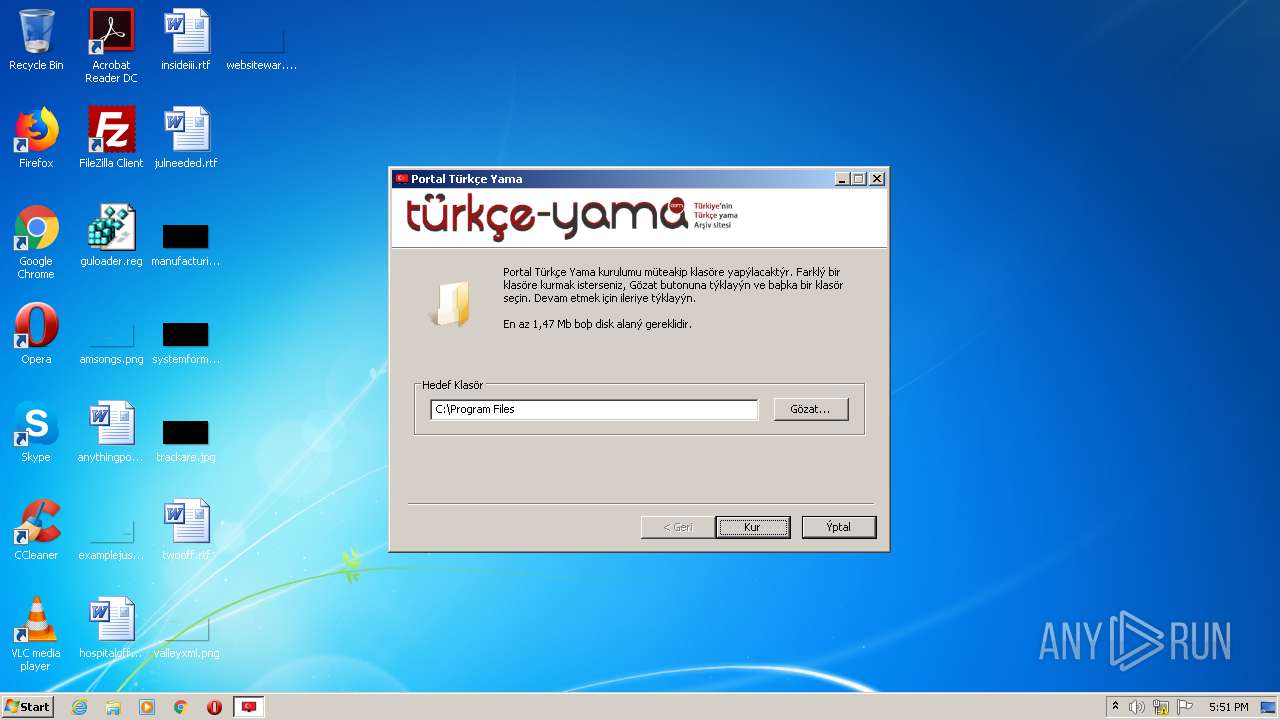
| File name: | Portal Turkce Yama.exe |
| Full analysis: | https://app.any.run/tasks/7c2f65d8-ad81-44fd-8a70-473d71ce3eb2 |
| Verdict: | Malicious activity |
| Analysis date: | November 29, 2020, 17:51:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 75A06B35D01B0F8983EE22D6CBFAF3F7 |
| SHA1: | 8DE4432E8388C57C90A132A4F40EC1EAF23EC3AC |
| SHA256: | 721AE90B24213689F2F70E1ADC969A4AB77F778F6DD7511C82E8263E7465385B |
| SSDEEP: | 6144:VZXBsWqsE/Ao+mv8Qv0LVmwq4FU0nN876IEmDYaNwPwQWgy81pw:TXmwRo+mv8QD4+0N46IEUlp8I |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates files in the program directory
- Portal Turkce Yama.exe (PID: 2948)
Creates a directory in Program Files
- Portal Turkce Yama.exe (PID: 2948)
Creates a software uninstall entry
- Portal Turkce Yama.exe (PID: 2948)
Starts Internet Explorer
- Portal Turkce Yama.exe (PID: 2948)
INFO
Application launched itself
- iexplore.exe (PID: 2836)
Changes internet zones settings
- iexplore.exe (PID: 2836)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3156)
Changes settings of System certificates
- iexplore.exe (PID: 3156)
Reads settings of System Certificates
- iexplore.exe (PID: 3156)
Reads internet explorer settings
- iexplore.exe (PID: 3156)
Creates files in the user directory
- iexplore.exe (PID: 3156)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (31.9) |
|---|---|---|
| .scr | | | Windows screen saver (29.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (14.8) |
| .exe | | | Win32 Executable (generic) (10.1) |
| .exe | | | Win16/32 Executable Delphi generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 148992 |
| InitializedDataSize: | 78848 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x25468 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | - |
| CompanyName: | Valve |
| FileDescription: | Portal Türkçe Yama 1.0 Installation |
| FileVersion: | 1.0 |
| LegalCopyright: | Valve |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 19-Jun-1992 22:22:17 |
| Detected languages: |
|
| Comments: | - |
| CompanyName: | Valve |
| FileDescription: | Portal Türkçe Yama 1.0 Installation |
| FileVersion: | 1.0 |
| LegalCopyright: | Valve |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 8 |
| Time date stamp: | 19-Jun-1992 22:22:17 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
CODE | 0x00001000 | 0x000244CC | 0x00024600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.59438 |
DATA | 0x00026000 | 0x00002894 | 0x00002A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.79376 |
BSS | 0x00029000 | 0x000010F5 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x0002B000 | 0x00001798 | 0x00001800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.88549 |
.tls | 0x0002D000 | 0x00000008 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x0002E000 | 0x00000018 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 0.204488 |
.reloc | 0x0002F000 | 0x00001884 | 0x00001A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 6.58665 |
.rsrc | 0x00031000 | 0x0000D50C | 0x0000D600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 5.29718 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.93923 | 886 | UNKNOWN | Russian - Russia | RT_MANIFEST |
50 | 2.62878 | 744 | UNKNOWN | UNKNOWN | RT_ICON |
51 | 2.95452 | 296 | UNKNOWN | UNKNOWN | RT_ICON |
52 | 4.16574 | 3752 | UNKNOWN | UNKNOWN | RT_ICON |
53 | 4.48853 | 2216 | UNKNOWN | UNKNOWN | RT_ICON |
54 | 4.64326 | 1384 | UNKNOWN | UNKNOWN | RT_ICON |
55 | 7.88386 | 11060 | UNKNOWN | UNKNOWN | RT_ICON |
56 | 3.5369 | 16936 | UNKNOWN | UNKNOWN | RT_ICON |
57 | 3.86664 | 9640 | UNKNOWN | UNKNOWN | RT_ICON |
58 | 4.15296 | 4264 | UNKNOWN | UNKNOWN | RT_ICON |
Imports
advapi32.dll |
cabinet.dll |
comctl32.dll |
gdi32.dll |
kernel32.dll |
ole32.dll |
oleaut32.dll |
shell32.dll |
user32.dll |
winmm.dll |
Total processes
41
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2392 | "C:\Users\admin\AppData\Local\Temp\Portal Turkce Yama.exe" | C:\Users\admin\AppData\Local\Temp\Portal Turkce Yama.exe | — | explorer.exe | |||||||||||
User: admin Company: Valve Integrity Level: MEDIUM Description: Portal Türkçe Yama 1.0 Installation Exit code: 3221226540 Version: 1.0 Modules
| |||||||||||||||
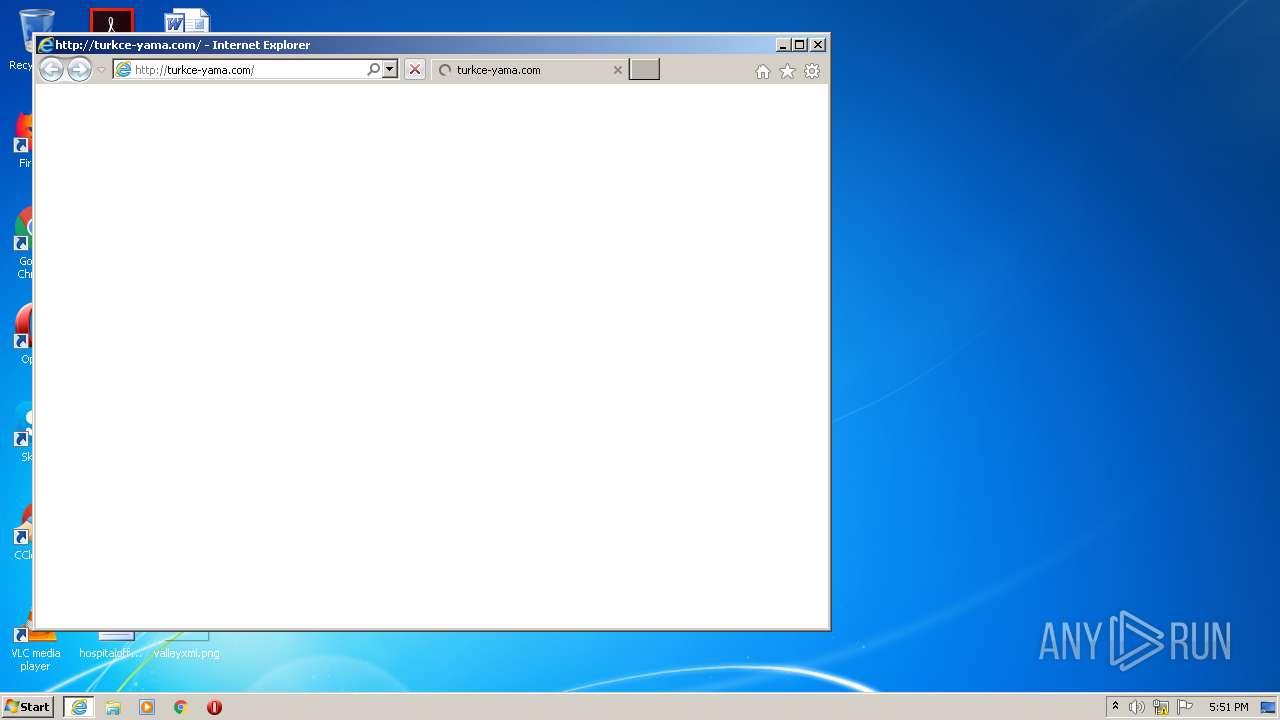
| 2836 | "C:\Program Files\Internet Explorer\iexplore.exe" http://turkce-yama.com/ | C:\Program Files\Internet Explorer\iexplore.exe | Portal Turkce Yama.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2948 | "C:\Users\admin\AppData\Local\Temp\Portal Turkce Yama.exe" | C:\Users\admin\AppData\Local\Temp\Portal Turkce Yama.exe | explorer.exe | ||||||||||||
User: admin Company: Valve Integrity Level: HIGH Description: Portal Türkçe Yama 1.0 Installation Exit code: 3221225547 Version: 1.0 Modules
| |||||||||||||||
| 3156 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2836 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
408
Read events
296
Write events
112
Delete events
0
Modification events
| (PID) Process: | (2948) Portal Turkce Yama.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Portal Türkçe Yama 1.0 |
| Operation: | write | Name: | DisplayName |
Value: Portal Türkçe Yama 1.0 | |||
| (PID) Process: | (2948) Portal Turkce Yama.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Portal Türkçe Yama 1.0 |
| Operation: | write | Name: | DisplayVersion |
Value: 1.0 | |||
| (PID) Process: | (2948) Portal Turkce Yama.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Portal Türkçe Yama 1.0 |
| Operation: | write | Name: | VersionMajor |
Value: 1 | |||
| (PID) Process: | (2948) Portal Turkce Yama.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Portal Türkçe Yama 1.0 |
| Operation: | write | Name: | VersionMinor |
Value: 0 | |||
| (PID) Process: | (2948) Portal Turkce Yama.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Portal Türkçe Yama 1.0 |
| Operation: | write | Name: | Publisher |
Value: Valve | |||
| (PID) Process: | (2948) Portal Turkce Yama.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Portal Türkçe Yama 1.0 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\Uninstall.exe | |||
| (PID) Process: | (2948) Portal Turkce Yama.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Portal Türkçe Yama 1.0 |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files\Uninstall.exe | |||
| (PID) Process: | (2948) Portal Turkce Yama.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Portal Türkçe Yama 1.0 |
| Operation: | write | Name: | URLInfoAbout |
Value: http://turkce-yama.com/ | |||
| (PID) Process: | (2948) Portal Turkce Yama.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Portal Türkçe Yama 1.0 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\ | |||
| (PID) Process: | (2948) Portal Turkce Yama.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Portal Türkçe Yama 1.0 |
| Operation: | write | Name: | InstallSource |
Value: C:\Users\admin\AppData\Local\Temp\ | |||
Executable files
0
Suspicious files
41
Text files
58
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2948 | Portal Turkce Yama.exe | C:\Users\admin\AppData\Local\Temp\$inst\temp_0.tmp | — | |
MD5:— | SHA256:— | |||
| 3156 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab41AB.tmp | — | |
MD5:— | SHA256:— | |||
| 3156 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar41AC.tmp | — | |
MD5:— | SHA256:— | |||
| 2948 | Portal Turkce Yama.exe | C:\Users\admin\AppData\Local\Temp\$inst\2.tmp | compressed | |
MD5:— | SHA256:— | |||
| 2948 | Portal Turkce Yama.exe | C:\Program Files\portal\resource\closecaption_russian.txt | text | |
MD5:— | SHA256:— | |||
| 2948 | Portal Turkce Yama.exe | C:\Program Files\portal\resource\portal_english.txt | text | |
MD5:— | SHA256:— | |||
| 2948 | Portal Turkce Yama.exe | C:\Program Files\portal\resource\portal_turkish.txt | text | |
MD5:— | SHA256:— | |||
| 2948 | Portal Turkce Yama.exe | C:\Program Files\portal\resource\closecaption_russian.dat | binary | |
MD5:— | SHA256:— | |||
| 2948 | Portal Turkce Yama.exe | C:\Program Files\portal\resource\closecaption_turkish.txt | text | |
MD5:— | SHA256:— | |||
| 2948 | Portal Turkce Yama.exe | C:\Program Files\portal\resource\closecaption_enlish.dat | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
32
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3156 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQC6YgyyDBC1Fte65XgTsh2k | US | der | 472 b | whitelisted |
3156 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
3156 | iexplore.exe | GET | 301 | 185.226.160.27:80 | http://turkce-yama.com/ | unknown | html | 147 b | whitelisted |
3156 | iexplore.exe | GET | 200 | 172.217.18.163:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQCKcuDfDBqJ0QIAAAAAgFWT | US | der | 472 b | whitelisted |
3156 | iexplore.exe | GET | 200 | 216.58.207.67:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEFcLuT0XSrlKAgAAAACAVZE%3D | US | der | 471 b | whitelisted |
3156 | iexplore.exe | GET | 200 | 216.58.207.67:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDgM%2F2Oalb9SggAAAAAYth0 | US | der | 472 b | whitelisted |
3156 | iexplore.exe | GET | 200 | 172.217.18.163:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEFcLuT0XSrlKAgAAAACAVZE%3D | US | der | 471 b | whitelisted |
3156 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
3156 | iexplore.exe | GET | 200 | 216.58.207.67:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDa2MTpyZrzlQgAAAAAYth4 | US | der | 472 b | whitelisted |
3156 | iexplore.exe | GET | 200 | 216.58.207.67:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQCKcuDfDBqJ0QIAAAAAgFWT | US | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3156 | iexplore.exe | 185.226.160.27:80 | turkce-yama.com | — | — | unknown |
3156 | iexplore.exe | 151.139.128.14:80 | ocsp.usertrust.com | Highwinds Network Group, Inc. | US | suspicious |
3156 | iexplore.exe | 185.226.160.27:443 | turkce-yama.com | — | — | unknown |
3156 | iexplore.exe | 199.232.192.134:443 | turkce-yama.disqus.com | — | US | suspicious |
3156 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3156 | iexplore.exe | 64.233.166.157:443 | stats.g.doubleclick.net | Google Inc. | US | whitelisted |
2836 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3156 | iexplore.exe | 172.217.23.174:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
3156 | iexplore.exe | 216.58.206.3:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
3156 | iexplore.exe | 172.217.21.194:443 | googleads.g.doubleclick.net | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
turkce-yama.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.google-analytics.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
googleads.g.doubleclick.net |
| whitelisted |
turkce-yama.disqus.com |
| suspicious |