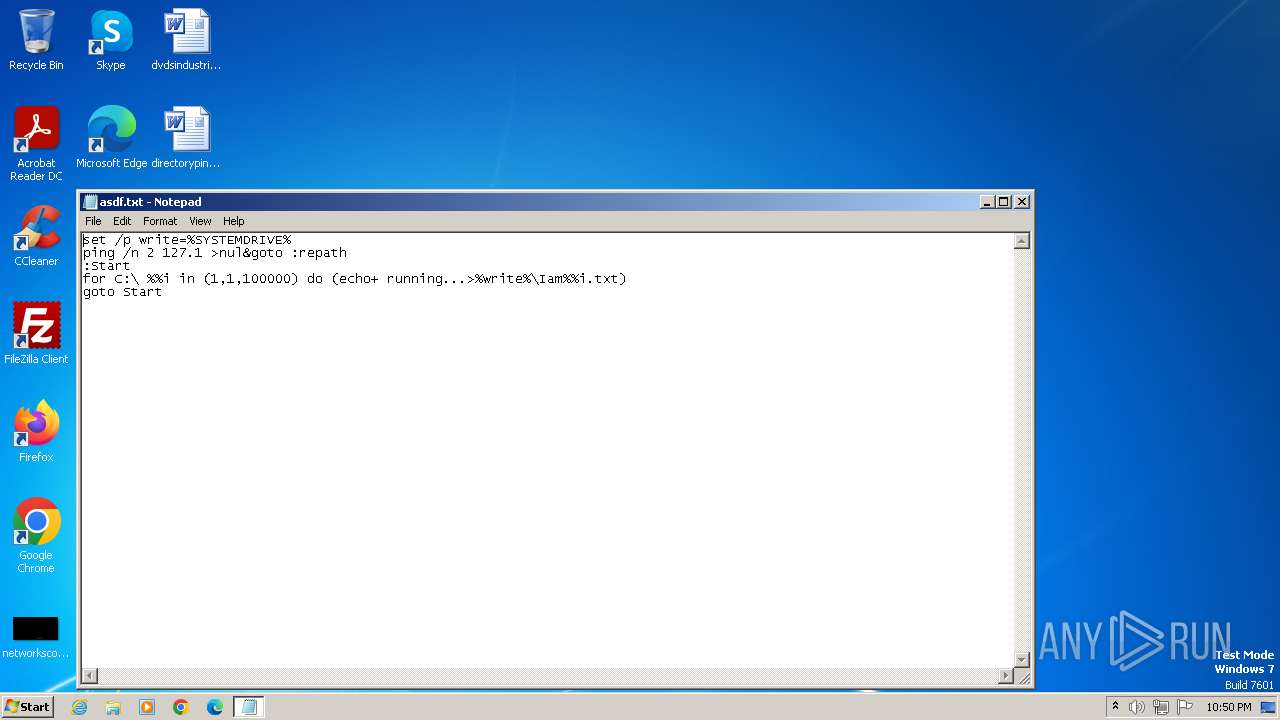
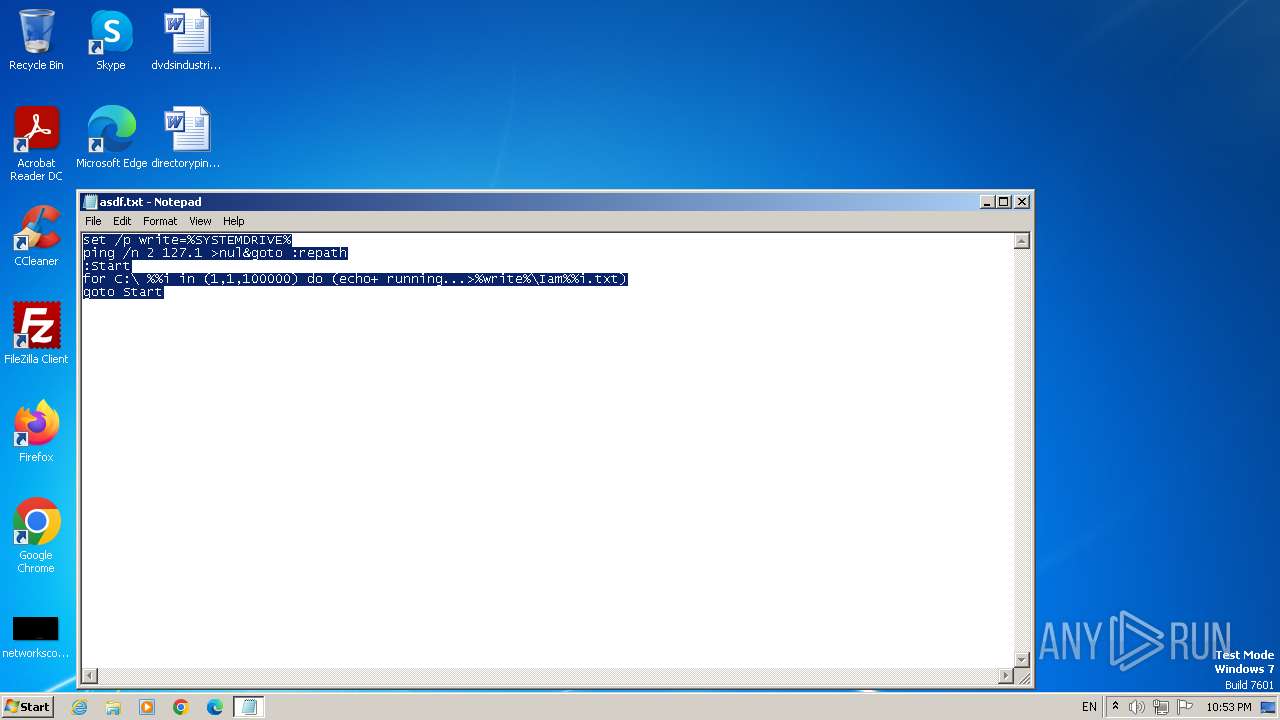
| File name: | asdf.txt |
| Full analysis: | https://app.any.run/tasks/6d67b97b-f148-4b59-bcfc-f4e607763031 |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2023, 21:50:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | B0F94F16ED5ACF5354D4775E4C7DC6D0 |
| SHA1: | A2CC0AF8136F079412367D81D08324E3E3EDB6AE |
| SHA256: | 7223954B63FC6D9873523CC549F27B755BBD4DD2F866D19B1DF340E1414D8852 |
| SSDEEP: | 3:WVobBy8dxXIh0e/AbWvDKXFmfv3UFdVEvsQhDUjsMvBon:HyEusbWvDMFovkFXEysuu |
MALICIOUS
Actions looks like stealing of personal data
- setup.exe (PID: 3320)
- setup.exe (PID: 3980)
Create files in the Startup directory
- regsvr32.exe (PID: 3020)
SUSPICIOUS
The process executes via Task Scheduler
- sipnotify.exe (PID: 1452)
Application launched itself
- ie4uinit.exe (PID: 2580)
- setup.exe (PID: 3320)
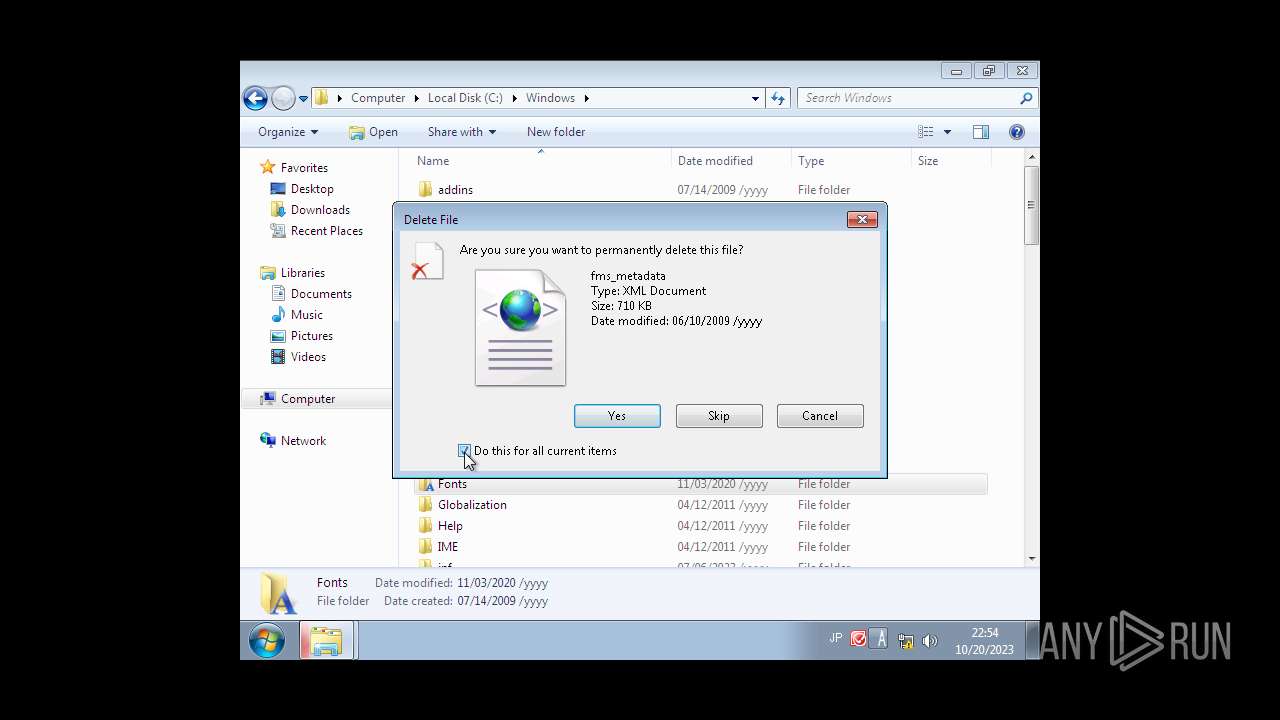
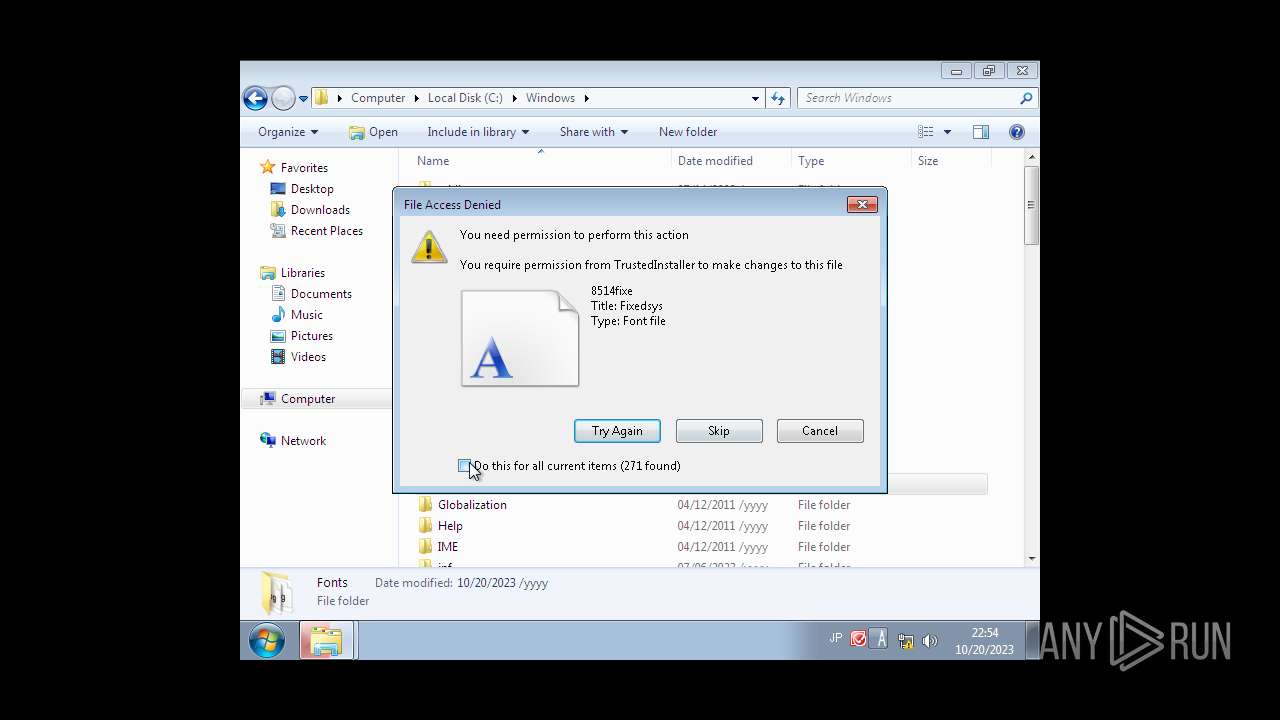
Write to the desktop.ini file (may be used to cloak folders)
- ie4uinit.exe (PID: 2580)
- WinMail.exe (PID: 3692)
- regsvr32.exe (PID: 3020)
Changes internet zones settings
- ie4uinit.exe (PID: 2580)
Reads the Internet Settings
- rundll32.exe (PID: 3788)
INFO
Manual execution by a user
- regedit.exe (PID: 2100)
- WinMail.exe (PID: 3692)
- ie4uinit.exe (PID: 2580)
- regsvr32.exe (PID: 3120)
- ie4uinit.exe (PID: 2120)
- unregmp2.exe (PID: 2304)
- regsvr32.exe (PID: 3020)
- ie4uinit.exe (PID: 2816)
- chrmstp.exe (PID: 4004)
- rundll32.exe (PID: 3788)
- setup.exe (PID: 3320)
- IMEKLMG.EXE (PID: 2976)
- IMEKLMG.EXE (PID: 3108)
- wmpnscfg.exe (PID: 2968)
- wmpnscfg.exe (PID: 3832)
Reads the computer name
- WinMail.exe (PID: 3692)
- setup.exe (PID: 3596)
- setup.exe (PID: 3980)
- IMEKLMG.EXE (PID: 3108)
- IMJPPDMG.EXE (PID: 3880)
- wmpnscfg.exe (PID: 2968)
- wmpnscfg.exe (PID: 3832)
- IMEKLMG.EXE (PID: 2976)
Checks supported languages
- WinMail.exe (PID: 3692)
- setup.exe (PID: 3596)
- setup.exe (PID: 3320)
- setup.exe (PID: 3980)
- IMEKLMG.EXE (PID: 2976)
- IMKRMIG.EXE (PID: 3164)
- IMJPPDMG.EXE (PID: 3880)
- wmpnscfg.exe (PID: 2968)
- wmpnscfg.exe (PID: 3832)
- IMEKLMG.EXE (PID: 3108)
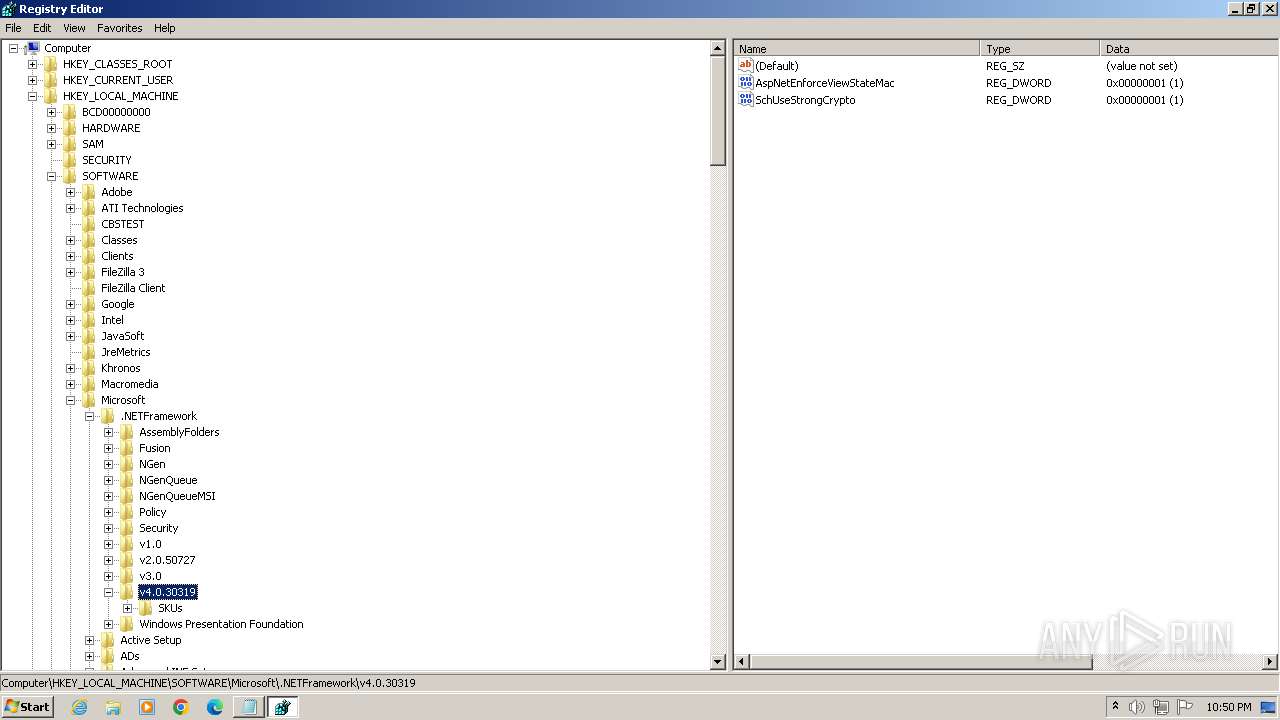
Reads the machine GUID from the registry
- WinMail.exe (PID: 3692)
- wmpnscfg.exe (PID: 2968)
- wmpnscfg.exe (PID: 3832)
Creates files or folders in the user directory
- unregmp2.exe (PID: 2304)
- regsvr32.exe (PID: 3020)
- WinMail.exe (PID: 3692)
Application launched itself
- chrmstp.exe (PID: 2564)
- chrmstp.exe (PID: 4004)
Process checks are UAC notifies on
- IMEKLMG.EXE (PID: 3108)
- IMJPPDMG.EXE (PID: 3880)
- wmpnscfg.exe (PID: 3832)
- wmpnscfg.exe (PID: 2968)
- IMEKLMG.EXE (PID: 2976)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
124
Monitored processes
26
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1240 | "C:\Windows\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\asdf.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1452 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 2100 | "C:\Windows\regedit.exe" | C:\Windows\regedit.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2120 | "C:\Windows\System32\ie4uinit.exe" -EnableTLS | C:\Windows\System32\ie4uinit.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IE Per-User Initialization Utility Exit code: 2147942402 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2304 | "C:\Windows\System32\unregmp2.exe" /FirstLogon /Shortcuts /RegBrowsers /ResetMUI | C:\Windows\System32\unregmp2.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Media Player Setup Utility Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2372 | "C:\Program Files\Google\Chrome\Application\109.0.5414.120\Installer\chrmstp.exe" --type=crashpad-handler /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler --database=C:\Windows\TEMP\Crashpad --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0x160,0x164,0x168,0x134,0x16c,0xed8ba8,0xed8bb8,0xed8bc4 | C:\Program Files\Google\Chrome\Application\109.0.5414.120\Installer\chrmstp.exe | — | chrmstp.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Installer Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2564 | "C:\Program Files\Google\Chrome\Application\109.0.5414.120\Installer\chrmstp.exe" --system-level --verbose-logging --installerdata="C:\Program Files\Google\Chrome\Application\master_preferences" --create-shortcuts=2 --install-level=0 | C:\Program Files\Google\Chrome\Application\109.0.5414.120\Installer\chrmstp.exe | — | chrmstp.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Installer Exit code: 73 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2580 | "C:\Windows\System32\ie4uinit.exe" -UserConfig | C:\Windows\System32\ie4uinit.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IE Per-User Initialization Utility Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2804 | C:\Windows\System32\ie4uinit.exe -ClearIconCache | C:\Windows\System32\ie4uinit.exe | — | ie4uinit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IE Per-User Initialization Utility Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2816 | "C:\Windows\System32\ie4uinit.exe" -DisableSSL3 | C:\Windows\System32\ie4uinit.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IE Per-User Initialization Utility Exit code: 2147942402 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
21 203
Read events
6 509
Write events
135
Delete events
14 559
Modification events
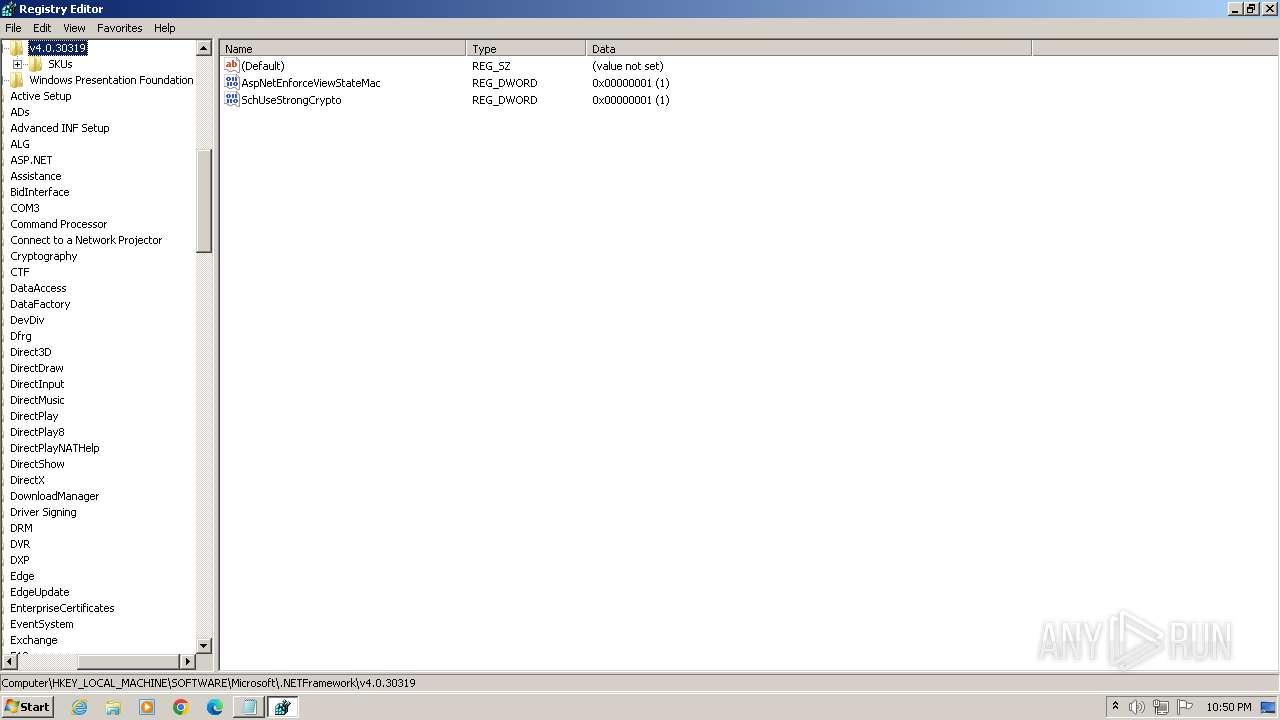
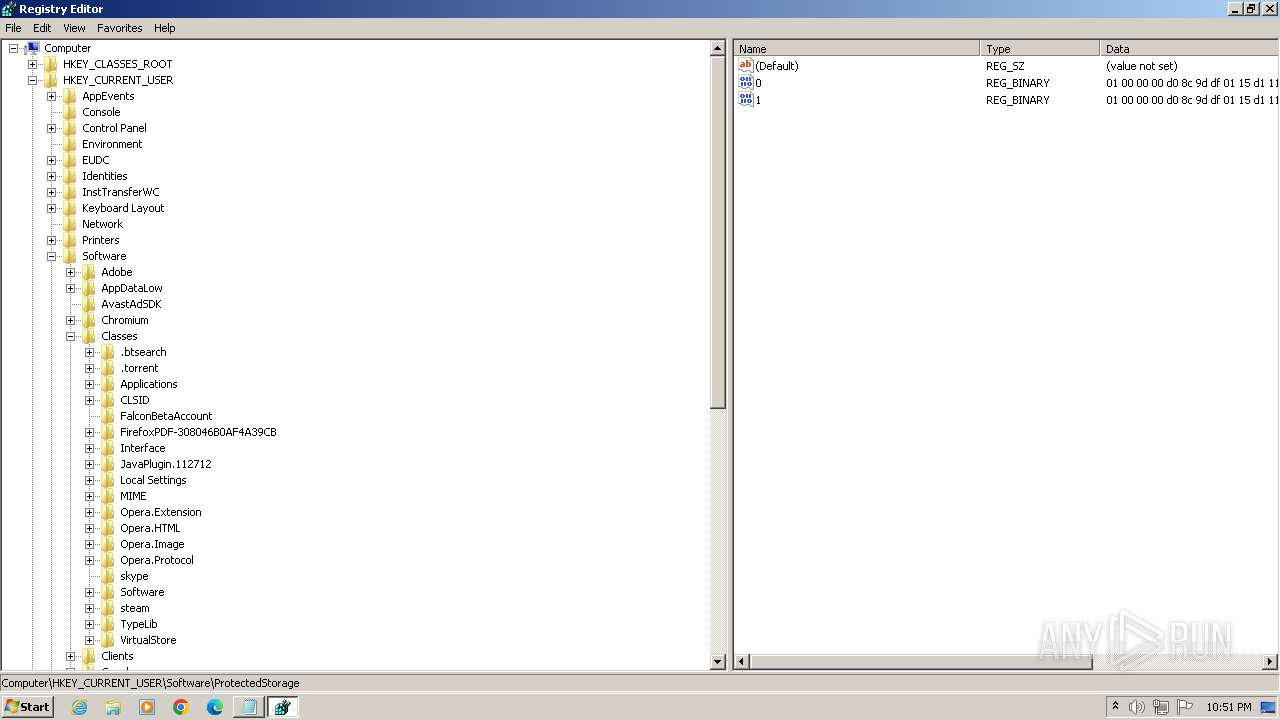
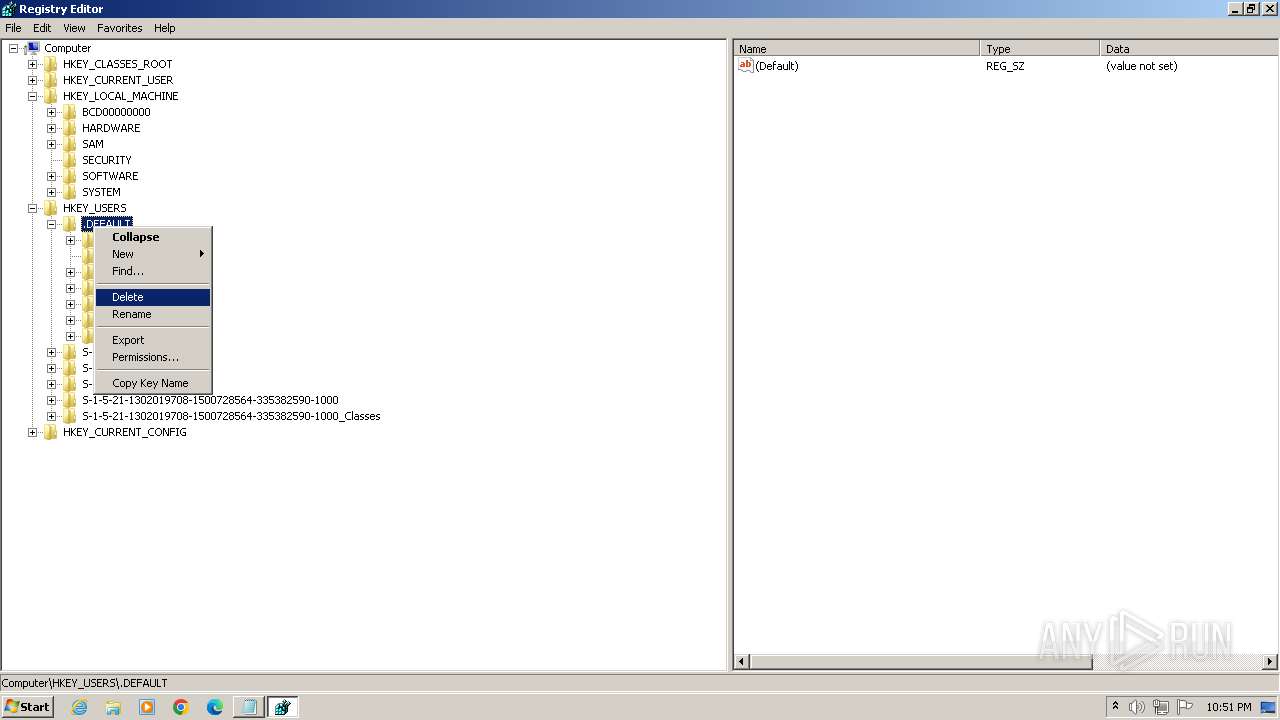
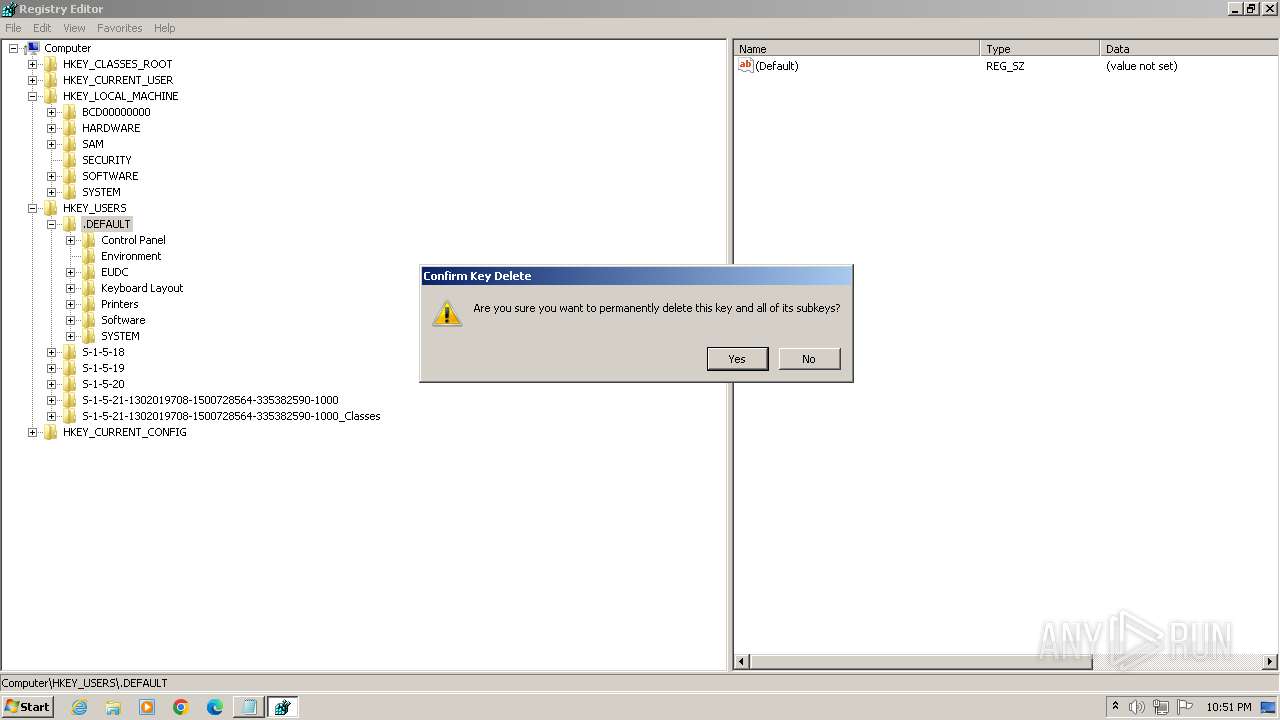
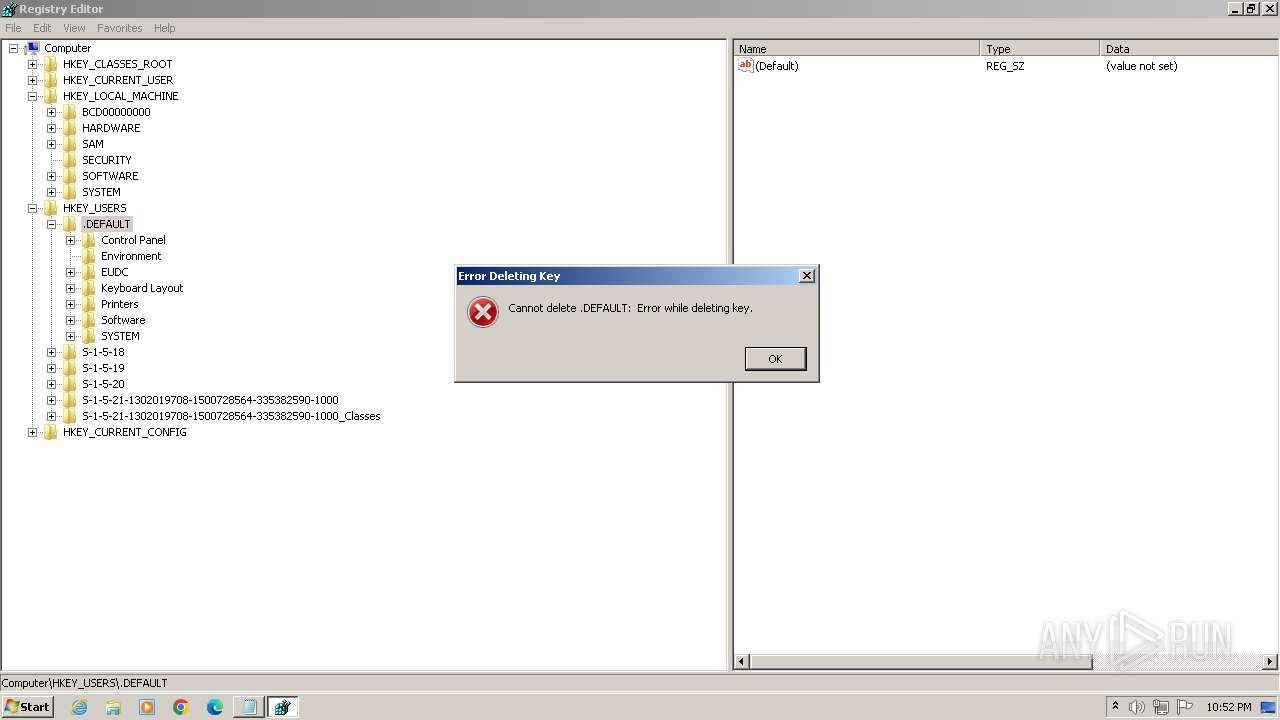
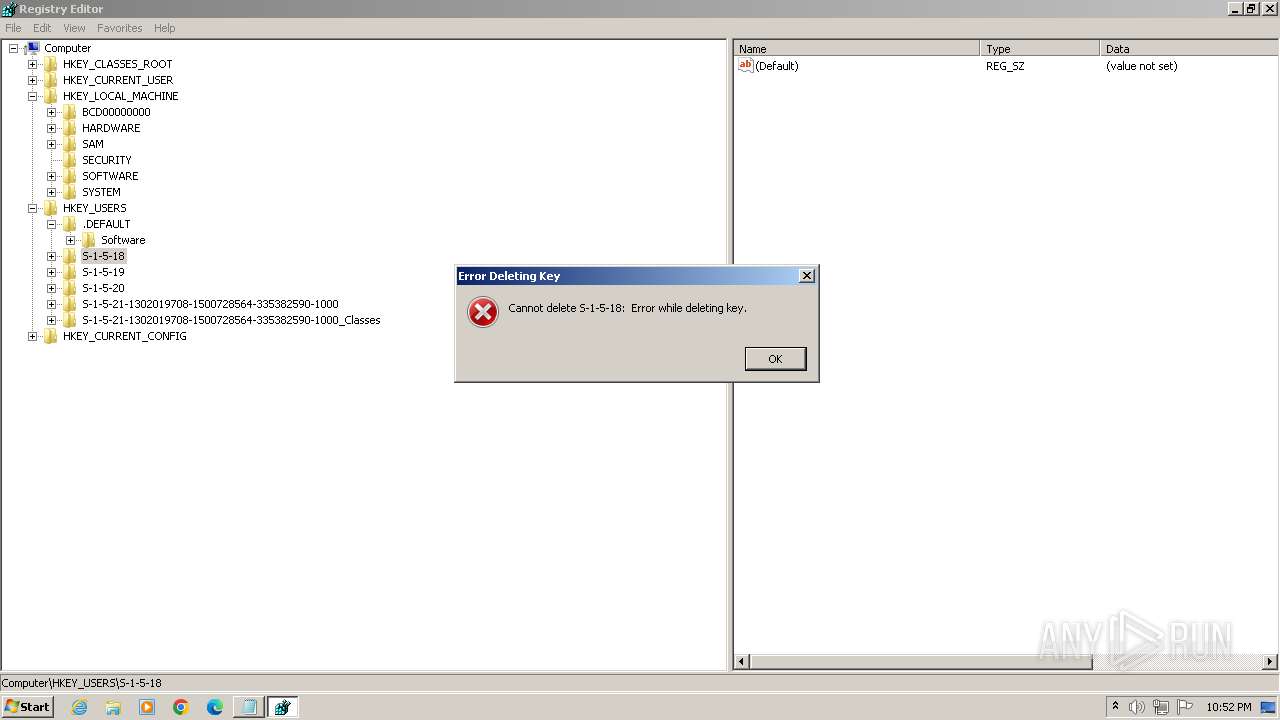
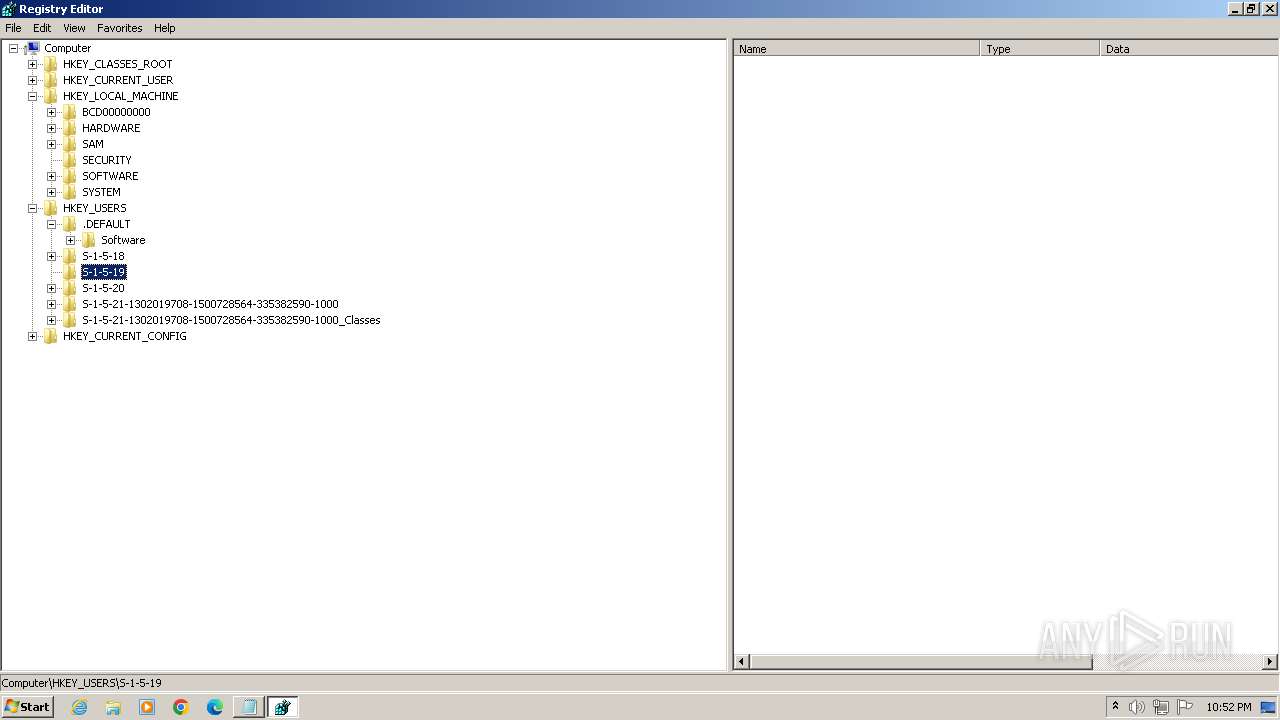
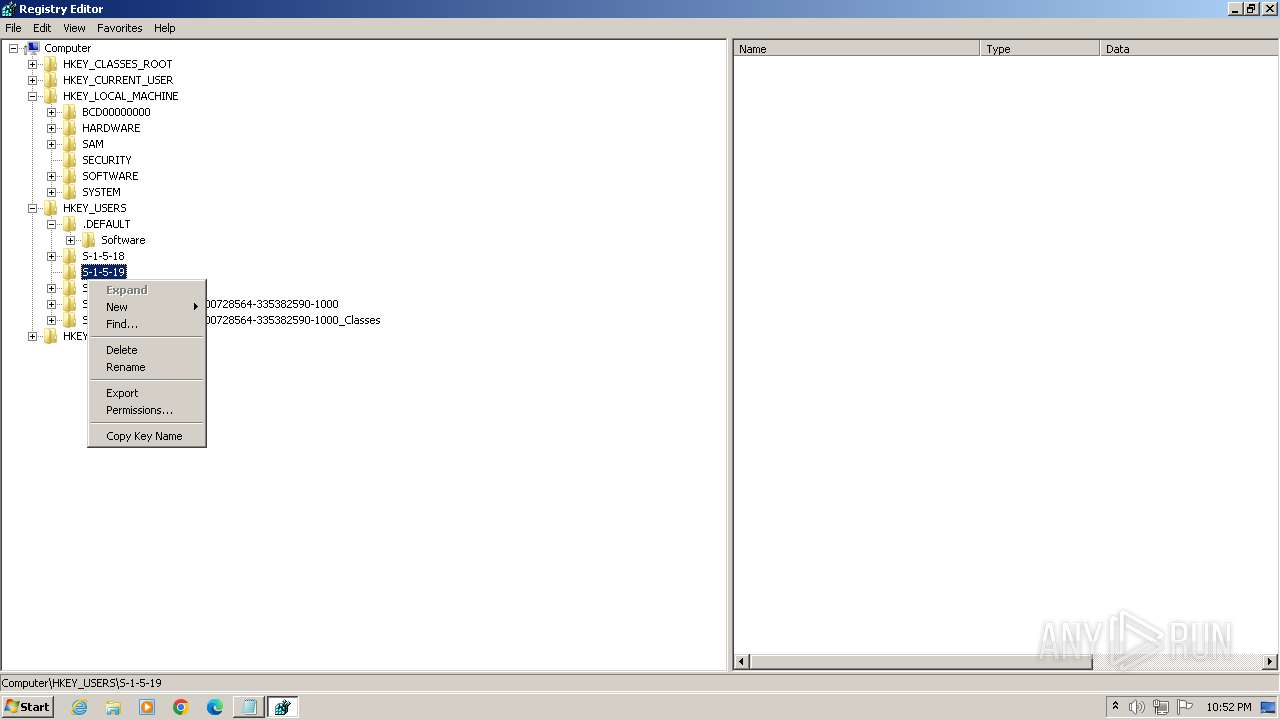
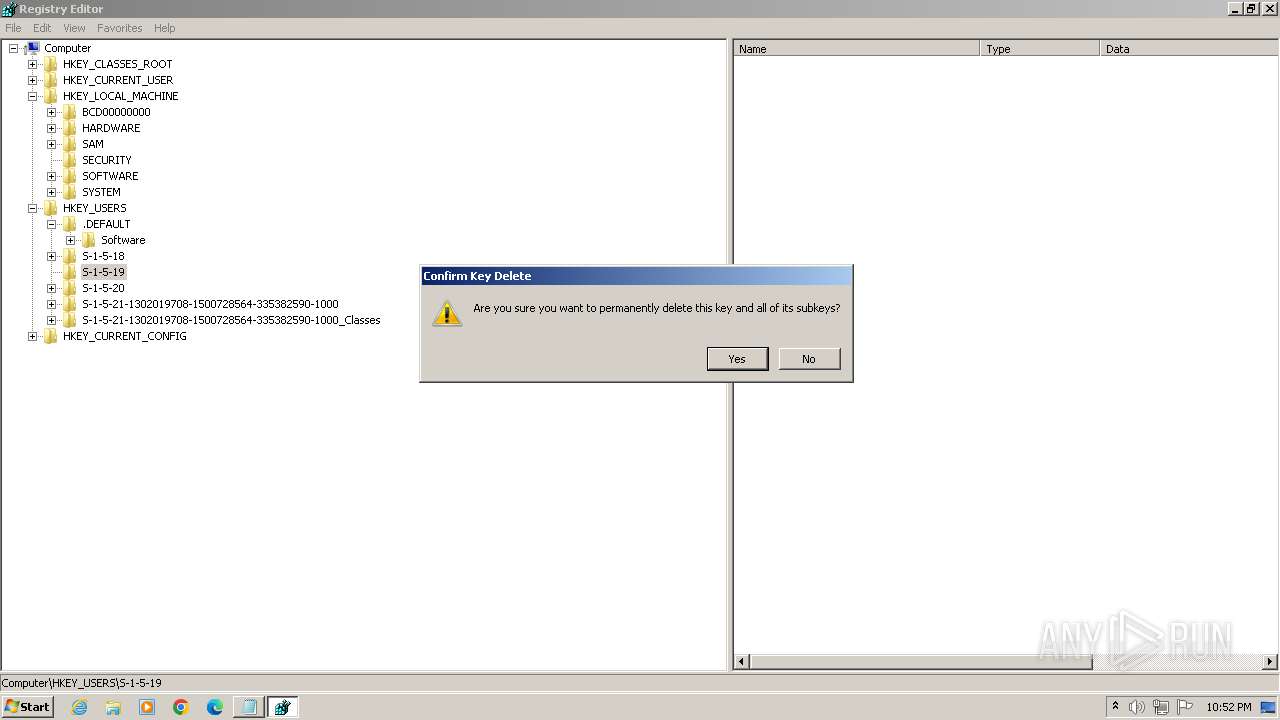
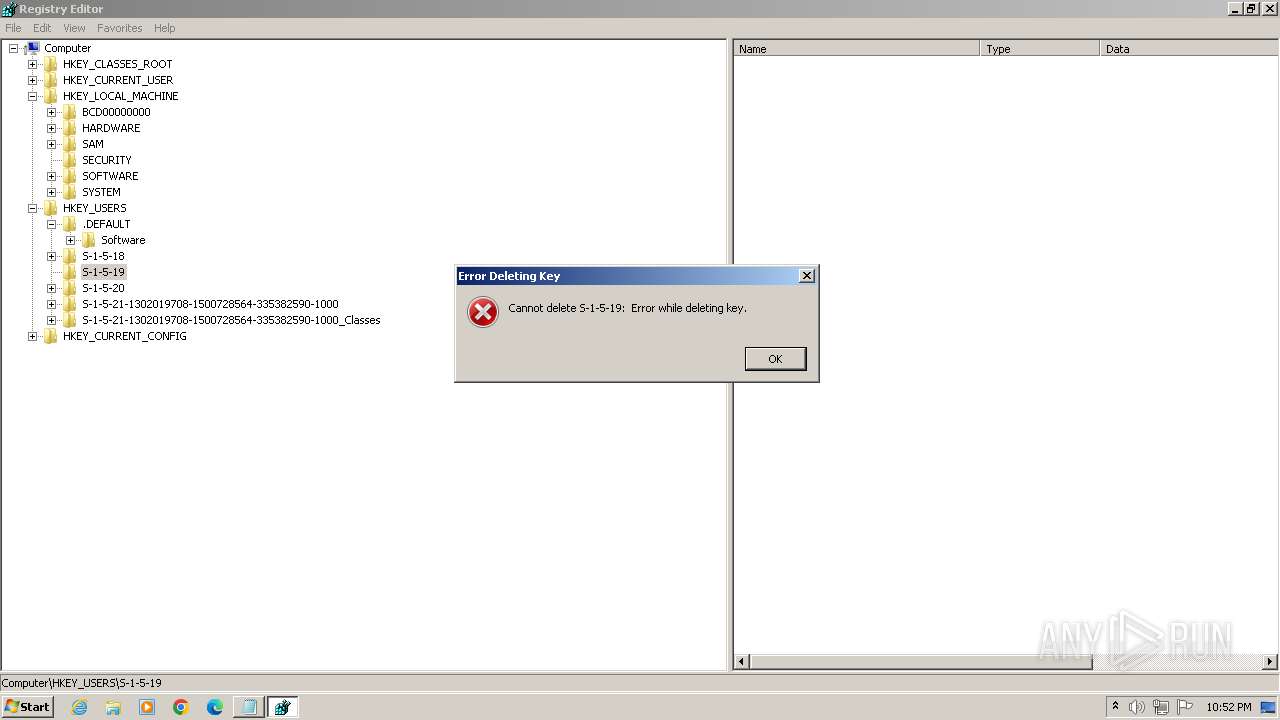
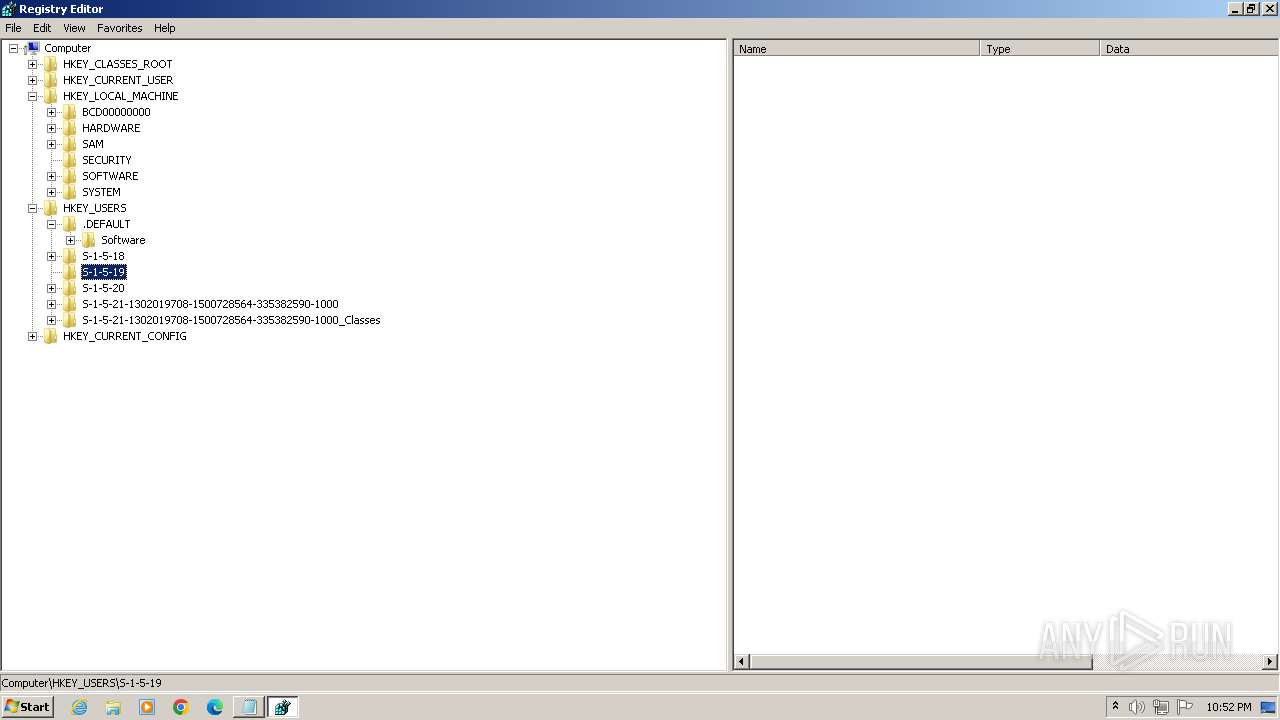
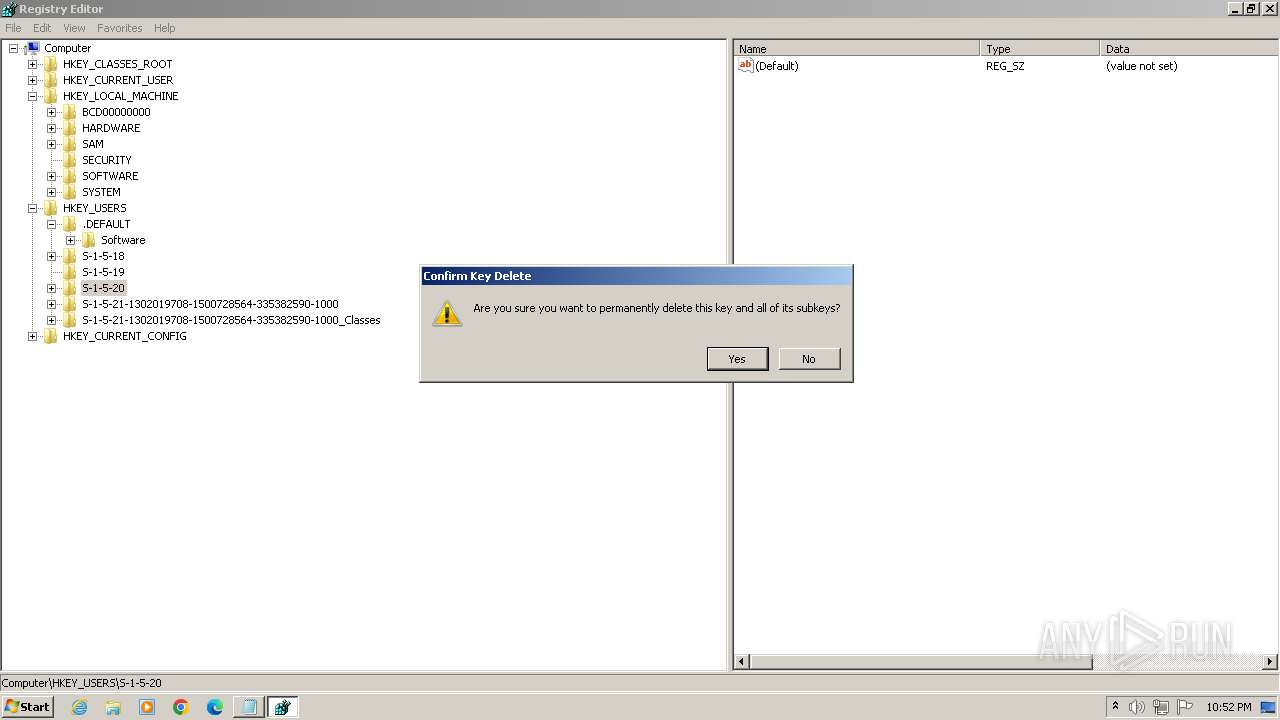
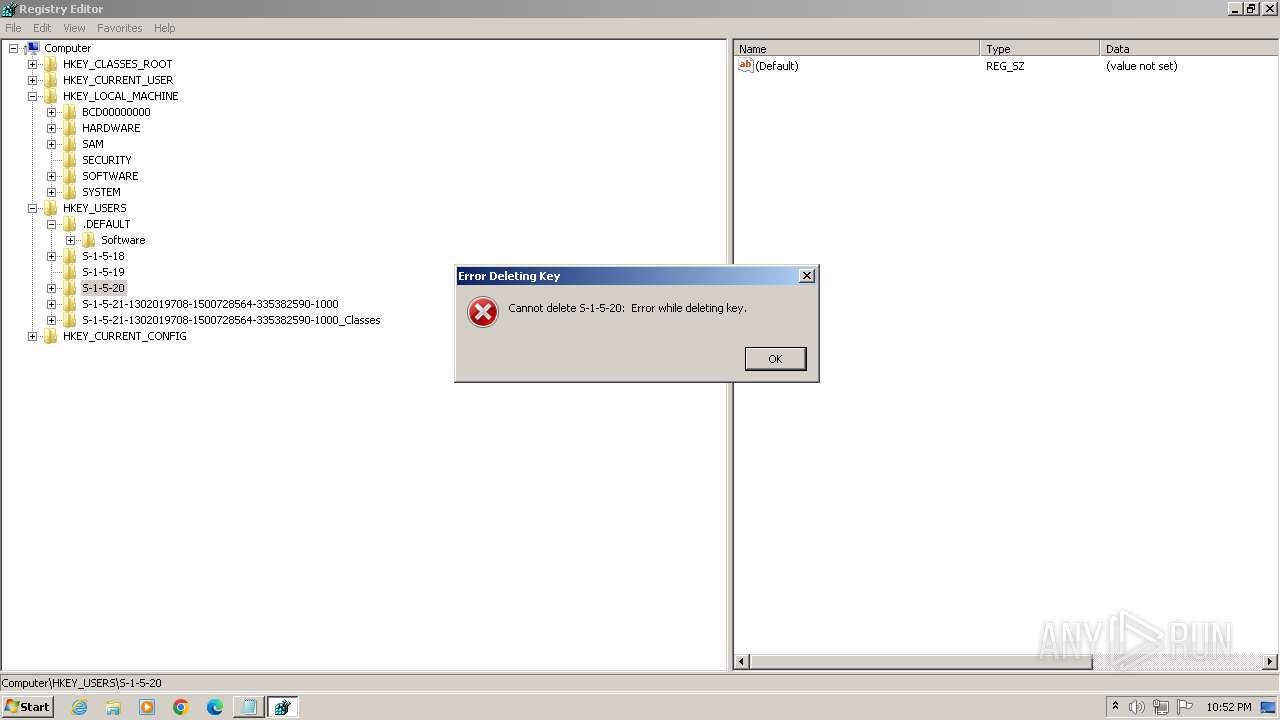
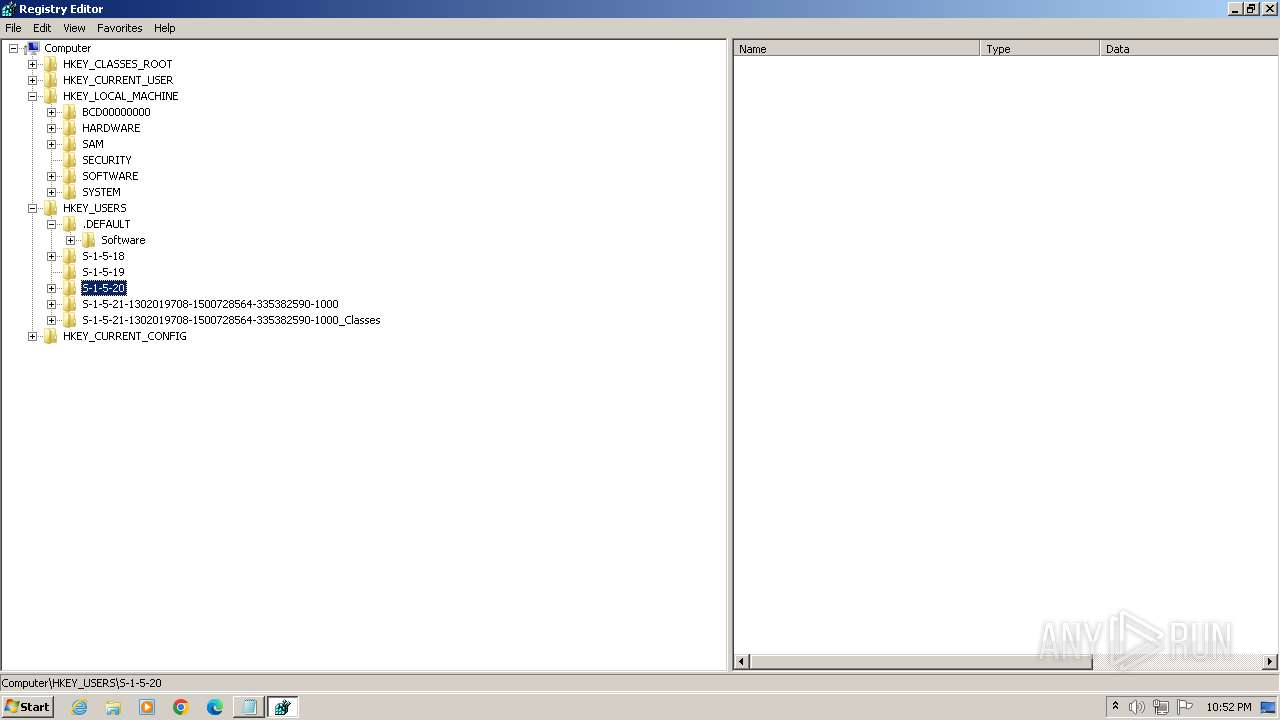
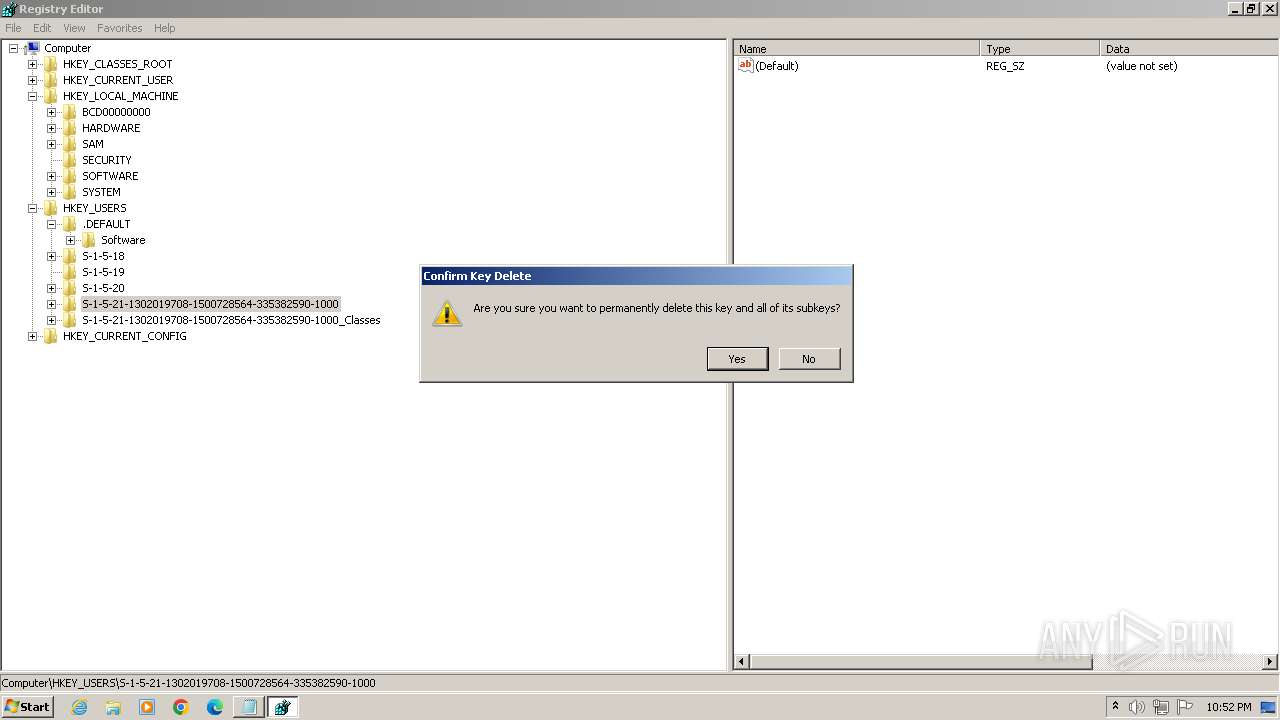
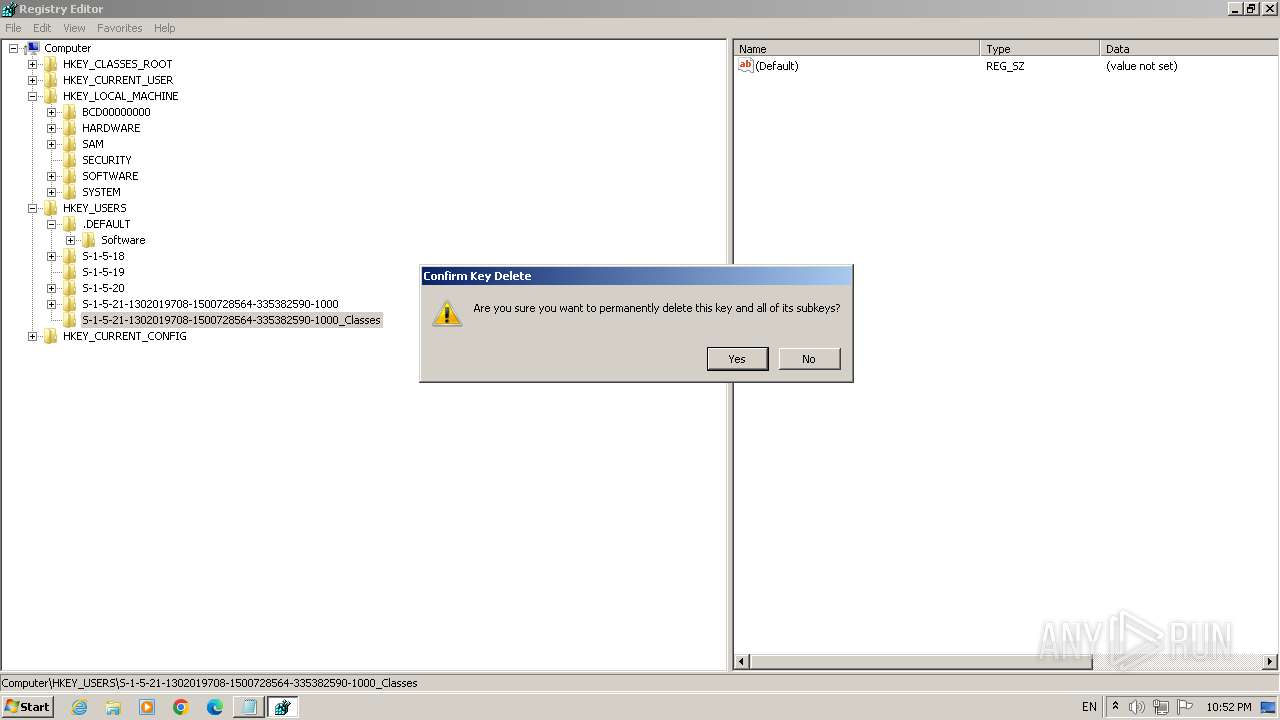
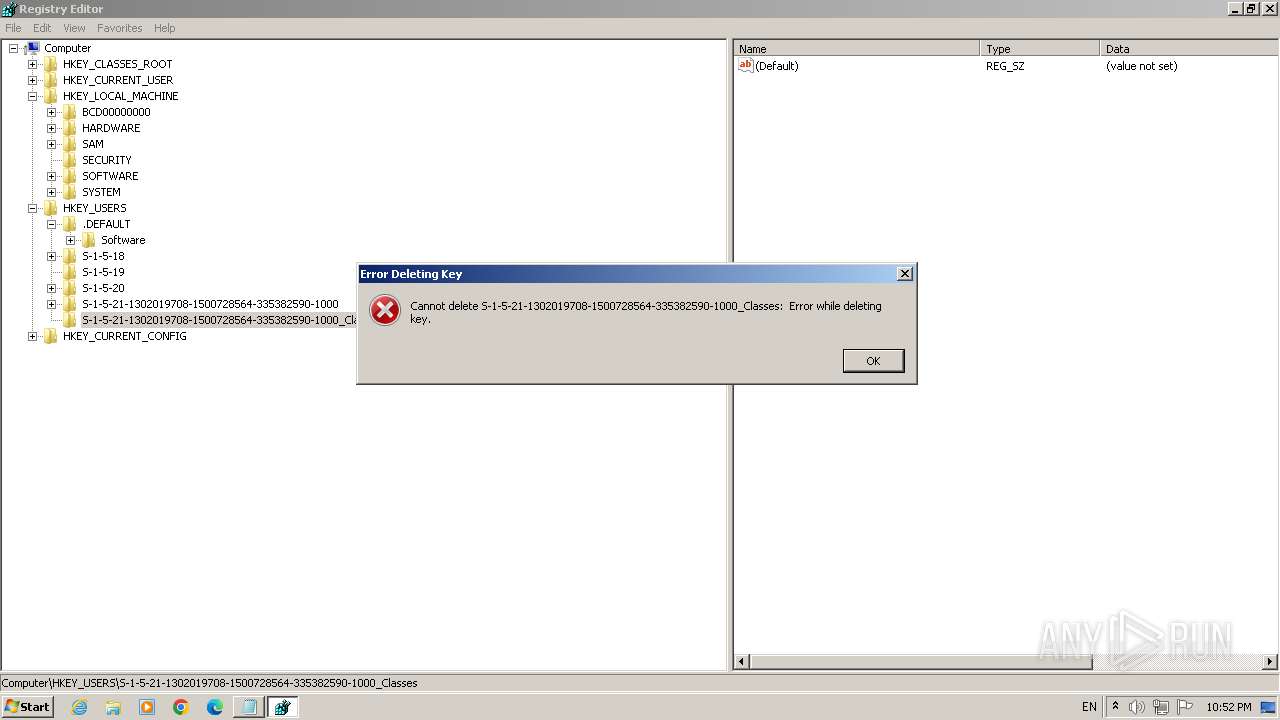
| (PID) Process: | (2100) regedit.exe | Key: | HKEY_USERS\.DEFAULT\Control Panel\Accessibility\Blind Access |
| Operation: | delete key | Name: | (default) |
Value: | |||
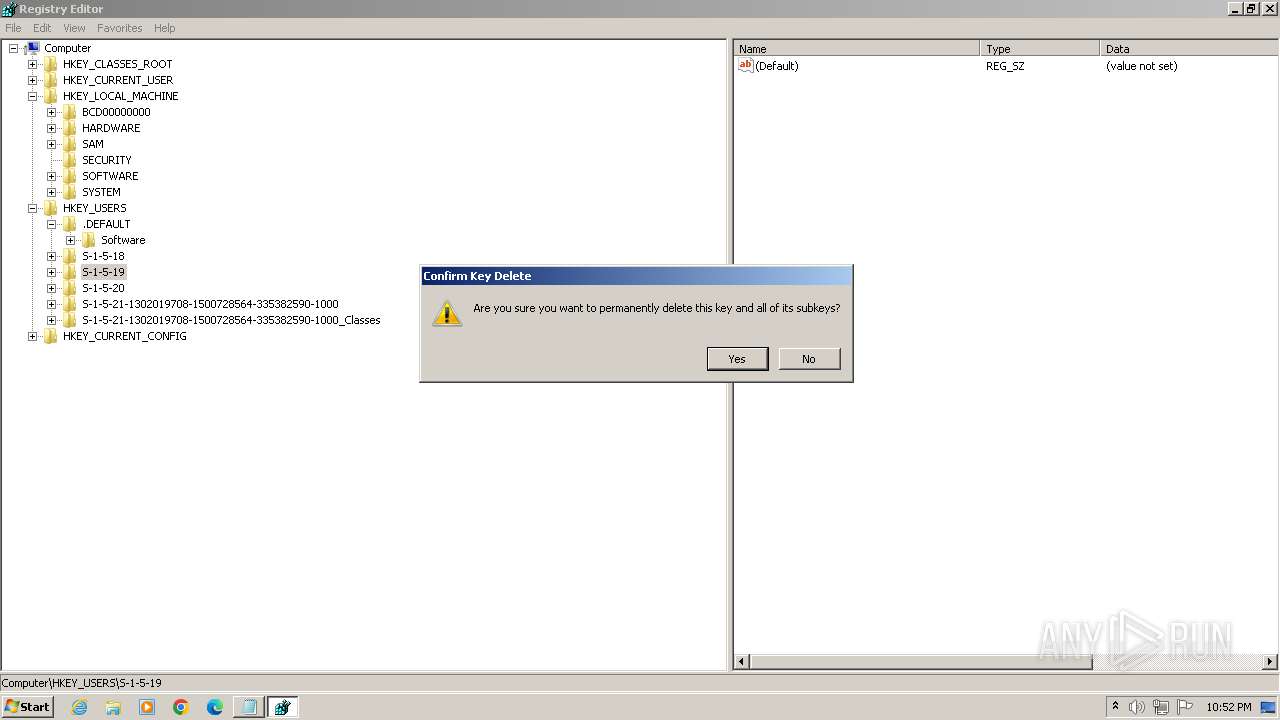
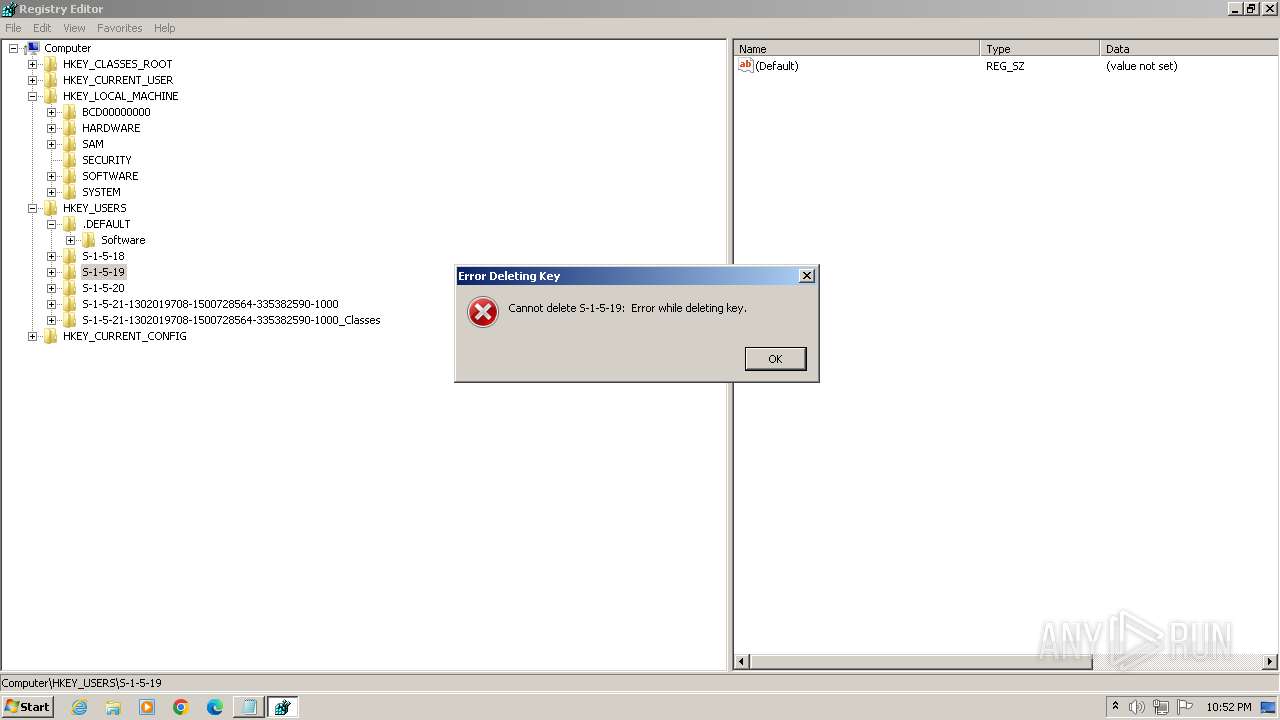
| (PID) Process: | (2100) regedit.exe | Key: | HKEY_USERS\.DEFAULT\Control Panel\Accessibility\HighContrast |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2100) regedit.exe | Key: | HKEY_USERS\.DEFAULT\Control Panel\Accessibility\Keyboard Preference |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2100) regedit.exe | Key: | HKEY_USERS\.DEFAULT\Control Panel\Accessibility\Keyboard Response |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2100) regedit.exe | Key: | HKEY_USERS\.DEFAULT\Control Panel\Accessibility\MouseKeys |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2100) regedit.exe | Key: | HKEY_USERS\.DEFAULT\Control Panel\Accessibility\ShowSounds |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2100) regedit.exe | Key: | HKEY_USERS\.DEFAULT\Control Panel\Accessibility\SoundSentry |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2100) regedit.exe | Key: | HKEY_USERS\.DEFAULT\Control Panel\Accessibility\StickyKeys |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2100) regedit.exe | Key: | HKEY_USERS\.DEFAULT\Control Panel\Accessibility\TimeOut |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2100) regedit.exe | Key: | HKEY_USERS\.DEFAULT\Control Panel\Accessibility\ToggleKeys |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
3
Suspicious files
21
Text files
86
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2580 | ie4uinit.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\brndlog.bak | text | |
MD5:E9E473C9777B0C24D50EE8C972A78FE2 | SHA256:90BE32975E76E679B01FF719148DF508CBBE2D7F2C47D93201F33A31994B4174 | |||
| 2580 | ie4uinit.exe | C:\Users\admin\Favorites\Links\Web Slice Gallery.url | text | |
MD5:1E7E5E93C2A5AADAF932F93D25C57F3E | SHA256:8B94D04FECE582E4182E8E73F46FB86EB8E965C69C526C42805ABB9E43641E35 | |||
| 3120 | regsvr32.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Themes\TranscodedWallpaper.jpg | image | |
MD5:DA288DCEAAFD7C97F1B09C594EAC7868 | SHA256:6EA9F8468C76AA511A5B3CFC36FB212B86E7ABD377F147042D2F25572BF206A2 | |||
| 3692 | WinMail.exe | C:\Users\admin\Contacts\admin (1).contact | xml | |
MD5:F9E956CED1AE0C34669B5EE3D3A58D7B | SHA256:05845C0F7707F4614598E8C9BEA594DA50B6C643C8D076977A6BDEF99DFB4746 | |||
| 2580 | ie4uinit.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Tiles\pin9728060290\msapplication.xml | xml | |
MD5:2A1C87CD272B6EE31F2239A3E194CD85 | SHA256:63FAE7434D8B46D1D7F23C865CB21D1DB562AB5249848486B2CC395E1D178BF0 | |||
| 3692 | WinMail.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Mail\edb.chk | binary | |
MD5:B6D05D0D510E7C5EF490646F7381AD30 | SHA256:462963F5A000A1794AD4E4BEBA2F495A5BEA81E2ABF2543CACF5E341D5465B74 | |||
| 2580 | ie4uinit.exe | C:\Windows\TEMP\www4585.tmp | binary | |
MD5:C2858B664C882DCCE6042C40041F6108 | SHA256:B4A6FB97B5E3F87BCD9FAE49A9174E3F5B230A37767D7A70BF33D151702EFF91 | |||
| 3692 | WinMail.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Mail\edb.log | binary | |
MD5:09F9EC30C43F61C1B4E3CF574CEF1740 | SHA256:3A2C8485989DE3437B107D5459308E6984CC2D0F029B25CA74DFA0BC4B754054 | |||
| 2580 | ie4uinit.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\brndlog.txt | text | |
MD5:D9E196C35C4E962D453619C09F9E373D | SHA256:68922153BBEE889DD3E2C0DA9CECE35EAD2ABBD858857A3A28D61BED8C6977AF | |||
| 2580 | ie4uinit.exe | C:\Users\admin\Favorites\Links\desktop.ini | text | |
MD5:3C106F431417240DA12FD827323B7724 | SHA256:E469ED17B4B54595B335DC51817A52B81FCF13AAD7B7B994626F84EC097C5D57 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
12
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
— | — | 239.255.255.250:3702 | — | — | — | unknown |
— | — | 239.255.255.250:1900 | — | — | — | unknown |