| File name: | ƁĕӊίᾓďƳỡטּ.exe |
| Full analysis: | https://app.any.run/tasks/7094cc4e-fa4d-4479-9d18-73eb836152b7 |
| Verdict: | Malicious activity |
| Analysis date: | June 04, 2025, 13:30:20 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | B070E830A6863A4C19A4F86B7D67CCFF |
| SHA1: | FB5E98A9BEFFB68D2D2A3A3A4ED523830E1F8718 |
| SHA256: | 72EAE37517EAED332BC583A116070F191452F38F8AD4DC5D04F79632B4E119C5 |
| SSDEEP: | 1536:z7fPGykbOqjoHm4pICdfkLtAfupcWX50MxFY+yIOlnToIfixQBgO:vq6+ouCpk2mpcWJ0r+QNTBfivO |
MALICIOUS
BABADEDA has been found (auto)
- ƁĕӊίᾓďƳỡטּ.exe (PID: 2644)
Starts NET.EXE for service management
- cmd.exe (PID: 6584)
- net.exe (PID: 6044)
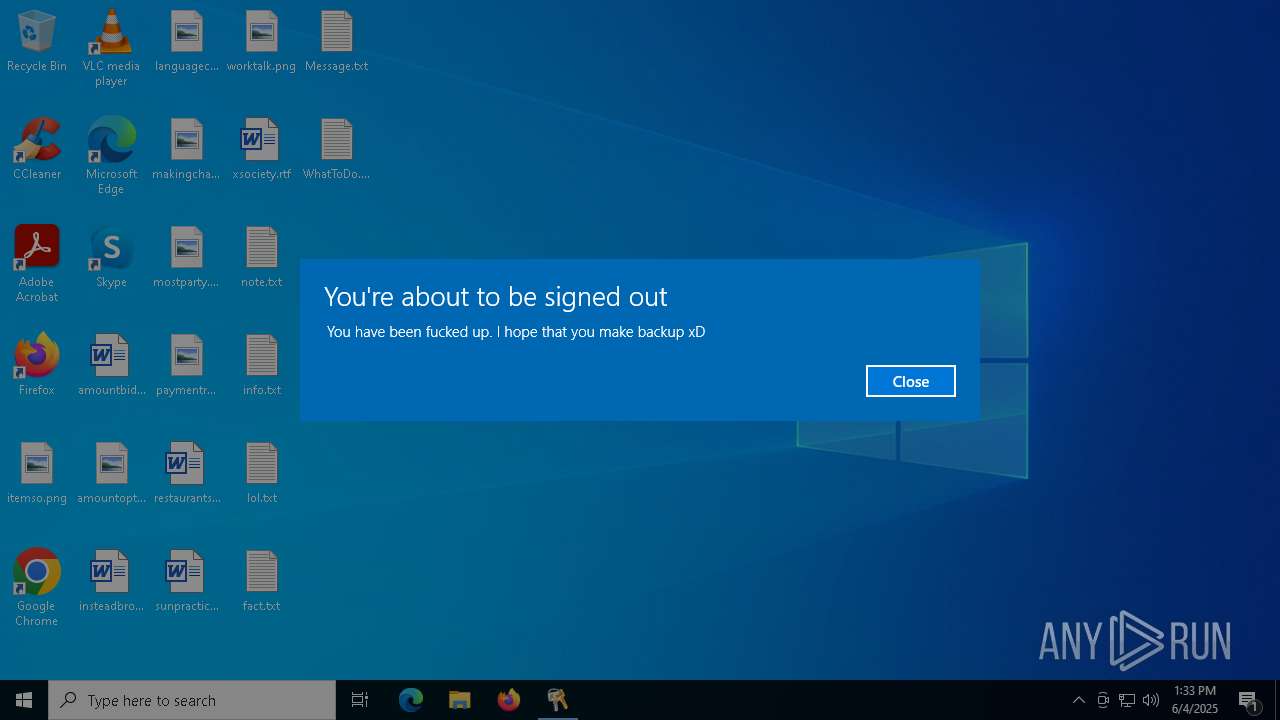
Disables task manager
- reg.exe (PID: 6068)
UAC/LUA settings modification
- reg.exe (PID: 1072)
Starts NET.EXE to view/add/change user profiles
- net.exe (PID: 8084)
- cmd.exe (PID: 6584)
- net.exe (PID: 856)
SUSPICIOUS
Reads security settings of Internet Explorer
- ƁĕӊίᾓďƳỡטּ.exe (PID: 2644)
- wordpad.exe (PID: 444)
- ShellExperienceHost.exe (PID: 6572)
Executing commands from a ".bat" file
- ƁĕӊίᾓďƳỡטּ.exe (PID: 2644)
Starts CMD.EXE for commands execution
- ƁĕӊίᾓďƳỡטּ.exe (PID: 2644)
Uses NETSH.EXE to change the status of the firewall
- cmd.exe (PID: 6584)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6584)
Process uses IPCONFIG to discard the IP address configuration
- cmd.exe (PID: 6584)
Sets XML DOM element text (SCRIPT)
- wordpad.exe (PID: 444)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 6584)
The system shut down or reboot
- cmd.exe (PID: 6584)
INFO
The sample compiled with english language support
- ƁĕӊίᾓďƳỡטּ.exe (PID: 2644)
Process checks computer location settings
- ƁĕӊίᾓďƳỡטּ.exe (PID: 2644)
Create files in a temporary directory
- ƁĕӊίᾓďƳỡטּ.exe (PID: 2644)
Reads the computer name
- ƁĕӊίᾓďƳỡטּ.exe (PID: 2644)
- ShellExperienceHost.exe (PID: 6572)
- wordpad.exe (PID: 444)
Checks supported languages
- ƁĕӊίᾓďƳỡטּ.exe (PID: 2644)
- ShellExperienceHost.exe (PID: 6572)
- wordpad.exe (PID: 444)
Reads security settings of Internet Explorer
- notepad.exe (PID: 7332)
- write.exe (PID: 780)
- notepad.exe (PID: 7900)
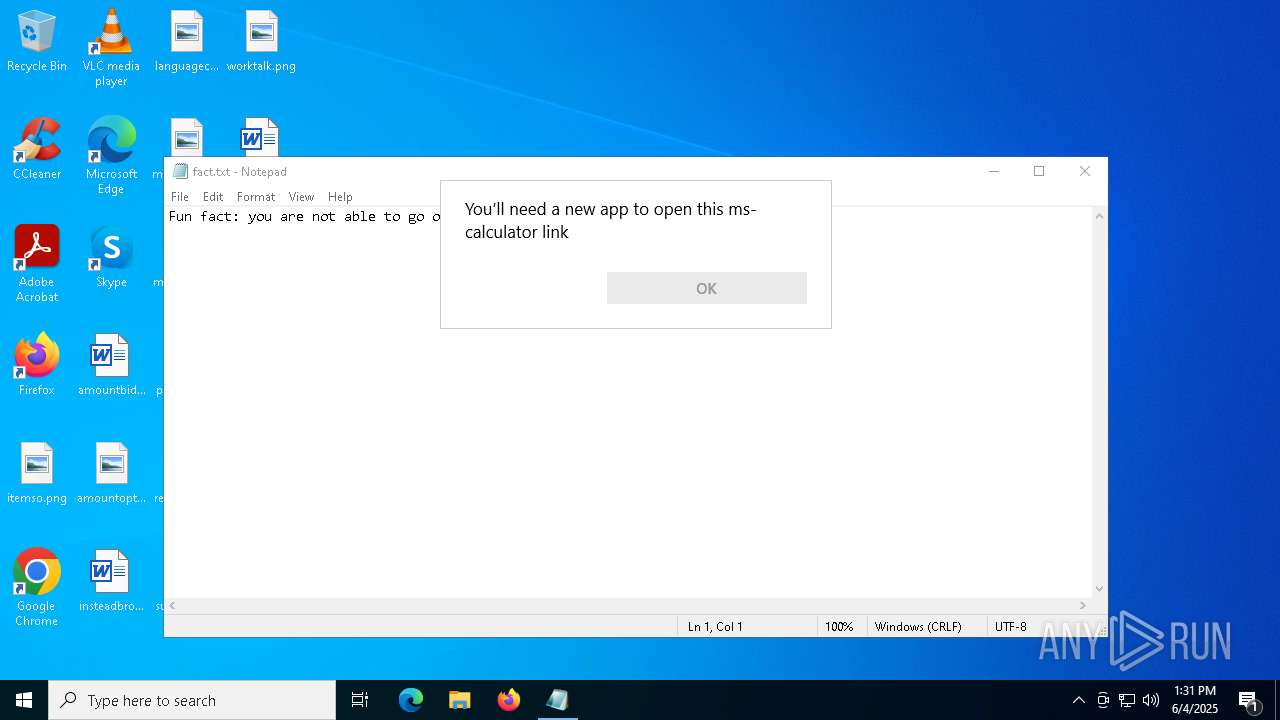
- OpenWith.exe (PID: 1012)
- notepad.exe (PID: 5360)
- notepad.exe (PID: 2124)
- calc.exe (PID: 7776)
- notepad.exe (PID: 6044)
Reads Environment values
- wordpad.exe (PID: 444)
Manual execution by a user
- notepad.exe (PID: 5360)
- notepad.exe (PID: 7900)
- notepad.exe (PID: 2124)
- notepad.exe (PID: 6044)
- notepad.exe (PID: 7332)
Reads the software policy settings
- slui.exe (PID: 2432)
- slui.exe (PID: 656)
Reads the time zone
- net1.exe (PID: 7896)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:07:30 08:52:50+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 68608 |
| InitializedDataSize: | 22528 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug, Pre-release, Private build |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileVersion: | 6.6.6 |
| ProductVersion: | 6.6.6 |
| ProductName: | ƁĕӊίᾓďƳỡטּ |
| OriginalFileName: | ƁĕӊίᾓďƳỡטּ |
| InternalName: | ƁĕӊίᾓďƳỡטּ |
| FileDescription: | This will not destroy your PC, this will KILL IT. |
| LegalCopyright: | i can see you ﻩ |
| Comments: | I am watching you ﻩ |
Total processes
195
Monitored processes
59
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | timeout 15 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 444 | "C:\Program Files\Windows NT\Accessories\wordpad.exe" | C:\Program Files\Windows NT\Accessories\wordpad.exe | — | write.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Wordpad Application Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
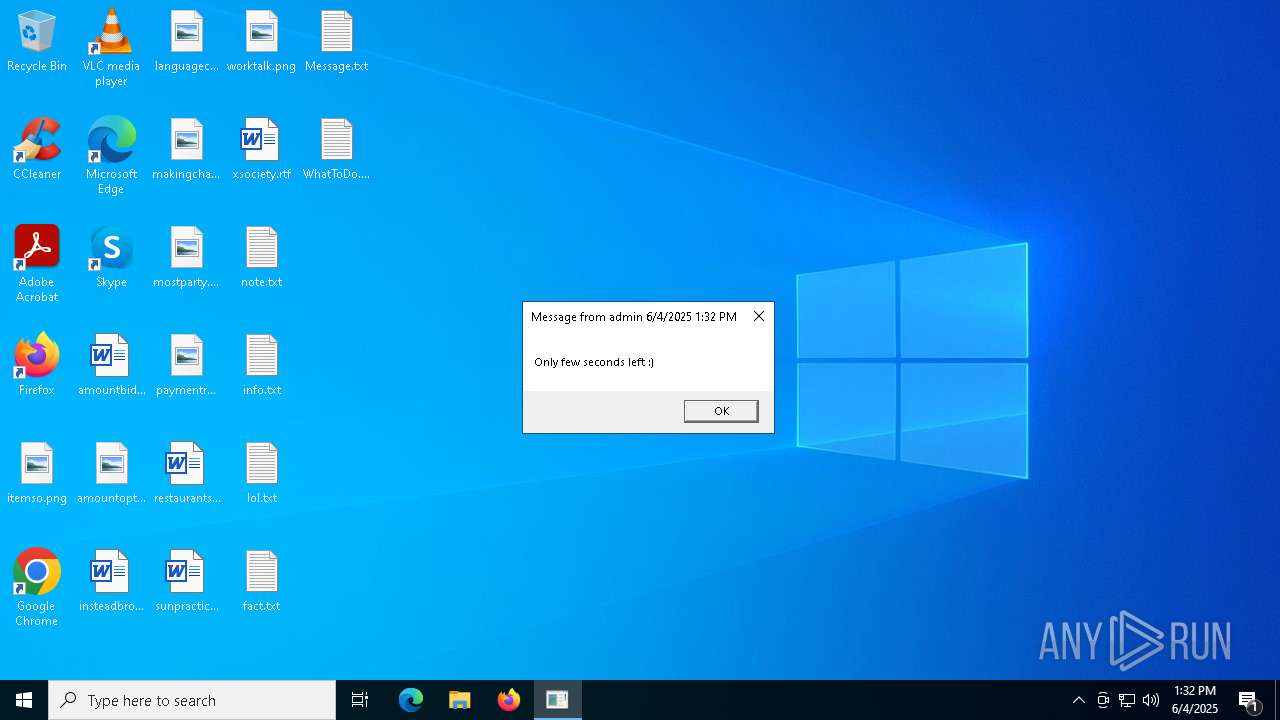
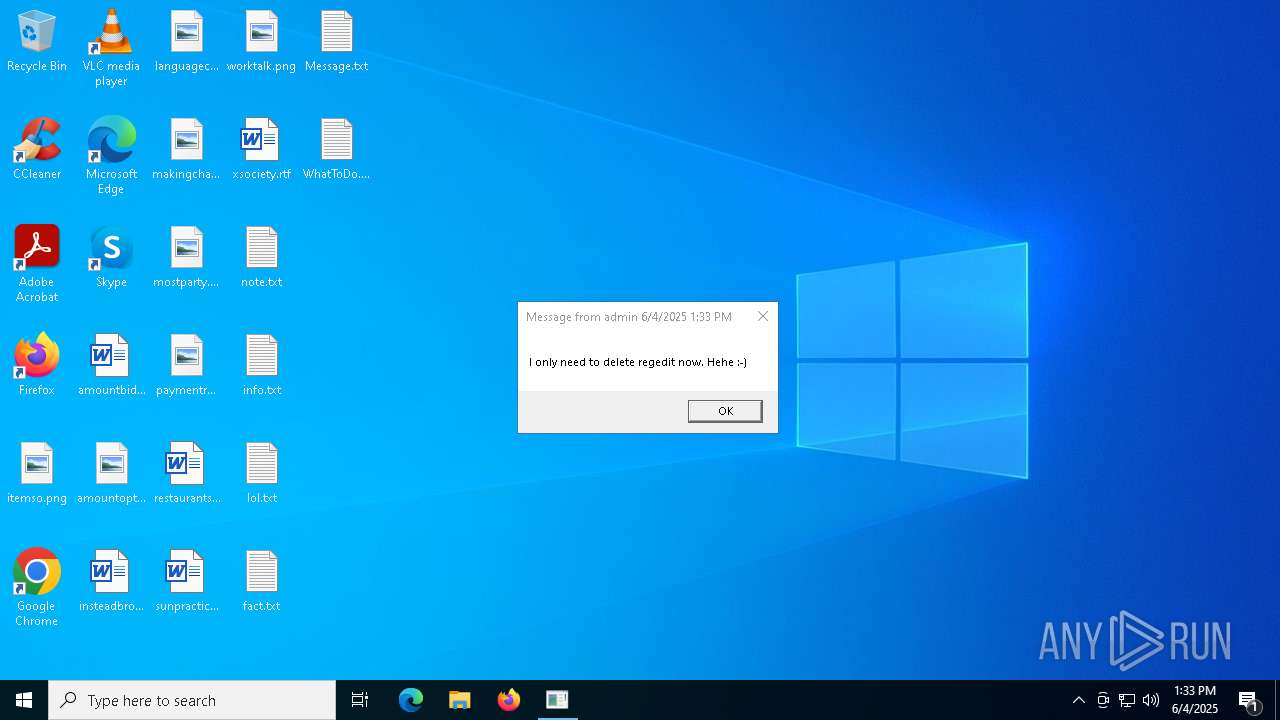
| 616 | msg * /w Only few seconds left :) | C:\Windows\System32\msg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Message Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 656 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 780 | write | C:\Windows\System32\write.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Write Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | net user /delete admin | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1072 | reg ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
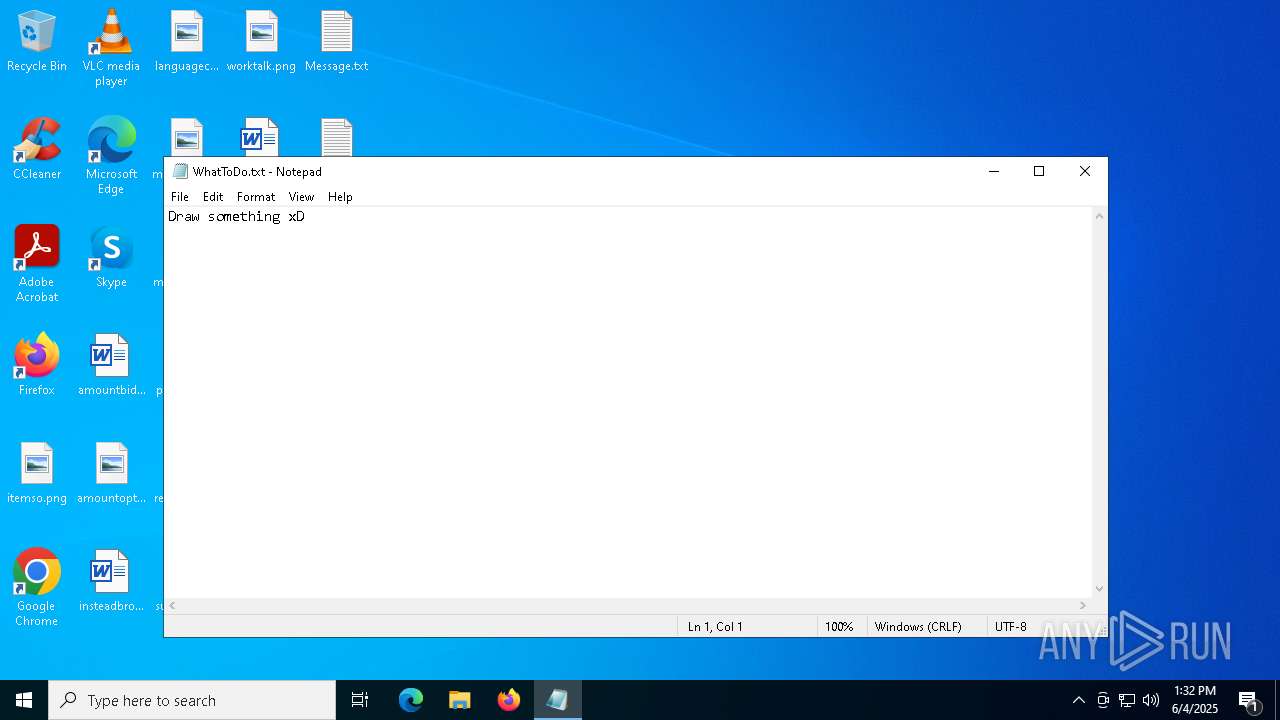
| 2124 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\WhatToDo.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | mspaint | C:\Windows\System32\mspaint.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
113 370
Read events
10 324
Write events
77
Delete events
102 969
Modification events
| (PID) Process: | (2416) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Windows\System |
| Operation: | write | Name: | DisableCMD |
Value: 2 | |||
| (PID) Process: | (1072) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (6572) ShellExperienceHost.exe | Key: | \REGISTRY\A\{62b945c1-8d89-c8e9-f44a-3dd97c2f0ea2}\LocalState |
| Operation: | write | Name: | PeekBadges |
Value: 5B005D0000006CEA66D854D5DB01 | |||
| (PID) Process: | (6572) ShellExperienceHost.exe | Key: | \REGISTRY\A\{62b945c1-8d89-c8e9-f44a-3dd97c2f0ea2}\LocalState |
| Operation: | write | Name: | PeekBadges |
Value: 5B005D000000C88767D854D5DB01 | |||
| (PID) Process: | (6068) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableTaskMgr |
Value: 1 | |||
| (PID) Process: | (444) wordpad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\wordpad.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: DB52120000000000 | |||
| (PID) Process: | (444) wordpad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Wordpad\Ribbon |
| Operation: | write | Name: | QatItems |
Value: <siq:customUI xmlns:siq="http://schemas.microsoft.com/windows/2009/ribbon/qat"><siq:ribbon minimized="false"><siq:qat position="0"><siq:sharedControls><siq:control idQ="siq:10002" visible="false" argument="0"/><siq:control idQ="siq:10003" visible="false" argument="0"/><siq:control idQ="siq:10004" visible="true" argument="0"/><siq:control idQ="siq:10020" visible="false" argument="0"/><siq:control idQ="siq:10017" visible="false" argument="0"/><siq:control idQ="siq:10018" visible="false" argument="0"/><siq:control idQ="siq:31001" visible="true" argument="0"/><siq:control idQ="siq:31002" visible="true" argument="0"/></siq:sharedControls></siq:qat></siq:ribbon></siq:customUI> | |||
| (PID) Process: | (444) wordpad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Wordpad\Options |
| Operation: | write | Name: | Wrap |
Value: 2 | |||
| (PID) Process: | (444) wordpad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Wordpad\Options |
| Operation: | write | Name: | ShowStatusBar |
Value: 1 | |||
| (PID) Process: | (444) wordpad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Wordpad\Options |
| Operation: | write | Name: | ShowRuler |
Value: 1 | |||
Executable files
0
Suspicious files
0
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2644 | ƁĕӊίᾓďƳỡטּ.exe | C:\Users\admin\AppData\Local\Temp\1CD.tmp\1CE.tmp\1CF.bat | text | |
MD5:AB2C458106FE04F1BC1229D8B585FA38 | SHA256:42FA05993F8C41EF816F29731A41DEC92F45FBF119243E399D12979813343F4B | |||
| 2136 | mspaint.exe | C:\Windows\debug\WIA\wiatrace.log | text | |
MD5:FF1351C41B384078040384774A318961 | SHA256:369E4EBE4DDE43D9A7A027B0BC7D5E29896D0E0801F557EB5C598ABCE643D29B | |||
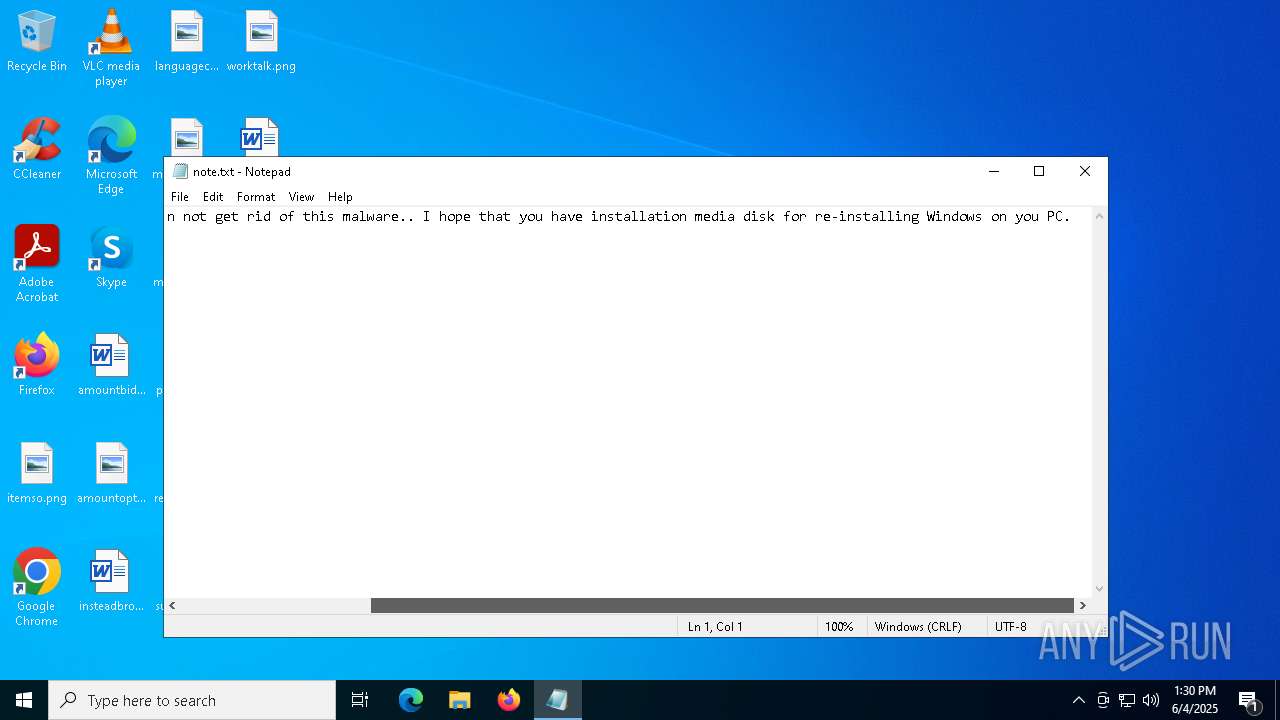
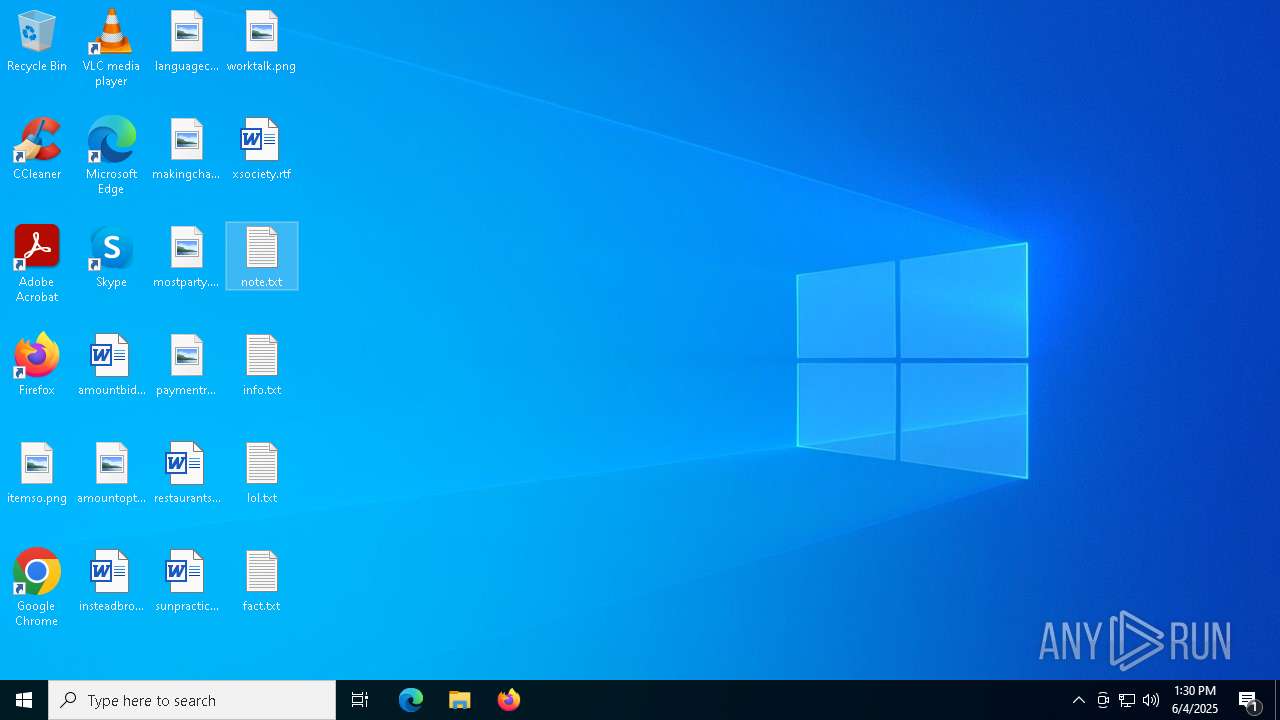
| 6584 | cmd.exe | C:\Users\admin\Desktop\WhatToDo.txt | text | |
MD5:0CF4A2FD2AC2B49328C571102E49880E | SHA256:B6DECB10F7133528BBCC3449EDD693497DDC0552AC85E1F6CAF2650FD2507ACF | |||
| 6584 | cmd.exe | C:\Users\admin\Desktop\info.txt | text | |
MD5:E1923D6D619AF6708BFC11C2986CEC2F | SHA256:CAE0D191C628396A336AC96170DA5F2D4A22141F7563B3251AA2EB2931CCB287 | |||
| 6584 | cmd.exe | C:\Users\admin\Desktop\lol.txt | text | |
MD5:EEDF23FEA79FCFD3B1486C16E947A549 | SHA256:3CFC90F75B470BA28A3C186C01CF277D760DC9A355A0B6598FE9A6717B05FBE6 | |||
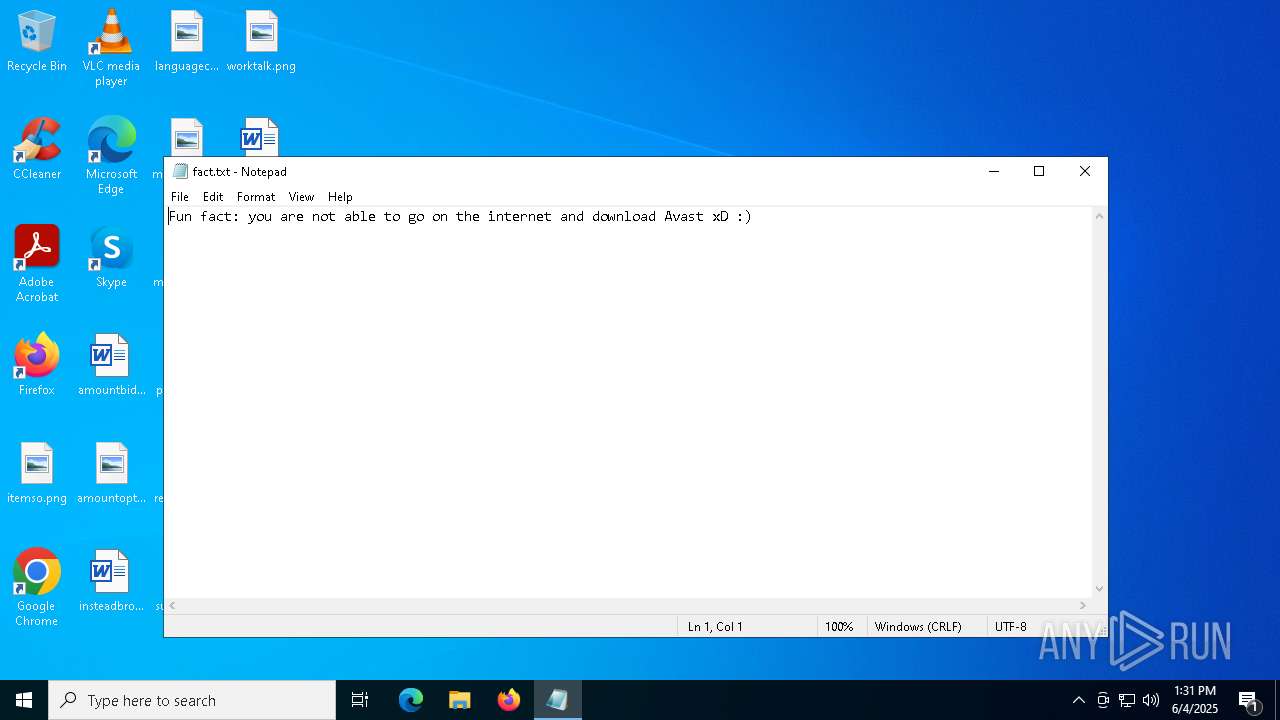
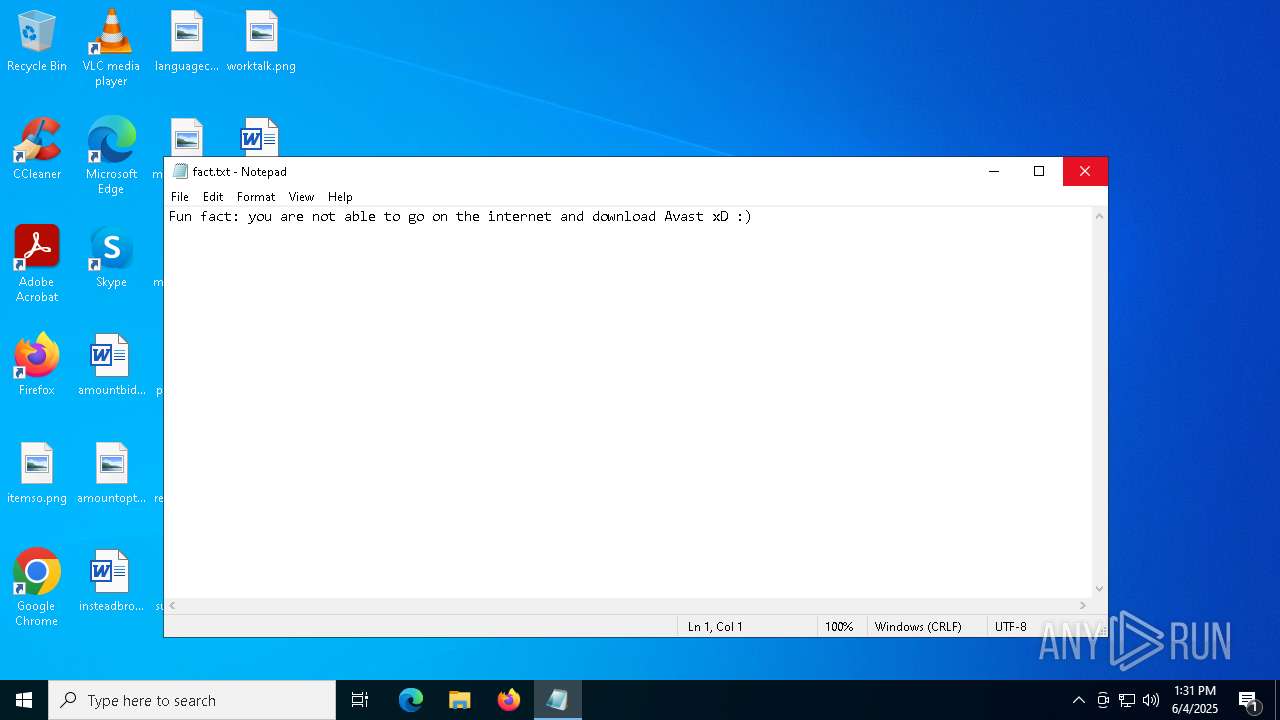
| 6584 | cmd.exe | C:\Users\admin\Desktop\fact.txt | text | |
MD5:9DE50E6853B31841492A8AF889A8508E | SHA256:5A68D17D4E00B254B0D2C1C18D96B7FFB79E726F1D5EF61C28A21C8D70F3F02B | |||
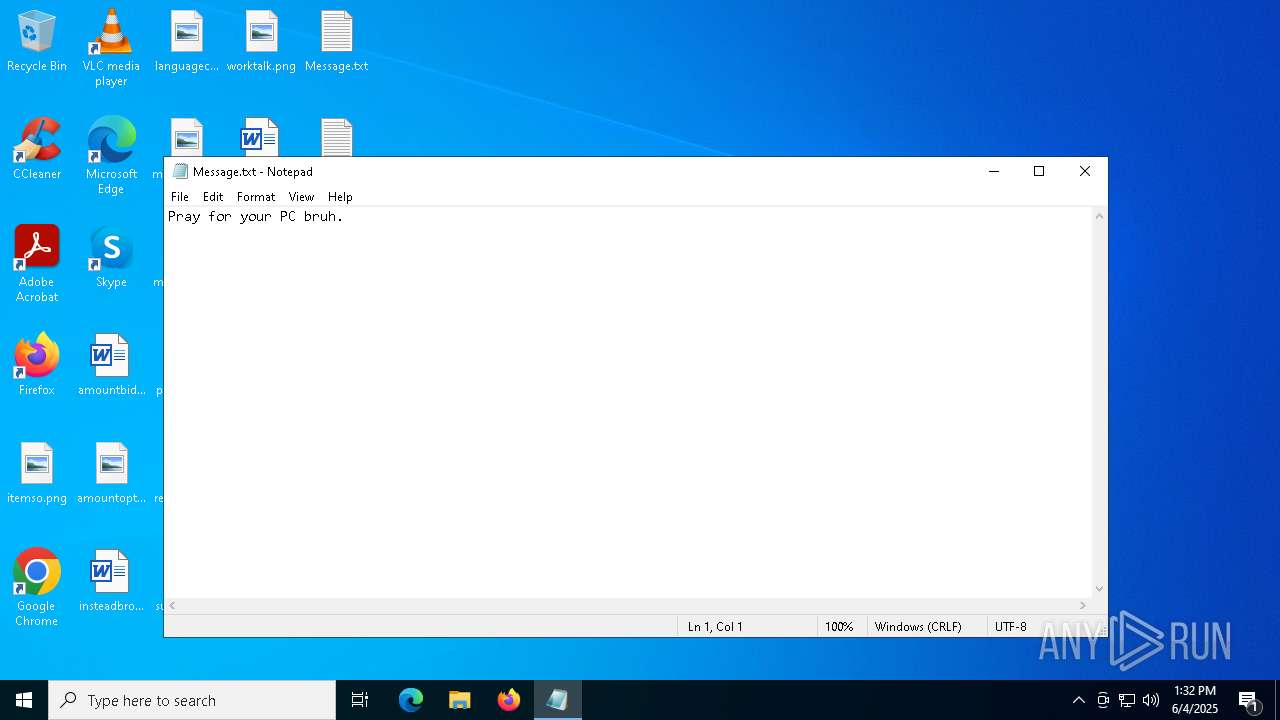
| 6584 | cmd.exe | C:\Users\admin\Desktop\Message.txt | text | |
MD5:CC16104498AA0CA0ECFE21B84C1362DB | SHA256:AA6B026D7DDED2C607263CDACE9CBC10B1B9DCBE5DFF5BC71C736301584B89FC | |||
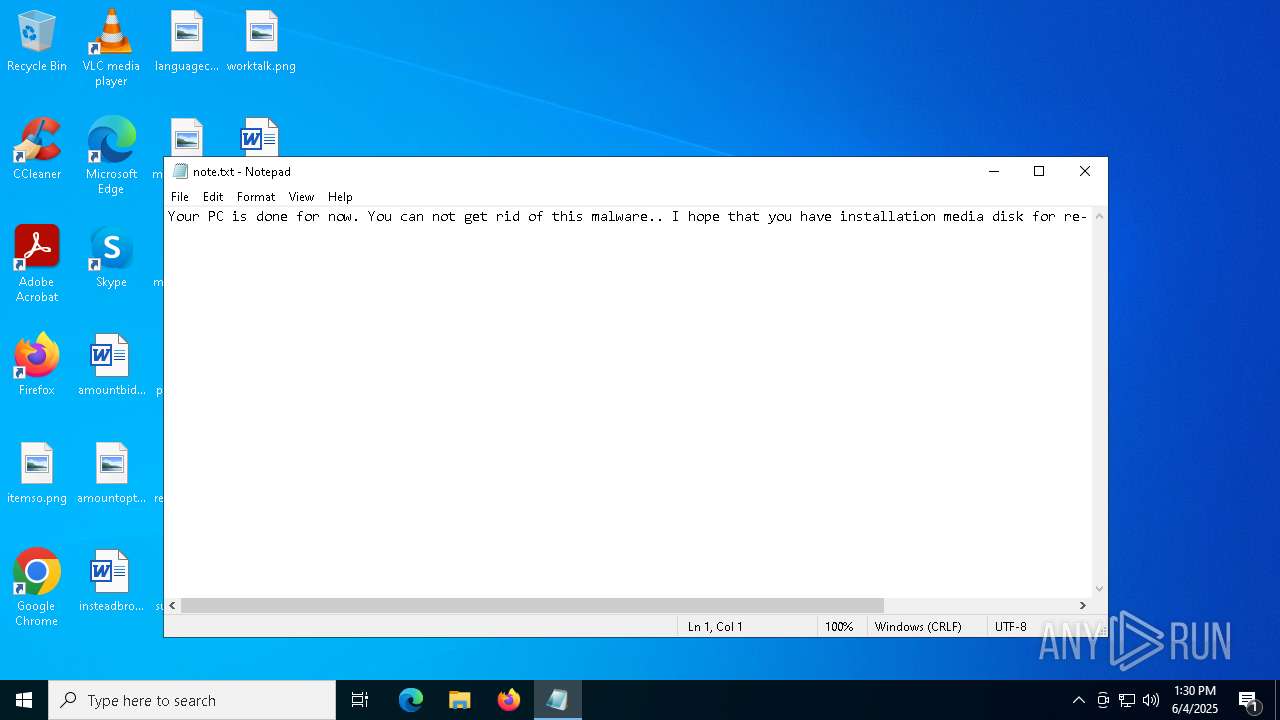
| 6584 | cmd.exe | C:\Users\admin\Desktop\note.txt | text | |
MD5:677B1CAECC3C84A180B7F2CD3B11A19D | SHA256:06C71D43C68DFAE78D6F8639A7067FEA4D41F9C36A7DF65D0AF7A7E4CAA29B1B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
34
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3112 | OfficeClickToRun.exe | GET | 200 | 23.63.118.230:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2908 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2908 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 20.190.160.128:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2292 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
3812 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.160.64:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
8036 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |