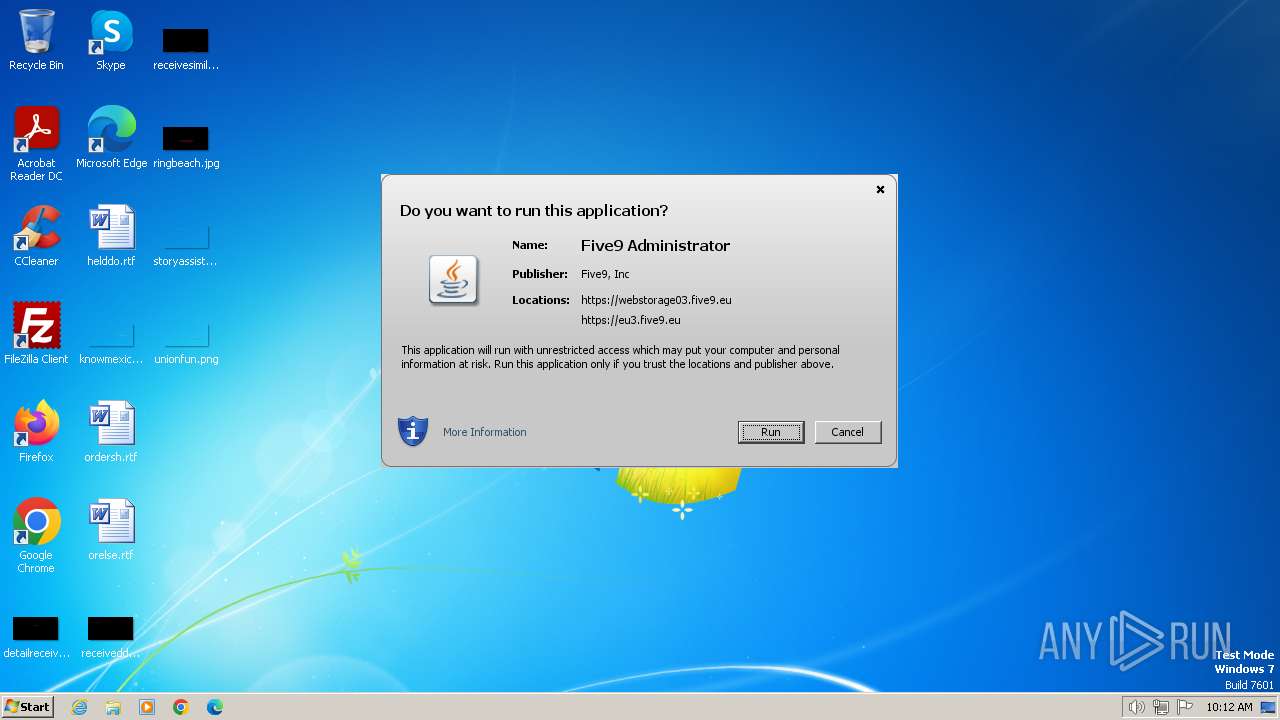
| File name: | domainAdmin (3).jnlp |
| Full analysis: | https://app.any.run/tasks/d637236b-c021-4825-b402-d5135718744a |
| Verdict: | Malicious activity |
| Analysis date: | January 26, 2024, 10:12:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/xml |
| File info: | XML 1.0 document, ASCII text |
| MD5: | 1E8FF518B57F26D9842158338D0F308B |
| SHA1: | 75901986A1C703153D82847B93C3B11D25554BEE |
| SHA256: | 732294723AB69E6646D5035F472F6ECA17925810465DC35761E4E834CF6DA529 |
| SSDEEP: | 24:2dasRv8ebxAqjAQe2qtBtRv8iStw5PRD7LpN9xhdz6FTS+dGPWgwCllvuop:caPebxxvhiZ9P9xHz6tS0GPWgwCllvHp |
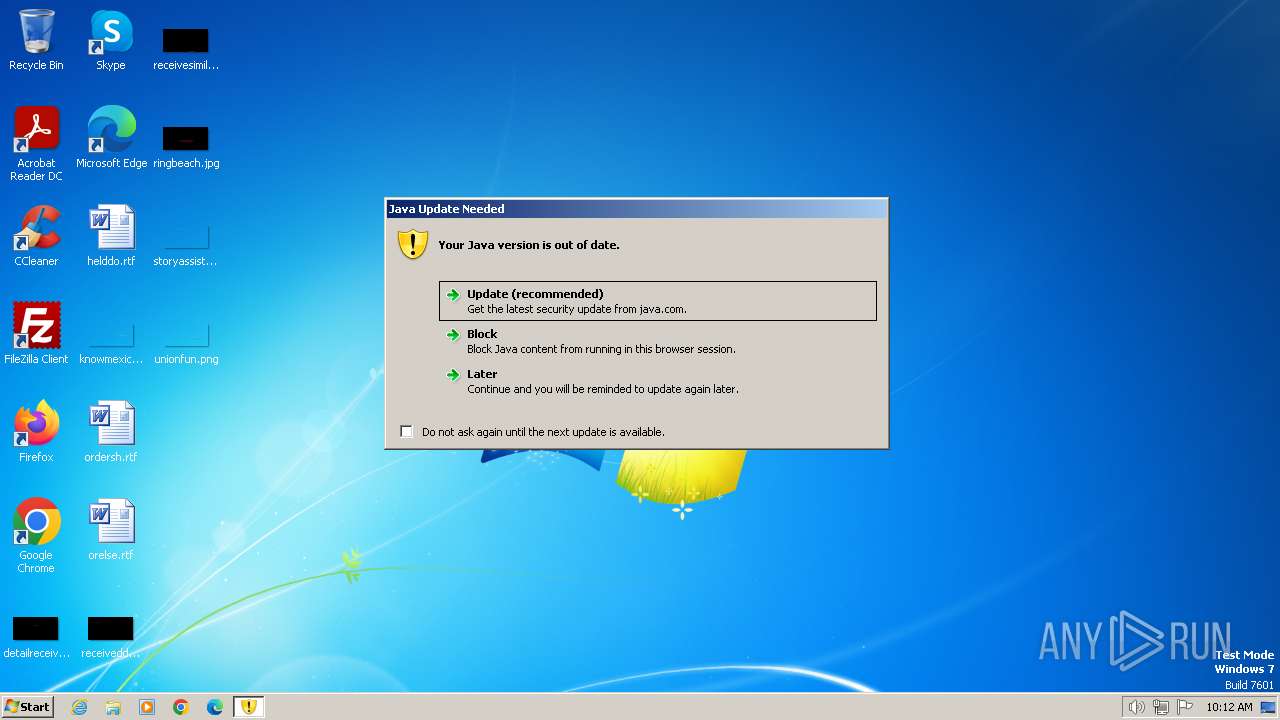
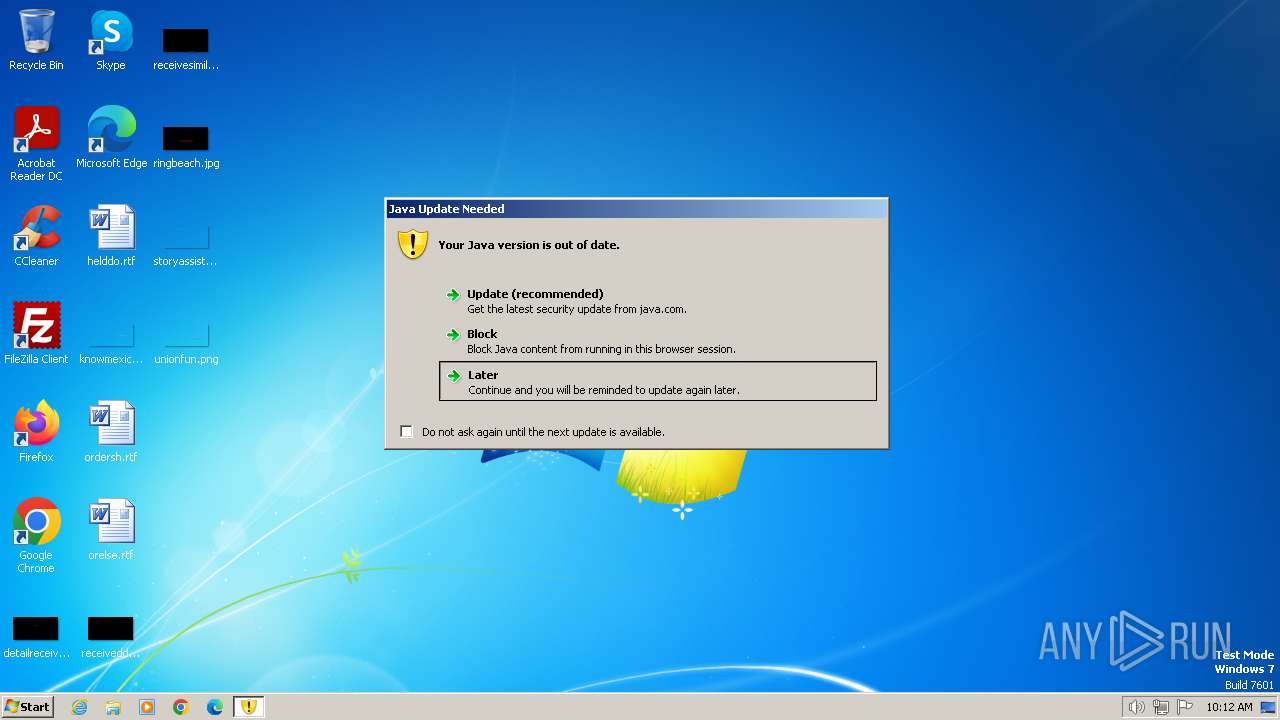
MALICIOUS
Drops the executable file immediately after the start
- jp2launcher.exe (PID: 2908)
SUSPICIOUS
Checks for Java to be installed
- javaws.exe (PID: 1036)
- javaw.exe (PID: 552)
- javaw.exe (PID: 1880)
- javaw.exe (PID: 2324)
- jp2launcher.exe (PID: 2908)
Application launched itself
- javaws.exe (PID: 1036)
Reads settings of System Certificates
- jp2launcher.exe (PID: 2908)
Executable content was dropped or overwritten
- jp2launcher.exe (PID: 2908)
Reads the Internet Settings
- jp2launcher.exe (PID: 2908)
INFO
Checks supported languages
- javaw.exe (PID: 552)
- javaws.exe (PID: 1036)
- javaw.exe (PID: 1880)
- javaw.exe (PID: 2324)
- javaws.exe (PID: 2756)
- jp2launcher.exe (PID: 2908)
Reads the computer name
- javaw.exe (PID: 552)
- javaw.exe (PID: 1880)
- javaw.exe (PID: 2324)
- jp2launcher.exe (PID: 2908)
Creates files in the program directory
- javaw.exe (PID: 552)
Create files in a temporary directory
- javaw.exe (PID: 552)
- javaw.exe (PID: 1880)
- javaw.exe (PID: 2324)
- jp2launcher.exe (PID: 2908)
Creates files or folders in the user directory
- jp2launcher.exe (PID: 2908)
Reads the machine GUID from the registry
- jp2launcher.exe (PID: 2908)
Checks proxy server information
- jp2launcher.exe (PID: 2908)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .jnlp | | | Java Web Start application descriptor (88.3) |
|---|---|---|
| .xml | | | Generic XML (ASCII) (11.6) |
EXIF
XMP
| JnlpSpec: | 6.0+ |
|---|---|
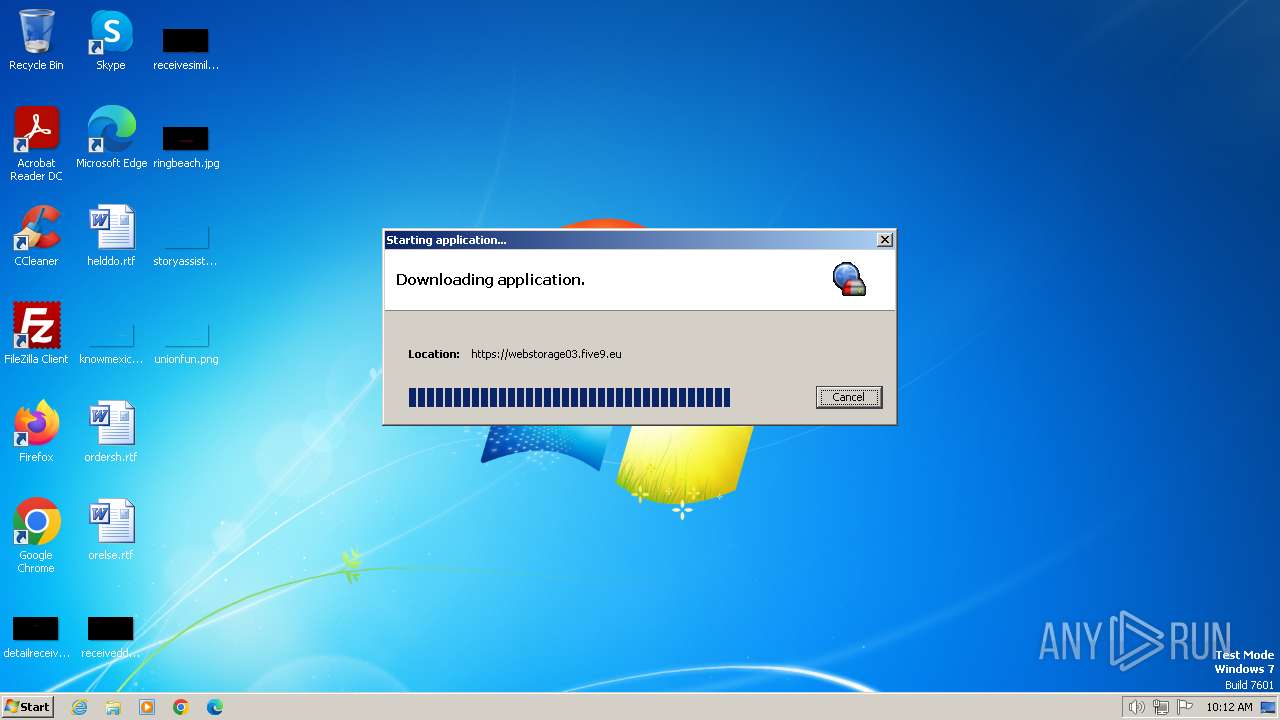
| JnlpCodebase: | https://webstorage03.five9.eu |
| JnlpHref: | https://eu3.five9.eu/start/lib/domainAdmin.jnlp?user=chris.henderson%40idealheating.com&domain=Ideal+Boilers |
| JnlpInformationTitle: | Five9 Administrator |
| JnlpInformationVendor: | Five9 |
| JnlpInformationHomepageHref: | http://www.five9.com/ |
| JnlpInformationDescription: | Five9 Administrator |
| JnlpInformationDescriptionKind: | short |
| JnlpInformationIconHref: | https://eu3.five9.eu/start/lib/../images/five9/administrator.gif |
| JnlpSecurityAll-permissions: | - |
| JnlpUpdateCheck: | always |
| JnlpUpdatePolicy: | always |
| JnlpResourcesJ2seVersion: | 1.6+ |
| JnlpResourcesJ2seInitial-heap-size: | 8M |
| JnlpResourcesJ2seMax-heap-size: | 256M |
| JnlpResourcesJarHref: | /13.0/start/lib/ual__V13.0.140.jar |
| JnlpResourcesJarMain: | |
| JnlpApplication-descMain-class: | com.five9.ual.launcher.LaunchManager |
| JnlpApplication-descArgument: | "five9.log.dir=env003.ldn.five9.com" |
Total processes
46
Monitored processes
7
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 552 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_2\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.11.271.2" "later" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 1036 | "C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe" "C:\Users\admin\AppData\Local\Temp\domainAdmin (3).jnlp" | C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe | — | explorer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Start Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
| 1880 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_2\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.timestamp.11.271.2" "1706263952" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 1904 | C:\Windows\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2324 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_2\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.suppression.11.271.2" "false" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 2756 | JavaWSSplashScreen -splash 49169 "C:\Program Files\Java\jre1.8.0_271\lib\deploy\splash.gif" | C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Start Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
| 2908 | "C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe" -secure -javaws -jre "C:\Program Files\Java\jre1.8.0_271" -vma LWNsYXNzcGF0aABDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxkZXBsb3kuamFyAC1EamF2YS5zZWN1cml0eS5wb2xpY3k9ZmlsZTpDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxzZWN1cml0eVxqYXZhd3MucG9saWN5AC1EdHJ1c3RQcm94eT10cnVlAC1YdmVyaWZ5OnJlbW90ZQAtRGpubHB4LmhvbWU9QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzI3MVxiaW4ALURqYXZhLnNlY3VyaXR5Lm1hbmFnZXIALURqbmxweC5vcmlnRmlsZW5hbWVBcmc9QzpcVXNlcnNcYWRtaW5cQXBwRGF0YVxMb2NhbFxUZW1wXGRvbWFpbkFkbWluICgzKS5qbmxwAC1Eam5scHgucmVtb3ZlPWZhbHNlAC1Ec3VuLmF3dC53YXJtdXA9dHJ1ZQAtWGJvb3RjbGFzc3BhdGgvYTpDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxqYXZhd3MuamFyO0M6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF8yNzFcbGliXGRlcGxveS5qYXI7QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzI3MVxsaWJccGx1Z2luLmphcgAtWG1zOE0ALVhteDI1Nk0ALURqbmxweC5oZWFwc2l6ZT04TSwyNTZNAC1Eam5scHguc3BsYXNocG9ydD00OTE3MAAtRGpubHB4Lmp2bT1DOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGJpblxqYXZhdy5leGU= -ma QzpcVXNlcnNcYWRtaW5cQXBwRGF0YVxMb2NhbFxUZW1wXGRvbWFpbkFkbWluICgzKS5qbmxw | C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe | javaws.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
Total events
8 234
Read events
8 201
Write events
23
Delete events
10
Modification events
| (PID) Process: | (552) javaw.exe | Key: | HKEY_CURRENT_USER\Software\JavaSoft\DeploymentProperties |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1880) javaw.exe | Key: | HKEY_CURRENT_USER\Software\JavaSoft\DeploymentProperties |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2324) javaw.exe | Key: | HKEY_CURRENT_USER\Software\JavaSoft\DeploymentProperties |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2908) jp2launcher.exe | Key: | HKEY_CURRENT_USER\Software\JavaSoft\DeploymentProperties |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2908) jp2launcher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2908) jp2launcher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2908) jp2launcher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2908) jp2launcher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2908) jp2launcher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2908) jp2launcher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005B010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
48
Suspicious files
93
Text files
44
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2908 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\39\26a42d27-1973bc4a.idx | abr | |
MD5:7A2B2A6A7418160B22D307F5BEA63383 | SHA256:F7118AFB02DDEAC1D903751E9E0F252CA7BDE1B5357CE966C777D471D1E1E50D | |||
| 2908 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\4\72f9b244-02081833da0e9b5d9b88a5027a0d5f69dd785238ef4c903b5cb47189f813c836-6.0.lap | text | |
MD5:E0CAB86145C888CD0253CEC39A3C5434 | SHA256:33EB3EA419AA0E253E126E8F19A0D369C35F395DC7E8EEEFEEC9595637E6A30F | |||
| 2908 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\4\72f9b244-2d6ca5b4.idx | binary | |
MD5:7A2B2A6A7418160B22D307F5BEA63383 | SHA256:F7118AFB02DDEAC1D903751E9E0F252CA7BDE1B5357CE966C777D471D1E1E50D | |||
| 2908 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\61\6fd4e47d-38d510eb.idx | abr | |
MD5:7A2B2A6A7418160B22D307F5BEA63383 | SHA256:F7118AFB02DDEAC1D903751E9E0F252CA7BDE1B5357CE966C777D471D1E1E50D | |||
| 2908 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\4\72f9b244-2d6ca5b4-temp | xml | |
MD5:1E8FF518B57F26D9842158338D0F308B | SHA256:732294723AB69E6646D5035F472F6ECA17925810465DC35761E4E834CF6DA529 | |||
| 552 | javaw.exe | C:\Users\admin\AppData\Local\Temp\JavaDeployReg.log | text | |
MD5:20378ADFF3F6AD2CEC7D9B2F39BDC0A2 | SHA256:AC7C9C05C187658110B0CDFCB480BB1D248FDCF60F6BA818C2883D7A3E366D1C | |||
| 2908 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\lastAccessed | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 552 | javaw.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\deployment.properties | text | |
MD5:24F8F10CB75A160DABDB0DB5018842A0 | SHA256:5BA67FBA8F8BB7E955CE47276A6702937F6D8313B86C5544F562C91068101220 | |||
| 2908 | jp2launcher.exe | C:\Users\admin\AppData\Local\Temp\jar_cache8172776409960437654.tmp | xml | |
MD5:AF579014E4E50D0386E2DFC5865B0C46 | SHA256:E694739B5814844FC82185649BD1A0C55EBF20783328CE3ADC4773AC3F297E65 | |||
| 2908 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\39\26a42d27-1973bc4a | java | |
MD5:A0FBD5FDD11BF13C5A2CD9AB3A4A9527 | SHA256:9E3962A558CE9C6FB2E50F623BE0BD376CB9359C25A923DD39C921A24D87B1F6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
23
DNS requests
4
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2908 | jp2launcher.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | binary | 471 b | unknown |
2908 | jp2launcher.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | binary | 471 b | unknown |
2908 | jp2launcher.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | binary | 471 b | unknown |
2908 | jp2launcher.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | binary | 471 b | unknown |
2908 | jp2launcher.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | binary | 727 b | unknown |
2908 | jp2launcher.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | binary | 471 b | unknown |
2908 | jp2launcher.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | binary | 727 b | unknown |
2908 | jp2launcher.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | binary | 727 b | unknown |
2908 | jp2launcher.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | binary | 727 b | unknown |
2908 | jp2launcher.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2908 | jp2launcher.exe | 212.187.211.96:443 | eu3.five9.eu | FIVE9 | GB | unknown |
2908 | jp2launcher.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2908 | jp2launcher.exe | 212.187.211.201:443 | webstorage03.five9.eu | FIVE9 | GB | unknown |
2908 | jp2launcher.exe | 23.199.222.107:443 | javadl-esd-secure.oracle.com | AKAMAI-AS | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
eu3.five9.eu |
| unknown |
ocsp.digicert.com |
| whitelisted |
webstorage03.five9.eu |
| unknown |
javadl-esd-secure.oracle.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2908 | jp2launcher.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
— | — | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |