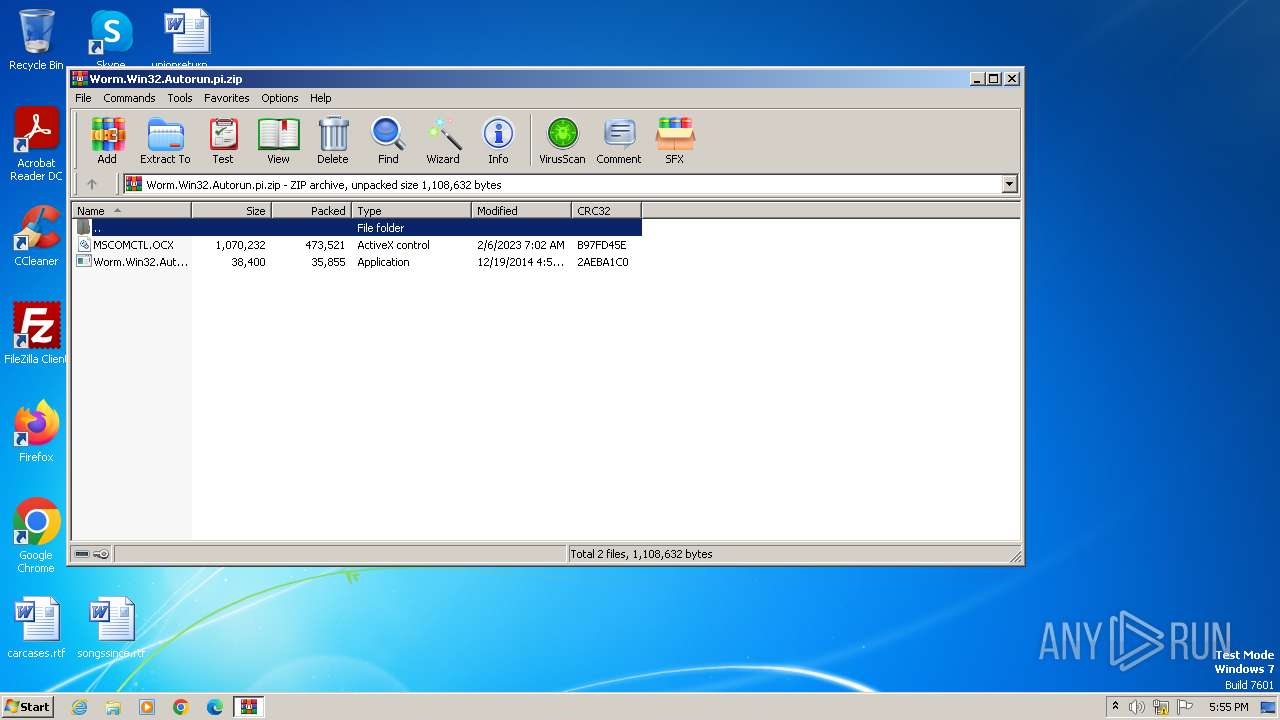
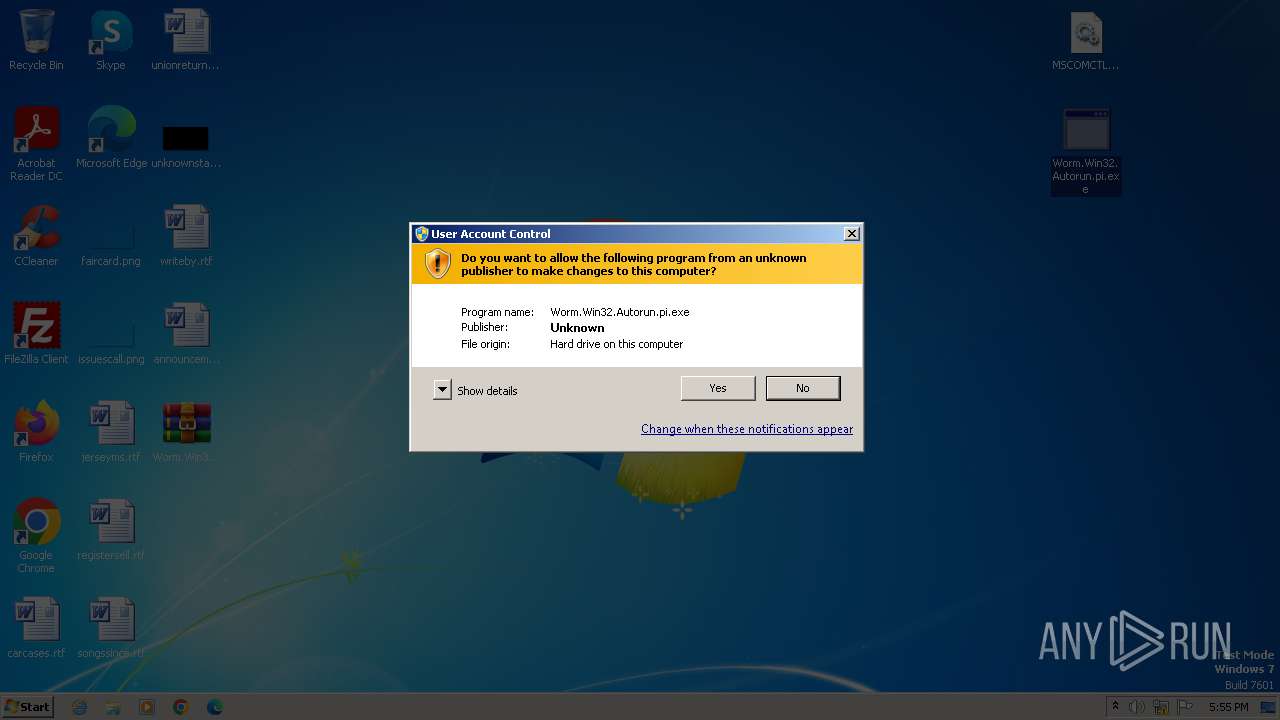
| File name: | Worm.Win32.Autorun.pi.zip |
| Full analysis: | https://app.any.run/tasks/d8b51d8d-8ace-4664-80d9-5647a9d2d5ed |
| Verdict: | Malicious activity |
| Analysis date: | December 04, 2023, 17:55:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 9A283DE90515D78F5523372412E0228E |
| SHA1: | 2EC1F4F55CB9D89EC3251F9636700056E27AED8A |
| SHA256: | 71FAA19A0FA3035460BD56AE7BE9F46C765A433F9666A8249CC6AD4712369942 |
| SSDEEP: | 24576:H9qVXua9jlQVTqLDvoCb0Em/xZRVTtkiVULnCh3Mh42Tymle7Bgn6A2HG2:HAVXua9jlQVTqLDoCQEmJZRVTtkiVULw |
MALICIOUS
Drops the executable file immediately after the start
- Worm.Win32.Autorun.pi.exe (PID: 1936)
- wisvf.exe (PID: 1608)
- adwya.exe (PID: 3112)
Creates a writable file in the system directory
- Worm.Win32.Autorun.pi.exe (PID: 1936)
- adwya.exe (PID: 3112)
Changes firewall settings
- Worm.Win32.Autorun.pi.exe (PID: 1936)
- wisvf.exe (PID: 1608)
- wlnoy.exe (PID: 3344)
- rkyjj.exe (PID: 1844)
- adwya.exe (PID: 3112)
- fzxxh.exe (PID: 2996)
- xczbz.exe (PID: 240)
Changes the autorun value in the registry
- wisvf.exe (PID: 1608)
- wlnoy.exe (PID: 3344)
- rkyjj.exe (PID: 1844)
- adwya.exe (PID: 3112)
- fzxxh.exe (PID: 2996)
- xczbz.exe (PID: 240)
- wlnoy.exe (PID: 2084)
- rkyjj.exe (PID: 2100)
- adwya.exe (PID: 2120)
- wisvf.exe (PID: 2064)
- xczbz.exe (PID: 2128)
- fzxxh.exe (PID: 2076)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 2412)
- Worm.Win32.Autorun.pi.exe (PID: 1936)
- wisvf.exe (PID: 1608)
- adwya.exe (PID: 3112)
Starts itself from another location
- Worm.Win32.Autorun.pi.exe (PID: 1936)
- wisvf.exe (PID: 1608)
- adwya.exe (PID: 3112)
The process executes via Task Scheduler
- sipnotify.exe (PID: 1704)
- ctfmon.exe (PID: 1612)
Reads the Internet Settings
- sipnotify.exe (PID: 1704)
Reads settings of System Certificates
- sipnotify.exe (PID: 1704)
INFO
Manual execution by a user
- Worm.Win32.Autorun.pi.exe (PID: 1936)
- IMEKLMG.EXE (PID: 2040)
- IMEKLMG.EXE (PID: 1068)
- wisvf.exe (PID: 2064)
- fzxxh.exe (PID: 2076)
- wlnoy.exe (PID: 2084)
- rkyjj.exe (PID: 2100)
- adwya.exe (PID: 2120)
- xczbz.exe (PID: 2128)
- wmpnscfg.exe (PID: 2364)
- wmpnscfg.exe (PID: 2408)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2412)
Reads Microsoft Office registry keys
- Worm.Win32.Autorun.pi.exe (PID: 1936)
- wisvf.exe (PID: 1608)
- adwya.exe (PID: 3112)
- wlnoy.exe (PID: 3344)
- rkyjj.exe (PID: 1844)
- fzxxh.exe (PID: 2996)
- xczbz.exe (PID: 240)
- fzxxh.exe (PID: 2076)
- wisvf.exe (PID: 2064)
- wlnoy.exe (PID: 2084)
- rkyjj.exe (PID: 2100)
- xczbz.exe (PID: 2128)
- adwya.exe (PID: 2120)
Create files in a temporary directory
- Worm.Win32.Autorun.pi.exe (PID: 1936)
- wisvf.exe (PID: 1608)
- adwya.exe (PID: 3112)
- wlnoy.exe (PID: 3344)
- rkyjj.exe (PID: 1844)
- fzxxh.exe (PID: 2996)
- xczbz.exe (PID: 240)
- wisvf.exe (PID: 2064)
- fzxxh.exe (PID: 2076)
- wlnoy.exe (PID: 2084)
- rkyjj.exe (PID: 2100)
- adwya.exe (PID: 2120)
- xczbz.exe (PID: 2128)
Reads mouse settings
- Worm.Win32.Autorun.pi.exe (PID: 1936)
- wisvf.exe (PID: 1608)
- adwya.exe (PID: 3112)
- wlnoy.exe (PID: 3344)
- rkyjj.exe (PID: 1844)
- fzxxh.exe (PID: 2996)
- xczbz.exe (PID: 240)
- xczbz.exe (PID: 2128)
- adwya.exe (PID: 2120)
- rkyjj.exe (PID: 2100)
- wlnoy.exe (PID: 2084)
- fzxxh.exe (PID: 2076)
- wisvf.exe (PID: 2064)
Checks supported languages
- wisvf.exe (PID: 1608)
- Worm.Win32.Autorun.pi.exe (PID: 1936)
- adwya.exe (PID: 3112)
- wlnoy.exe (PID: 3344)
- rkyjj.exe (PID: 1844)
- fzxxh.exe (PID: 2996)
- xczbz.exe (PID: 240)
- IMEKLMG.EXE (PID: 2040)
- IMEKLMG.EXE (PID: 1068)
- wisvf.exe (PID: 2064)
- fzxxh.exe (PID: 2076)
- wlnoy.exe (PID: 2084)
- rkyjj.exe (PID: 2100)
- adwya.exe (PID: 2120)
- xczbz.exe (PID: 2128)
- wmpnscfg.exe (PID: 2364)
- wmpnscfg.exe (PID: 2408)
Reads the machine GUID from the registry
- Worm.Win32.Autorun.pi.exe (PID: 1936)
- wisvf.exe (PID: 1608)
- adwya.exe (PID: 3112)
- wlnoy.exe (PID: 3344)
- rkyjj.exe (PID: 1844)
- fzxxh.exe (PID: 2996)
- xczbz.exe (PID: 240)
- wisvf.exe (PID: 2064)
- fzxxh.exe (PID: 2076)
- wlnoy.exe (PID: 2084)
- rkyjj.exe (PID: 2100)
- xczbz.exe (PID: 2128)
- adwya.exe (PID: 2120)
Creates files in the program directory
- Worm.Win32.Autorun.pi.exe (PID: 1936)
Reads the computer name
- wisvf.exe (PID: 1608)
- IMEKLMG.EXE (PID: 2040)
- IMEKLMG.EXE (PID: 1068)
- wisvf.exe (PID: 2064)
- wmpnscfg.exe (PID: 2364)
- wmpnscfg.exe (PID: 2408)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 1704)
Process checks are UAC notifies on
- IMEKLMG.EXE (PID: 2040)
- IMEKLMG.EXE (PID: 1068)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:02:06 01:02:44 |
| ZipCRC: | 0xb97fd45e |
| ZipCompressedSize: | 473521 |
| ZipUncompressedSize: | 1070232 |
| ZipFileName: | MSCOMCTL.OCX |
Total processes
102
Monitored processes
20
Malicious processes
14
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | c:\windows\system32\xczbz.exe | C:\Windows\System32\xczbz.exe | adwya.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: 5.2.3790.0 (srv03_rtm.030324-2048) Exit code: 1073807364 Version: 1.00.0019 Modules
| |||||||||||||||
| 1068 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 1608 | c:\windows\system32\wisvf.exe | C:\Windows\System32\wisvf.exe | Worm.Win32.Autorun.pi.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: 5.2.3790.0 (srv03_rtm.030324-2048) Exit code: 1073807364 Version: 1.00.0019 Modules
| |||||||||||||||
| 1612 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1704 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 1844 | "c:\program files\common files\rkyjj.exe" | C:\Program Files\common files\rkyjj.exe | Worm.Win32.Autorun.pi.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: 5.2.3790.0 (srv03_rtm.030324-2048) Exit code: 1073807364 Version: 1.00.0019 Modules
| |||||||||||||||
| 1936 | "C:\Users\admin\Desktop\Worm.Win32.Autorun.pi.exe" | C:\Users\admin\Desktop\Worm.Win32.Autorun.pi.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: 5.2.3790.0 (srv03_rtm.030324-2048) Exit code: 0 Version: 1.00.0019 Modules
| |||||||||||||||
| 2040 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2064 | "C:\Windows\System32\wisvf.exe" | C:\Windows\System32\wisvf.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: 5.2.3790.0 (srv03_rtm.030324-2048) Exit code: 0 Version: 1.00.0019 Modules
| |||||||||||||||
| 2076 | "C:\Windows\system\fzxxh.exe" | C:\Windows\system\fzxxh.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: 5.2.3790.0 (srv03_rtm.030324-2048) Exit code: 0 Version: 1.00.0019 Modules
| |||||||||||||||
Total events
20 787
Read events
20 663
Write events
124
Delete events
0
Modification events
| (PID) Process: | (2412) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
8
Suspicious files
8
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1936 | Worm.Win32.Autorun.pi.exe | C:\windows\inf\adwya.exe | executable | |
MD5:BEE2D7595B1A0E7F6B03585226B37AE7 | SHA256:A1B86391CFA945BB5BBFD0C8A3EA8B66CFD78194A5DA175B86CF6827534DA915 | |||
| 2412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2412.2282\MSCOMCTL.OCX | executable | |
MD5:273676426739B02A45A0FC9349500B65 | SHA256:152121A5D1AC8F12002C18AFC294BB1EBCECC1D61DEEC6211DF586C11ACDE9B6 | |||
| 1936 | Worm.Win32.Autorun.pi.exe | C:\windows\system32\wisvf.exe | executable | |
MD5:BEE2D7595B1A0E7F6B03585226B37AE7 | SHA256:A1B86391CFA945BB5BBFD0C8A3EA8B66CFD78194A5DA175B86CF6827534DA915 | |||
| 3112 | adwya.exe | C:\windows\system32\xczbz.exe | executable | |
MD5:BEE2D7595B1A0E7F6B03585226B37AE7 | SHA256:A1B86391CFA945BB5BBFD0C8A3EA8B66CFD78194A5DA175B86CF6827534DA915 | |||
| 1608 | wisvf.exe | C:\windows\system32\Restore\04122023.kp_ | text | |
MD5:C77067E60345FF6383002AF85704816D | SHA256:251FB8F223A39EFF61094F69BB94E8A06A1756551EA051185135C3A1DF3DF4FF | |||
| 240 | xczbz.exe | C:\Users\admin\AppData\Local\Temp\~DFD7F75F8EC21BAC70.TMP | binary | |
MD5:DD87748AD723F4AA899EC6C375855A6C | SHA256:1E2054F6F258B804A93D934D8AC4BC178D01680DC3D5D341F5AB8A51648B6332 | |||
| 2996 | fzxxh.exe | C:\Users\admin\AppData\Local\Temp\~DF2E73A1FED3A3AC06.TMP | binary | |
MD5:DD87748AD723F4AA899EC6C375855A6C | SHA256:1E2054F6F258B804A93D934D8AC4BC178D01680DC3D5D341F5AB8A51648B6332 | |||
| 1608 | wisvf.exe | C:\windows\wlnoy.exe | executable | |
MD5:BEE2D7595B1A0E7F6B03585226B37AE7 | SHA256:A1B86391CFA945BB5BBFD0C8A3EA8B66CFD78194A5DA175B86CF6827534DA915 | |||
| 1844 | rkyjj.exe | C:\Users\admin\AppData\Local\Temp\~DF8C115B6D45078621.TMP | binary | |
MD5:DD87748AD723F4AA899EC6C375855A6C | SHA256:1E2054F6F258B804A93D934D8AC4BC178D01680DC3D5D341F5AB8A51648B6332 | |||
| 1936 | Worm.Win32.Autorun.pi.exe | C:\Users\admin\AppData\Local\Temp\~DF142A8D242BBCA6B6.TMP | binary | |
MD5:2161A3FFBEBB81CFF21DA7A7E5CBB945 | SHA256:6F1FF0A6A3136AC836A583810DE4F731D6468AE9AACF8B1B393740733915A0DD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
8
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1704 | sipnotify.exe | HEAD | 200 | 104.102.39.173:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133461862032650000 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1704 | sipnotify.exe | 104.102.39.173:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | DE | unknown |
1116 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
query.prod.cms.rt.microsoft.com |
| whitelisted |