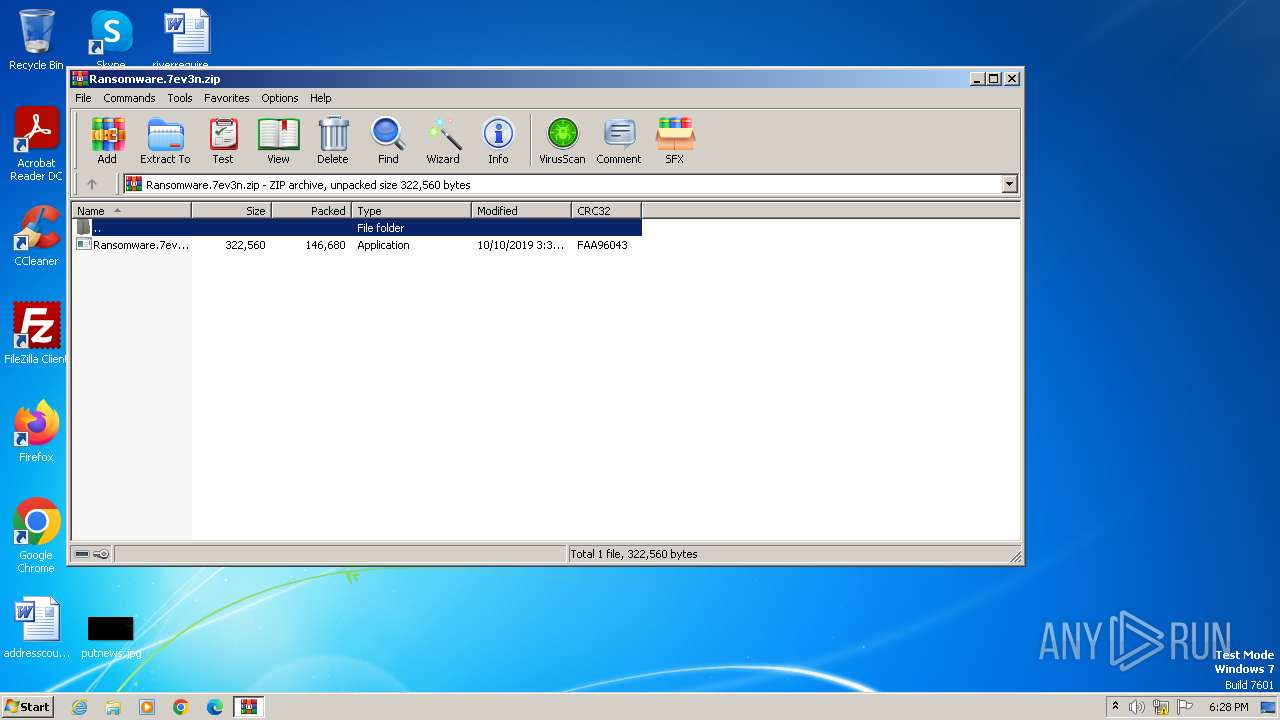
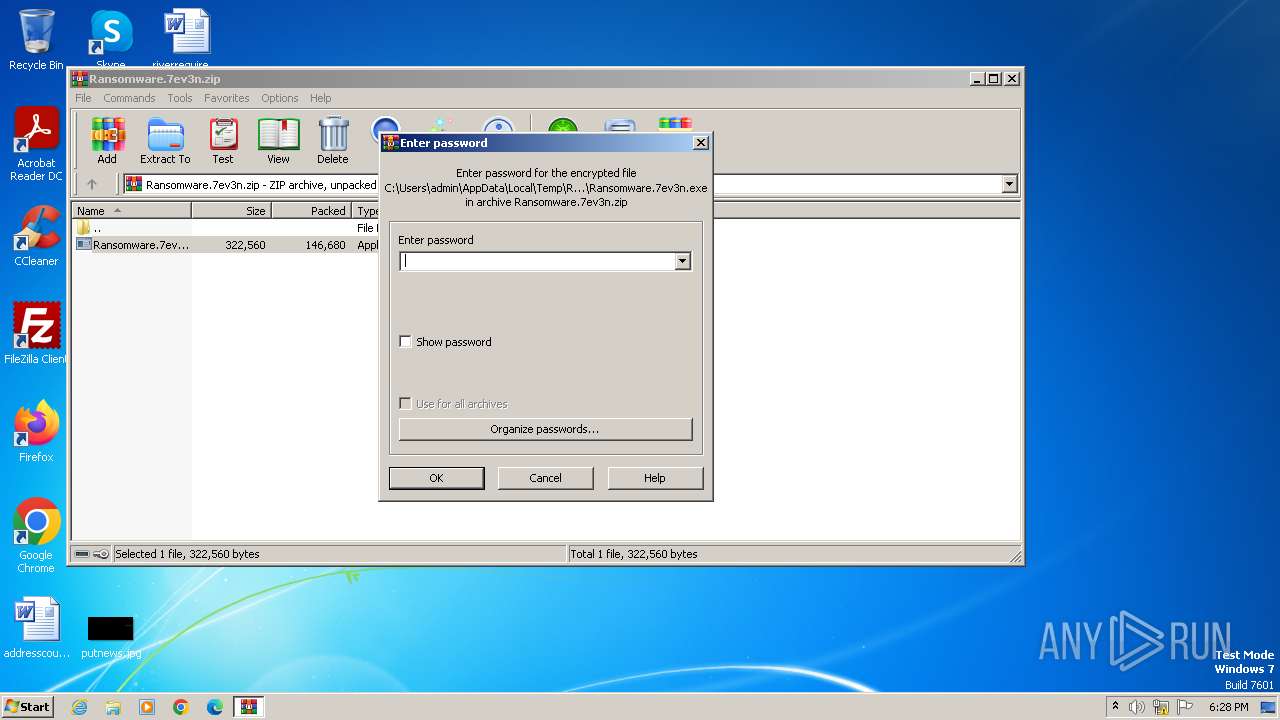
| File name: | Ransomware.7ev3n.zip |
| Full analysis: | https://app.any.run/tasks/cf679f26-2f69-4630-8cae-87c494dd418b |
| Verdict: | Malicious activity |
| Analysis date: | June 04, 2024, 17:28:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=AES Encrypted |
| MD5: | 71F4666373DB57958635DE89EDB58A65 |
| SHA1: | 71B4504062E2C0C08B03E39387633FB068705DA7 |
| SHA256: | 72810CDF913169DF2B42ABAF2D34840CA04B91D640B778CA2580F744BE1DAA1D |
| SSDEEP: | 6144:4CXgeVc8YG8ekHKb4s1pNLAsqbzZFRWqe:4CXgeVc8DjkHDKpusqRFRWqe |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3964)
- Ransomware.7ev3n.exe (PID: 4004)
- uac.exe (PID: 1876)
- system.exe (PID: 1020)
Creates a writable file in the system directory
- wusa.exe (PID: 1604)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 2284)
Changes the login/logoff helper path in the registry
- reg.exe (PID: 2448)
Changes the autorun value in the registry
- reg.exe (PID: 2340)
UAC/LUA settings modification
- reg.exe (PID: 1044)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3964)
- Ransomware.7ev3n.exe (PID: 4004)
- uac.exe (PID: 1876)
- system.exe (PID: 1852)
The process creates files with name similar to system file names
- Ransomware.7ev3n.exe (PID: 4004)
Executable content was dropped or overwritten
- Ransomware.7ev3n.exe (PID: 4004)
- uac.exe (PID: 1876)
- wusa.exe (PID: 1604)
- system.exe (PID: 1020)
Reads the Internet Settings
- Ransomware.7ev3n.exe (PID: 4004)
- uac.exe (PID: 1876)
- cmd.exe (PID: 336)
- system.exe (PID: 1852)
Starts itself from another location
- Ransomware.7ev3n.exe (PID: 4004)
Executing commands from a ".bat" file
- system.exe (PID: 1020)
- system.exe (PID: 1852)
Starts CMD.EXE for commands execution
- system.exe (PID: 1020)
- uac.exe (PID: 1876)
- system.exe (PID: 1852)
Process drops legitimate windows executable
- uac.exe (PID: 1876)
- wusa.exe (PID: 1604)
The executable file from the user directory is run by the CMD process
- uac.exe (PID: 1876)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1936)
- cmd.exe (PID: 2172)
- cmd.exe (PID: 1804)
- cmd.exe (PID: 2080)
- cmd.exe (PID: 2524)
- cmd.exe (PID: 1676)
- cmd.exe (PID: 2692)
INFO
Checks supported languages
- Ransomware.7ev3n.exe (PID: 4004)
- system.exe (PID: 1020)
- uac.exe (PID: 1876)
- system.exe (PID: 1852)
Reads the computer name
- Ransomware.7ev3n.exe (PID: 4004)
- system.exe (PID: 1020)
- uac.exe (PID: 1876)
- system.exe (PID: 1852)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3964)
Reads the machine GUID from the registry
- Ransomware.7ev3n.exe (PID: 4004)
- system.exe (PID: 1020)
- system.exe (PID: 1852)
Creates files or folders in the user directory
- Ransomware.7ev3n.exe (PID: 4004)
- system.exe (PID: 1020)
- system.exe (PID: 1852)
Checks proxy server information
- Ransomware.7ev3n.exe (PID: 4004)
- system.exe (PID: 1852)
Create files in a temporary directory
- uac.exe (PID: 1876)
Drops the executable file immediately after the start
- wusa.exe (PID: 1604)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2019:10:10 18:33:38 |
| ZipCRC: | 0xfaa96043 |
| ZipCompressedSize: | 146680 |
| ZipUncompressedSize: | 322560 |
| ZipFileName: | Ransomware.7ev3n.exe |
Total processes
80
Monitored processes
30
Malicious processes
5
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 336 | "C:\Windows\System32\cmd.exe" /c wusa C:\Users\admin\AppData\Local\Temp\ellocnak.msu /extract:%windir%\system32\sysprep | C:\Windows\System32\cmd.exe | — | uac.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 664 | REG ADD "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Keyboard Layout" /v "Scancode Map" /t REG_BINARY /d "00000000000000001700000000003800000038e000005be000005ce00000360000001d0000001de000000f000000010000001c0000003e0000003b00000044000000450000003d0000005de000000000" /f /reg:64 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 752 | cmd.exe /c C:\Users\admin\AppData\Local\uac.exe 32 C:\Users\admin\AppData\Local\system.exe | C:\Windows\System32\cmd.exe | — | system.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1020 | "C:\Users\admin\AppData\Local\system.exe" | C:\Users\admin\AppData\Local\system.exe | Ransomware.7ev3n.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 1036 | C:\Windows\system32\cmd.exe /c C:\Users\admin\AppData\Local\del.bat | C:\Windows\System32\cmd.exe | — | system.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1044 | REG ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System" /v "EnableLUA" /t REG_DWORD /d 0 /f /reg:64 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1424 | "C:\Windows\system32\sysprep\winsat.exe" | C:\Windows\System32\sysprep\winsat.exe | — | uac.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows System Assessment Tool Exit code: 3221226540 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1604 | "C:\Windows\system32\wusa.exe" C:\Users\admin\AppData\Local\Temp\ellocnak.msu /extract:C:\Windows\system32\sysprep | C:\Windows\System32\wusa.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Update Standalone Installer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1676 | C:\windows\system32\cmd.exe /c REG ADD "HKEY_CURRENT_USER\Control Panel\Accessibility\StickyKeys" /v "Flags" /t REG_SZ /d 506 /f /reg:64 | C:\Windows\System32\cmd.exe | — | system.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1804 | C:\windows\system32\cmd.exe /c REG ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon" /v "Shell" /t REG_SZ /d "C:\Users\admin\AppData\Local\system.exe" /f /reg:64 | C:\Windows\System32\cmd.exe | — | system.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
6 619
Read events
6 494
Write events
110
Delete events
15
Modification events
| (PID) Process: | (3964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3964) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Ransomware.7ev3n.zip | |||
| (PID) Process: | (3964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3964) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
9
Suspicious files
42
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3964 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3964.41109\Ransomware.7ev3n.exe | executable | |
MD5:9F8BC96C96D43ECB69F883388D228754 | SHA256:7D373CCB96D1DBB1856EF31AFA87C2112A0C1795A796AB01CB154700288AFEC5 | |||
| 1020 | system.exe | C:\Users\admin\AppData\Local\uac.exe | executable | |
MD5:7A681D8650D2C28D18AC630C34B2014E | SHA256:DC9A23D245F51AF512782F637CD97C29FFB0809D9245DBC1C0DFA34AE2024C21 | |||
| 1876 | uac.exe | C:\Users\admin\AppData\Local\Temp\winsat.exe | executable | |
MD5:886B0EAA3B0FE76B3204E687C8DA6F66 | SHA256:B007057E6728C7E954CAEB45EAE0ADCD1C027DCB160746CCD2E78F91D18CCF80 | |||
| 4004 | Ransomware.7ev3n.exe | C:\Users\admin\AppData\Local\system.exe | executable | |
MD5:9F8BC96C96D43ECB69F883388D228754 | SHA256:7D373CCB96D1DBB1856EF31AFA87C2112A0C1795A796AB01CB154700288AFEC5 | |||
| 1876 | uac.exe | C:\Users\admin\AppData\Local\Temp\powrprof.dll | executable | |
MD5:F035352F9FDA534E2BF8417EFDED77DC | SHA256:150E78743248CAF78E1972A293B7AA18CF219F146CEF7B5771A76B51A9829D3A | |||
| 1876 | uac.exe | C:\Users\admin\AppData\Local\Temp\emc7E59.tmp | binary | |
MD5:4FC49E1A0F83A21BDC5E34B62EEB0D62 | SHA256:DAFC9806A73EC7652F24F11477A71681AA82A20C56CB752943A39E360CD794A6 | |||
| 1876 | uac.exe | C:\Users\admin\AppData\Local\Temp\ellocnak.msu | compressed | |
MD5:1DCA187AC48871627D2BC7471786B368 | SHA256:60F69AD330F33A0716366DEEDFEDC61A81FF32EDD581218CD3C63A11C8F487FD | |||
| 1876 | uac.exe | C:\Users\admin\AppData\Local\Temp\emc7E5B.tmp | binary | |
MD5:39C8E62DC7158D24AB6DFF87200C5386 | SHA256:17F4D890E57082463F7267E4768210A77690952223A4F37B871AE3EA76912358 | |||
| 1876 | uac.exe | C:\Users\admin\AppData\Local\Temp\emc7E5D.tmp | binary | |
MD5:A7F30B548064E90EB78A31EA25365C62 | SHA256:886F45A01E33622362828D49D0EDAADD59D8760A0581095B42916055059B50A4 | |||
| 1876 | uac.exe | C:\Users\admin\AppData\Local\Temp\emc7E5C.tmp | binary | |
MD5:C049AC4B753B53C51EAFDBF5A77AD54E | SHA256:8457508294FACA764A33CE788C3F6B1A35C02A3A602A3A904E45156998A6A44B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
8
DNS requests
4
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4004 | Ransomware.7ev3n.exe | 104.16.236.243:443 | blockchain.info | CLOUDFLARENET | — | unknown |
1852 | system.exe | 49.13.77.253:80 | jaster.in | Hetzner Online GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
blockchain.info |
| unknown |
jaster.in |
| unknown |
dns.msftncsi.com |
| shared |
Threats
Process | Message |
|---|---|
uac.exe | [UCM] Dll dropped successfully |
winsat.exe | Akagi letter found |
winsat.exe | C:\Users\admin\AppData\Local\system.exe |
winsat.exe | Fubuki at your service.
|