| URL: | https://cos.na-ashburn.myqcloud.com/azgyruiazgeruysdfqgsqdfert-1316406552/hg5jsdf6q40f6qsd4f.html#/697671729956/8931854/2266042935321276/ramadankarim?od=1syvouttt6624debe83cf6.vz7517.S00mdrfs9yc25aw00t_xl1588.fs9yc.._xl.._xl._xl.fs9yc..._xl.YnY4eWotMzhuc3F0cQ==5x697l |
| Full analysis: | https://app.any.run/tasks/4a127d5d-ccf2-4684-95ed-305dac112486 |
| Verdict: | Malicious activity |
| Analysis date: | April 23, 2024, 04:15:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 84BE48679240882D7F7F79C34FF87F6E |
| SHA1: | 5628F94399EB6D30F2A0A129849C3DDC2DD4DAA5 |
| SHA256: | 72BD72D0582C8BE50DC27C9BC09278CABDBF5A7C3E28E19FFA3F13482E437ED3 |
| SSDEEP: | 6:2vIVHA1FcBLRUO7U7SgtEOlE/EqQI7Tv6f0H3EyPFK/2IjYYW:2MHR97UvtEwBYv6G0yNi2IjU |
MALICIOUS
PHISHING has been detected (SURICATA)
- iexplore.exe (PID: 2928)
SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 2032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
37
Monitored processes
2
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2032 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://cos.na-ashburn.myqcloud.com/azgyruiazgeruysdfqgsqdfert-1316406552/hg5jsdf6q40f6qsd4f.html#/697671729956/8931854/2266042935321276/ramadankarim?od=1syvouttt6624debe83cf6.vz7517.S00mdrfs9yc25aw00t_xl1588.fs9yc.._xl.._xl._xl.fs9yc..._xl.YnY4eWotMzhuc3F0cQ==5x697l" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2928 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2032 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
16 898
Read events
16 782
Write events
81
Delete events
35
Modification events
| (PID) Process: | (2032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31102260 | |||
| (PID) Process: | (2032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31102260 | |||
| (PID) Process: | (2032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
Executable files
0
Suspicious files
6
Text files
7
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\0DA515F703BB9B49479E8697ADB0B955_786387CC77858B88BA3234B304062475 | der | |
MD5:1D03412FE4559674F85564920B0D5BA0 | SHA256:651A41F90CA5492230385CC8DC01C8397103C69A8F7CBA46198865FFE0EFD53A | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\imagestore\f7ruq93\imagestore.dat | binary | |
MD5:17BDA84E837AAA4257114C9280B1DB58 | SHA256:C36BCF9CC79F7A4089E5777A2B44A77CA079661FF4553B7556BB47B4CE587484 | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\out[1].htm | html | |
MD5:28F1ED2679ECF29D64E0A395CD3BCE08 | SHA256:237089313BAE85FE371B5E6CF5A1256544E79957347F5B4CE04C8D26B7094CCC | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\favicon[2].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\hg5jsdf6q40f6qsd4f[1].htm | html | |
MD5:FCEE7B7A25ED69644ADC82AE4C996EE9 | SHA256:785CE161D9060F6C1749FBCE5100B935161E09DD4A3151CDE7152E13C586456B | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\out[1].htm | html | |
MD5:E15D282708C6E02E48986F3E07E816BB | SHA256:5E179CCA1531C387ED6839353D0F187D064ECECB8524F0BF9F1878FD08BB2219 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | der | |
MD5:C2532B80E88C04459E7343C228BAA34D | SHA256:D3869EBF9664381824049CE97805B1774F4B62485917EA96E9CFF0BA3AC55832 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\0DA515F703BB9B49479E8697ADB0B955_786387CC77858B88BA3234B304062475 | binary | |
MD5:658F46FDB113D2AEFEC1D1ABBEC943E8 | SHA256:6917AD8D2DF8E14F3223DCA33C6297979F73E4290E1F464C288764E95674F432 | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CF14D1855652602540DFCFECD21854DB_828FD49BEF8D67A75A56AC0EBB3FA8E5 | binary | |
MD5:25D51E5BCABC78C43361C47A933C12A4 | SHA256:764FC922244720FF12D52D396FAC47FEB4C8283F86D540F58CEBCA863B08091C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
19
DNS requests
13
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2928 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7f68a02ba6df2d36 | unknown | — | — | unknown |
2928 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?13701d01566341eb | unknown | — | — | unknown |
2928 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/rootr1/ME8wTTBLMEkwRzAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDkcHsQGaDFetObPhfan5 | unknown | — | — | unknown |
2928 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp2.globalsign.com/gsorganizationvalsha2g3/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBSVLM6m9XSaK2pXyc357yFJVjgNwQQUaIa4fXrZbUlrhy8YixU0bNe0eg4CDDFHk4Qi9KXJvsTh7w%3D%3D | unknown | — | — | unknown |
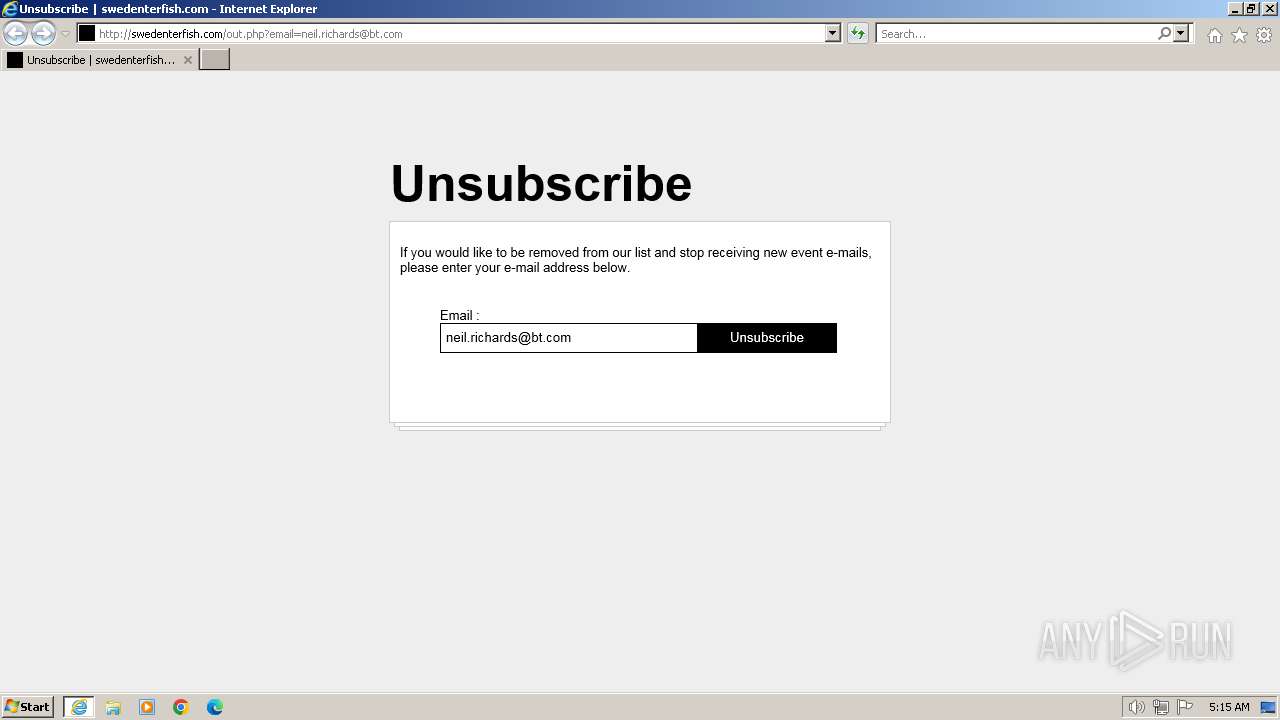
2928 | iexplore.exe | GET | 302 | 84.16.247.175:80 | http://swedenterfish.com//697671729956/8931854/2266042935321276/ramadankarim?od=1syvouttt6624debe83cf6.vz7517.S00mdrfs9yc25aw00t_xl1588.fs9yc.._xl.._xl._xl.fs9yc..._xl.YnY4eWotMzhuc3F0cQ==5x697l | unknown | — | — | unknown |
2032 | iexplore.exe | GET | 200 | 84.16.247.175:80 | http://swedenterfish.com/favicon.ico | unknown | — | — | unknown |
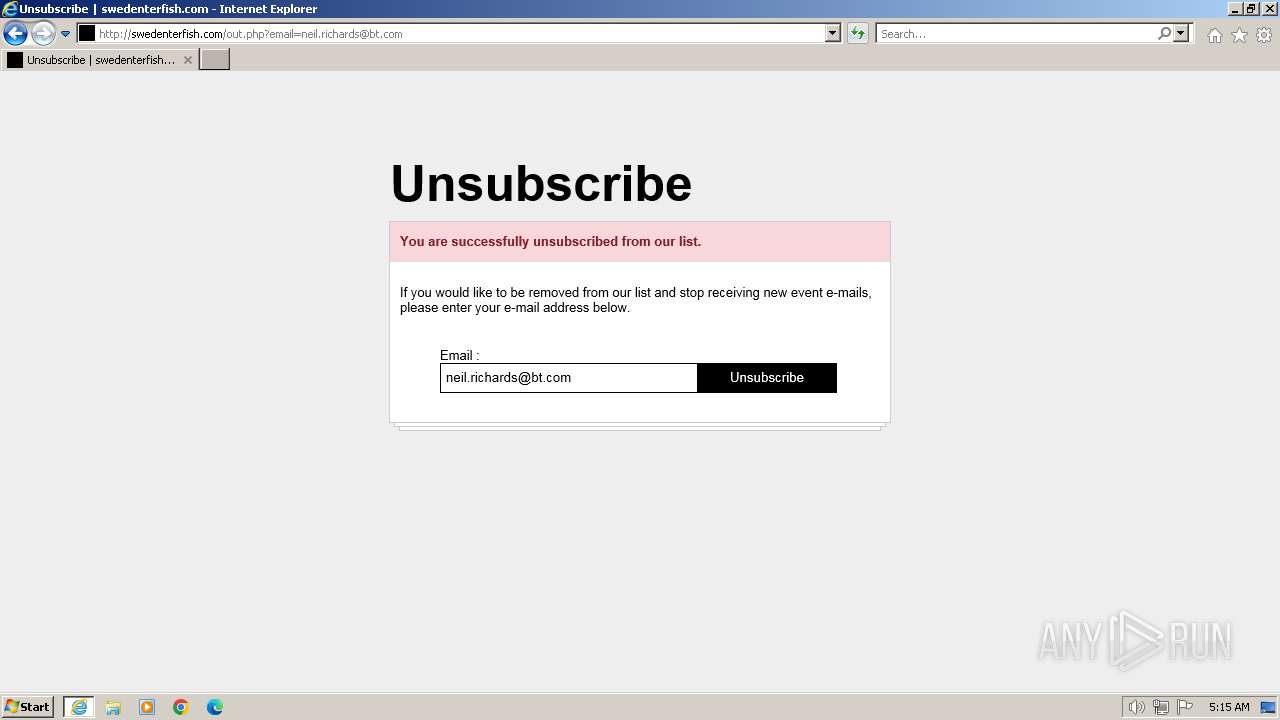
2928 | iexplore.exe | GET | 200 | 84.16.247.175:80 | http://swedenterfish.com/out.php?email=neil.richards@bt.com | unknown | — | — | unknown |
2928 | iexplore.exe | POST | 200 | 84.16.247.175:80 | http://swedenterfish.com/out.php?email=neil.richards@bt.com | unknown | — | — | unknown |
2032 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e7e9e17f6d2a28fe | unknown | — | — | unknown |
2032 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b5f00da5b3c986a4 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
2928 | iexplore.exe | 49.51.78.226:443 | cos.na-ashburn.myqcloud.com | Tencent Building, Kejizhongyi Avenue | US | unknown |
2928 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2928 | iexplore.exe | 104.18.20.226:80 | ocsp.globalsign.com | CLOUDFLARENET | — | shared |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2928 | iexplore.exe | 84.16.247.175:80 | swedenterfish.com | Leaseweb Deutschland GmbH | DE | unknown |
2032 | iexplore.exe | 84.16.247.175:80 | swedenterfish.com | Leaseweb Deutschland GmbH | DE | unknown |
2032 | iexplore.exe | 2.18.29.200:443 | www.bing.com | Akamai International B.V. | PL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cos.na-ashburn.myqcloud.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
swedenterfish.com |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO Tencent Cloud Storage Domain in DNS Lookup (myqcloud .com) |
2928 | iexplore.exe | Misc activity | ET INFO Observed Tencent Cloud Storage Domain (myqcloud .com in TLS SNI) |
2928 | iexplore.exe | Misc activity | ET INFO Observed Tencent Cloud Storage Domain (myqcloud .com in TLS SNI) |
2928 | iexplore.exe | Possible Social Engineering Attempted | ET PHISHING Suspicious Redirect - Possible Phishing May 25 2016 |