| File name: | DreamAPIPortable.exe |
| Full analysis: | https://app.any.run/tasks/9a451c2b-7623-492e-bfac-0b7adbe80329 |
| Verdict: | Malicious activity |
| Analysis date: | May 18, 2025, 00:09:17 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | 6610CB5FCF05BDB313186355C3C6318A |
| SHA1: | DC214B097FDB66249E43A4DE65B86C68153AD6AA |
| SHA256: | 7305CBB1E020126157B14EFC7C923ED0E6553E03A0C79209895C778F2C17C442 |
| SSDEEP: | 196608:3lZZ06Vx6mDDAZzDNBcMgi9FEEuOHsN9t:1Zm6Vx6mIZzk1iKOMft |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process drops C-runtime libraries
- DreamAPIPortable.exe (PID: 2320)
Executable content was dropped or overwritten
- DreamAPIPortable.exe (PID: 2320)
Process drops legitimate windows executable
- DreamAPIPortable.exe (PID: 2320)
Process drops python dynamic module
- DreamAPIPortable.exe (PID: 2320)
Drops a system driver (possible attempt to evade defenses)
- DreamAPIPortable.exe (PID: 2320)
Application launched itself
- DreamAPIPortable.exe (PID: 2320)
Loads Python modules
- DreamAPIPortable.exe (PID: 4976)
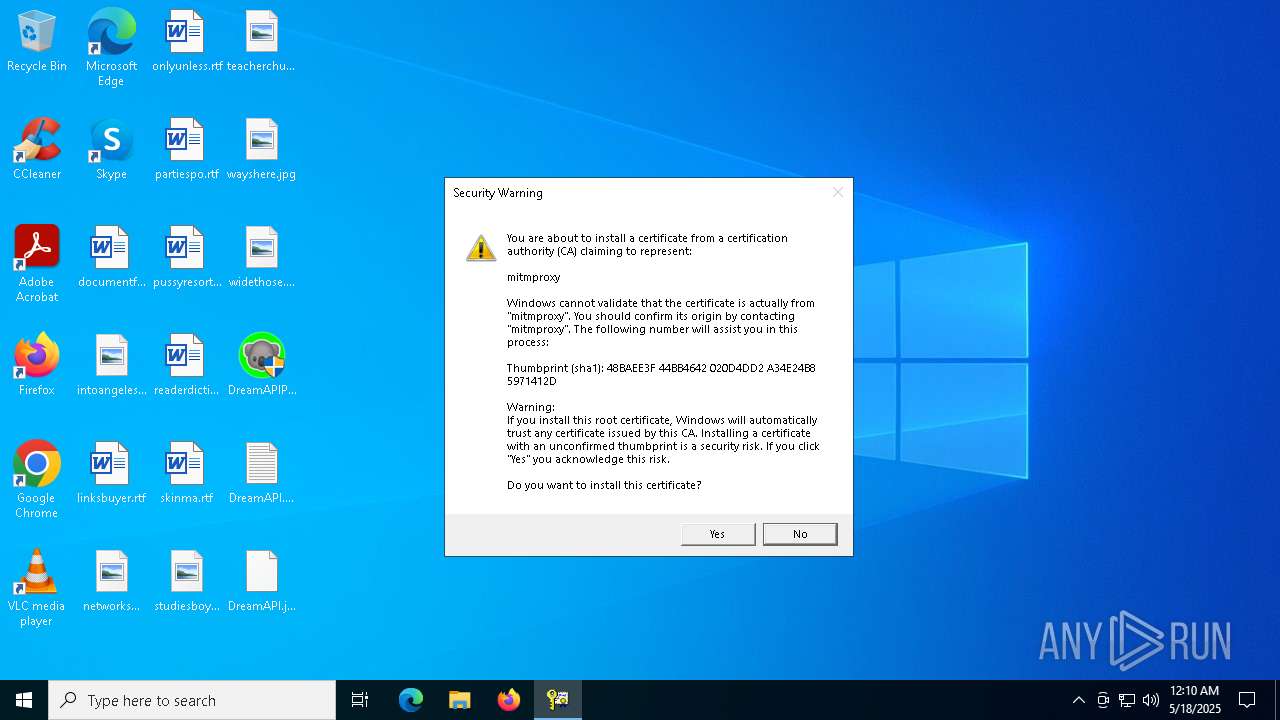
Adds/modifies Windows certificates
- slui.exe (PID: 1012)
Starts CMD.EXE for commands execution
- DreamAPIPortable.exe (PID: 4976)
There is functionality for taking screenshot (YARA)
- DreamAPIPortable.exe (PID: 4976)
Reads security settings of Internet Explorer
- DreamAPIPortable.exe (PID: 4976)
INFO
The sample compiled with english language support
- DreamAPIPortable.exe (PID: 2320)
Reads the computer name
- DreamAPIPortable.exe (PID: 2320)
- DreamAPIPortable.exe (PID: 4976)
Checks supported languages
- DreamAPIPortable.exe (PID: 2320)
- DreamAPIPortable.exe (PID: 4976)
Create files in a temporary directory
- DreamAPIPortable.exe (PID: 2320)
- DreamAPIPortable.exe (PID: 4976)
PyInstaller has been detected (YARA)
- DreamAPIPortable.exe (PID: 2320)
- DreamAPIPortable.exe (PID: 4976)
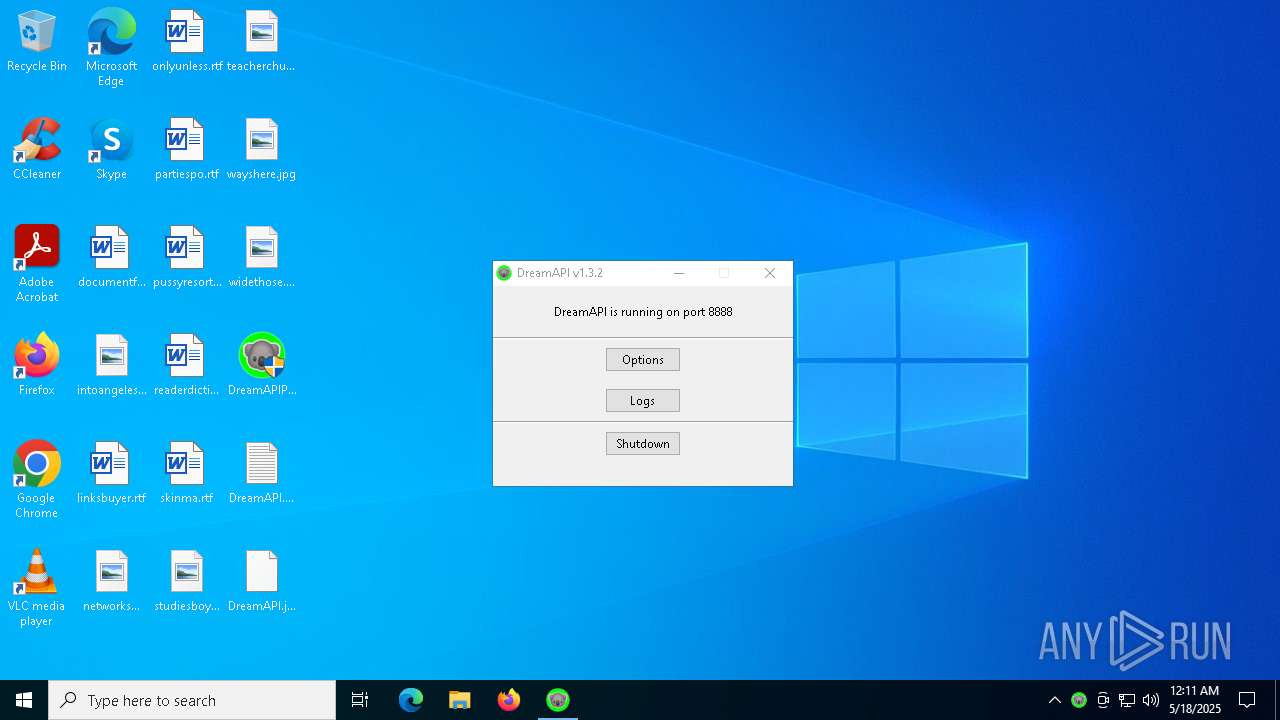
Checks proxy server information
- slui.exe (PID: 1012)
- DreamAPIPortable.exe (PID: 4976)
Reads the software policy settings
- slui.exe (PID: 1012)
Reads the machine GUID from the registry
- DreamAPIPortable.exe (PID: 4976)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2021:04:15 05:29:49+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.28 |
| CodeSize: | 136704 |
| InitializedDataSize: | 244224 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x90ac |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.3.2.0 |
| ProductVersionNumber: | 1.3.2.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | acidicoala |
| FileDescription: | DreamAPI |
| FileVersion: | 1.3.2.0 |
| InternalName: | DreamAPI |
| LegalCopyright: | Fuck the copyright >:D |
| OriginalFileName: | DreamAPI.exe |
| ProductName: | DreamAPI |
| ProductVersion: | 1.3.2.0 |
Total processes
131
Monitored processes
10
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1012 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | certutil -addstore -user Root "C:\Users\admin\.mitmproxy\mitmproxy-ca-cert.cer" | C:\Windows\System32\certutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2236 | "C:\Users\admin\Desktop\DreamAPIPortable.exe" | C:\Users\admin\Desktop\DreamAPIPortable.exe | — | explorer.exe | |||||||||||
User: admin Company: acidicoala Integrity Level: MEDIUM Description: DreamAPI Exit code: 3221226540 Version: 1.3.2.0 Modules
| |||||||||||||||
| 2284 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2320 | "C:\Users\admin\Desktop\DreamAPIPortable.exe" | C:\Users\admin\Desktop\DreamAPIPortable.exe | explorer.exe | ||||||||||||
User: admin Company: acidicoala Integrity Level: HIGH Description: DreamAPI Version: 1.3.2.0 Modules
| |||||||||||||||
| 2852 | C:\WINDOWS\system32\cmd.exe /c "certutil -addstore -user Root "C:\Users\admin\.mitmproxy\mitmproxy-ca-cert.cer"" | C:\Windows\System32\cmd.exe | — | DreamAPIPortable.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4976 | "C:\Users\admin\Desktop\DreamAPIPortable.exe" | C:\Users\admin\Desktop\DreamAPIPortable.exe | DreamAPIPortable.exe | ||||||||||||
User: admin Company: acidicoala Integrity Level: HIGH Description: DreamAPI Version: 1.3.2.0 Modules
| |||||||||||||||
| 5864 | certutil -store -user Root mitmproxy | C:\Windows\System32\certutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 2148073489 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6476 | C:\WINDOWS\system32\cmd.exe /c "certutil -store -user Root mitmproxy" | C:\Windows\System32\cmd.exe | — | DreamAPIPortable.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2148073489 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6652 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 191
Read events
8 178
Write events
11
Delete events
2
Modification events
| (PID) Process: | (5864) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.1!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_AUTO_UPDATE_CA_REVOCATION | |||
| (PID) Process: | (5864) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.2!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_AUTO_UPDATE_END_REVOCATION | |||
| (PID) Process: | (5864) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.3!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_NO_OCSP_FAILOVER_TO_CRL | |||
| (PID) Process: | (4976) DreamAPIPortable.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (4976) DreamAPIPortable.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyOverride |
Value: | |||
| (PID) Process: | (4976) DreamAPIPortable.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyServer |
Value: | |||
| (PID) Process: | (4976) DreamAPIPortable.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 1 | |||
| (PID) Process: | (4976) DreamAPIPortable.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyOverride |
Value: <local> | |||
| (PID) Process: | (4976) DreamAPIPortable.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyServer |
Value: 127.0.0.1:8888 | |||
| (PID) Process: | (1012) slui.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\SystemCertificates\Root\Certificates |
| Operation: | delete value | Name: | 48BAEE3F44BB4642020D4DD2A34E24B85971412D |
Value: | |||
Executable files
90
Suspicious files
7
Text files
933
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2320 | DreamAPIPortable.exe | C:\Users\admin\AppData\Local\Temp\_MEI23202\VCRUNTIME140.dll | executable | |
MD5:7942BE5474A095F673582997AE3054F1 | SHA256:8EE6B49830436FF3BEC9BA89213395427B5535813930489F118721FD3D2D942C | |||
| 2320 | DreamAPIPortable.exe | C:\Users\admin\AppData\Local\Temp\_MEI23202\_ruamel_yaml.cp38-win_amd64.pyd | executable | |
MD5:BE49FB611B1272FF3E9CBEE594B8777C | SHA256:ED39E4F7524E50247C802C60EF972E78A0345E9534C08B451C74B0EF4577DE61 | |||
| 2320 | DreamAPIPortable.exe | C:\Users\admin\AppData\Local\Temp\_MEI23202\_queue.pyd | executable | |
MD5:C81D66A03763EDBEDD7ABEC2773974A6 | SHA256:C752ABE44BC4D04657B9CB3A415FA1EE592B6AE77A3661F598F9F21FA9EEF710 | |||
| 2320 | DreamAPIPortable.exe | C:\Users\admin\AppData\Local\Temp\_MEI23202\_hashlib.pyd | executable | |
MD5:3400DA54FAF3C3128F9C9E126A881BE0 | SHA256:68913D6D5102D32DDDF5A21A4770AC2791F29106C0D2D3A3D0192356EA366C66 | |||
| 2320 | DreamAPIPortable.exe | C:\Users\admin\AppData\Local\Temp\_MEI23202\_asyncio.pyd | executable | |
MD5:C660EC7E25CA590AE605CA2EF9A0F668 | SHA256:586B1B8B933F55AC1E059240E9323540E6886DC06587CA60A42F452FBADC62B6 | |||
| 2320 | DreamAPIPortable.exe | C:\Users\admin\AppData\Local\Temp\_MEI23202\_lzma.pyd | executable | |
MD5:0CAA4DA7B74FC8E8F08BA736274BDB46 | SHA256:167C5550B93541C703C8AFEB4D912719D5039230A7EFCE8F4BC500F175252ED8 | |||
| 2320 | DreamAPIPortable.exe | C:\Users\admin\AppData\Local\Temp\_MEI23202\_brotli.cp38-win_amd64.pyd | executable | |
MD5:C128F362316BAB15BF314523BEC9E41D | SHA256:620738F5433F23A5AB6A0A7CAA59383F0984C11A9139D480D5DAC2D4582B1644 | |||
| 2320 | DreamAPIPortable.exe | C:\Users\admin\AppData\Local\Temp\_MEI23202\_bz2.pyd | executable | |
MD5:6FD0281BCA7EEE0F354A91F958714EDB | SHA256:03D8966F4D8AB347140A3AD9938FB91DB11E01E028E980721451070EB0483CF7 | |||
| 2320 | DreamAPIPortable.exe | C:\Users\admin\AppData\Local\Temp\_MEI23202\_cffi_backend.cp38-win_amd64.pyd | executable | |
MD5:275AD9FE8DADF2865EFD2584A9C453EE | SHA256:A1B7AB2AE94C7B68EEA8F6425C746CAEEDE235374B07576071282E932A7D2816 | |||
| 2320 | DreamAPIPortable.exe | C:\Users\admin\AppData\Local\Temp\_MEI23202\_ctypes.pyd | executable | |
MD5:DA2FF1686AB85C37A2A247BB8595C258 | SHA256:279560B61E20B869A059A103FB010093F9E367420BC81182646E357DE8B9740F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
40
DNS requests
14
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5680 | SIHClient.exe | GET | 200 | 104.124.11.58:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5680 | SIHClient.exe | GET | 200 | 104.124.11.58:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
5680 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
5680 | SIHClient.exe | GET | 200 | 104.124.11.58:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
5680 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5680 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
5680 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
5680 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
5680 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5680 | SIHClient.exe | 104.124.11.58:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5680 | SIHClient.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
5680 | SIHClient.exe | 13.95.31.18:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5216 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4976 | DreamAPIPortable.exe | 185.199.109.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |