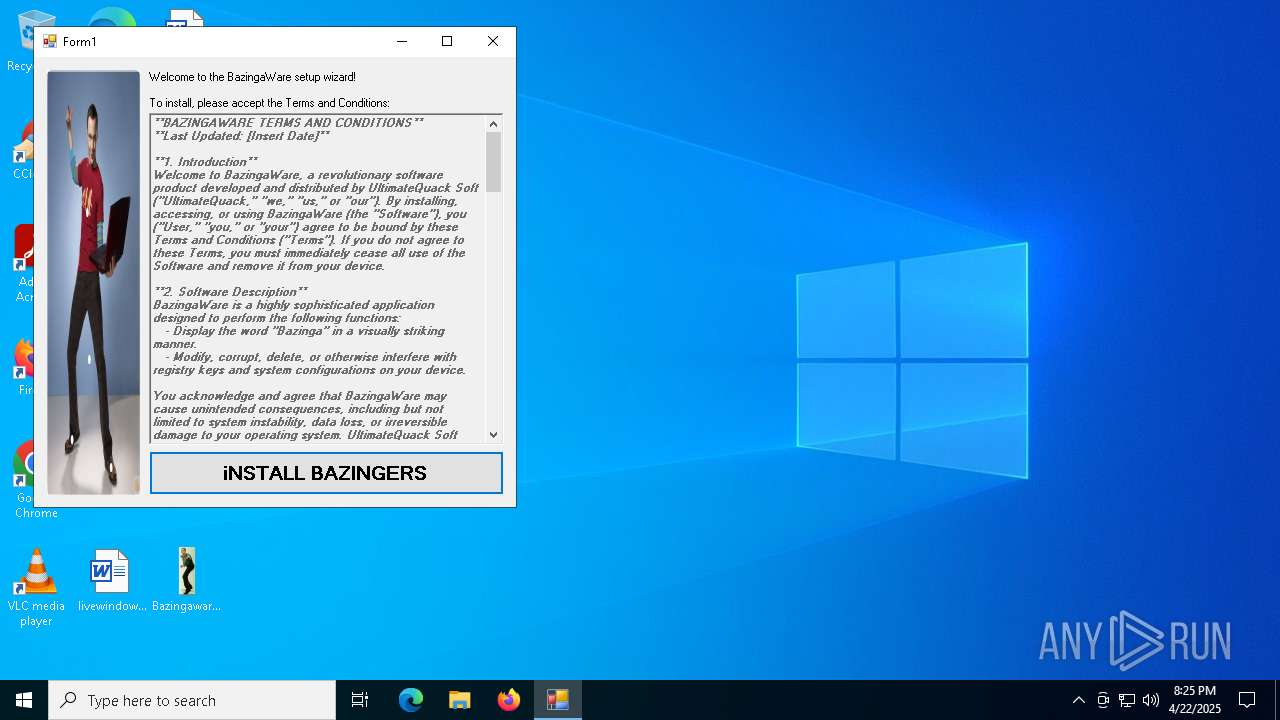
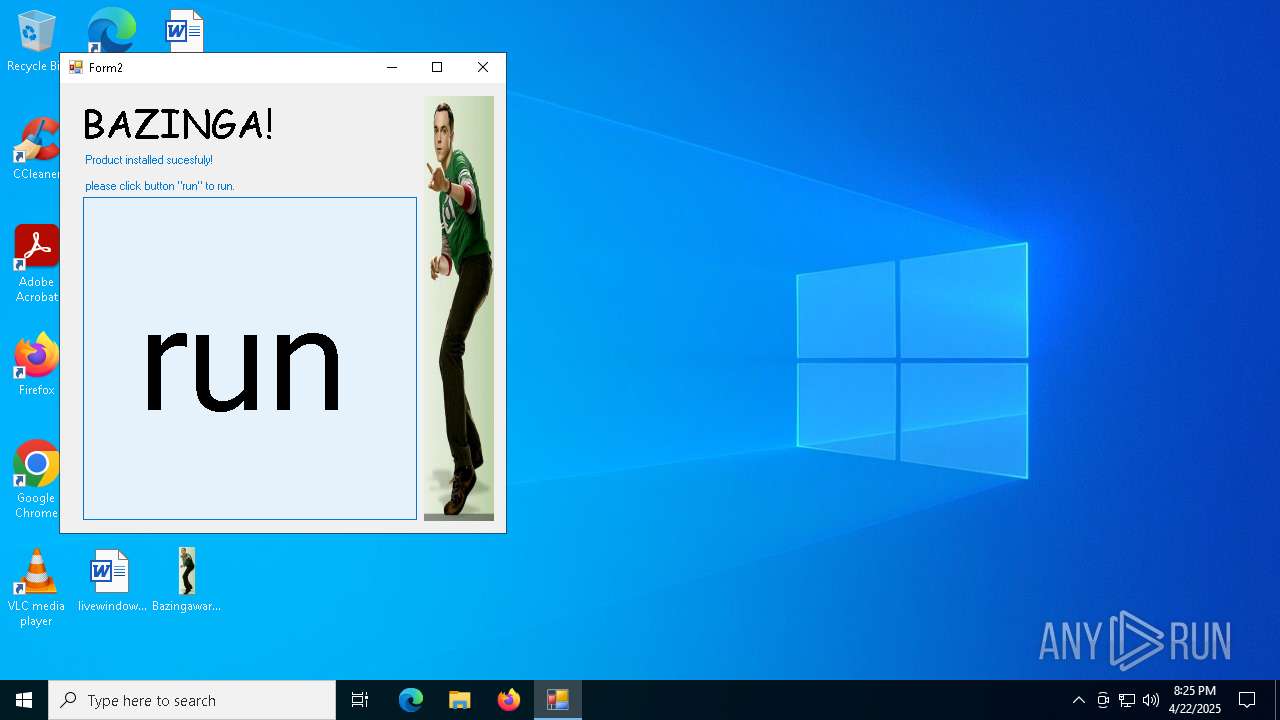
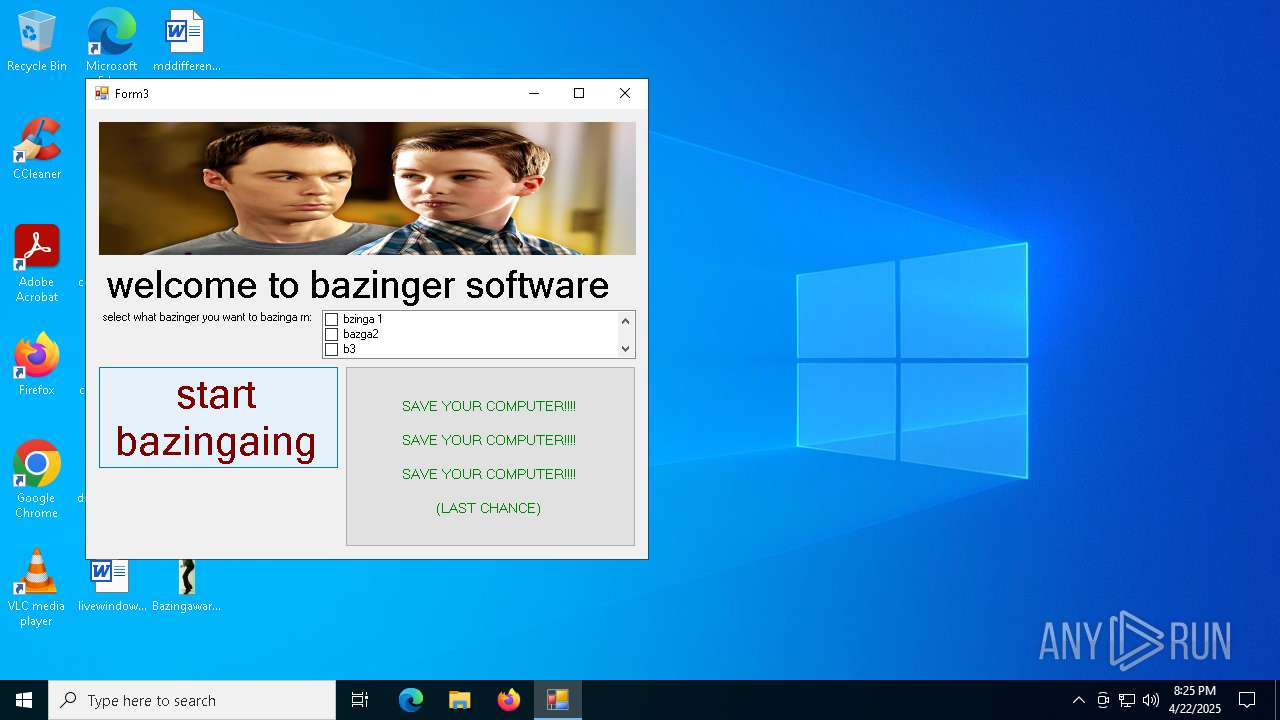
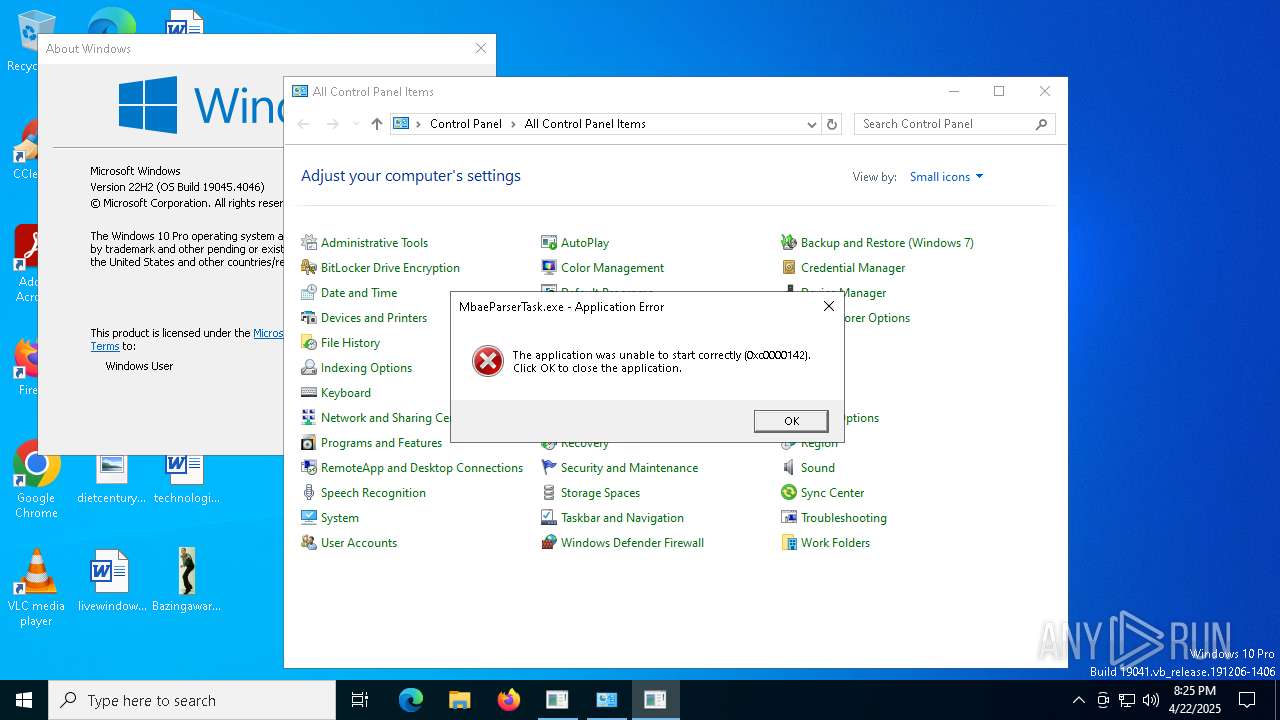
| File name: | Bazingaware.exe |
| Full analysis: | https://app.any.run/tasks/492af76d-ba77-4fad-8232-0ccfc7982147 |
| Verdict: | Malicious activity |
| Analysis date: | April 22, 2025, 20:25:00 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64 Mono/.Net assembly, for MS Windows, 2 sections |
| MD5: | 26304CBDFB6374B8688E453691C2E54D |
| SHA1: | 21218655BA35DAE0AC2AB5073A36F689615CE579 |
| SHA256: | 72A4C7E34726AD4682140B33D75F1646B4C83C6F492F9F288B2249F9F1DBFFC9 |
| SSDEEP: | 98304:YX1WQgtiSCRh8dXFHAPEWmJVXOWlgtvSCOvJEc1bdFrNfveDbhVA22Ybs8SYO4hJ:hUh+ |
MALICIOUS
Changes the autorun value in the registry
- Bazingaware.exe (PID: 5344)
Create files in the Startup directory
- Bazingaware.exe (PID: 5344)
Scans artifacts that could help determine the target
- Bazingaware.exe (PID: 5344)
Execute application with conhost.exe as parent process
- WerFault.exe (PID: 1228)
- WerFault.exe (PID: 2772)
SUSPICIOUS
Executing commands from a ".bat" file
- Bazingaware.exe (PID: 5344)
Reads Internet Explorer settings
- Bazingaware.exe (PID: 5344)
Starts CMD.EXE for commands execution
- Bazingaware.exe (PID: 5344)
Reads security settings of Internet Explorer
- Bazingaware.exe (PID: 5344)
Changes the Home page of Internet Explorer
- Bazingaware.exe (PID: 5344)
There is functionality for taking screenshot (YARA)
- Bazingaware.exe (PID: 5344)
- Bazingaware.exe (PID: 1388)
Executable content was dropped or overwritten
- Bazingaware.exe (PID: 5344)
Changes the title of the Internet Explorer window
- Bazingaware.exe (PID: 5344)
Process changes security settings for the VBA macro
- Bazingaware.exe (PID: 5344)
Reads the date of Windows installation
- Bazingaware.exe (PID: 5344)
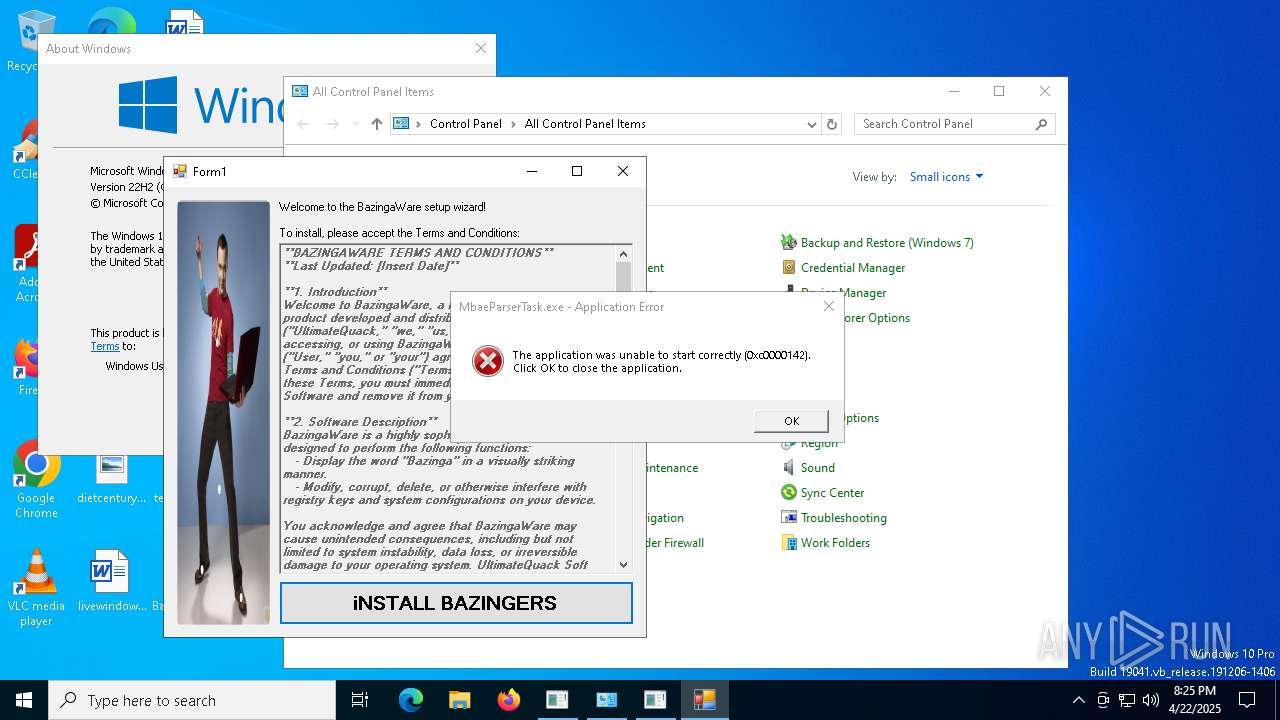
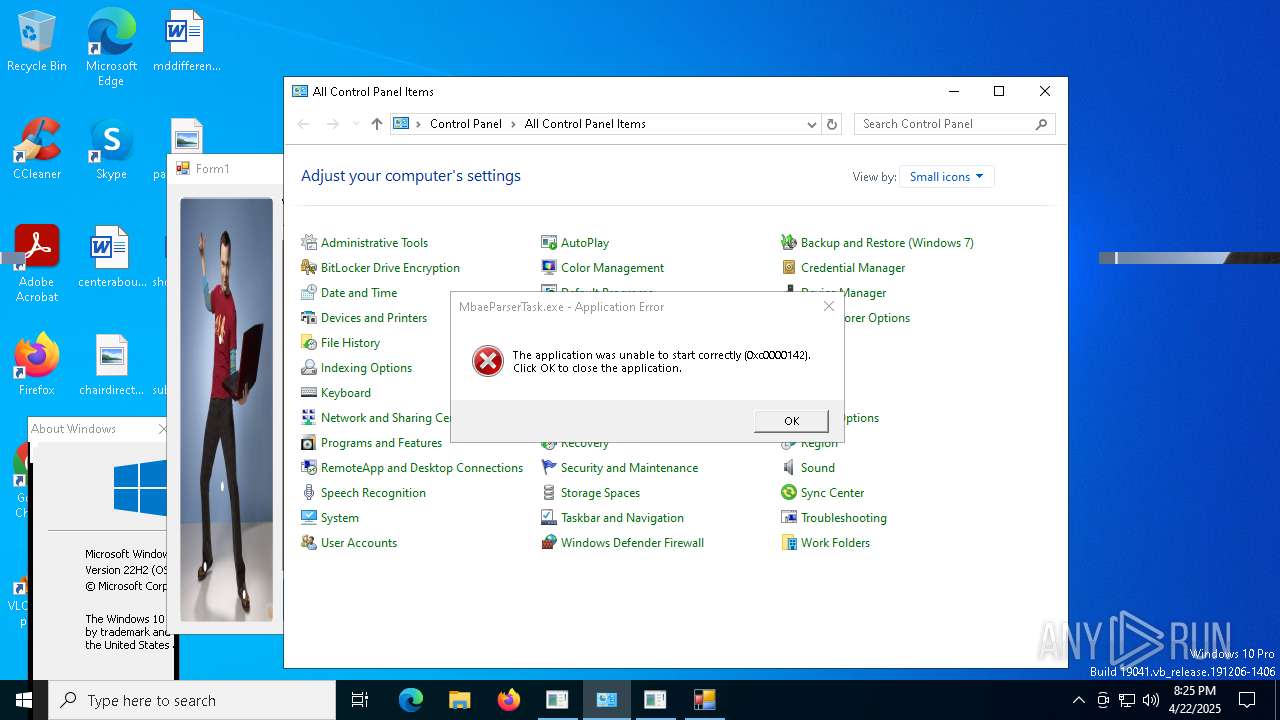
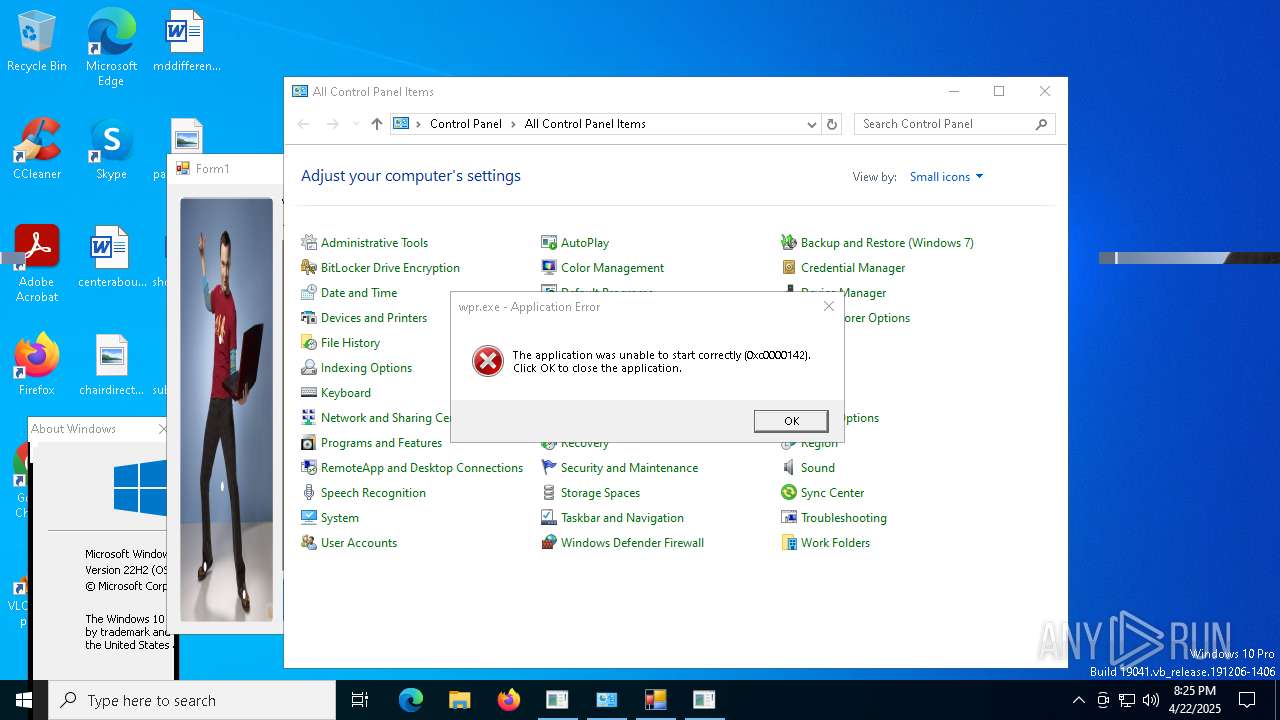
Executes application which crashes
- conhost.exe (PID: 4880)
- Bazingaware.exe (PID: 5344)
- conhost.exe (PID: 6988)
The process creates files with name similar to system file names
- WerFault.exe (PID: 1228)
- WerFault.exe (PID: 2772)
INFO
Creates files or folders in the user directory
- Bazingaware.exe (PID: 5344)
- WerFault.exe (PID: 1228)
- WerFault.exe (PID: 2772)
- WerFault.exe (PID: 5200)
- WerFault.exe (PID: 720)
Reads mouse settings
- Bazingaware.exe (PID: 5344)
Reads the computer name
- Bazingaware.exe (PID: 5344)
- Bazingaware.exe (PID: 1388)
Auto-launch of the file from Registry key
- Bazingaware.exe (PID: 5344)
Create files in a temporary directory
- Bazingaware.exe (PID: 5344)
Auto-launch of the file from Startup directory
- Bazingaware.exe (PID: 5344)
Reads the machine GUID from the registry
- Bazingaware.exe (PID: 5344)
- Bazingaware.exe (PID: 1388)
Checks supported languages
- Bazingaware.exe (PID: 5344)
- Bazingaware.exe (PID: 1388)
Process checks computer location settings
- Bazingaware.exe (PID: 5344)
Manual execution by a user
- Bazingaware.exe (PID: 1388)
Reads Microsoft Office registry keys
- Bazingaware.exe (PID: 5344)
Reads the software policy settings
- slui.exe (PID: 2692)
Checks proxy server information
- slui.exe (PID: 2692)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2040:06:30 22:39:32+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 48 |
| CodeSize: | 3513856 |
| InitializedDataSize: | 143360 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x0000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | BAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGABAZINGA |
| CompanyName: | UltimateQuack |
| FileDescription: | Bazingaware |
| FileVersion: | 1.0.0.0 |
| InternalName: | Bazingaware.exe |
| LegalCopyright: | Copyright © 2025 |
| LegalTrademarks: | Bazingaware TM |
| OriginalFileName: | Bazingaware.exe |
| ProductName: | Bazingaware |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
141
Monitored processes
17
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 720 | C:\WINDOWS\system32\WerFault.exe -u -p 5344 -s 3680 | C:\Windows\System32\WerFault.exe | — | Bazingaware.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\finish.bat"" | C:\Windows\System32\cmd.exe | — | Bazingaware.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | C:\WINDOWS\system32\WerFault.exe -u -p 6988 -s 808 | C:\Windows\System32\WerFault.exe | — | conhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1388 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Bazingaware.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Bazingaware.exe | — | explorer.exe | |||||||||||
User: admin Company: UltimateQuack Integrity Level: MEDIUM Description: Bazingaware Version: 1.0.0.0 Modules
| |||||||||||||||
| 2692 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2772 | C:\WINDOWS\system32\WerFault.exe -u -p 4880 -s 724 | C:\Windows\System32\WerFault.exe | — | conhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3888 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3900 | "C:\WINDOWS\system32\MbaeParserTask.exe" | C:\Windows\System32\MbaeParserTask.exe | — | Bazingaware.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Mobile Broadband Account Experience Parser Task Exit code: 3221225794 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4448 | "C:\WINDOWS\system32\control.exe" | C:\Windows\System32\control.exe | — | Bazingaware.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Control Panel Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4880 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | wpr.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 3221226505 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
48 330
Read events
43 537
Write events
4 793
Delete events
0
Modification events
| (PID) Process: | (5344) Bazingaware.exe | Key: | HKEY_CURRENT_USER\AppEvents\EventLabels\Notification.Looping.Alarm3 |
| Operation: | write | Name: | ExcludeFromCPL |
Value: | |||
| (PID) Process: | (5344) Bazingaware.exe | Key: | HKEY_CURRENT_USER\AppEvents\EventLabels\Notification.Looping.Alarm4 |
| Operation: | write | Name: | ExcludeFromCPL |
Value: | |||
| (PID) Process: | (5344) Bazingaware.exe | Key: | HKEY_CURRENT_USER\AppEvents\EventLabels\Notification.Looping.Alarm5 |
| Operation: | write | Name: | ExcludeFromCPL |
Value: | |||
| (PID) Process: | (5344) Bazingaware.exe | Key: | HKEY_CURRENT_USER\AppEvents\EventLabels\Notification.Looping.Alarm6 |
| Operation: | write | Name: | ExcludeFromCPL |
Value: | |||
| (PID) Process: | (5344) Bazingaware.exe | Key: | HKEY_CURRENT_USER\Control Panel\International\User Profile |
| Operation: | write | Name: | ShowCasing |
Value: | |||
| (PID) Process: | (5344) Bazingaware.exe | Key: | HKEY_CURRENT_USER\Control Panel\International\User Profile |
| Operation: | write | Name: | ShowShiftLock |
Value: | |||
| (PID) Process: | (5344) Bazingaware.exe | Key: | HKEY_CURRENT_USER\Control Panel\International\User Profile |
| Operation: | write | Name: | HttpAcceptLanguageOptOut |
Value: | |||
| (PID) Process: | (5344) Bazingaware.exe | Key: | HKEY_CURRENT_USER\Control Panel\International |
| Operation: | write | Name: | sPositiveSign |
Value: | |||
| (PID) Process: | (5344) Bazingaware.exe | Key: | HKEY_CURRENT_USER\Control Panel\Mouse |
| Operation: | write | Name: | ActiveWindowTracking |
Value: | |||
| (PID) Process: | (5344) Bazingaware.exe | Key: | HKEY_CURRENT_USER\Control Panel\Mouse |
| Operation: | write | Name: | DoubleClickWidth |
Value: S | |||
Executable files
1
Suspicious files
61
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5344 | Bazingaware.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\UserCache64.bin | binary | |
MD5:FF92FA2C986DDC6DC79909DBA9079CA2 | SHA256:00A9C8E1AAD0982E0A06BF023743825DB351960C753A8DE78DB18FBE69D60609 | |||
| 5344 | Bazingaware.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeSysFnt23.lst | binary | |
MD5:6E0D2936ADB9D18EAAAA263A0351CA24 | SHA256:F2D49214F9C5B7E3ABA4E34A6095821BEEECBD3F4708B58BA778D4C694C4E6AC | |||
| 5344 | Bazingaware.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeCMapFnt23.lst | binary | |
MD5:31DD82A610C62DC47DE9D653EB17F85E | SHA256:05778A98ED3CE88A7C1037D252D699D168B96CCBB3DAC03435DC843FE7138C05 | |||
| 5344 | Bazingaware.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\Files\DC_Reader_Convert_LHP_Banner | binary | |
MD5:2C9BFC9B098FC8F772A6E155DB2C7B46 | SHA256:D8301471FEAC0F0D4755737246F1ECB549A5508C7F511EBDD29FA8819CFE01F0 | |||
| 5344 | Bazingaware.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\Files\DC_Reader_Disc_LHP_Banner | binary | |
MD5:F7A97A78CAAC4EC777A99E86A8DB9D78 | SHA256:C5A2C1DDCF535970E99988CD4309570911160350C9144C8DCA81F9B05E9DB291 | |||
| 5344 | Bazingaware.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\Cache\AcroFnt23.lst | binary | |
MD5:5C61DD37C82214D08D022236D6578606 | SHA256:E37427A7FECEC3C02BCD5AFEBA4EB6744B8C8A8705D47C54E825B9A5B349E941 | |||
| 5344 | Bazingaware.exe | C:\Users\admin\AppData\Local\Comms\UnistoreDB\store.vol | — | |
MD5:— | SHA256:— | |||
| 5344 | Bazingaware.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\Files\DC_Reader_More_LHP_Banner | binary | |
MD5:DE0DE7008644C828422DEBFE525227B5 | SHA256:8C9C712CABDED3204BD754A35E5AD4F48599DC741018D6BFE8A8AEBBD777BC3B | |||
| 5344 | Bazingaware.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\Files\DC_Reader_RHP_Banner | binary | |
MD5:D3921796981081AEF9AE8D493E158C0C | SHA256:943AECE563C15EC842401BAE9D7D11329E2CD516E1E12F675BFC524CFD6BF32B | |||
| 5344 | Bazingaware.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\Files\DC_Reader_Sign_LHP_Banner | binary | |
MD5:06A6FD01FB809D89DC1D3442B43CE97E | SHA256:9649F40E89D3C5828A50B0A50E9407E346544AC30E5B405F46A1389F17F78477 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
20
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
896 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2692 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |