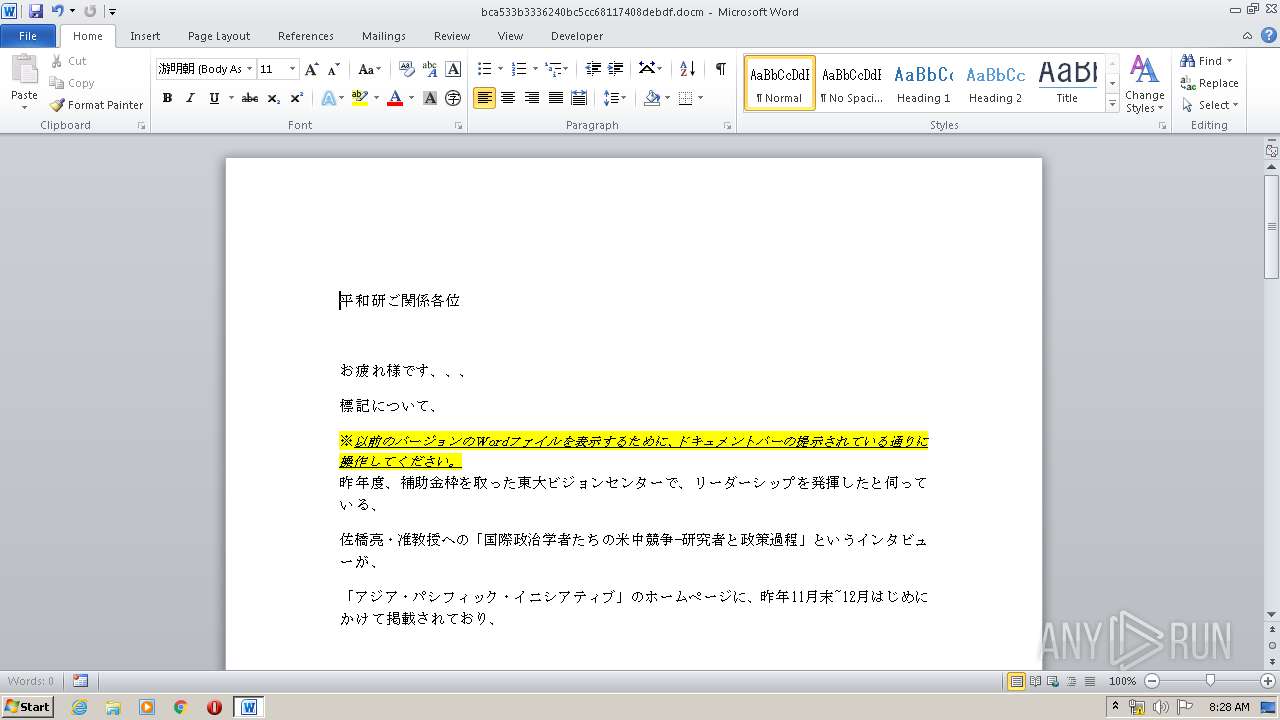
| File name: | bca533b3336240bc5cc68117408debdf |
| Full analysis: | https://app.any.run/tasks/aa54600c-e6fb-449c-b30e-d224e59b402a |
| Verdict: | Malicious activity |
| Analysis date: | May 27, 2020, 07:27:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | BCA533B3336240BC5CC68117408DEBDF |
| SHA1: | 608295F7C71F08327D720BD569BA0D2A2EBC08CD |
| SHA256: | 73470EA496126133FD025CFA9B3599BEA9550ABE2C8D065DE11AFB6F7AA6B5DF |
| SSDEEP: | 12288:8ivJsw94U3FOKRbjirZMzgmZ6+GvlccUzlMrXUYOmPUNQL3n:8nwyU3FJb4q69vl3xkYVPPn |
MALICIOUS
Loads dropped or rewritten executable
- SfsDllSample.exe (PID: 1452)
Application was dropped or rewritten from another process
- SfsDllSample.exe (PID: 1452)
Changes the autorun value in the registry
- SfsDllSample.exe (PID: 1452)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 1764)
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 1764)
SUSPICIOUS
Reads Internet Cache Settings
- SfsDllSample.exe (PID: 1452)
Connects to server without host name
- SfsDllSample.exe (PID: 1452)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1764)
Creates files in the user directory
- WINWORD.EXE (PID: 1764)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x7aec387e |
| ZipCompressedSize: | 391 |
| ZipUncompressedSize: | 1453 |
| ZipFileName: | [Content_Types].xml |
XML
| Template: | Normal.dotm |
|---|---|
| TotalEditTime: | 5 minutes |
| Pages: | 5 |
| Words: | 701 |
| Characters: | 3997 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 33 |
| Paragraphs: | 9 |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 4689 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 15 |
| Keywords: | - |
| LastModifiedBy: | user |
| RevisionNumber: | 7 |
| CreateDate: | 2020:05:25 03:25:00Z |
| ModifyDate: | 2020:05:26 07:20:00Z |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | D3vle0 |
| Description: | - |
Total processes
37
Monitored processes
2
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1452 | "C:\Users\admin\AppData\Local\Temp\TRJ\SfsDllSample.exe" | C:\Users\admin\AppData\Local\Temp\TRJ\SfsDllSample.exe | WINWORD.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1764 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\bca533b3336240bc5cc68117408debdf.docm" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
1 744
Read events
975
Write events
627
Delete events
142
Modification events
| (PID) Process: | (1764) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 3w7 |
Value: 33773700E4060000010000000000000000000000 | |||
| (PID) Process: | (1764) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1764) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1764) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1764) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1764) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1764) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1764) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1764) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1764) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
2
Suspicious files
2
Text files
1
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1764 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR1B93.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1764 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~WRD0000.tmp | — | |
MD5:— | SHA256:— | |||
| 1764 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~WRL0001.tmp | document | |
MD5:— | SHA256:— | |||
| 1764 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$a533b3336240bc5cc68117408debdf.docm | pgc | |
MD5:— | SHA256:— | |||
| 1764 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1764 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 1764 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\bca533b3336240bc5cc68117408debdf.docm | document | |
MD5:— | SHA256:— | |||
| 1764 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\KHKERL | text | |
MD5:— | SHA256:— | |||
| 1764 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\TRJ\SfsDll32.dll | executable | |
MD5:— | SHA256:— | |||
| 1764 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\TRJ\SfsDllSample.exe | executable | |
MD5:45FBD8574D9EEABDBDE01524B87560AA | SHA256:4F83DA50B194E370EAEE89AEA9866C8F8B39745E7718E6E72FDA85B8252C85F8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
0
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1452 | SfsDllSample.exe | POST | 200 | 103.27.184.27:80 | http://103.27.184.27/ | JP | text | 144 b | malicious |
1452 | SfsDllSample.exe | POST | — | 103.27.184.27:80 | http://103.27.184.27/ | JP | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1452 | SfsDllSample.exe | 103.27.184.27:80 | — | Starry Network Limited | JP | malicious |
— | — | 103.27.184.27:80 | — | Starry Network Limited | JP | malicious |