| File name: | ZeroAccess_xxx-porn-movie.avi.exe_ |
| Full analysis: | https://app.any.run/tasks/3a3dbe6d-00d2-4213-8c70-2bdf1a04b84d |
| Verdict: | Malicious activity |
| Analysis date: | June 08, 2025, 23:18:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, 4 sections |
| MD5: | A2611095F689FADFFD3068E0D4E3E7ED |
| SHA1: | 6D21FC25B9DA49D746B2B7609A5EFAED4D332E6A |
| SHA256: | 71B38F041B4A4AE169C44E3AFF412E527E1156F92C27F1340A8ABE70A45BEE10 |
| SSDEEP: | 6144:3yL9TAhWmj1HqIH835CbffrVzNZv8XDCY18LfRgM:5suKIH83wbffr5NZ0XBEfRg |
MALICIOUS
ZEROACCESS mutex has been found
- ZeroAccess_xxx-porn-movie.avi.exe_.exe (PID: 4428)
- InstallFlashPlayer.exe (PID: 6584)
ZEROACCESS has been detected
- ZeroAccess_xxx-porn-movie.avi.exe_.exe (PID: 4428)
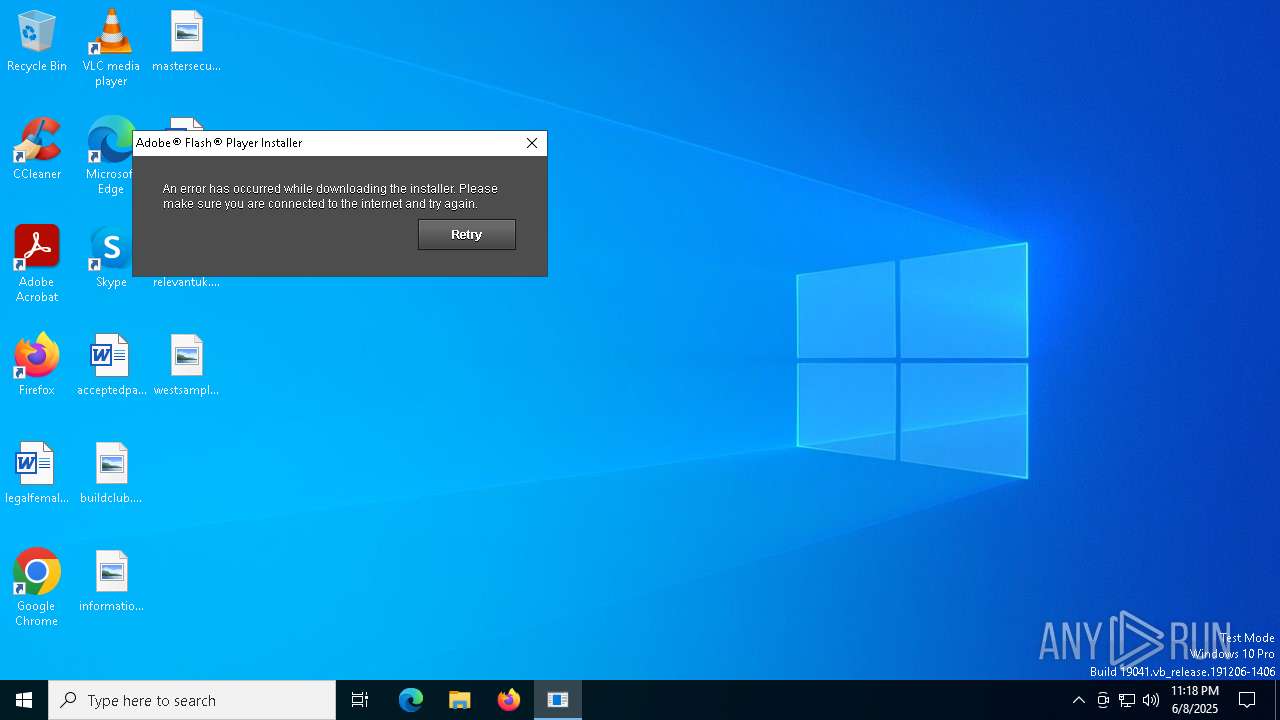
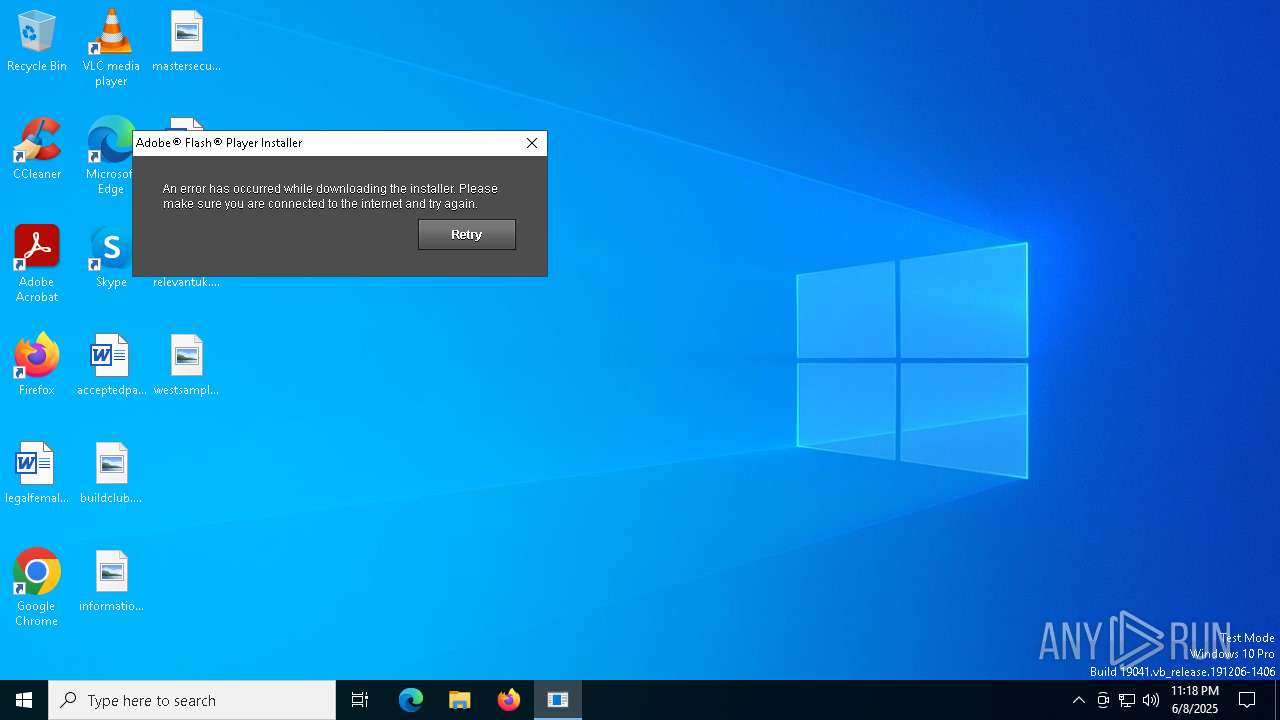
Executing a file with an untrusted certificate
- InstallFlashPlayer.exe (PID: 6584)
ZEROACCESS has been detected (SURICATA)
- ZeroAccess_xxx-porn-movie.avi.exe_.exe (PID: 4428)
- InstallFlashPlayer.exe (PID: 6584)
SUSPICIOUS
Executable content was dropped or overwritten
- ZeroAccess_xxx-porn-movie.avi.exe_.exe (PID: 4428)
Reads the date of Windows installation
- ZeroAccess_xxx-porn-movie.avi.exe_.exe (PID: 4428)
Reads security settings of Internet Explorer
- ZeroAccess_xxx-porn-movie.avi.exe_.exe (PID: 4428)
- InstallFlashPlayer.exe (PID: 6584)
Creates/Modifies COM task schedule object
- ZeroAccess_xxx-porn-movie.avi.exe_.exe (PID: 4428)
There is functionality for taking screenshot (YARA)
- InstallFlashPlayer.exe (PID: 6584)
Starts CMD.EXE for commands execution
- ZeroAccess_xxx-porn-movie.avi.exe_.exe (PID: 4428)
There is functionality for lookup Geolocation (YARA)
- InstallFlashPlayer.exe (PID: 6584)
INFO
Reads the computer name
- ZeroAccess_xxx-porn-movie.avi.exe_.exe (PID: 4428)
- InstallFlashPlayer.exe (PID: 6584)
Reads the machine GUID from the registry
- ZeroAccess_xxx-porn-movie.avi.exe_.exe (PID: 4428)
Checks supported languages
- ZeroAccess_xxx-porn-movie.avi.exe_.exe (PID: 4428)
- InstallFlashPlayer.exe (PID: 6584)
Process checks computer location settings
- ZeroAccess_xxx-porn-movie.avi.exe_.exe (PID: 4428)
The sample compiled with english language support
- ZeroAccess_xxx-porn-movie.avi.exe_.exe (PID: 4428)
Reads the software policy settings
- slui.exe (PID: 5588)
Checks proxy server information
- InstallFlashPlayer.exe (PID: 6584)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
| .vxd | | | VXD Driver (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2004:04:29 03:00:54+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, 32-bit, No debug, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 150706 |
| InitializedDataSize: | - |
| UninitializedDataSize: | 4096 |
| EntryPoint: | 0x3515 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Total processes
135
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1672 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\SysWOW64\cmd.exe | — | ZeroAccess_xxx-porn-movie.avi.exe_.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 4294967295 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2600 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4428 | "C:\Users\admin\AppData\Local\Temp\ZeroAccess_xxx-porn-movie.avi.exe_.exe" | C:\Users\admin\AppData\Local\Temp\ZeroAccess_xxx-porn-movie.avi.exe_.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5588 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
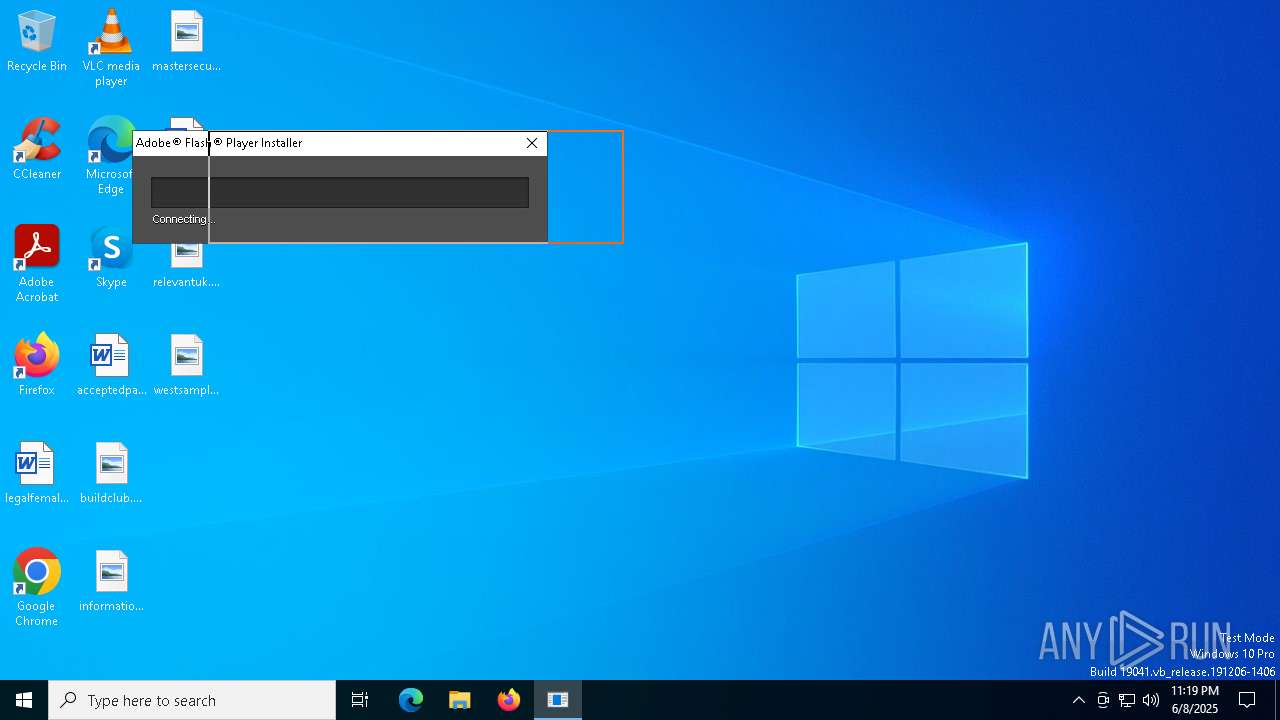
| 6584 | "C:\Users\admin\AppData\Local\Temp\InstallFlashPlayer.exe" | C:\Users\admin\AppData\Local\Temp\InstallFlashPlayer.exe | ZeroAccess_xxx-porn-movie.avi.exe_.exe | ||||||||||||
User: admin Company: Adobe Systems, Inc. Integrity Level: HIGH Description: Adobe® Flash® Player Installer/Uninstaller 11.0 r1 Version: 11,0,1,152 Modules
| |||||||||||||||
| 6980 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7200 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 738
Read events
2 724
Write events
14
Delete events
0
Modification events
| (PID) Process: | (4428) ZeroAccess_xxx-porn-movie.avi.exe_.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 461A466800000000 | |||
| (PID) Process: | (4428) ZeroAccess_xxx-porn-movie.avi.exe_.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (4428) ZeroAccess_xxx-porn-movie.avi.exe_.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4428) ZeroAccess_xxx-porn-movie.avi.exe_.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4428) ZeroAccess_xxx-porn-movie.avi.exe_.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4428) ZeroAccess_xxx-porn-movie.avi.exe_.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4428) ZeroAccess_xxx-porn-movie.avi.exe_.exe | Key: | HKEY_CLASSES_ROOT\CLSID\{fbeb8a05-beee-4442-804e-409d6c4515e9}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Both | |||
| (PID) Process: | (6584) InstallFlashPlayer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6584) InstallFlashPlayer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6584) InstallFlashPlayer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
3
Suspicious files
1
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4428 | ZeroAccess_xxx-porn-movie.avi.exe_.exe | C:\$Recycle.Bin\S-1-5-21-1693682860-607145093-2874071422-1001\$81b8c3da9d80cef97346aaa39584b477\@ | binary | |
MD5:B16232FD25A39108E432291828ED2A6E | SHA256:855341B28C2A0B63D0F99335F0857B133EFC8C0A0811CF562C8B8366025ED6B5 | |||
| 4428 | ZeroAccess_xxx-porn-movie.avi.exe_.exe | C:\Users\admin\AppData\Local\Temp\msimg32.dll | executable | |
MD5:D6F7C05386CAA9ABFF7CBF41D6C51470 | SHA256:67FAD3B5C42794783EC3757AE5CB6F1A06F5B76214C1CC967108DFE84F76626C | |||
| 4428 | ZeroAccess_xxx-porn-movie.avi.exe_.exe | C:\Users\admin\AppData\Local\Temp\InstallFlashPlayer.exe | executable | |
MD5:2FF9B590342C62748885D459D082295F | SHA256:672EC8DCEAFD429C1A09CFAFBC4951968953E2081E0D97243040DB16EDB24429 | |||
| 4428 | ZeroAccess_xxx-porn-movie.avi.exe_.exe | C:\$Recycle.Bin\S-1-5-21-1693682860-607145093-2874071422-1001\$81b8c3da9d80cef97346aaa39584b477\n | executable | |
MD5:9E0CD37B6D0809CF7D5FA5B521538D0D | SHA256:55D9748F0556576A8D522CF4B8DCFC9717436ADCC487D49B3320770432960DB2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
49
DNS requests
17
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6584 | InstallFlashPlayer.exe | GET | 404 | 104.102.57.130:80 | http://fpdownload.macromedia.com/get/flashplayer/update/current/install/install_all_win_cab_64_ax_sgn.z | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6584 | InstallFlashPlayer.exe | GET | 404 | 104.102.57.130:80 | http://fpdownload.macromedia.com/get/flashplayer/update/current/install/install_all_win_cab_64_ax_sgn.z | unknown | — | — | whitelisted |
5036 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5036 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
7556 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4428 | ZeroAccess_xxx-porn-movie.avi.exe_.exe | 66.85.130.234:53 | — | — | — | malicious |
4428 | ZeroAccess_xxx-porn-movie.avi.exe_.exe | 194.165.17.3:53 | — | — | — | malicious |
6584 | InstallFlashPlayer.exe | 194.165.17.3:53 | — | — | — | malicious |
6584 | InstallFlashPlayer.exe | 66.85.130.234:53 | — | — | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
j.maxmind.com |
| shared |
fpdownload.macromedia.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4428 | ZeroAccess_xxx-porn-movie.avi.exe_.exe | A Network Trojan was detected | ET MALWARE ZeroAccess udp traffic detected |
4428 | ZeroAccess_xxx-porn-movie.avi.exe_.exe | A Network Trojan was detected | ET MALWARE ZeroAccess udp traffic detected |
4428 | ZeroAccess_xxx-porn-movie.avi.exe_.exe | A Network Trojan was detected | ET MALWARE ZeroAccess udp traffic detected |
4428 | ZeroAccess_xxx-porn-movie.avi.exe_.exe | A Network Trojan was detected | ET MALWARE ZeroAccess udp traffic detected |
4428 | ZeroAccess_xxx-porn-movie.avi.exe_.exe | A Network Trojan was detected | ET MALWARE ZeroAccess udp traffic detected |
4428 | ZeroAccess_xxx-porn-movie.avi.exe_.exe | A Network Trojan was detected | ET MALWARE ZeroAccess udp traffic detected |
4428 | ZeroAccess_xxx-porn-movie.avi.exe_.exe | A Network Trojan was detected | ET MALWARE ZeroAccess udp traffic detected |
4428 | ZeroAccess_xxx-porn-movie.avi.exe_.exe | A Network Trojan was detected | ET MALWARE ZeroAccess udp traffic detected |
4428 | ZeroAccess_xxx-porn-movie.avi.exe_.exe | A Network Trojan was detected | ET MALWARE ZeroAccess udp traffic detected |
4428 | ZeroAccess_xxx-porn-movie.avi.exe_.exe | A Network Trojan was detected | ET MALWARE ZeroAccess udp traffic detected |