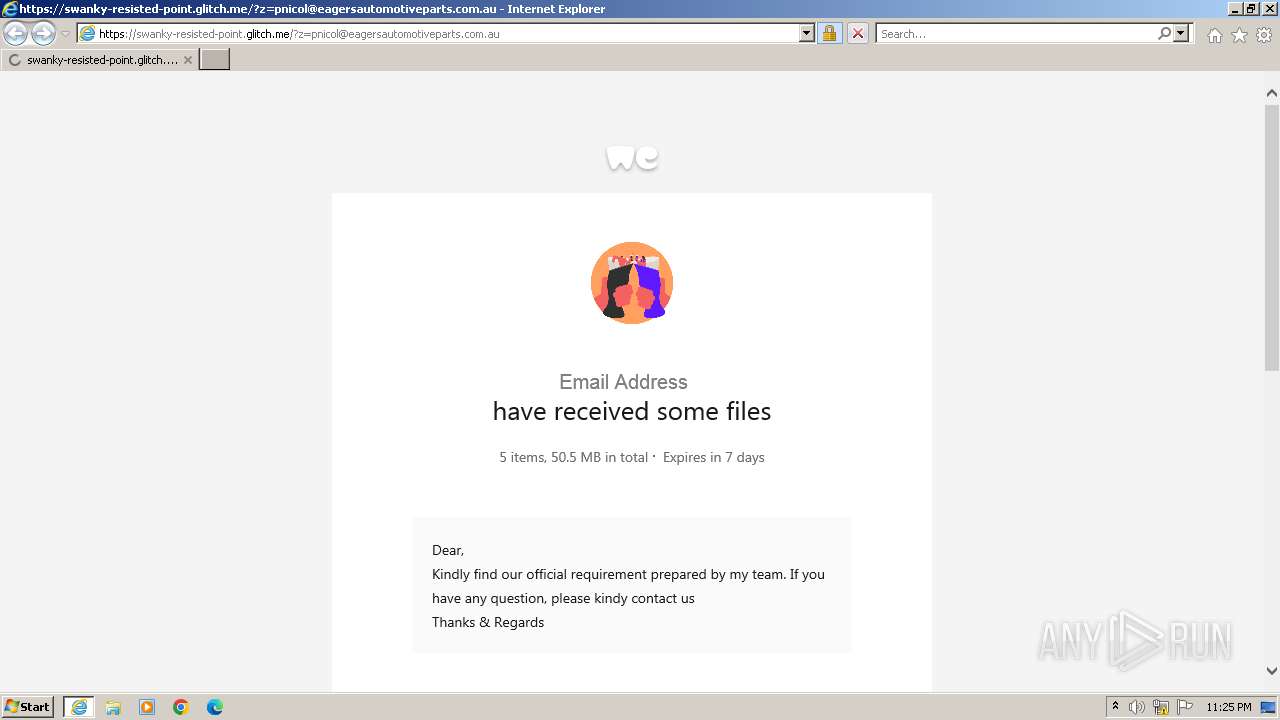
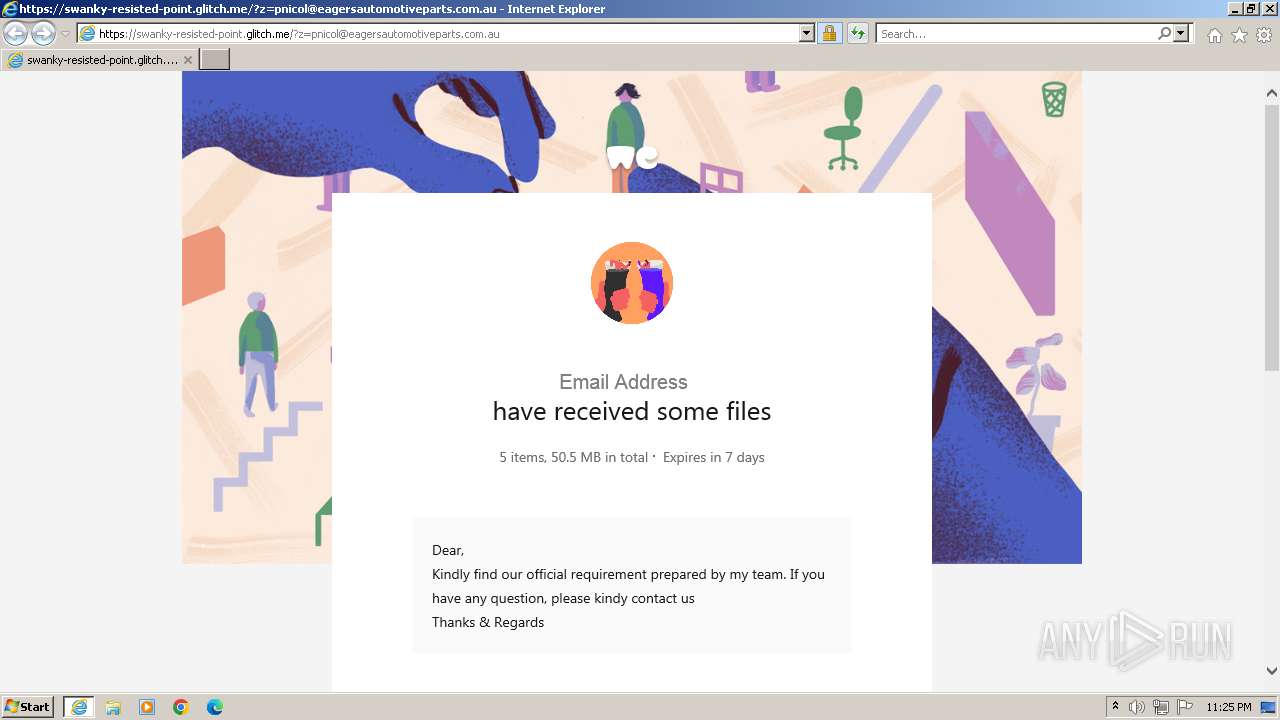
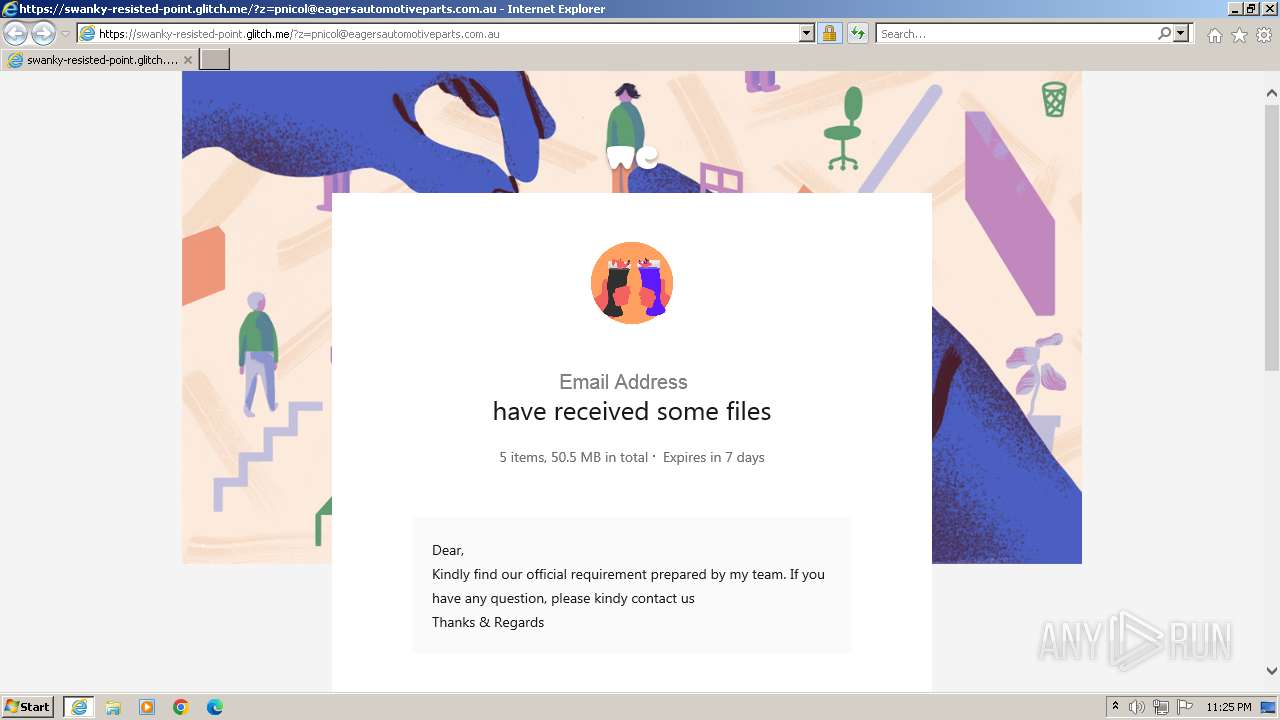
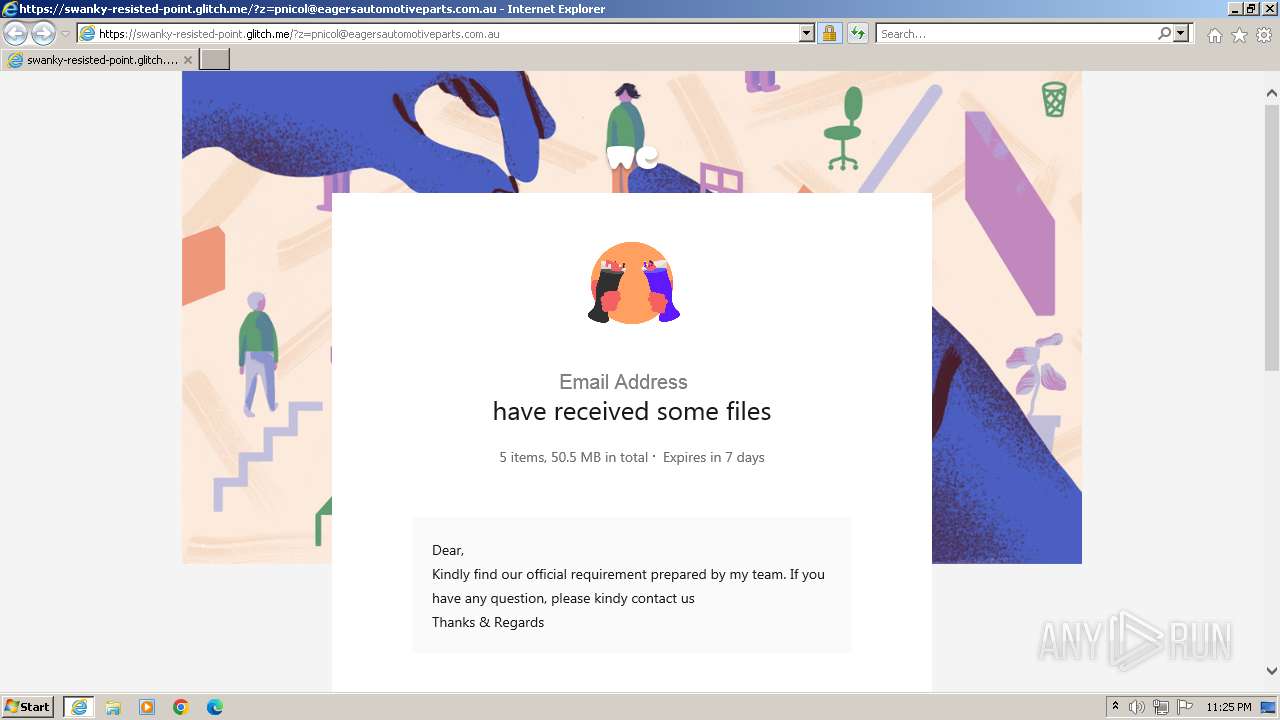
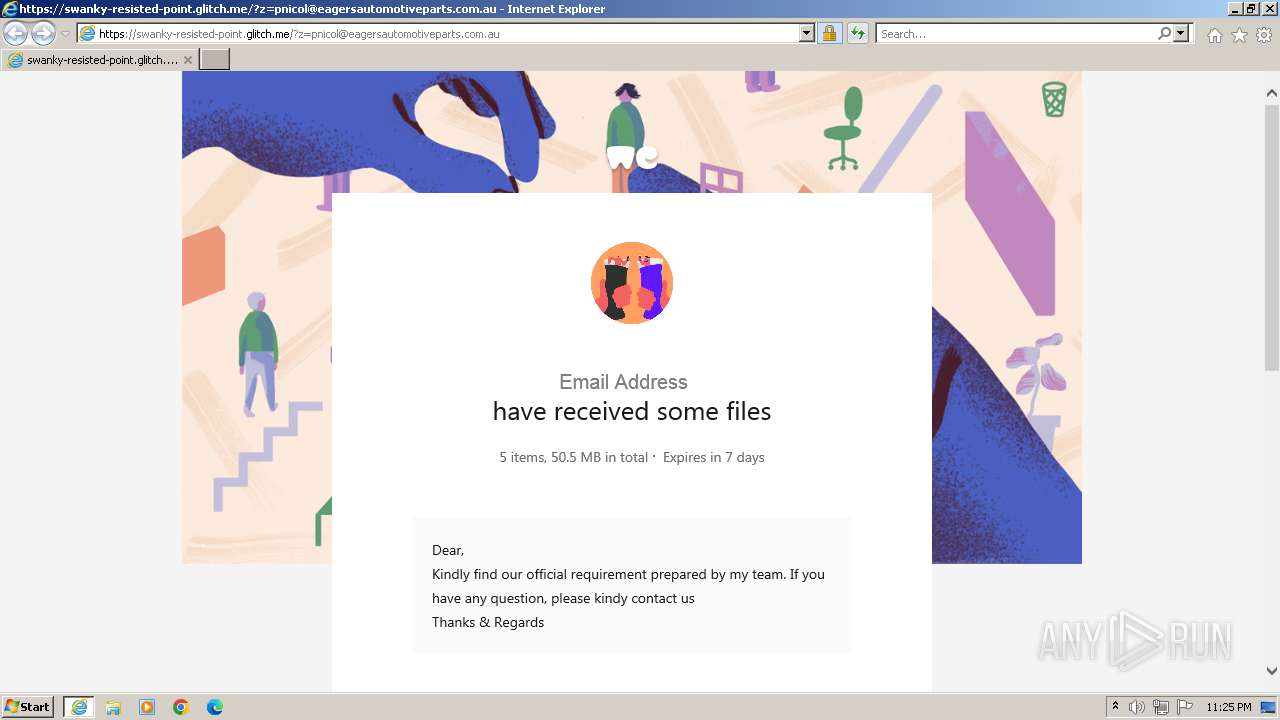
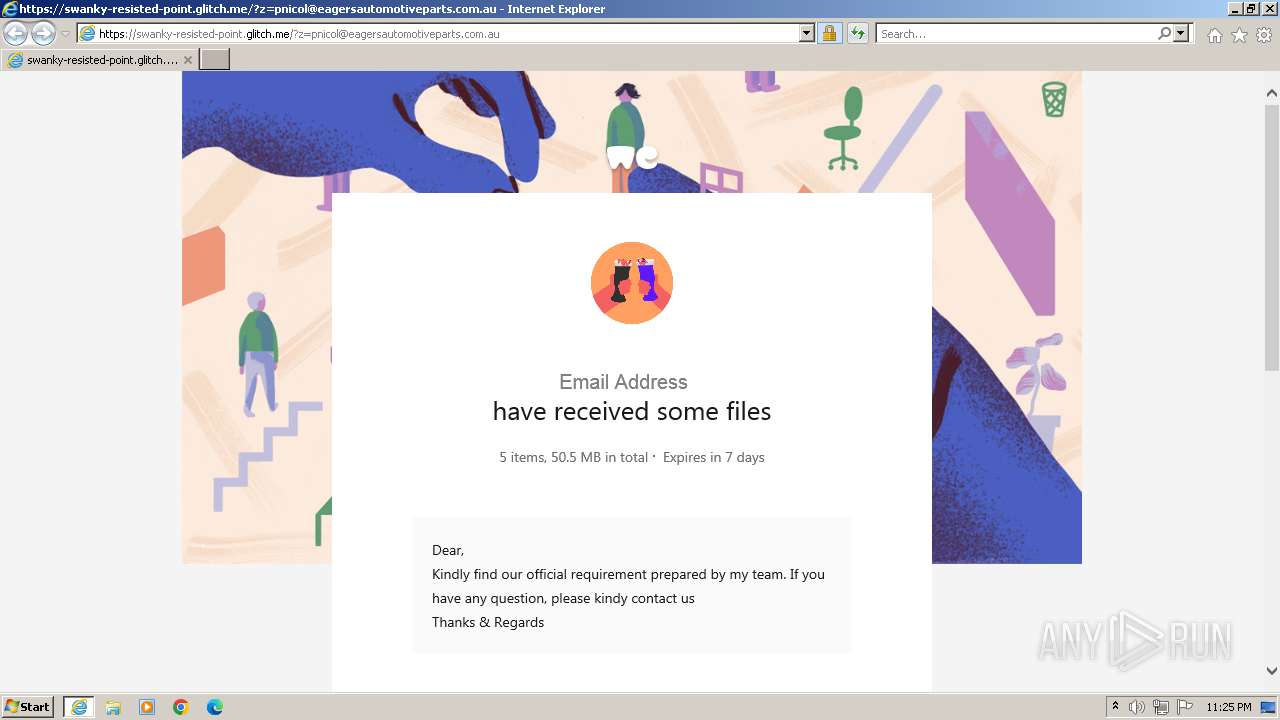
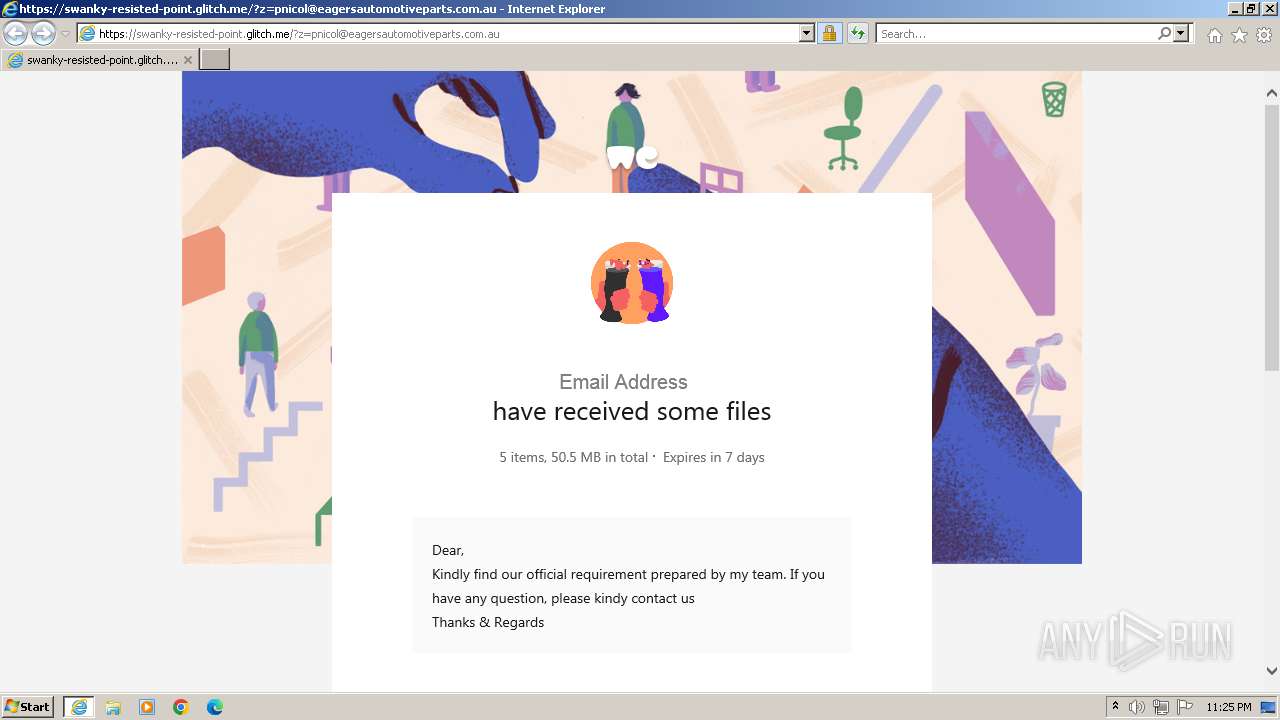
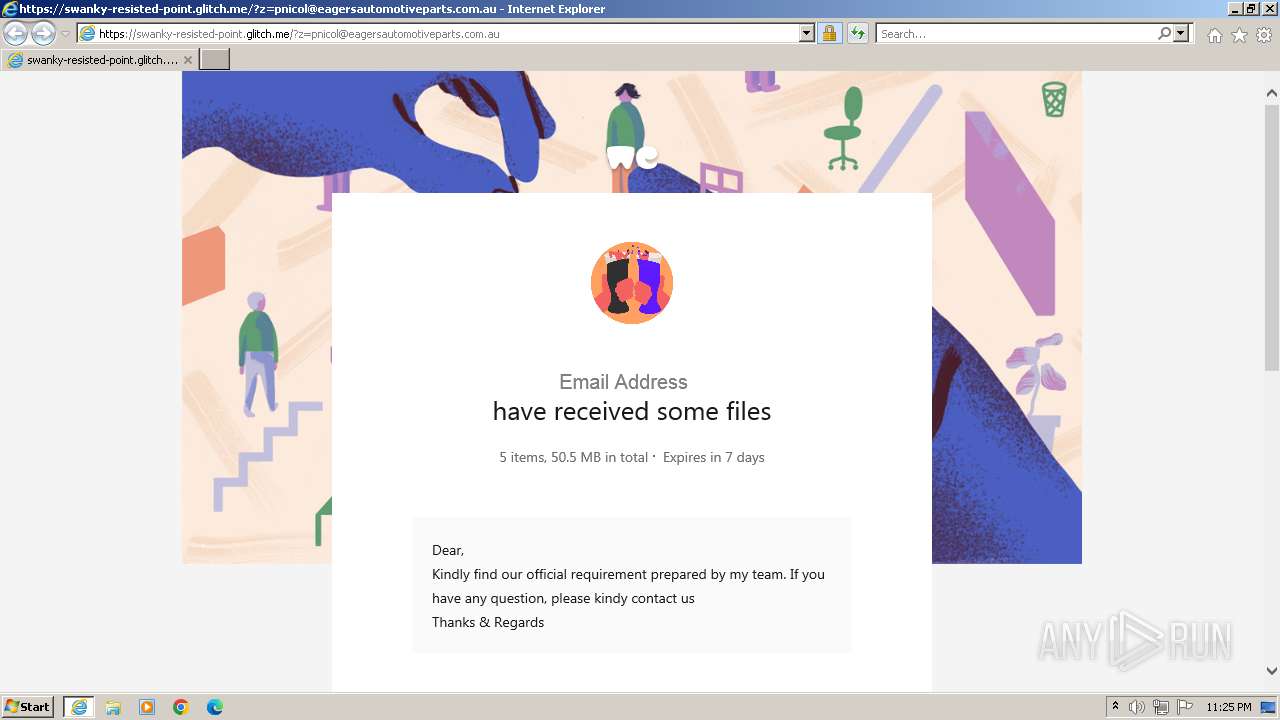
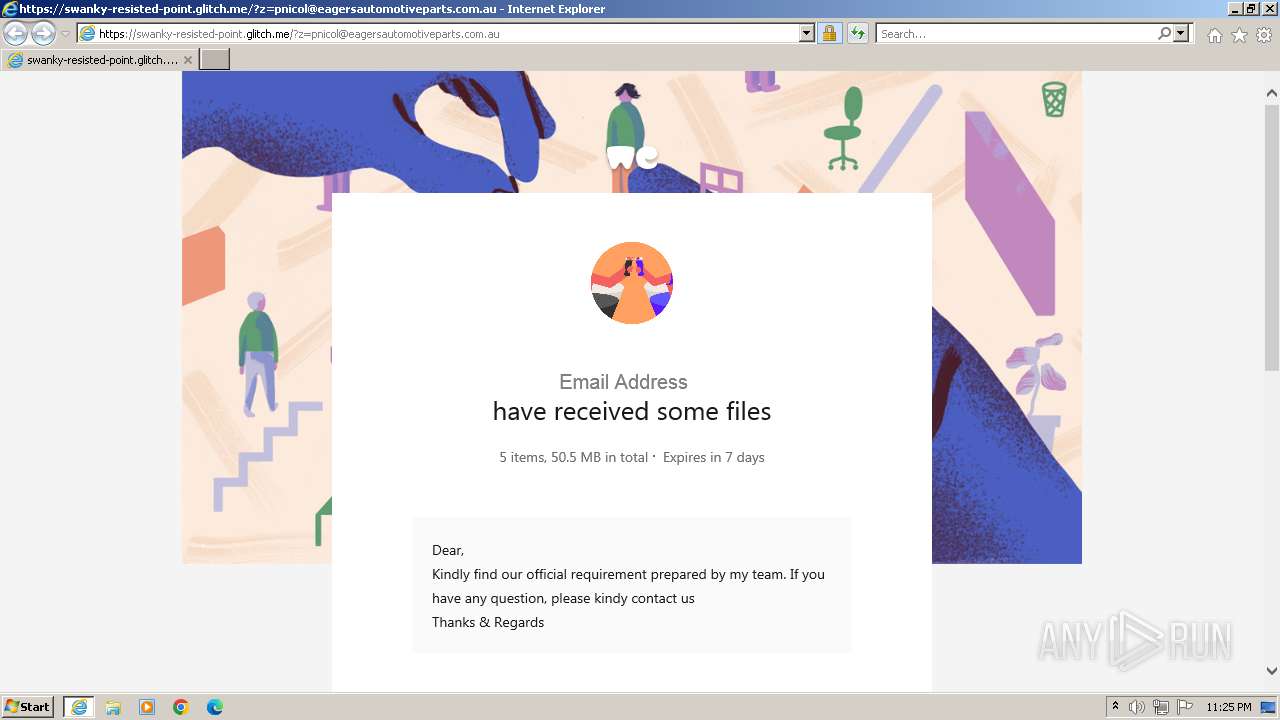
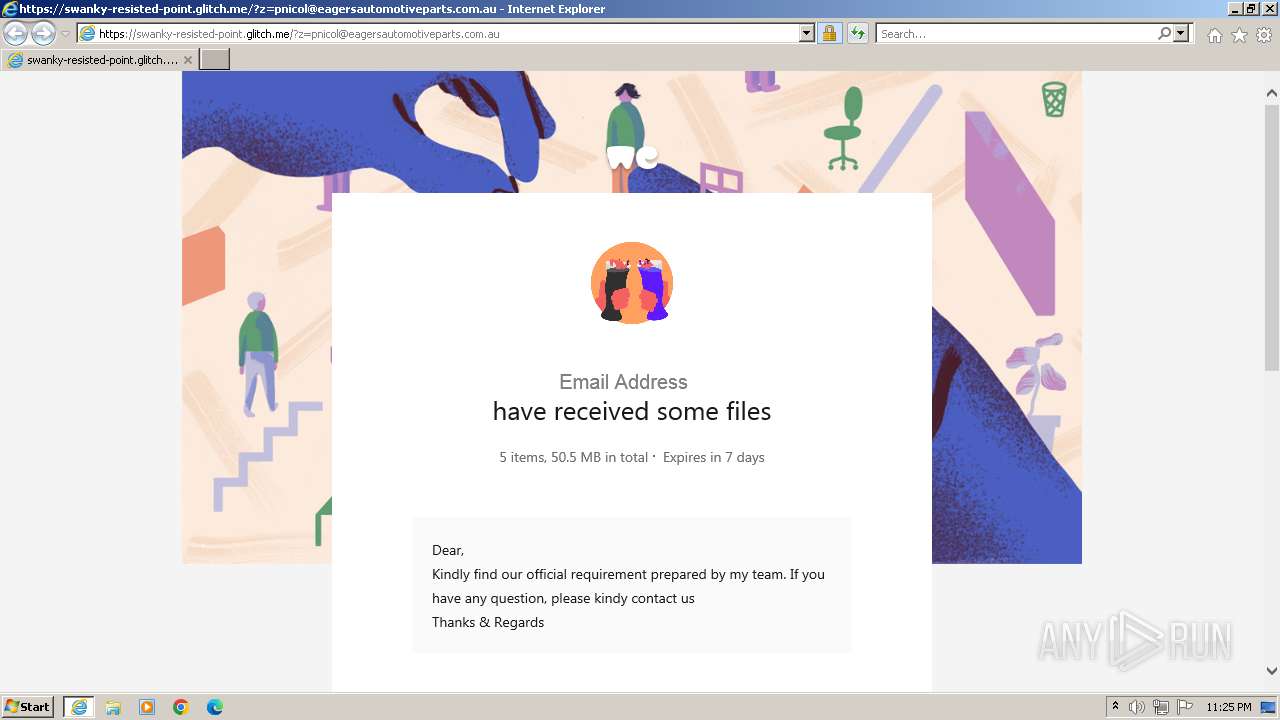
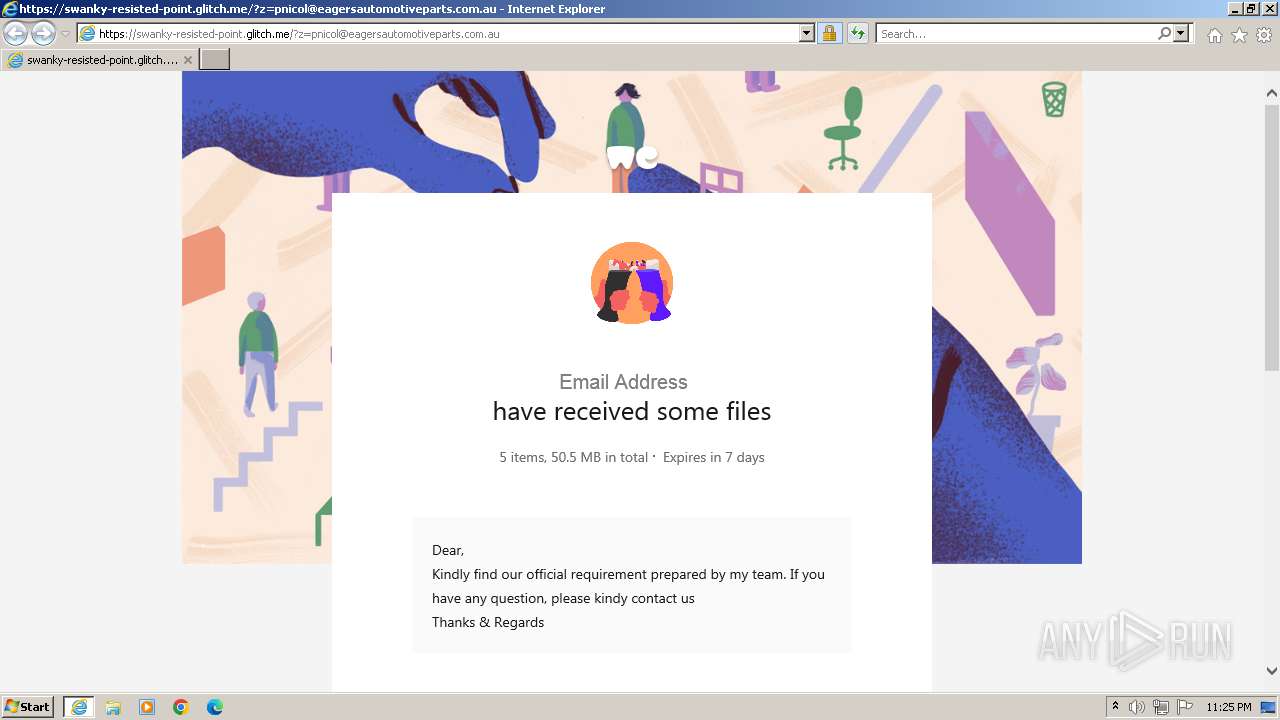
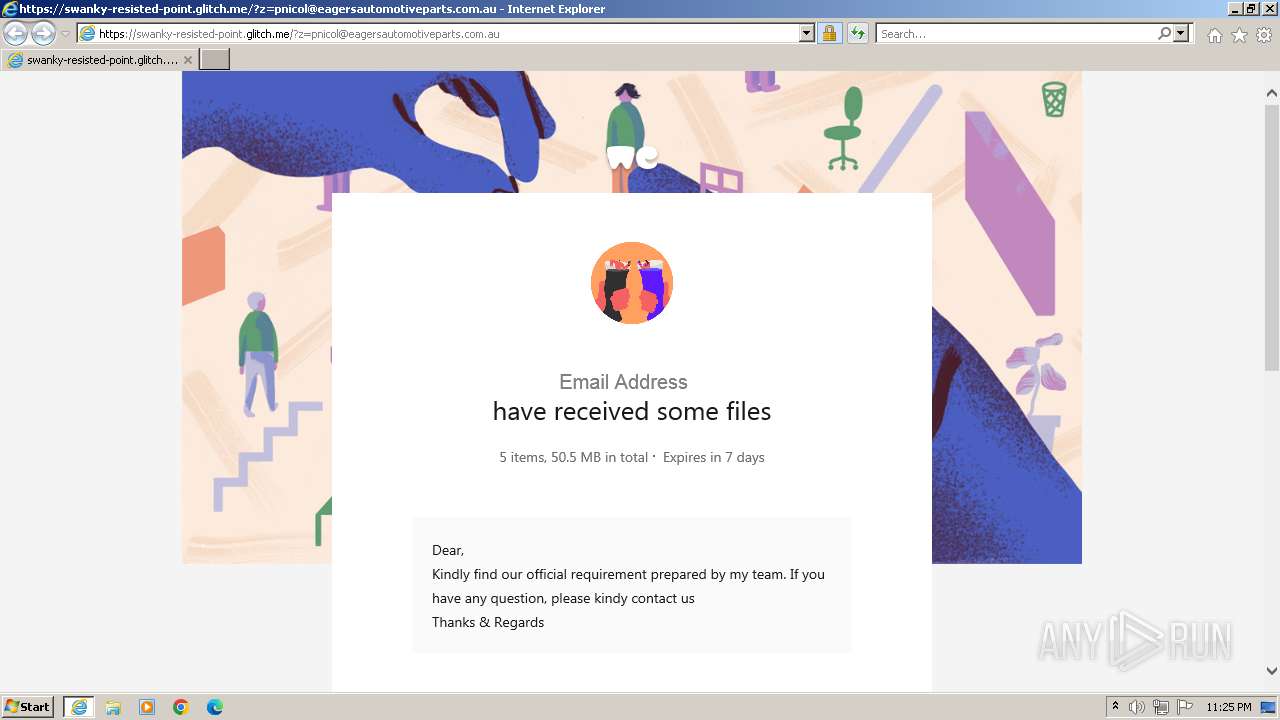
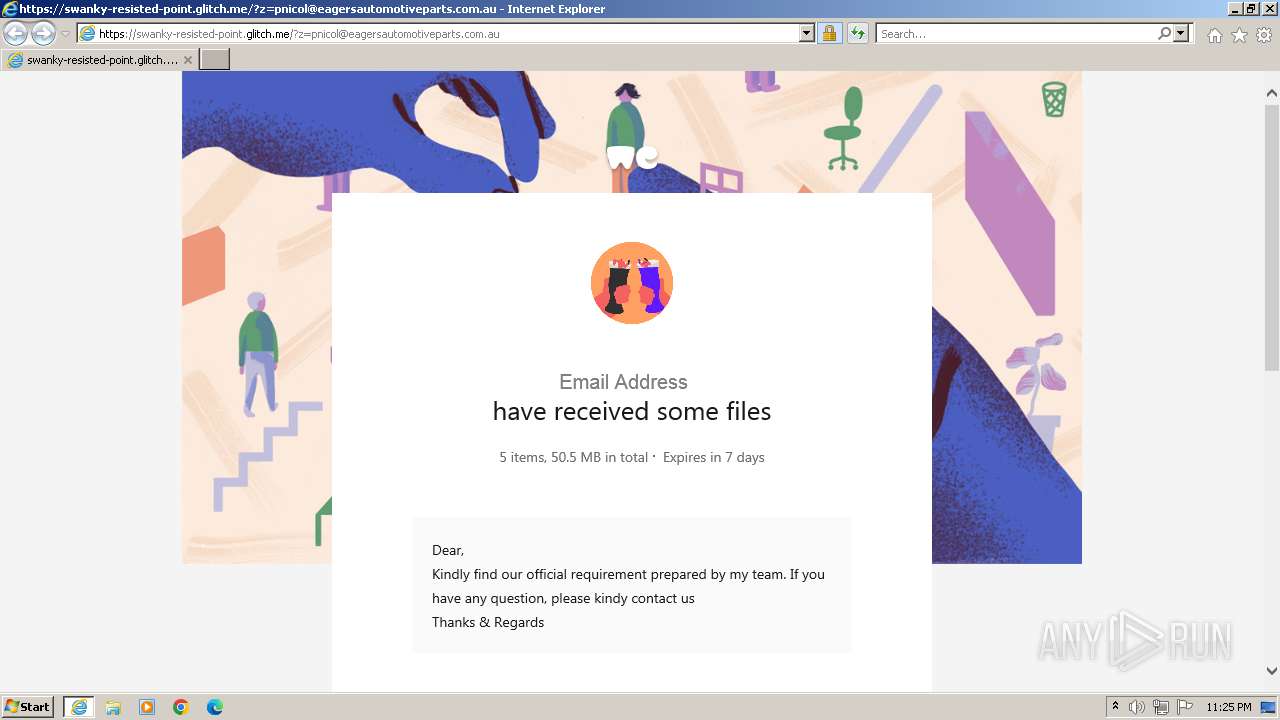
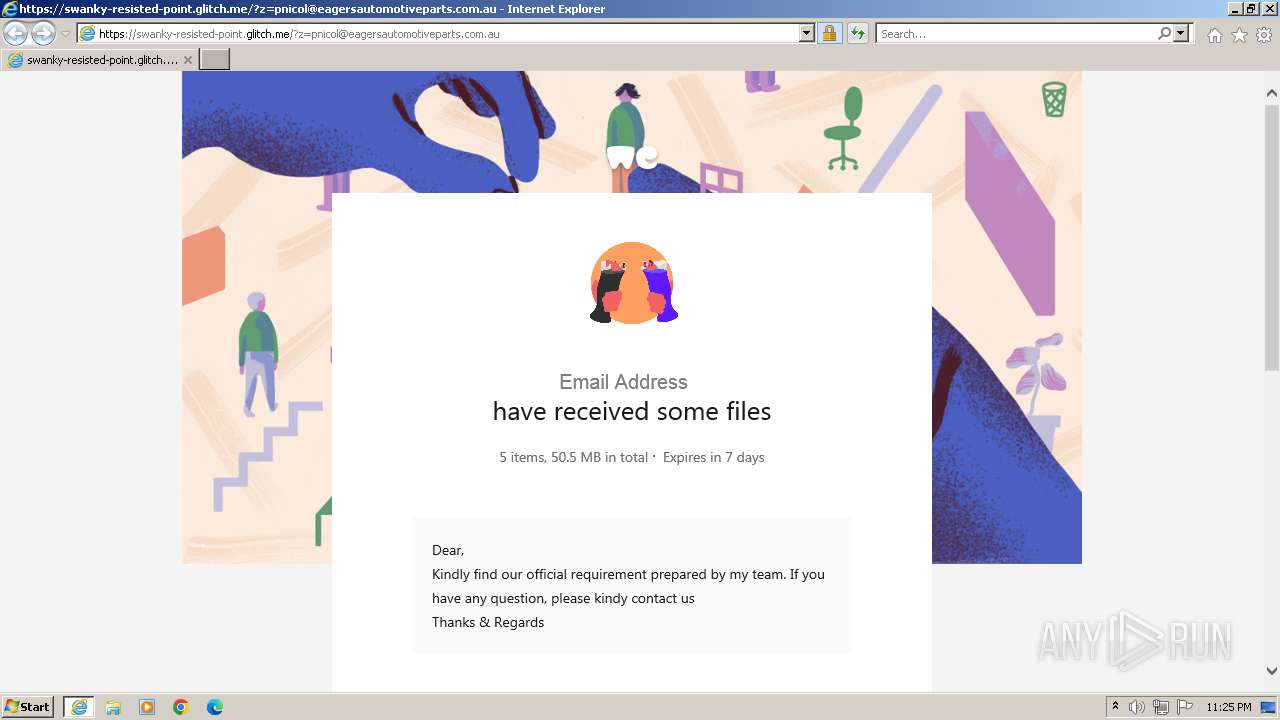
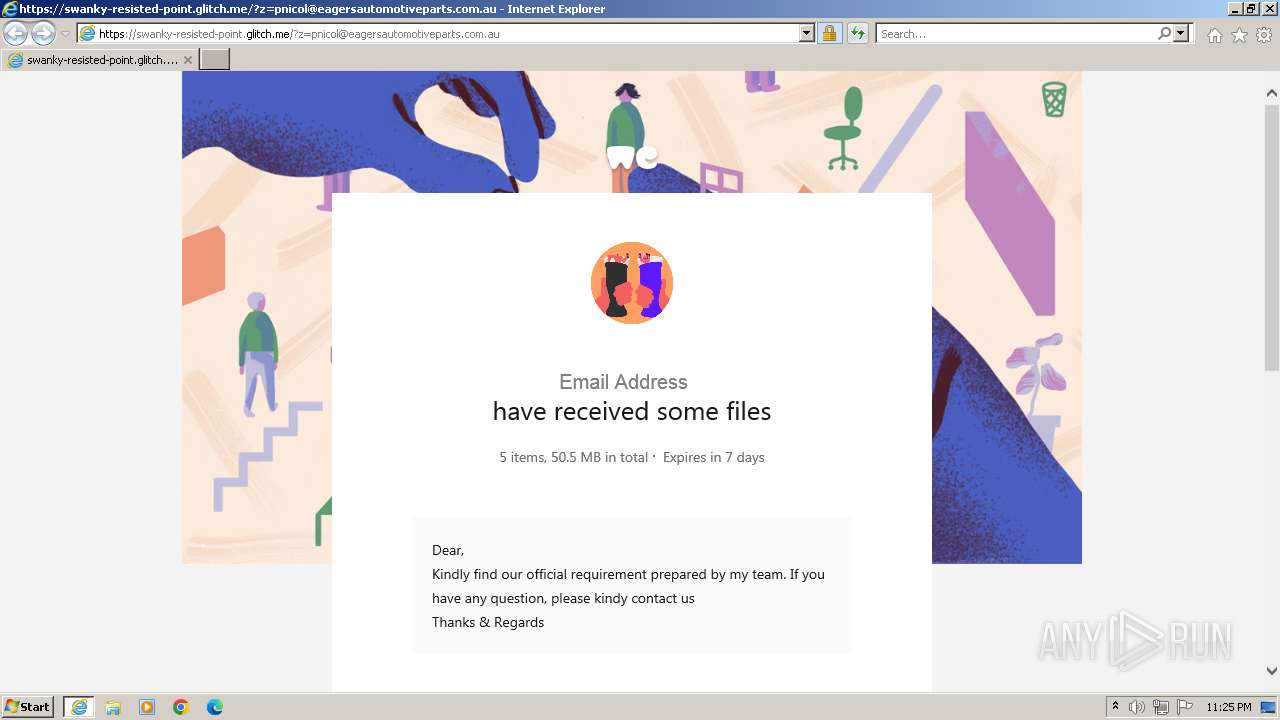
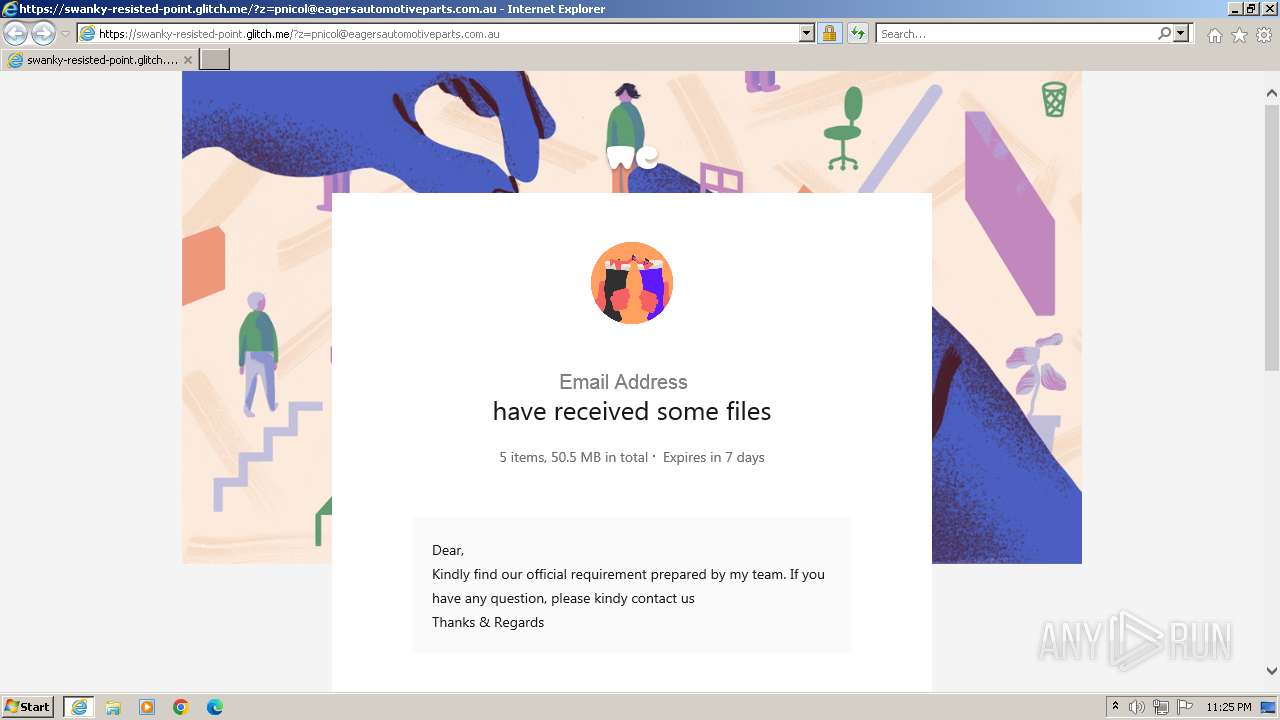
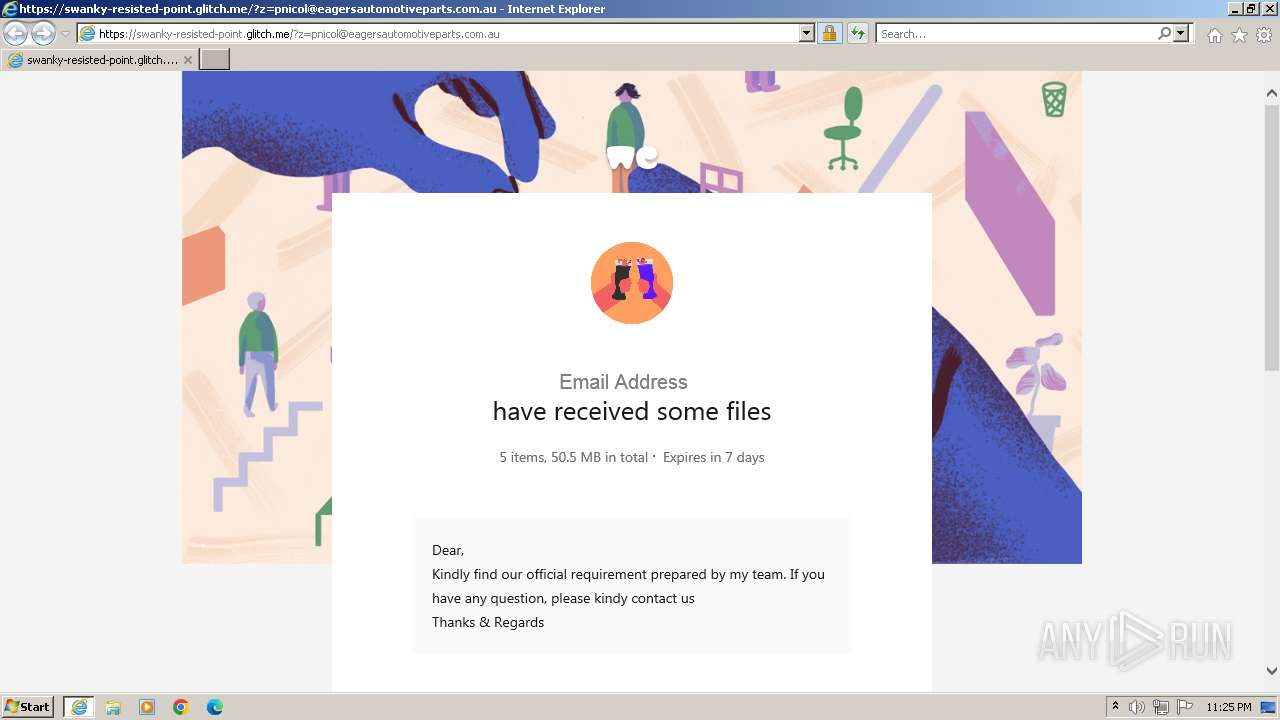
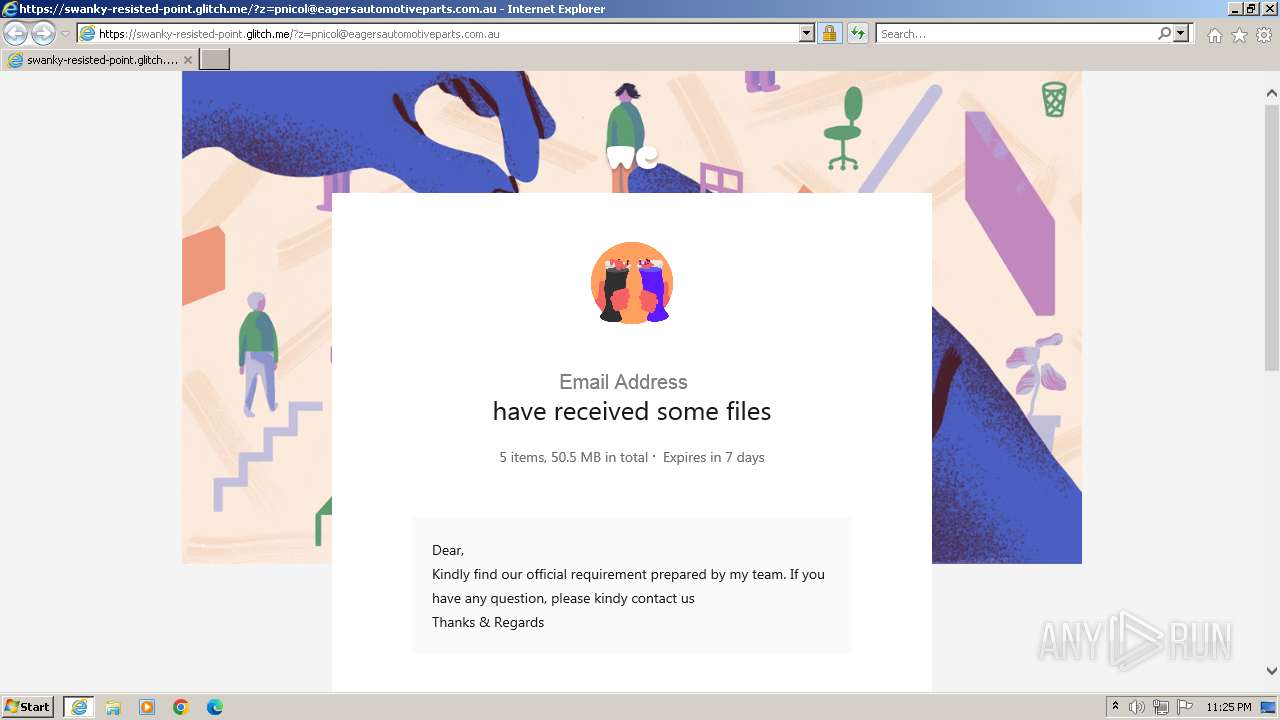
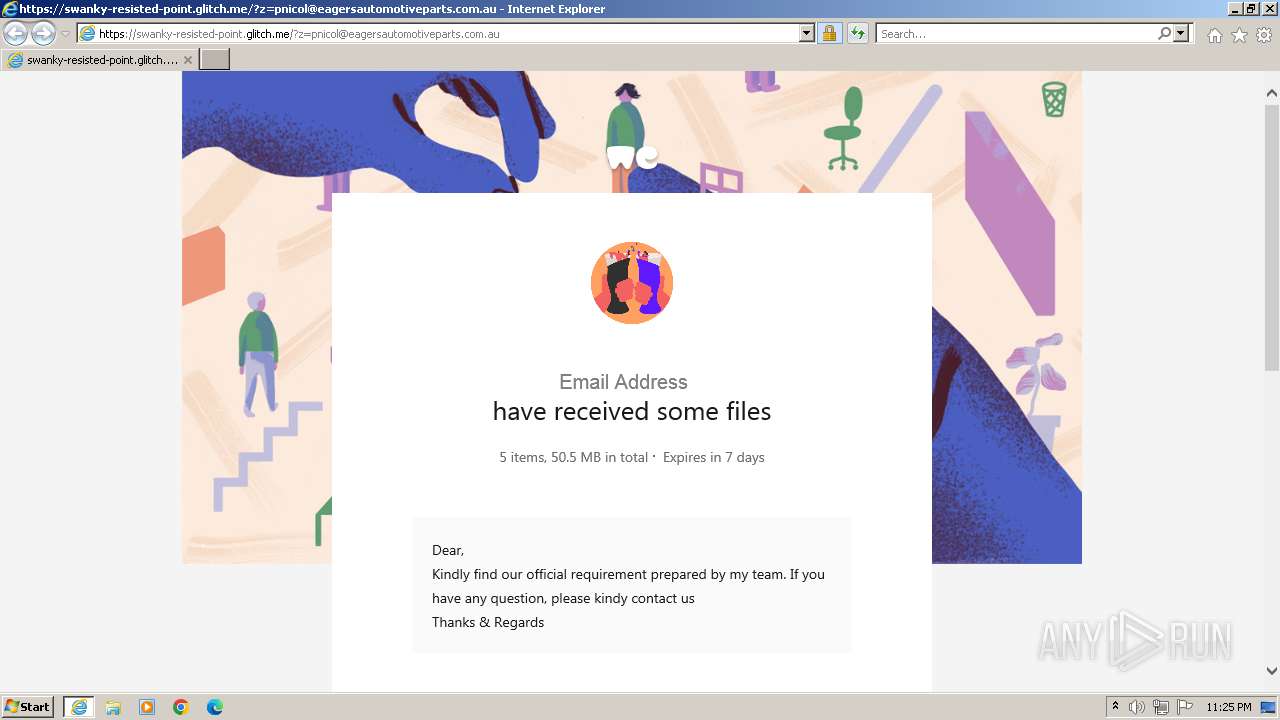
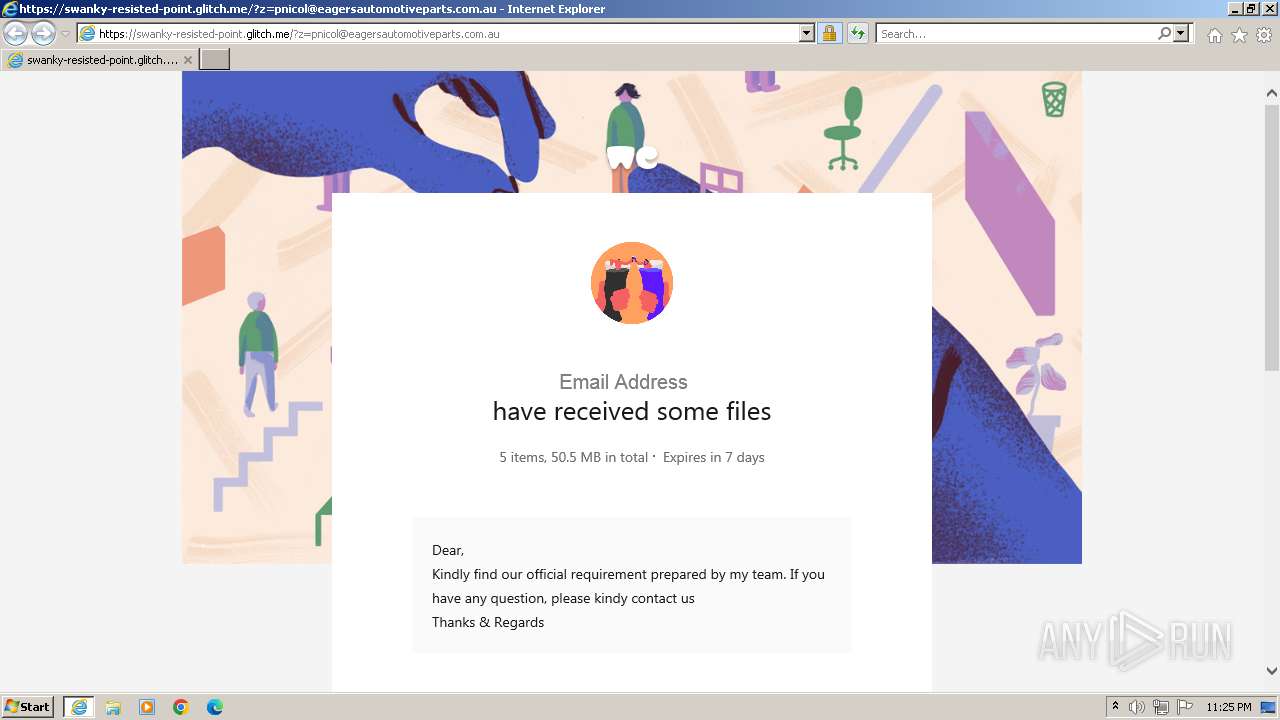
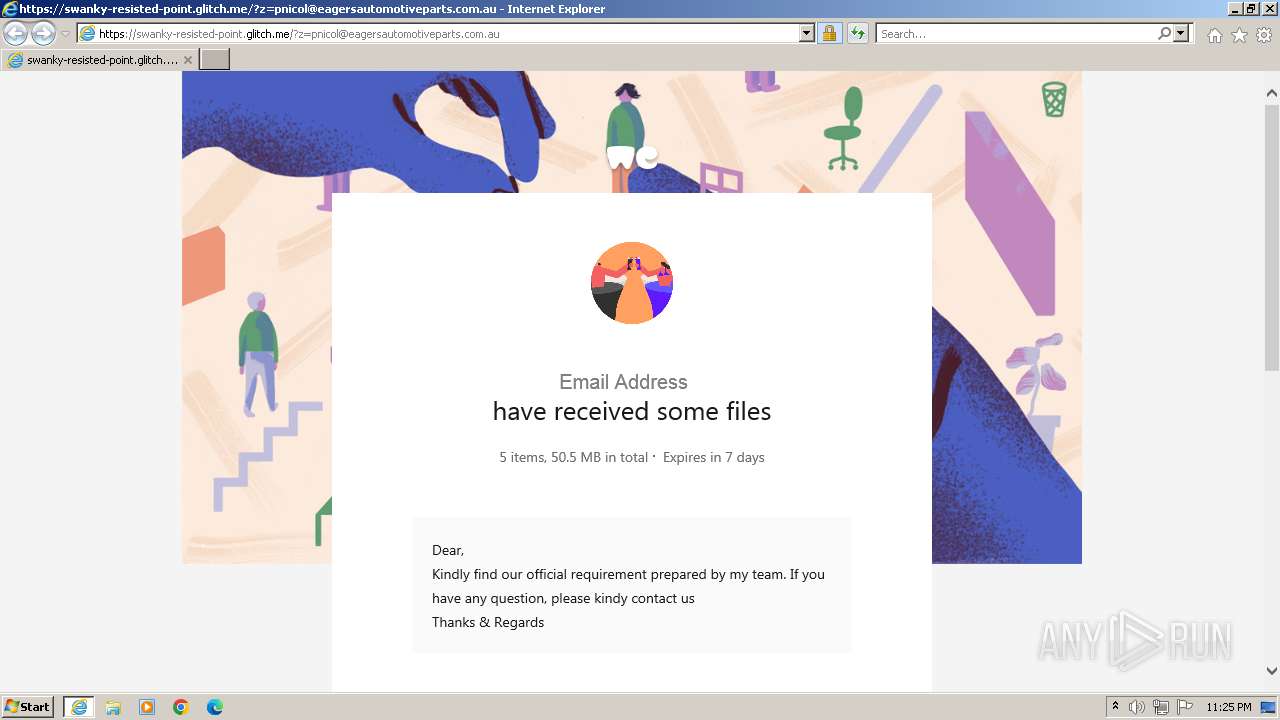
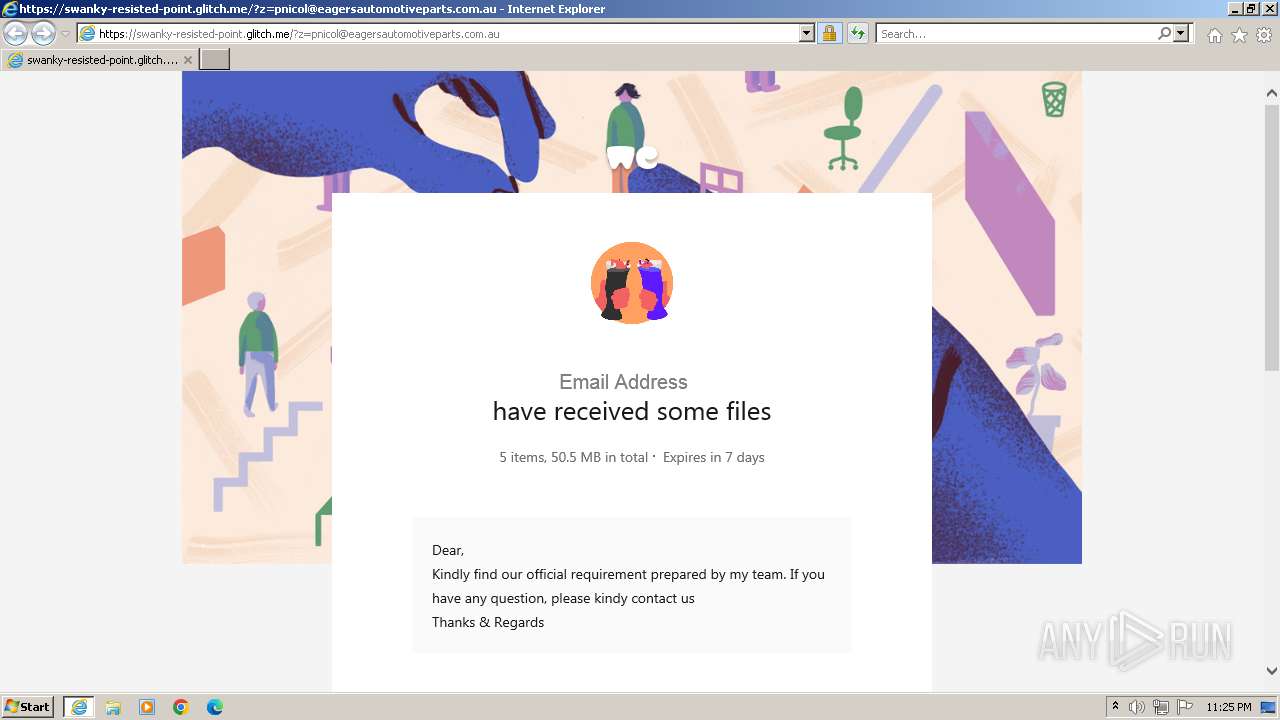
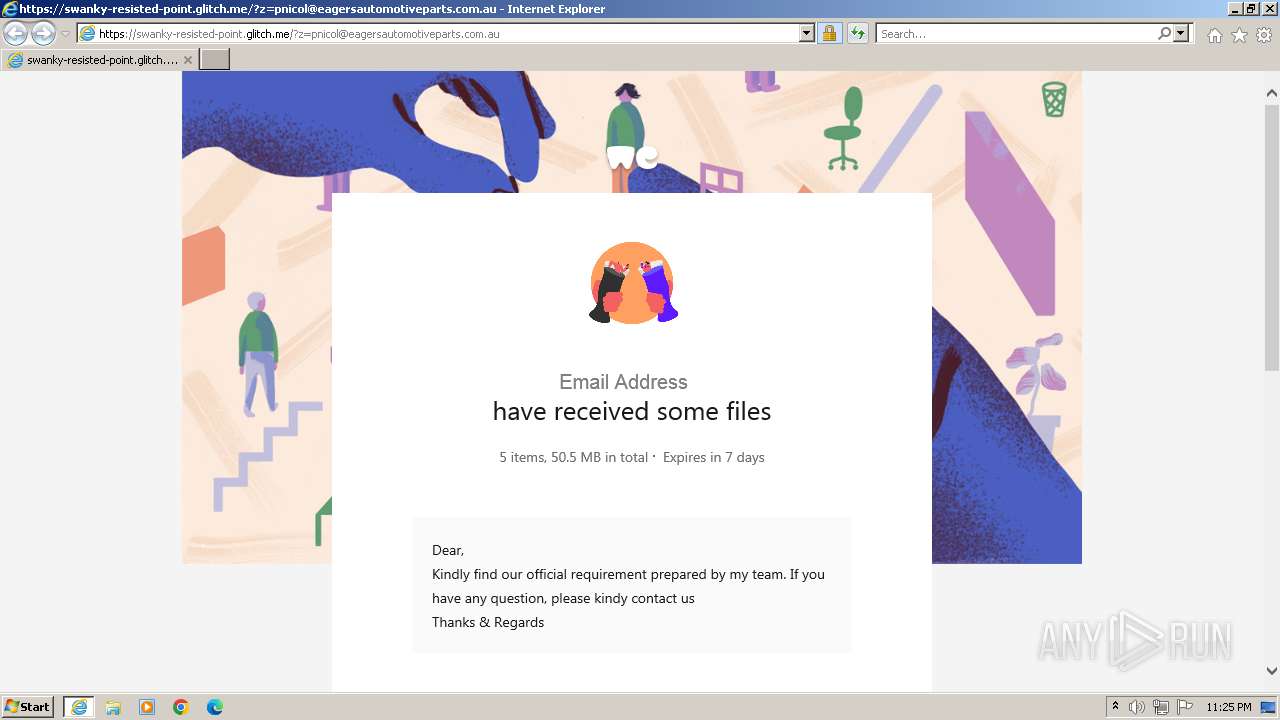
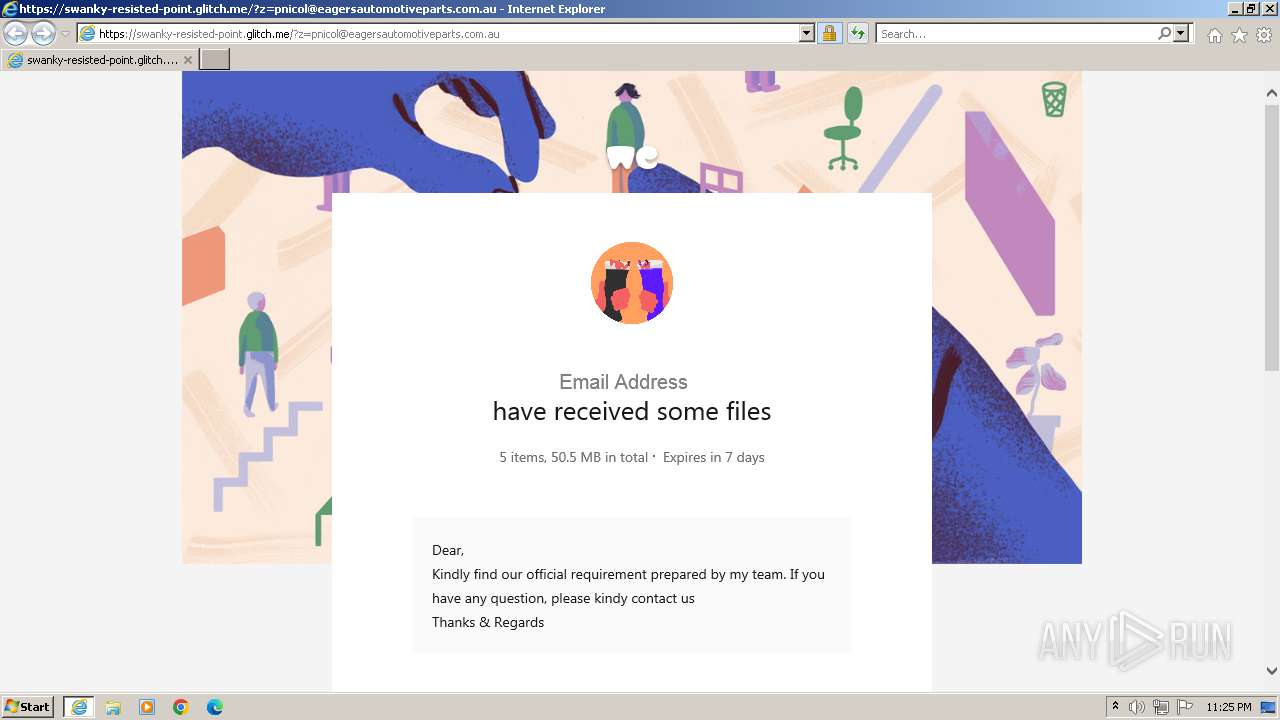
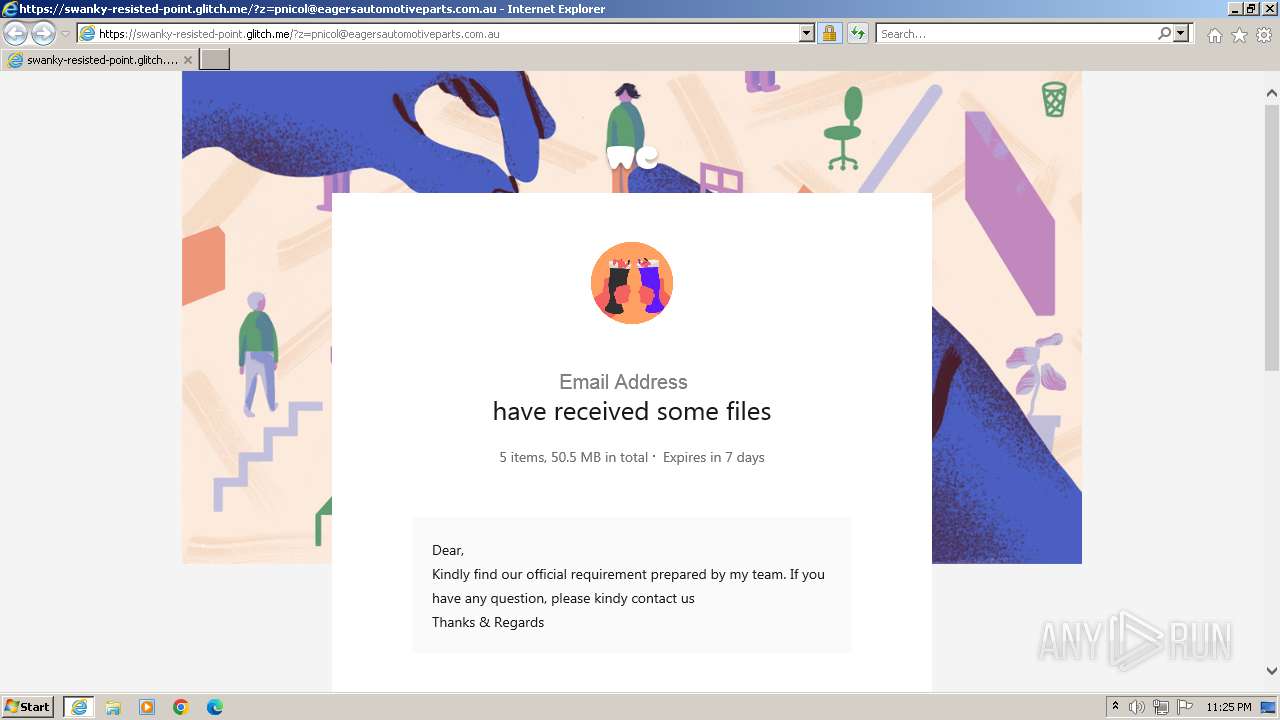
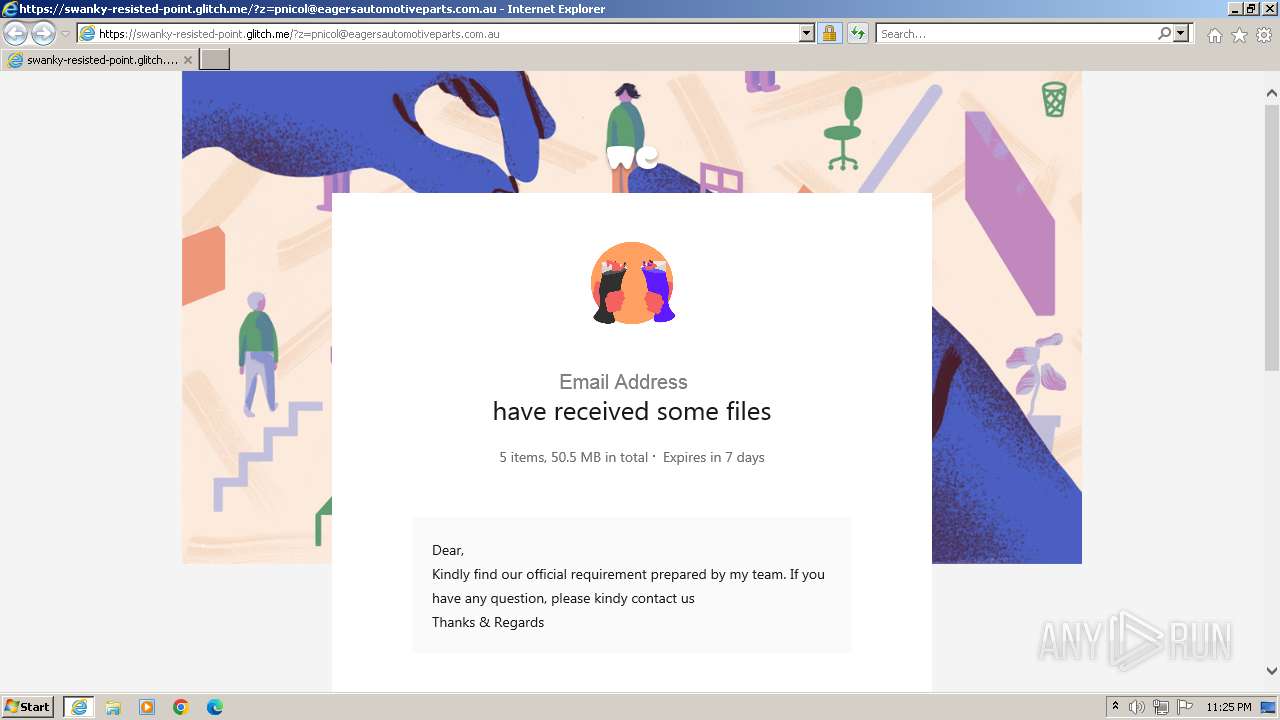
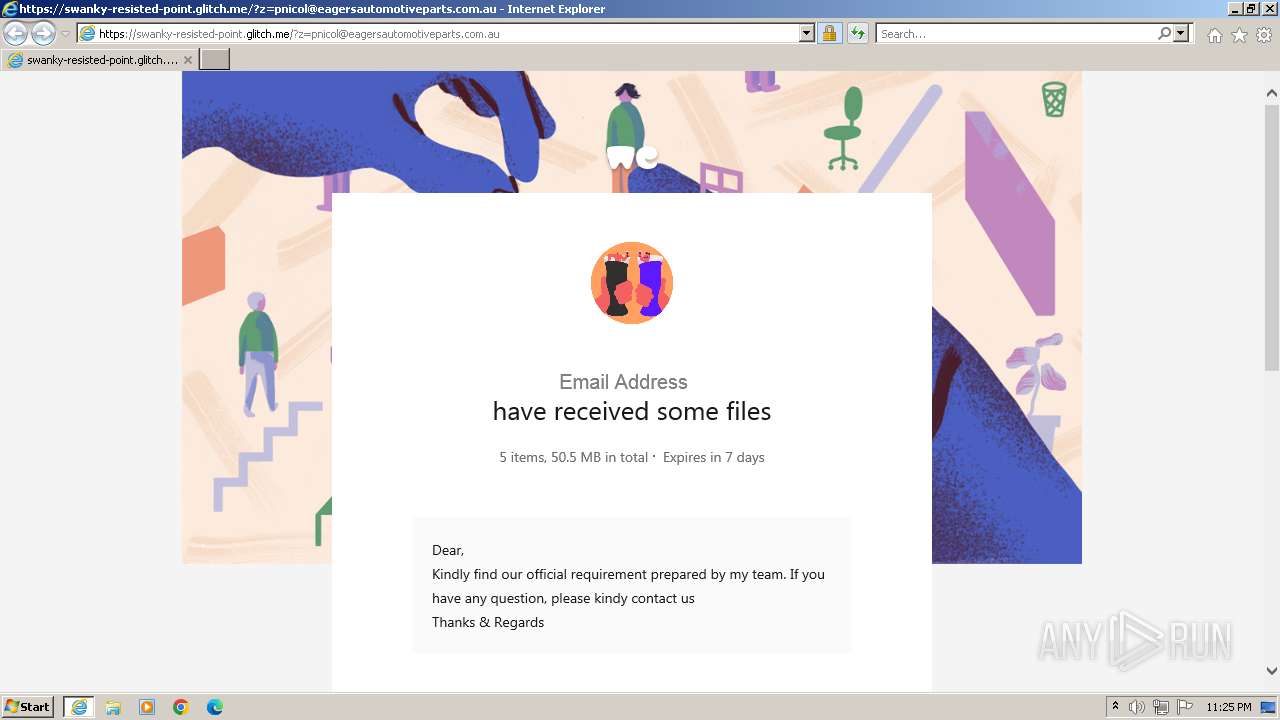
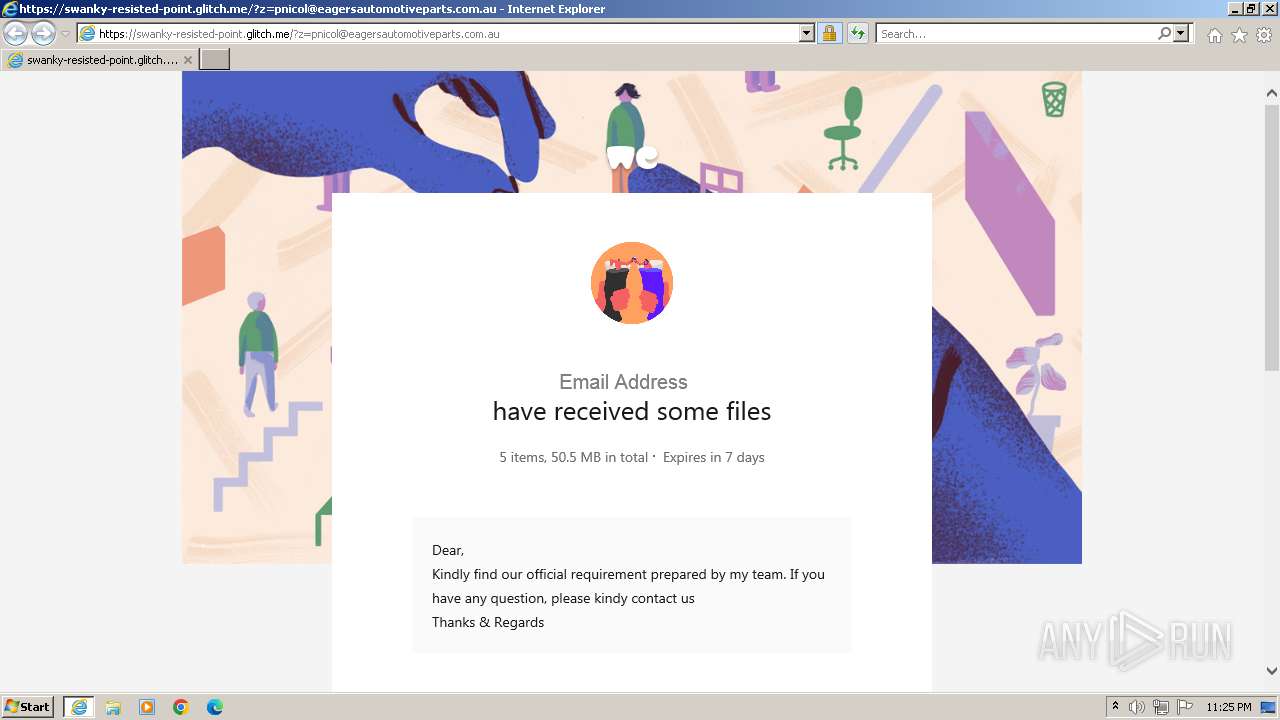
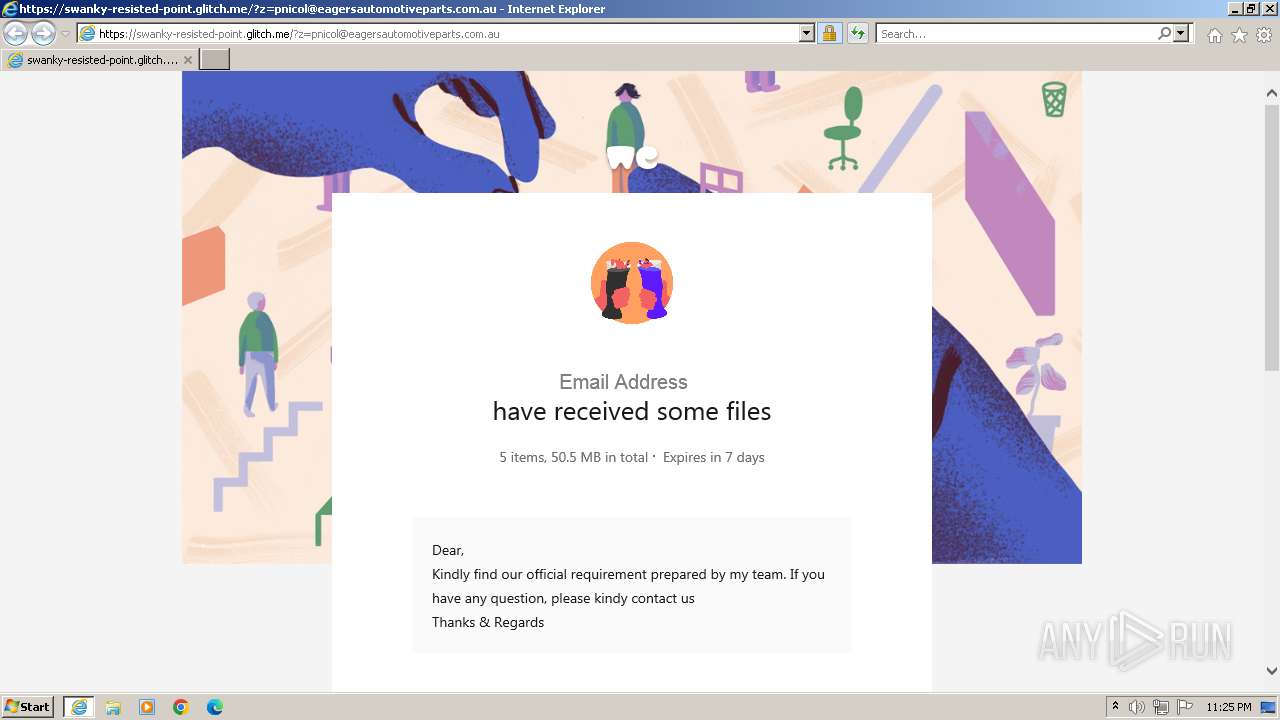
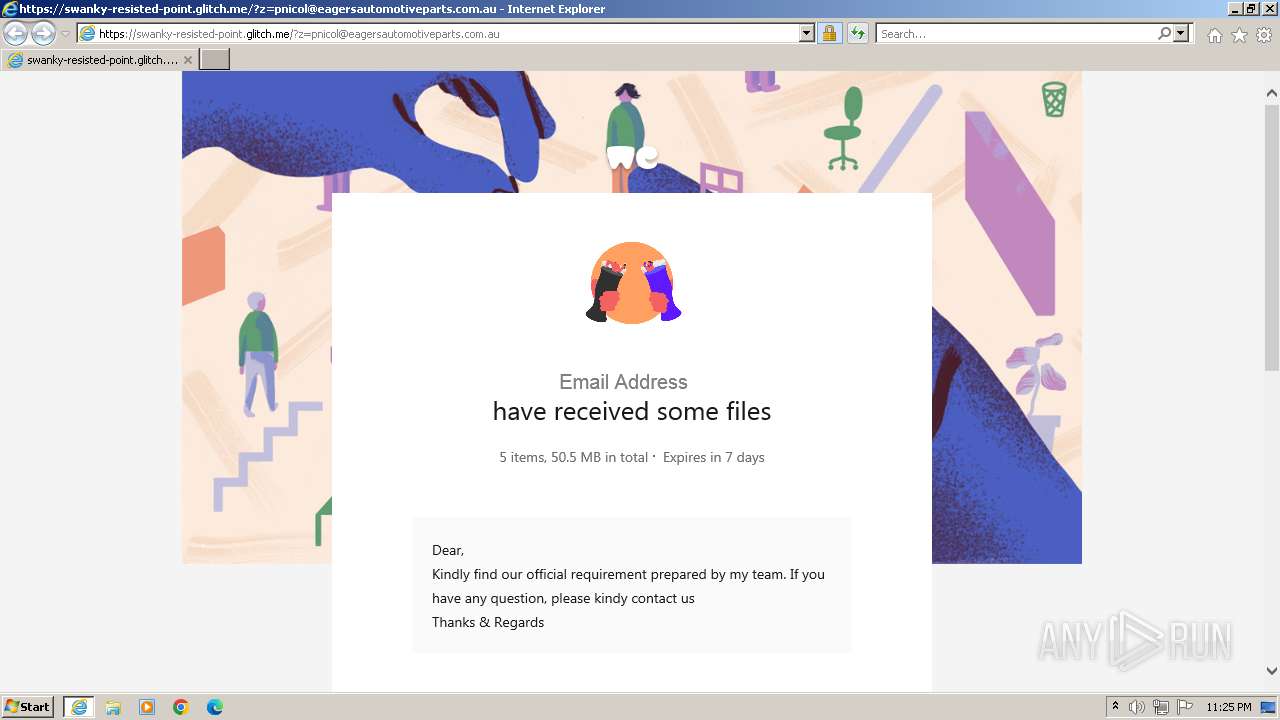
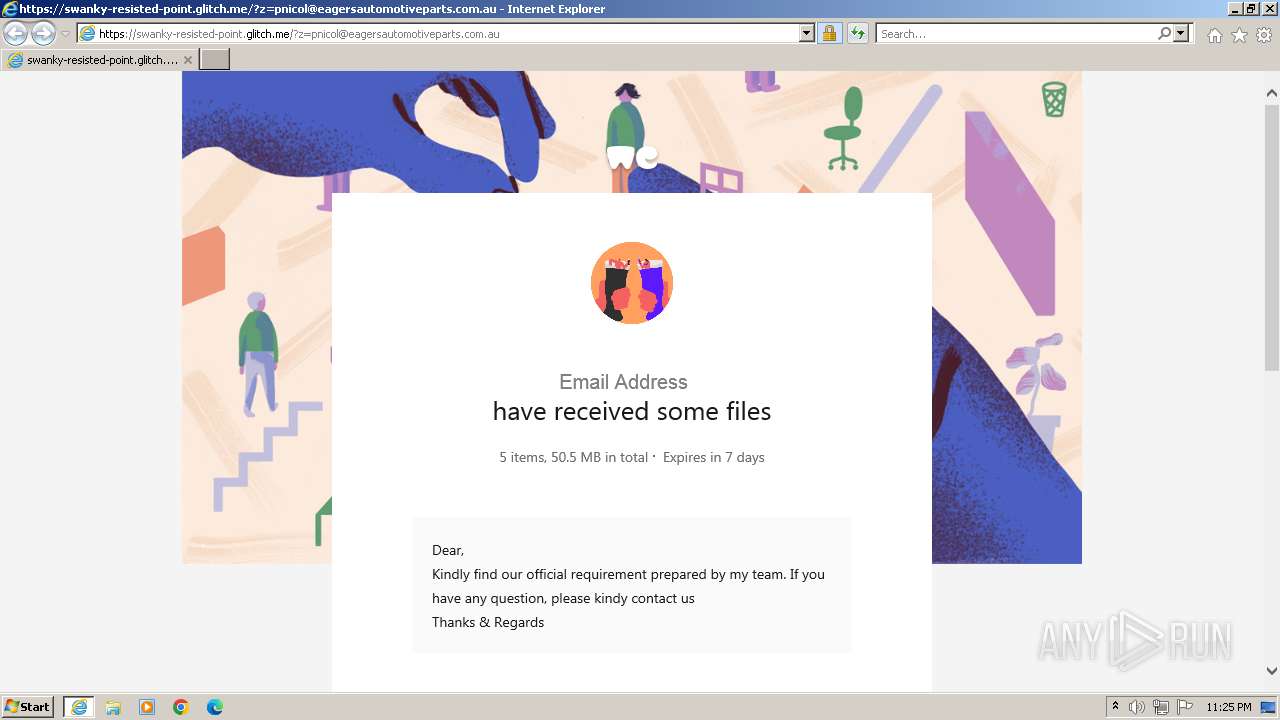
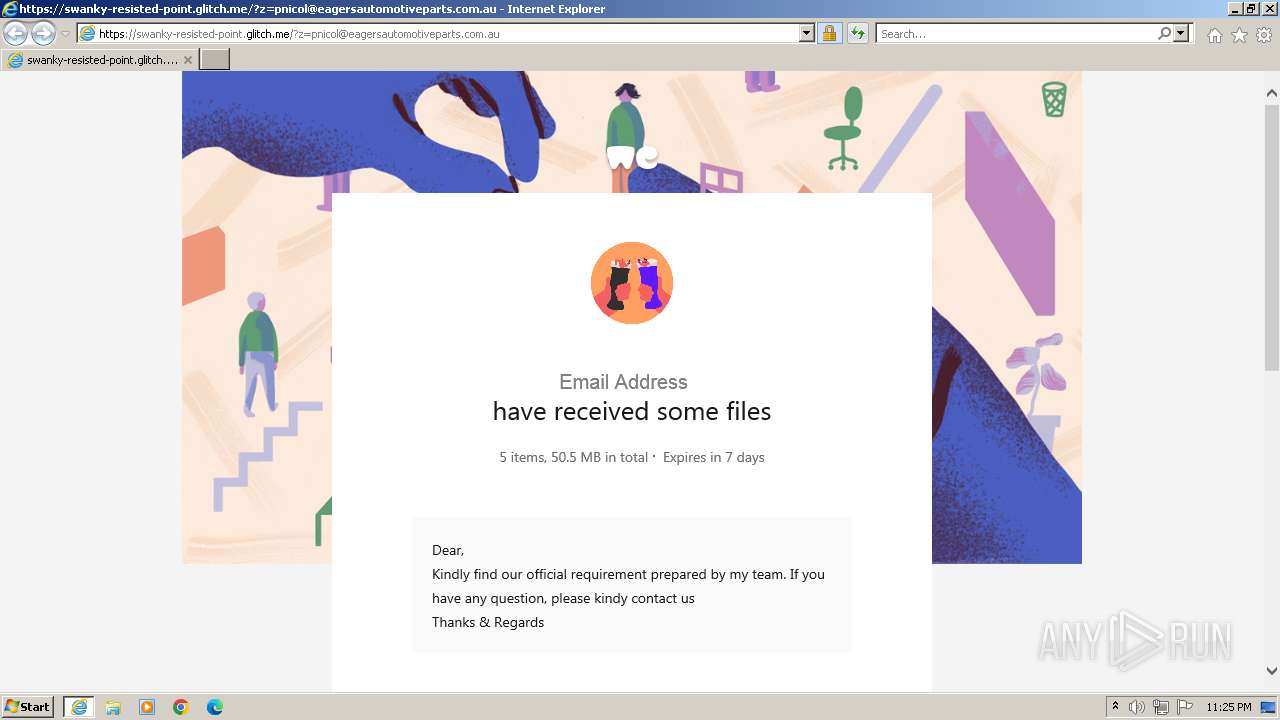
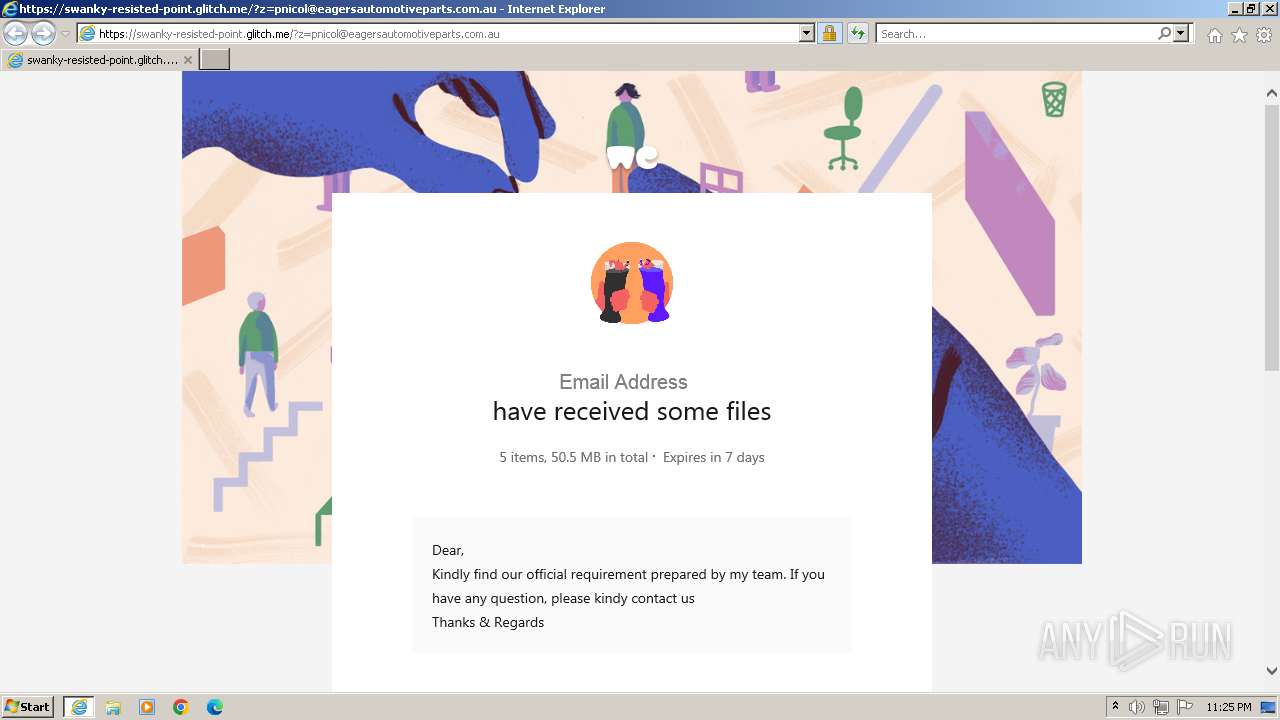
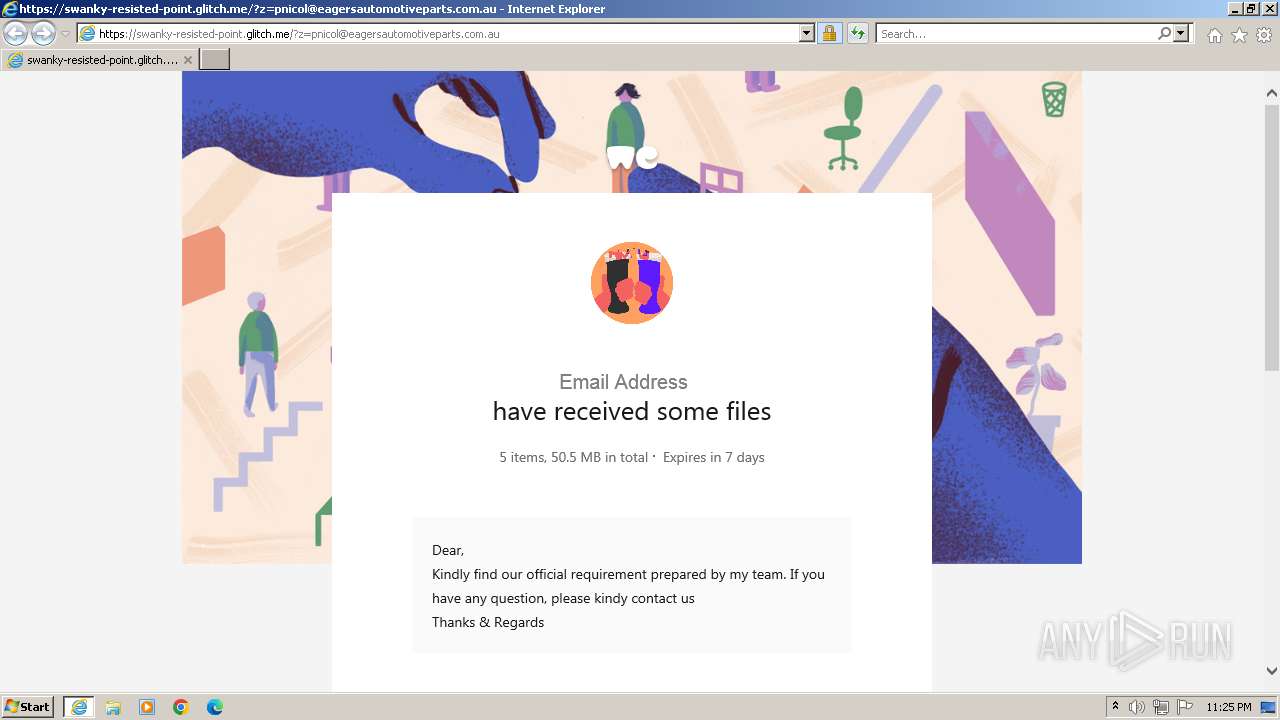
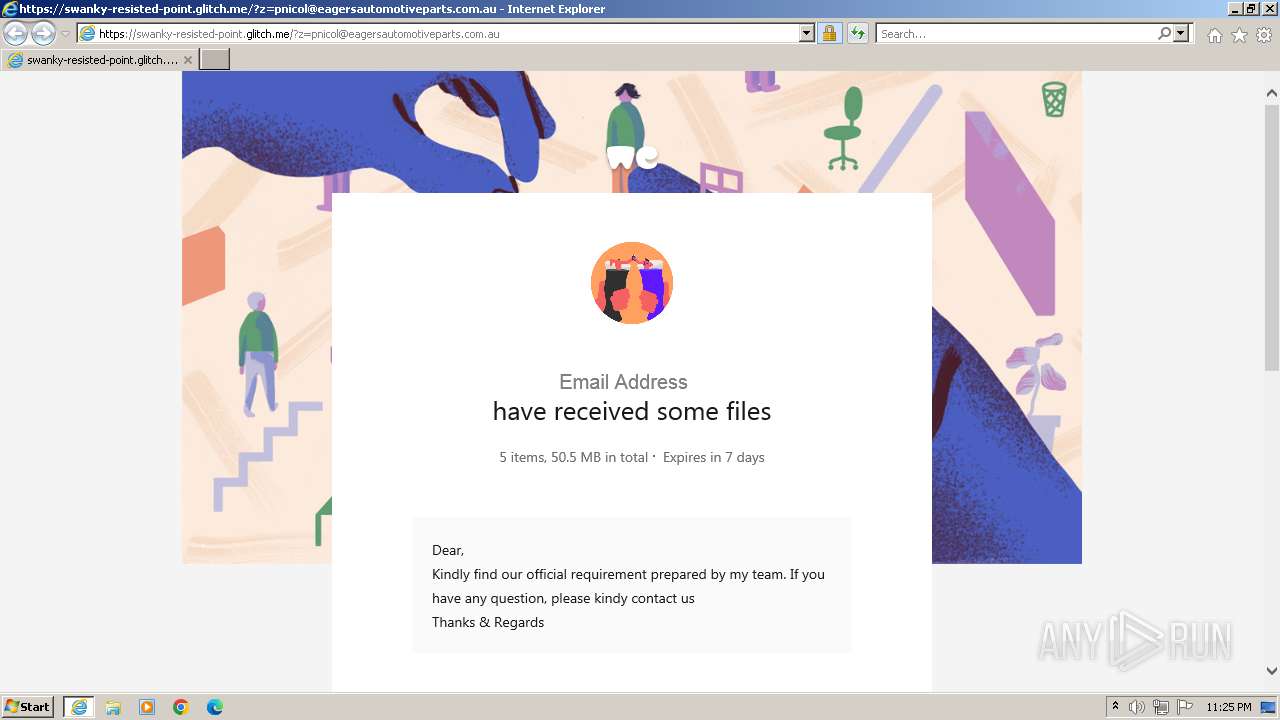
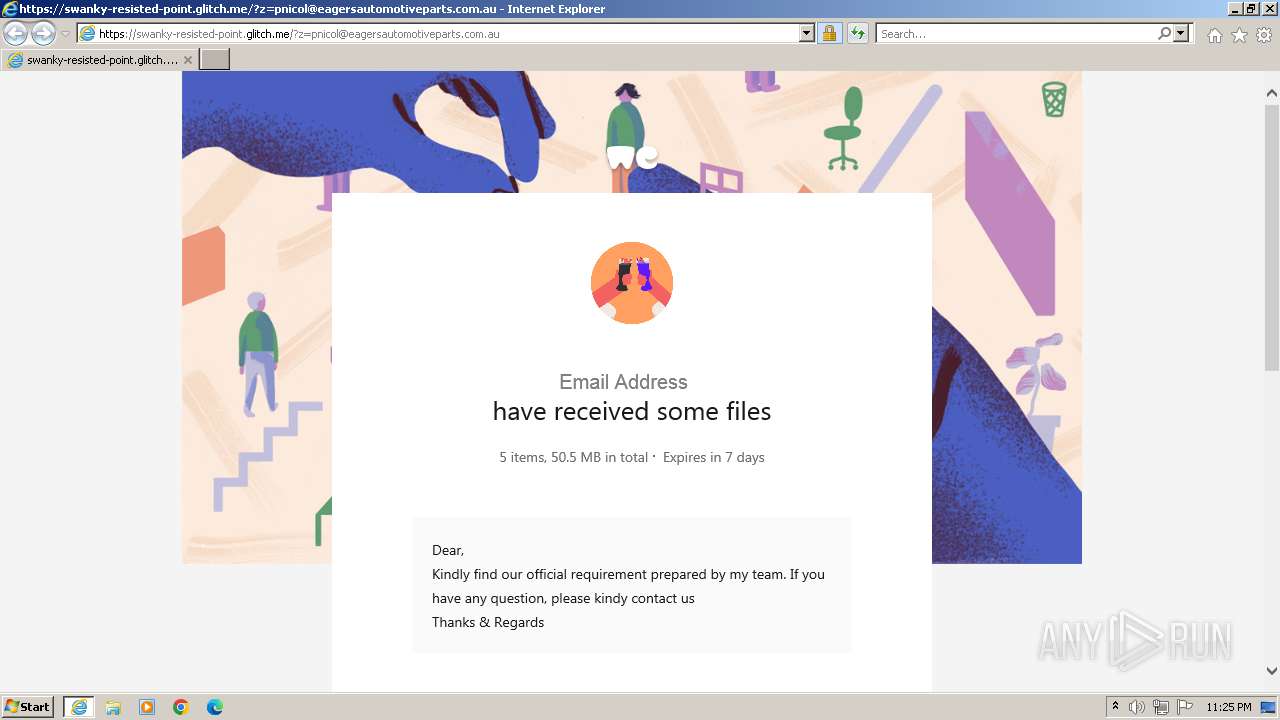
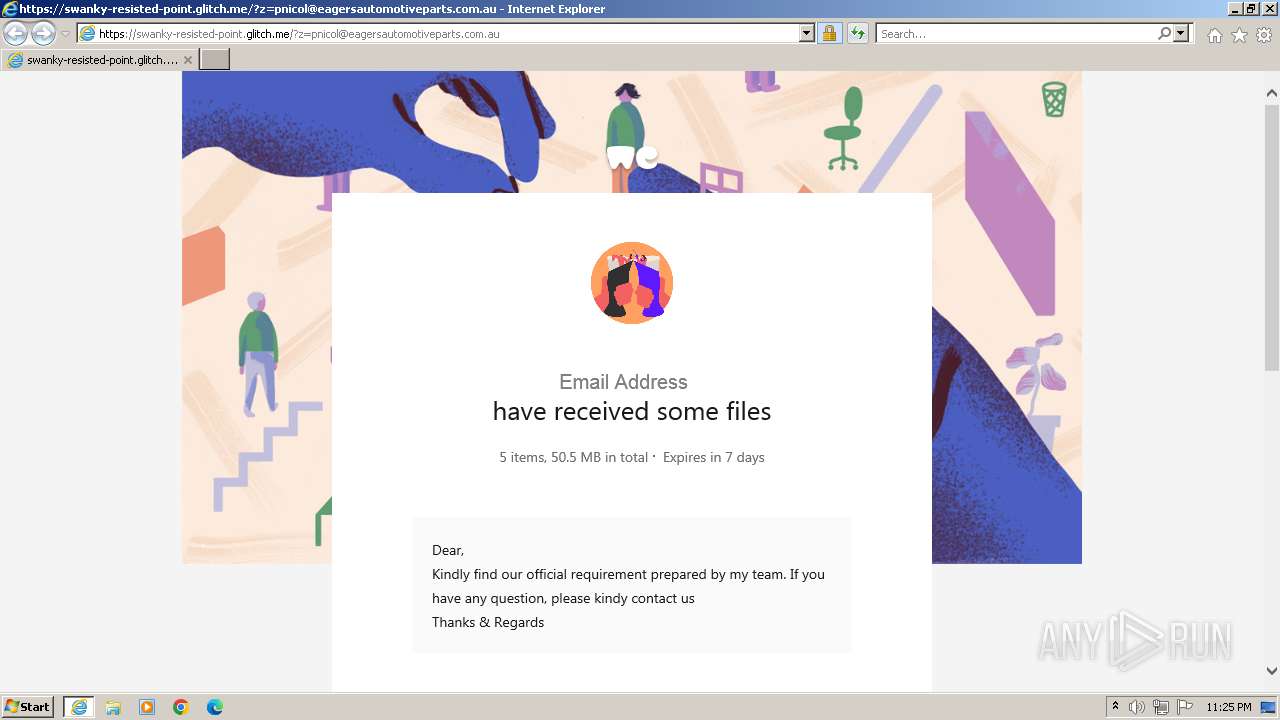
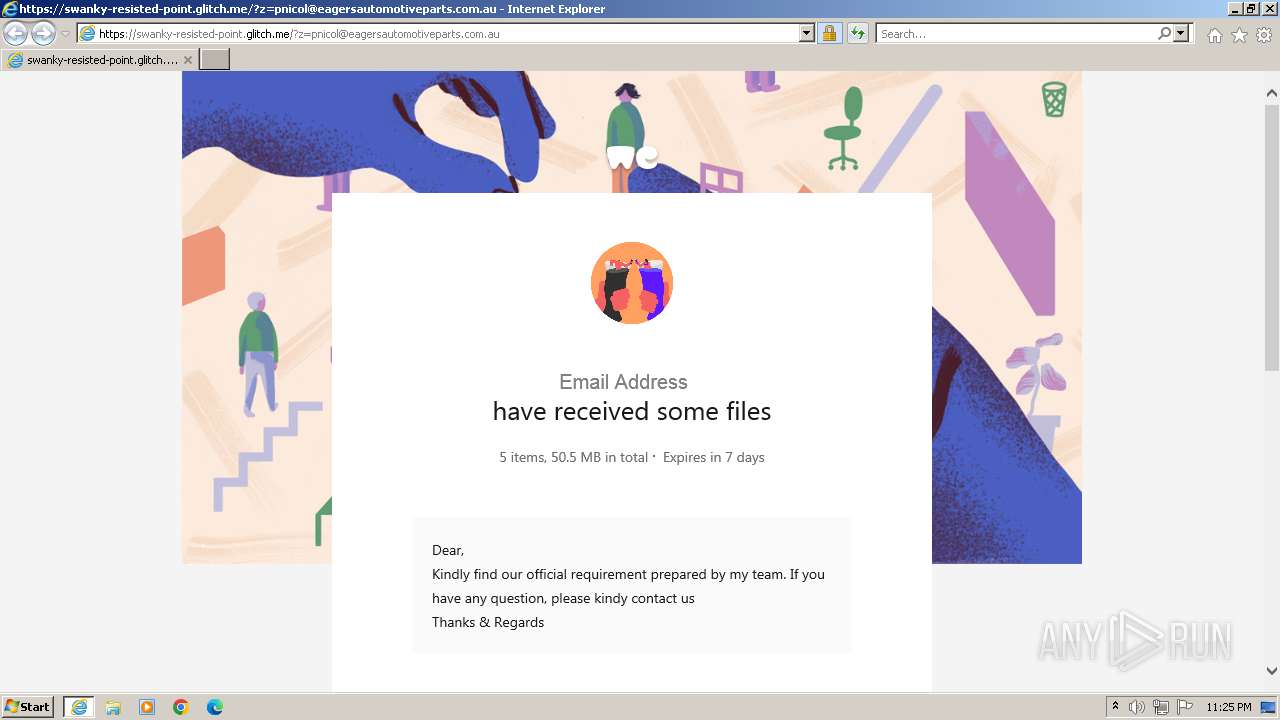
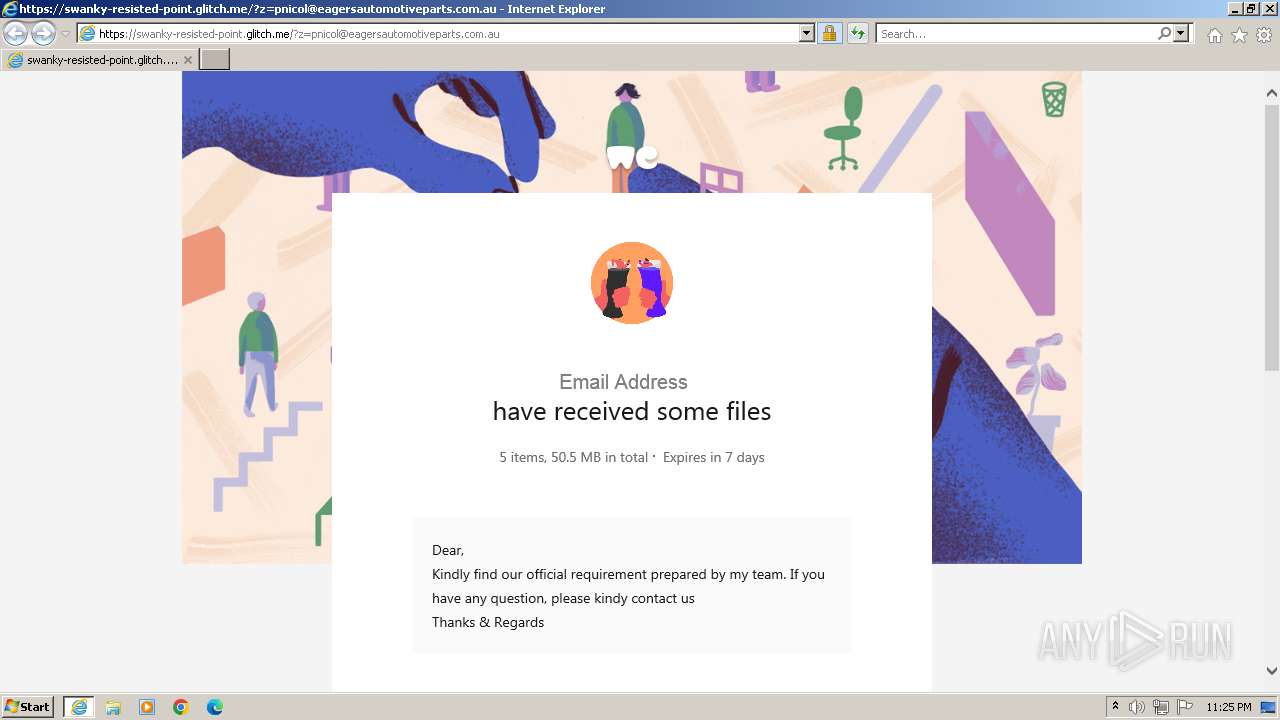
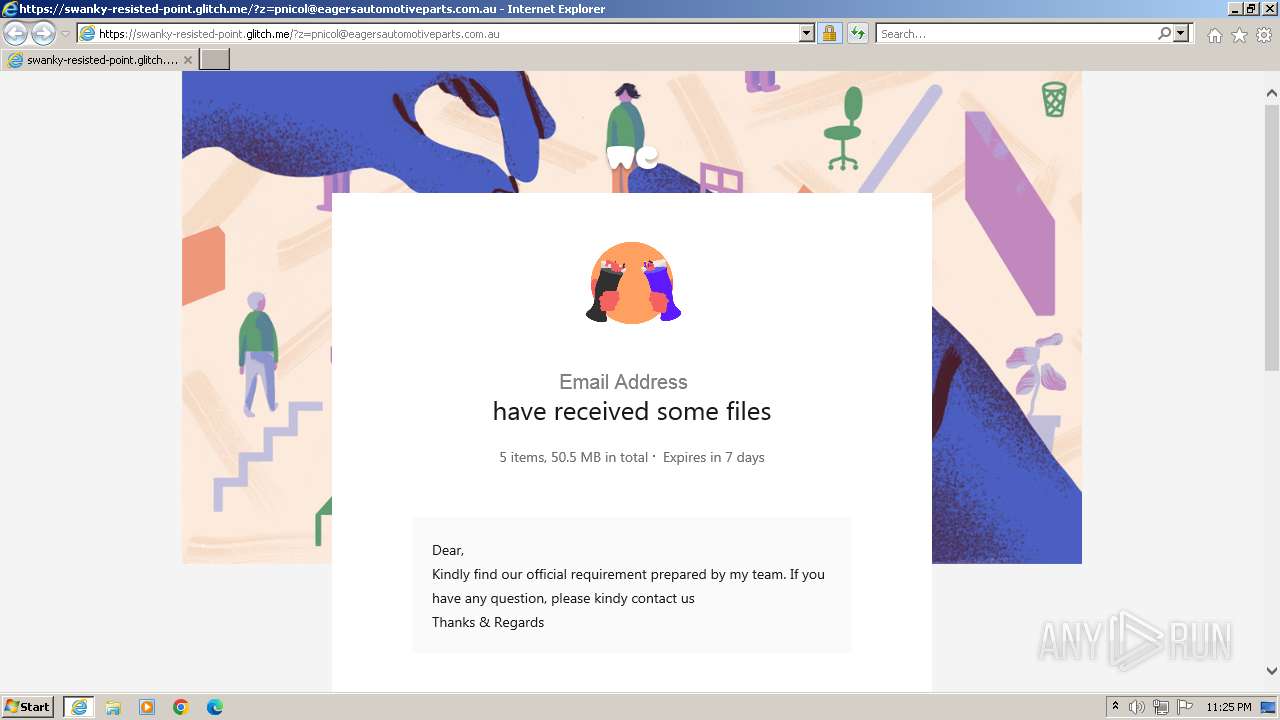
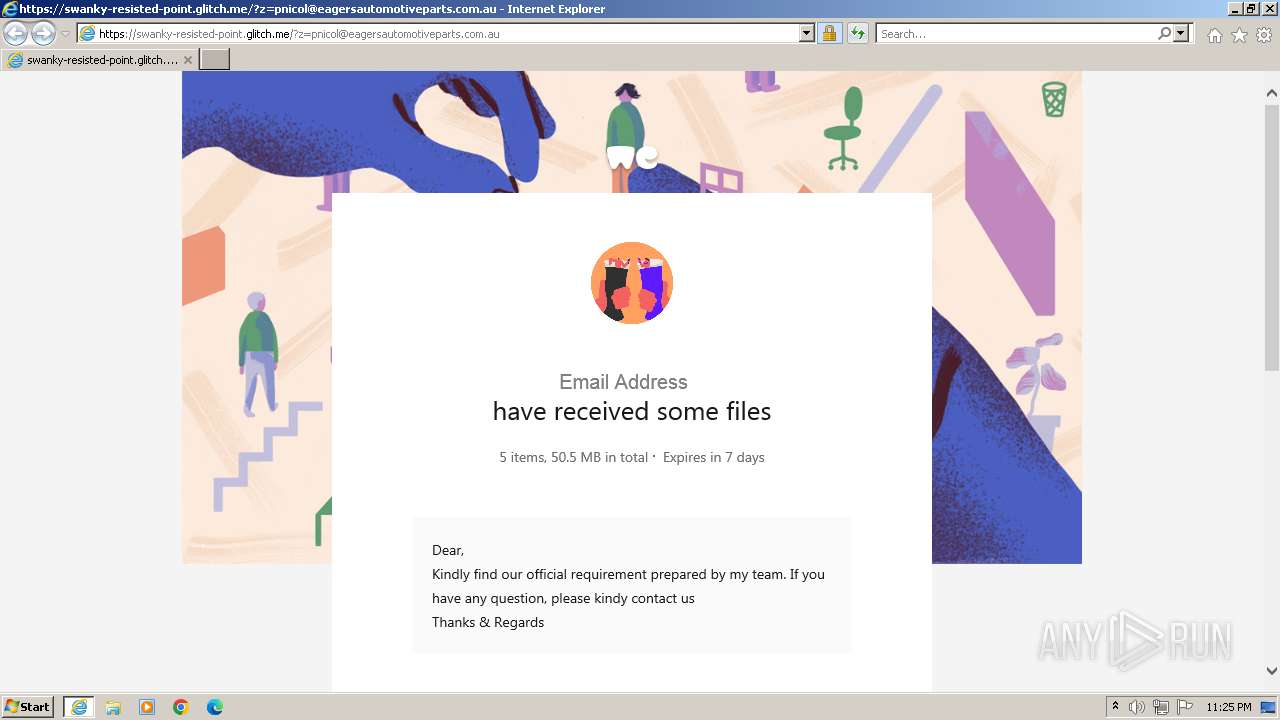
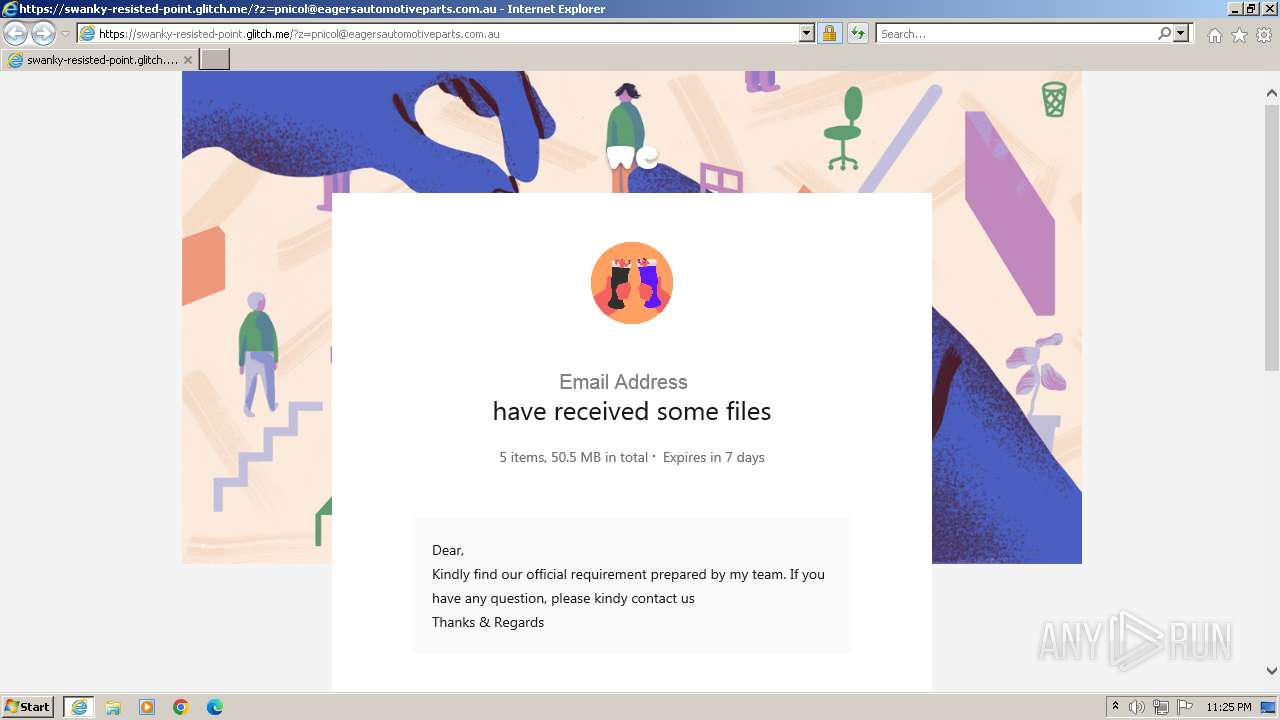
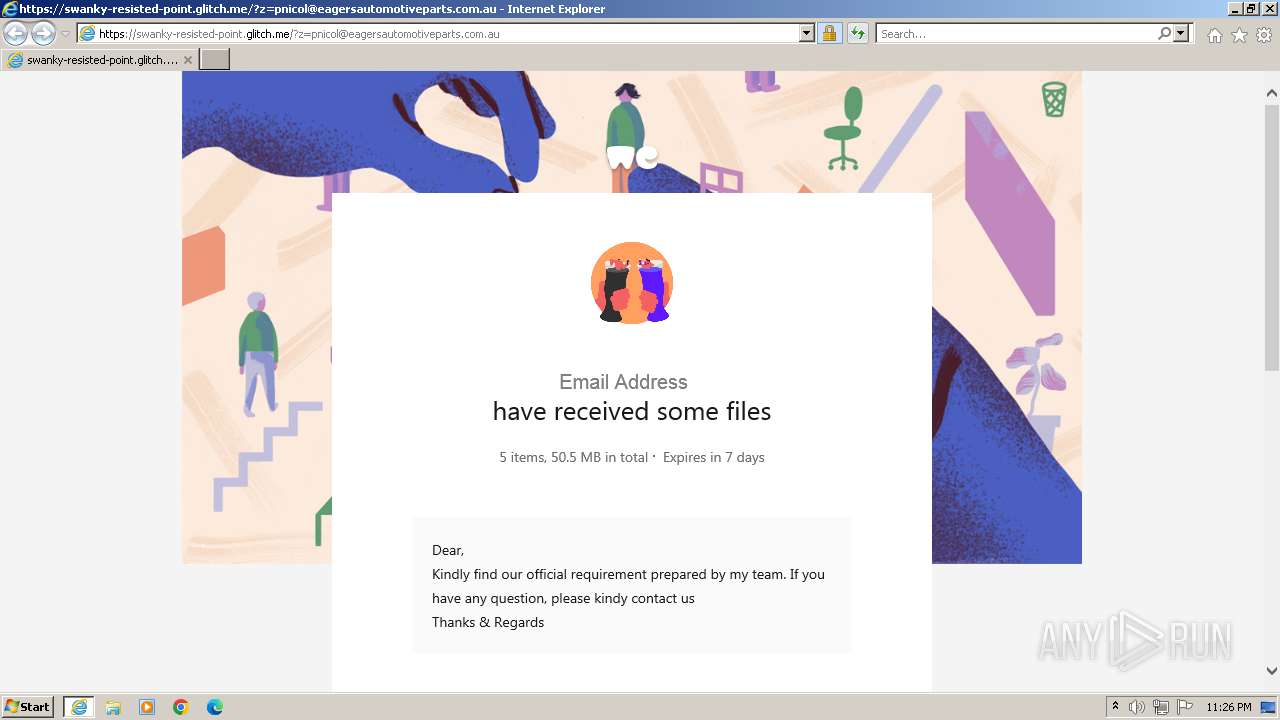
| URL: | https://swanky-resisted-point.glitch.me/?z=pnicol@eagersautomotiveparts.com.au |
| Full analysis: | https://app.any.run/tasks/366c4344-b14a-4e28-ab71-d0c5cd2a417e |
| Verdict: | Malicious activity |
| Analysis date: | May 26, 2024, 22:24:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 8193EBA76591CBD111DE83E1D029C421 |
| SHA1: | 5807F7860B070962A5EDCF563193E04C273F6356 |
| SHA256: | 728F6C75874E271E192AA018A3514ADF88A76BAF063AB44FC7FE7B753DFEE2A7 |
| SSDEEP: | 3:N8fuqCIrD2oUbGSlhD/oAYRn5n:2vCin8RhD/oRt5 |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Reads the computer name
- wmpnscfg.exe (PID: 316)
Checks supported languages
- wmpnscfg.exe (PID: 316)
Manual execution by a user
- wmpnscfg.exe (PID: 316)
Application launched itself
- iexplore.exe (PID: 3968)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
36
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3968 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://swanky-resisted-point.glitch.me/?z=pnicol@eagersautomotiveparts.com.au" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 4028 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3968 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
19 697
Read events
19 571
Write events
91
Delete events
35
Modification events
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31109051 | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31109051 | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
30
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_645BC4A49DCDC40FE5917FA45C6D4517 | binary | |
MD5:4069C5E5C9B68F36A995B029F0873865 | SHA256:340F86DF429DD8689033A4E827E0C3E8CE1DA7B5D1C7E01E5D0258113BF0D4EE | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:D095A9850CA4D363499EA87D213637BE | SHA256:6714EB42CAAAE28E9366184D110583D60F2660A87CBDCC9F8D62D7F085C24E39 | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:97F278ADCA9BDA81BC56229D82ACFAF5 | SHA256:7B522D1EF71594EA447B8900BB77CCAA41849D428B3D6144CB307198C90914D5 | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\white_2x-f4cfc880393aea615941f54a0ec4fc3745378c8c3e2699d852c8fced5562f10d[1].png | image | |
MD5:3D178BC7D315AC1E8FEBCBCA2EF487C5 | SHA256:F4CFC880393AEA615941F54A0EC4FC3745378C8C3E2699D852C8FCED5562F10D | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_B5D3A17E5BEDD2EDA793611A0A74E1E8 | binary | |
MD5:E972356913E5BBF0D32ED21D51022B67 | SHA256:623F716A14B5AA9D0AB29B399D8FBD0C169EEB284A5E361AB3540064F2B326E3 | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_49536AB5156BDD74EFF881D01C36A419 | binary | |
MD5:3093DFF837FF85E9EEB11CA4B06FAE3E | SHA256:BDFA223944DFD71FD785379DBEDF679DC184B131D3FAC31278822E192824CD0A | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D03E46CD585BBE111C712E6577BC5F07_5C7AA733A26CC779AF88EBB5B7FEEFA4 | binary | |
MD5:60F9CA1732B09C860A1829A310ACD7DC | SHA256:EC3889BDB95D4A96177A032F8CDFC95E9A24B9508AE77D12CD7AE9B1308F5A40 | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_49536AB5156BDD74EFF881D01C36A419 | binary | |
MD5:B7681553DC7B3933962867215AAD955B | SHA256:3E0401FE864B5F28063EABC80E29F36513E51691AA9E42C4F151501A58CC7989 | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\75CA58072B9926F763A91F0CC2798706_645BC4A49DCDC40FE5917FA45C6D4517 | binary | |
MD5:6C01A0C6CBC5F29BDA94F44244BB503C | SHA256:92F3E8178CC9F0ECC3BADFD7EA922AB13F1D0B42C4806176F7870F3EA53B850F | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:653BB22C0C7556EE602352BB9BBC4E96 | SHA256:119DB8C5ADEA27C9C38C888ECDC3CB50F472EF6002DE266003BC1546A145F475 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
34
DNS requests
23
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4028 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9d16a895bffb80f6 | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?068eb670bb243701 | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 108.138.2.10:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkzUBtJnwJkc3SmanzgxeYU%3D | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 18.245.65.219:80 | http://ocsp.r2m03.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQqHI%2BsdmapawQncL1rpCEZZ8gTSAQUVdkYX9IczAHhWLS%2Bq9lVQgHXLgICEAwavBUkaGm72E%2BRs0Tgw3Q%3D | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEjgLnWaIozse2b%2BczaaODg8%3D | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 18.245.65.219:80 | http://ocsp.r2m01.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBShdVEFnSEQ0gG5CBtzM48cPMe9XwQUgbgOY4qJEhjl%2Bjs7UJWf5uWQE4UCEAqFHNMUTb3%2B%2FNnQWmcy9Rg%3D | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?3efec3cabca71489 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4028 | iexplore.exe | 3.95.107.114:443 | swanky-resisted-point.glitch.me | AMAZON-AES | US | unknown |
4028 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
4028 | iexplore.exe | 108.138.2.10:80 | o.ss2.us | AMAZON-02 | US | unknown |
4028 | iexplore.exe | 18.245.39.64:80 | ocsp.rootg2.amazontrust.com | — | US | unknown |
4028 | iexplore.exe | 18.245.65.219:80 | ocsp.r2m03.amazontrust.com | — | US | unknown |
4028 | iexplore.exe | 13.32.27.4:443 | prod-cdn.wetransfer.net | AMAZON-02 | US | unknown |
4028 | iexplore.exe | 52.217.202.120:443 | s3.amazonaws.com | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
swanky-resisted-point.glitch.me |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.r2m03.amazontrust.com |
| unknown |
prod-cdn.wetransfer.net |
| whitelisted |
i.pinimg.com |
| whitelisted |
s3.amazonaws.com |
| shared |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Misc activity | ET INFO DNS Query to Online Application Hosting Domain (glitch .me) |
1088 | svchost.exe | Possible Social Engineering Attempted | ET HUNTING Suspicious Glitch Hosted DNS Request - Possible Phishing Landing |
4028 | iexplore.exe | Misc activity | ET INFO Observed Online Application Hosting Domain (glitch .me in TLS SNI) |
4028 | iexplore.exe | Misc activity | ET INFO Observed Online Application Hosting Domain (glitch .me in TLS SNI) |
4028 | iexplore.exe | Possible Social Engineering Attempted | ET HUNTING Suspicious Glitch Hosted TLS SNI Request - Possible Phishing Landing |
4028 | iexplore.exe | Possible Social Engineering Attempted | ET HUNTING Suspicious Glitch Hosted TLS SNI Request - Possible Phishing Landing |
3968 | iexplore.exe | Misc activity | ET INFO Observed Online Application Hosting Domain (glitch .me in TLS SNI) |
3968 | iexplore.exe | Misc activity | ET INFO Observed Online Application Hosting Domain (glitch .me in TLS SNI) |
3968 | iexplore.exe | Possible Social Engineering Attempted | ET HUNTING Suspicious Glitch Hosted TLS SNI Request - Possible Phishing Landing |
3968 | iexplore.exe | Possible Social Engineering Attempted | ET HUNTING Suspicious Glitch Hosted TLS SNI Request - Possible Phishing Landing |