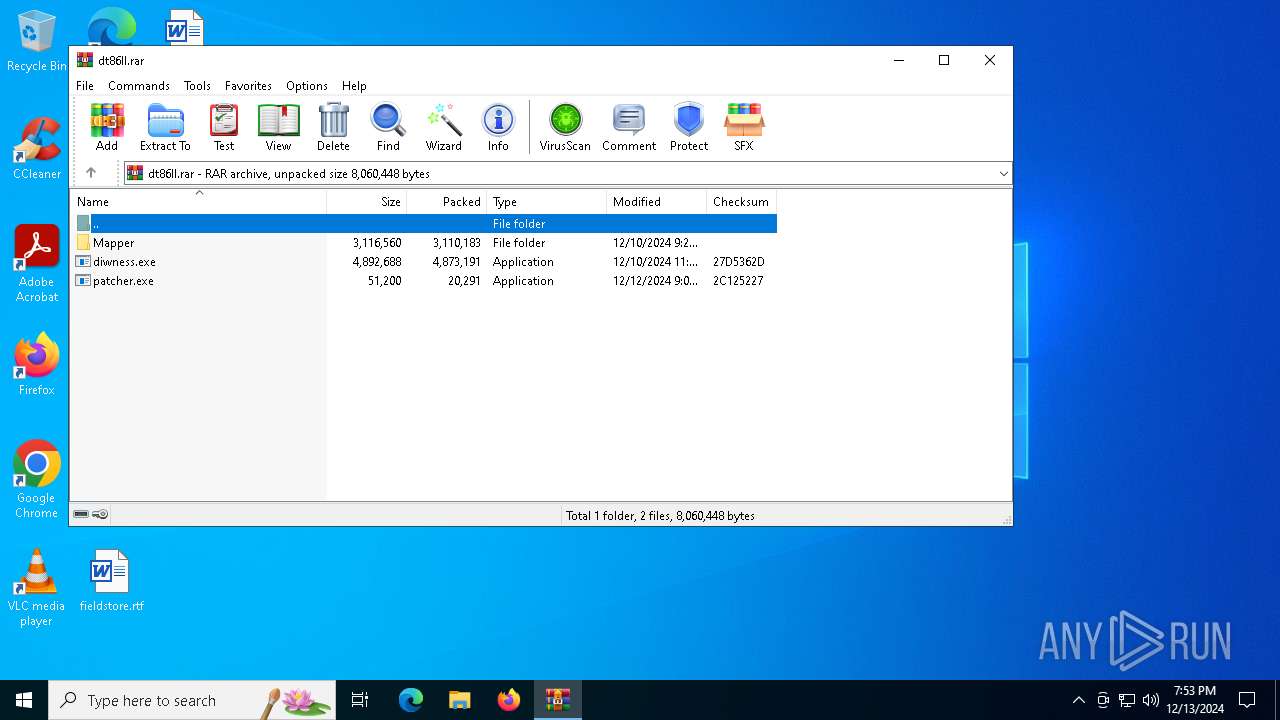
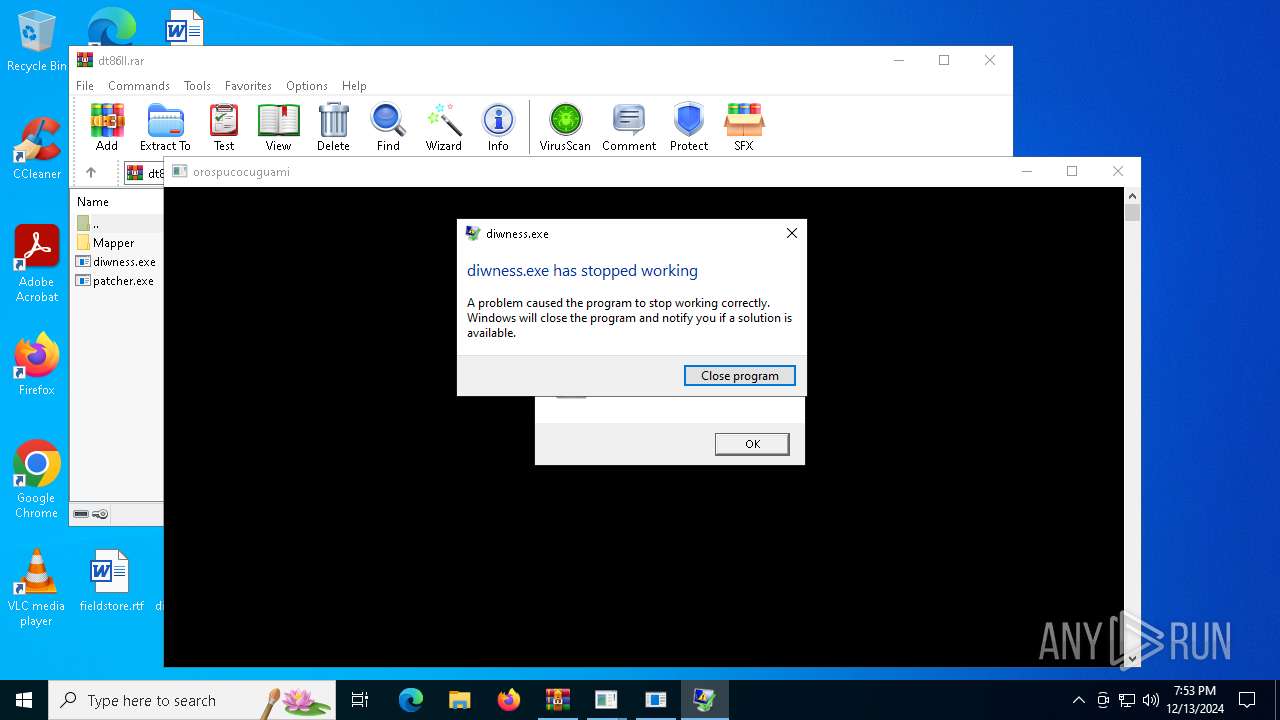
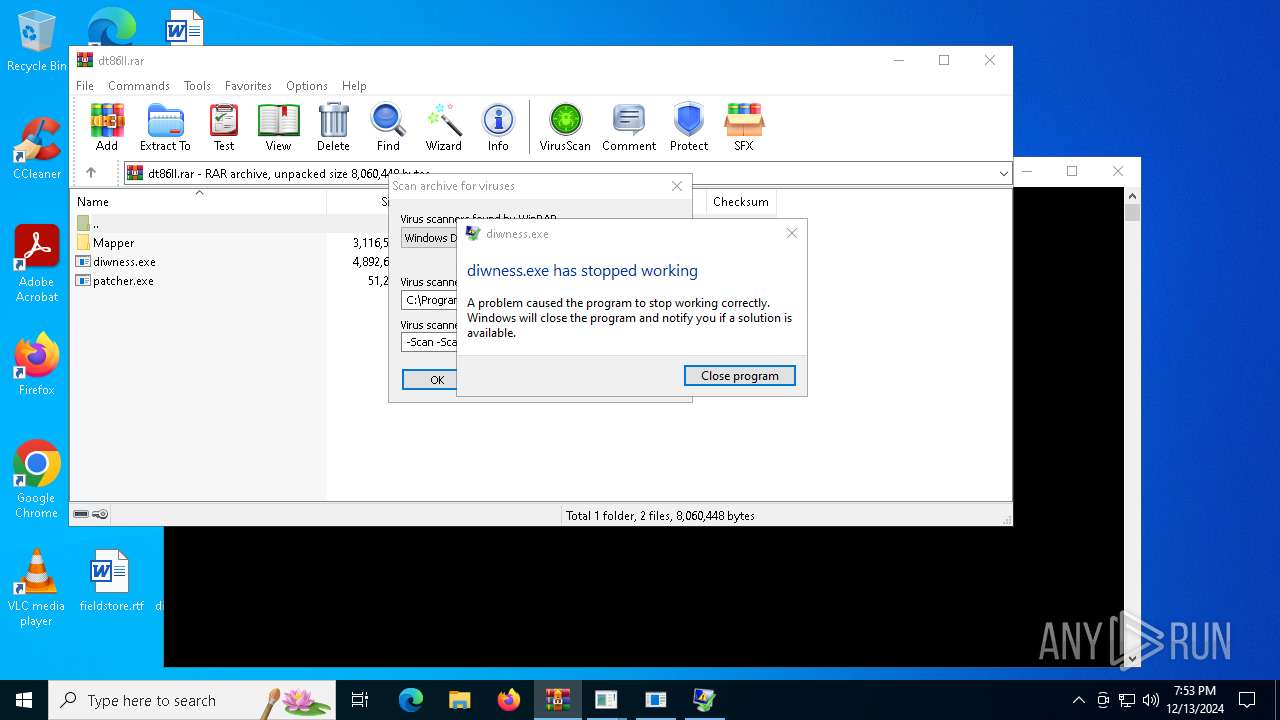
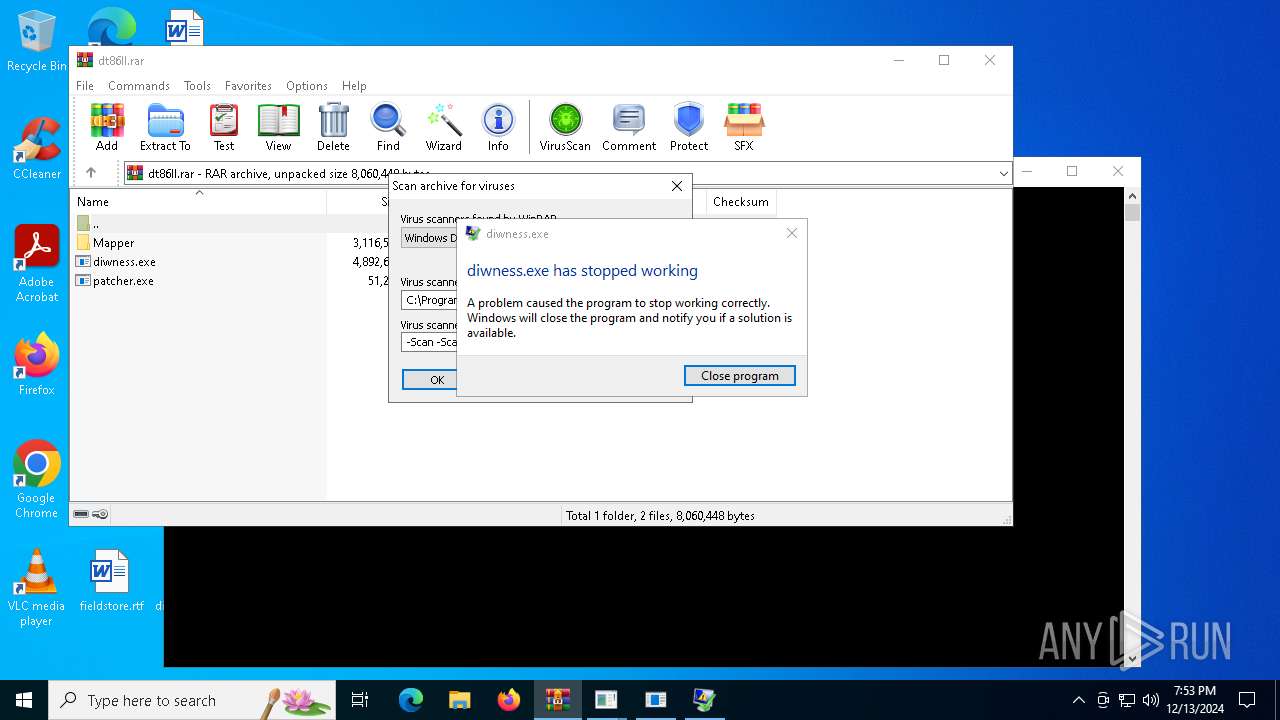
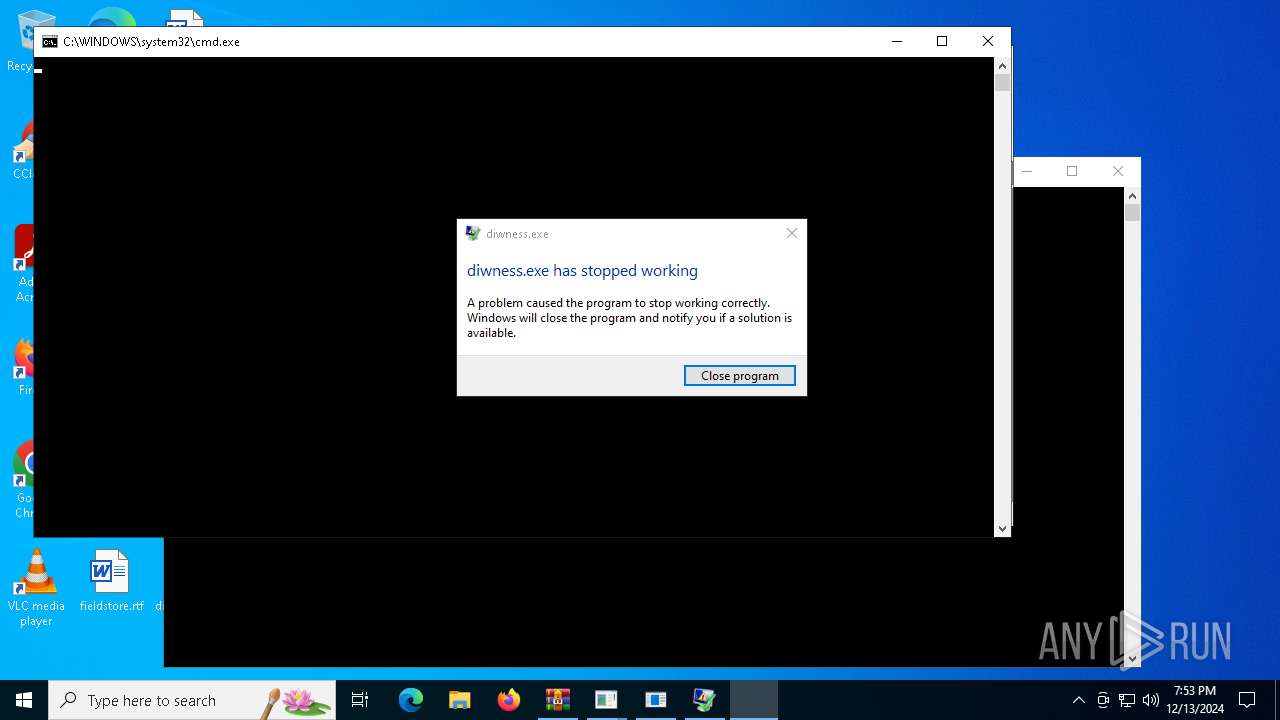
| File name: | dt86ll.rar |
| Full analysis: | https://app.any.run/tasks/4d4b4011-8a03-4fe2-969b-3d3a51f705b0 |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2024, 19:53:12 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | A386131EEBE7C6443EDE7A0793C327AD |
| SHA1: | AE5385F669C5269FEFF39AA51E236A6B5282504B |
| SHA256: | 733DF7E11040C3F2AB80585E72E9E3A5264C382447ABF88B904DB22376CB8AE2 |
| SSDEEP: | 98304:2DRfMaE2TLfeE3oOVBj6ri/jZHCDXuDNeBFoxP51AwyJ7wsBu0RHwWicTMpfqXxz:Ye1bO3qLj24T |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5964)
Antivirus name has been found in the command line (generic signature)
- MpCmdRun.exe (PID: 3080)
SUSPICIOUS
Reads the BIOS version
- diwness.exe (PID: 4548)
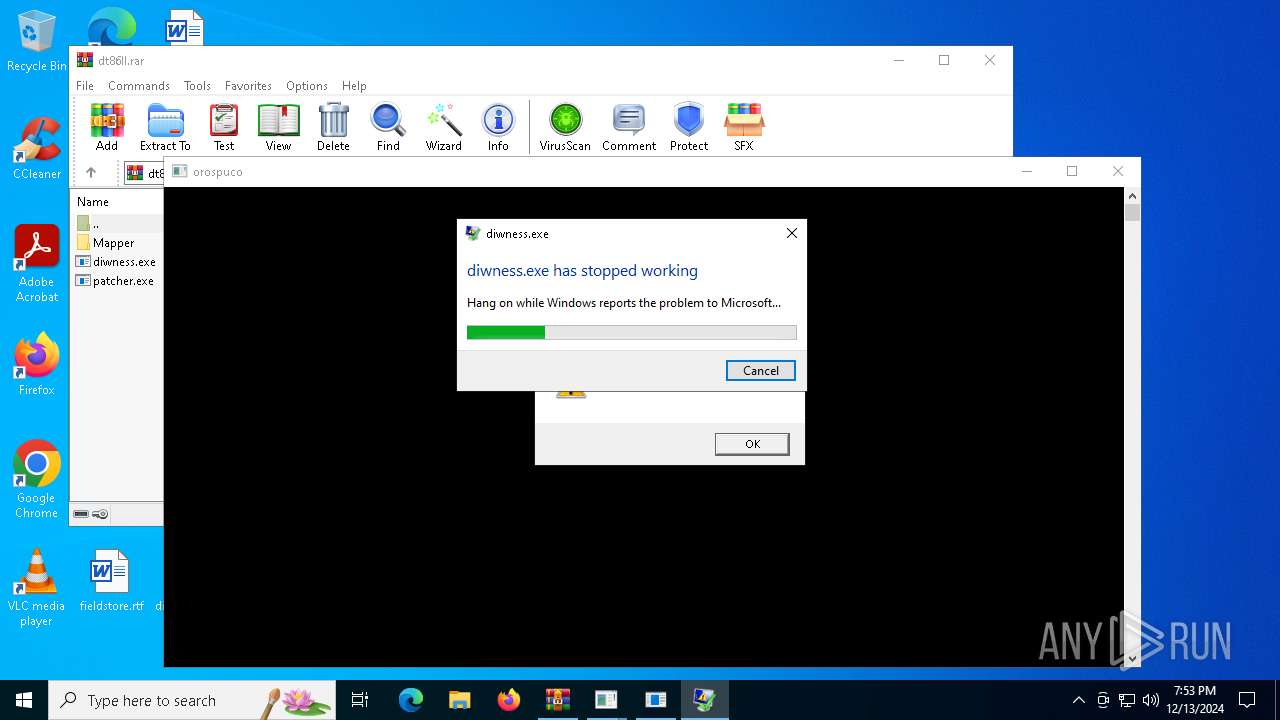
Executes application which crashes
- diwness.exe (PID: 4548)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5964)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 5964)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 5964)
INFO
Manual execution by a user
- patcher.exe (PID: 3128)
- patcher.exe (PID: 3540)
- diwness.exe (PID: 4548)
Reads the computer name
- patcher.exe (PID: 3128)
- diwness.exe (PID: 4548)
- MpCmdRun.exe (PID: 3080)
Checks supported languages
- patcher.exe (PID: 3128)
- diwness.exe (PID: 4548)
- MpCmdRun.exe (PID: 3080)
Checks proxy server information
- WerFault.exe (PID: 2800)
Create files in a temporary directory
- MpCmdRun.exe (PID: 3080)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5964)
Reads the software policy settings
- WerFault.exe (PID: 2800)
The process uses the downloaded file
- WinRAR.exe (PID: 5964)
Themida protector has been detected
- diwness.exe (PID: 4548)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 4873191 |
| UncompressedSize: | 4892688 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | diwness.exe |
Total processes
128
Monitored processes
9
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2800 | C:\WINDOWS\system32\WerFault.exe -u -p 4548 -s 532 | C:\Windows\System32\WerFault.exe | diwness.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3080 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR5964.43089" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3128 | "C:\Users\admin\Desktop\patcher.exe" | C:\Users\admin\Desktop\patcher.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 3488 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3540 | "C:\Users\admin\Desktop\patcher.exe" | C:\Users\admin\Desktop\patcher.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3988 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | patcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4548 | "C:\Users\admin\Desktop\diwness.exe" | C:\Users\admin\Desktop\diwness.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5200 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR5964.43089\Rar$Scan19388.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5964 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\dt86ll.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
8 205
Read events
8 196
Write events
9
Delete events
0
Modification events
| (PID) Process: | (5964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\dt86ll.rar | |||
| (PID) Process: | (5964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
3
Suspicious files
1
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2800 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_diwness.exe_2cbb9aeebdc31ccb28ce020e1c0566acbdc4c6d_3cf9e409_d202d098-4404-4e43-b114-bd485bca0527\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5964 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5964.43089\dt86ll.rar\diwness.exe | executable | |
MD5:547F205B2EE089AA5394B0769B7317F8 | SHA256:A8C307C53A259A42001753902A4B3BF69CF9150A6596675F14BD7043D7FF816F | |||
| 2800 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER76EB.tmp.xml | xml | |
MD5:F690585D2673F8D6DEE788EA26528562 | SHA256:8B92F491423A2102E7E98806D0EC365562AE142E06425690E2A0AB8308AFC51E | |||
| 2800 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER769B.tmp.WERInternalMetadata.xml | xml | |
MD5:881FEB7AC95DEC3F2CB34AAA2DF63EB5 | SHA256:3BB94FFF752DADD8BDC7B65E895F5C0025058D875887758AEA5BF4FAB357E6A2 | |||
| 5964 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5964.43089\Rar$Scan19388.bat | text | |
MD5:79FFB28509D443AE890EFAF763EC5DE4 | SHA256:7B7D22E6F5CB9C58602A11DEB5BECA235A381C0DFEA2732A22A726286996B406 | |||
| 2800 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER75C0.tmp.dmp | binary | |
MD5:A8188DE3C39779BB7812CA06A27CEB34 | SHA256:3997C189DB2874E268421E58C75422505BC9D99E577D9FA09D11496D3BCE8451 | |||
| 5964 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5964.43089\dt86ll.rar\patcher.exe | executable | |
MD5:CD3DD900476B6AD34586EA6FE8A43A5D | SHA256:3E11CEB0F44F218773B0638546C5AAF24E6B26BAE4AA0CADCFEDE3B8B2C17658 | |||
| 5964 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5964.43089\dt86ll.rar\Mapper\Mapper.exe | executable | |
MD5:F360158F01156FEDDBCFF28B19C2A305 | SHA256:6752BD7AFBA1D78337F63A53E81FF63BFB29EFD3D9B9835985B2A9017FD0E0C1 | |||
| 3080 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | text | |
MD5:978FA425465CEE0416EBDC6E1B80B5CE | SHA256:E3AC6CD4A59752AEC27F825420FB712A761272E643F1E80BFC706BAA8158142D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
20
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3040 | svchost.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3040 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3040 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3040 | svchost.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3040 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3040 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |