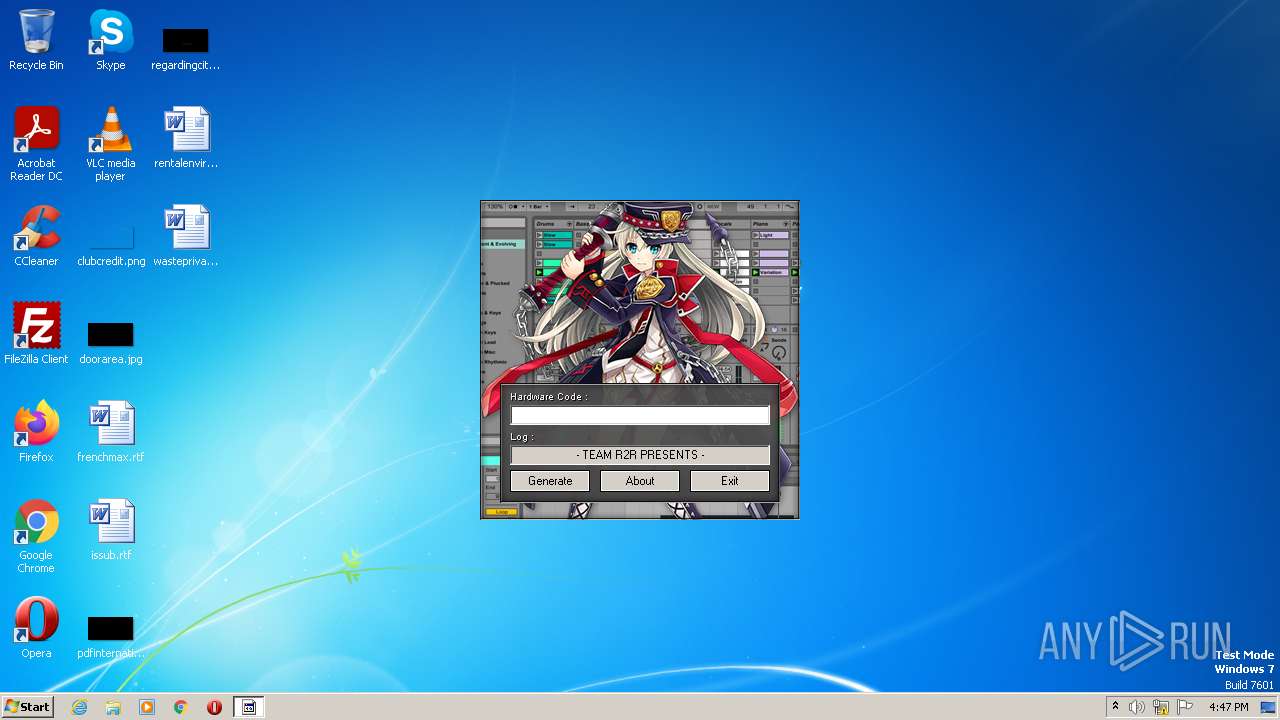
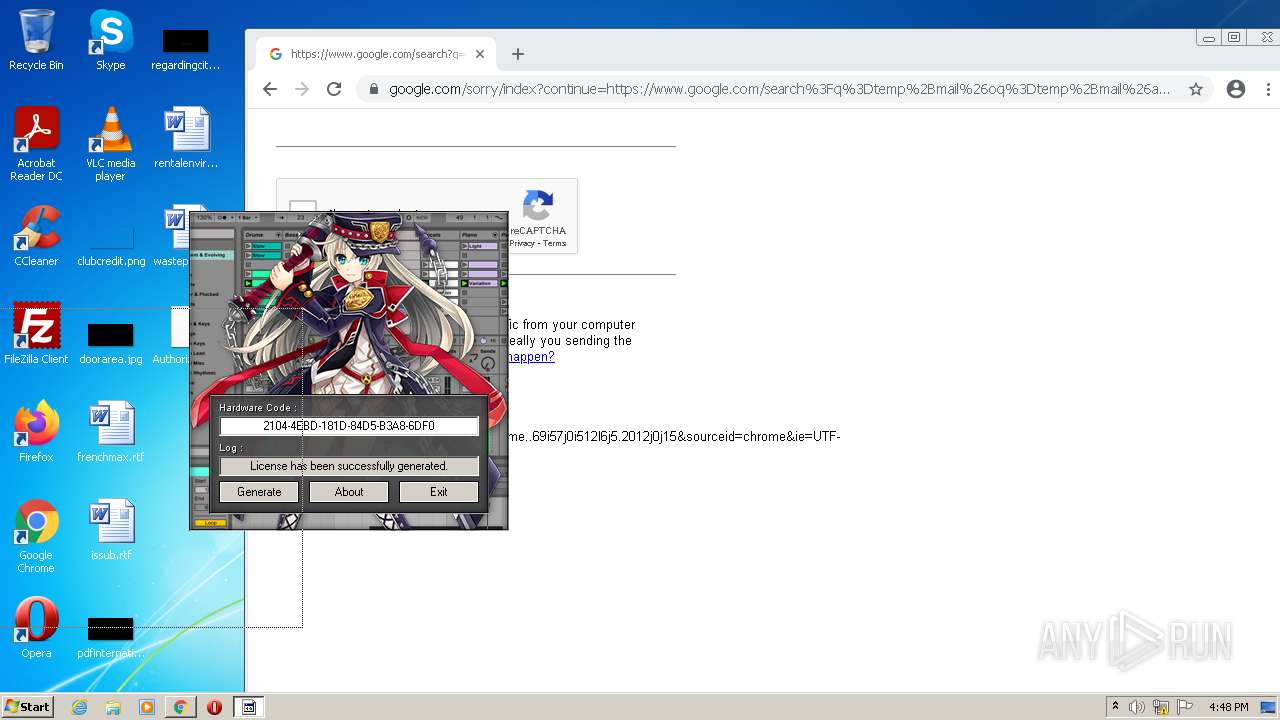
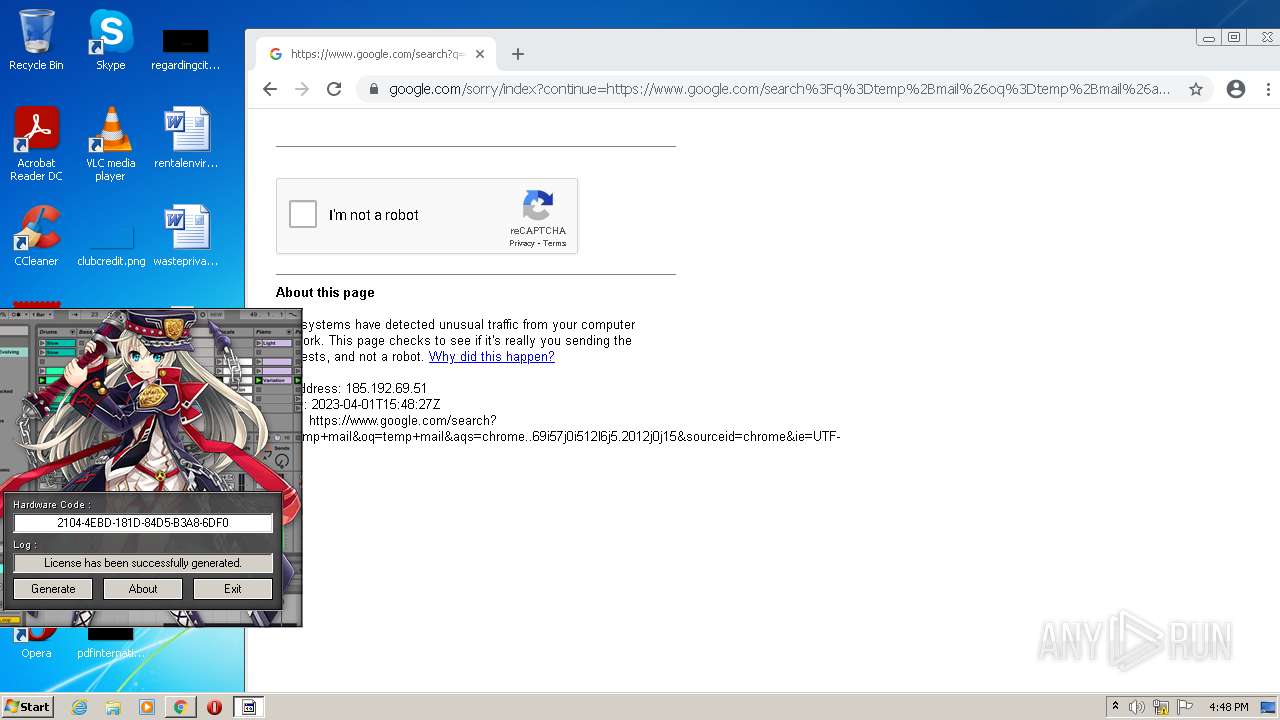
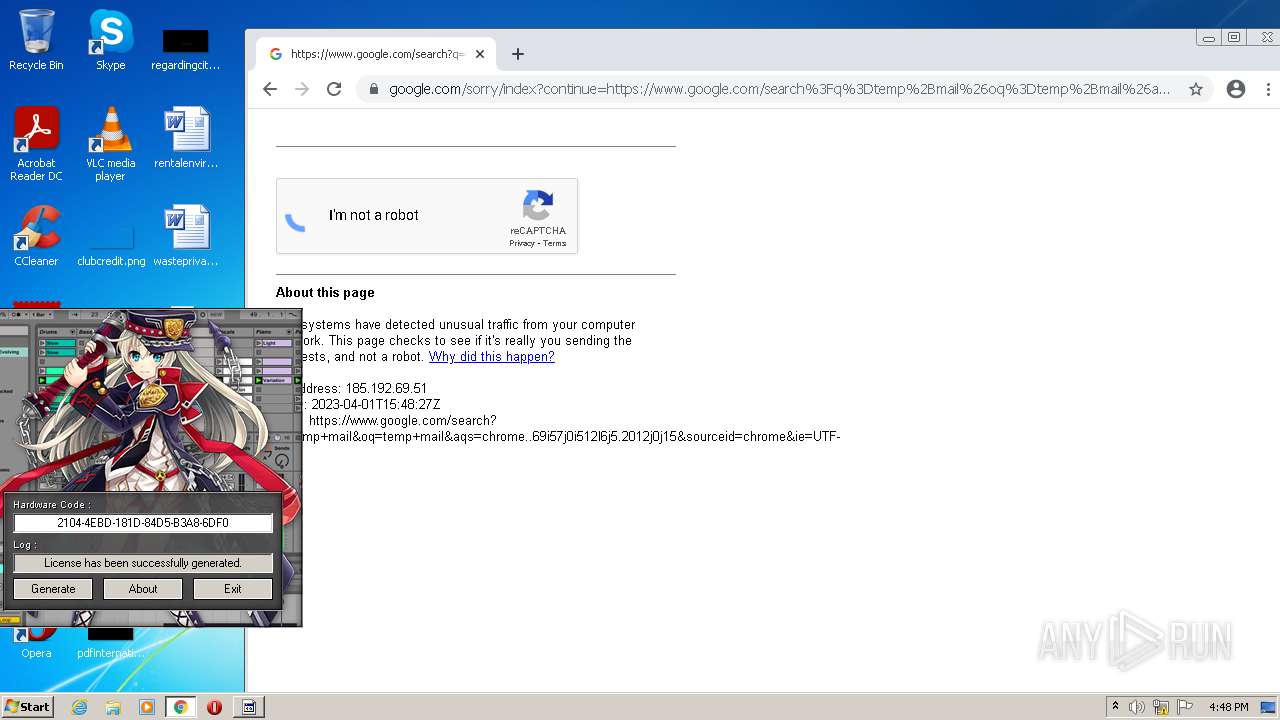
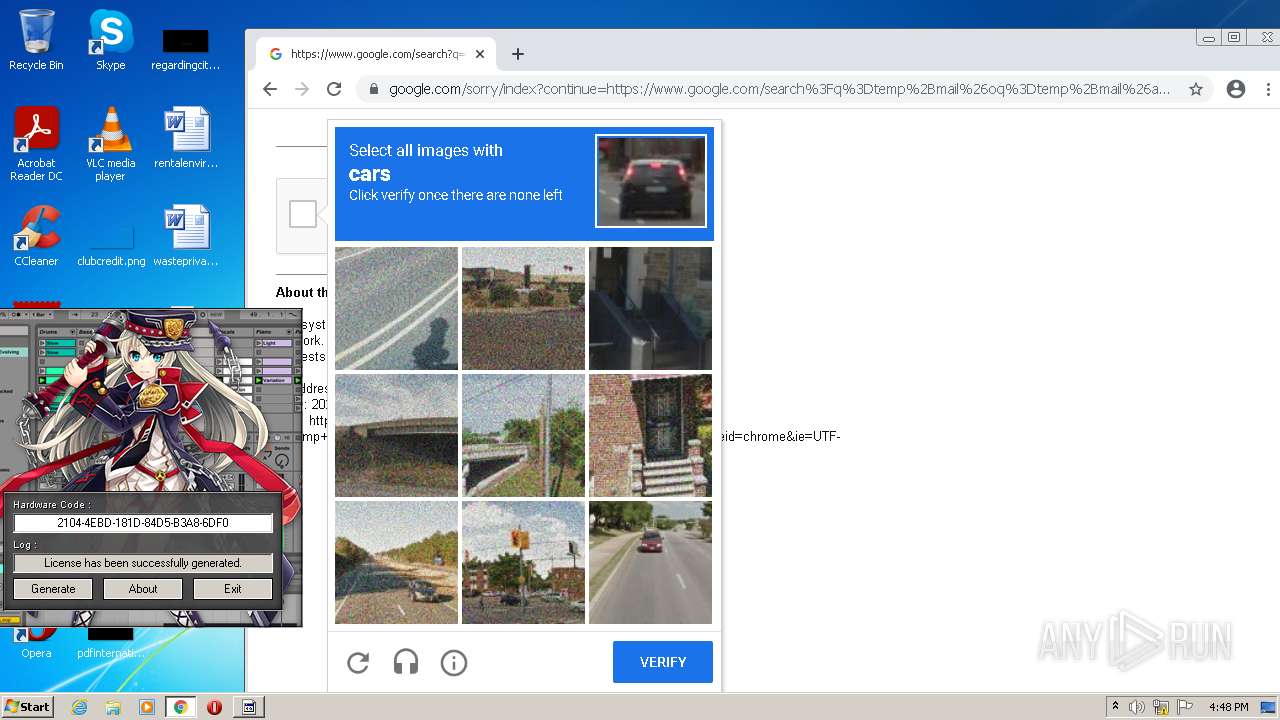
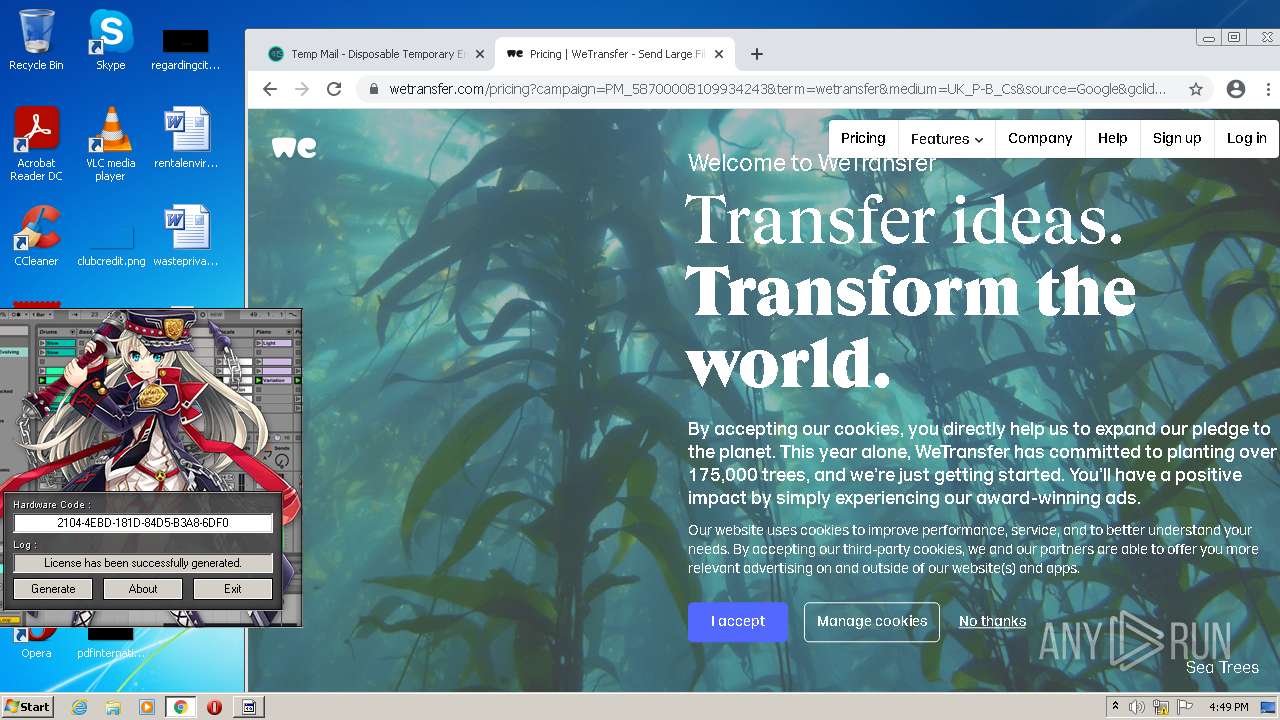
| File name: | Ableton_KeyGen.exe |
| Full analysis: | https://app.any.run/tasks/3f2d2b09-e186-4193-a26f-bbf8e8c8fe70 |
| Verdict: | Malicious activity |
| Analysis date: | April 01, 2023, 15:47:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 5137F6C1B6FEC54E3C4FCE6261905DD6 |
| SHA1: | 2ACFA6961576086CB34376222CCA49027B77871D |
| SHA256: | 72C96F7E2F4823BB9F28944C96AA1B737BE20EDD52CA97B699085D3498E4AB74 |
| SSDEEP: | 24576:scLyLVBj7bonifxHi8nnM6+uRCy/4cZTKRZiKx9j1zp9KtyUHW:sAOsif1TMC1wcZTK+KZzxUHW |
MALICIOUS
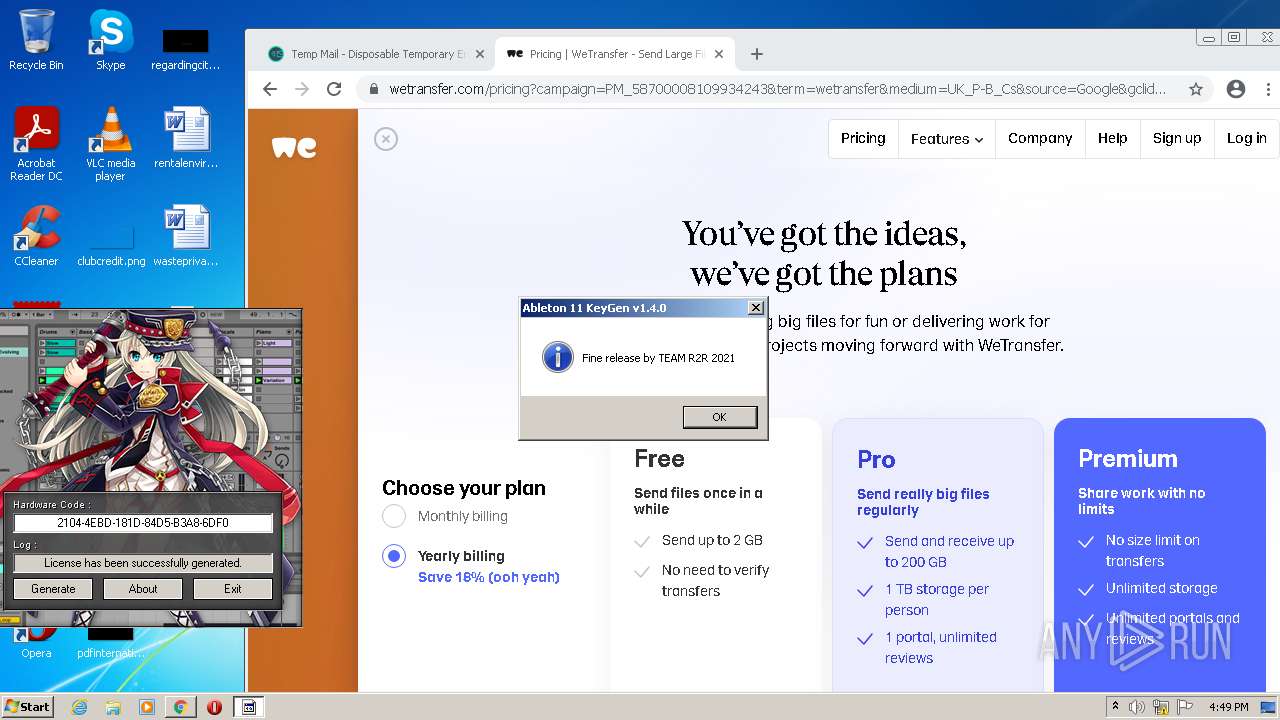
Application was dropped or rewritten from another process
- keygen.exe (PID: 3520)
SUSPICIOUS
Executable content was dropped or overwritten
- Ableton_KeyGen.exe (PID: 3368)
Reads the Internet Settings
- keygen.exe (PID: 3520)
INFO
Reads the computer name
- Ableton_KeyGen.exe (PID: 3368)
- keygen.exe (PID: 3520)
Checks supported languages
- Ableton_KeyGen.exe (PID: 3368)
- keygen.exe (PID: 3520)
The process checks LSA protection
- keygen.exe (PID: 3520)
- Ableton_KeyGen.exe (PID: 3368)
Create files in a temporary directory
- Ableton_KeyGen.exe (PID: 3368)
- chrome.exe (PID: 2416)
- keygen.exe (PID: 3520)
- chrome.exe (PID: 2860)
Reads the machine GUID from the registry
- keygen.exe (PID: 3520)
Manual execution by a user
- chrome.exe (PID: 2860)
Application launched itself
- chrome.exe (PID: 2860)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| Subsystem: | Windows GUI |
|---|---|
| SubsystemVersion: | 4 |
| ImageVersion: | 6 |
| OSVersion: | 4 |
| EntryPoint: | 0x3328 |
| UninitializedDataSize: | 1024 |
| InitializedDataSize: | 118784 |
| CodeSize: | 25088 |
| LinkerVersion: | 6 |
| PEType: | PE32 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| TimeStamp: | 2018:01:30 03:57:38+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 30-Jan-2018 03:57:38 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 30-Jan-2018 03:57:38 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00006077 | 0x00006200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.40397 |
.rdata | 0x00008000 | 0x00001248 | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.04426 |
.data | 0x0000A000 | 0x0001A838 | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.22445 |
.ndata | 0x00025000 | 0x00008000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x0002D000 | 0x00022910 | 0x00022A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.06462 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.28733 | 841 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 7.92764 | 54264 | UNKNOWN | English - United States | RT_ICON |
3 | 4.51849 | 9640 | UNKNOWN | English - United States | RT_ICON |
4 | 4.75617 | 4264 | UNKNOWN | English - United States | RT_ICON |
5 | 4.93004 | 2440 | UNKNOWN | English - United States | RT_ICON |
6 | 5.08765 | 1128 | UNKNOWN | English - United States | RT_ICON |
103 | 2.8213 | 90 | UNKNOWN | English - United States | RT_GROUP_ICON |
105 | 2.66174 | 256 | UNKNOWN | English - United States | RT_DIALOG |
106 | 2.88094 | 284 | UNKNOWN | English - United States | RT_DIALOG |
111 | 2.48825 | 96 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
133
Monitored processes
93
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1056,12660695627737036496,11259929299428881710,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=82 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5972 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 312 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1056,12660695627737036496,11259929299428881710,131072 --enable-features=PasswordImport --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1556 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 568 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1056,12660695627737036496,11259929299428881710,131072 --enable-features=PasswordImport --lang=en-US --instant-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1620 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 692 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1056,12660695627737036496,11259929299428881710,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=40 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3944 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1060 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1056,12660695627737036496,11259929299428881710,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=76 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5076 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1124 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1056,12660695627737036496,11259929299428881710,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2164 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1204 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1056,12660695627737036496,11259929299428881710,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=23 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2104 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1236 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1056,12660695627737036496,11259929299428881710,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=57 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=6080 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1240 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1056,12660695627737036496,11259929299428881710,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=53 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5008 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1244 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1056,12660695627737036496,11259929299428881710,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=4400 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
56 756
Read events
56 340
Write events
396
Delete events
20
Modification events
| (PID) Process: | (3520) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3520) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0C000000000000000B00000001000000020000000D00000007000000060000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3520) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3520) keygen.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRU |
| Operation: | write | Name: | MRUListEx |
Value: 020000000100000000000000FFFFFFFF | |||
| (PID) Process: | (3520) keygen.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\* |
| Operation: | write | Name: | MRUListEx |
Value: 06000000050000000400000003000000020000000100000000000000FFFFFFFF | |||
| (PID) Process: | (3520) keygen.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | delete value | Name: | 4 |
Value: 6B0065007900670065006E002E006500780065000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000000000000 | |||
| (PID) Process: | (3520) keygen.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | delete value | Name: | 4 |
Value: 6B0065007900670065006E002E0065007800650000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000E0010000BE000000600400009E020000000000000000000000000000000000000100000000000000 | |||
| (PID) Process: | (3520) keygen.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | write | Name: | MRUListEx |
Value: 00000000030000000200000001000000FFFFFFFF | |||
| (PID) Process: | (3520) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\82\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | Mode |
Value: 6 | |||
| (PID) Process: | (3520) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\82\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | LogicalViewMode |
Value: 2 | |||
Executable files
6
Suspicious files
684
Text files
500
Unknown types
98
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2860 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-64285239-B2C.pma | — | |
MD5:— | SHA256:— | |||
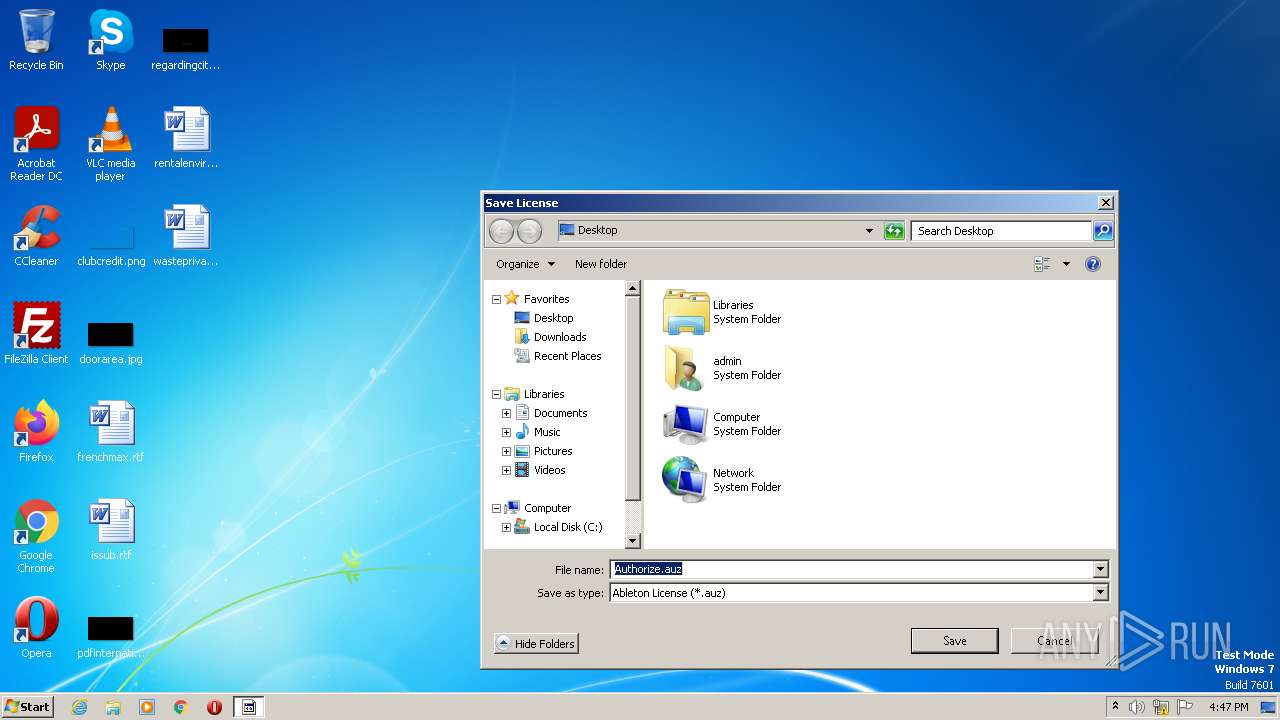
| 3520 | keygen.exe | C:\Users\admin\Desktop\Authorize.auz | text | |
MD5:— | SHA256:— | |||
| 2860 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\e23f554e-4ea4-414c-b803-20801f07264e.tmp | text | |
MD5:— | SHA256:— | |||
| 2860 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:00046F773EFDD3C8F8F6D0F87A2B93DC | SHA256:593EDE11D17AF7F016828068BCA2E93CF240417563FB06DC8A579110AEF81731 | |||
| 3368 | Ableton_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\keygen.exe | executable | |
MD5:88FB2EFAEF130C7256BF703580A414A7 | SHA256:2EF24CB81741BCDCCE8FDAE0812ECB86A334B0A98160B4C068D2B59913C3896D | |||
| 2860 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 2860 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:5BD3C311F2136A7A88D3E197E55CF902 | SHA256:FA331915E1797E59979A3E4BCC2BD0D3DEAA039B94D4DB992BE251FD02A224B9 | |||
| 3368 | Ableton_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\bgm.xm | xm | |
MD5:EAC249A6CBD92E5A744F1921261B4134 | SHA256:9AE311E672F224A27350DD37CCE871187377531741DF048082B9CB680CD12882 | |||
| 3368 | Ableton_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\BASSMOD.dll | executable | |
MD5:E4EC57E8508C5C4040383EBE6D367928 | SHA256:8AD9E47693E292F381DA42DDC13724A3063040E51C26F4CA8E1F8E2F1DDD547F | |||
| 3368 | Ableton_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\R2RLIVE.dll | executable | |
MD5:4CE264468BE29F6504EB745D11AA1D5C | SHA256:33339FD831B14D39514593CF7494BA1985DF6E32DBEF166B70D94EBAAD78CD3B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
284
DNS requests
203
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
860 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/jewvegtcs2qdew3nlzz4kvsjqm_9.44.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.44.0_all_pywouuhjzu3khiqqvvfs2jt53q.crx3 | US | — | — | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/jewvegtcs2qdew3nlzz4kvsjqm_9.44.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.44.0_all_pywouuhjzu3khiqqvvfs2jt53q.crx3 | US | binary | 8.36 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/jewvegtcs2qdew3nlzz4kvsjqm_9.44.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.44.0_all_pywouuhjzu3khiqqvvfs2jt53q.crx3 | US | binary | 9.15 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/jewvegtcs2qdew3nlzz4kvsjqm_9.44.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.44.0_all_pywouuhjzu3khiqqvvfs2jt53q.crx3 | US | binary | 7.91 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/jewvegtcs2qdew3nlzz4kvsjqm_9.44.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.44.0_all_pywouuhjzu3khiqqvvfs2jt53q.crx3 | US | binary | 9.25 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 9.84 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 34.2 Kb | whitelisted |
860 | svchost.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac3n3d6wycjs4wavg2t6kq4eghoq_7945/hfnkpimlhhgieaddgfemjhofmfblmnib_7945_all_ac62jxv5dg4l2uvidem4cyh4xyqa.crx3 | US | crx | 24.8 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 56.8 Kb | whitelisted |
860 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 7.91 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2416 | chrome.exe | 142.250.186.131:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
2416 | chrome.exe | 172.217.16.195:443 | update.googleapis.com | GOOGLE | US | whitelisted |
— | — | 34.104.35.123:80 | edgedl.me.gvt1.com | GOOGLE | US | whitelisted |
— | — | 142.250.186.110:443 | encrypted-tbn0.gstatic.com | GOOGLE | US | whitelisted |
— | — | 172.217.16.195:443 | update.googleapis.com | GOOGLE | US | whitelisted |
2416 | chrome.exe | 142.250.181.227:443 | www.gstatic.com | GOOGLE | US | whitelisted |
— | — | 142.250.186.161:443 | lh5.googleusercontent.com | GOOGLE | US | whitelisted |
— | — | 142.250.181.227:443 | www.gstatic.com | GOOGLE | US | whitelisted |
2416 | chrome.exe | 142.250.186.99:443 | fonts.gstatic.com | GOOGLE | US | whitelisted |
— | — | 142.250.186.99:443 | fonts.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| malicious |
clients2.google.com |
| whitelisted |
accounts.google.com |
| shared |
clients2.googleusercontent.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
edgedl.me.gvt1.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
lh5.googleusercontent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO Commonly Abused Content Delivery Network Domain in DNS Lookup (btloader .com) |
2416 | chrome.exe | Potentially Bad Traffic | ET INFO Observed Abused Content Delivery Network Domain (btloader .com in TLS SNI) |
— | — | Potentially Bad Traffic | ET INFO Commonly Abused Content Delivery Network Domain in DNS Lookup (btloader .com) |
2416 | chrome.exe | Potentially Bad Traffic | ET INFO Observed Abused Content Delivery Network Domain (btloader .com in TLS SNI) |
2416 | chrome.exe | Potentially Bad Traffic | ET INFO Observed Abused Content Delivery Network Domain (btloader .com in TLS SNI) |