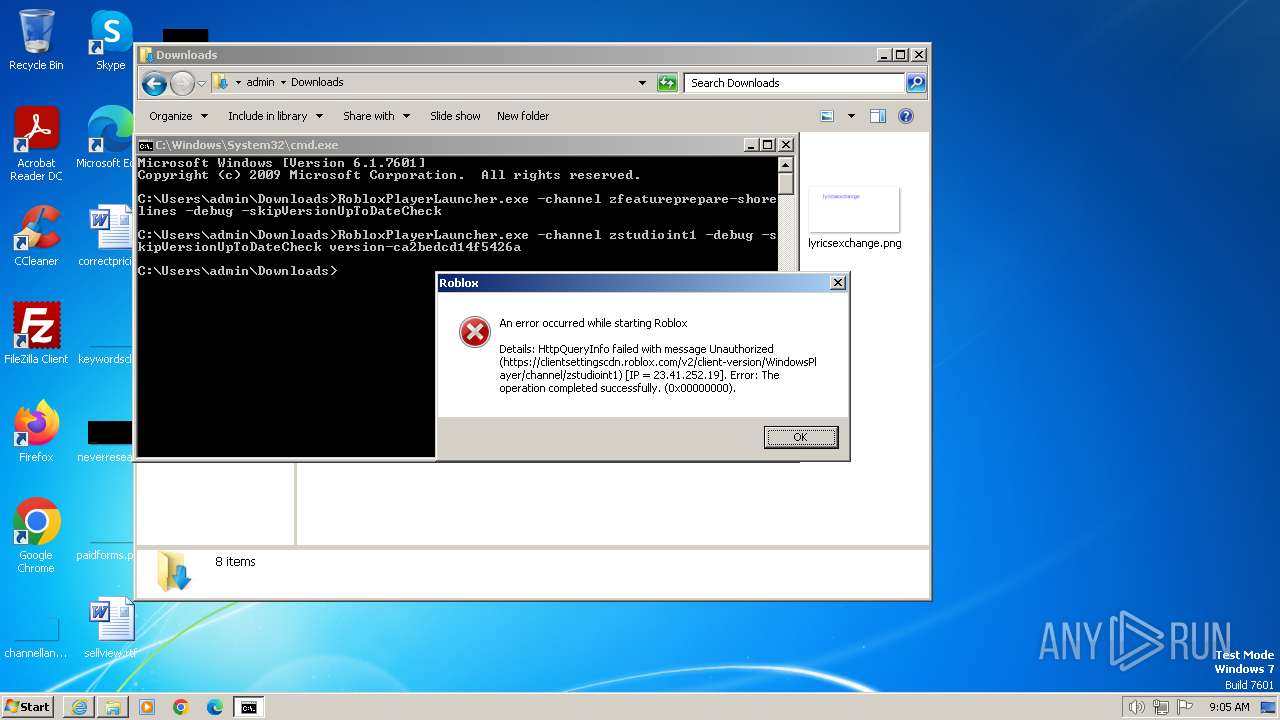
| 2880 | RobloxPlayerLauncher.exe -channel zstudioint1 -debug -skipVersionUpToDateCheck version-ca2bedcd14f5426a | C:\Users\admin\Downloads\RobloxPlayerLauncher.exe | cmd.exe | ||||||||||||
User: admin Company: Roblox Corporation Integrity Level: MEDIUM Description: Roblox Exit code: 4294967295 Version: 1, 6, 0, 6180546 Modules
| |||||||||||||||
| 3016 | C:\Users\admin\Downloads\RobloxPlayerLauncher.exe --crashpad --no-rate-limit --database=C:\Users\admin\AppData\Local\Temp\crashpad_roblox --metrics-dir=C:\Users\admin\AppData\Local\Temp\crashpad_roblox --url=https://uploads.backtrace.rbx.com/post --annotation=RobloxChannel=zstudioint1 --annotation=RobloxGitHash=771b72f8e35b7c83e6a74bce1125195c9f128786 --annotation=UploadAttachmentKiloByteLimit=100 --annotation=UploadPercentage=100 --annotation=format=minidump --annotation=token=a2440b0bfdada85f34d79b43839f2b49ea6bba474bd7d126e844bc119271a1c3 --initial-client-data=0x574,0x578,0x57c,0x550,0x584,0x1db7948,0x1db7958,0x1db7968 | C:\Users\admin\Downloads\RobloxPlayerLauncher.exe | RobloxPlayerLauncher.exe | ||||||||||||
User: admin Company: Roblox Corporation Integrity Level: MEDIUM Description: Roblox Exit code: 0 Version: 1, 6, 0, 6180546 Modules
| |||||||||||||||
| 3272 | RobloxPlayerLauncher.exe -channel zstudioint1 -debug -skipVersionUpToDateCheck version-ca2bedcd14f5426a | C:\Users\admin\Downloads\RobloxPlayerLauncher.exe | cmd.exe | ||||||||||||
User: admin Company: Roblox Corporation Integrity Level: MEDIUM Description: Roblox Exit code: 4294967295 Version: 1, 6, 0, 6180546 Modules
| |||||||||||||||
| 3680 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
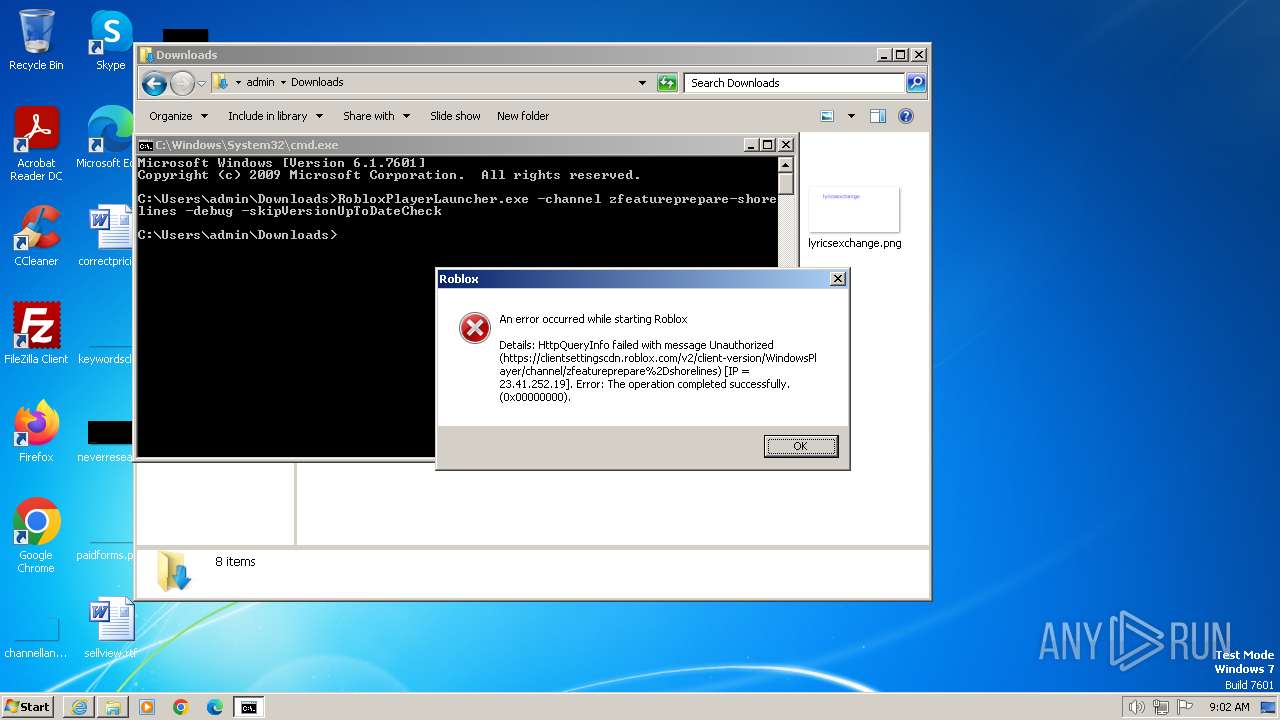
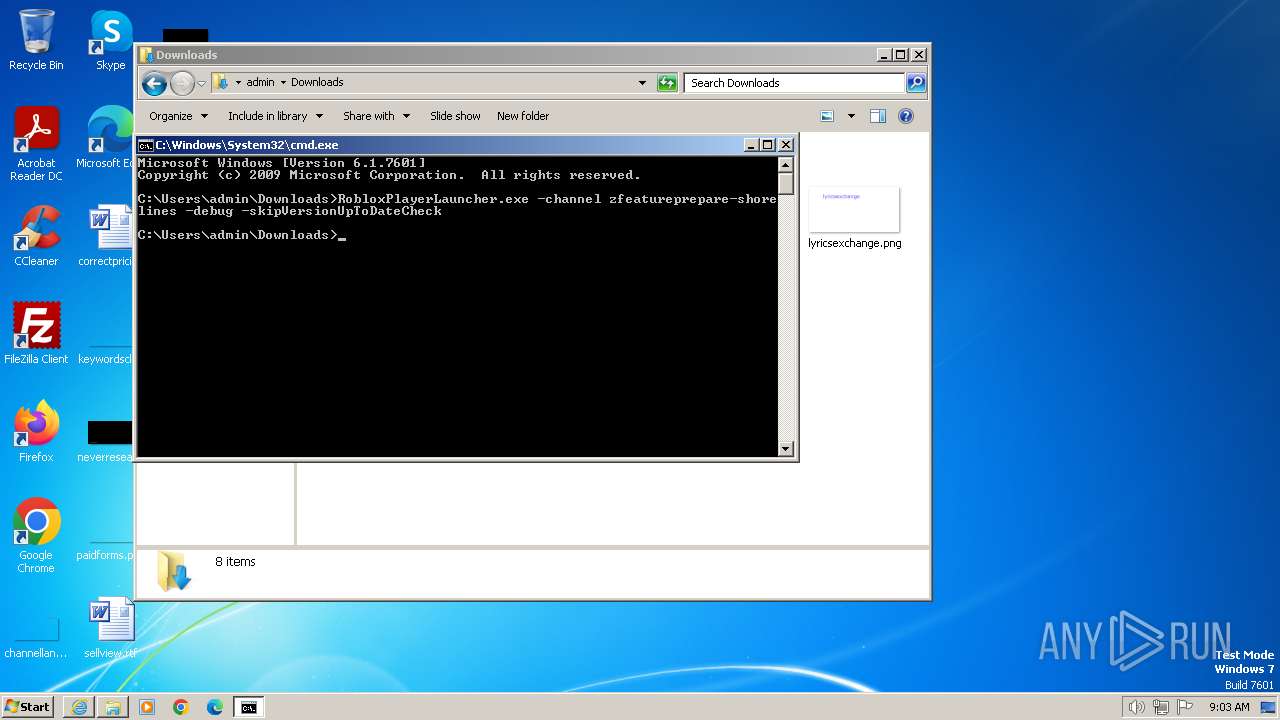
| 3800 | RobloxPlayerLauncher.exe -channel zfeatureprepare-shorelines -debug -skipVersionUpToDateCheck | C:\Users\admin\Downloads\RobloxPlayerLauncher.exe | cmd.exe | ||||||||||||
User: admin Company: Roblox Corporation Integrity Level: MEDIUM Description: Roblox Exit code: 4294967295 Version: 1, 6, 0, 6180546 Modules
| |||||||||||||||
Total events
45 026
Read events
44 636
Write events
328
Delete events
62
Modification events
| (PID) Process: | (1836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (1836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31098067 | |||
| (PID) Process: | (1836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 63845872 | |||
| (PID) Process: | (1836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31098068 | |||
| (PID) Process: | (1836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
2
Suspicious files
11
Text files
20
Unknown types
25
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4000 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 4000 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:— | SHA256:— | |||
| 4000 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:— | SHA256:— | |||
| 4000 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:— | SHA256:— | |||
| 4000 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:— | SHA256:— | |||
| 4000 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\75CA58072B9926F763A91F0CC2798706_645BC4A49DCDC40FE5917FA45C6D4517 | binary | |
MD5:— | SHA256:— | |||
| 4000 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_645BC4A49DCDC40FE5917FA45C6D4517 | binary | |
MD5:— | SHA256:— | |||
| 4000 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\RobloxPlayerLauncher[1].exe | executable | |
MD5:— | SHA256:— | |||
| 4000 | iexplore.exe | C:\Users\admin\Downloads\RobloxPlayerLauncher.exe.v3k9p51.partial | executable | |
MD5:— | SHA256:— | |||
| 1836 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF0F0F079402E58371.TMP | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
41
DNS requests
38
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4000 | iexplore.exe | GET | 304 | 88.221.110.106:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b150b552b216e1f4 | unknown | — | — | unknown |
4000 | iexplore.exe | GET | 304 | 88.221.110.121:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?36ca310eb28aaa33 | unknown | — | — | unknown |
4000 | iexplore.exe | GET | 200 | 108.138.2.10:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | unknown | — | — | unknown |
4000 | iexplore.exe | GET | 200 | 18.66.142.79:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | unknown | — | — | unknown |
1080 | svchost.exe | GET | 200 | 88.221.110.121:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?1b8fee253118cbef | unknown | — | — | unknown |
4000 | iexplore.exe | GET | 200 | 18.66.142.79:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkzUBtJnwJkc3SmanzgxeYU%3D | unknown | — | — | unknown |
1836 | iexplore.exe | GET | 304 | 88.221.110.121:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?aeb32cb922858c96 | unknown | — | — | unknown |
1836 | iexplore.exe | GET | 304 | 88.221.110.121:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?dca56d26e7d9ce15 | unknown | — | — | unknown |
1080 | svchost.exe | GET | 304 | 88.221.110.121:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e90c163b6659448e | unknown | — | — | unknown |
1836 | iexplore.exe | GET | 304 | 88.221.110.121:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?719f0b64dcb4a601 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4000 | iexplore.exe | 13.224.189.57:443 | setup.rbxcdn.com | AMAZON-02 | US | unknown |
4000 | iexplore.exe | 88.221.110.106:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
4000 | iexplore.exe | 88.221.110.121:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
4000 | iexplore.exe | 108.138.2.10:80 | o.ss2.us | AMAZON-02 | US | unknown |
4000 | iexplore.exe | 18.66.142.79:80 | ocsp.rootg2.amazontrust.com | AMAZON-02 | US | unknown |
1080 | svchost.exe | 88.221.110.121:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
setup.rbxcdn.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |