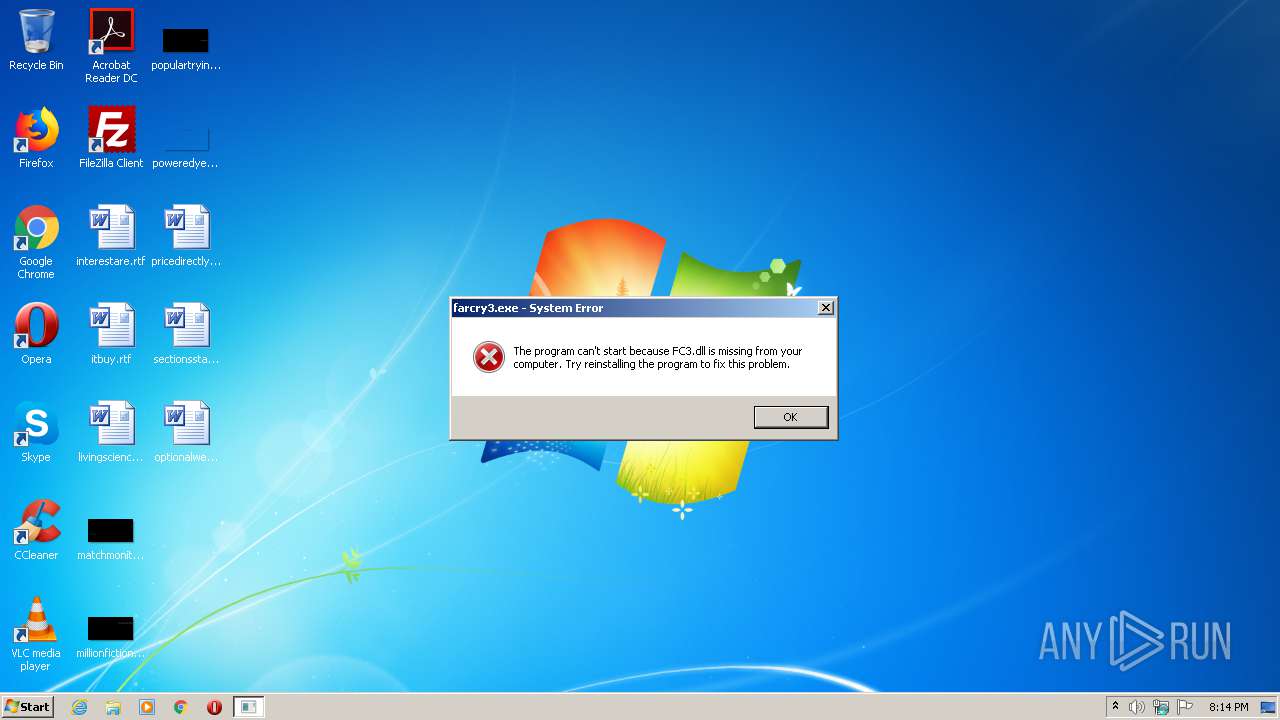
| File name: | farcry3.exe |
| Full analysis: | https://app.any.run/tasks/2e69d97b-5597-4ed8-8b91-65006f35c153 |
| Verdict: | Malicious activity |
| Analysis date: | July 12, 2020, 19:14:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | D712327B6D8A981BFDADD275E57DF328 |
| SHA1: | 05D639AA57A6EC5B2383E15E6E552031B72E75EC |
| SHA256: | 72994B08E0388906E606BA37DF92AC016329F53823E385F0954B25F6796E4D93 |
| SSDEEP: | 3072:lUAilgOxMzR/YemgAQb0OGi7ktAwTLJdoRw/QqUrPKINEU9pSwPp:qhIRK/Q+wwLJD/bURNEUGK |
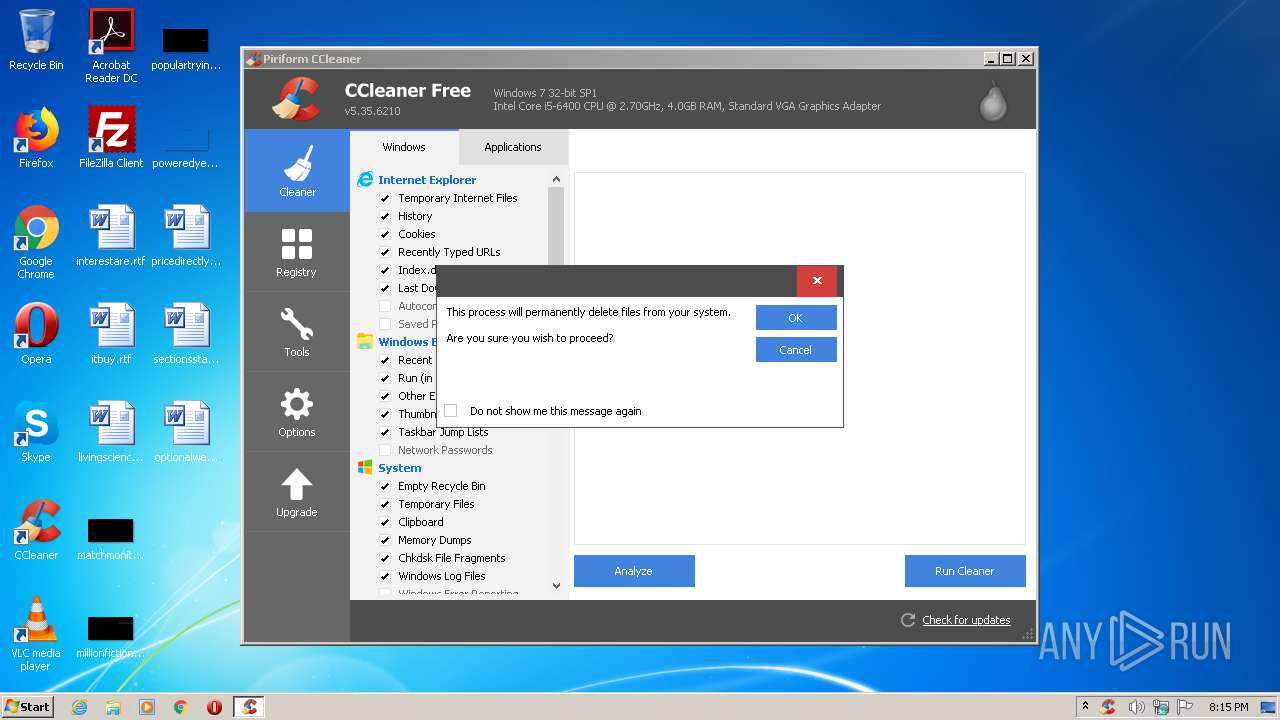
MALICIOUS
Loads the Task Scheduler COM API
- CCleaner.exe (PID: 1464)
- CCleaner.exe (PID: 812)
Changes the autorun value in the registry
- CCleaner.exe (PID: 812)
Actions looks like stealing of personal data
- CCleaner.exe (PID: 3804)
- CCleaner.exe (PID: 812)
Changes settings of System certificates
- CCleaner.exe (PID: 3804)
SUSPICIOUS
Reads internet explorer settings
- CCleaner.exe (PID: 3804)
- CCleaner.exe (PID: 812)
Executed via Task Scheduler
- CCleaner.exe (PID: 3804)
Reads the cookies of Mozilla Firefox
- CCleaner.exe (PID: 3804)
Application launched itself
- CCleaner.exe (PID: 3804)
Creates files in the user directory
- CCleaner.exe (PID: 3804)
Reads the cookies of Google Chrome
- CCleaner.exe (PID: 3804)
Low-level read access rights to disk partition
- CCleaner.exe (PID: 3804)
Reads Internet Cache Settings
- CCleaner.exe (PID: 3804)
Adds / modifies Windows certificates
- CCleaner.exe (PID: 3804)
INFO
Manual execution by user
- CCleaner.exe (PID: 1464)
Reads settings of System Certificates
- CCleaner.exe (PID: 3804)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:11:22 20:23:25+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 2560 |
| InitializedDataSize: | 191488 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x12f5 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.1.0.1 |
| ProductVersionNumber: | 0.1.0.1 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Unknown (0009) |
| CharacterSet: | Unicode |
| FileDescription: | Far Cry 3 |
| CompanyName: | Ubisoft Entertainment |
| FileVersion: | 0, 1, 0, 1 |
| InternalName: | FarCry3 |
| LegalCopyright: | Copyright (C) 2008 Ubisoft Entertainment |
| OriginalFileName: | FarCry3.exe |
| ProductName: | Far Cry 3 |
| ProductVersion: | 0, 1, 0, 1 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 22-Nov-2012 19:23:25 |
| Detected languages: |
|
| Debug artifacts: |
|
| FileDescription: | Far Cry 3 |
| CompanyName: | Ubisoft Entertainment |
| FileVersion: | 0, 1, 0, 1 |
| InternalName: | FarCry3 |
| LegalCopyright: | Copyright (C) 2008 Ubisoft Entertainment |
| OriginalFilename: | FarCry3.exe |
| ProductName: | Far Cry 3 |
| ProductVersion: | 0, 1, 0, 1 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000E0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 22-Nov-2012 19:23:25 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0000084A | 0x00000A00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.44402 |
.rdata | 0x00002000 | 0x00000636 | 0x00000800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.17788 |
.data | 0x00003000 | 0x0000038C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0.352759 |
.rsrc | 0x00004000 | 0x0002DDE8 | 0x0002DE00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.88035 |
.reloc | 0x00032000 | 0x00000360 | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 2.64173 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.79597 | 346 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 4.35559 | 744 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 3.9793 | 296 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 7.94422 | 53815 | Latin 1 / Western European | English - United States | RT_ICON |
5 | 6.6376 | 3752 | Latin 1 / Western European | English - United States | RT_ICON |
6 | 6.75256 | 2216 | Latin 1 / Western European | English - United States | RT_ICON |
7 | 6.34226 | 1384 | Latin 1 / Western European | English - United States | RT_ICON |
8 | 7.11956 | 7336 | Latin 1 / Western European | English - United States | RT_ICON |
9 | 7.30083 | 3240 | Latin 1 / Western European | English - United States | RT_ICON |
10 | 7.2996 | 872 | Latin 1 / Western European | English - United States | RT_ICON |
Imports
FC3.dll |
KERNEL32.dll |
MSVCR100.dll |
Total processes
38
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 812 | "C:\Program Files\CCleaner\CCleaner.exe" /monitor | C:\Program Files\CCleaner\CCleaner.exe | CCleaner.exe | ||||||||||||
User: admin Company: Piriform Ltd Integrity Level: HIGH Description: CCleaner Exit code: 0 Version: 5, 35, 0, 6210 Modules
| |||||||||||||||
| 1432 | "C:\Users\admin\AppData\Local\Temp\farcry3.exe" | C:\Users\admin\AppData\Local\Temp\farcry3.exe | — | explorer.exe | |||||||||||
User: admin Company: Ubisoft Entertainment Integrity Level: MEDIUM Description: Far Cry 3 Exit code: 3221225781 Version: 0, 1, 0, 1 Modules
| |||||||||||||||
| 1464 | "C:\Program Files\CCleaner\CCleaner.exe" | C:\Program Files\CCleaner\CCleaner.exe | — | explorer.exe | |||||||||||
User: admin Company: Piriform Ltd Integrity Level: MEDIUM Description: CCleaner Exit code: 0 Version: 5, 35, 0, 6210 Modules
| |||||||||||||||
| 3804 | "C:\Program Files\CCleaner\CCleaner.exe" /uac | C:\Program Files\CCleaner\CCleaner.exe | taskeng.exe | ||||||||||||
User: admin Company: Piriform Ltd Integrity Level: HIGH Description: CCleaner Exit code: 0 Version: 5, 35, 0, 6210 Modules
| |||||||||||||||
Total events
2 153
Read events
461
Write events
1 691
Delete events
1
Modification events
| (PID) Process: | (3804) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Piriform\CCleaner |
| Operation: | write | Name: | WipeFreeSpaceDrives |
Value: C:\ | |||
| (PID) Process: | (3804) CCleaner.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (812) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Piriform\CCleaner |
| Operation: | write | Name: | Monitoring |
Value: 1 | |||
| (PID) Process: | (812) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | CCleaner Monitoring |
Value: "C:\Program Files\CCleaner\CCleaner.exe" /MONITOR | |||
| (PID) Process: | (812) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Piriform\CCleaner |
| Operation: | write | Name: | SystemMonitoring |
Value: 1 | |||
| (PID) Process: | (3804) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Piriform\CCleaner |
| Operation: | write | Name: | CookiesToSave |
Value: *.piriform.com | |||
| (PID) Process: | (3804) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Piriform\CCleaner |
| Operation: | write | Name: | RunICS |
Value: 0 | |||
| (PID) Process: | (3804) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Piriform\CCleaner |
| Operation: | delete value | Name: | AutoICS |
Value: 1 | |||
| (PID) Process: | (3804) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3804) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
10
Text files
3
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3804 | CCleaner.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WebCache\WebCacheV01.dat | — | |
MD5:— | SHA256:— | |||
| 3804 | CCleaner.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WebCache\tmp.edb | — | |
MD5:— | SHA256:— | |||
| 3804 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3804 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\webappsstore.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3804 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\HXFEDK3TN6IY2ORRU9W1.temp | — | |
MD5:— | SHA256:— | |||
| 3804 | CCleaner.exe | C:\Users\admin\AppData\Local\Temp\CabDC99.tmp | — | |
MD5:— | SHA256:— | |||
| 3804 | CCleaner.exe | C:\Users\admin\AppData\Local\Temp\TarDC9A.tmp | — | |
MD5:— | SHA256:— | |||
| 3804 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\RR3MMDFQ5TTVGJ2XFHAG.temp | — | |
MD5:— | SHA256:— | |||
| 3804 | CCleaner.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WebCache\V01.log | binary | |
MD5:— | SHA256:— | |||
| 3804 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\ACF244F1A10D4DBED0D88EBA0C43A9B5_16756CC7371BB76A269719AA1471E96C | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
8
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3804 | CCleaner.exe | GET | 301 | 151.101.0.64:80 | http://www.piriform.com/auto?a=0&p=cc&v=5.35.6210&l=1033&lk=&mk=IJR6-W5SV-5KYR-QBZD-6BY4-RN5Z-WAV9-RVK2-VJCA&o=6.1W3&au=1&mx=97B7721C4994E2556FF6A439510F665DB45337A341A47E15F4997584423BF714&gu=00000000-0000-4000-8000-d6f7f2be5127 | US | — | — | whitelisted |
3804 | CCleaner.exe | GET | 200 | 151.101.2.109:80 | http://license.piriform.com/verify/?p=ccpro&c=cc&cv=5.35.6210&l=1033&lk=CJ9T-J7CU-SPNV-GWMB-WBEC&mk=IJR6-W5SV-5KYR-QBZD-6BY4-RN5Z-WAV9-RVK2-VJCA&mx=97B7721C4994E2556FF6A439510F665DB45337A341A47E15F4997584423BF714&gu=00000000-0000-4000-8000-d6f7f2be5127 | US | text | 14 b | whitelisted |
3804 | CCleaner.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/rootr1/ME8wTTBLMEkwRzAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDkbwjNvPLFRm7zMB3V80 | US | der | 1.49 Kb | whitelisted |
3804 | CCleaner.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/rootr1/MEwwSjBIMEYwRDAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCCwQAAAAAAURO8EJH | US | der | 1.49 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3804 | CCleaner.exe | 151.101.0.64:80 | www.piriform.com | Fastly | US | whitelisted |
3804 | CCleaner.exe | 151.101.0.64:443 | www.piriform.com | Fastly | US | whitelisted |
3804 | CCleaner.exe | 104.18.21.226:80 | ocsp.globalsign.com | Cloudflare Inc | US | shared |
3804 | CCleaner.exe | 151.101.2.202:443 | www.ccleaner.com | Fastly | US | suspicious |
3804 | CCleaner.exe | 104.18.20.226:80 | ocsp.globalsign.com | Cloudflare Inc | US | shared |
3804 | CCleaner.exe | 151.101.2.109:443 | license.piriform.com | Fastly | US | suspicious |
3804 | CCleaner.exe | 151.101.2.109:80 | license.piriform.com | Fastly | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.piriform.com |
| whitelisted |
www.ccleaner.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
license.piriform.com |
| whitelisted |