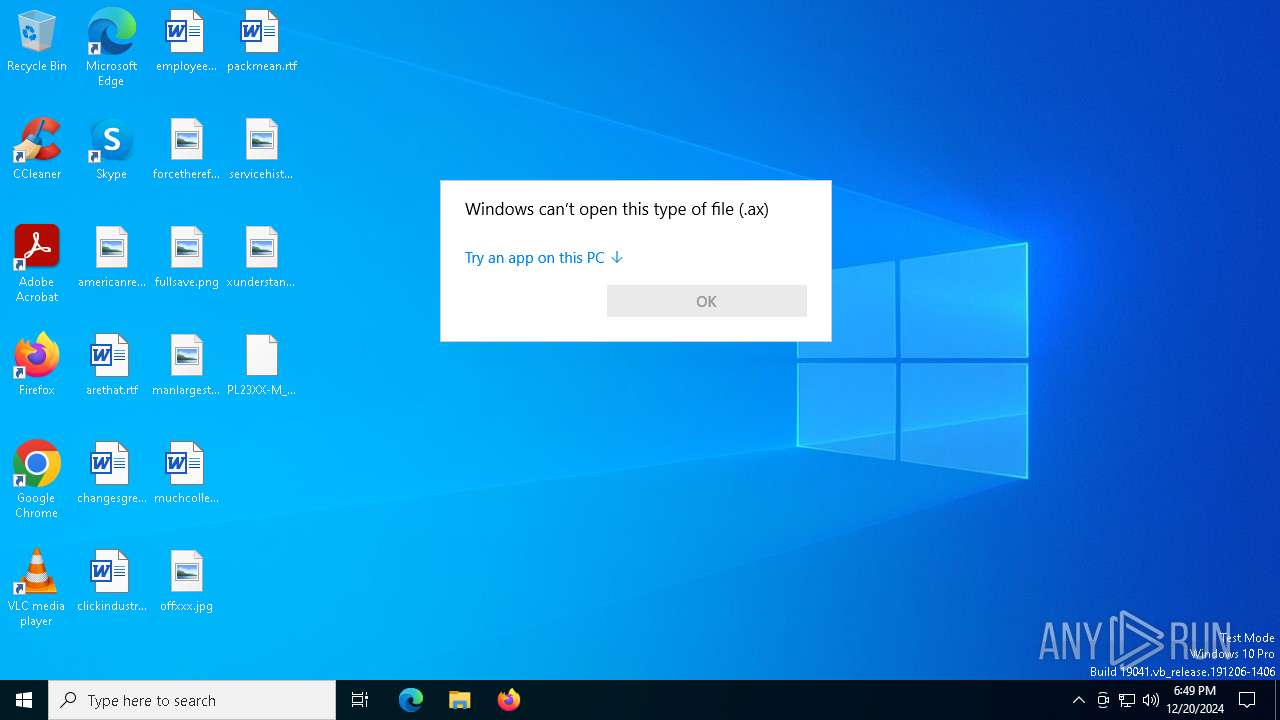
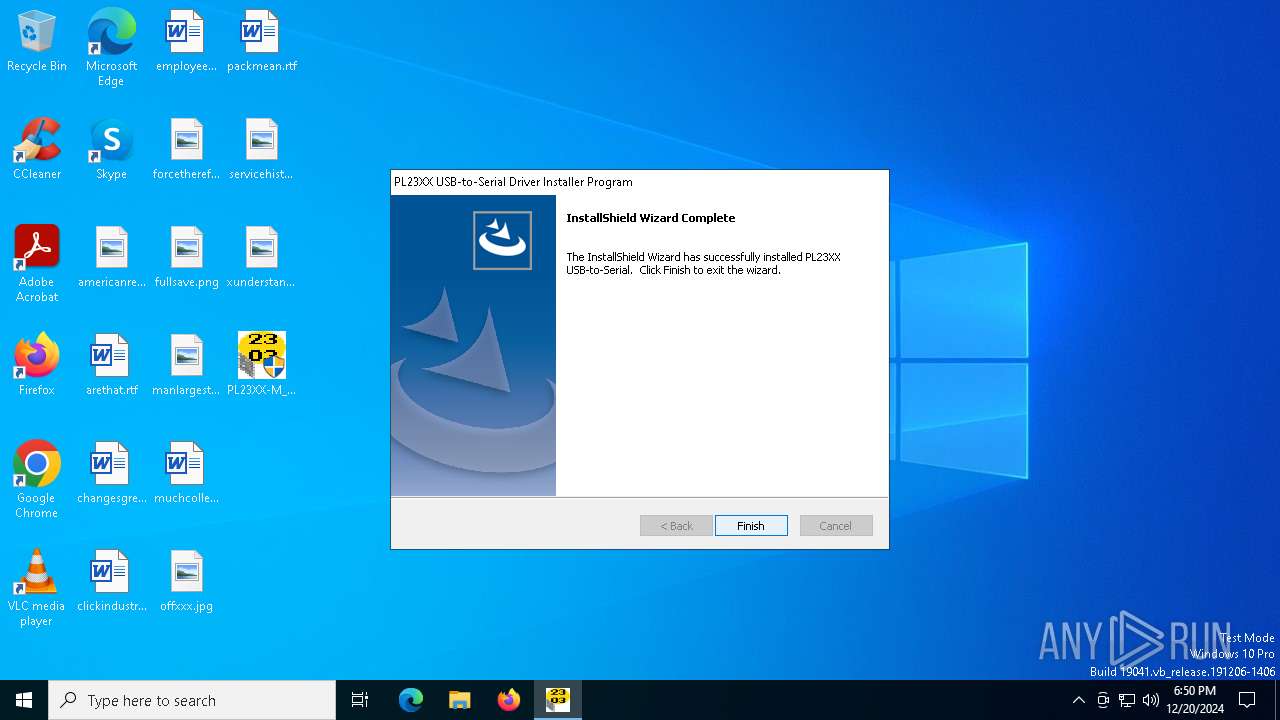
| File name: | PL23XX-M_LogoDriver_Setup_v401_20220225.exe |
| Full analysis: | https://app.any.run/tasks/529c93ff-9cf4-4617-925a-5b652fb78b36 |
| Verdict: | Malicious activity |
| Analysis date: | December 20, 2024, 18:49:43 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 1647C6E067DB2CB2C803277FE5F701BC |
| SHA1: | D9CDFBE7BAD0EA7FEFAF1836EBF6F716237A8AEF |
| SHA256: | 72E5C709A937AF1CF6F2ADF101453195288DA4BA598817DD682B0CC70C257CDB |
| SSDEEP: | 98304:wgMplFQm5Tf+S+PY6httnCGmY3mM+1BqQFA5b+xA242gFaEXvdfp7Mo2+r7mjbxU:0ns4r73HSwVqSyb |
MALICIOUS
Executing a file with an untrusted certificate
- dpinst64.exe (PID: 6836)
SUSPICIOUS
Executable content was dropped or overwritten
- PL23XX-M_LogoDriver_Setup_v401_20220225.exe (PID: 5748)
- PL23XX-M_LogoDriver_Setup_v401_20220225.exe (PID: 4980)
- dpinst64.exe (PID: 6836)
- drvinst.exe (PID: 6004)
- drvinst.exe (PID: 3532)
Process drops legitimate windows executable
- PL23XX-M_LogoDriver_Setup_v401_20220225.exe (PID: 5748)
Searches for installed software
- dllhost.exe (PID: 3608)
Creates a software uninstall entry
- PL23XX-M_LogoDriver_Setup_v401_20220225.exe (PID: 5748)
Starts a Microsoft application from unusual location
- dpinst64.exe (PID: 6836)
Executes as Windows Service
- VSSVC.exe (PID: 4392)
Drops a system driver (possible attempt to evade defenses)
- drvinst.exe (PID: 6004)
- PL23XX-M_LogoDriver_Setup_v401_20220225.exe (PID: 5748)
- dpinst64.exe (PID: 6836)
- drvinst.exe (PID: 3532)
Creates files in the driver directory
- drvinst.exe (PID: 3532)
Checks Windows Trust Settings
- drvinst.exe (PID: 3532)
- drvinst.exe (PID: 6004)
Starts itself from another location
- PL23XX-M_LogoDriver_Setup_v401_20220225.exe (PID: 4980)
INFO
The sample compiled with english language support
- OpenWith.exe (PID: 6676)
- PL23XX-M_LogoDriver_Setup_v401_20220225.exe (PID: 4980)
- drvinst.exe (PID: 6004)
- dpinst64.exe (PID: 6836)
- drvinst.exe (PID: 3532)
- PL23XX-M_LogoDriver_Setup_v401_20220225.exe (PID: 5748)
Checks supported languages
- SearchApp.exe (PID: 5064)
- ISBEW64.exe (PID: 4824)
- ISBEW64.exe (PID: 5792)
- PL23XX-M_LogoDriver_Setup_v401_20220225.exe (PID: 4980)
- ISBEW64.exe (PID: 6176)
- dpinst64.exe (PID: 6836)
- ISBEW64.exe (PID: 6204)
- ISBEW64.exe (PID: 6240)
- drvinst.exe (PID: 6004)
- drvinst.exe (PID: 3532)
- PL23XX-M_LogoDriver_Setup_v401_20220225.exe (PID: 5748)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 6676)
Manual execution by a user
- PL23XX-M_LogoDriver_Setup_v401_20220225.exe (PID: 5572)
- PL23XX-M_LogoDriver_Setup_v401_20220225.exe (PID: 4980)
Create files in a temporary directory
- PL23XX-M_LogoDriver_Setup_v401_20220225.exe (PID: 4980)
- dpinst64.exe (PID: 6836)
- PL23XX-M_LogoDriver_Setup_v401_20220225.exe (PID: 5748)
The sample compiled with arabic language support
- PL23XX-M_LogoDriver_Setup_v401_20220225.exe (PID: 5748)
Creates files in the program directory
- PL23XX-M_LogoDriver_Setup_v401_20220225.exe (PID: 5748)
Manages system restore points
- SrTasks.exe (PID: 5300)
Reads the machine GUID from the registry
- drvinst.exe (PID: 6004)
- drvinst.exe (PID: 3532)
- SearchApp.exe (PID: 5064)
The sample compiled with chinese language support
- drvinst.exe (PID: 6004)
- drvinst.exe (PID: 3532)
- dpinst64.exe (PID: 6836)
- PL23XX-M_LogoDriver_Setup_v401_20220225.exe (PID: 5748)
Reads the software policy settings
- drvinst.exe (PID: 6004)
- drvinst.exe (PID: 3532)
Reads the computer name
- drvinst.exe (PID: 3532)
- ISBEW64.exe (PID: 5792)
Process checks computer location settings
- SearchApp.exe (PID: 5064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .ax | | | DirectShow filter (55.8) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (7.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.8) |
| .exe | | | Win32 Executable (generic) (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:12:14 19:01:46+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 438784 |
| InitializedDataSize: | 516608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x437a7 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.0.0.0 |
| ProductVersionNumber: | 4.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Prolific |
| FileDescription: | InstallScript Setup Launcher Unicode |
| FileVersion: | 4.0.0 |
| InternalName: | Setup |
| LegalCopyright: | Copyright (c) 2021 Flexera. All Rights Reserved. |
| OriginalFileName: | PL23XX-M_LogoDriver_Setup_401_20220225.exe |
| ProductName: | PL2303 USB-to-Serial |
| ProductVersion: | 4.0.0 |
| InternalBuildNumber: | 203988 |
| ISInternalVersion: | 27.0.122 |
| ISInternalDescription: | InstallScript Setup Launcher Unicode |
Total processes
152
Monitored processes
20
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2092 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3532 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{b5319b7e-3494-574b-85c7-40589185f1bf}\ser2pl.inf" "9" "4b3a911ef" "00000000000001DC" "WinSta0\Default" "00000000000001E4" "208" "c:\users\admin\appdata\local\temp\{ebf2125f-fc66-4d9c-a061-5700f983bb2a}\{618d450a-b26a-4cb2-abca-f59c209b312e}\vista" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3608 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4392 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4824 | C:\Users\admin\AppData\Local\Temp\{EBF2125F-FC66-4D9C-A061-5700F983BB2A}\ISBEW64.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{9BCD175F-8E83-4875-A9A8-28A930661C01} | C:\Users\admin\AppData\Local\Temp\{EBF2125F-FC66-4D9C-A061-5700F983BB2A}\ISBEW64.exe | — | PL23XX-M_LogoDriver_Setup_v401_20220225.exe | |||||||||||
User: admin Company: Flexera Integrity Level: HIGH Description: InstallShield (R) 64-bit Setup Engine Exit code: 0 Version: 27.0.122 Modules
| |||||||||||||||
| 4980 | "C:\Users\admin\Desktop\PL23XX-M_LogoDriver_Setup_v401_20220225.exe" | C:\Users\admin\Desktop\PL23XX-M_LogoDriver_Setup_v401_20220225.exe | explorer.exe | ||||||||||||
User: admin Company: Prolific Integrity Level: HIGH Description: InstallScript Setup Launcher Unicode Exit code: 0 Version: 4.0.0 Modules
| |||||||||||||||
| 5064 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5300 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5572 | "C:\Users\admin\Desktop\PL23XX-M_LogoDriver_Setup_v401_20220225.exe" | C:\Users\admin\Desktop\PL23XX-M_LogoDriver_Setup_v401_20220225.exe | — | explorer.exe | |||||||||||
User: admin Company: Prolific Integrity Level: MEDIUM Description: InstallScript Setup Launcher Unicode Exit code: 3221226540 Version: 4.0.0 Modules
| |||||||||||||||
| 5748 | C:\Users\admin\AppData\Local\Temp\{D25FC38A-7ABC-46E7-8C1D-D25C2E86147A}\PL23XX-M_LogoDriver_Setup_v401_20220225.exe -package:"C:\Users\admin\Desktop\PL23XX-M_LogoDriver_Setup_v401_20220225.exe" -no_selfdeleter -IS_temp -media_path:"C:\Users\admin\AppData\Local\Temp\{D25FC38A-7ABC-46E7-8C1D-D25C2E86147A}\Disk1\" -tempdisk1folder:"C:\Users\admin\AppData\Local\Temp\{D25FC38A-7ABC-46E7-8C1D-D25C2E86147A}\" -IS_OriginalLauncher:"C:\Users\admin\AppData\Local\Temp\{D25FC38A-7ABC-46E7-8C1D-D25C2E86147A}\Disk1\PL23XX-M_LogoDriver_Setup_v401_20220225.exe" | C:\Users\admin\AppData\Local\Temp\{D25FC38A-7ABC-46E7-8C1D-D25C2E86147A}\PL23XX-M_LogoDriver_Setup_v401_20220225.exe | PL23XX-M_LogoDriver_Setup_v401_20220225.exe | ||||||||||||
User: admin Company: Prolific Integrity Level: HIGH Description: InstallScript Setup Launcher Unicode Exit code: 0 Version: 4.0.0 Modules
| |||||||||||||||
Total events
15 897
Read events
15 571
Write events
295
Delete events
31
Modification events
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\Internet Explorer\DOMStorage\bing.com |
| Operation: | write | Name: | Total |
Value: 929 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\ConstraintIndex |
| Operation: | write | Name: | CurrentConstraintIndexCabPath |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C005000610063006B0061006700650073005C004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E005300650061007200630068005F006300770035006E003100680032007400780079006500770079005C004C006F00630061006C00530074006100740065005C0043006F006E00730074007200610069006E00740049006E006400650078005C0049006E007000750074005F007B00380033003200620036003800640032002D0037006600650032002D0034006500370031002D0061003300610064002D003200360031003600360062003600350036006500630036007D00000082F400FA0F53DB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\AppsConstraintIndex |
| Operation: | write | Name: | LatestConstraintIndexFolder |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C005000610063006B0061006700650073005C004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E005300650061007200630068005F006300770035006E003100680032007400780079006500770079005C004C006F00630061006C00530074006100740065005C0043006F006E00730074007200610069006E00740049006E006400650078005C0041007000700073005F007B00370066003200330061006500630032002D0036003100650037002D0034006100640036002D0062003400650038002D003400320033003500370032003200360065003200330038007D00000082F400FA0F53DB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\AppsConstraintIndex |
| Operation: | write | Name: | LastConstraintIndexBuildCompleted |
Value: 8D2303FA0F53DB0182F400FA0F53DB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Microsoft.Windows.Search_cw5n1h2txyewy\AppsConstraintIndex |
| Operation: | write | Name: | CurrentConstraintIndexCabPath |
Value: C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Input_{832b68d2-7fe2-4e71-a3ad-26166b656ec6} | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Microsoft.Windows.Search_cw5n1h2txyewy\AppsConstraintIndex |
| Operation: | write | Name: | LatestConstraintIndexFolder |
Value: C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{7f23aec2-61e7-4ad6-b4e8-42357226e238} | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | SafeSearchMode |
Value: 1 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Microsoft.Windows.Search_cw5n1h2txyewy\AppsConstraintIndex |
| Operation: | write | Name: | IndexedLanguage |
Value: en-US | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\AppIndexer |
| Operation: | write | Name: | LatestCacheFileName |
Value: 410070007000430061006300680065003100330033003700390031003900340031003900320037003700360038003600350036002E0074007800740000004A5903FA0F53DB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\AppIndexer |
| Operation: | write | Name: | InstalledWin32AppsRevision |
Value: 7B00440042003700460044003000320033002D0044003700330030002D0034003500370042002D0038003000310032002D003700310034003400300041003600320044004100360046007D0000004A5903FA0F53DB01 | |||
Executable files
86
Suspicious files
146
Text files
195
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{7f23aec2-61e7-4ad6-b4e8-42357226e238}\Apps.ft | binary | |
MD5:AB5CF5D309581951ACE7978FF8DF0FF0 | SHA256:CA45CAA7DE38CB805EC43EDC8B9332E1E95124A27FBB6E5BD3DDD5E8A526AFC7 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{7f23aec2-61e7-4ad6-b4e8-42357226e238}\0.2.filtertrie.intermediate.txt | text | |
MD5:C204E9FAAF8565AD333828BEFF2D786E | SHA256:D65B6A3BF11A27A1CED1F7E98082246E40CF01289FD47FE4A5ED46C221F2F73F | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{7f23aec2-61e7-4ad6-b4e8-42357226e238}\0.1.filtertrie.intermediate.txt | text | |
MD5:34BD1DFB9F72CF4F86E6DF6DA0A9E49A | SHA256:8E1E6A3D56796A245D0C7B0849548932FEE803BBDB03F6E289495830E017F14C | |||
| 4980 | PL23XX-M_LogoDriver_Setup_v401_20220225.exe | C:\Users\admin\AppData\Local\Temp\{D25FC38A-7ABC-46E7-8C1D-D25C2E86147A}\Disk1\ISSetup.dll | executable | |
MD5:825682254C5A8FEF67E399649AD3E043 | SHA256:E94778284BC6E5CAA2BE2A2BA7D8B9AD993D62FBECAC3F4DC71D691D0FA232FE | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\Internet Explorer\DOMStore\ZWUI0EBX\www.bing[1].xml | text | |
MD5:EC0D083B08FCEBA6AE4AC860536D8F59 | SHA256:5E410D2FFFF6C09D8F256AEA55CE8890D15B8EBAB740BF181B58724848DC7430 | |||
| 4980 | PL23XX-M_LogoDriver_Setup_v401_20220225.exe | C:\Users\admin\AppData\Local\Temp\{D25FC38A-7ABC-46E7-8C1D-D25C2E86147A}\Disk1\setup.iss | binary | |
MD5:6B4F84B03AF904494FFD314932077C47 | SHA256:8091F714475C8BE1679079D8AC0221ACCB0046B444667496A3317826C580CD2E | |||
| 4980 | PL23XX-M_LogoDriver_Setup_v401_20220225.exe | C:\Users\admin\AppData\Local\Temp\{D25FC38A-7ABC-46E7-8C1D-D25C2E86147A}\Disk1\0x0409.ini | text | |
MD5:A108F0030A2CDA00405281014F897241 | SHA256:8B76DF0FFC9A226B532B60936765B852B89780C6E475C152F7C320E085E43948 | |||
| 4980 | PL23XX-M_LogoDriver_Setup_v401_20220225.exe | C:\Users\admin\AppData\Local\Temp\{D25FC38A-7ABC-46E7-8C1D-D25C2E86147A}\Disk1\setup.exe | executable | |
MD5:2DD048D89EDCE1F0C4C09AC7B09CD1FC | SHA256:499BAB8E29DE600BCEA5B76EF4A8339223F60871391B359C6F133F826C6DD4C3 | |||
| 4980 | PL23XX-M_LogoDriver_Setup_v401_20220225.exe | C:\Users\admin\AppData\Local\Temp\{D25FC38A-7ABC-46E7-8C1D-D25C2E86147A}\Disk1\setup.inx | binary | |
MD5:F4B7D051A385084A1DA269FDC604663F | SHA256:CF44296845EF05900BF8D1CADE2A3880D979C6DFDD321ED42026F2597D4C3143 | |||
| 4980 | PL23XX-M_LogoDriver_Setup_v401_20220225.exe | C:\Users\admin\AppData\Local\Temp\{D25FC38A-7ABC-46E7-8C1D-D25C2E86147A}\Disk1\data1.cab | compressed | |
MD5:39EDE6A90CEAA3A0588DD2004D515D3C | SHA256:0901596F28D184C6B0A8889609BA2C69B9997AE172DB05C27CBEF58A3A5ADC58 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
56
DNS requests
31
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6292 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6292 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6440 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 104.126.37.130:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1076 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| unknown |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |