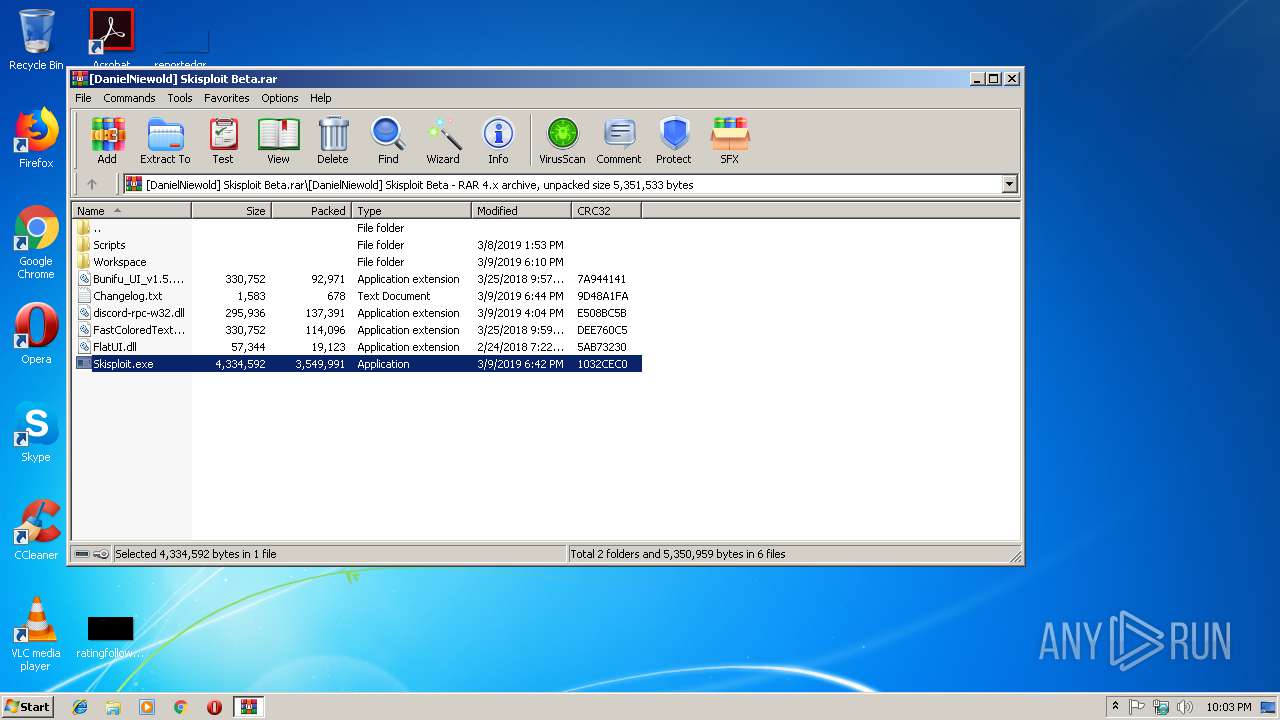
| File name: | [DanielNiewold] Skisploit Beta.rar |
| Full analysis: | https://app.any.run/tasks/129482c4-28cb-42c9-b163-57e1a8a5e15e |
| Verdict: | Malicious activity |
| Analysis date: | March 12, 2019, 22:02:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 73020B1A7E43A6C543BFA25B12C5EB14 |
| SHA1: | 8B8E45554FD56BD267B82584C626EBA1C96BDBFC |
| SHA256: | 72936825F557C6D2A29D05FD9325D8D4B912F80E8DF5C2890080112750E4D2DF |
| SSDEEP: | 98304:UtjLz1Uy1pTJA/EZcqnch0Gq2H/sn7CLMoKEyx8P:IbBakcGGq2H0n7CwLEh |
MALICIOUS
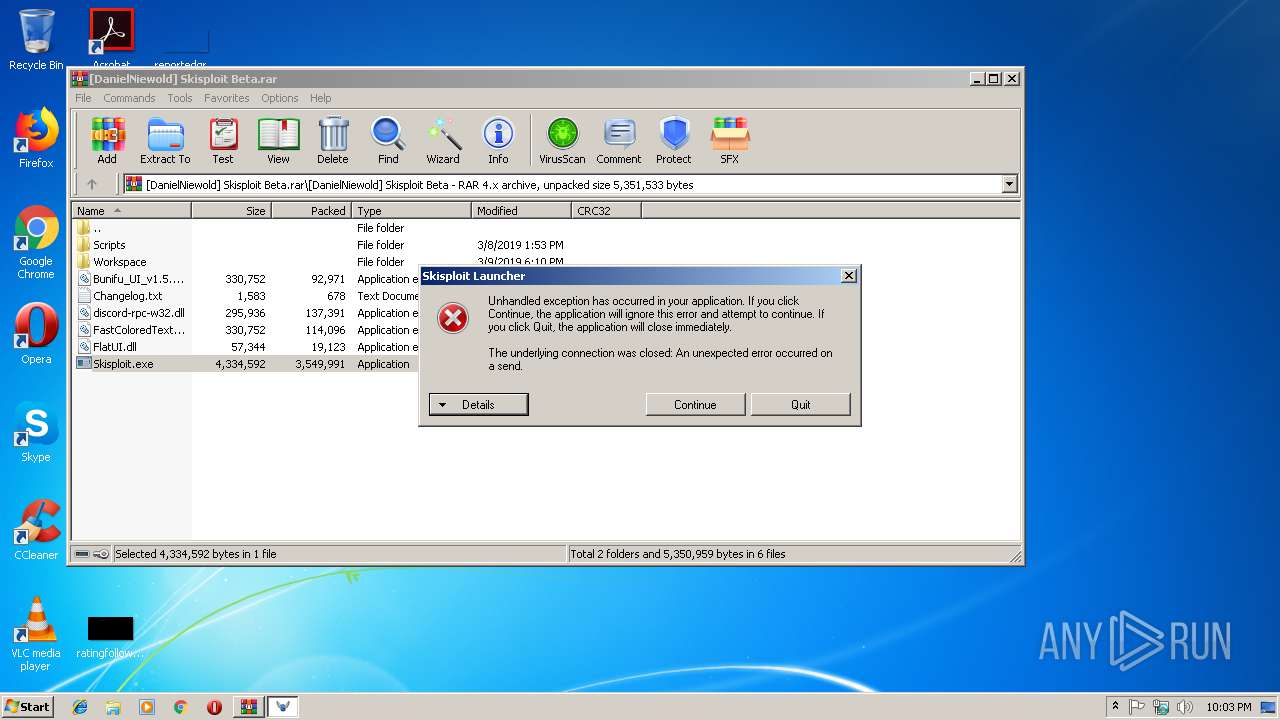
Application was dropped or rewritten from another process
- Skisploit.exe (PID: 3316)
- Skisploit.exe (PID: 3780)
Loads dropped or rewritten executable
- Skisploit.exe (PID: 3780)
SUSPICIOUS
Reads Environment values
- Skisploit.exe (PID: 3780)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3060)
Creates files in the program directory
- Skisploit.exe (PID: 3780)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 3060)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 93043 |
|---|---|
| UncompressedSize: | 330752 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2018:03:25 09:57:11 |
| PackingMethod: | Normal |
| ArchivedFileName: | [DanielNiewold] Skisploit Beta\Bunifu_UI_v1.5.3.dll |
Total processes
35
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3060 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\[DanielNiewold] Skisploit Beta.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
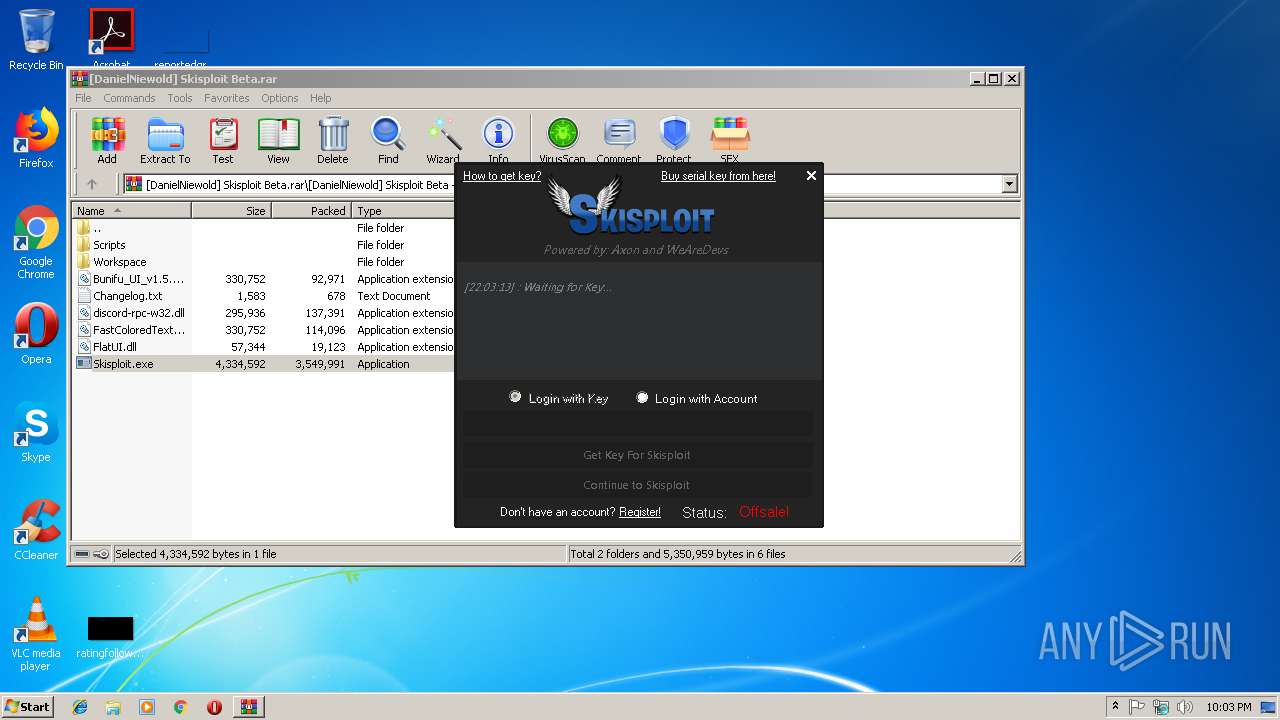
| 3316 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3060.18240\[DanielNiewold] Skisploit Beta\Skisploit.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3060.18240\[DanielNiewold] Skisploit Beta\Skisploit.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Skisploit Exit code: 3221226540 Version: 1.7.1.1 Modules
| |||||||||||||||
| 3780 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3060.18240\[DanielNiewold] Skisploit Beta\Skisploit.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3060.18240\[DanielNiewold] Skisploit Beta\Skisploit.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Skisploit Exit code: 0 Version: 1.7.1.1 Modules
| |||||||||||||||
Total events
475
Read events
450
Write events
25
Delete events
0
Modification events
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\[DanielNiewold] Skisploit Beta.rar | |||
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
5
Suspicious files
0
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3060.18240\[DanielNiewold] Skisploit Beta\Scripts\Need help.txt | text | |
MD5:661E6654680AD49FD2890E5C0847D868 | SHA256:42A70911B8F795A8D12BA0209E388A71A7EC2D0E94D81BBD1ADC75AD10584982 | |||
| 3060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3060.18240\[DanielNiewold] Skisploit Beta\discord-rpc-w32.dll | executable | |
MD5:A1C35901AD26A30C5B7836771B6BADFF | SHA256:517240600B04D454CC5AB7B03E43C4AF5A0B831FD2515F25C015A83652AD4CAC | |||
| 3060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3060.18240\[DanielNiewold] Skisploit Beta\Changelog.txt | text | |
MD5:102ED0D4448345CAC56415D9385E6879 | SHA256:51F9D8AA21DC0E476A037F5957C72EA78868BAEDCE73D8EA7A58152D6789DA16 | |||
| 3060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3060.18240\[DanielNiewold] Skisploit Beta\FastColoredTextBox.dll | executable | |
MD5:71963EB6707EF2DE595D336D5810082B | SHA256:F67F8CAF9216123C0F669AE7A0E9A086A28AD9FEE7E4756C224A7706CEAAB1CD | |||
| 3060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3060.18240\[DanielNiewold] Skisploit Beta\FlatUI.dll | executable | |
MD5:797261F587BB9C6B223B81D31D3B1507 | SHA256:EE5AA955CC297FD7ADBE641EE3A913D08FC0013C239B9710C9C87E10002DB089 | |||
| 3780 | Skisploit.exe | C:\Program Files (x86)\Skisploit\autoexec\init.txt | text | |
MD5:CA8605C31C33D922FDFA3C19EF0B0E89 | SHA256:01CE901E2BB322DC609CE04CDBC69F4916AE0DEDC62F2E10F4C32BC5FB5446B5 | |||
| 3060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3060.18240\[DanielNiewold] Skisploit Beta\Scripts\Where is quick execute.txt | text | |
MD5:D53B51EC8A31341A2005D25791942AF5 | SHA256:BFC9E202948113AD136DB4CE7D544084B858A40BABBB943EFB37248A383962EC | |||
| 3780 | Skisploit.exe | C:\Program Files (x86)\Skisploit\autoexec\ReadMe.txt | text | |
MD5:CC99ACB1A73FA64CA8C3665C27A38834 | SHA256:A69D52B3DD07B69788040A0DCCF8AE2875DDA917ACEDCF1F42CCD06062EAF653 | |||
| 3060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3060.18240\[DanielNiewold] Skisploit Beta\Bunifu_UI_v1.5.3.dll | executable | |
MD5:E0EF2817EE5A7C8CD1EB837195768BD2 | SHA256:76E1D3EC95FDEF74ABAF90392DD6F4AA5E344922ABF11E572707287D467F2930 | |||
| 3060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3060.18240\[DanielNiewold] Skisploit Beta\Scripts\How to add scripts here.txt | text | |
MD5:84AD93C0BA83600C918785C8ED2625E0 | SHA256:94F09700B0C39956419C21E02253CAB1B5A6115AC6645A0F420D7CCDA4897356 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
3
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3780 | Skisploit.exe | GET | 200 | 185.11.145.5:80 | http://api.thundermods.com/version.txt | NL | text | 7 b | malicious |
3780 | Skisploit.exe | GET | 200 | 185.11.145.5:80 | http://api.thundermods.com/onsale.txt | NL | text | 4 b | malicious |
3780 | Skisploit.exe | GET | 200 | 185.11.145.5:80 | http://api.thundermods.com/version.txt | NL | text | 7 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3780 | Skisploit.exe | 68.65.123.241:443 | roxploits.com | Namecheap, Inc. | US | suspicious |
3780 | Skisploit.exe | 185.11.145.5:80 | api.thundermods.com | Dotsi, Unipessoal Lda. | NL | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.thundermods.com |
| malicious |
roxploits.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Skisploit.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |