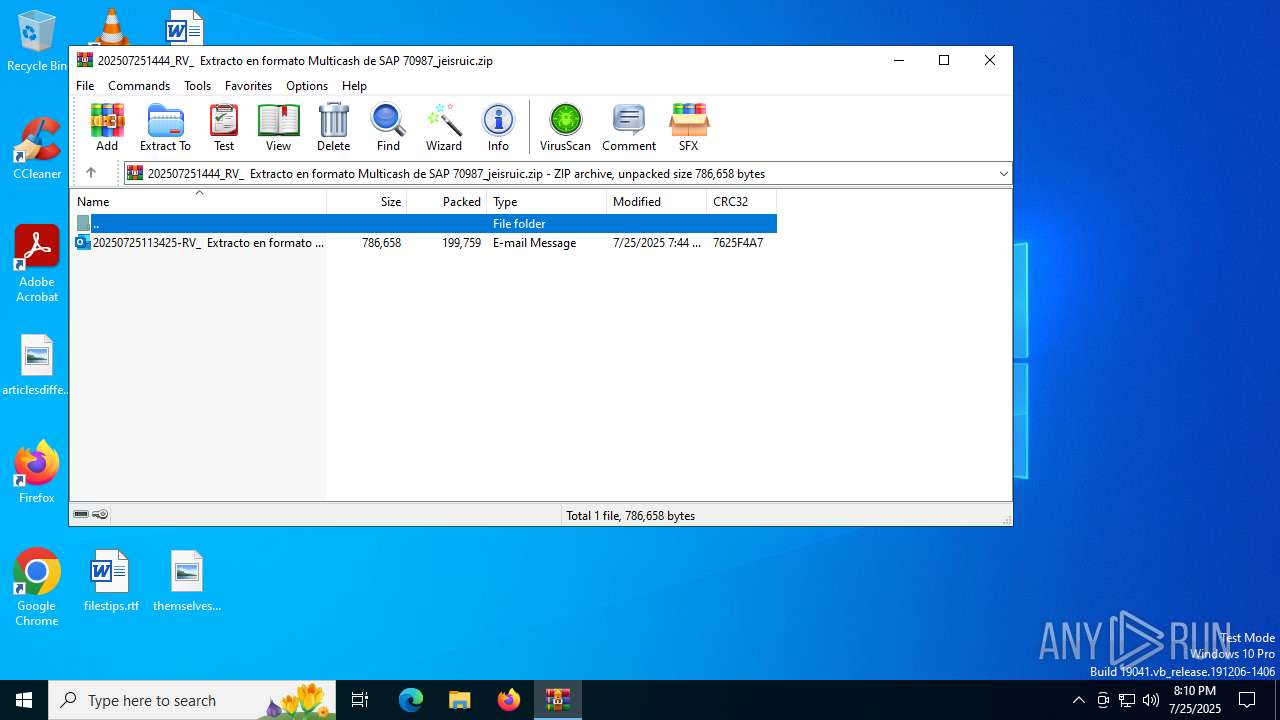
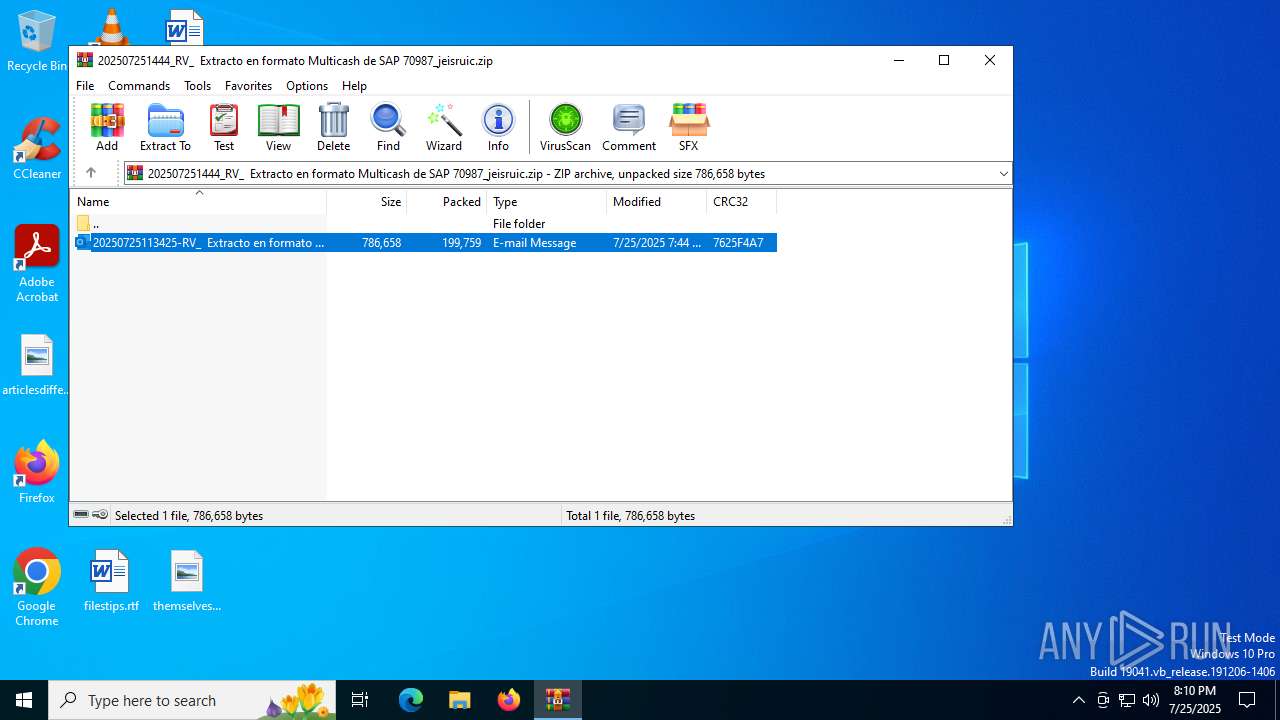
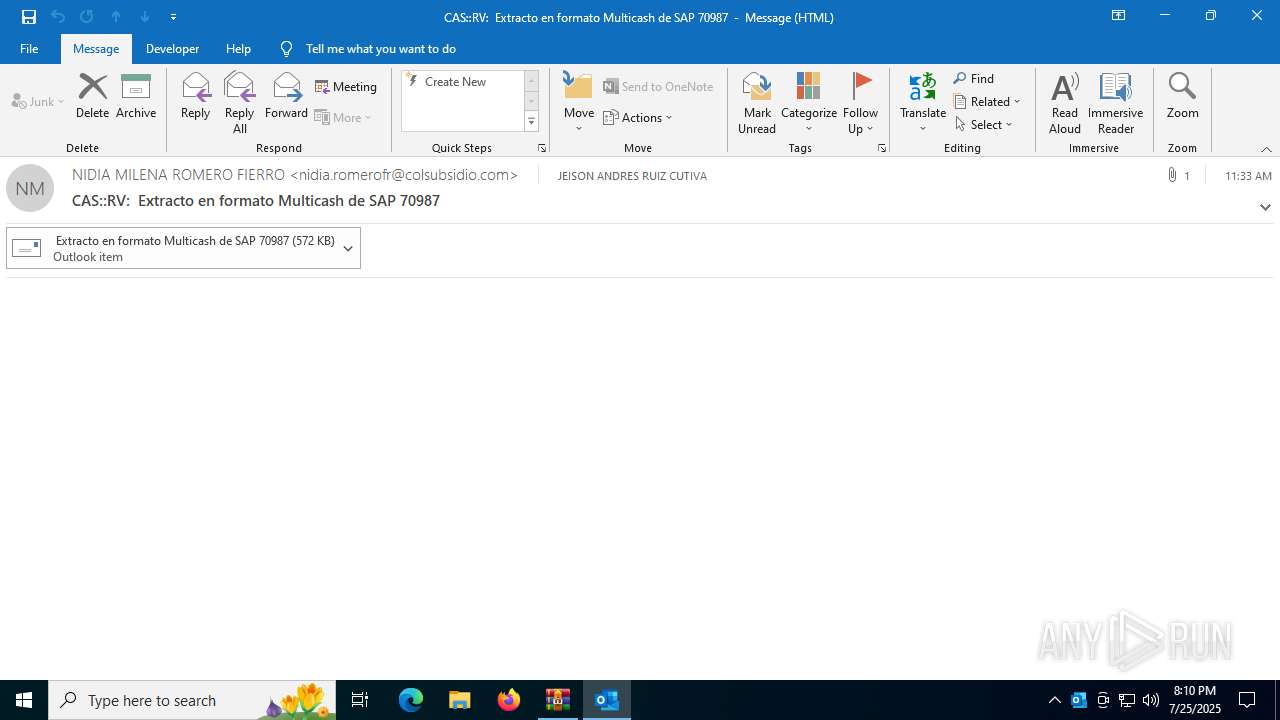
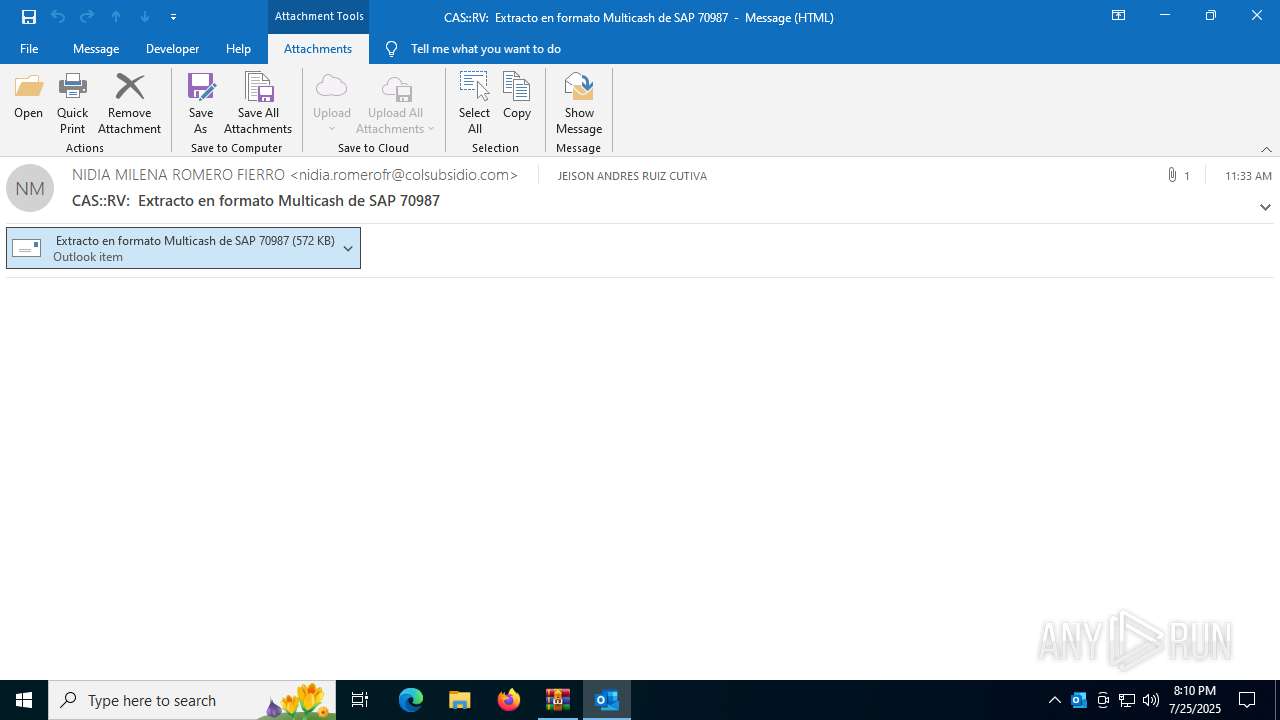
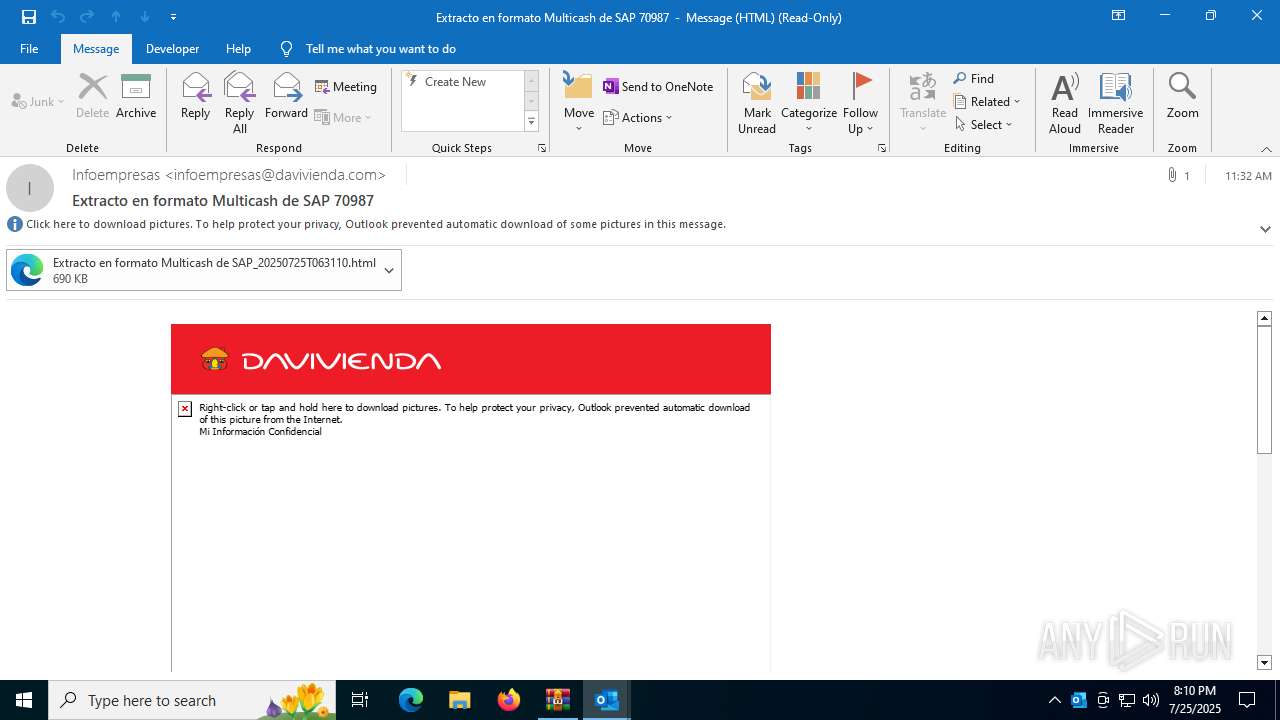
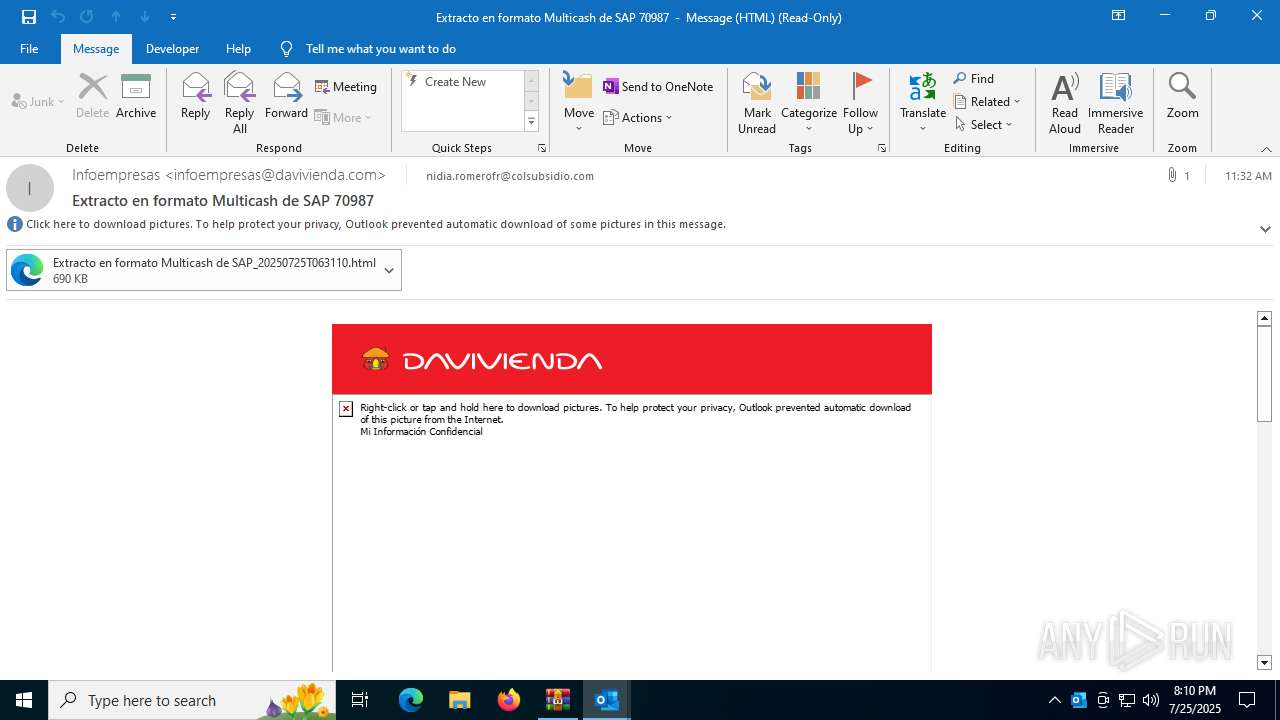
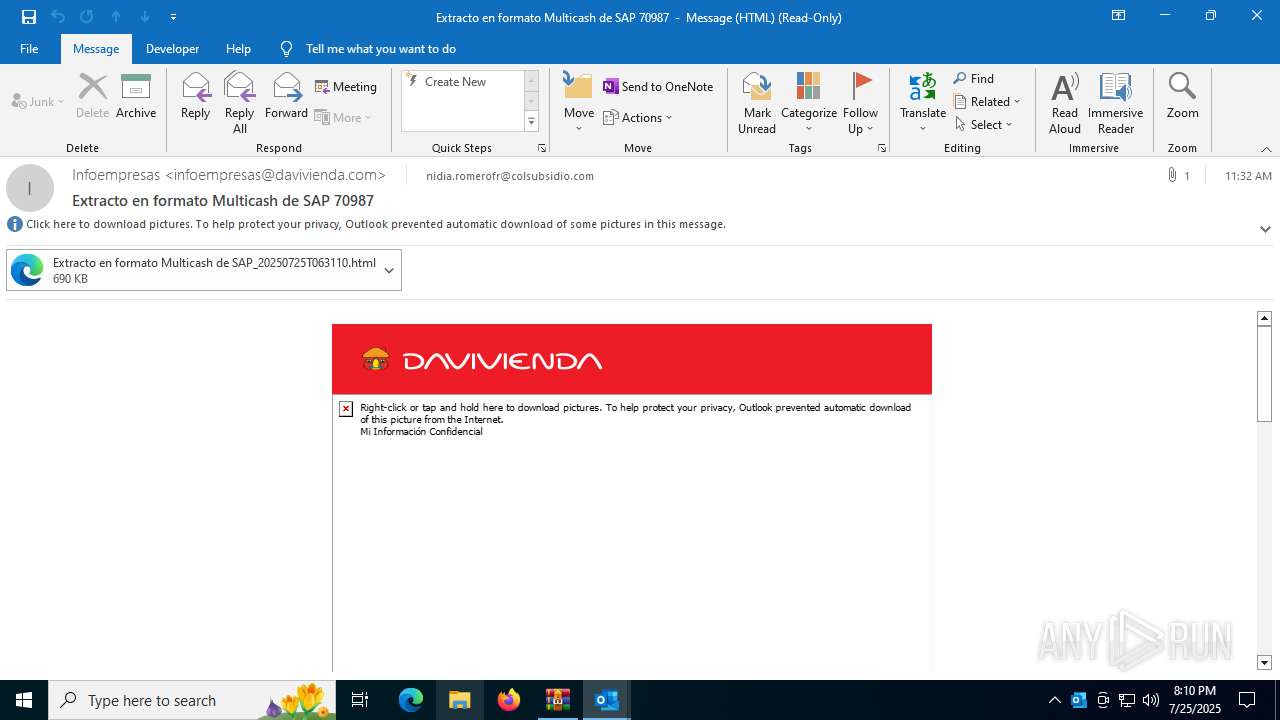
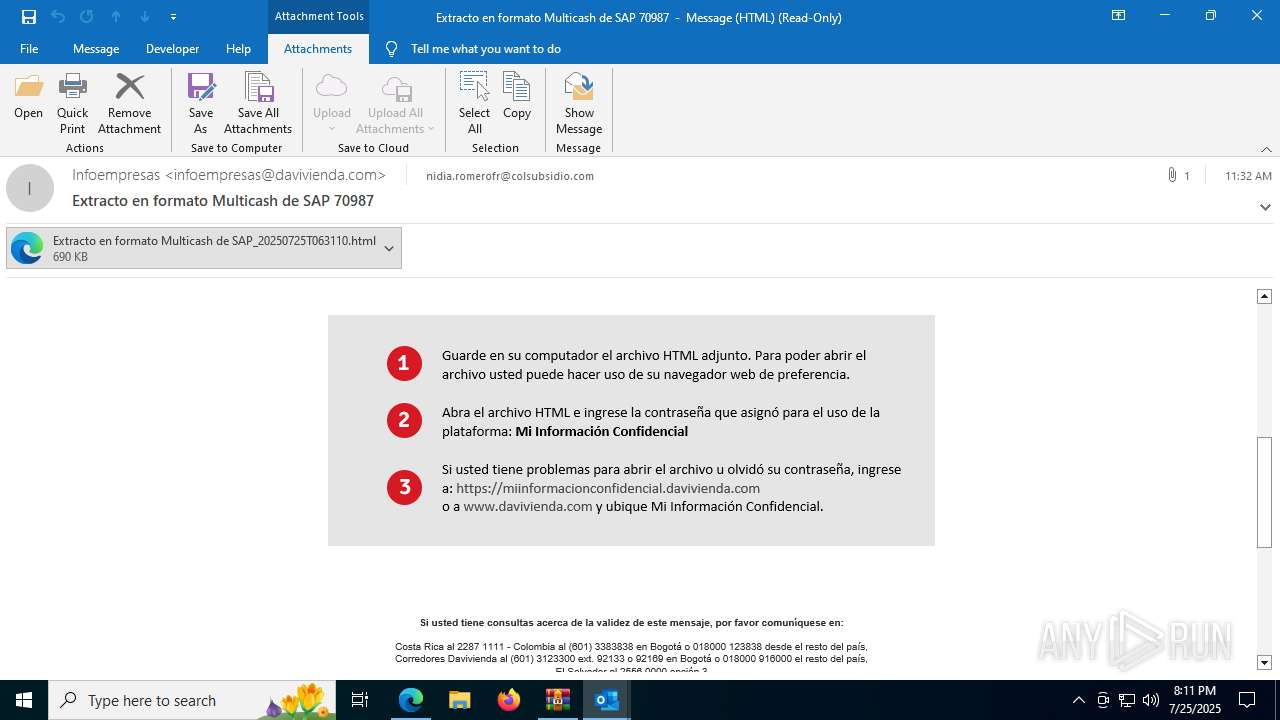
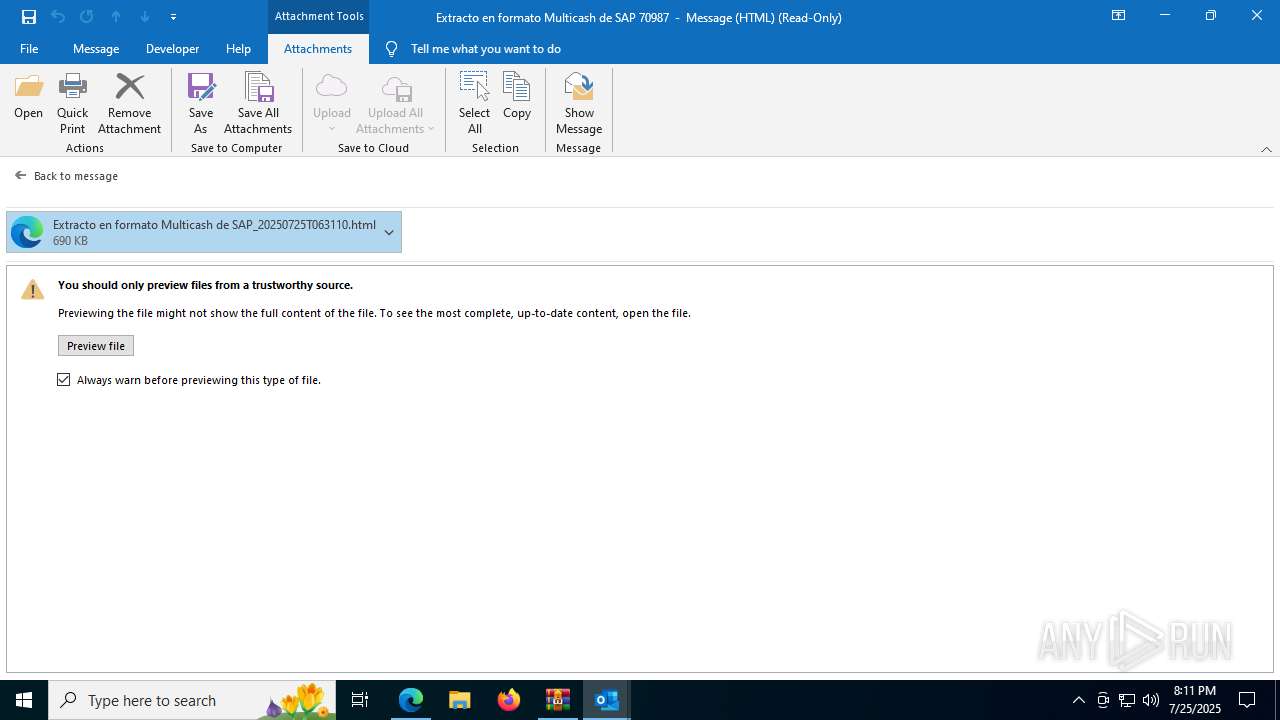
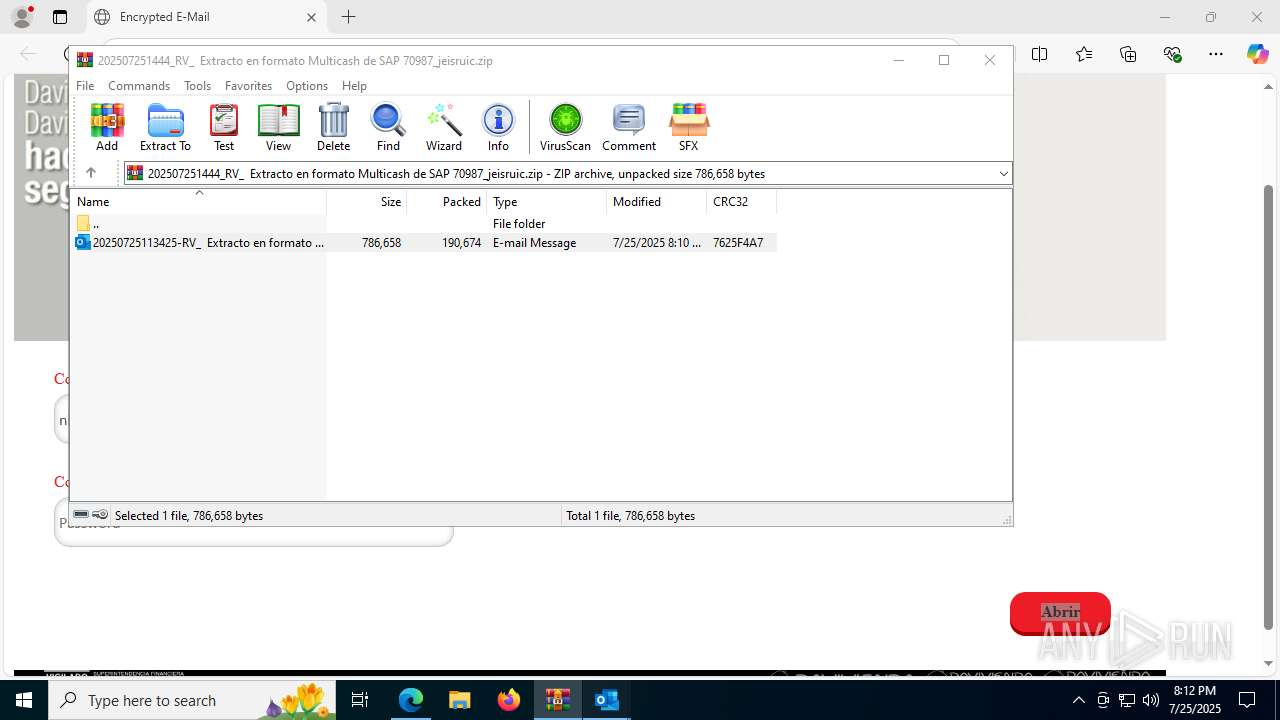
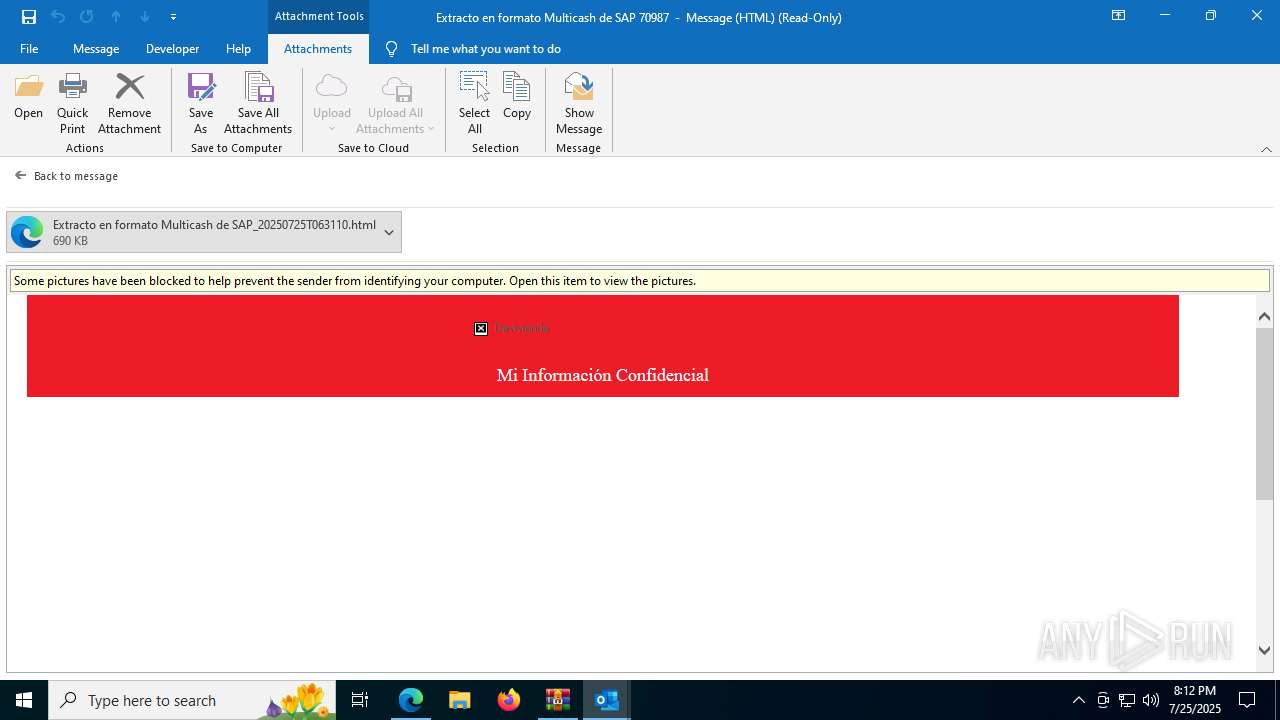
| File name: | 202507251444_RV_ Extracto en formato Multicash de SAP 70987_jeisruic.zip |
| Full analysis: | https://app.any.run/tasks/ae5b6bc5-e80c-4212-b744-55de1ff6ec78 |
| Verdict: | Malicious activity |
| Analysis date: | July 25, 2025, 20:09:57 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 3E9FBEBE6075A810D52A237301345433 |
| SHA1: | 0D80BE06F2337847D4EF05442845F88DEB014886 |
| SHA256: | 728E647B08217EBEA1C43FFD700ACF0EDF15CAA695D1E5FA4F1A8FB1C27A42B0 |
| SSDEEP: | 6144:vyp+o3z/Ndx6mTXoEoXBgEd2ctVYC4R1NqFPPh39WQzo:Kp+mz/Ndx6BEKBF8QV/OMdPh39WWo |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1592)
Reads Microsoft Outlook installation path
- WinRAR.exe (PID: 1592)
INFO
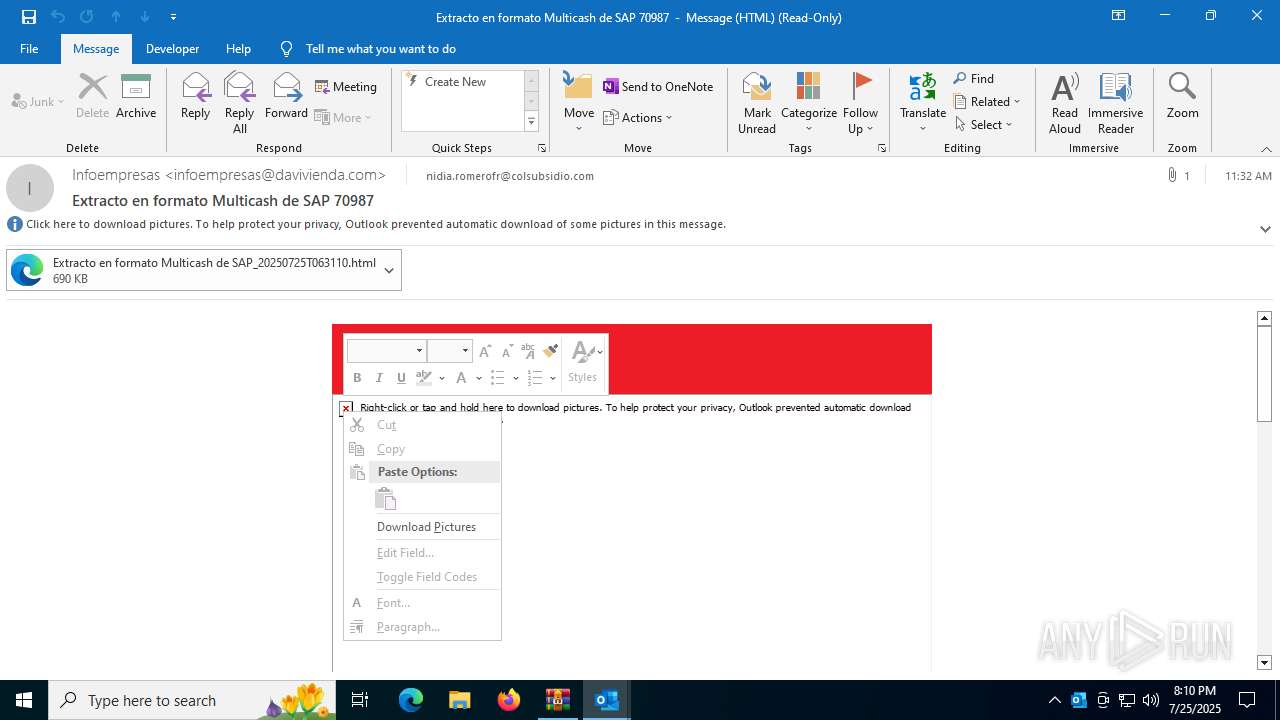
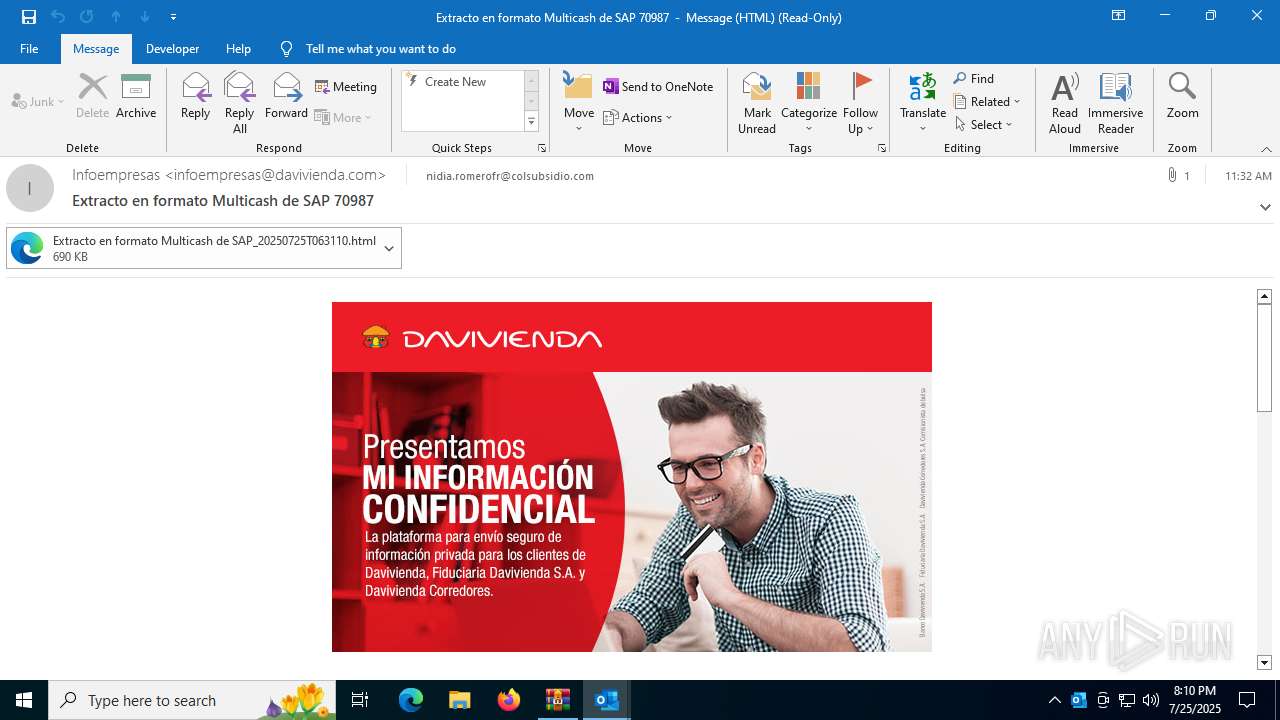
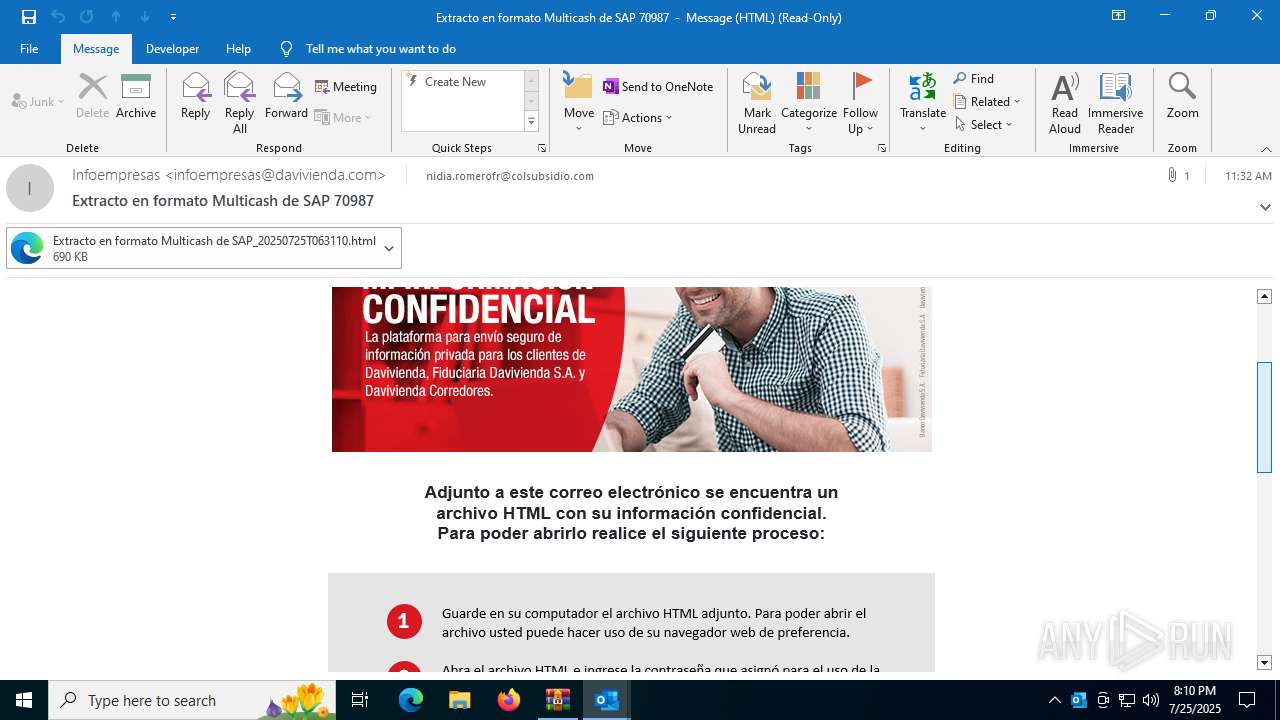
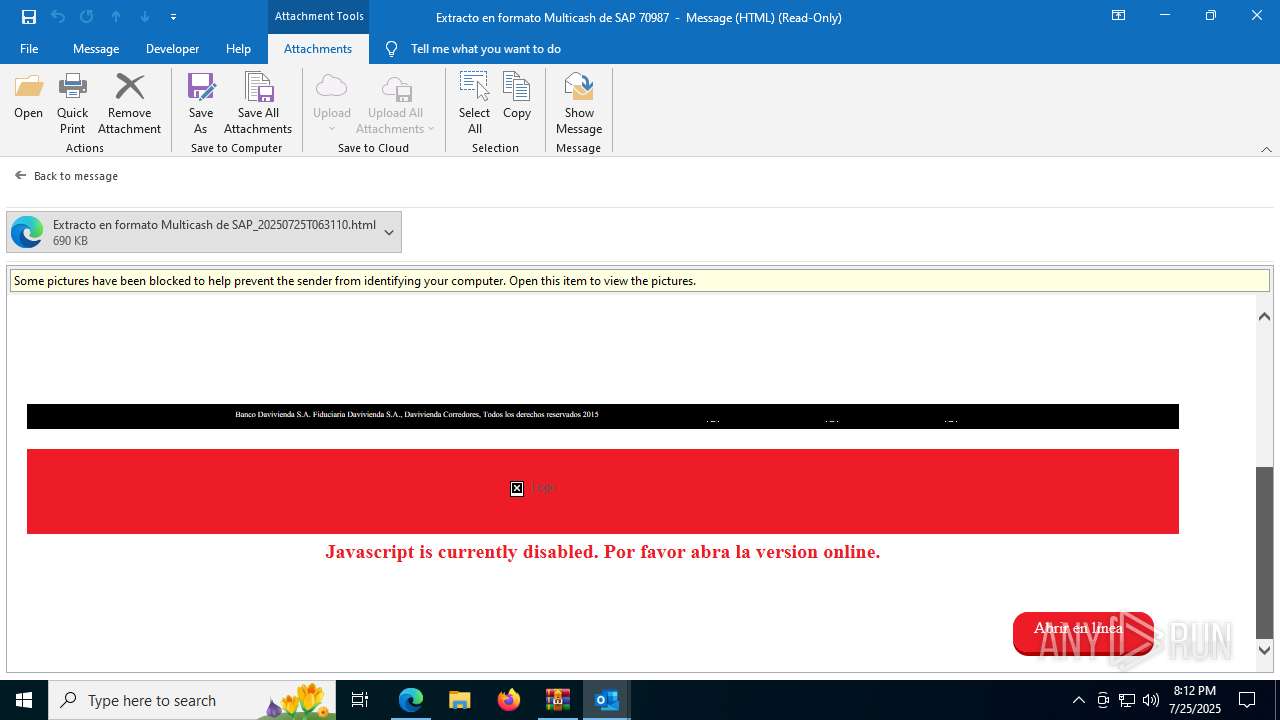
Email with attachments
- WinRAR.exe (PID: 1592)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 1592)
Application launched itself
- msedge.exe (PID: 1520)
Checks supported languages
- identity_helper.exe (PID: 7212)
Reads the computer name
- identity_helper.exe (PID: 7212)
Reads Environment values
- identity_helper.exe (PID: 7212)
Checks proxy server information
- slui.exe (PID: 7124)
- prevhost.exe (PID: 6344)
Reads the software policy settings
- slui.exe (PID: 7124)
Creates files or folders in the user directory
- prevhost.exe (PID: 6344)
Reads security settings of Internet Explorer
- prevhost.exe (PID: 6344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:07:25 19:44:32 |
| ZipCRC: | 0x7625f4a7 |
| ZipCompressedSize: | 199759 |
| ZipUncompressedSize: | 786658 |
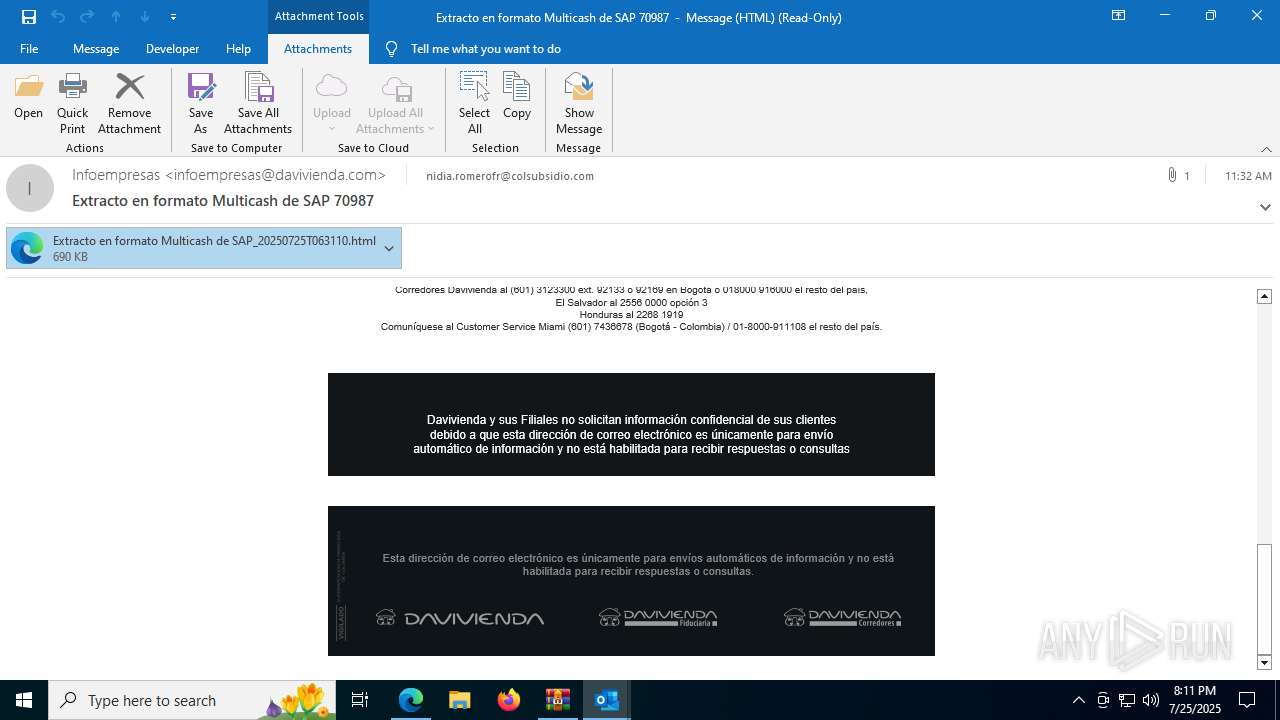
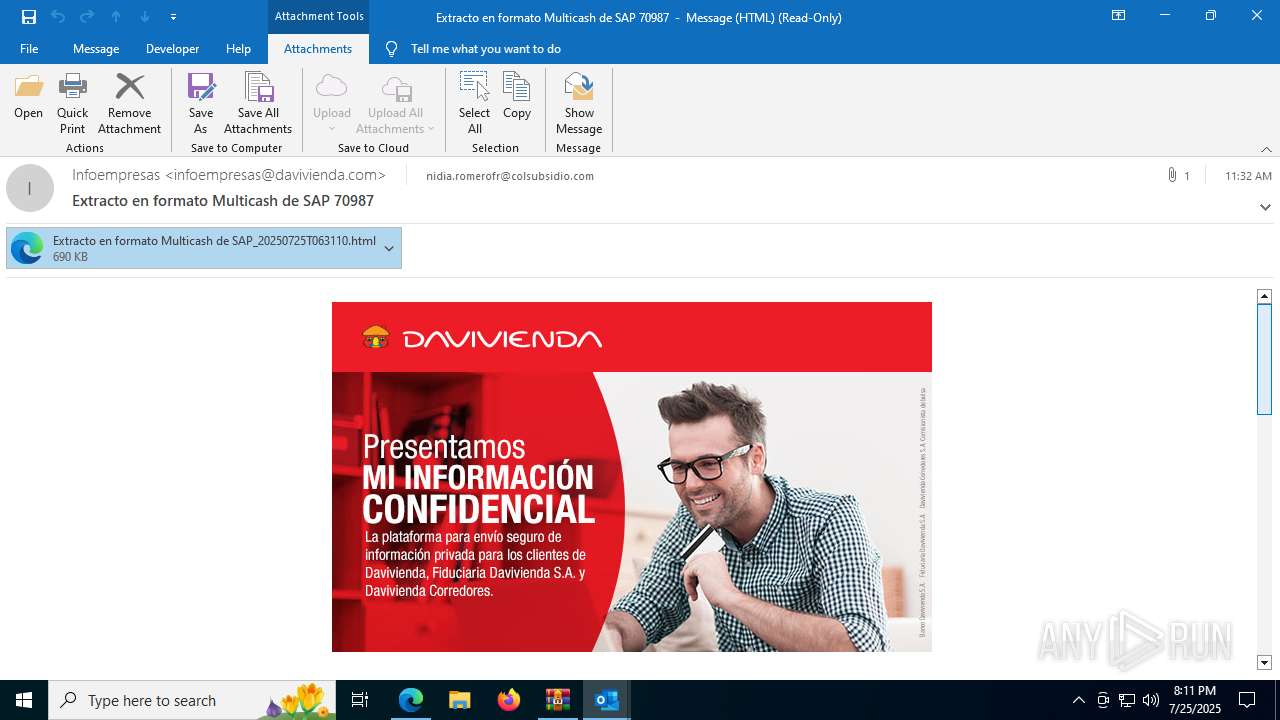
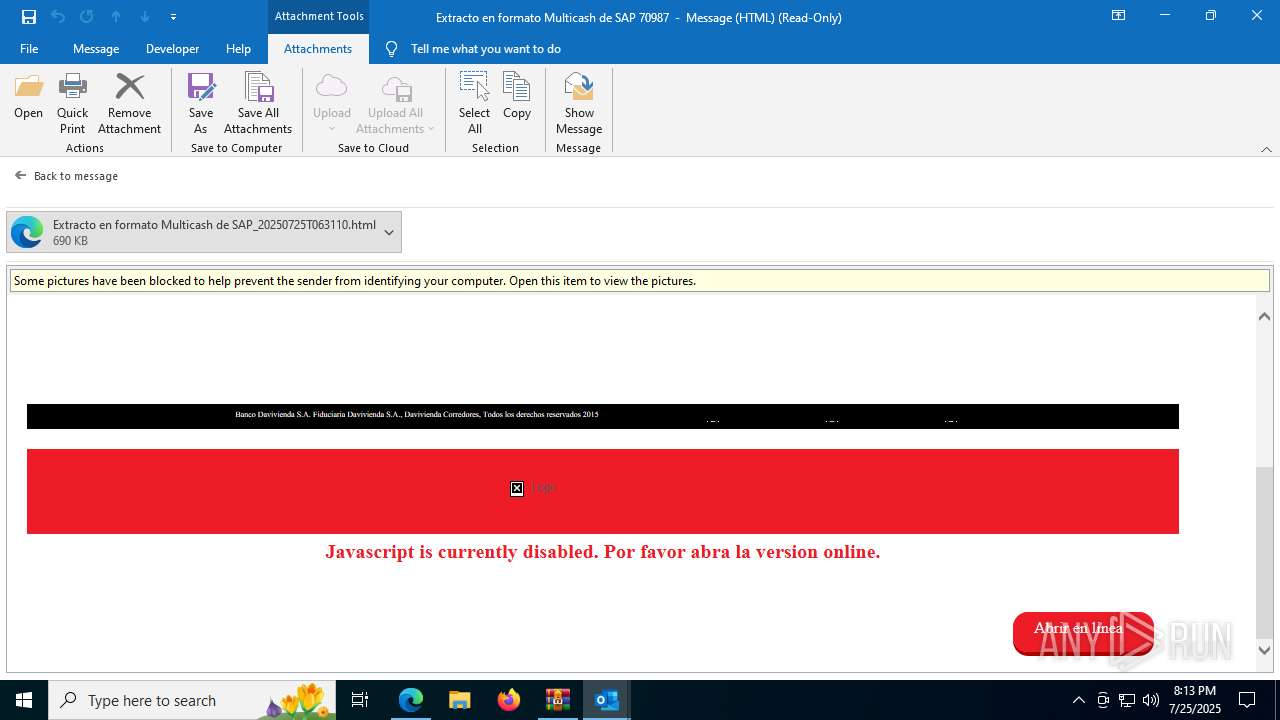
| ZipFileName: | 20250725113425-RV_ Extracto en formato Multicash de SAP 70987-jeisruic.eml |
Total processes
187
Monitored processes
38
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
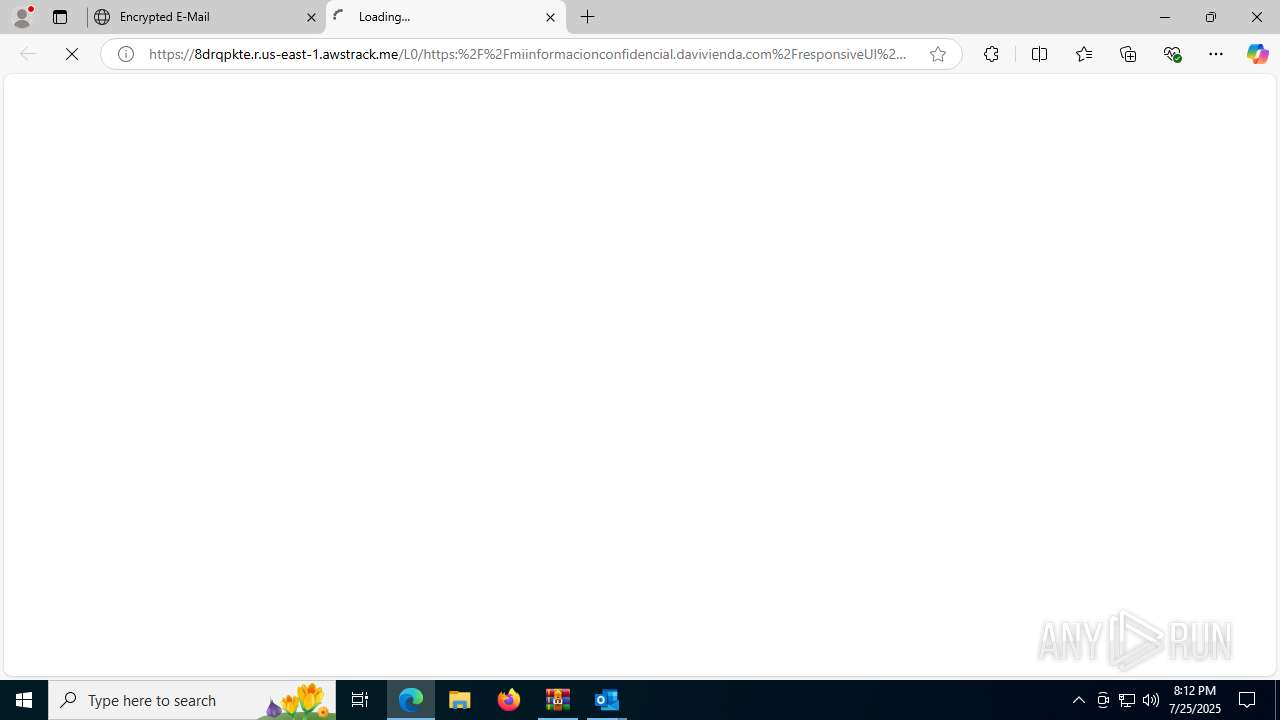
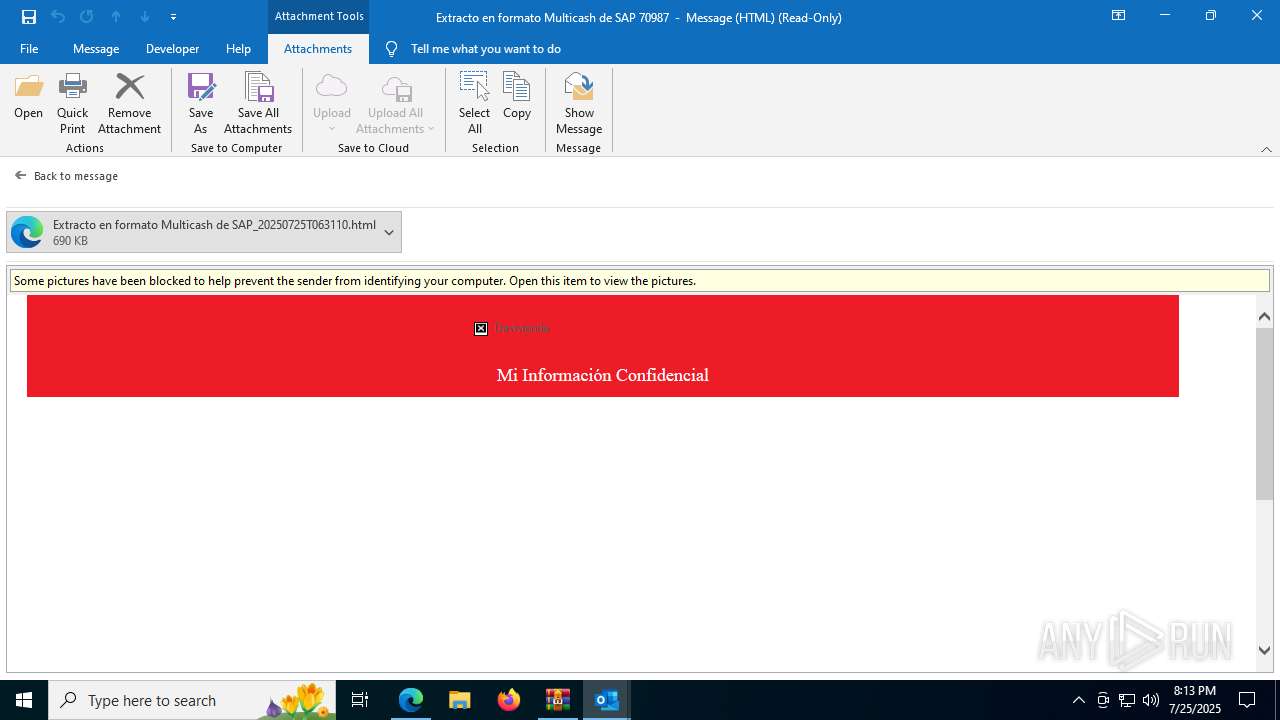
| 1388 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument https://8drqpkte.r.us-east-1.awstrack.me/L0/https:%2F%2Fmiinformacionconfidencial.davivienda.com%2FresponsiveUI%2FEnvelopeOpenServlet%3FenvelopeAction=displayLoginChunkedImages%26messageId=560_85300%26templateName=BcoDaviV2EnvelopeTemplate.vm%26useLinkedStyle=false%26envelopeRecipient=nidia.romerofr%2540colsubsidio.com%26attachment=false%26supportsOpenOnlinetrue/1/01000198415b1254-31680af6-bdc2-44e3-b92f-3c858ab6008a-000000/dm2BH-IP3y6qVLidR_gW9z8pF_g=436 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | prevhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
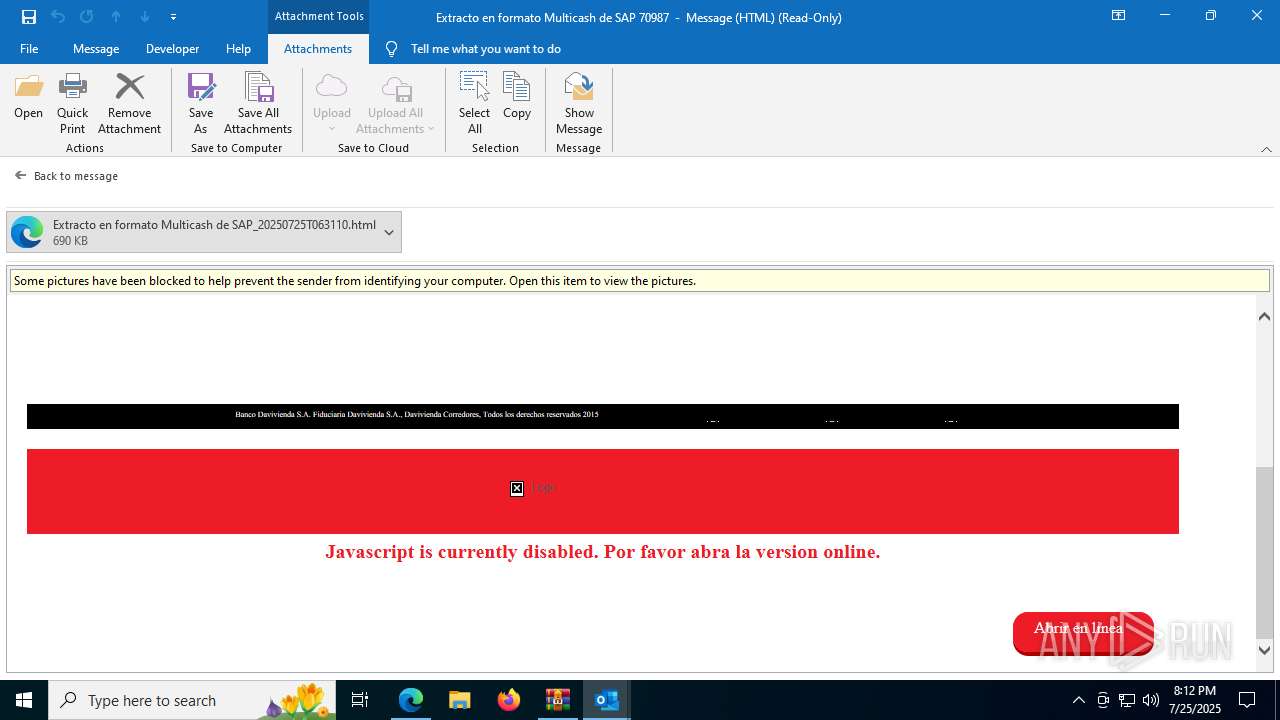
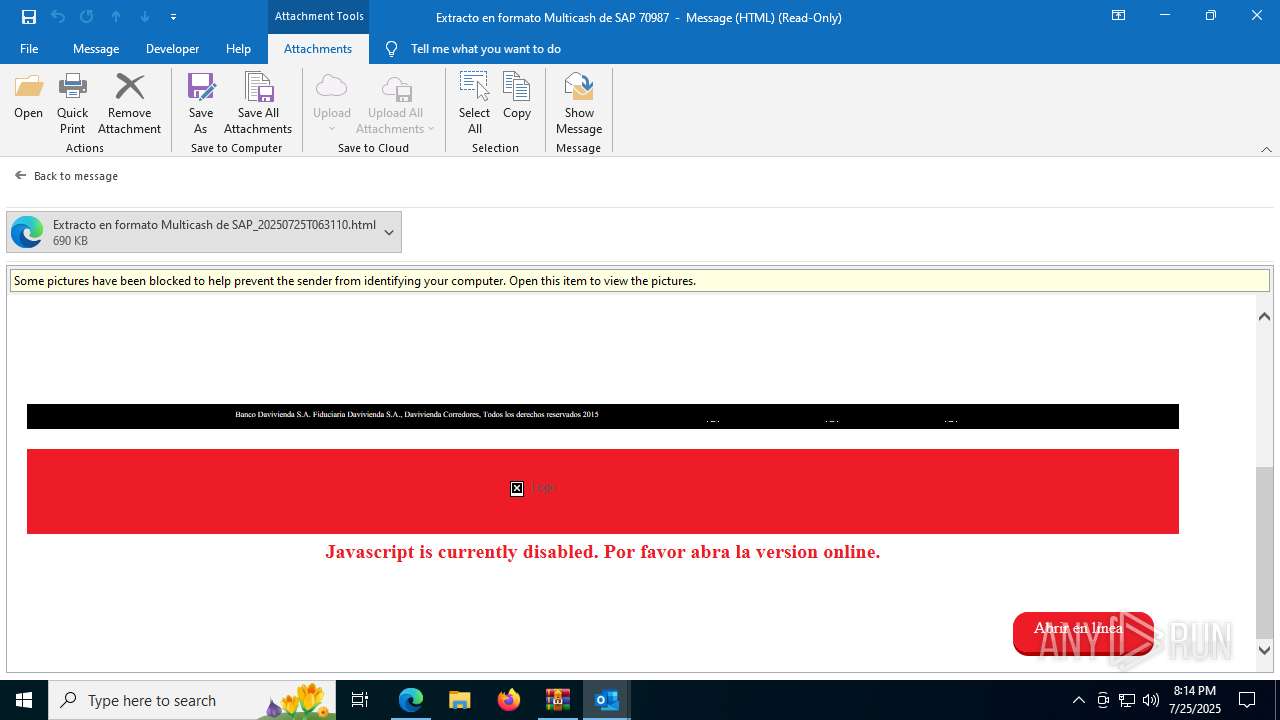
| 1520 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\VYQCRE2V\Extracto en formato Multicash de SAP_20250725T063110.html | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
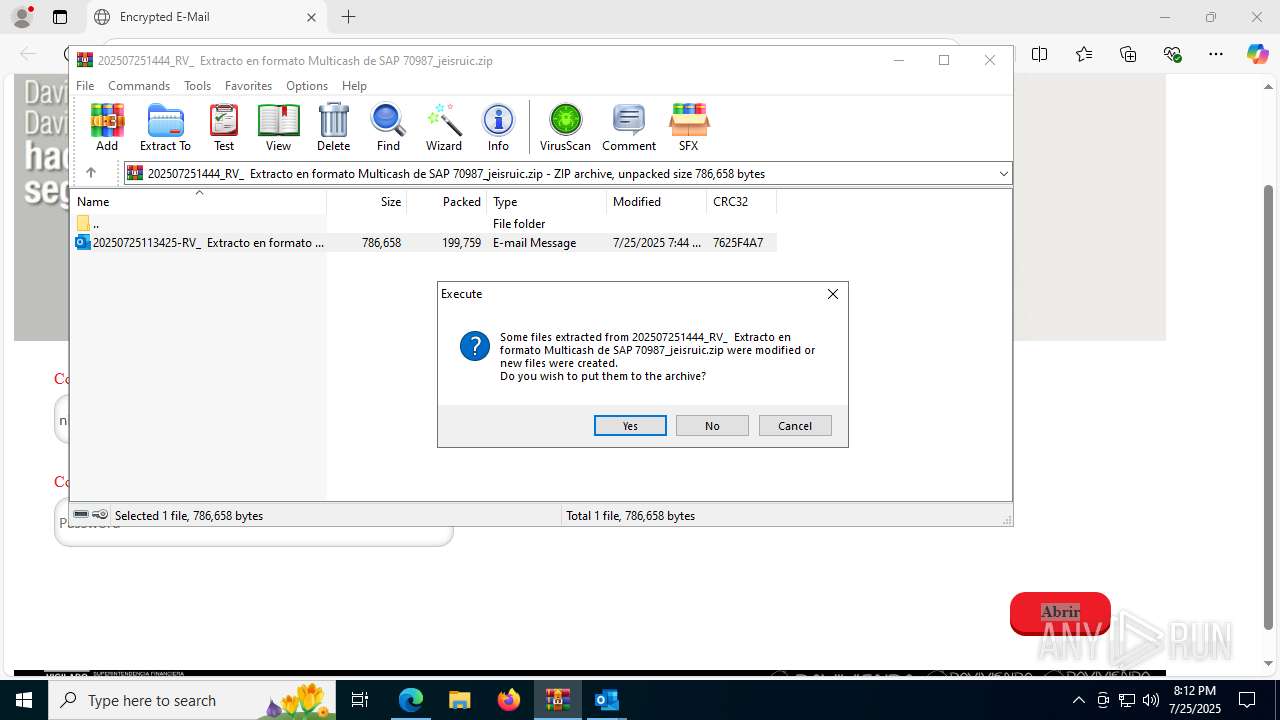
| 1592 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\202507251444_RV_ Extracto en formato Multicash de SAP 70987_jeisruic.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1752 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x304,0x308,0x30c,0x2fc,0x314,0x7ffc3624f208,0x7ffc3624f214,0x7ffc3624f220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2384 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --always-read-main-dll --field-trial-handle=4264,i,14453879269378287196,634289046997710968,262144 --variations-seed-version --mojo-platform-channel-handle=4276 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2504 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6928,i,14453879269378287196,634289046997710968,262144 --variations-seed-version --mojo-platform-channel-handle=6944 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3460 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2240,i,14453879269378287196,634289046997710968,262144 --variations-seed-version --mojo-platform-channel-handle=2064 /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3836 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=4864,i,14453879269378287196,634289046997710968,262144 --variations-seed-version --mojo-platform-channel-handle=4880 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3880 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --string-annotations --gpu-preferences=UAAAAAAAAADoAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAABCAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=6892,i,14453879269378287196,634289046997710968,262144 --variations-seed-version --mojo-platform-channel-handle=5868 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3896 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "B44DF4F1-BAD3-44AB-AB9C-27354E7A8D25" "25F13E86-6A3F-4D3A-ABDF-DE6B80FAD13B" "4172" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
Total events
22 676
Read events
21 310
Write events
1 174
Delete events
192
Modification events
| (PID) Process: | (1592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\202507251444_RV_ Extracto en formato Multicash de SAP 70987_jeisruic.zip | |||
| (PID) Process: | (1592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.eml\OpenWithProgids |
| Operation: | write | Name: | Outlook.File.eml.15 |
Value: | |||
| (PID) Process: | (1592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {5FA29220-36A1-40F9-89C6-F4B384B7642E} {886D8EEB-8CF2-4446-8D02-CDBA1DBDCF99} 0xFFFF |
Value: 010000000000000046990A20A0FDDB01 | |||
Executable files
0
Suspicious files
264
Text files
102
Unknown types
47
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4172 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 4172 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:D8353D2C83D585F0A583E8CD6D8C035E | SHA256:968CD6C3D82B5027E45AA9ACA0726BBAE82AC5F39AAEFCB7C50DDB1D4194ADB5 | |||
| 4172 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olkF44F.tmp | binary | |
MD5:AE88D7C392A211EFBC764D2D1D39E984 | SHA256:4A9E195ACC6976D704A3EAAC9D6F027C5C7B3AAAA3956B31633272BDF7D61F01 | |||
| 4172 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\98243713-B3D9-4E61-A86B-5EDB128C8358 | xml | |
MD5:D97C7C8B3846F79B7D16B4E56A249C32 | SHA256:64D187601AB005A78A0DFF2B3AEDC5C84D1E5CF7C9284FD93E936492CAE074B6 | |||
| 4172 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olkF45F.tmp | text | |
MD5:9DEEBFD9AC3536FBCE7714E0B792516F | SHA256:B7B6C4E9911C23A8522C815A73033EE22E48585CD1BB3C1489D14205DDC88ACA | |||
| 4172 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_0FB9553B978E7F00C6B2309507DEB64A | der | |
MD5:2E2F6B31BBDE1EA4D6800CB96408F17B | SHA256:9DDA126A92124DD6792842A207E7FD31BC8F1B420E1FAC8E06736AD0E93493BA | |||
| 4172 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:D61039AF0A640CB5090D9C2A2CF0F82C | SHA256:B7F5E77056B570989777A0B5EACC305BCFC9296E090B923B5A5A8CD23F72EE54 | |||
| 4172 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_0FB9553B978E7F00C6B2309507DEB64A | binary | |
MD5:698759AD1A5D674643ECC06FF2C57B27 | SHA256:D32362DB97E25AAC315E58F14A30DAB9DCA4B9EE278AA90A6C4AA3D20C94EA03 | |||
| 4172 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\5475cb191e478c39370a215b2da98a37e9dc813d.tbres | binary | |
MD5:9F36FF0D6F4E619F6978B8593DFD25CC | SHA256:4F4F655C6AACC31040FEE7FD84492DDCD108627A6CAB6EEA965AAA1C3637A380 | |||
| 4172 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
100
DNS requests
90
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
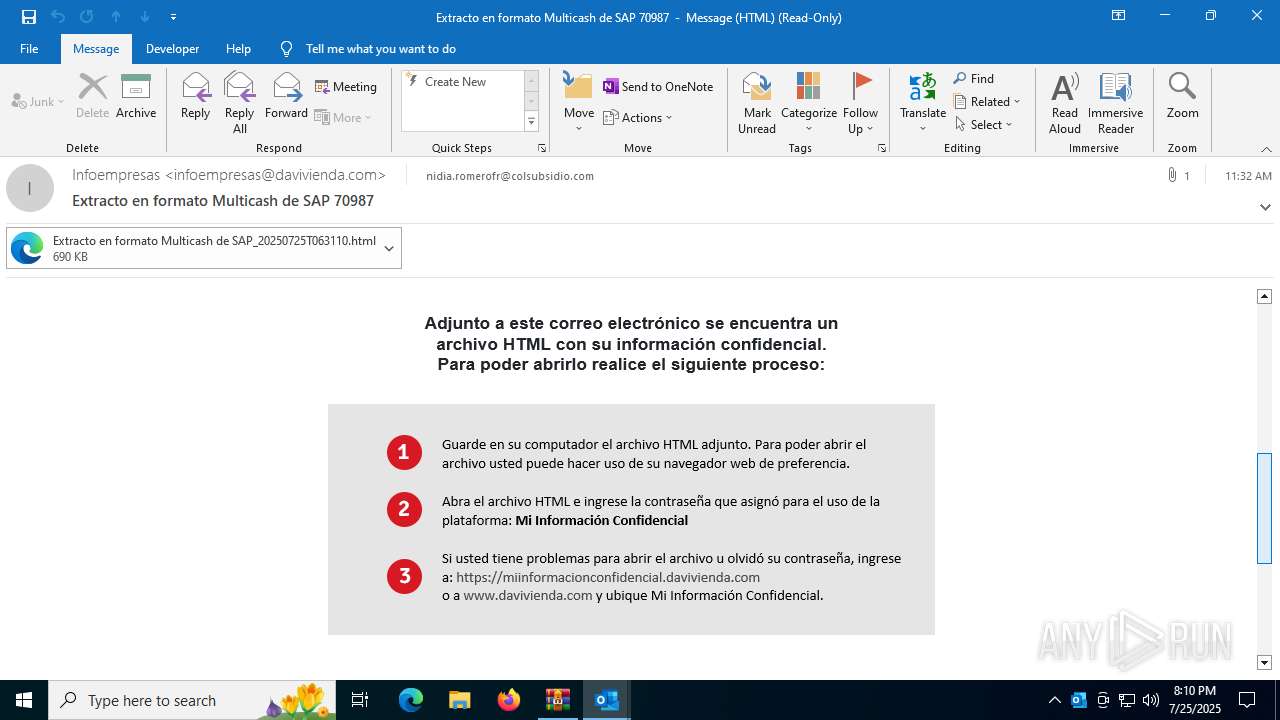
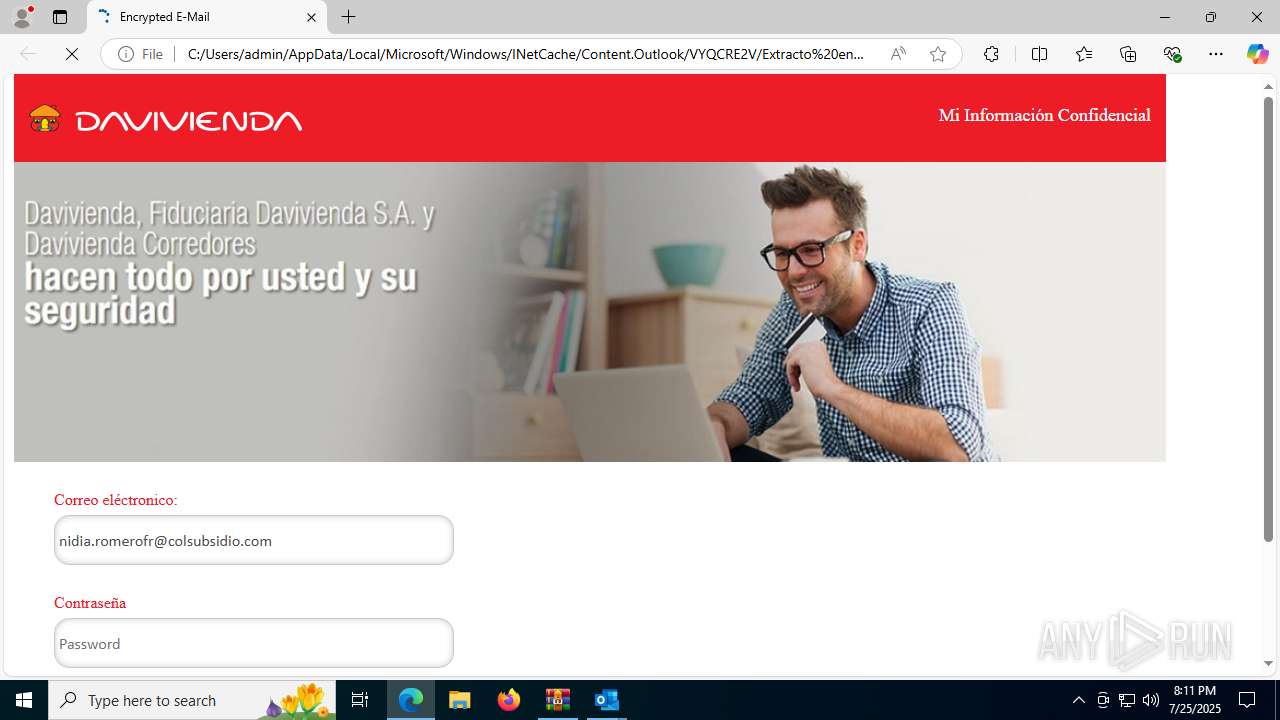
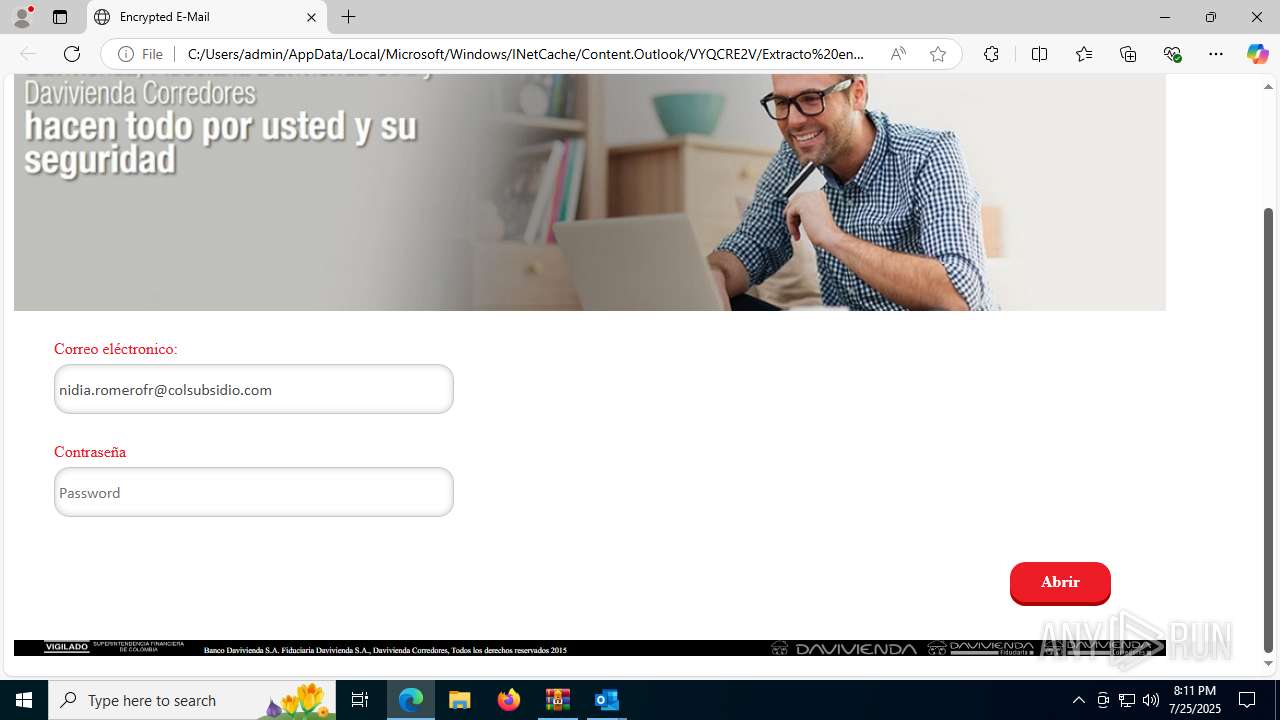
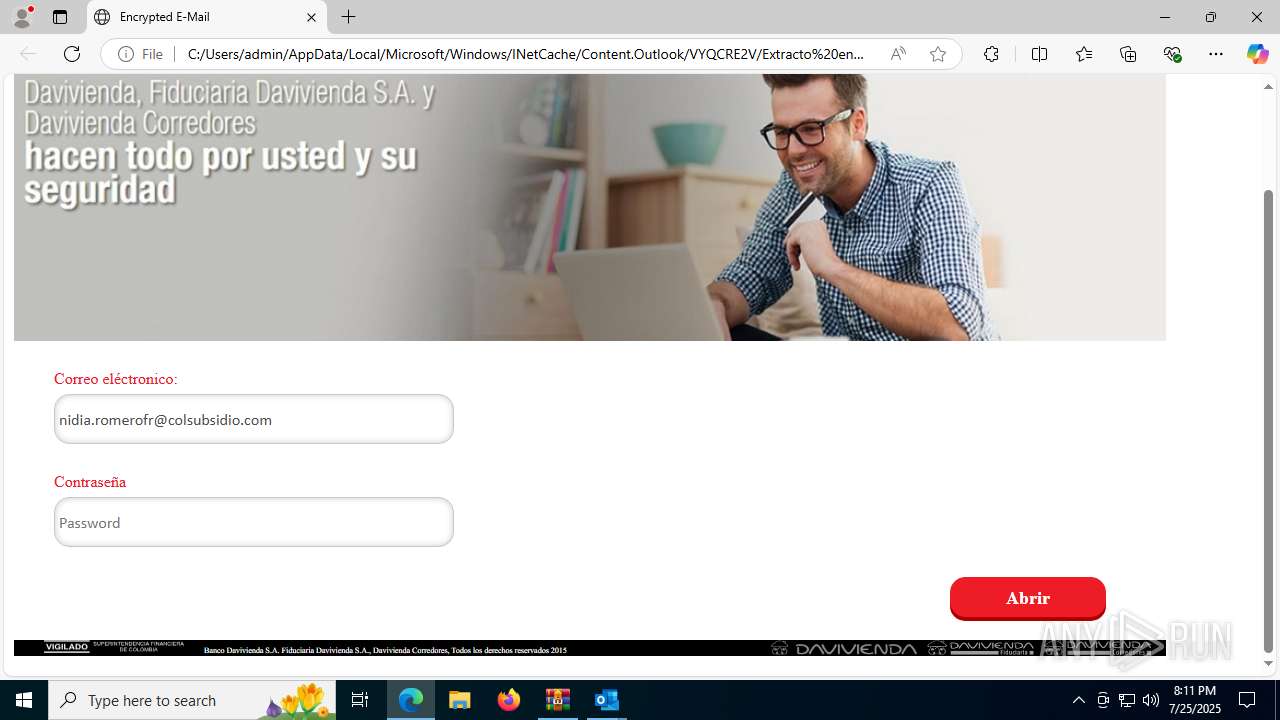
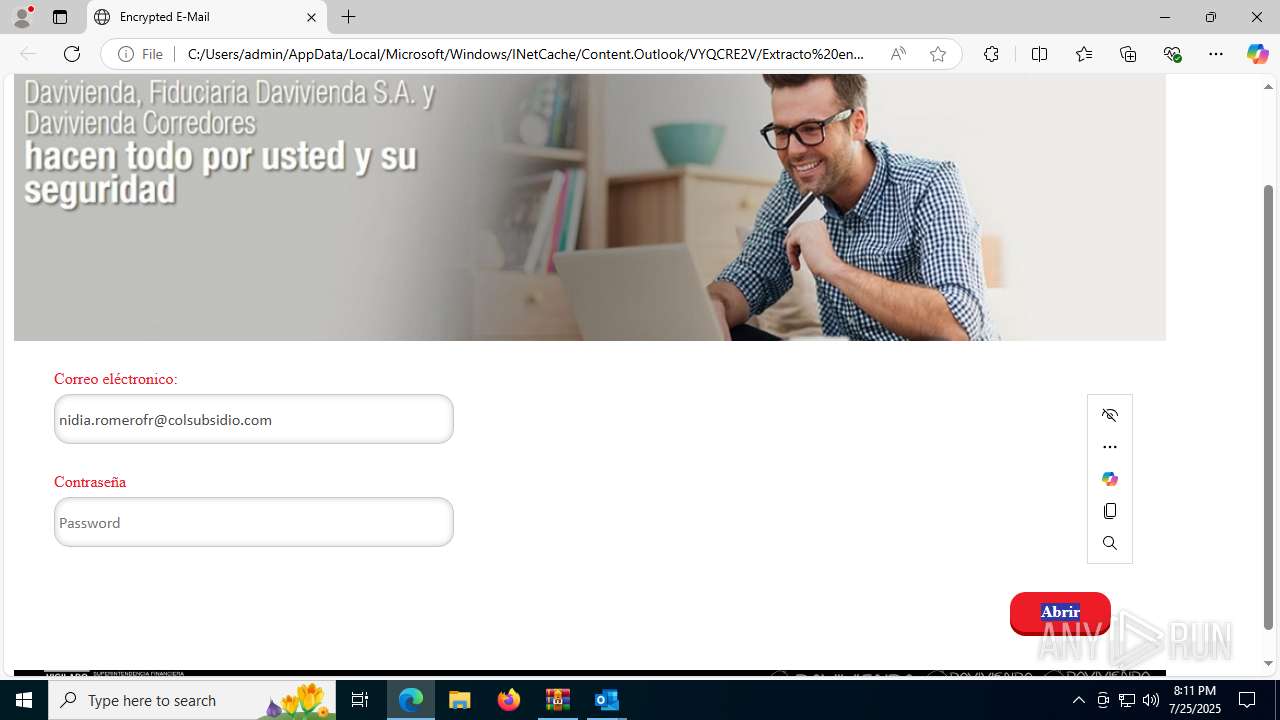
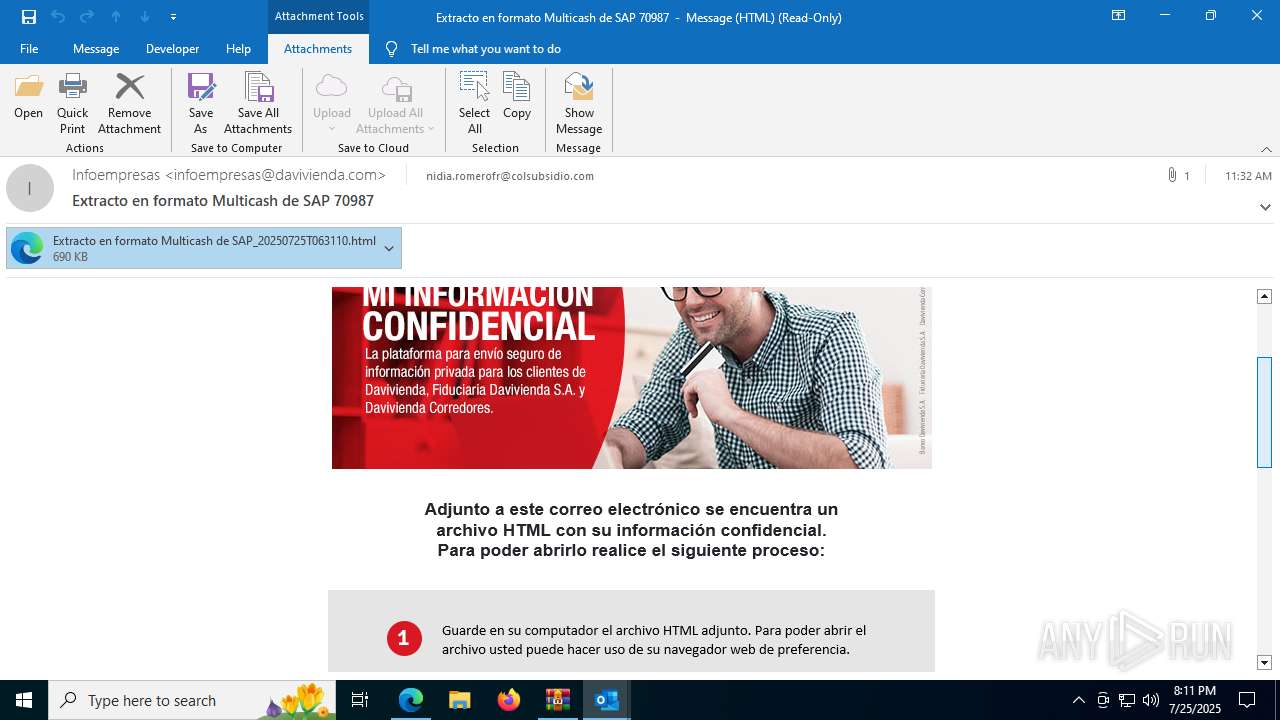
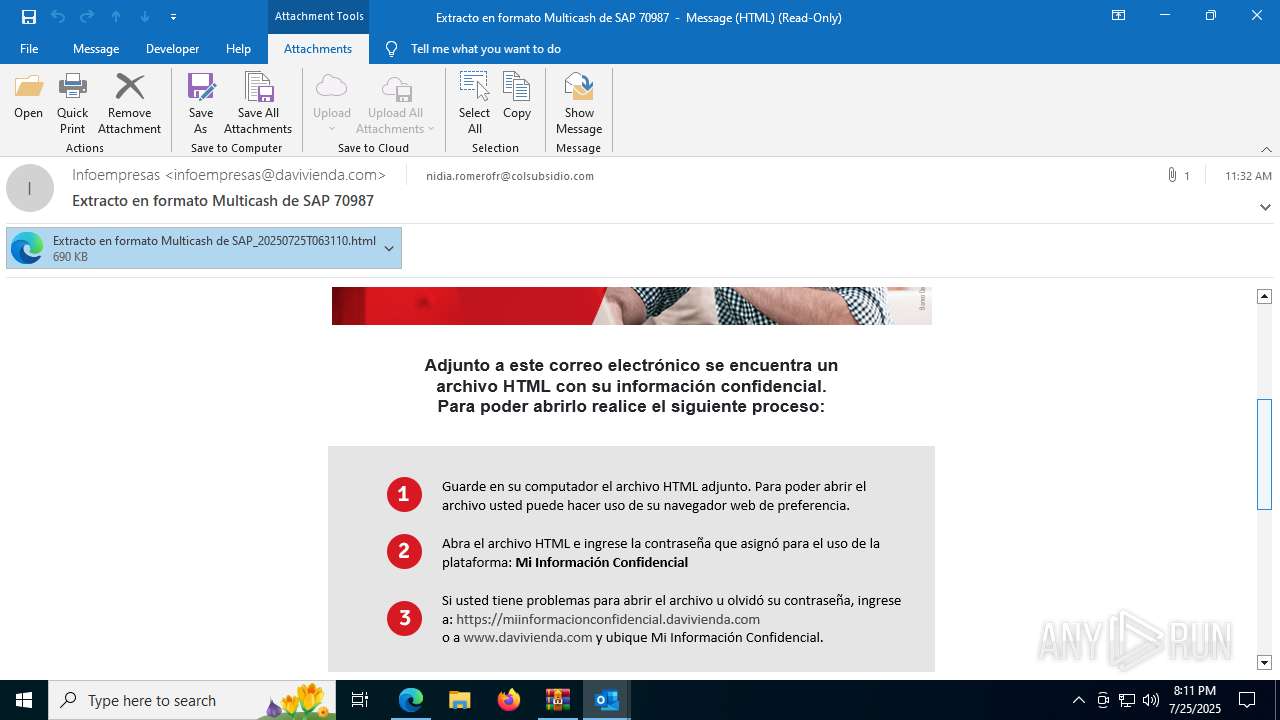
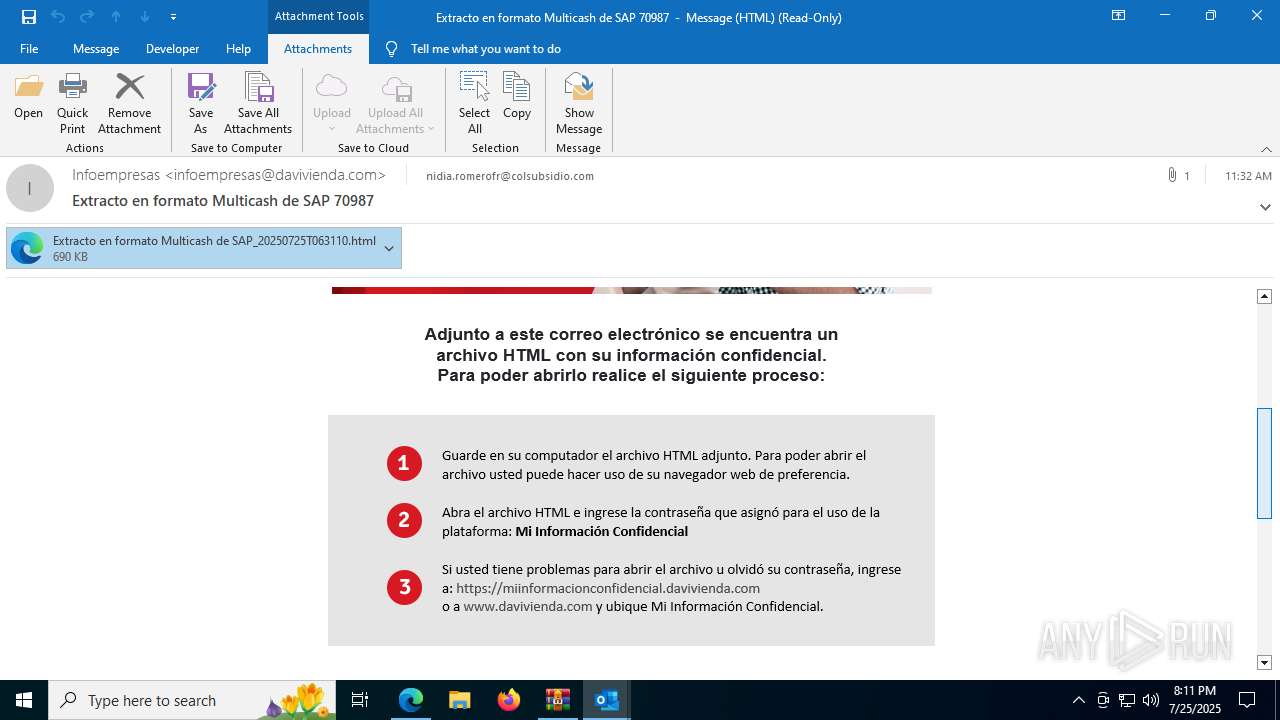
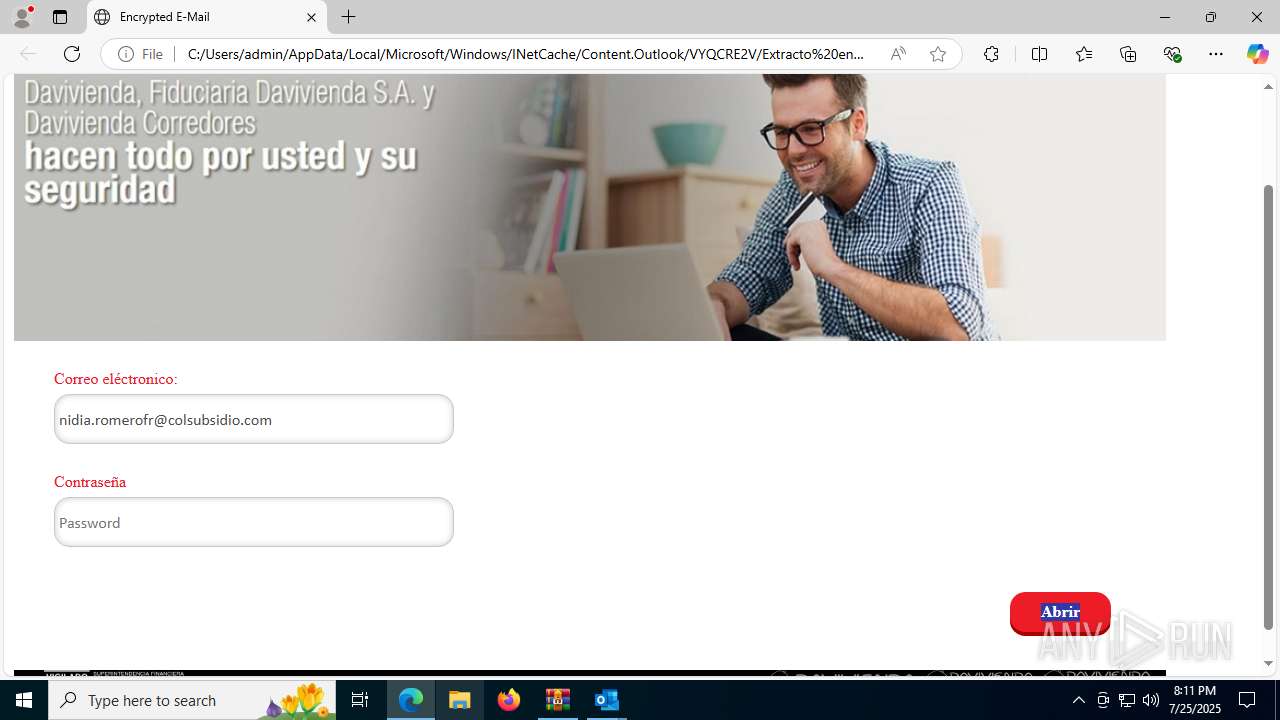
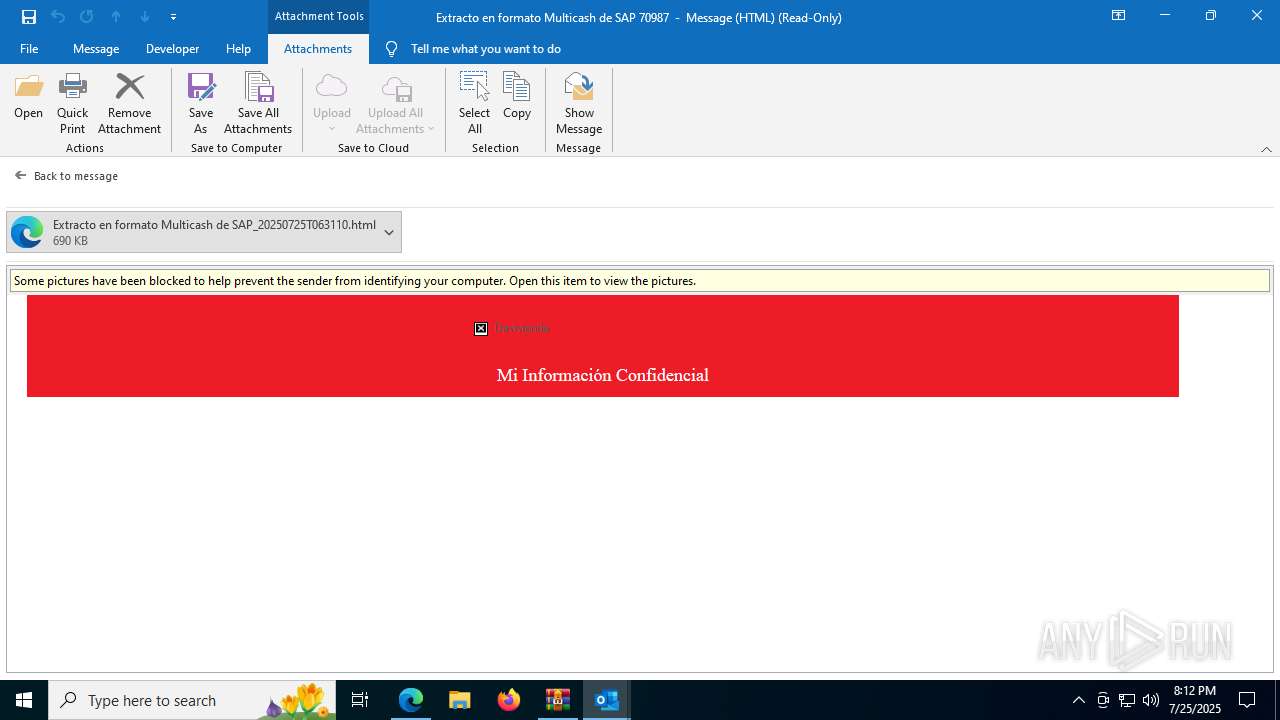
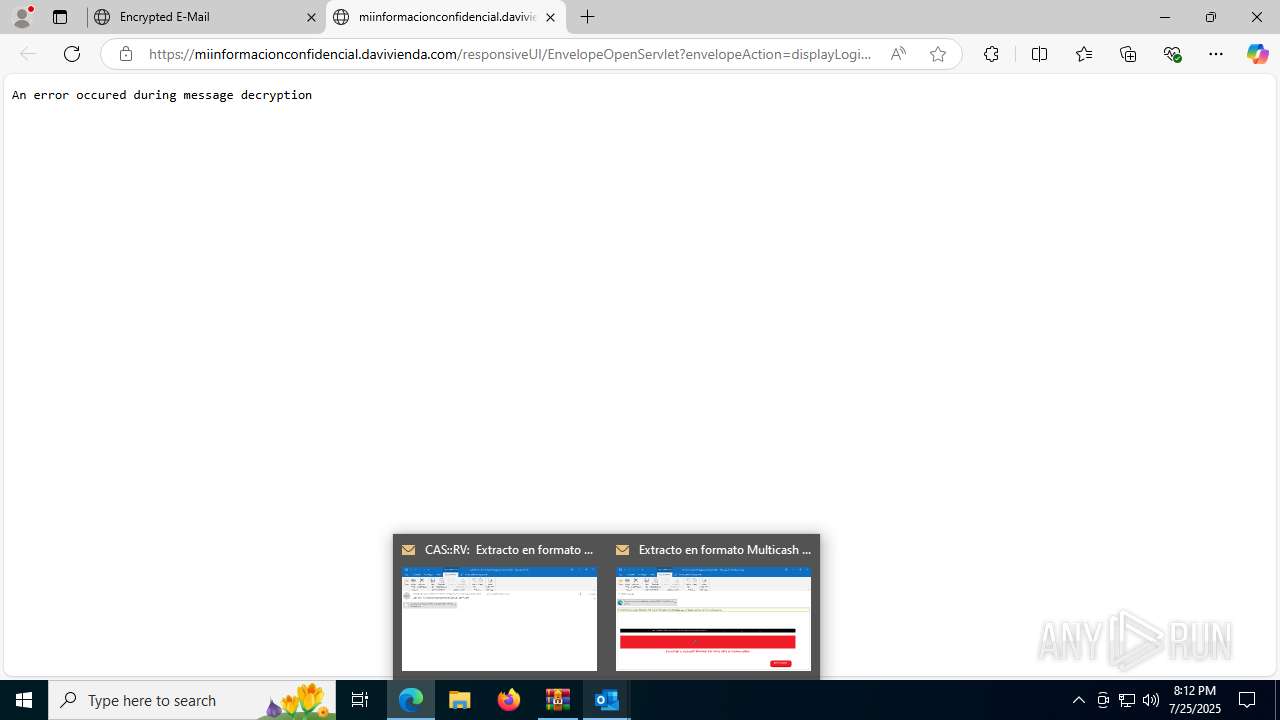
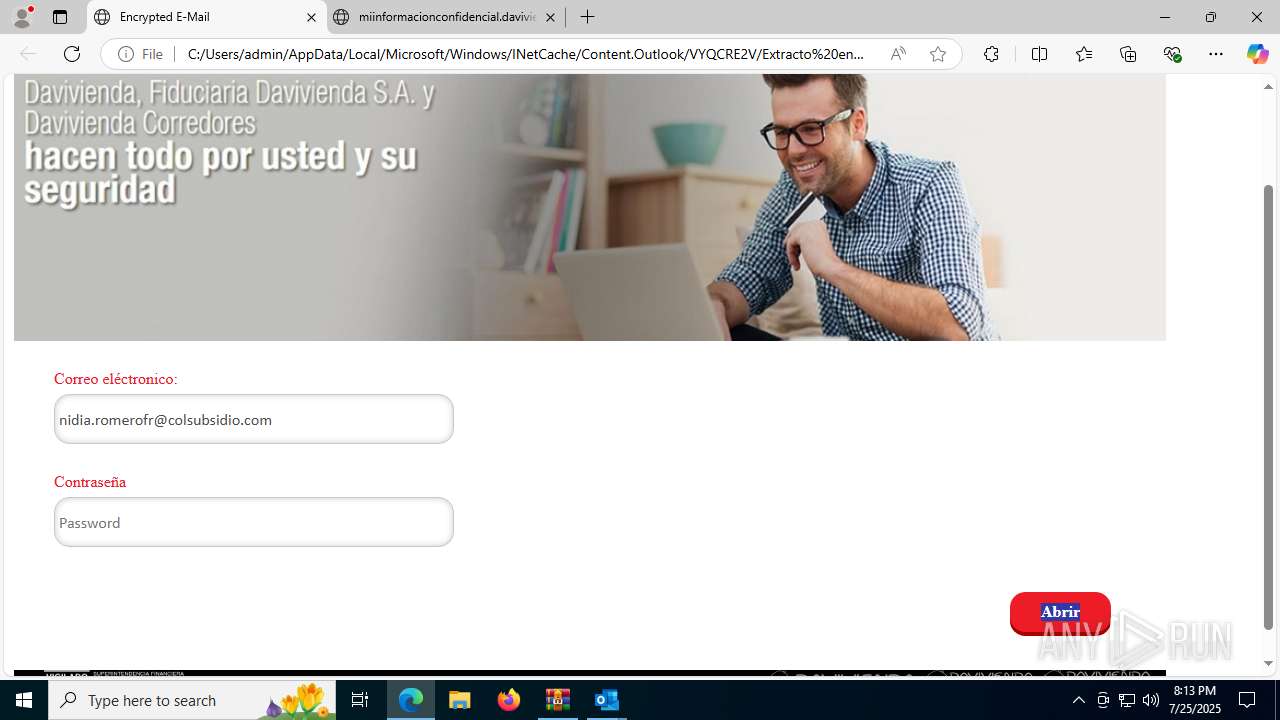
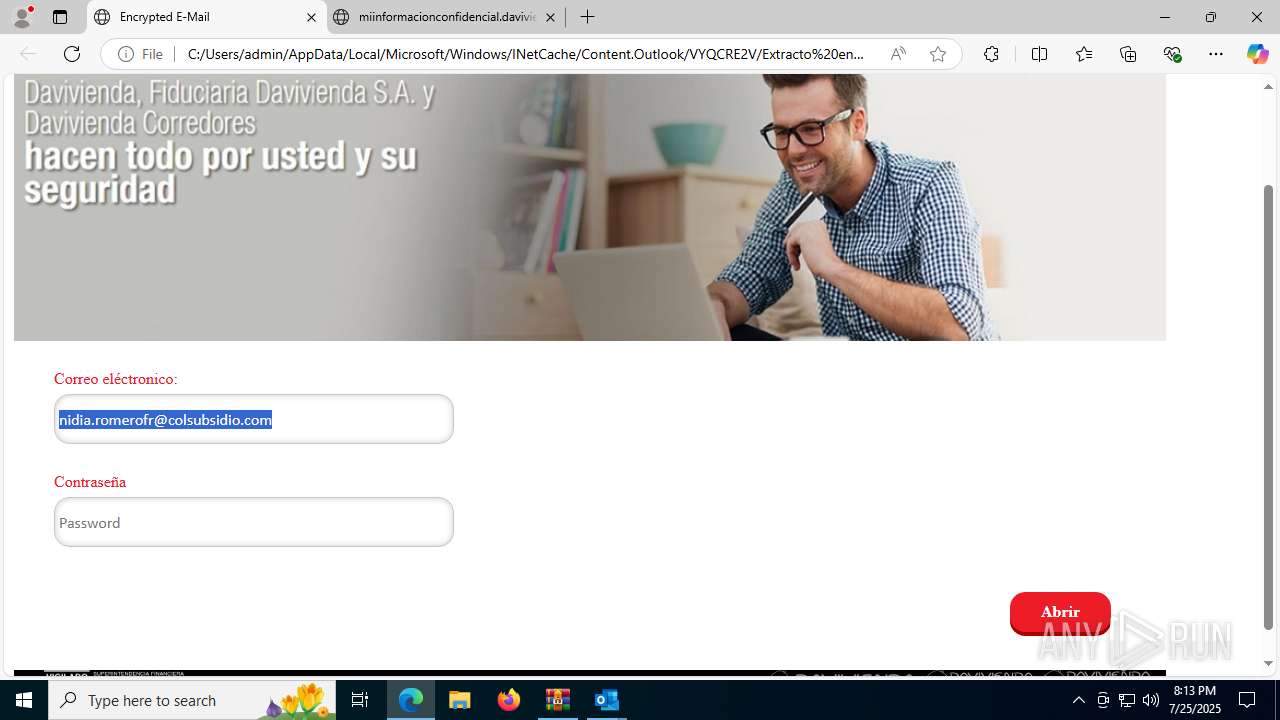
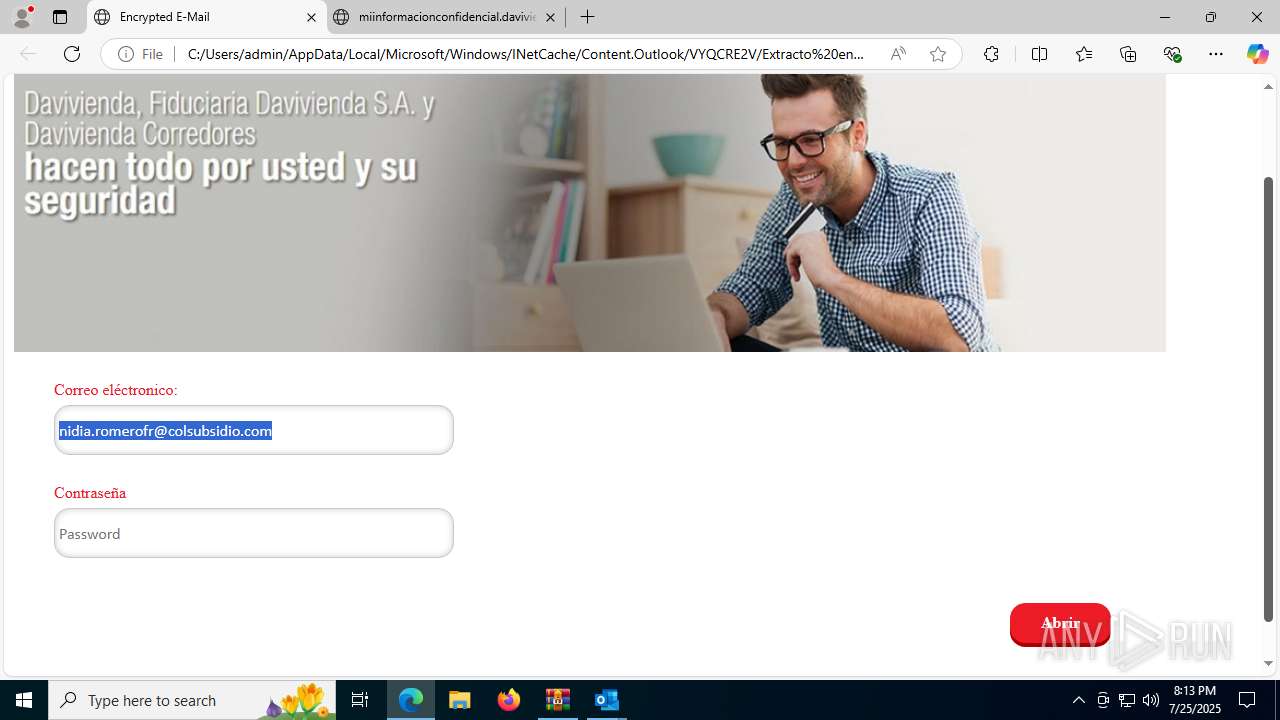
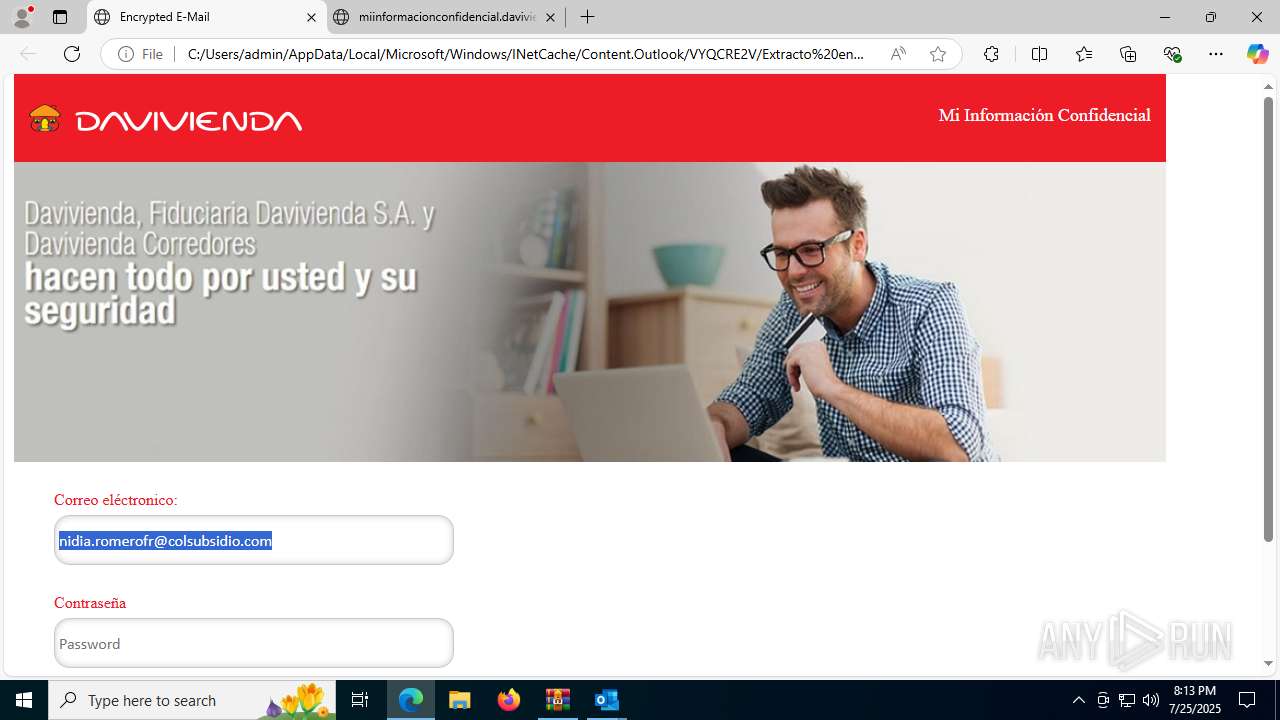
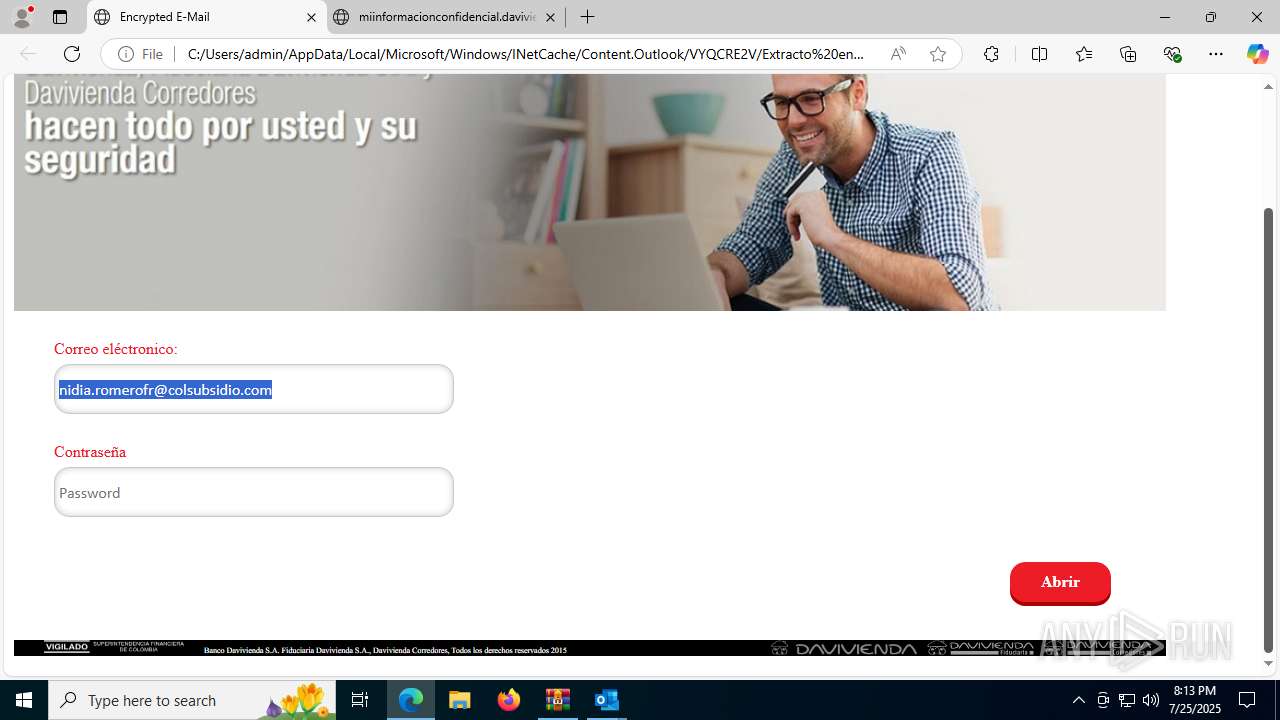
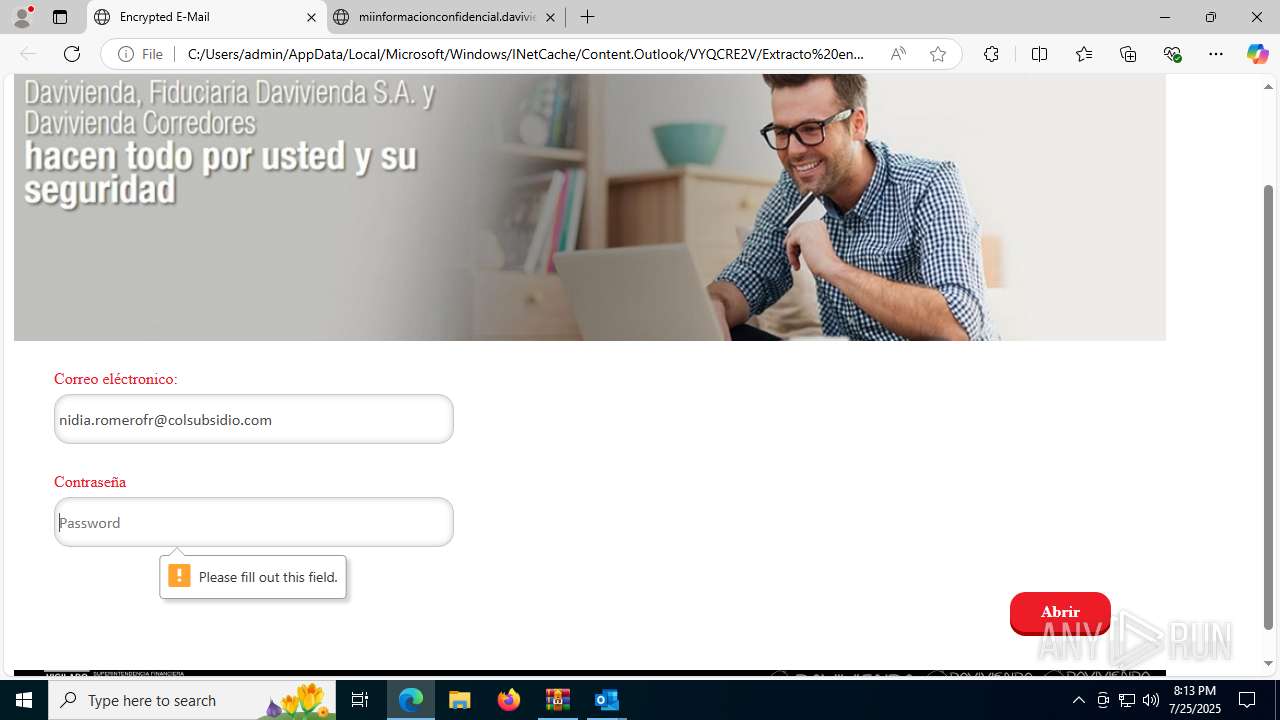
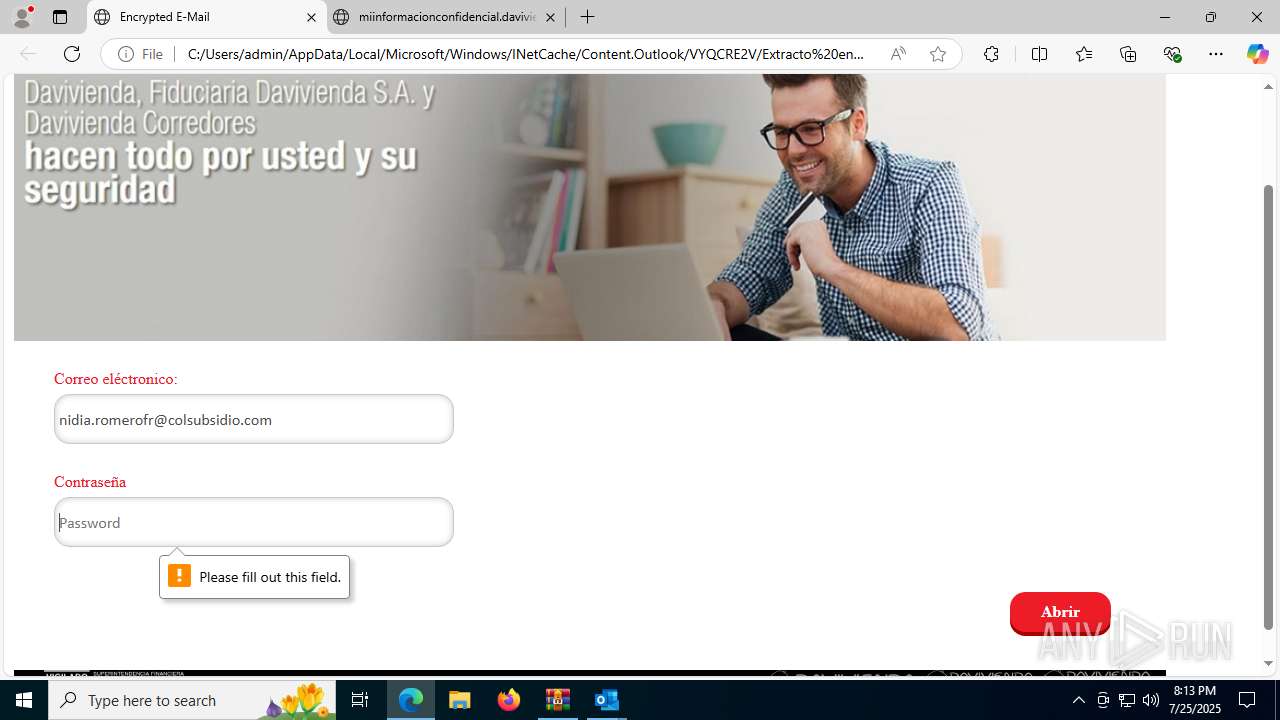
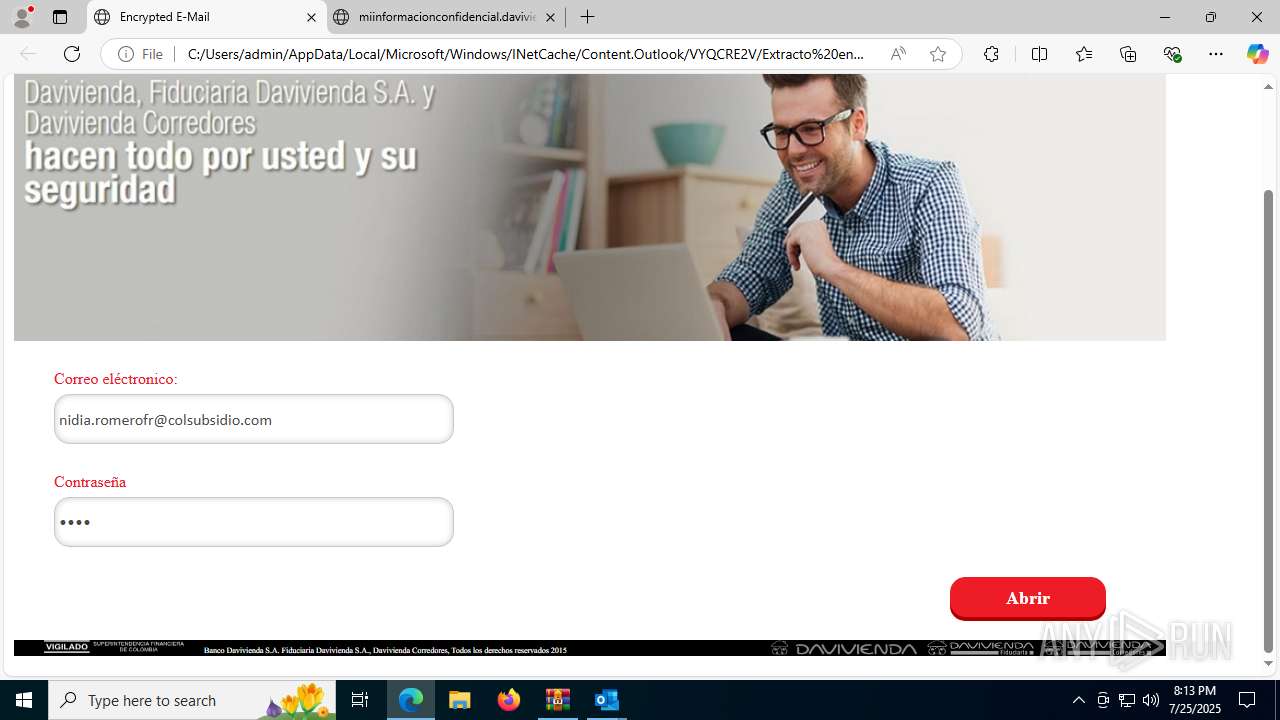
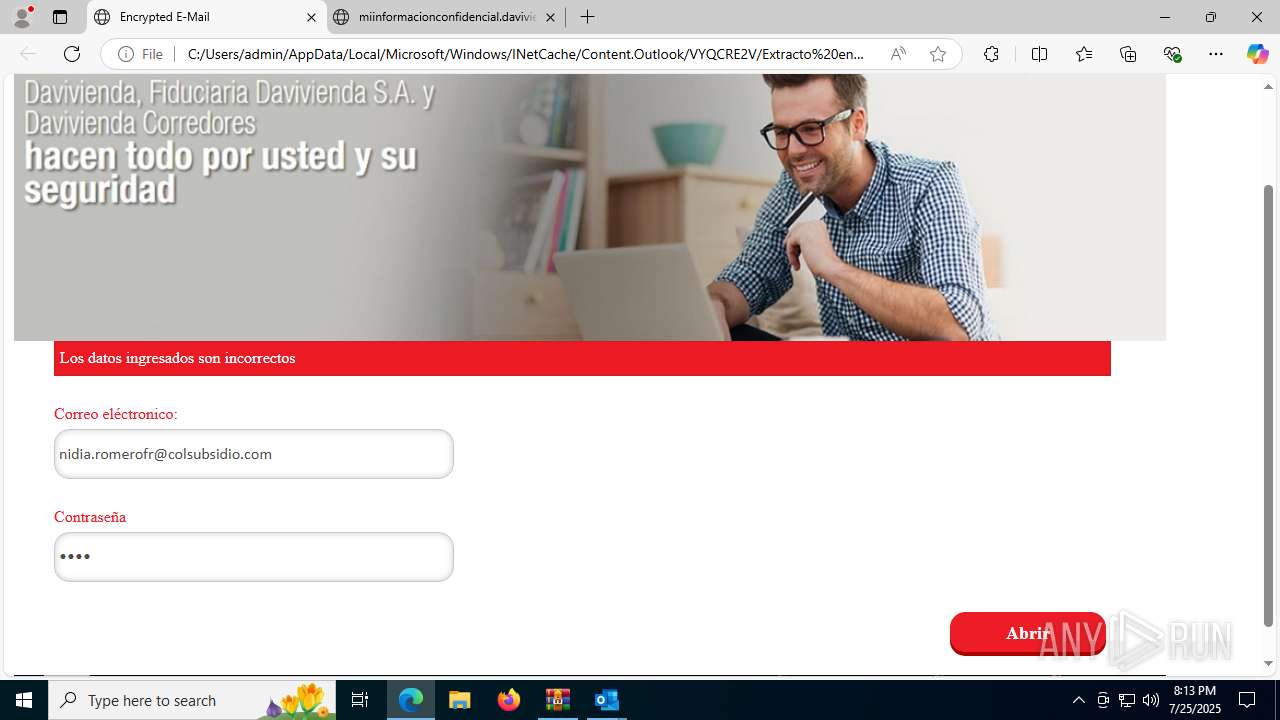
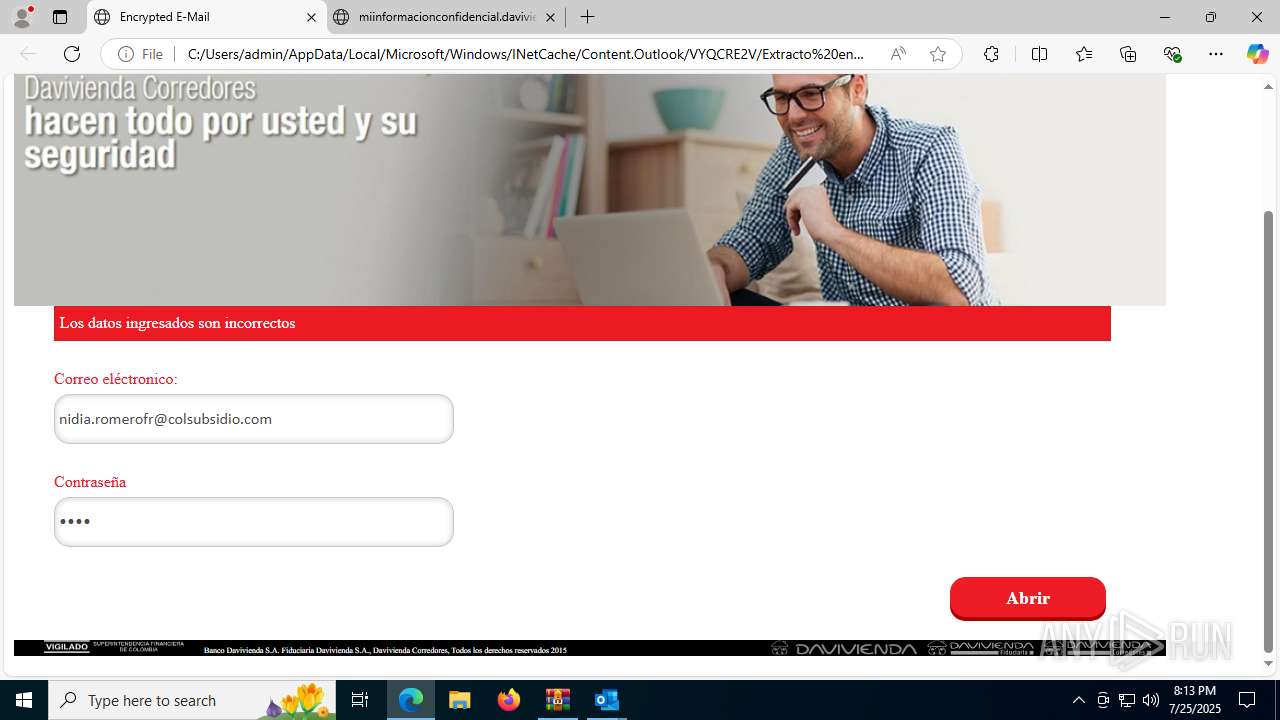
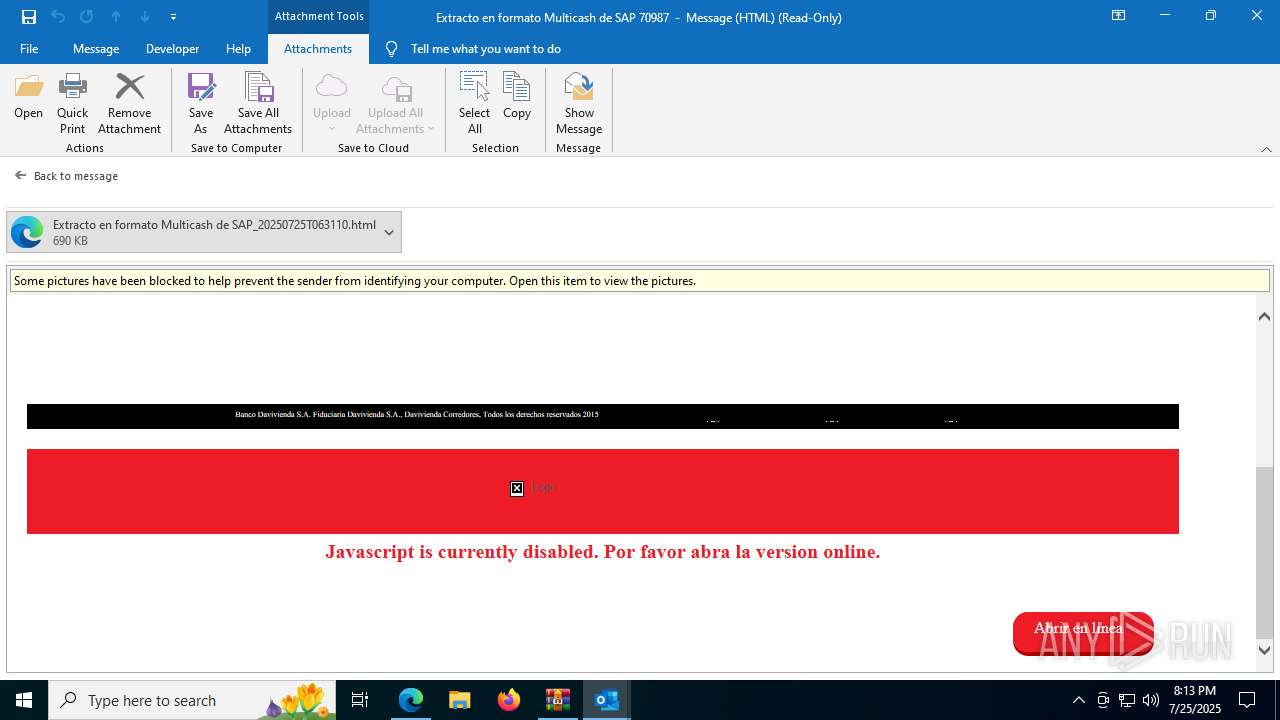
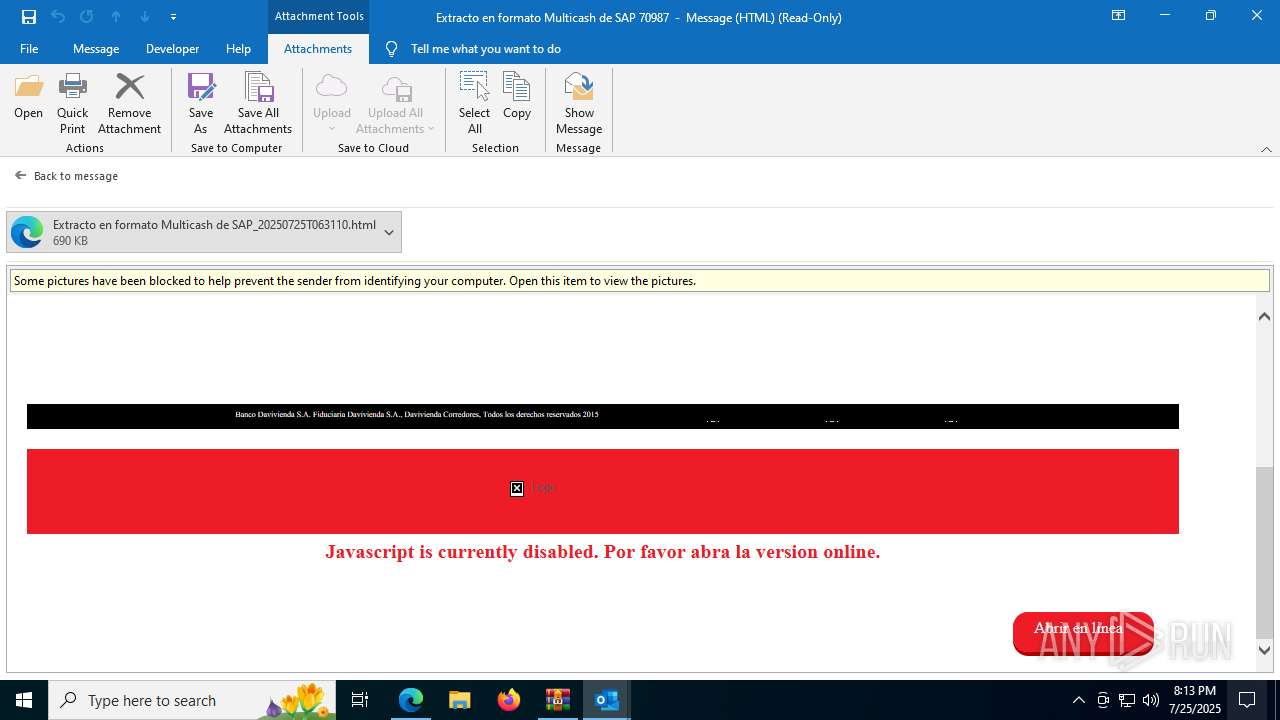
4172 | OUTLOOK.EXE | GET | — | 45.60.197.231:80 | http://miinformacionconfidencial.davivienda.com/email/banner.jpg | unknown | — | — | whitelisted |
4172 | OUTLOOK.EXE | GET | 200 | 45.60.197.231:80 | http://miinformacionconfidencial.davivienda.com/email/1.png | unknown | — | — | whitelisted |
4172 | OUTLOOK.EXE | GET | 304 | 45.60.197.231:80 | http://miinformacionconfidencial.davivienda.com/email/1.png | unknown | — | — | whitelisted |
4172 | OUTLOOK.EXE | GET | 304 | 45.60.197.231:80 | http://miinformacionconfidencial.davivienda.com/email/vigilado.png | unknown | — | — | whitelisted |
4172 | OUTLOOK.EXE | GET | 200 | 45.60.197.231:80 | http://miinformacionconfidencial.davivienda.com/email/banner.jpg | unknown | — | — | whitelisted |
3460 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:PoMjm7LgMMVLrir-fCKFGcGUVKIsl3ppXNMHfJ-TW94&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
4172 | OUTLOOK.EXE | GET | 200 | 18.66.145.213:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkzUBtJnwJkc3SmanzgxeYU%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.74.161.32:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
4172 | OUTLOOK.EXE | GET | 200 | 18.245.65.219:80 | http://ocsp.r2m03.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQqHI%2BsdmapawQncL1rpCEZZ8gTSAQUVdkYX9IczAHhWLS%2Bq9lVQgHXLgICEAqwa1sTQFnohBowmsVh5pA%3D | unknown | — | — | whitelisted |
7856 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1753772300&P2=404&P3=2&P4=SD6HPHIqVPvZekehEEZneDqUXGbAqOMhQe1KvOukTH4Q%2f1bSccLtdO5o082iaUW%2bhDKn0X1nZ1%2bhyZq3YBBcXw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4196 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2996 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2996 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.55.110.211:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
4172 | OUTLOOK.EXE | Misc activity | ET INFO Observed UA-CPU Header |
— | — | Potentially Bad Traffic | ET INFO Possible Chrome Plugin install |
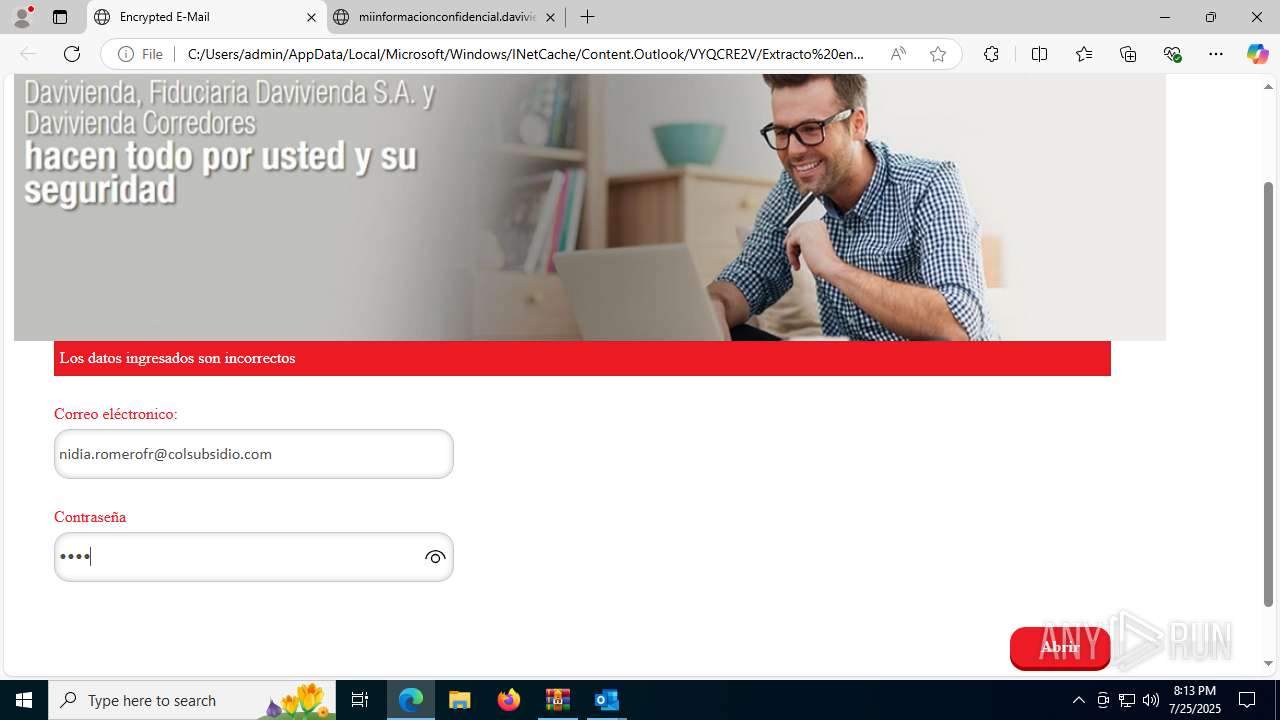
— | — | Potential Corporate Privacy Violation | ET INFO Http Client Body contains otp= in cleartext |
— | — | Potential Corporate Privacy Violation | ET INFO Http Client Body contains otp= in cleartext |