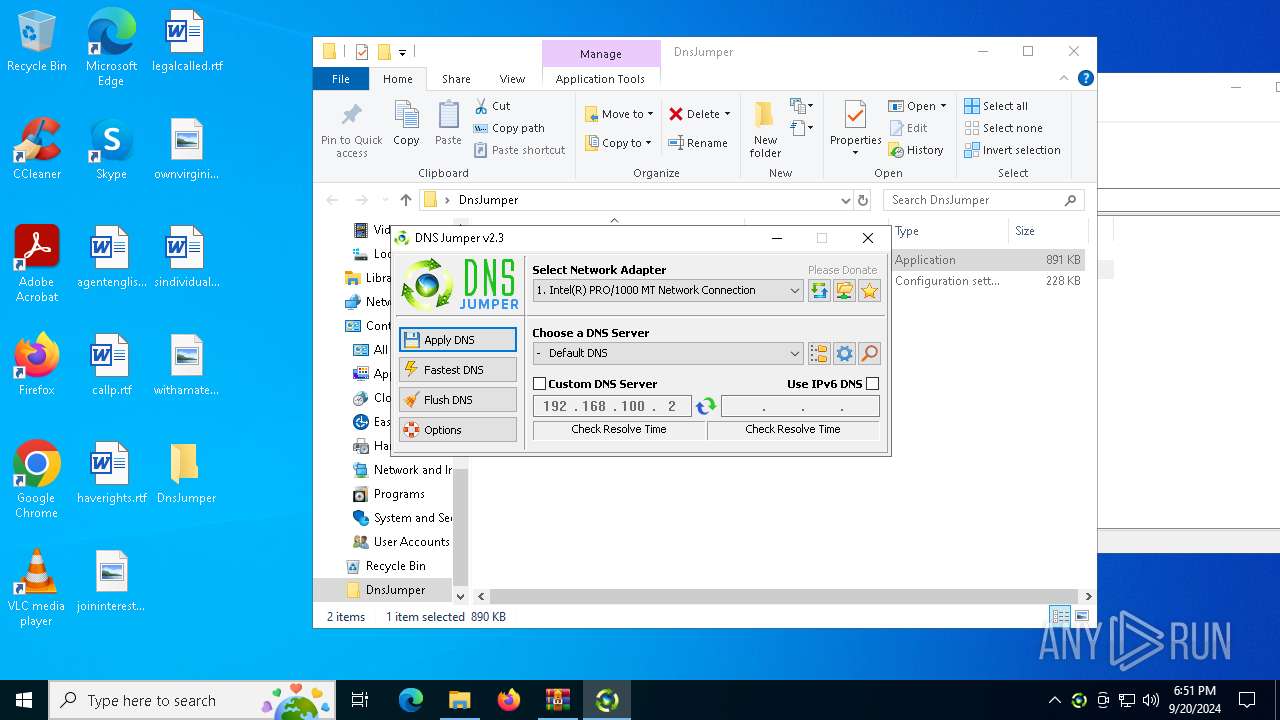
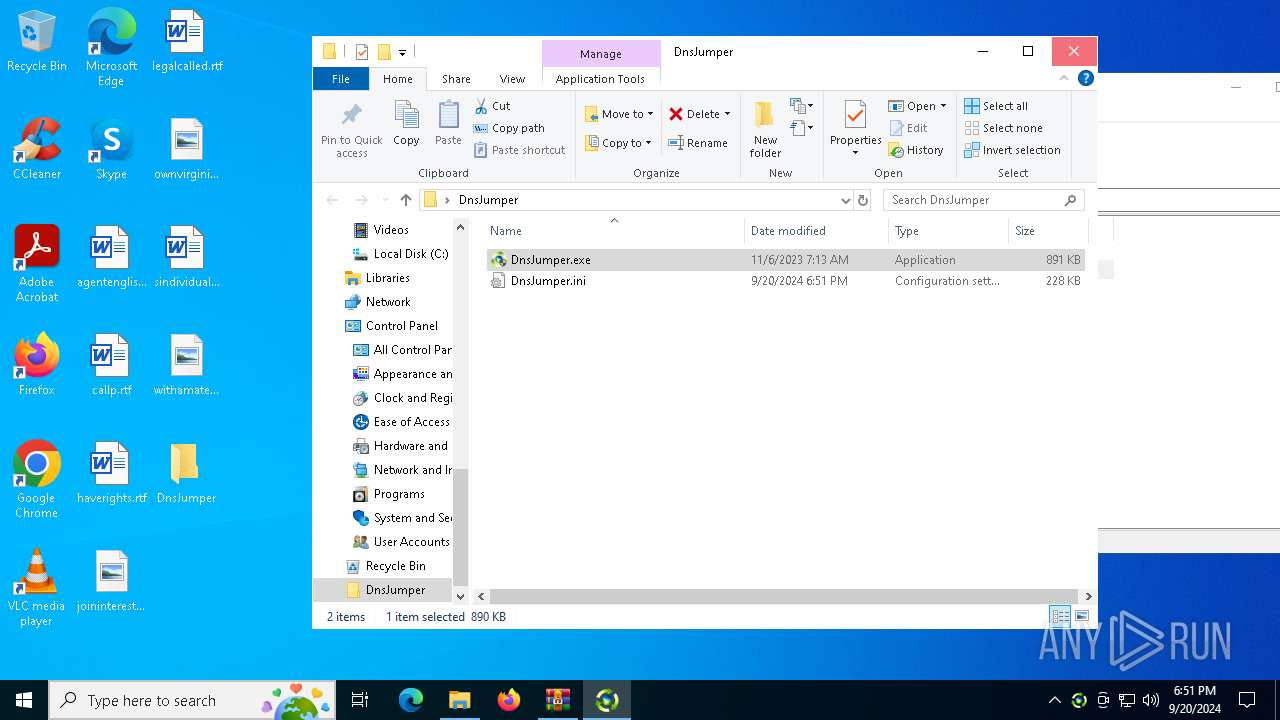
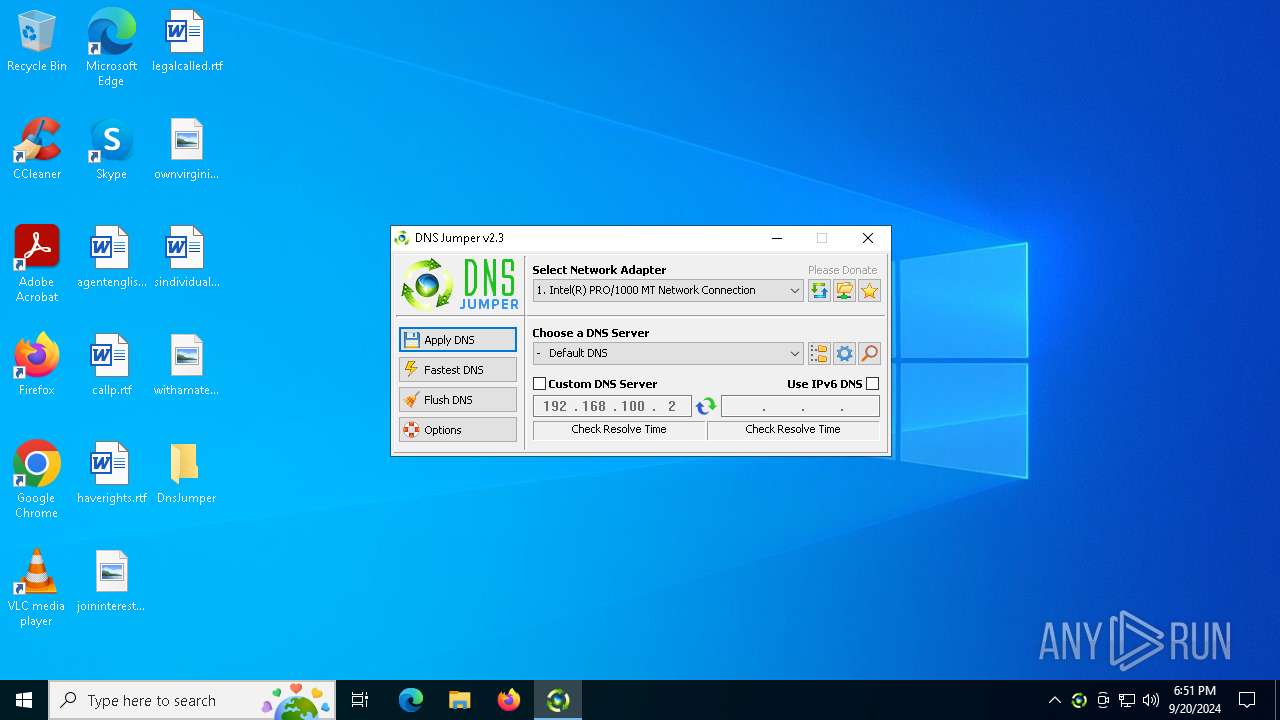
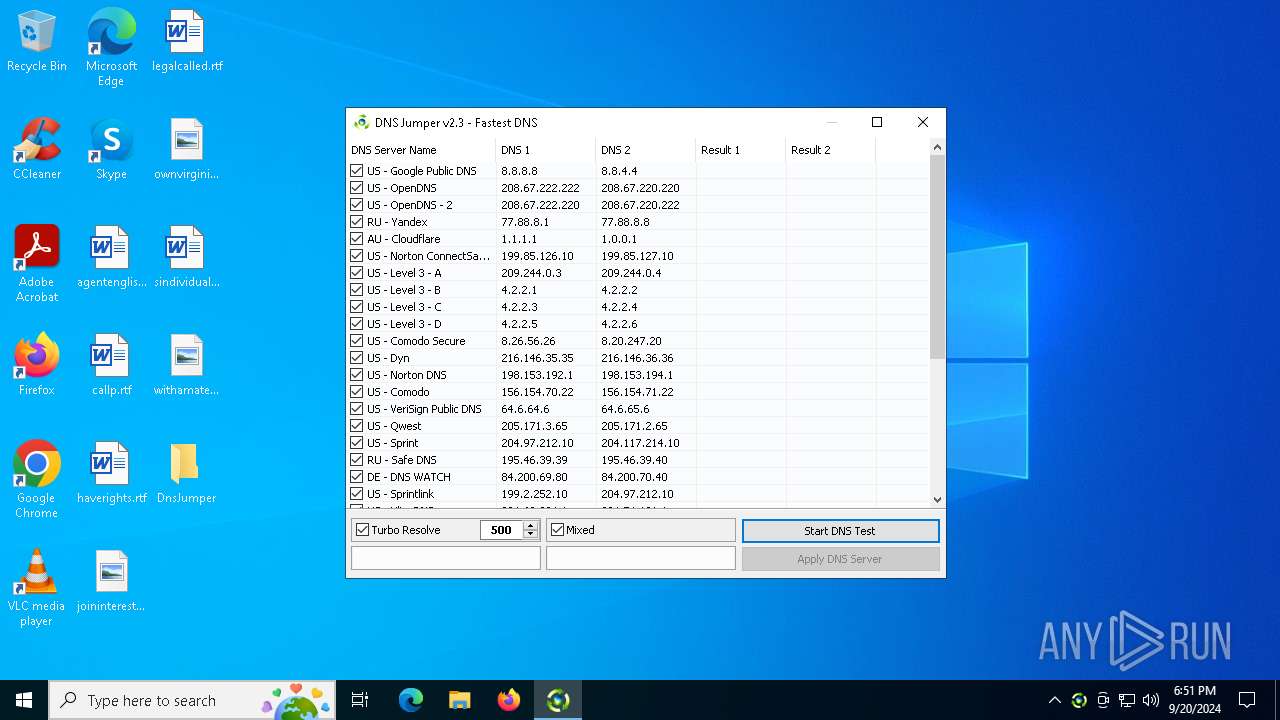
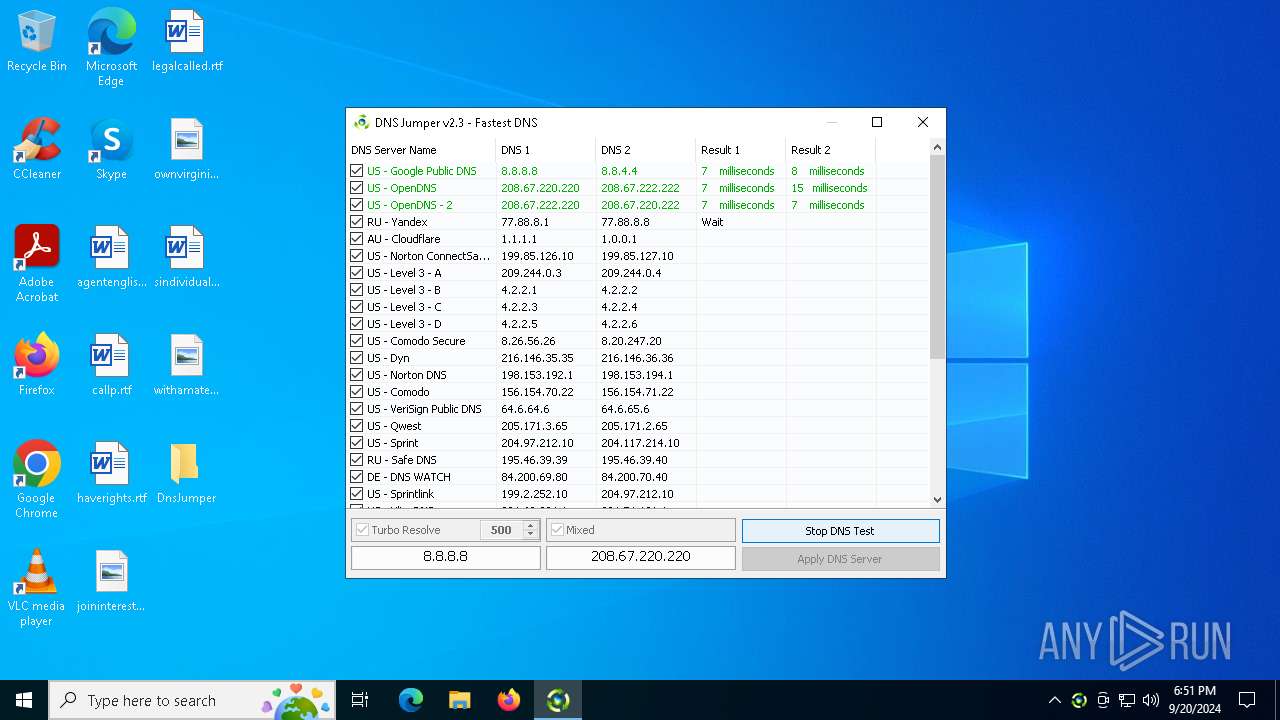
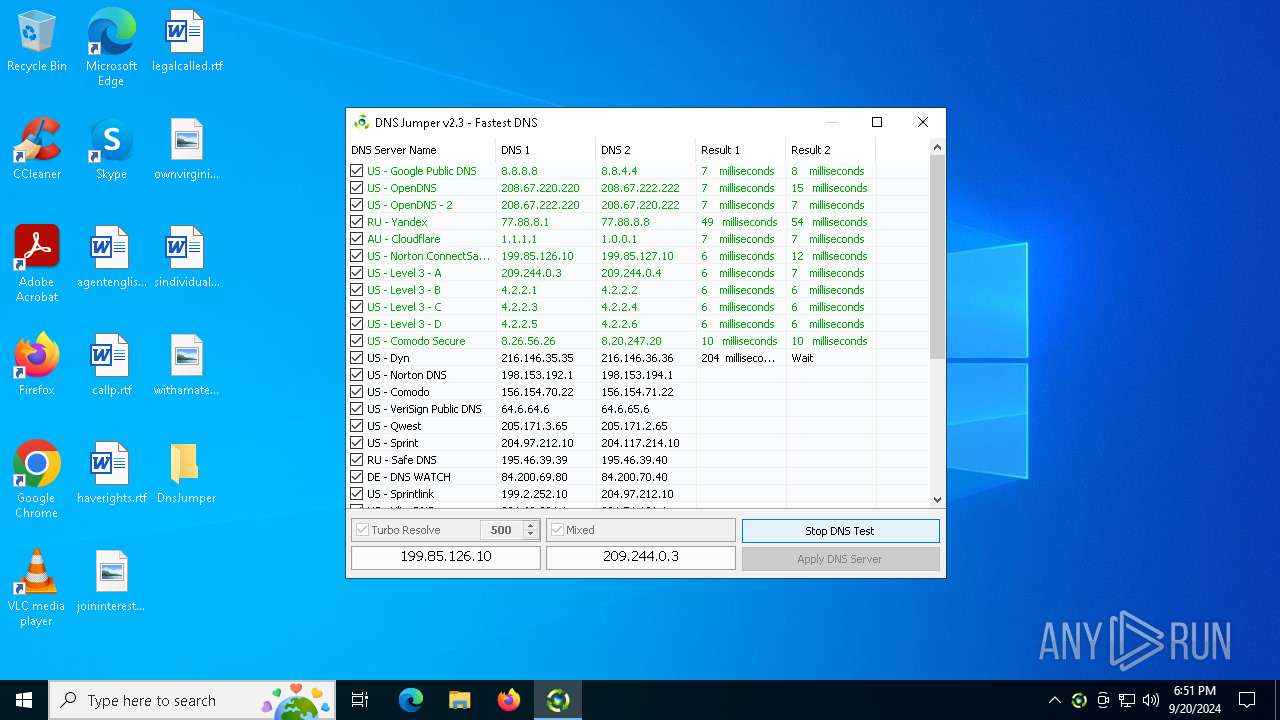
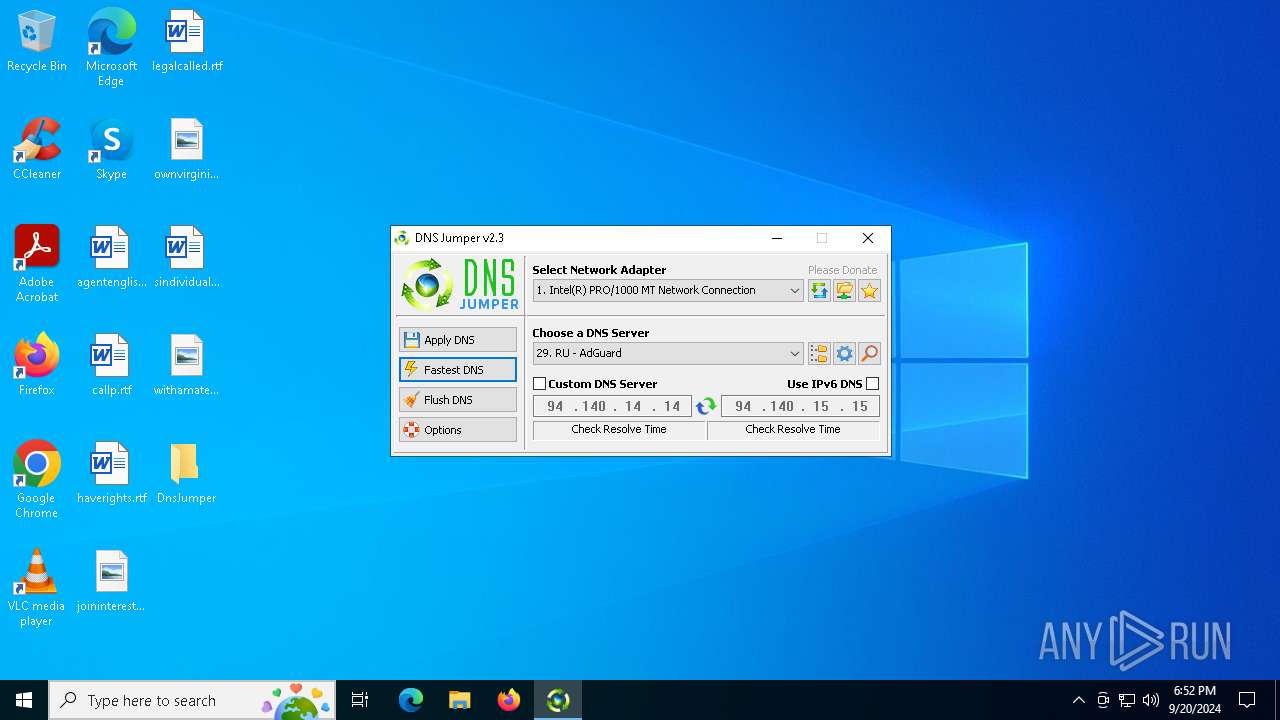
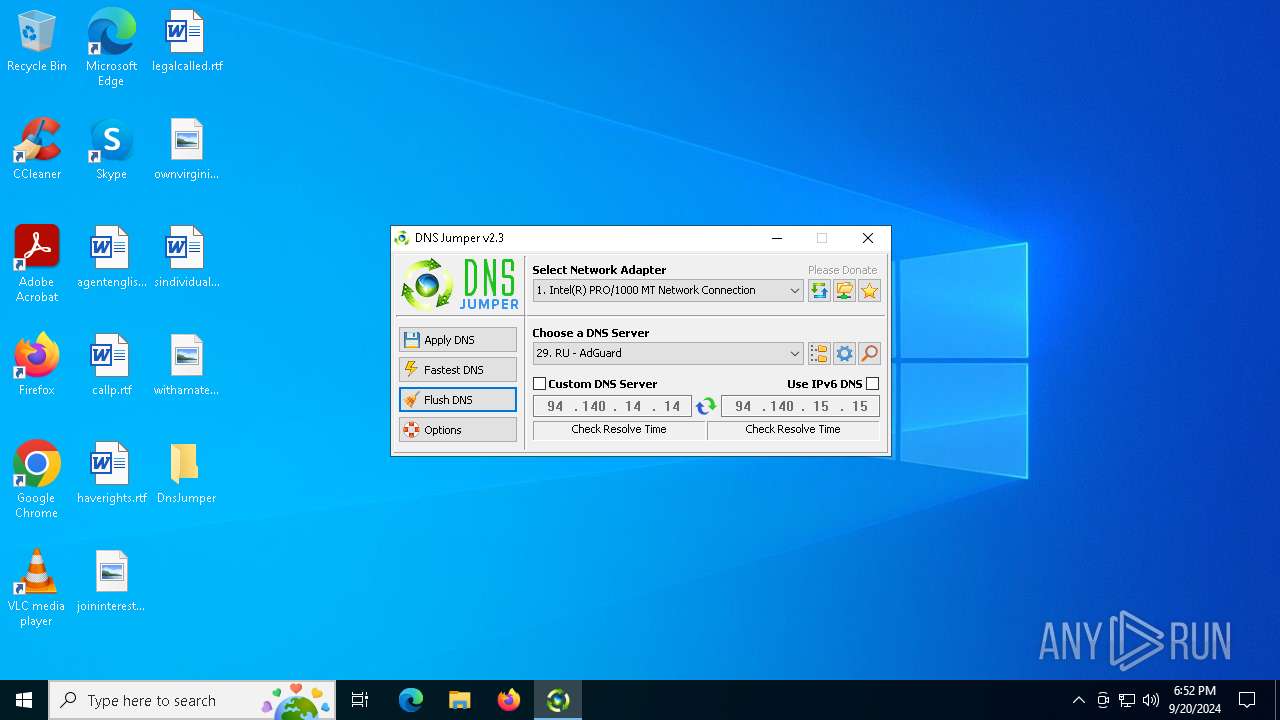
| File name: | DnsJumper.zip |
| Full analysis: | https://app.any.run/tasks/f1be1d12-8d21-4590-a444-66c54f1fbd61 |
| Verdict: | Malicious activity |
| Analysis date: | September 20, 2024, 18:50:18 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 0FF3B69123B826AEA047184CA0626D0A |
| SHA1: | 6B6009723F50E84E1A2BAF20742AB44074B431C7 |
| SHA256: | 737BF53FF5A0BD55FA3761EE8C7EB3FD1DDBFC5424AEAB3B129C4C4F4430B6C6 |
| SSDEEP: | 24576:fm8gPlpKyyt7mknO374E0fViFlEqdHY43Z3FwRR5csENCJ:fm8gPlpKyyt7mknO374E0fVi3rdHY43o |
MALICIOUS
No malicious indicators.SUSPICIOUS
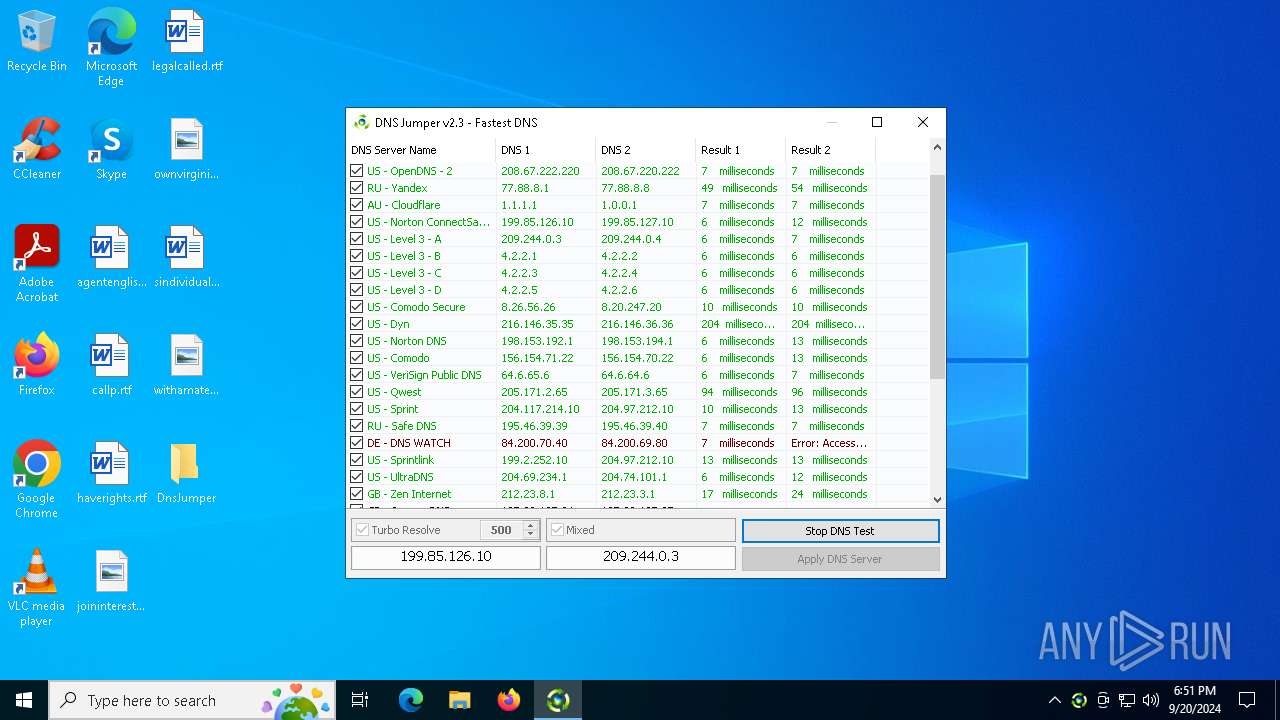
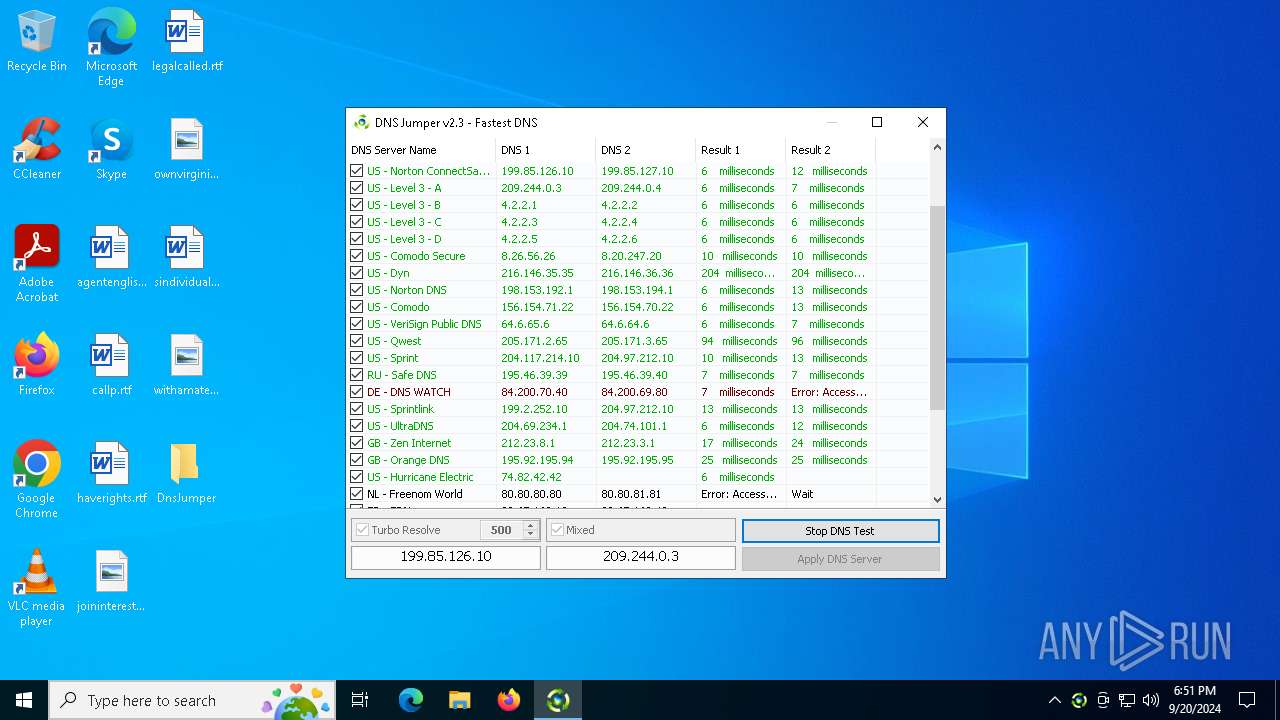
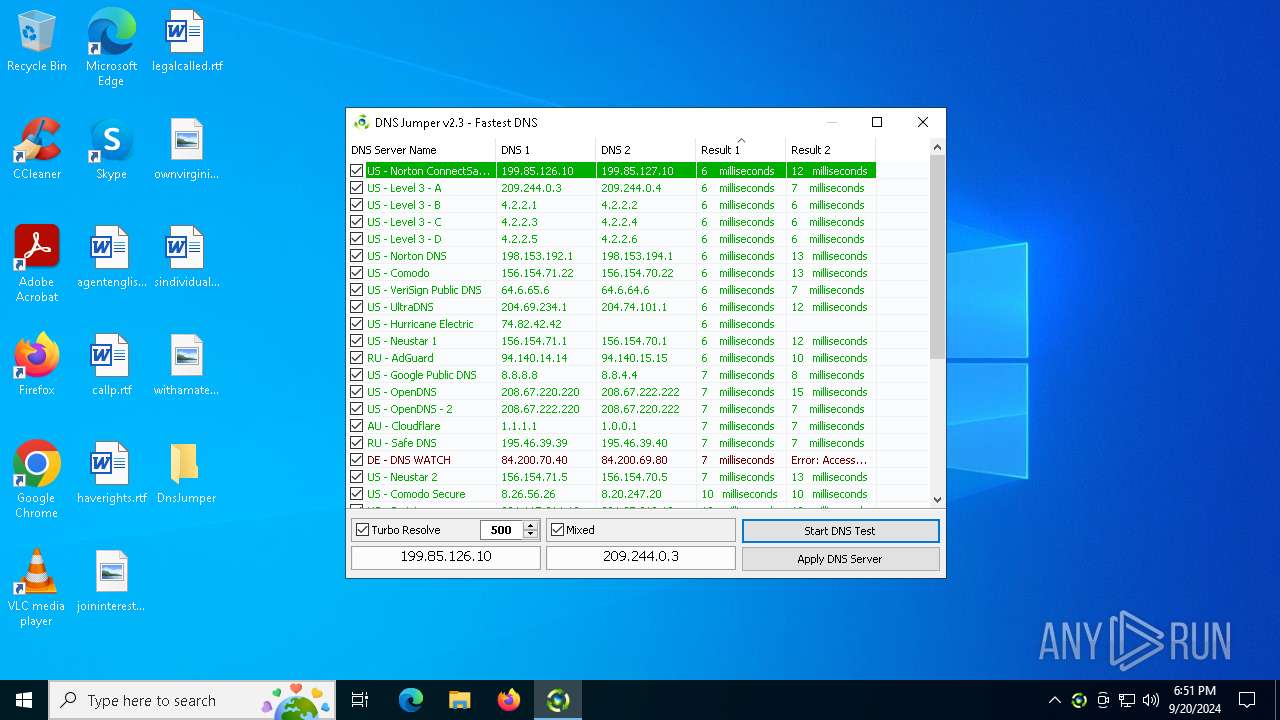
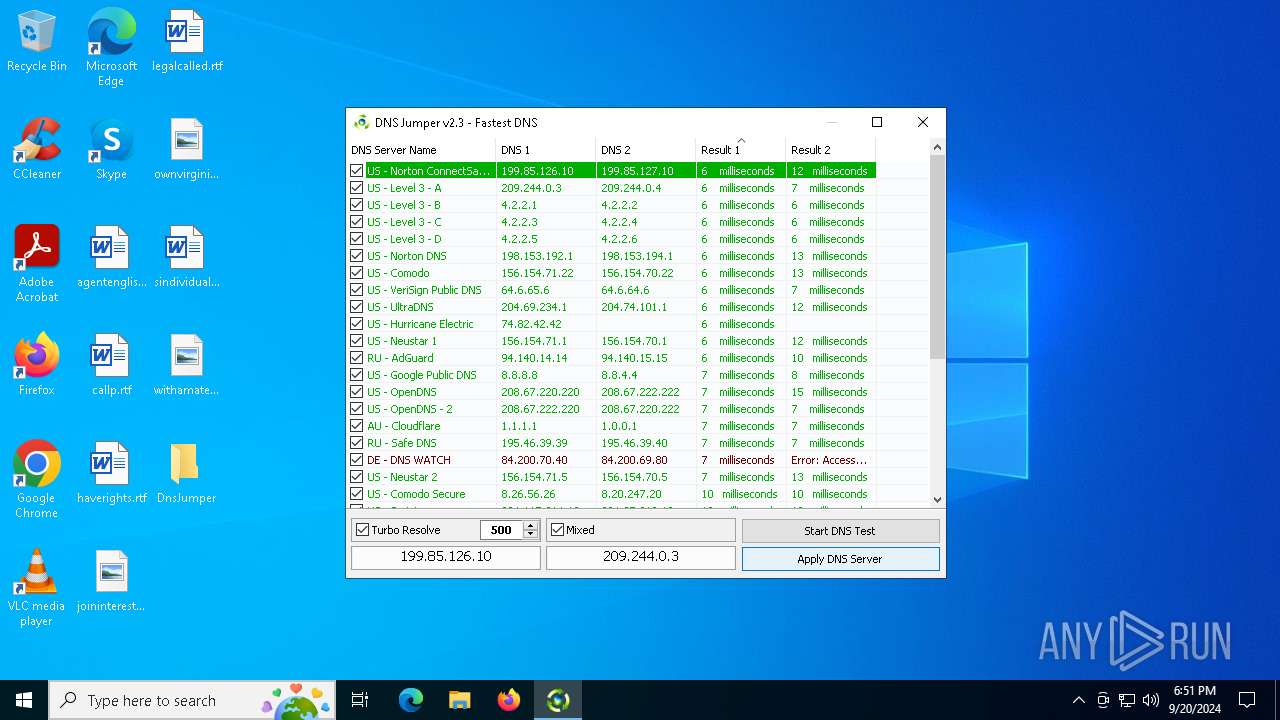
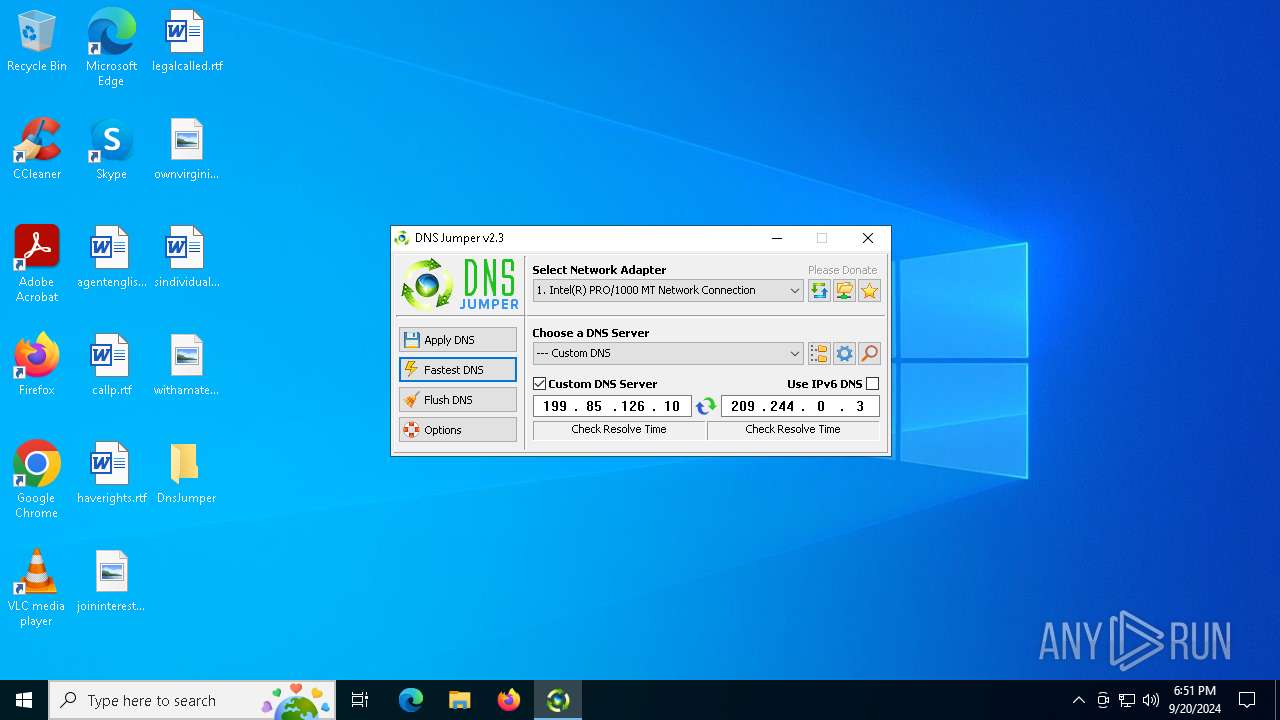
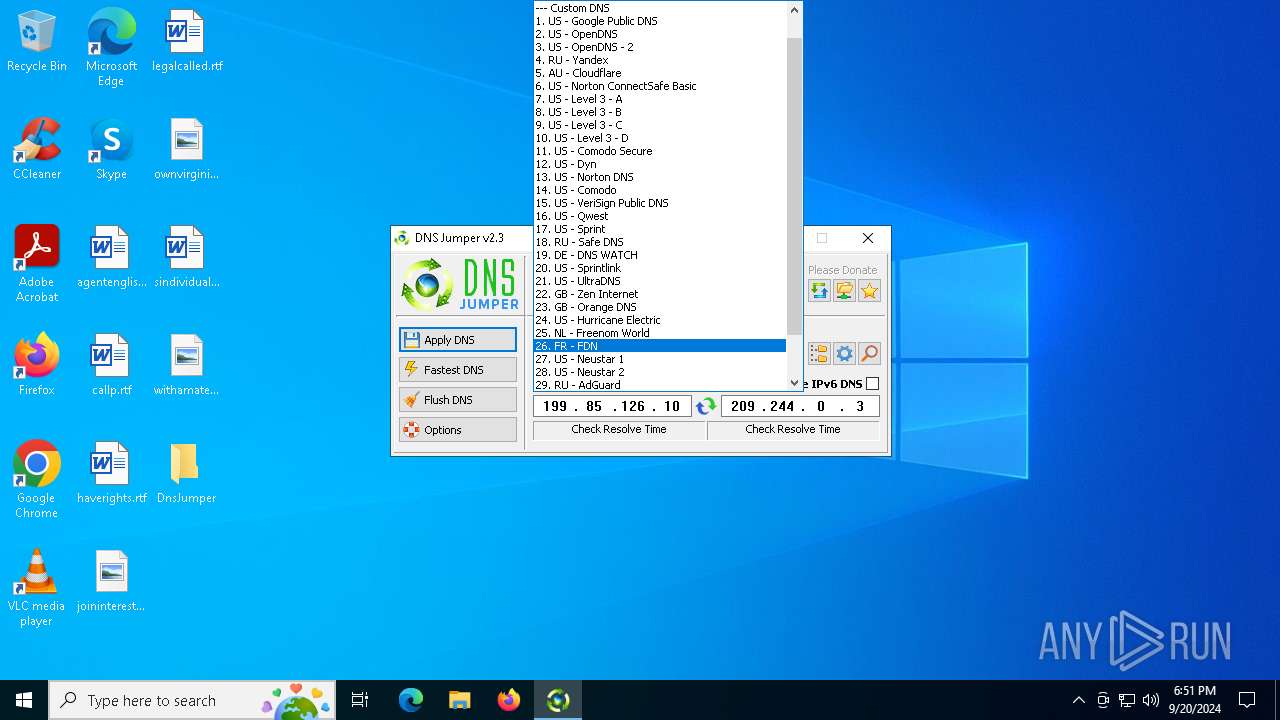
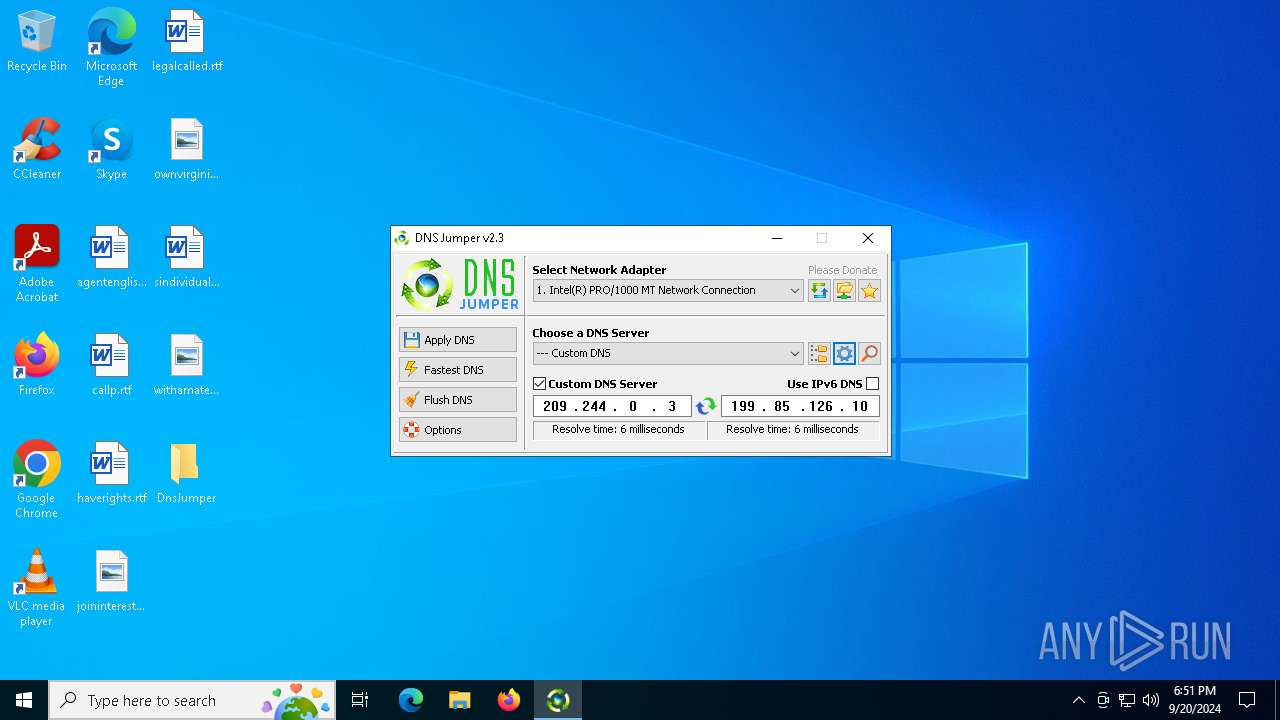
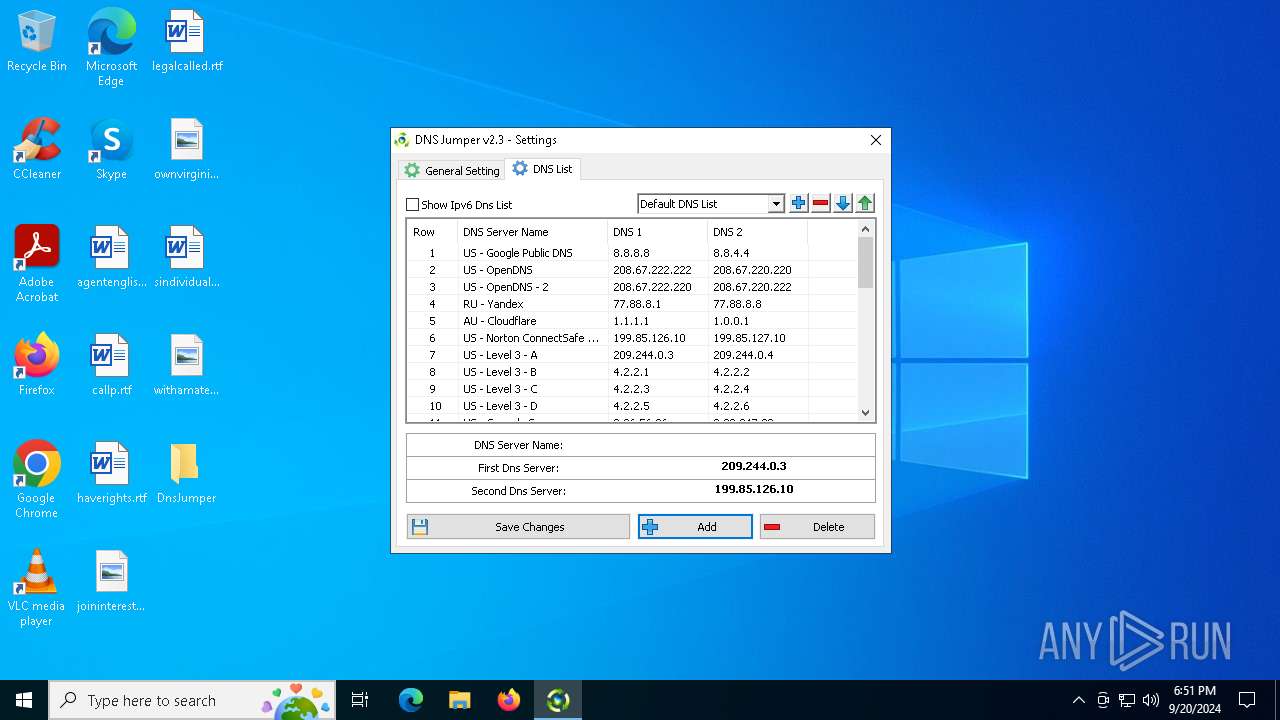
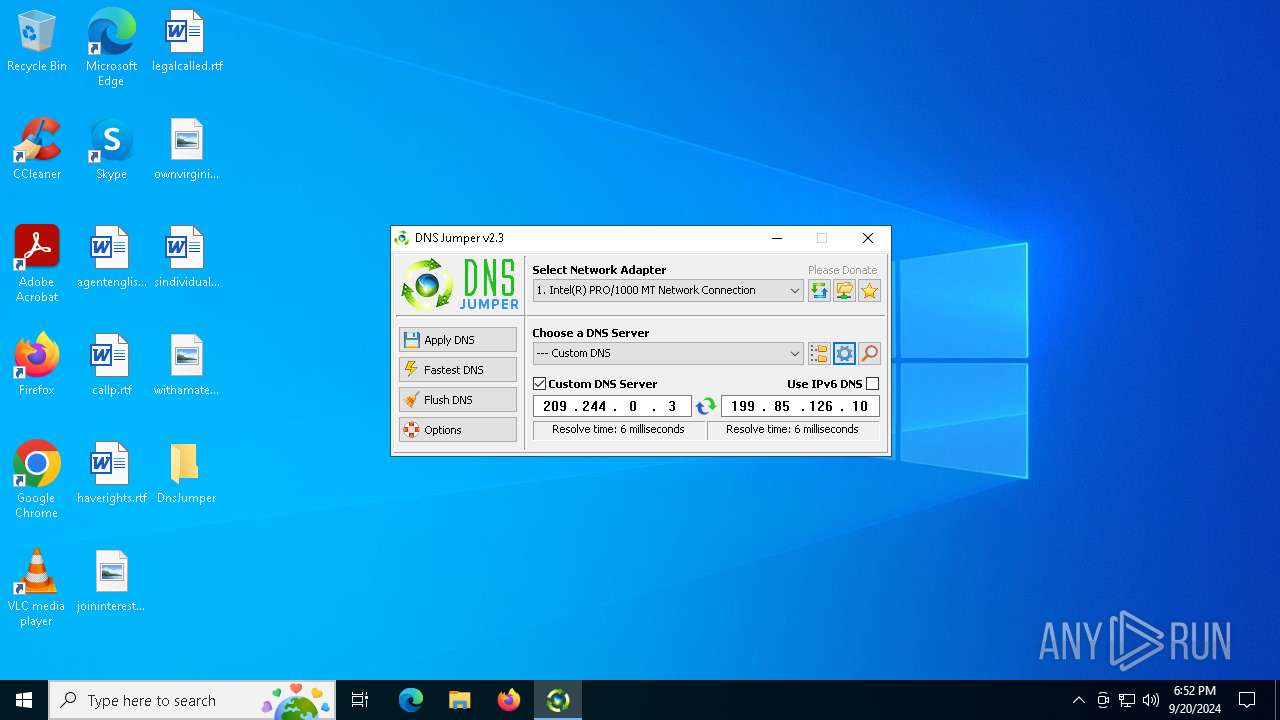
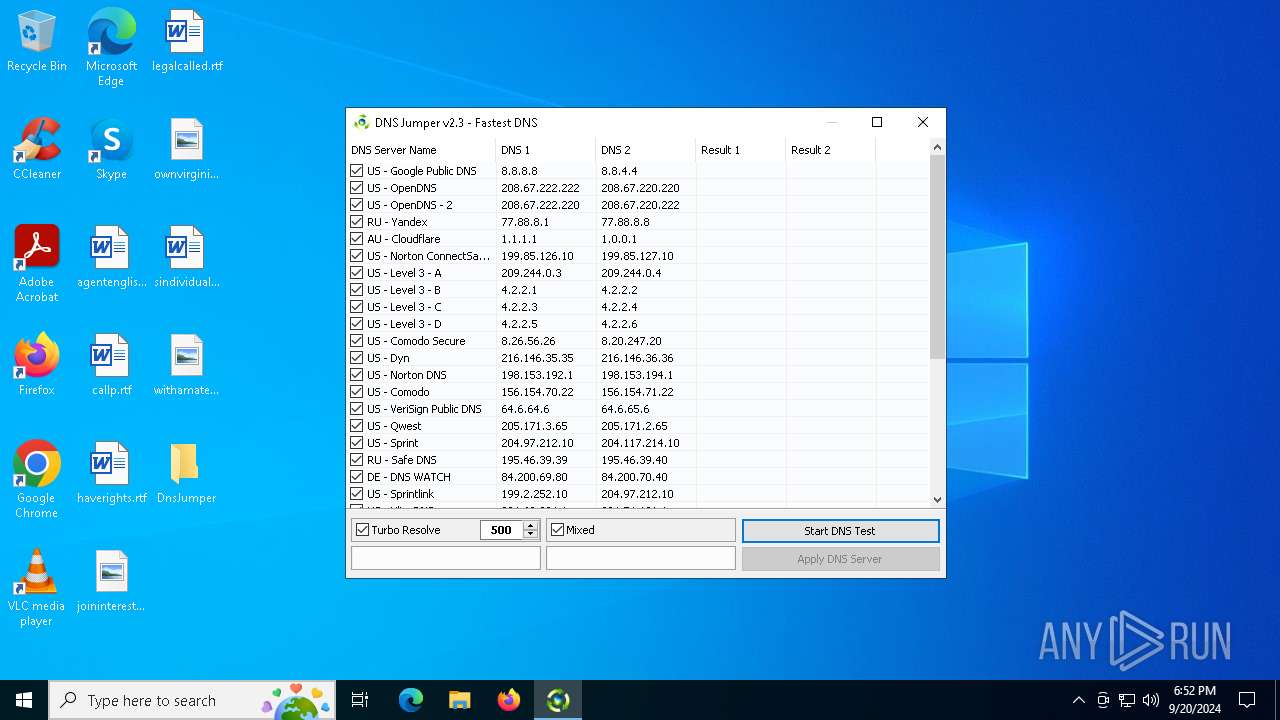
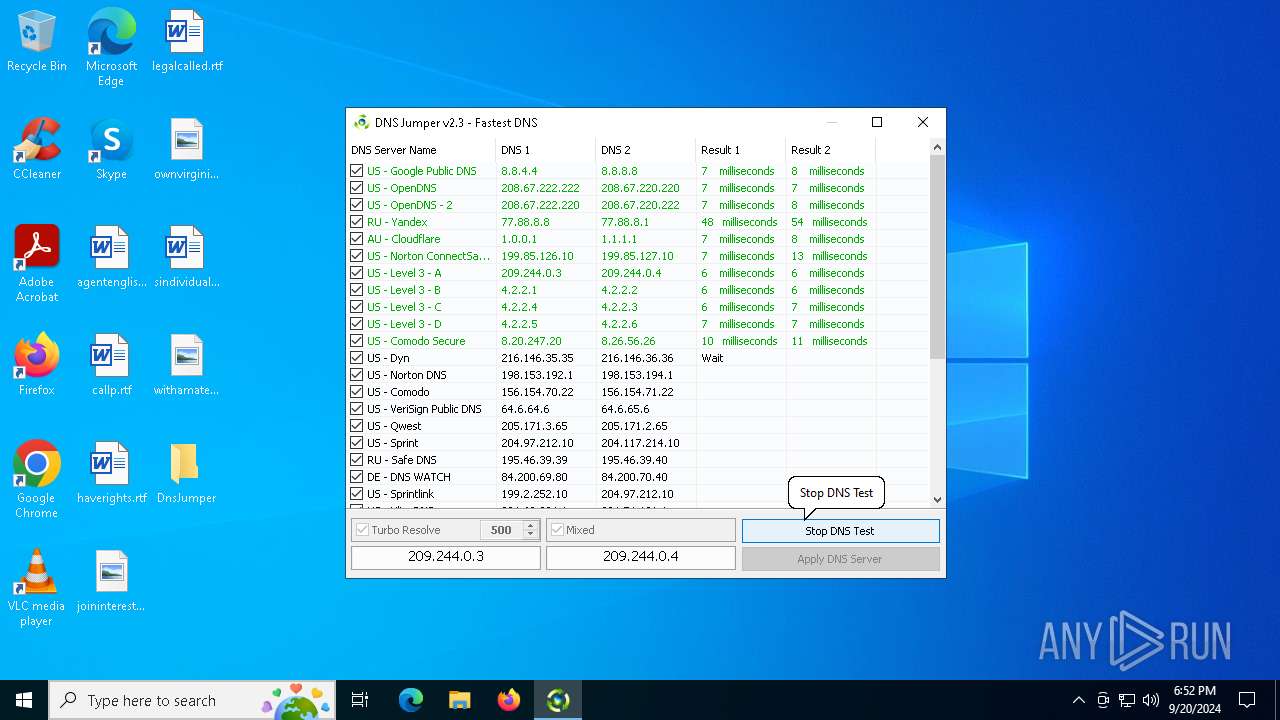
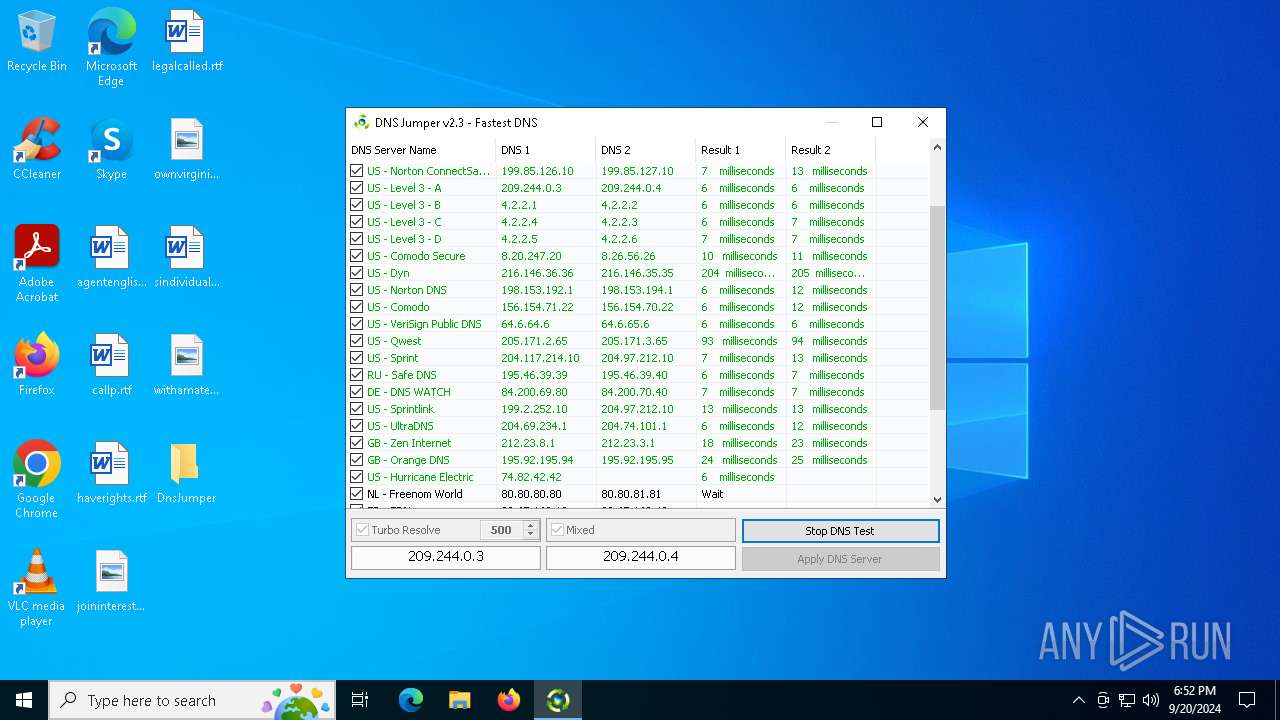
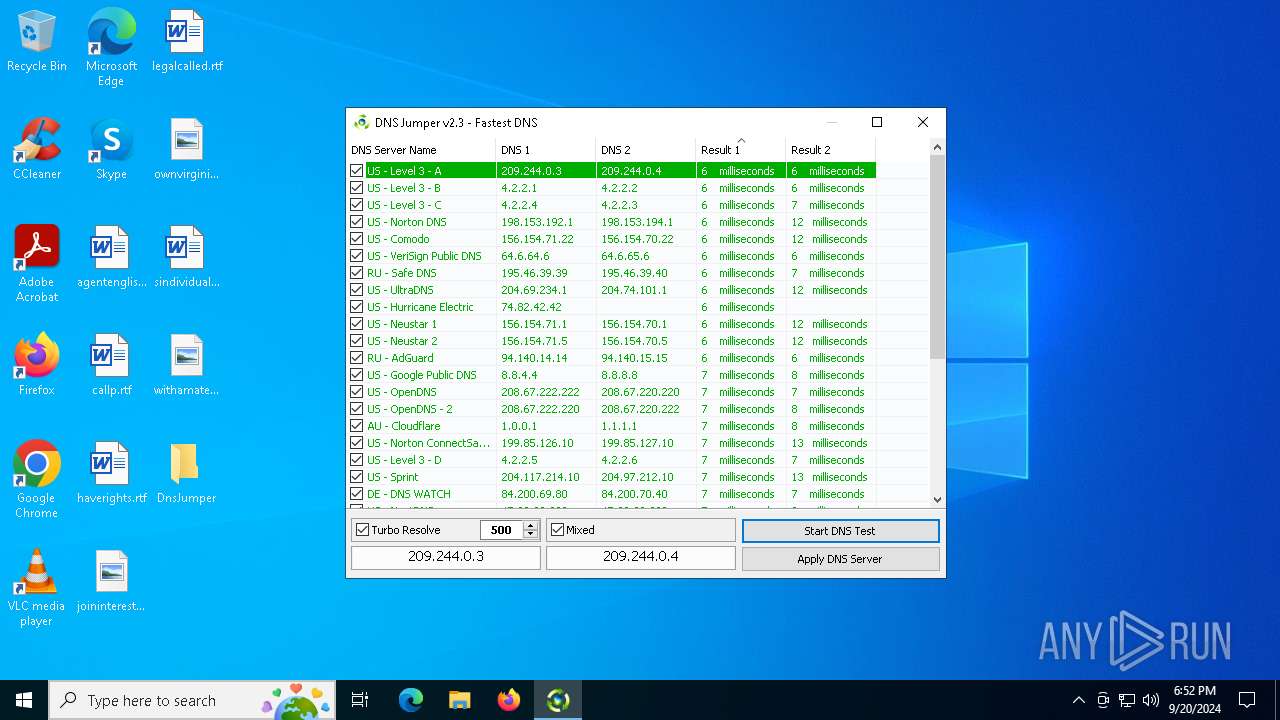
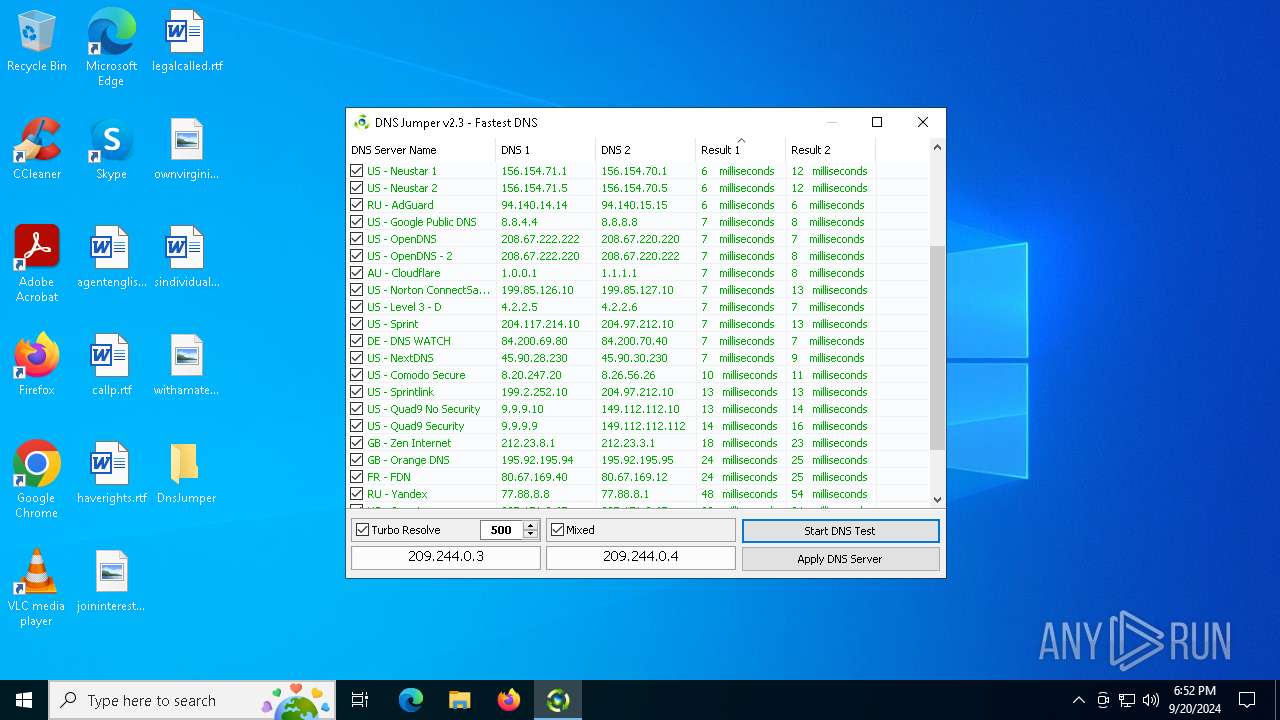
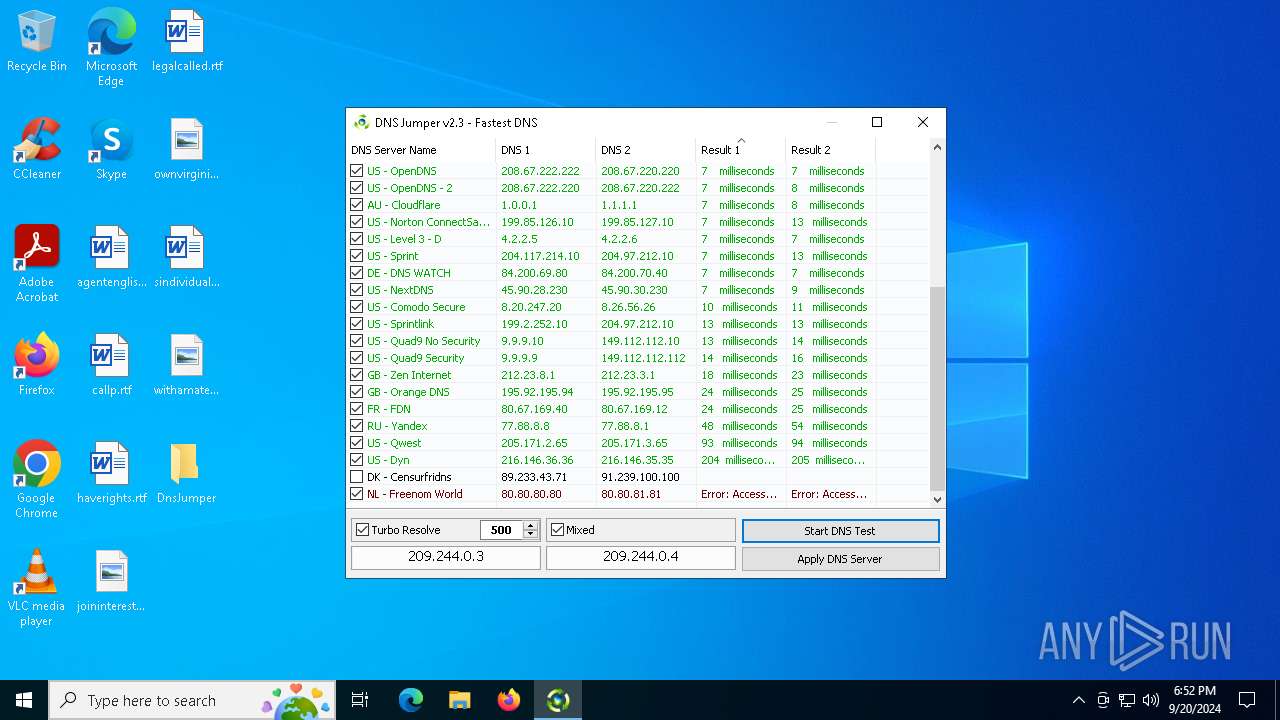
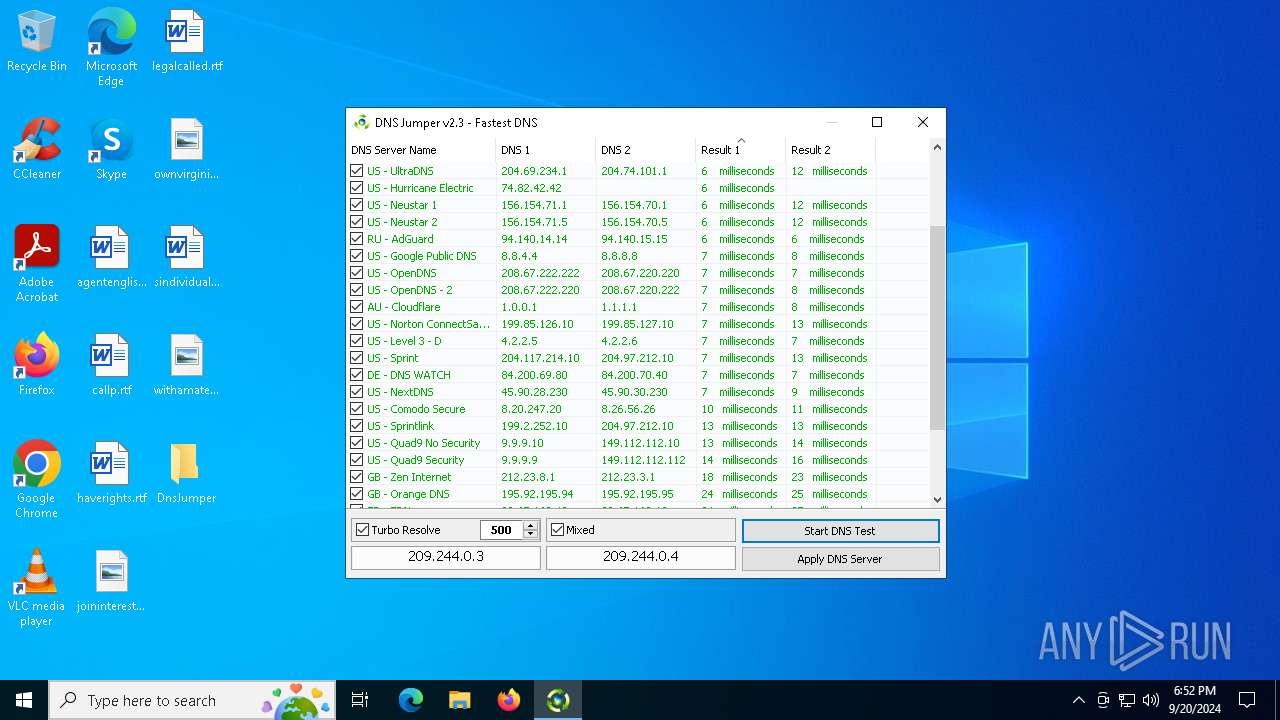
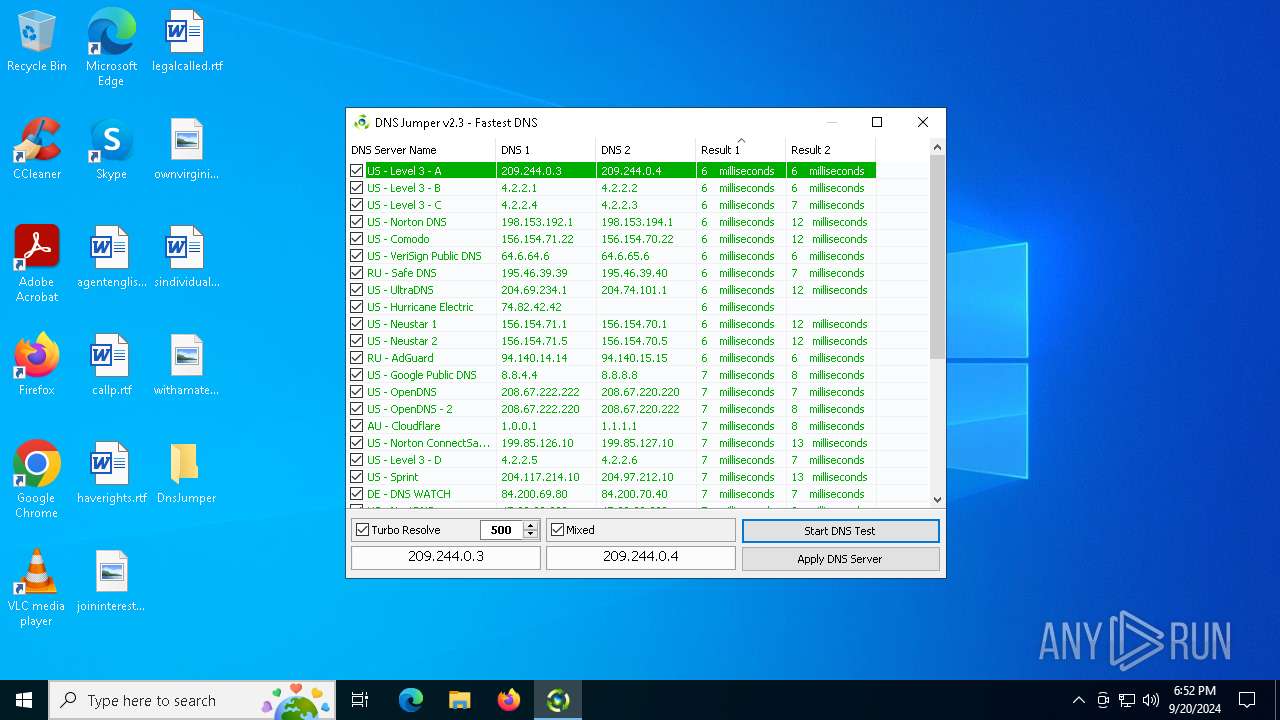
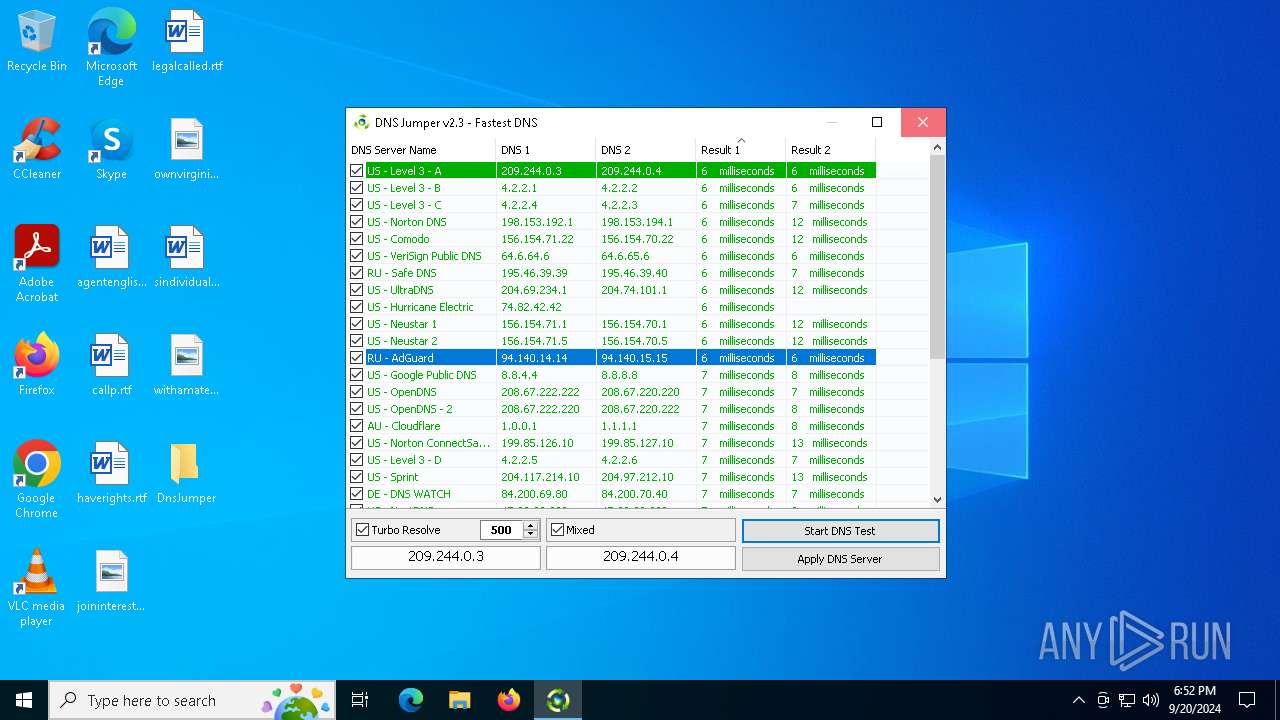
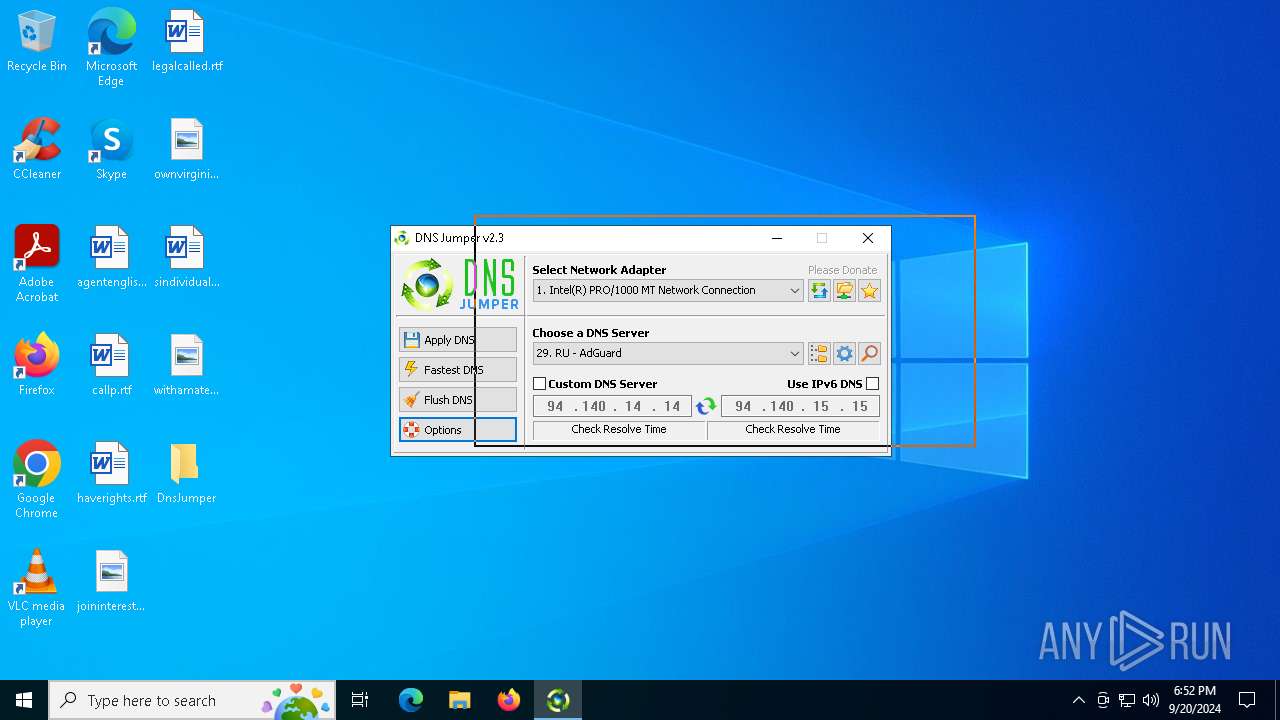
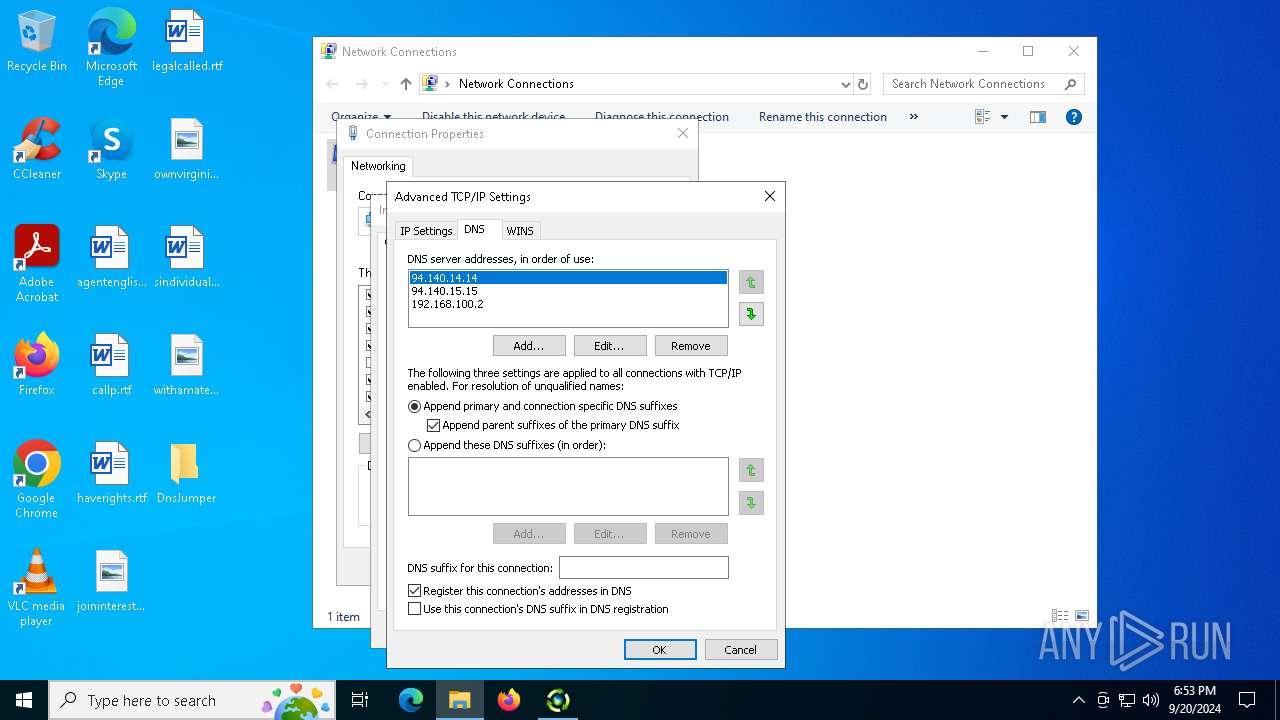
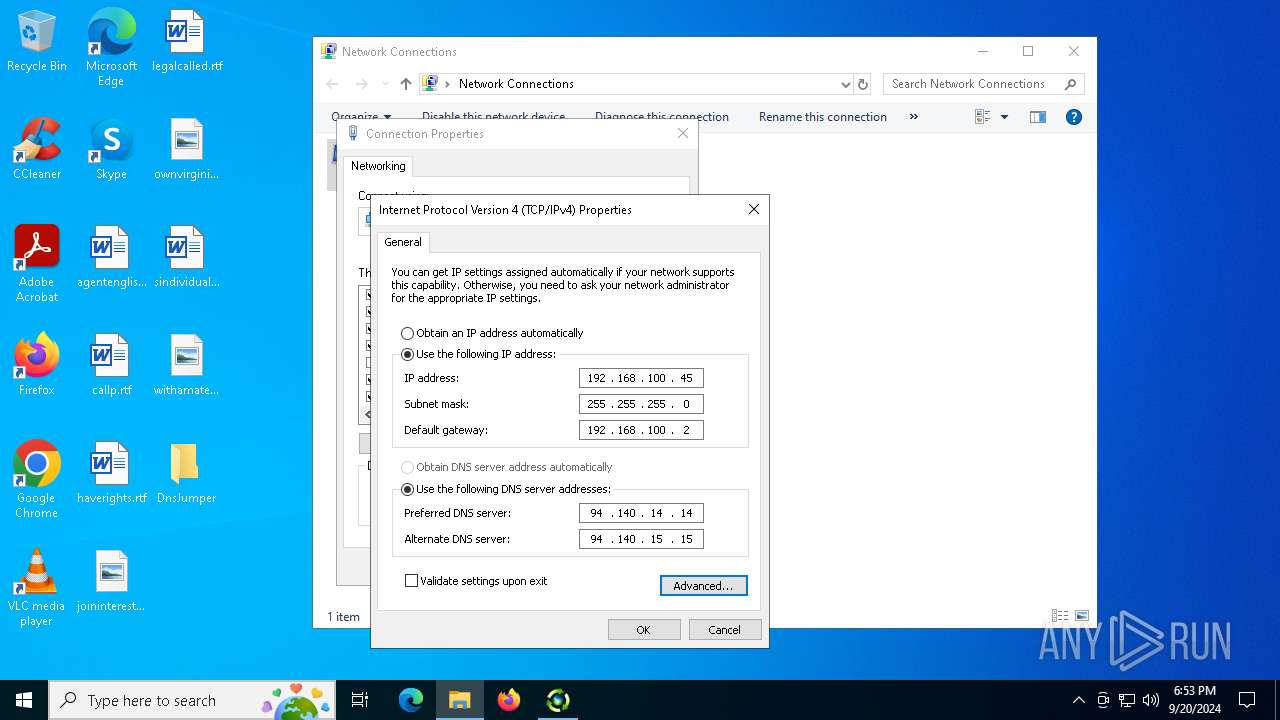
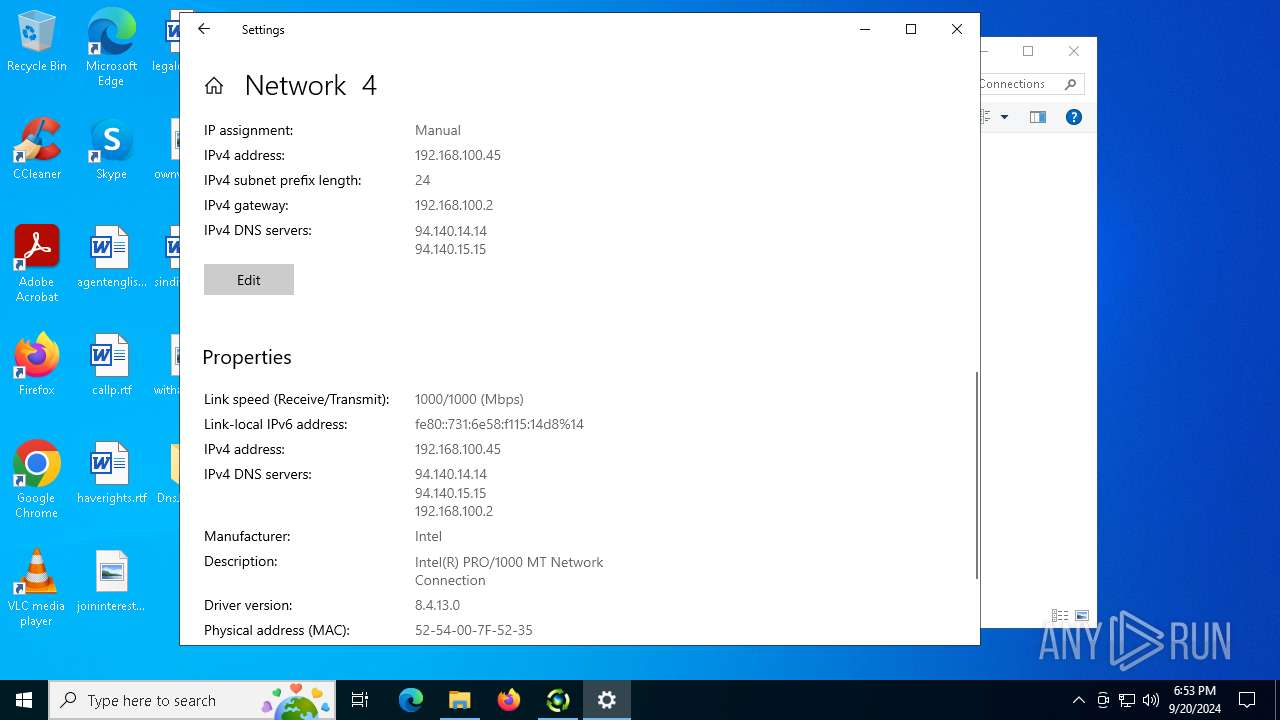
Process uses IPCONFIG to clear DNS cache
- DnsJumper.exe (PID: 1184)
INFO
Manual execution by a user
- DnsJumper.exe (PID: 1048)
- DnsJumper.exe (PID: 1184)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7044)
The process uses the downloaded file
- WinRAR.exe (PID: 7044)
The process uses AutoIt
- DnsJumper.exe (PID: 1184)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2023:12:07 12:30:02 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | DnsJumper/ |
Total processes
155
Monitored processes
17
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1048 | "C:\Users\admin\Desktop\DnsJumper\DnsJumper.exe" | C:\Users\admin\Desktop\DnsJumper\DnsJumper.exe | — | explorer.exe | |||||||||||
User: admin Company: www.sordum.org Integrity Level: MEDIUM Description: DNS Jumper v2.3 Exit code: 3221226540 Version: 2.3.0.0 Modules
| |||||||||||||||
| 1184 | "C:\Users\admin\Desktop\DnsJumper\DnsJumper.exe" | C:\Users\admin\Desktop\DnsJumper\DnsJumper.exe | explorer.exe | ||||||||||||
User: admin Company: www.sordum.org Integrity Level: HIGH Description: DNS Jumper v2.3 Exit code: 0 Version: 2.3.0.0 Modules
| |||||||||||||||
| 1332 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ipconfig.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2560 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2944 | ipconfig.exe /flushdns | C:\Windows\SysWOW64\ipconfig.exe | — | DnsJumper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: IP Configuration Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4292 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ipconfig.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5048 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5592 | ipconfig.exe /flushdns | C:\Windows\SysWOW64\ipconfig.exe | — | DnsJumper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: IP Configuration Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6032 | ipconfig.exe /flushdns | C:\Windows\SysWOW64\ipconfig.exe | — | DnsJumper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: IP Configuration Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6248 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 288
Read events
6 235
Write events
51
Delete events
2
Modification events
| (PID) Process: | (7044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (7044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\DnsJumper.zip | |||
| (PID) Process: | (7044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (7044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFE800000044000000A80400002D020000 | |||
| (PID) Process: | (7044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (7044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
1
Suspicious files
3
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1184 | DnsJumper.exe | C:\Users\admin\AppData\Local\Temp\aut47DA.tmp | binary | |
MD5:5228DE209CDFC22D50411FBDEE0C1CC9 | SHA256:1F520421CBA47A957651274DEDC499360A27FE6C520B15F64B2E4E7846CF641C | |||
| 7044 | WinRAR.exe | C:\Users\admin\Desktop\DnsJumper\DnsJumper.exe | executable | |
MD5:142C1CB2E06B3F3E231F99B7CC4A91B2 | SHA256:6FE6BAC71A82A58ABCB06B0DF4A836116543302EFE6E076402FA518DFA455BAA | |||
| 1184 | DnsJumper.exe | C:\Users\admin\AppData\Local\Temp\aut47DB.tmp | binary | |
MD5:9AE7BC01CB20282790CB1D63B50E1382 | SHA256:CCC9034CEA45EB38DFC03C9A13026B449E0B0BFCD7A4BFBF5E55411CFBE7305C | |||
| 1184 | DnsJumper.exe | C:\Users\admin\AppData\Local\Temp\aut47DC.tmp | binary | |
MD5:FC4070E186CED8398F66C7F91A247194 | SHA256:63977C7A86AE84077B33BAB1644D43153F2705CDFB0EBC977A9525E128A04174 | |||
| 7044 | WinRAR.exe | C:\Users\admin\Desktop\DnsJumper\DnsJumper.ini | text | |
MD5:36FBA1B2C214A233FFD4B2B6B2CEC1E8 | SHA256:C506229B94BADB6795C51F8137C49A5F71100223987C5903F094434782442972 | |||
| 1184 | DnsJumper.exe | C:\Users\admin\AppData\Local\Temp\1w1w8n4e.tmp | text | |
MD5:AF689E2D924E12BD7337B32FBE10BCD3 | SHA256:083DF3C84F3B07FA2B49BB09AD52A6E23BD3C93CDFD98FC4963748BB3CD09FD5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
37
DNS requests
152
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4040 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6048 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4784 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4784 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1028 | SystemSettings.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1028 | SystemSettings.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4032 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4040 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4040 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4040 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6048 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
www.google.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |