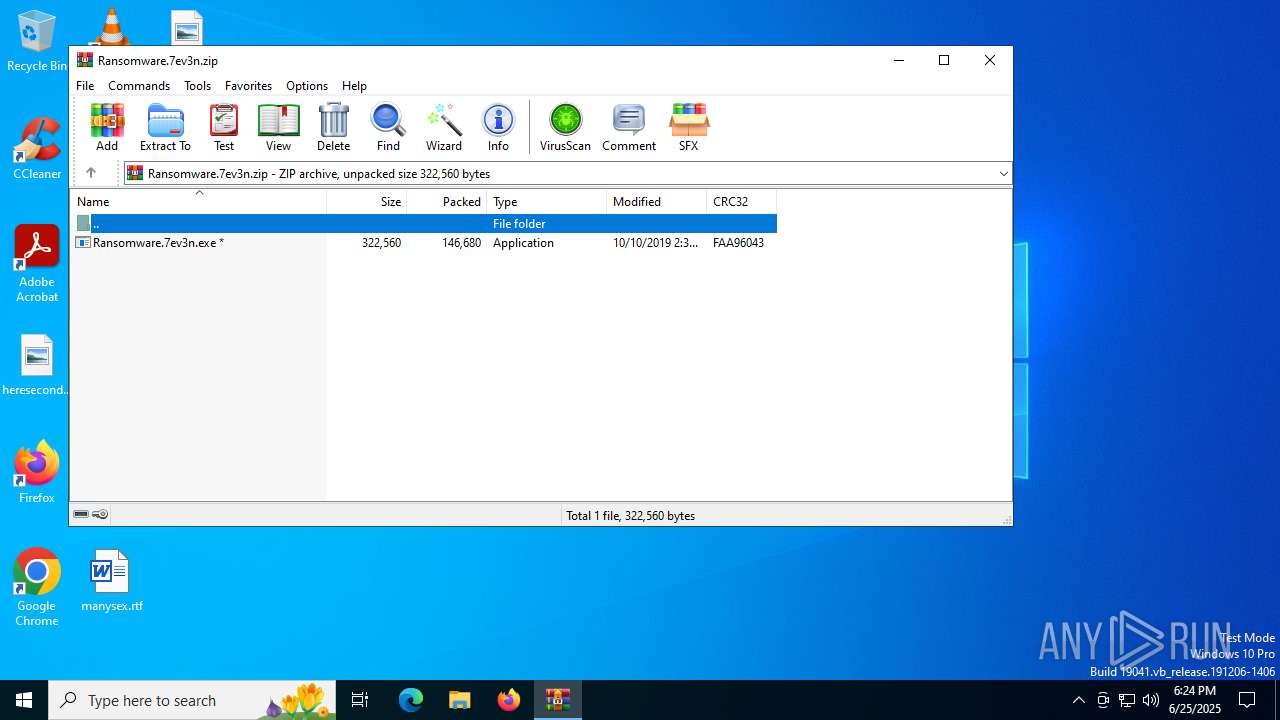
| File name: | Ransomware.7ev3n.zip |
| Full analysis: | https://app.any.run/tasks/2e2cdf2b-6396-4192-98c9-abd4e15bb518 |
| Verdict: | Malicious activity |
| Analysis date: | June 25, 2025, 18:24:23 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
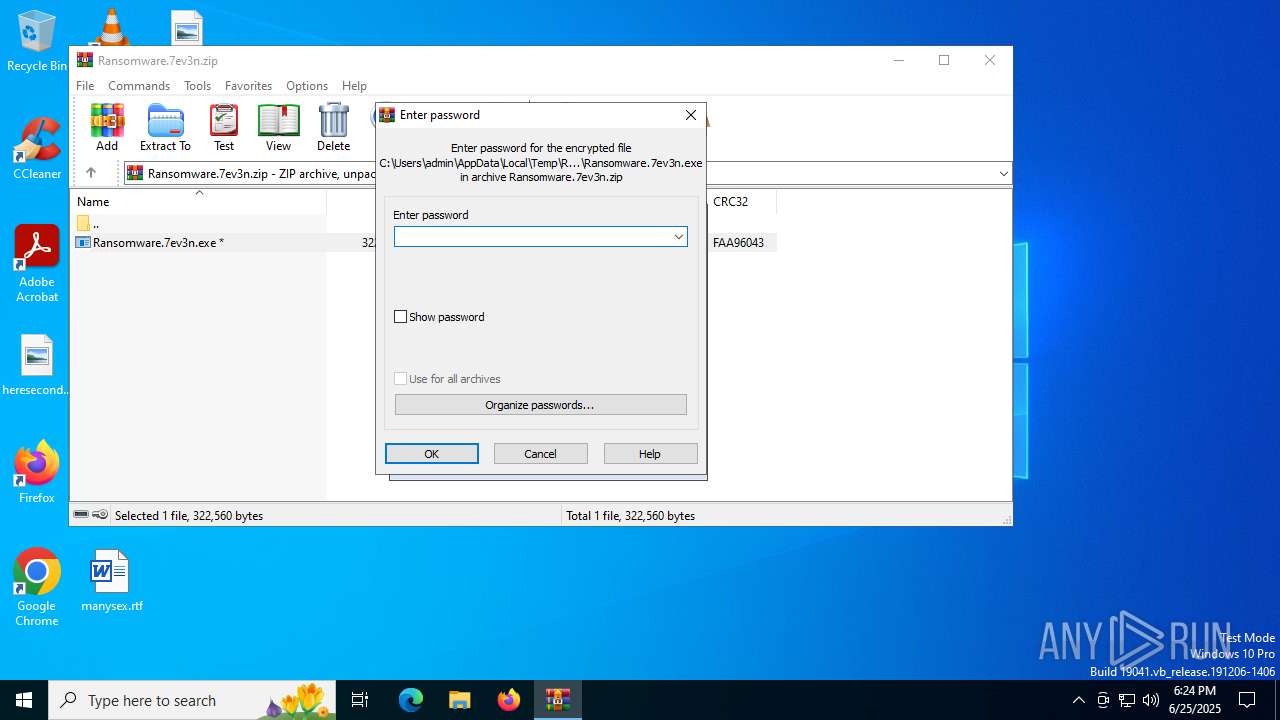
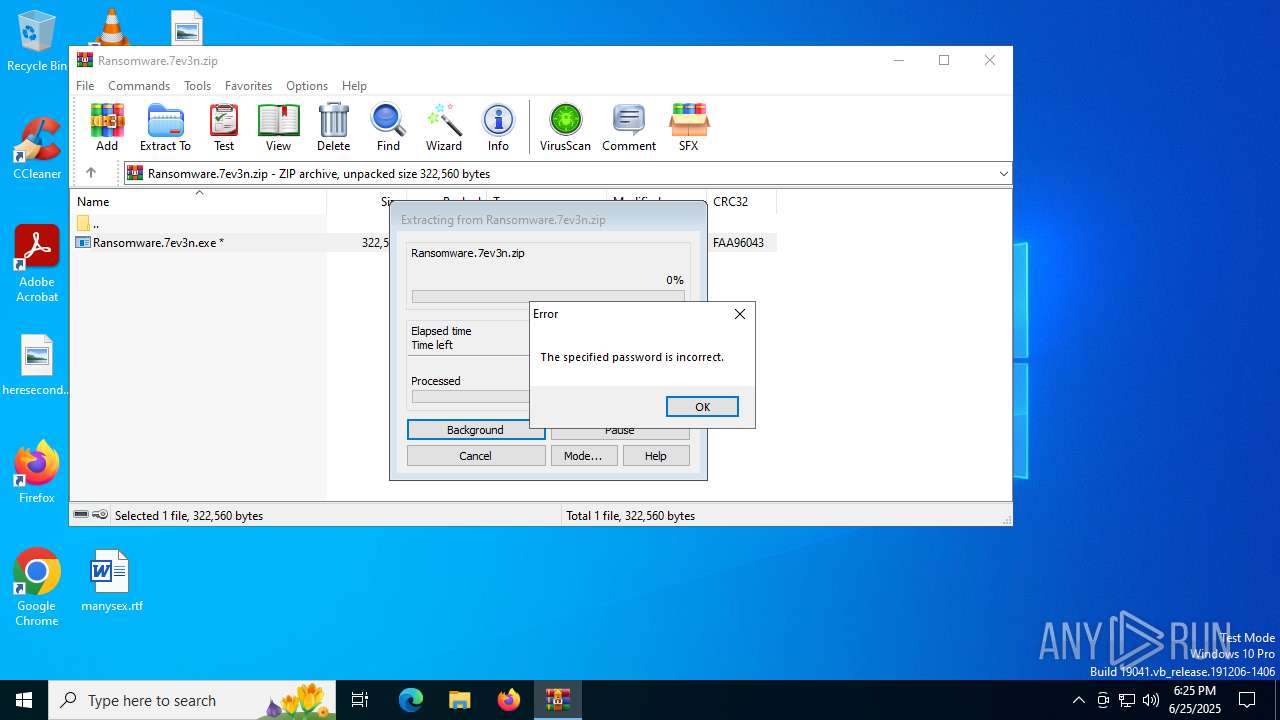
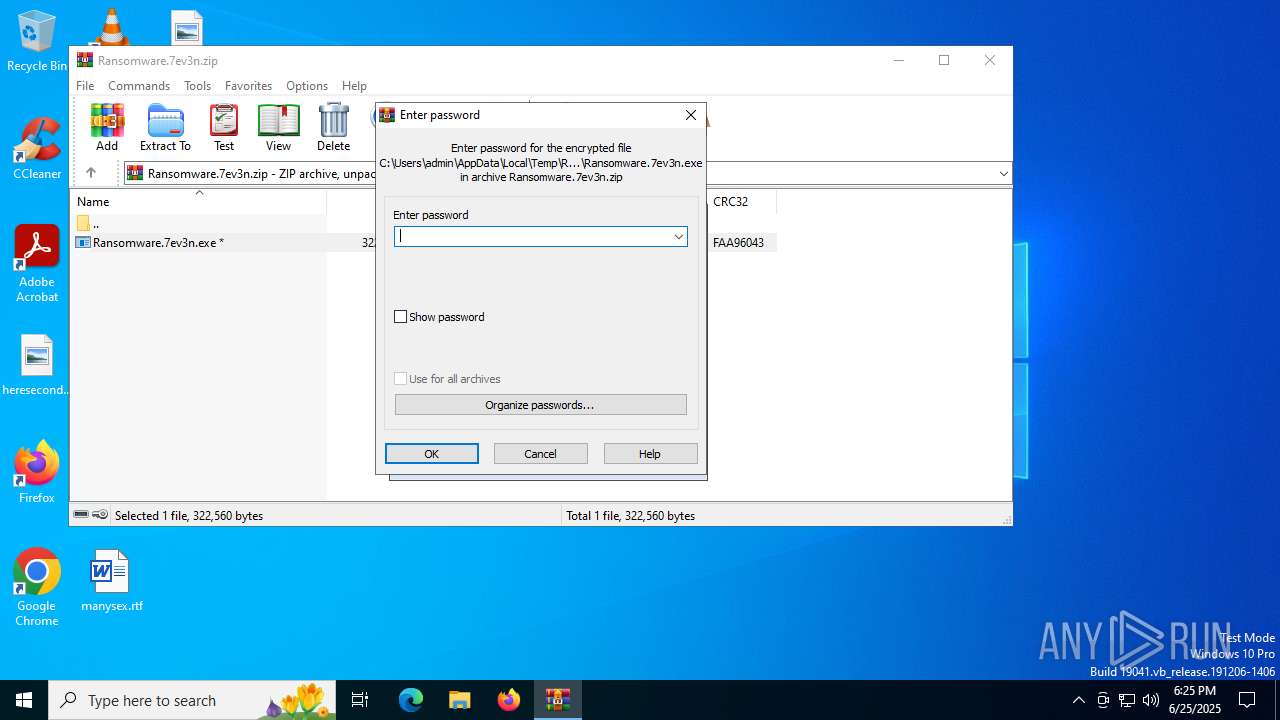
| File info: | Zip archive data, at least v2.0 to extract, compression method=AES Encrypted |
| MD5: | 71F4666373DB57958635DE89EDB58A65 |
| SHA1: | 71B4504062E2C0C08B03E39387633FB068705DA7 |
| SHA256: | 72810CDF913169DF2B42ABAF2D34840CA04B91D640B778CA2580F744BE1DAA1D |
| SSDEEP: | 6144:4CXgeVc8YG8ekHKb4s1pNLAsqbzZFRWqe:4CXgeVc8DjkHDKpusqRFRWqe |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5980)
Application was injected by another process
- explorer.exe (PID: 4772)
Runs injected code in another process
- uac.exe (PID: 2692)
- uac.exe (PID: 1128)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5980)
- Ransomware.7ev3n.exe (PID: 3704)
- uac.exe (PID: 2692)
- uac.exe (PID: 1128)
The process creates files with name similar to system file names
- Ransomware.7ev3n.exe (PID: 3704)
Executable content was dropped or overwritten
- Ransomware.7ev3n.exe (PID: 3704)
- system.exe (PID: 3572)
- uac.exe (PID: 2692)
- dllhost.exe (PID: 1336)
- uac.exe (PID: 1128)
- dllhost.exe (PID: 5468)
Starts itself from another location
- Ransomware.7ev3n.exe (PID: 3704)
Executing commands from a ".bat" file
- system.exe (PID: 3572)
- Ransomware.7ev3n.exe (PID: 5020)
Starts CMD.EXE for commands execution
- system.exe (PID: 3572)
- Ransomware.7ev3n.exe (PID: 5020)
The executable file from the user directory is run by the CMD process
- uac.exe (PID: 2692)
- uac.exe (PID: 1128)
Reads the date of Windows installation
- uac.exe (PID: 2692)
- uac.exe (PID: 1128)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5980)
Reads the computer name
- Ransomware.7ev3n.exe (PID: 3704)
- system.exe (PID: 3572)
- uac.exe (PID: 2692)
- Ransomware.7ev3n.exe (PID: 5020)
- uac.exe (PID: 1128)
Checks supported languages
- Ransomware.7ev3n.exe (PID: 3704)
- system.exe (PID: 3572)
- uac.exe (PID: 2692)
- Ransomware.7ev3n.exe (PID: 5020)
- uac.exe (PID: 1128)
Reads the machine GUID from the registry
- Ransomware.7ev3n.exe (PID: 3704)
- system.exe (PID: 3572)
- Ransomware.7ev3n.exe (PID: 5020)
Creates files or folders in the user directory
- Ransomware.7ev3n.exe (PID: 3704)
- system.exe (PID: 3572)
- mmc.exe (PID: 4920)
Checks proxy server information
- Ransomware.7ev3n.exe (PID: 3704)
Reads the software policy settings
- Ransomware.7ev3n.exe (PID: 3704)
- mmc.exe (PID: 4920)
- mmc.exe (PID: 5920)
The sample compiled with english language support
- system.exe (PID: 3572)
- uac.exe (PID: 2692)
- dllhost.exe (PID: 1336)
- dllhost.exe (PID: 5468)
- uac.exe (PID: 1128)
Create files in a temporary directory
- uac.exe (PID: 2692)
- uac.exe (PID: 1128)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 1336)
- mmc.exe (PID: 4920)
- dllhost.exe (PID: 5468)
- mmc.exe (PID: 5920)
- explorer.exe (PID: 4772)
Checks transactions between databases Windows and Oracle
- explorer.exe (PID: 4772)
Process checks computer location settings
- uac.exe (PID: 2692)
- uac.exe (PID: 1128)
Creates files in the program directory
- mmc.exe (PID: 4920)
- mmc.exe (PID: 5920)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2019:10:10 18:33:38 |
| ZipCRC: | 0xfaa96043 |
| ZipCompressedSize: | 146680 |
| ZipUncompressedSize: | 322560 |
| ZipFileName: | Ransomware.7ev3n.exe |
Total processes
163
Monitored processes
22
Malicious processes
3
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1128 | C:\Users\admin\AppData\Local\uac.exe 64 C:\Users\admin\AppData\Local\system.exe | C:\Users\admin\AppData\Local\uac.exe | cmd.exe | ||||||||||||
User: admin Company: UG North Integrity Level: MEDIUM Description: UACMe main module Exit code: 0 Version: 1.9.0.0 Modules
| |||||||||||||||
| 1336 | C:\WINDOWS\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\System32\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1936 | "C:\Windows\System32\mmc.exe" eventvwr.msc | C:\Windows\System32\mmc.exe | — | uac.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Management Console Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1948 | cmd.exe /c C:\Users\admin\AppData\Local\uac.exe 64 C:\Users\admin\AppData\Local\system.exe | C:\Windows\SysWOW64\cmd.exe | — | Ransomware.7ev3n.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2076 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2692 | C:\Users\admin\AppData\Local\uac.exe 64 C:\Users\admin\AppData\Local\system.exe | C:\Users\admin\AppData\Local\uac.exe | cmd.exe | ||||||||||||
User: admin Company: UG North Integrity Level: MEDIUM Description: UACMe main module Exit code: 0 Version: 1.9.0.0 Modules
| |||||||||||||||
| 3148 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3196 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3572 | "C:\Users\admin\AppData\Local\system.exe" | C:\Users\admin\AppData\Local\system.exe | Ransomware.7ev3n.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
Total events
17 394
Read events
17 340
Write events
50
Delete events
4
Modification events
| (PID) Process: | (5980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Ransomware.7ev3n.zip | |||
| (PID) Process: | (5980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000702E4 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (5980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
8
Suspicious files
3
Text files
5
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3704 | Ransomware.7ev3n.exe | C:\Users\admin\AppData\Local\system.exe | executable | |
MD5:9F8BC96C96D43ECB69F883388D228754 | SHA256:7D373CCB96D1DBB1856EF31AFA87C2112A0C1795A796AB01CB154700288AFEC5 | |||
| 5980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb5980.18407\Ransomware.7ev3n.exe | executable | |
MD5:9F8BC96C96D43ECB69F883388D228754 | SHA256:7D373CCB96D1DBB1856EF31AFA87C2112A0C1795A796AB01CB154700288AFEC5 | |||
| 3704 | Ransomware.7ev3n.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\80237EE4964FC9C409AAF55BF996A292_FB287BEB63DB9E8D59A799779773B97C | der | |
MD5:DF57E40E8F20D3FB38F9EE66C563DBB1 | SHA256:EE4E705944312BFBEDE0056BEA1EA3160BA7B5C0FF353156138327B680CF40D9 | |||
| 3704 | Ransomware.7ev3n.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\receive[1].htm | html | |
MD5:4F8E702CC244EC5D4DE32740C0ECBD97 | SHA256:9E17CB15DD75BBBD5DBB984EDA674863C3B10AB72613CF8A39A00C3E11A8492A | |||
| 3704 | Ransomware.7ev3n.exe | C:\Users\admin\AppData\Local\del.bat | text | |
MD5:5CBDF0B61A5168397A01AB1CFEC738A4 | SHA256:FBD6A50385FAD2B305032CE7A284256A8FD85F89E44B9AB5131E74907D9167DC | |||
| 3704 | Ransomware.7ev3n.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\80237EE4964FC9C409AAF55BF996A292_FB287BEB63DB9E8D59A799779773B97C | binary | |
MD5:AEA7584A40C23C9BC7E28F421A21BE8E | SHA256:7C6527FE45550B0B06DFECCA3C2EAC0D615425D5FC308247C8BB5058F15CF212 | |||
| 5468 | dllhost.exe | C:\Windows\System32\elsext.dll | executable | |
MD5:63378F143DF2BFD0080A02DAF249BF84 | SHA256:13052876487FBEBC38F71FC156B6B6C8A11B6231D6B36AFA6A40E099043D7462 | |||
| 4920 | mmc.exe | C:\Users\admin\AppData\Local\Microsoft\Event Viewer\Settings.Xml | text | |
MD5:884320A9B8F018F309F5A96107133F89 | SHA256:50FD9D76D1C43BB16B166DE02AAF8ADEC09EB5BC4CEFDCA9D1AF2E0F7B1D8F64 | |||
| 4920 | mmc.exe | C:\Users\admin\AppData\Local\Microsoft\Event Viewer\RecentViews | pi2 | |
MD5:785FB8E1B562E2FCC8C0C0C6572EE3D7 | SHA256:5607B57C3C58070F54B8F68FA22808F9AD14C60BBF05F00DA92A162585C3C562 | |||
| 5980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb5980.20210\Ransomware.7ev3n.exe | executable | |
MD5:9F8BC96C96D43ECB69F883388D228754 | SHA256:7D373CCB96D1DBB1856EF31AFA87C2112A0C1795A796AB01CB154700288AFEC5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
25
DNS requests
19
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3704 | Ransomware.7ev3n.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAhflMAthXvozBT%2FU%2B2iPio%3D | unknown | — | — | whitelisted |
6224 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3944 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6224 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4888 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3944 | svchost.exe | 40.126.31.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3944 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
blockchain.info |
| whitelisted |
www.blockchain.com |
| unknown |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
— | — | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
— | — | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
— | — | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
— | — | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
— | — | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
Process | Message |
|---|---|
uac.exe | [UCM] Dll dropped successfully |
mmc.exe | ViewerViewsFolderPath = 'C:\ProgramData\Microsoft\Event Viewer\Views': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerExternalLogsPath = 'C:\ProgramData\Microsoft\Event Viewer\ExternalLogs': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerAdminViewsPath = 'C:\ProgramData\Microsoft\Event Viewer\Views\ApplicationViewsRootNode': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerConfigPath = 'C:\ProgramData\Microsoft\Event Viewer': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | Failed to get ChannelConfigOwningPublisher -122-The data area passed to a system call is too small
|
mmc.exe | Getting next publisher from enum failed-259-No more data is available
|
mmc.exe | Failed to get ChannelConfigOwningPublisher -122-The data area passed to a system call is too small
|
mmc.exe | ExpandNode:After EventsNode:InsertChildren CountOfChildren = 5
|
mmc.exe | PublisherMetadataKeywordName failed for not providing enough memory. Trying with the correct memory -122-The data area passed to a system call is too small
|