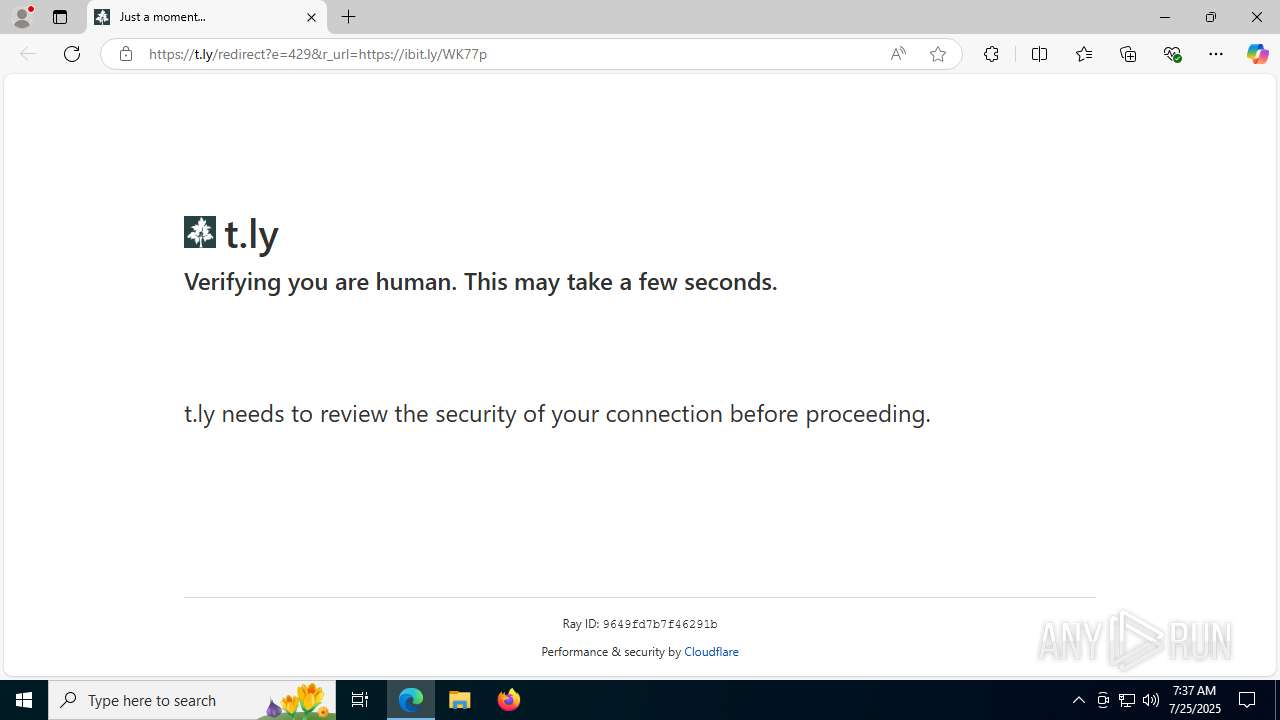
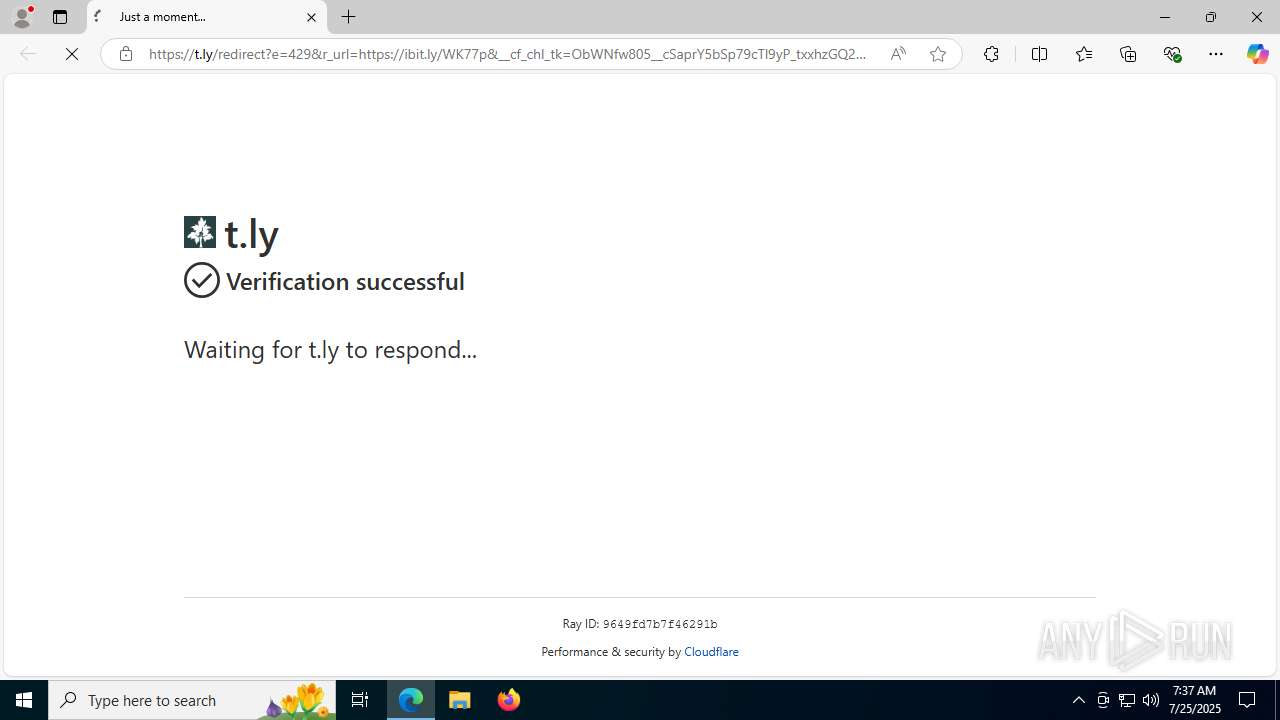
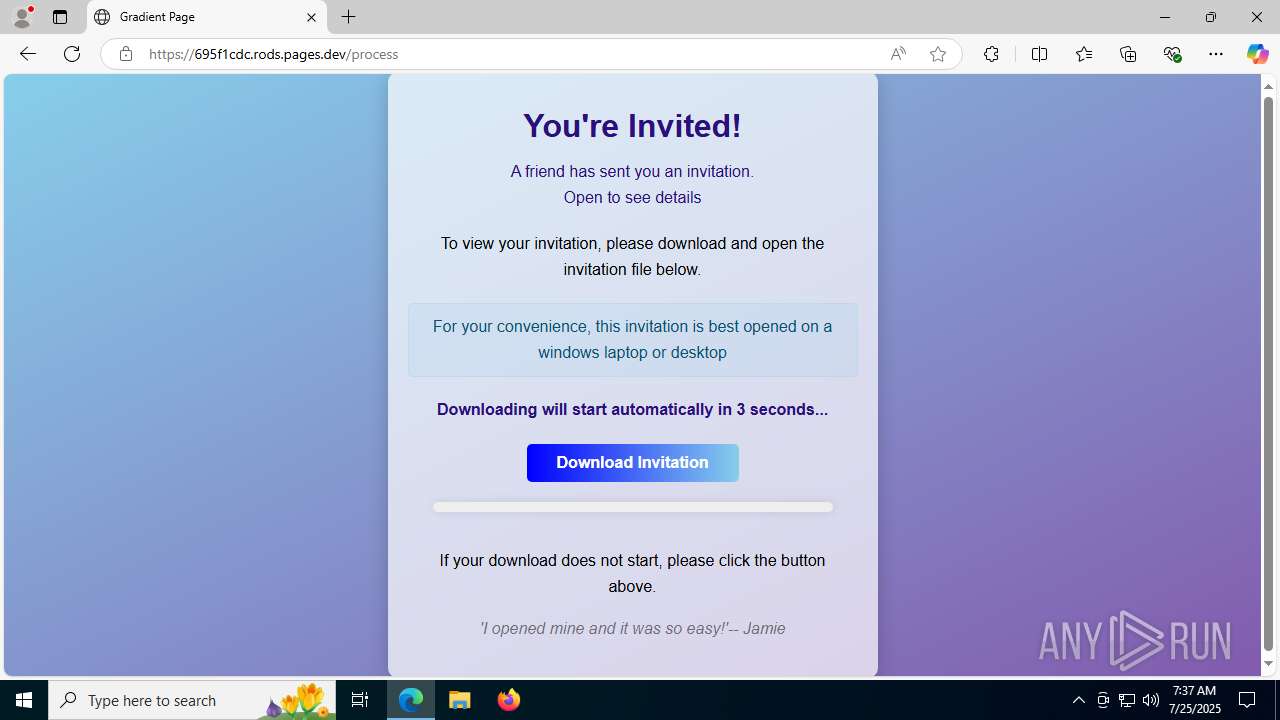
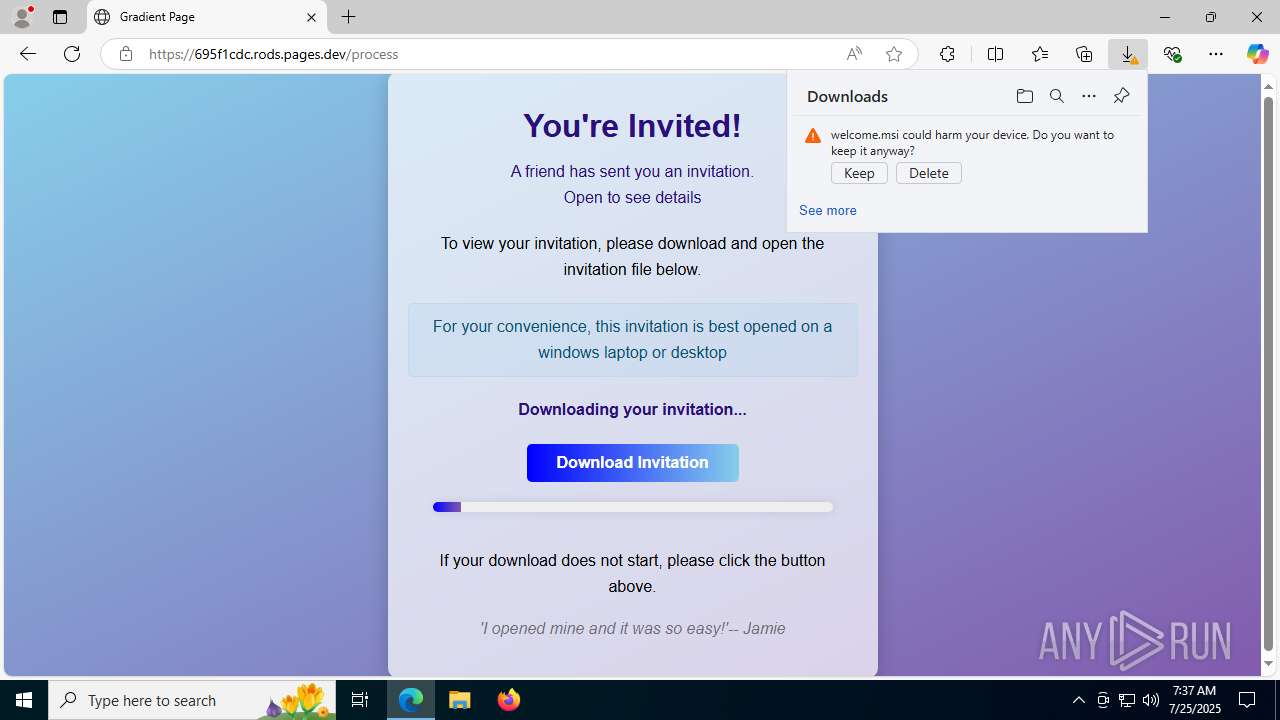
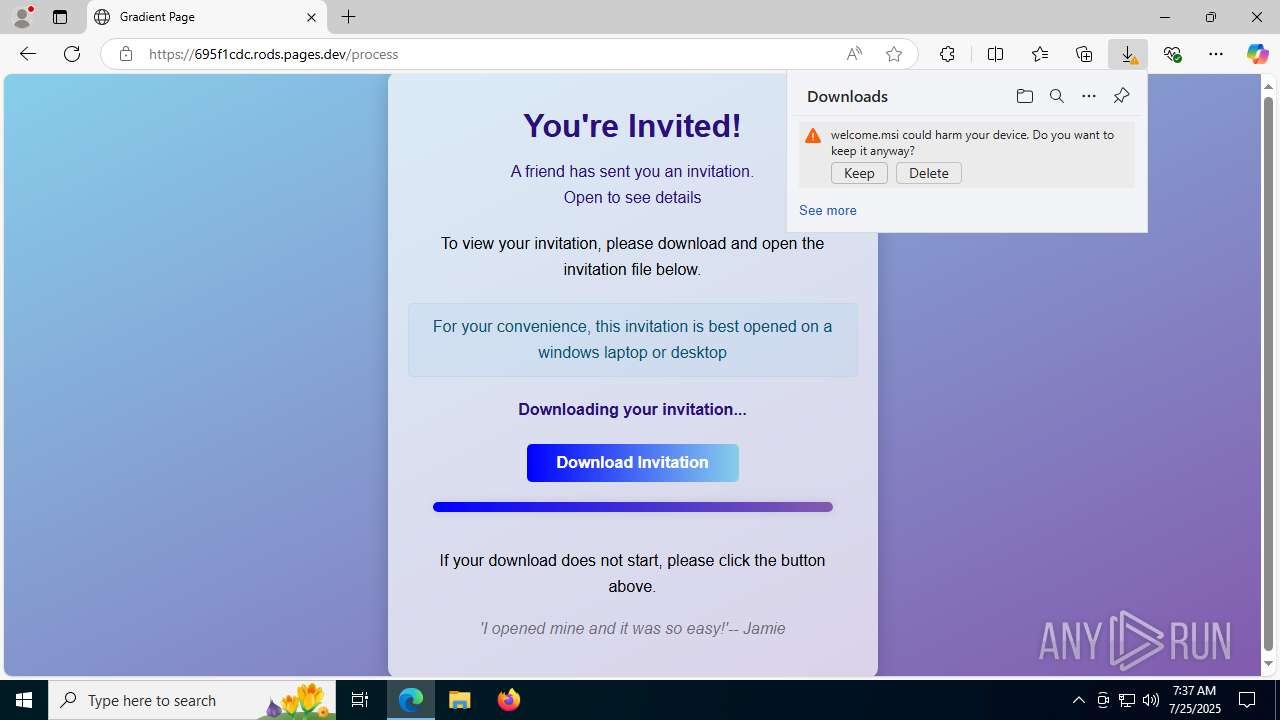
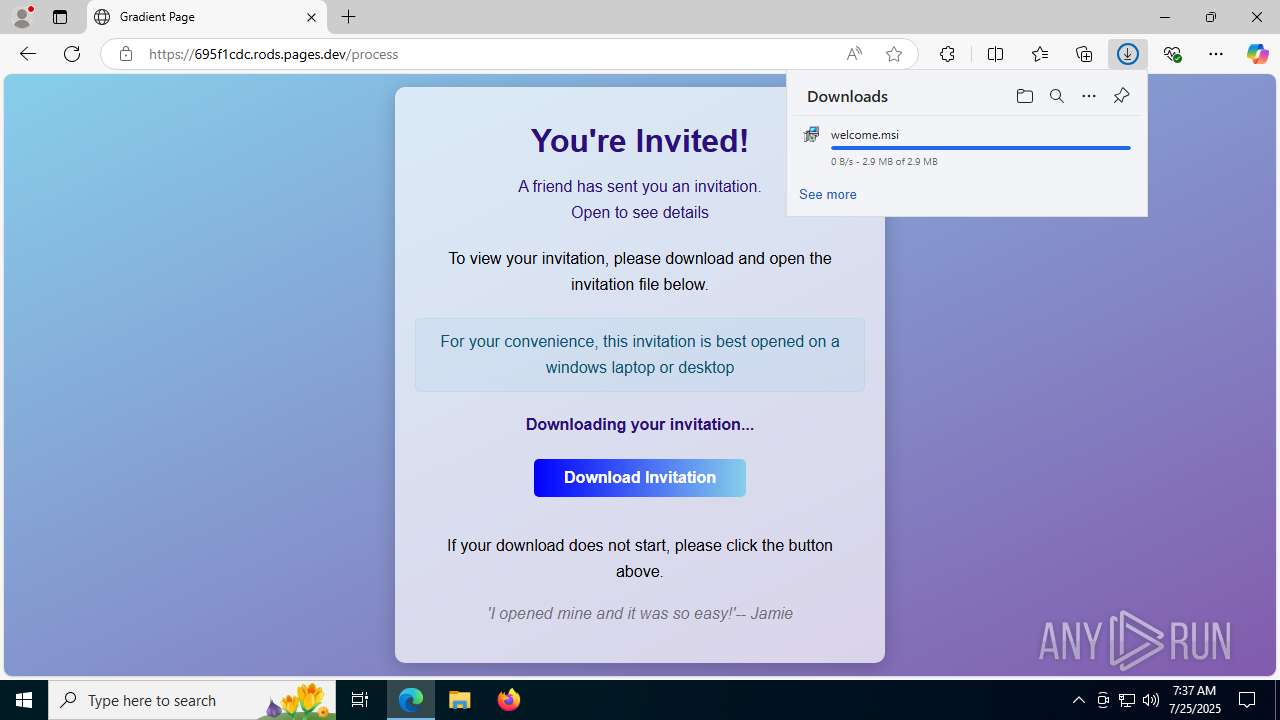
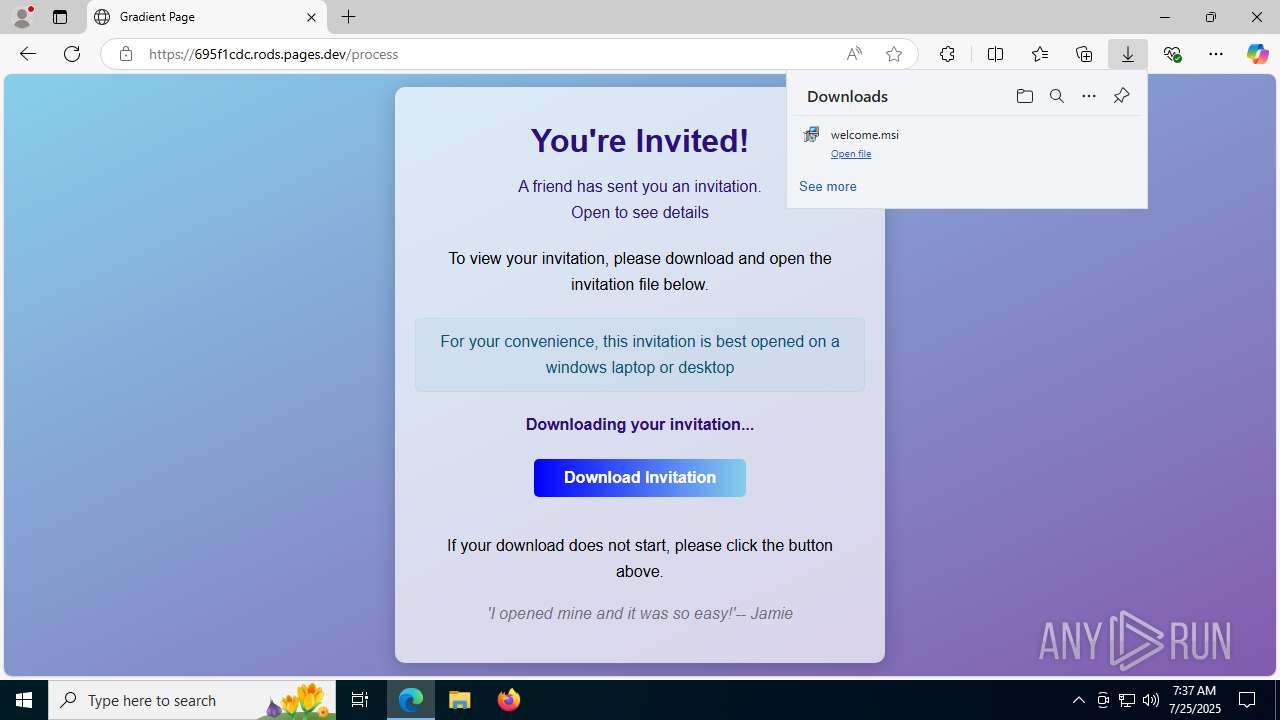
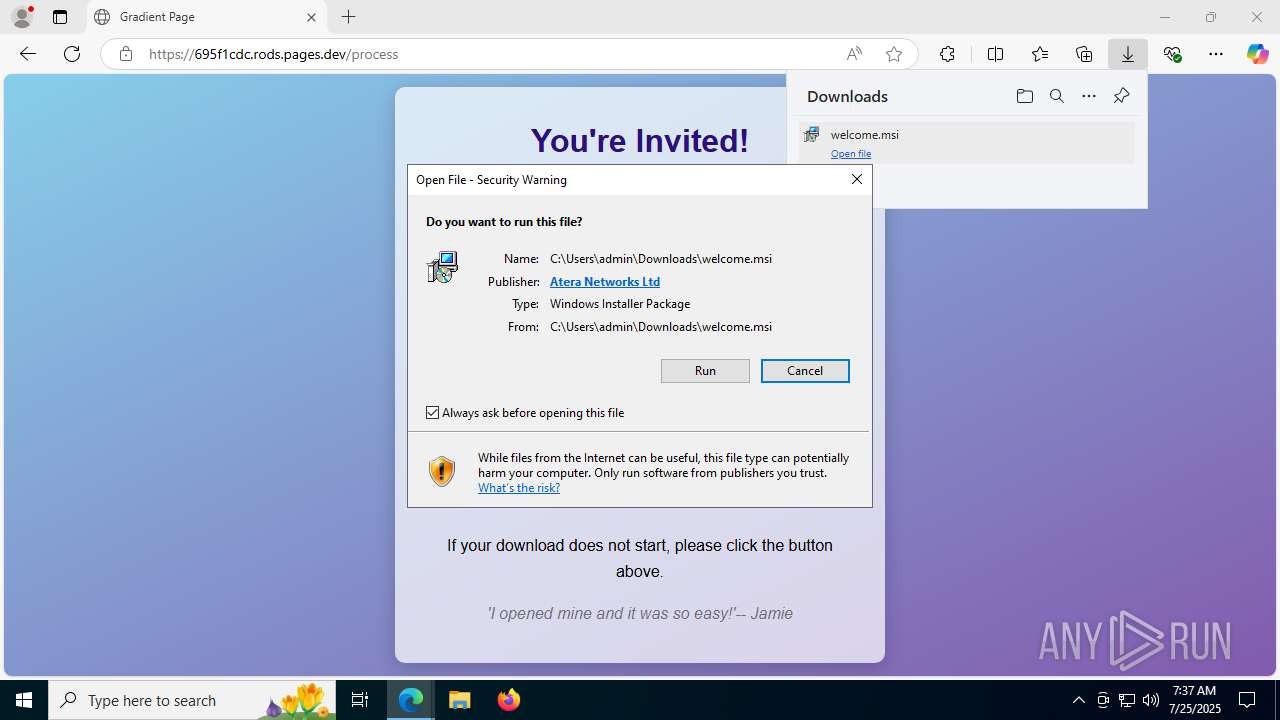
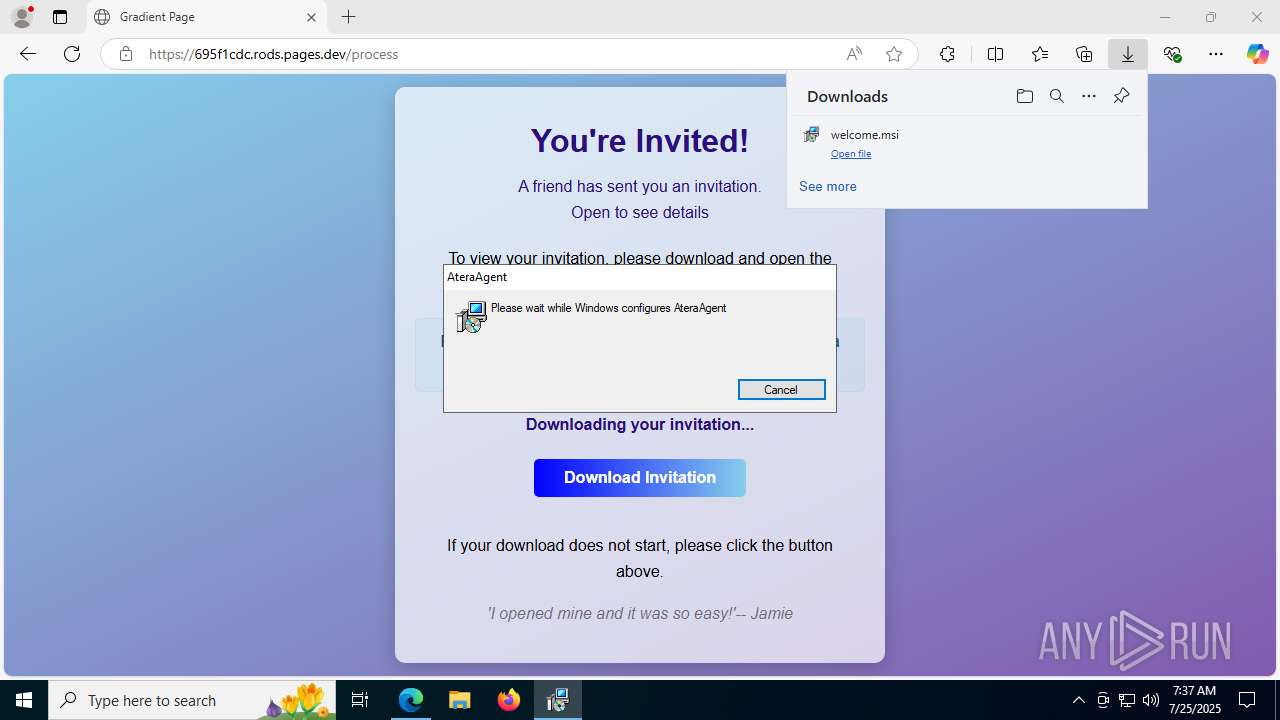
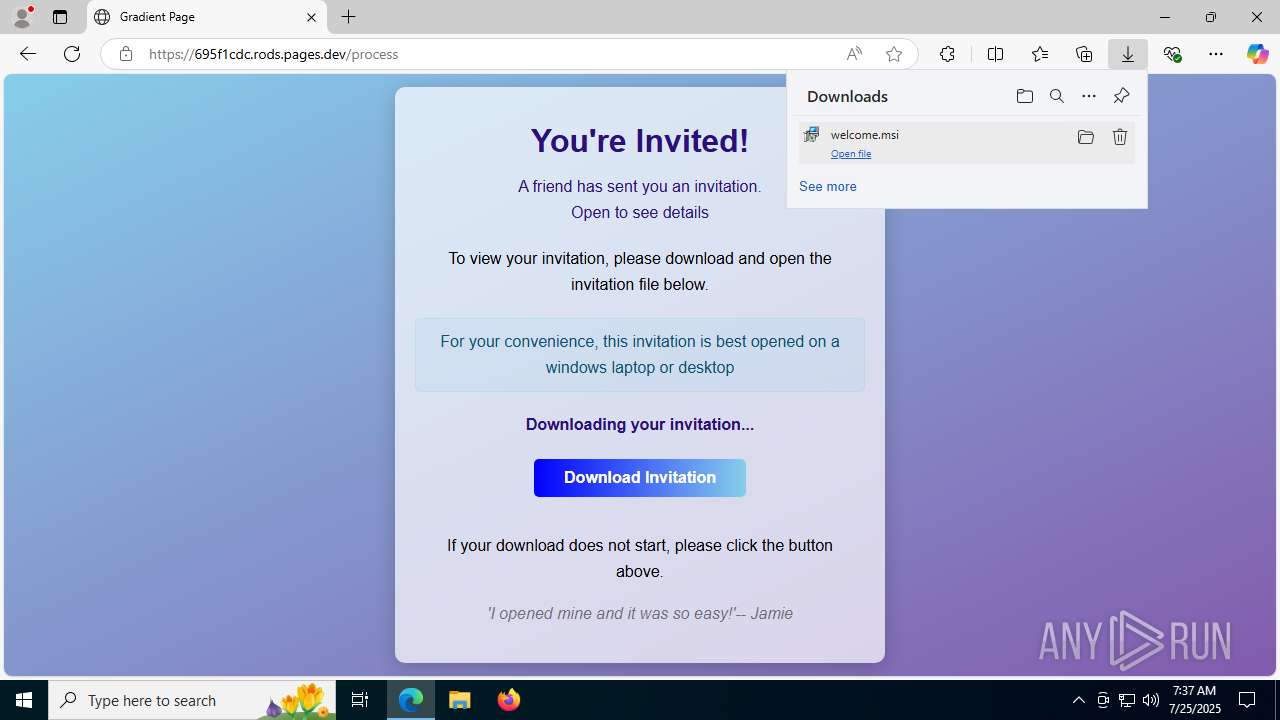
| URL: | https://ibit.ly/WK77p |
| Full analysis: | https://app.any.run/tasks/e67bd21f-8286-46eb-9161-dda030be1462 |
| Verdict: | Malicious activity |
| Analysis date: | July 25, 2025, 07:36:58 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | C5683E0E3C2CDCEEB047EDFF7C22D4D3 |
| SHA1: | 362D94768B07F111D4564B918B169640FB0F12AB |
| SHA256: | 723858B5E66538A2AB226C3FC99BC98FDFF745037E9A14000B740DA9207405D8 |
| SSDEEP: | 3:N8FtJjV:2f7 |
MALICIOUS
Starts NET.EXE for service management
- msiexec.exe (PID: 7192)
- net.exe (PID: 8004)
- msiexec.exe (PID: 8780)
- net.exe (PID: 2696)
- net.exe (PID: 7572)
Bypass execution policy to execute commands
- powershell.exe (PID: 7184)
- powershell.exe (PID: 7156)
Changes powershell execution policy (Bypass)
- AgentPackageAgentInformation.exe (PID: 7056)
- AgentPackageAgentInformation.exe (PID: 7872)
ATERA mutex has been found
- AgentPackageInternalPoller.exe (PID: 4188)
- AgentPackageMonitoring.exe (PID: 6232)
Changes the autorun value in the registry
- dotnet-runtime-8.0.11-win-x64.exe (PID: 1028)
SUSPICIOUS
Process drops legitimate windows executable
- msedge.exe (PID: 5528)
- msiexec.exe (PID: 7928)
- msedge.exe (PID: 1356)
- AteraAgent.exe (PID: 1948)
- AteraAgent.exe (PID: 7276)
- AgentPackageUpgradeAgent.exe (PID: 7748)
- 8-0-11.exe (PID: 9056)
- 8-0-11.exe (PID: 9132)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 1028)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7928)
Executes as Windows Service
- VSSVC.exe (PID: 8048)
- AteraAgent.exe (PID: 1948)
- AteraAgent.exe (PID: 7276)
- AteraAgent.exe (PID: 5900)
Executable content was dropped or overwritten
- rundll32.exe (PID: 1232)
- rundll32.exe (PID: 7584)
- rundll32.exe (PID: 4156)
- rundll32.exe (PID: 7868)
- csc.exe (PID: 7268)
- AteraAgent.exe (PID: 1948)
- AteraAgent.exe (PID: 7276)
- AgentPackageUpgradeAgent.exe (PID: 7748)
- AgentPackageTicketing.exe (PID: 7788)
- rundll32.exe (PID: 8868)
- rundll32.exe (PID: 8820)
- AgentPackageRuntimeInstaller.exe (PID: 3400)
- rundll32.exe (PID: 8952)
- csc.exe (PID: 9064)
- 8-0-11.exe (PID: 9056)
- 8-0-11.exe (PID: 9132)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 1028)
- rundll32.exe (PID: 5652)
Uses TASKKILL.EXE to kill process
- msiexec.exe (PID: 7192)
- msiexec.exe (PID: 8780)
ATERAAGENT has been detected
- AteraAgent.exe (PID: 4308)
- AteraAgent.exe (PID: 1948)
- AteraAgent.exe (PID: 7276)
- AteraAgent.exe (PID: 7312)
- AteraAgent.exe (PID: 5900)
- AteraAgent.exe (PID: 8940)
Reads security settings of Internet Explorer
- AteraAgent.exe (PID: 4308)
- AteraAgent.exe (PID: 1948)
- AteraAgent.exe (PID: 7276)
- AgentPackageAgentInformation.exe (PID: 7056)
- AgentPackageAgentInformation.exe (PID: 7872)
- 8-0-11.exe (PID: 9132)
- AteraAgent.exe (PID: 8940)
- AteraAgent.exe (PID: 5900)
Potential Corporate Privacy Violation
- rundll32.exe (PID: 7584)
- AteraAgent.exe (PID: 1948)
- AgentPackageAgentInformation.exe (PID: 2380)
- rundll32.exe (PID: 7868)
- AteraAgent.exe (PID: 7276)
- AgentPackageMonitoring.exe (PID: 7356)
- AgentPackageSTRemote.exe (PID: 6264)
- AgentPackageAgentInformation.exe (PID: 7056)
- AgentPackageInternalPoller.exe (PID: 4188)
- rundll32.exe (PID: 8868)
- AgentPackageTicketing.exe (PID: 7788)
- AgentPackageAgentInformation.exe (PID: 7872)
- AgentPackageMonitoring.exe (PID: 6232)
- rundll32.exe (PID: 5652)
- AteraAgent.exe (PID: 5900)
Starts SC.EXE for service management
- AteraAgent.exe (PID: 1948)
- AteraAgent.exe (PID: 7276)
- AteraAgent.exe (PID: 5900)
Restarts service on failure
- sc.exe (PID: 7812)
- sc.exe (PID: 4916)
- sc.exe (PID: 8244)
Reads the date of Windows installation
- AteraAgent.exe (PID: 1948)
- AteraAgent.exe (PID: 7276)
- AteraAgent.exe (PID: 5900)
Starts POWERSHELL.EXE for commands execution
- AgentPackageAgentInformation.exe (PID: 7056)
- AgentPackageAgentInformation.exe (PID: 7872)
The process executes Powershell scripts
- AgentPackageAgentInformation.exe (PID: 7056)
- AgentPackageAgentInformation.exe (PID: 7872)
The process hides Powershell's copyright startup banner
- AgentPackageAgentInformation.exe (PID: 7056)
- AgentPackageAgentInformation.exe (PID: 7872)
The process bypasses the loading of PowerShell profile settings
- AgentPackageAgentInformation.exe (PID: 7056)
- AgentPackageAgentInformation.exe (PID: 7872)
CSC.EXE is used to compile C# code
- csc.exe (PID: 7268)
- csc.exe (PID: 9064)
Starts CMD.EXE for commands execution
- AgentPackageAgentInformation.exe (PID: 7056)
- AgentPackageRuntimeInstaller.exe (PID: 3400)
- AgentPackageAgentInformation.exe (PID: 7872)
Gets a collection of all available drive names (SCRIPT)
- cscript.exe (PID: 2064)
- cscript.exe (PID: 700)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 2064)
- cscript.exe (PID: 700)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 2064)
- cscript.exe (PID: 700)
Accesses OperatingSystem(Win32_OperatingSystem) via WMI (SCRIPT)
- cscript.exe (PID: 2064)
- cscript.exe (PID: 700)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- cscript.exe (PID: 2064)
- cscript.exe (PID: 700)
The process executes VB scripts
- cmd.exe (PID: 7716)
- cmd.exe (PID: 9204)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 2064)
- cscript.exe (PID: 700)
Checks whether a specific file exists (SCRIPT)
- cscript.exe (PID: 2064)
- cscript.exe (PID: 700)
Accesses computer name via WMI (SCRIPT)
- cscript.exe (PID: 2064)
- cscript.exe (PID: 700)
Searches for installed software
- AgentPackageAgentInformation.exe (PID: 7056)
- 8-0-11.exe (PID: 9132)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 1028)
- AgentPackageAgentInformation.exe (PID: 7872)
The process creates files with name similar to system file names
- AteraAgent.exe (PID: 7276)
- msiexec.exe (PID: 7928)
Gets the drive type (SCRIPT)
- cscript.exe (PID: 2064)
- cscript.exe (PID: 700)
Starts itself from another location
- 8-0-11.exe (PID: 9132)
Starts a Microsoft application from unusual location
- dotnet-runtime-8.0.11-win-x64.exe (PID: 1028)
- 8-0-11.exe (PID: 9132)
Creates a software uninstall entry
- dotnet-runtime-8.0.11-win-x64.exe (PID: 1028)
INFO
Application launched itself
- msedge.exe (PID: 1356)
Reads the computer name
- identity_helper.exe (PID: 7884)
- msiexec.exe (PID: 7928)
- msiexec.exe (PID: 2064)
- msiexec.exe (PID: 7192)
- AteraAgent.exe (PID: 4308)
- AteraAgent.exe (PID: 1948)
- AgentPackageAgentInformation.exe (PID: 2380)
- AgentPackageAgentInformation.exe (PID: 7764)
- AgentPackageAgentInformation.exe (PID: 7056)
- AgentPackageAgentInformation.exe (PID: 6664)
- AteraAgent.exe (PID: 7276)
- AgentPackageMonitoring.exe (PID: 7356)
- AgentPackageAgentInformation.exe (PID: 7872)
- AgentPackageHeartbeat.exe (PID: 2588)
- AgentPackageSTRemote.exe (PID: 6264)
- AgentPackageInternalPoller.exe (PID: 4188)
- AgentPackageMonitoring.exe (PID: 6232)
- AgentPackageSystemTools.exe (PID: 7248)
- AgentPackageADRemote.exe (PID: 7296)
- AgentPackageUpgradeAgent.exe (PID: 7748)
- AgentPackageRuntimeInstaller.exe (PID: 3400)
- AgentPackageMarketplace.exe (PID: 7448)
- AgentPackageTicketing.exe (PID: 7788)
- Agent.Package.Software.exe (PID: 8336)
- AgentPackageOsUpdates.exe (PID: 8460)
- Agent.Package.Availability.exe (PID: 8136)
- Agent.Package.Watchdog.exe (PID: 8328)
- msiexec.exe (PID: 8780)
- 8-0-11.exe (PID: 9056)
- 8-0-11.exe (PID: 9132)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 1028)
- AteraAgent.exe (PID: 7312)
- AteraAgent.exe (PID: 8940)
- AteraAgent.exe (PID: 5900)
- msiexec.exe (PID: 8172)
- msiexec.exe (PID: 4312)
- msiexec.exe (PID: 7740)
Reads Environment values
- identity_helper.exe (PID: 7884)
- AteraAgent.exe (PID: 4308)
- AteraAgent.exe (PID: 1948)
- AgentPackageAgentInformation.exe (PID: 7764)
- AgentPackageAgentInformation.exe (PID: 2380)
- AgentPackageAgentInformation.exe (PID: 7056)
- AgentPackageAgentInformation.exe (PID: 6664)
- AteraAgent.exe (PID: 7276)
- AgentPackageMonitoring.exe (PID: 7356)
- AgentPackageAgentInformation.exe (PID: 7872)
- AgentPackageSTRemote.exe (PID: 6264)
- AgentPackageHeartbeat.exe (PID: 2588)
- AgentPackageMonitoring.exe (PID: 6232)
- AgentPackageInternalPoller.exe (PID: 4188)
- AgentPackageUpgradeAgent.exe (PID: 7748)
- AgentPackageADRemote.exe (PID: 7296)
- AgentPackageSystemTools.exe (PID: 7248)
- AgentPackageMarketplace.exe (PID: 7448)
- AgentPackageRuntimeInstaller.exe (PID: 3400)
- AgentPackageTicketing.exe (PID: 7788)
- AgentPackageOsUpdates.exe (PID: 8460)
- AteraAgent.exe (PID: 7312)
- AteraAgent.exe (PID: 8940)
- AteraAgent.exe (PID: 5900)
Executable content was dropped or overwritten
- msedge.exe (PID: 5528)
- msedge.exe (PID: 1356)
- msiexec.exe (PID: 7928)
Reads Microsoft Office registry keys
- msedge.exe (PID: 1356)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 7172)
Checks supported languages
- msiexec.exe (PID: 7928)
- msiexec.exe (PID: 2064)
- msiexec.exe (PID: 7192)
- AteraAgent.exe (PID: 4308)
- AteraAgent.exe (PID: 1948)
- identity_helper.exe (PID: 7884)
- AgentPackageAgentInformation.exe (PID: 2380)
- AgentPackageAgentInformation.exe (PID: 7764)
- AgentPackageAgentInformation.exe (PID: 7056)
- AgentPackageAgentInformation.exe (PID: 6664)
- AteraAgent.exe (PID: 7276)
- AgentPackageMonitoring.exe (PID: 7356)
- csc.exe (PID: 7268)
- cvtres.exe (PID: 1588)
- AgentPackageAgentInformation.exe (PID: 7872)
- AgentPackageHeartbeat.exe (PID: 2588)
- AgentPackageSTRemote.exe (PID: 6264)
- AgentPackageInternalPoller.exe (PID: 4188)
- AgentPackageMonitoring.exe (PID: 6232)
- AgentPackageADRemote.exe (PID: 7296)
- AgentPackageMarketplace.exe (PID: 7448)
- AgentPackageRuntimeInstaller.exe (PID: 3400)
- AgentPackageUpgradeAgent.exe (PID: 7748)
- AgentPackageSystemTools.exe (PID: 7248)
- Agent.Package.Availability.exe (PID: 8136)
- Agent.Package.Software.exe (PID: 8336)
- AgentPackageTicketing.exe (PID: 7788)
- Agent.Package.Watchdog.exe (PID: 8328)
- AgentPackageOsUpdates.exe (PID: 8460)
- msiexec.exe (PID: 8780)
- csc.exe (PID: 9064)
- 8-0-11.exe (PID: 9056)
- cvtres.exe (PID: 9084)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 1028)
- 8-0-11.exe (PID: 9132)
- AteraAgent.exe (PID: 7312)
- AteraAgent.exe (PID: 5900)
- AteraAgent.exe (PID: 8940)
- msiexec.exe (PID: 8172)
- msiexec.exe (PID: 4312)
- dotnet.exe (PID: 8396)
- dotnet.exe (PID: 7156)
- msiexec.exe (PID: 7740)
Manages system restore points
- SrTasks.exe (PID: 6176)
Reads the software policy settings
- msiexec.exe (PID: 7928)
- rundll32.exe (PID: 7584)
- AteraAgent.exe (PID: 4308)
- rundll32.exe (PID: 7868)
- AteraAgent.exe (PID: 1948)
- AgentPackageAgentInformation.exe (PID: 2380)
- AgentPackageAgentInformation.exe (PID: 7764)
- msiexec.exe (PID: 7172)
- AteraAgent.exe (PID: 7276)
- AgentPackageMonitoring.exe (PID: 7356)
- cscript.exe (PID: 2064)
- AgentPackageAgentInformation.exe (PID: 7056)
- AgentPackageHeartbeat.exe (PID: 2588)
- AgentPackageSTRemote.exe (PID: 6264)
- AgentPackageInternalPoller.exe (PID: 4188)
- AgentPackageMarketplace.exe (PID: 7448)
- AgentPackageADRemote.exe (PID: 7296)
- AgentPackageUpgradeAgent.exe (PID: 7748)
- AgentPackageRuntimeInstaller.exe (PID: 3400)
- AgentPackageTicketing.exe (PID: 7788)
- rundll32.exe (PID: 8868)
- cscript.exe (PID: 700)
- AgentPackageAgentInformation.exe (PID: 7872)
- AteraAgent.exe (PID: 8940)
- AgentPackageMonitoring.exe (PID: 6232)
- rundll32.exe (PID: 5652)
- AteraAgent.exe (PID: 5900)
- slui.exe (PID: 7728)
Reads the machine GUID from the registry
- msiexec.exe (PID: 7928)
- AteraAgent.exe (PID: 4308)
- AteraAgent.exe (PID: 1948)
- AgentPackageAgentInformation.exe (PID: 2380)
- AgentPackageAgentInformation.exe (PID: 7764)
- AgentPackageAgentInformation.exe (PID: 7056)
- AgentPackageAgentInformation.exe (PID: 6664)
- AgentPackageMonitoring.exe (PID: 7356)
- AteraAgent.exe (PID: 7276)
- csc.exe (PID: 7268)
- AgentPackageHeartbeat.exe (PID: 2588)
- AgentPackageSTRemote.exe (PID: 6264)
- AgentPackageAgentInformation.exe (PID: 7872)
- AgentPackageMonitoring.exe (PID: 6232)
- AgentPackageInternalPoller.exe (PID: 4188)
- AgentPackageUpgradeAgent.exe (PID: 7748)
- AgentPackageSystemTools.exe (PID: 7248)
- AgentPackageRuntimeInstaller.exe (PID: 3400)
- AgentPackageADRemote.exe (PID: 7296)
- AgentPackageMarketplace.exe (PID: 7448)
- AgentPackageTicketing.exe (PID: 7788)
- AgentPackageOsUpdates.exe (PID: 8460)
- csc.exe (PID: 9064)
- AteraAgent.exe (PID: 7312)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 1028)
- AteraAgent.exe (PID: 8940)
- AteraAgent.exe (PID: 5900)
The sample compiled with english language support
- rundll32.exe (PID: 1232)
- rundll32.exe (PID: 7584)
- rundll32.exe (PID: 4156)
- rundll32.exe (PID: 7868)
- AteraAgent.exe (PID: 1948)
- AteraAgent.exe (PID: 7276)
- rundll32.exe (PID: 8868)
- rundll32.exe (PID: 8952)
- rundll32.exe (PID: 8820)
- 8-0-11.exe (PID: 9056)
- 8-0-11.exe (PID: 9132)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 1028)
- rundll32.exe (PID: 5652)
- msiexec.exe (PID: 7928)
Create files in a temporary directory
- rundll32.exe (PID: 7584)
- rundll32.exe (PID: 4156)
- rundll32.exe (PID: 7868)
- rundll32.exe (PID: 1232)
Disables trace logs
- rundll32.exe (PID: 7584)
- AteraAgent.exe (PID: 1948)
- rundll32.exe (PID: 7868)
- AgentPackageAgentInformation.exe (PID: 2380)
- AgentPackageAgentInformation.exe (PID: 7764)
- AgentPackageMonitoring.exe (PID: 7356)
- AteraAgent.exe (PID: 7276)
- AgentPackageAgentInformation.exe (PID: 7056)
- AgentPackageSTRemote.exe (PID: 6264)
- AgentPackageInternalPoller.exe (PID: 4188)
- AgentPackageHeartbeat.exe (PID: 2588)
- AgentPackageADRemote.exe (PID: 7296)
- AgentPackageMarketplace.exe (PID: 7448)
- AgentPackageUpgradeAgent.exe (PID: 7748)
- AgentPackageRuntimeInstaller.exe (PID: 3400)
- rundll32.exe (PID: 8868)
- AgentPackageTicketing.exe (PID: 7788)
- AgentPackageAgentInformation.exe (PID: 7872)
- AgentPackageMonitoring.exe (PID: 6232)
- rundll32.exe (PID: 5652)
- AteraAgent.exe (PID: 5900)
Checks proxy server information
- rundll32.exe (PID: 7584)
- rundll32.exe (PID: 7868)
- slui.exe (PID: 7728)
Creates files in the program directory
- AteraAgent.exe (PID: 4308)
- AgentPackageMonitoring.exe (PID: 7356)
- AteraAgent.exe (PID: 1948)
- AgentPackageAgentInformation.exe (PID: 7056)
- AteraAgent.exe (PID: 7276)
- AgentPackageInternalPoller.exe (PID: 4188)
- AgentPackageSystemTools.exe (PID: 7248)
- AgentPackageRuntimeInstaller.exe (PID: 3400)
- AgentPackageUpgradeAgent.exe (PID: 7748)
- AgentPackageMonitoring.exe (PID: 6232)
- AgentPackageTicketing.exe (PID: 7788)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 1028)
- AteraAgent.exe (PID: 8940)
Creates a software uninstall entry
- msiexec.exe (PID: 7928)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7184)
- powershell.exe (PID: 7156)
Launching a file from a Registry key
- dotnet-runtime-8.0.11-win-x64.exe (PID: 1028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
290
Monitored processes
147
Malicious processes
16
Suspicious processes
10
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 700 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=17 --always-read-main-dll --field-trial-handle=5064,i,3618120825830951626,12152057578156483294,262144 --variations-seed-version --mojo-platform-channel-handle=6660 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 700 | cscript "C:\Program Files\Microsoft Office\Office16\ospp.vbs" /dstatus | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1028 | "C:\WINDOWS\Temp\{267D19C1-01F2-4FEB-8D95-380AB73ABCBB}\.be\dotnet-runtime-8.0.11-win-x64.exe" -q -burn.elevated BurnPipe.{EDC4FAB2-E9A3-4D77-A221-198A09221E37} {5D415D13-9318-41CA-B00A-9D4EFF381402} 9132 | C:\Windows\Temp\{267D19C1-01F2-4FEB-8D95-380AB73ABCBB}\.be\dotnet-runtime-8.0.11-win-x64.exe | 8-0-11.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft .NET Runtime - 8.0.11 (x64) Exit code: 0 Version: 8.0.11.34217 Modules
| |||||||||||||||
| 1068 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1232 | rundll32.exe "C:\WINDOWS\Installer\MSI7620.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1668734 2 AlphaControlAgentInstallation!AlphaControlAgentInstallation.CustomActions.GenerateAgentId | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1356 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" "https://ibit.ly/WK77p" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1580 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1588 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\WINDOWS\TEMP\RESB973.tmp" "c:\Windows\Temp\w4t3tsur\CSC7AB16655AF1142B2BF7FAD9860879F9B.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 1948 | "C:\Program Files (x86)\ATERA Networks\AteraAgent\AteraAgent.exe" | C:\Program Files (x86)\ATERA Networks\AteraAgent\AteraAgent.exe | services.exe | ||||||||||||
User: SYSTEM Company: ATERA Networks Ltd. Integrity Level: SYSTEM Description: AteraAgent Exit code: 0 Version: 1.8.7.2 Modules
| |||||||||||||||
| 2028 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=1488,i,3618120825830951626,12152057578156483294,262144 --variations-seed-version --mojo-platform-channel-handle=7464 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
85 677
Read events
84 201
Write events
1 282
Delete events
194
Modification events
| (PID) Process: | (1356) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1356) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1356) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1356) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (1356) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: E82CC64A52992F00 | |||
| (PID) Process: | (1356) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459394 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {1F1B4D8D-44AE-4B4D-8B5D-B51085BF90E4} | |||
| (PID) Process: | (1356) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459394 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {74B226CE-29FB-421E-B01A-95ED62CA4550} | |||
| (PID) Process: | (1356) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459394 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {05286333-6212-4841-BE0D-A7605B00E1F1} | |||
| (PID) Process: | (1356) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459394 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {E1C8B7E3-C920-4B62-B576-1D5491E00A46} | |||
| (PID) Process: | (1356) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: E54AF24A52992F00 | |||
Executable files
694
Suspicious files
331
Text files
173
Unknown types
84
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1356 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF18d5ba.TMP | — | |
MD5:— | SHA256:— | |||
| 1356 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1356 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF18d5c9.TMP | — | |
MD5:— | SHA256:— | |||
| 1356 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1356 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF18d5e9.TMP | — | |
MD5:— | SHA256:— | |||
| 1356 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1356 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF18d5e9.TMP | — | |
MD5:— | SHA256:— | |||
| 1356 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF18d5f8.TMP | — | |
MD5:— | SHA256:— | |||
| 1356 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1356 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
128
DNS requests
96
Threats
67
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5708 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4308 | AteraAgent.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
4308 | AteraAgent.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
2064 | cscript.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
4216 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1753959824&P2=404&P3=2&P4=nD4Y6qVYQV2U3zRyPotO2qfqfUbOjIeEBeD18Bxe8gBDzQTzZq5apcdbMQzz3VAn4EGBFf3PUX%2f%2fAIrMCgCIEw%3d%3d | unknown | — | — | whitelisted |
4216 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4c4fdee0-d69c-42b7-bf5c-3ec046e9dfc9?P1=1753956225&P2=404&P3=2&P4=IH9uvYpauqirX6BEN9YmKwFYxu23bGlmWiRCI3Ne6QQX51MuwiM9hsKHftoIuzkM1Dg1TzQifBu3VkZkjhZRew%3d%3d | unknown | — | — | whitelisted |
4216 | svchost.exe | GET | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4c4fdee0-d69c-42b7-bf5c-3ec046e9dfc9?P1=1753956225&P2=404&P3=2&P4=IH9uvYpauqirX6BEN9YmKwFYxu23bGlmWiRCI3Ne6QQX51MuwiM9hsKHftoIuzkM1Dg1TzQifBu3VkZkjhZRew%3d%3d | unknown | — | — | whitelisted |
4216 | svchost.exe | GET | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9244b52a-55cc-41a2-b7c4-7f4983d8753c?P1=1753956232&P2=404&P3=2&P4=bFknpXmGLSTyN7na2c8g5CSJ0REY3WjhqMWTZ5PBb9KK%2fjoGD4g0%2bV4Alw3IgODAKyxvGiQp08dcdaNY29z2kQ%3d%3d | unknown | — | — | whitelisted |
4216 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/2ef98485-cbad-4d99-b4c2-cd4abac73fb4?P1=1753959824&P2=404&P3=2&P4=V5aAJgRJMNRmzp%2fNzkZCBJVXEJlELUkD7nQ3OLUBFFAJ6wLV%2bYRgH%2fuBQyqJTt0VcjpJkpLw39aRKiopx%2bebbw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7032 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5528 | msedge.exe | 150.171.27.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5528 | msedge.exe | 150.171.22.17:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5528 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5528 | msedge.exe | 168.220.91.95:443 | ibit.ly | FLY | US | malicious |
5528 | msedge.exe | 2.16.241.220:443 | copilot.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
ibit.ly |
| malicious |
copilot.microsoft.com |
| whitelisted |
t.ly |
| whitelisted |
www.bing.com |
| whitelisted |
static.cloudflareinsights.com |
| whitelisted |
challenges.cloudflare.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5528 | msedge.exe | Misc activity | INFO [ANY.RUN] Possible short link service (ibit .ly) |
5528 | msedge.exe | Misc activity | INFO [ANY.RUN] Possible short link service (ibit .ly) |
5528 | msedge.exe | Misc activity | INFO [ANY.RUN] Possible short link service (t .ly) |
5528 | msedge.exe | Misc activity | INFO [ANY.RUN] Possible short link service (t .ly) |
5528 | msedge.exe | Misc activity | ET INFO URL Shortening Service Domain in DNS Lookup (t .ly) |
5528 | msedge.exe | Misc activity | ET INFO Observed URL Shortening Service Domain (t .ly in TLS SNI) |
5528 | msedge.exe | Misc activity | ET INFO URL Shortening Service Domain in DNS Lookup (t .ly) |
5528 | msedge.exe | Misc activity | ET INFO URL Shortening Service Domain in DNS Lookup (t .ly) |
5528 | msedge.exe | Misc activity | INFO [ANY.RUN] Possible short link service (t .ly) |
5528 | msedge.exe | Misc activity | ET INFO Observed URL Shortening Service Domain (t .ly in TLS SNI) |
Process | Message |
|---|---|
AgentPackageMonitoring.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\AgentPackageMonitoring\x64\SQLite.Interop.dll"...
|
AgentPackageMonitoring.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\AgentPackageMonitoring\x64\SQLite.Interop.dll"...
|
Agent.Package.Availability.exe | You must install .NET to run this application.
App: C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\Agent.Package.Availability\Agent.Package.Availability.exe
Architecture: x64
App host version: 8.0.11
.NET location: Not found
Learn more:
https://aka.ms/dotnet/app-launch-failed
Download the .NET runtime:
https://aka.ms/dotnet-core-applaunch?missing_runtime=true&arch=x64&rid=win-x64&os=win10&apphost_version=8.0.11 |
Agent.Package.Watchdog.exe | You must install .NET to run this application.
App: C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\Agent.Package.Watchdog\Agent.Package.Watchdog.exe
Architecture: x64
App host version: 8.0.11
.NET location: Not found
Learn more:
https://aka.ms/dotnet/app-launch-failed
Download the .NET runtime:
https://aka.ms/dotnet-core-applaunch?missing_runtime=true&arch=x64&rid=win-x64&os=win10&apphost_version=8.0.11 |
Agent.Package.Software.exe | You must install .NET to run this application.
App: C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\Agent.Package.Software\Agent.Package.Software.exe
Architecture: x64
App host version: 8.0.16
.NET location: Not found
Learn more:
https://aka.ms/dotnet/app-launch-failed
Download the .NET runtime:
https://aka.ms/dotnet-core-applaunch?missing_runtime=true&arch=x64&rid=win-x64&os=win10&apphost_version=8.0.16 |