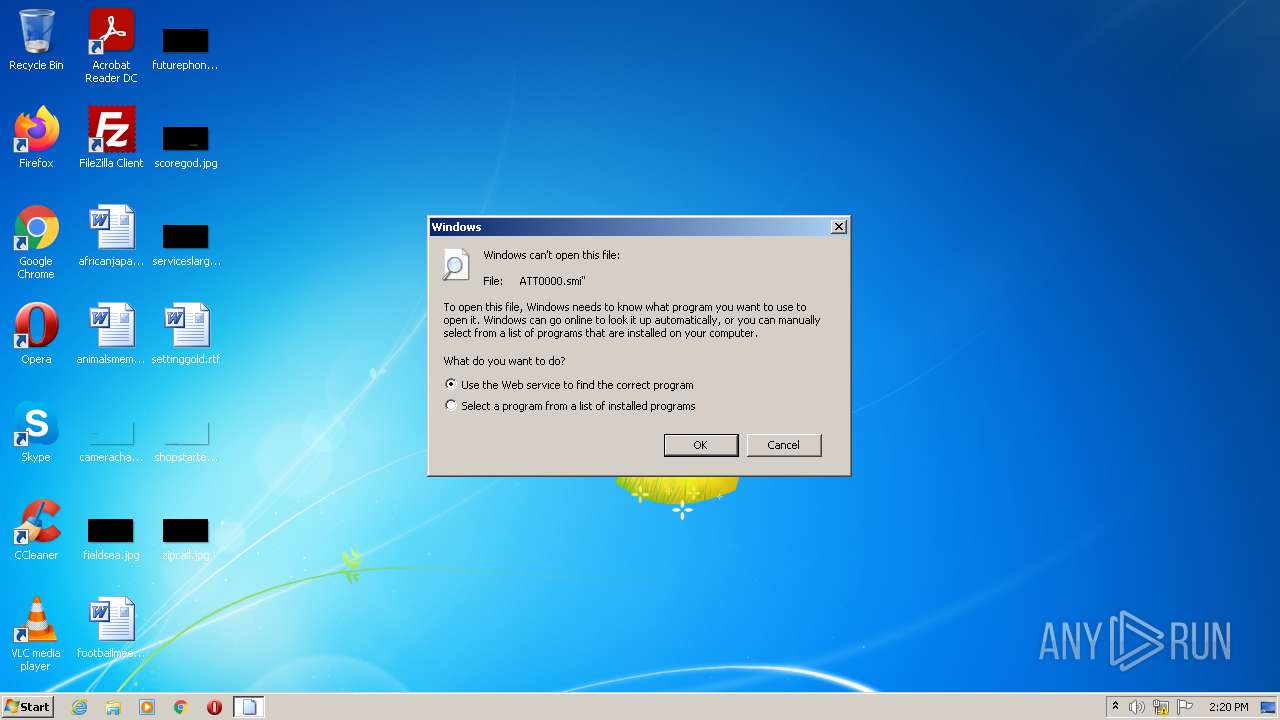
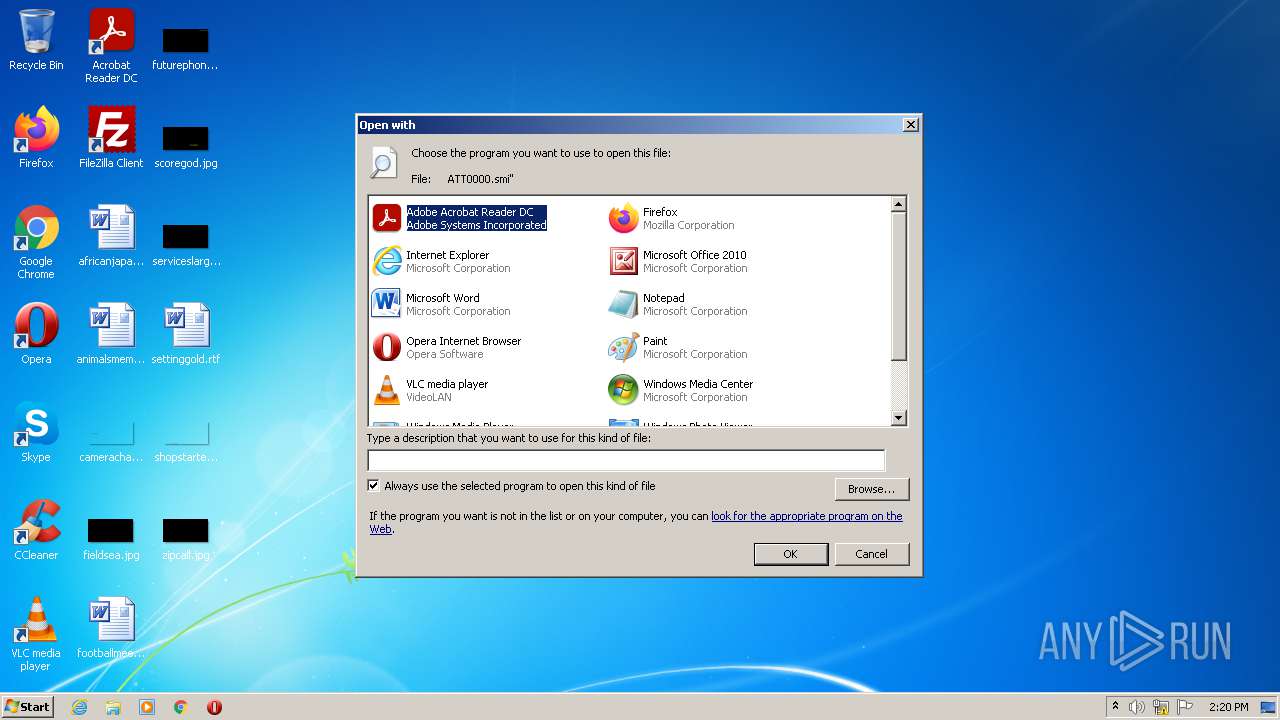
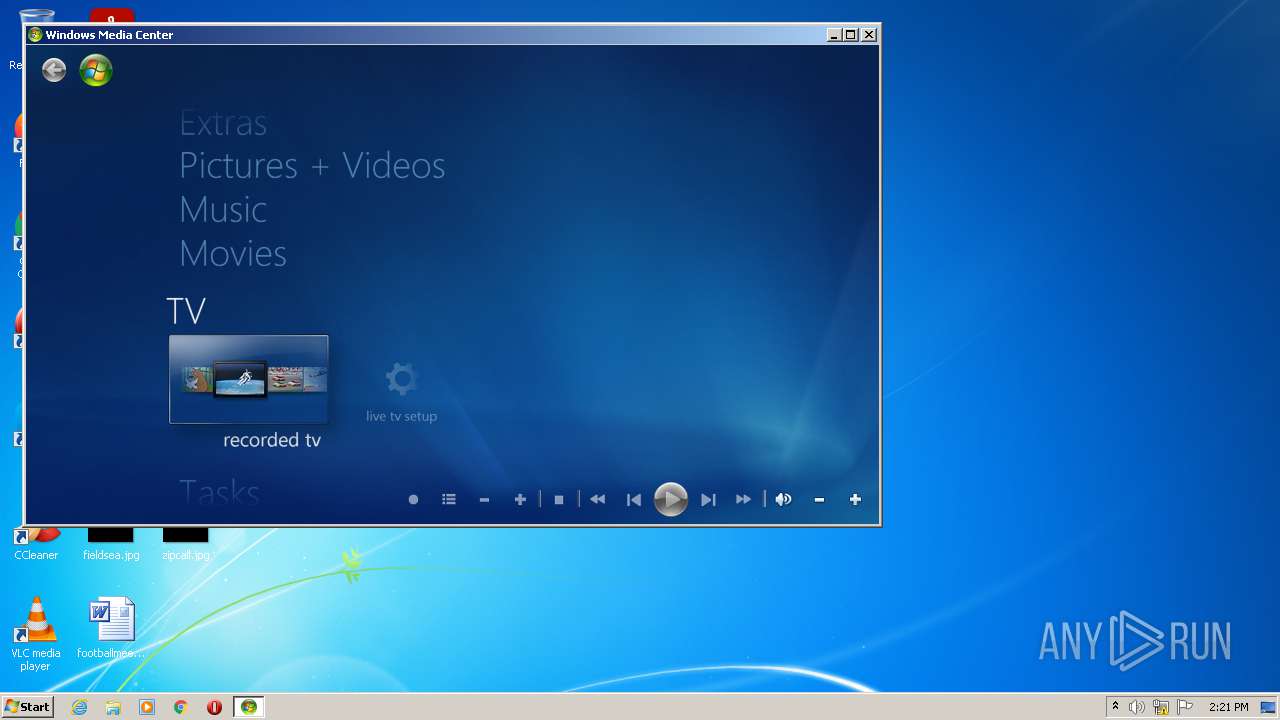
| File name: | ATT0000 |
| Full analysis: | https://app.any.run/tasks/67e88fae-b515-4582-9759-67a846e0e41f |
| Verdict: | Malicious activity |
| Analysis date: | November 26, 2021, 14:20:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, ASCII text |
| MD5: | 6A2D72D8F7F73027218F65BAFA3B63AC |
| SHA1: | 38358D2376654E2FAFB5A37F85E3D19D93E37B8B |
| SHA256: | 72423D57D2E2CE12CAD4565D4DDB9DBE6CC270FC129F1921EE16294641CEFC43 |
| SSDEEP: | 6:6MmboBdh2qT89LO58vCujcz89Xu5iLHK02hdxQsqWqq0RsqRHJuq4WT:MErh2qT89LZjy89jt4xQjC0hJMg |
MALICIOUS
Loads the Task Scheduler COM API
- ehshell.exe (PID: 1068)
- ehRec.exe (PID: 2620)
SUSPICIOUS
Reads the computer name
- ehshell.exe (PID: 1068)
- EhTray.exe (PID: 412)
- wmplayer.exe (PID: 3072)
- ehsched.exe (PID: 4064)
- ehRec.exe (PID: 2620)
Checks supported languages
- ehRec.exe (PID: 2620)
- ehshell.exe (PID: 1068)
- wmplayer.exe (PID: 3072)
- ehsched.exe (PID: 4064)
- EhTray.exe (PID: 412)
Reads CPU info
- ehshell.exe (PID: 1068)
Creates files in the user directory
- ehshell.exe (PID: 1068)
- EhTray.exe (PID: 412)
- wmplayer.exe (PID: 3072)
Creates files in the program directory
- ehshell.exe (PID: 1068)
Creates files in the Windows directory
- ehRec.exe (PID: 2620)
Executed as Windows Service
- ehsched.exe (PID: 4064)
Executed via COM
- ehRec.exe (PID: 2620)
INFO
Checks supported languages
- rundll32.exe (PID: 3696)
Reads the computer name
- rundll32.exe (PID: 3696)
Changes default file association
- rundll32.exe (PID: 3696)
Manual execution by user
- EhTray.exe (PID: 412)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .smi | | | Synchronized Multimedia Integration Language (100) |
|---|
Total processes
40
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 412 | "C:\Windows\eHome\EhTray.exe" /nav:-2 | C:\Windows\eHome\EhTray.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Center Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1068 | "C:\Windows\eHome\ehshell.exe" "C:\Users\admin\AppData\Local\Temp\ATT0000.smi" | C:\Windows\eHome\ehshell.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Center Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2620 | C:\Windows\ehome\ehRec.exe -Embedding | C:\Windows\ehome\ehRec.exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Media Center Host Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3072 | "C:\Program Files\Windows Media Player\wmplayer.exe" /SkipFUE /RemoteOCXLaunch /SuppressDialogs | C:\Program Files\Windows Media Player\wmplayer.exe | ehshell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Exit code: 0 Version: 12.0.7601.23517 (win7sp1_ldr.160812-0732) Modules
| |||||||||||||||
| 3696 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL "C:\Users\admin\AppData\Local\Temp\ATT0000.smi" | C:\Windows\system32\rundll32.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4064 | C:\Windows\ehome\ehsched.exe | C:\Windows\ehome\ehsched.exe | — | services.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Media Center Scheduler Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
7 070
Read events
6 677
Write events
391
Delete events
2
Modification events
| (PID) Process: | (3696) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\eHome\ehshell.exe |
Value: Windows Media Center | |||
| (PID) Process: | (3696) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: Firefox | |||
| (PID) Process: | (3696) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\mspaint.exe |
Value: Paint | |||
| (PID) Process: | (3696) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\NOTEPAD.EXE |
Value: Notepad | |||
| (PID) Process: | (3696) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
| (PID) Process: | (3696) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Opera\Opera.exe |
Value: Opera Internet Browser | |||
| (PID) Process: | (3696) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Windows Photo Viewer\PhotoViewer.dll |
Value: Windows Photo Viewer | |||
| (PID) Process: | (3696) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\VideoLAN\VLC\vlc.exe |
Value: VLC media player | |||
| (PID) Process: | (3696) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE |
Value: Microsoft Word | |||
| (PID) Process: | (3696) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
0
Suspicious files
7
Text files
19
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3072 | wmplayer.exe | C:\Users\Public\Music\Sample Music\AlbumArtSmall.jpg | — | |
MD5:— | SHA256:— | |||
| 3072 | wmplayer.exe | C:\Users\Public\Music\Sample Music\Folder.jpg | — | |
MD5:— | SHA256:— | |||
| 3072 | wmplayer.exe | C:\Users\Public\Music\Sample Music\AlbumArt_{5FA05D35-A682-4AF6-96F7-0773E42D4D16}_Large.jpg | — | |
MD5:— | SHA256:— | |||
| 3072 | wmplayer.exe | C:\Users\Public\Music\Sample Music\AlbumArt_{5FA05D35-A682-4AF6-96F7-0773E42D4D16}_Small.jpg | — | |
MD5:— | SHA256:— | |||
| 1068 | ehshell.exe | C:\ProgramData\Microsoft\eHome\logs\~ehshell.exe.1068.sqm | sqm | |
MD5:— | SHA256:— | |||
| 1068 | ehshell.exe | C:\ProgramData\Microsoft\eHome\Logs\FirstRun.log | xml | |
MD5:— | SHA256:— | |||
| 3072 | wmplayer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\74d7f43c1561fc1e.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2620 | ehRec.exe | C:\programdata\microsoft\ehome\mcepg2-0.db | binary | |
MD5:— | SHA256:— | |||
| 3072 | wmplayer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\4XVLX9WYPRSZEJU34HCN.temp | binary | |
MD5:— | SHA256:— | |||
| 2620 | ehRec.exe | C:\Windows\ServiceProfiles\NetworkService\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-20\8f96978fc46d9f00d8780351026924d7_90059c37-1320-41a4-b58d-2b75a9850d2f | dbf | |
MD5:DB733E033C397FEC5917611957620271 | SHA256:1F3FFADD3B80C7F95BE06E245410768E8302A24E573868DA3C6FD91230025BDC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
8
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3072 | wmplayer.exe | GET | 302 | 2.16.106.49:80 | http://redir.metaservices.microsoft.com/redir/allservices/?sv=5&locale=409&geoid=f4&version=12.0.7601.24499&userlocale=409 | unknown | — | — | whitelisted |
3072 | wmplayer.exe | GET | 200 | 2.21.242.187:80 | http://onlinestores.metaservices.microsoft.com/bing/bing.xml?locale=409&geoid=f4&version=12.0.7601.24499&userlocale=409 | NL | text | 523 b | whitelisted |
3072 | wmplayer.exe | GET | 200 | 2.21.242.213:80 | http://images.windowsmedia.com/svcswitch/mg4_wmp12_30x30_2.png | NL | image | 2.00 Kb | whitelisted |
3072 | wmplayer.exe | GET | 302 | 2.16.106.49:80 | http://redir.metaservices.microsoft.com/redir/getmdrcdbackground/?locale=409&geoid=f4&version=12.0.7601.24499&userlocale=409&wmid=5FA05D35-A682-4AF6-96F7-0773E42D4D16 | unknown | — | — | whitelisted |
3072 | wmplayer.exe | GET | 200 | 2.21.242.187:80 | http://onlinestores.metaservices.microsoft.com/serviceswitching/AllServices.aspx?sv=5&locale=409&geoid=f4&version=12.0.7601.24499&userlocale=409 | NL | xml | 546 b | whitelisted |
3072 | wmplayer.exe | GET | 200 | 2.21.242.213:80 | http://images.windowsmedia.com/svcswitch/media_guide_16x16.png | NL | image | 897 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3072 | wmplayer.exe | 2.16.106.49:80 | redir.metaservices.microsoft.com | Akamai International B.V. | — | whitelisted |
3072 | wmplayer.exe | 2.21.242.187:80 | onlinestores.metaservices.microsoft.com | Akamai International B.V. | NL | whitelisted |
3072 | wmplayer.exe | 2.21.242.213:80 | images.windowsmedia.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
redir.metaservices.microsoft.com |
| whitelisted |
onlinestores.metaservices.microsoft.com |
| whitelisted |
images.windowsmedia.com |
| whitelisted |
toc.music.metaservices.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
ehshell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ehshell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ehshell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ehshell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ehshell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|