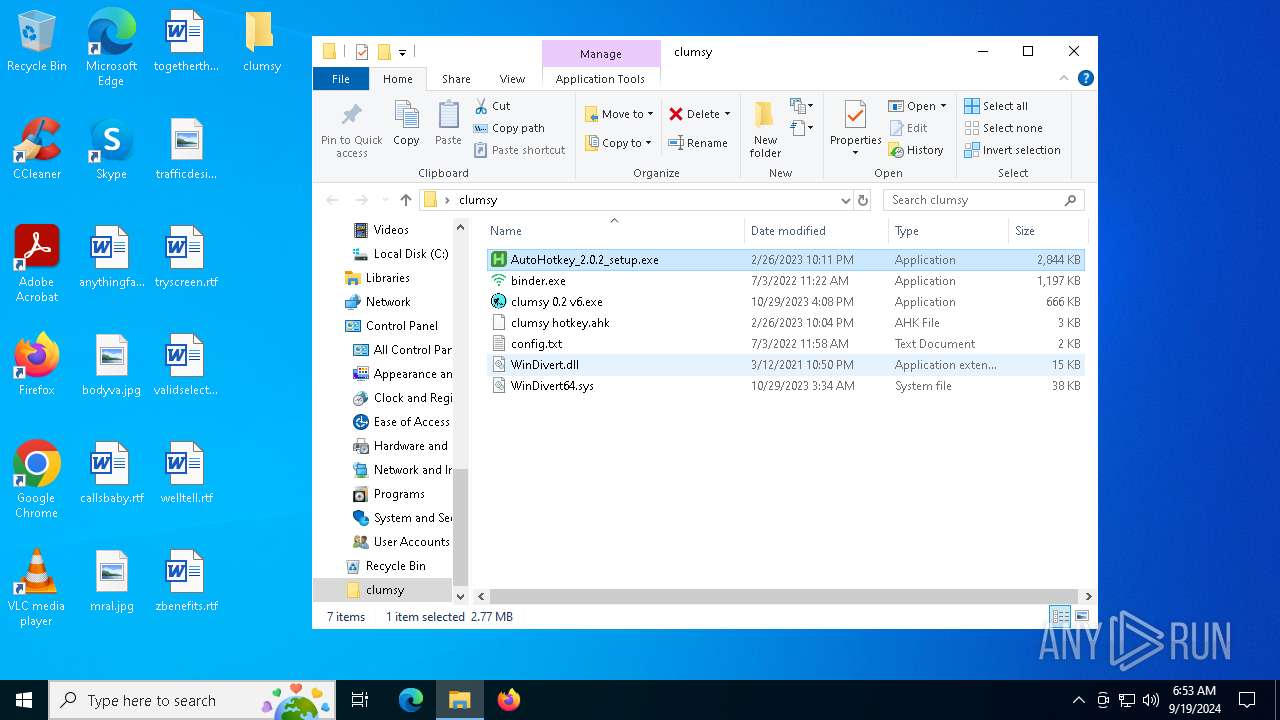
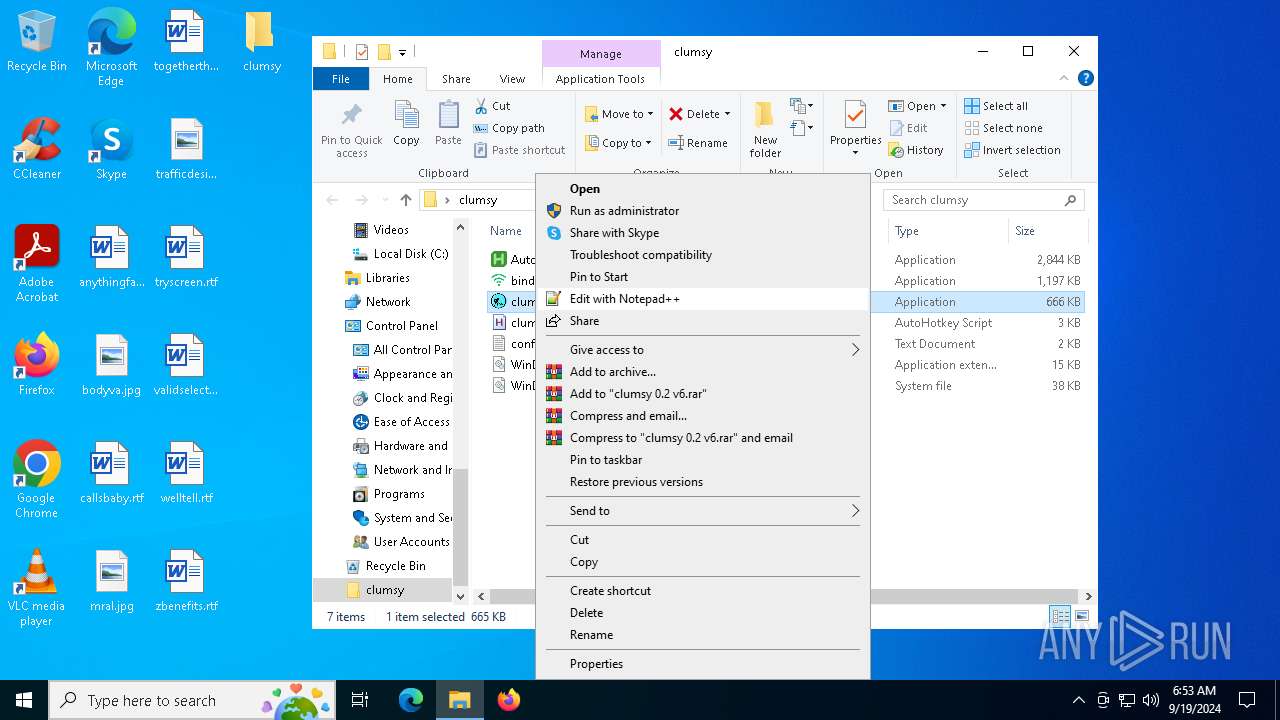
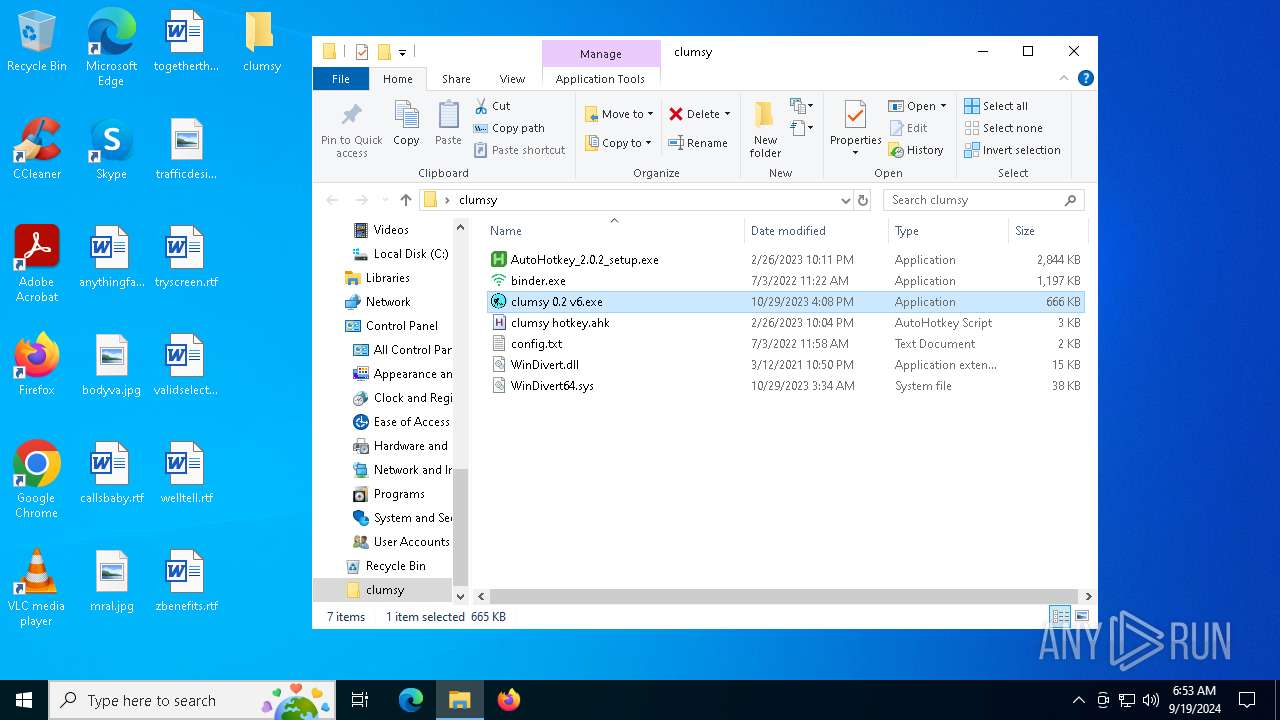
| File name: | clumsy.zip |
| Full analysis: | https://app.any.run/tasks/ff1ee773-14cc-4916-9749-8141f5b51737 |
| Verdict: | Malicious activity |
| Analysis date: | September 19, 2024, 06:52:37 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 4540076E0AAFAD3E9BE704E805FB05E0 |
| SHA1: | BCBBD6A2DF76AE3093784A77EB00B79C781ABD4D |
| SHA256: | 718D0C897FF489C2EA06346A5E38EBD3BAE844A32FB17E4E0179AE4106AA8D7E |
| SSDEEP: | 98304:FdAuqKbEn8KnJX/PUIju2MT/jFO40e0tAlJXJGF4KGSRjNuAwJvX5qOUtMGSG4XT:seJJYyziaIo |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
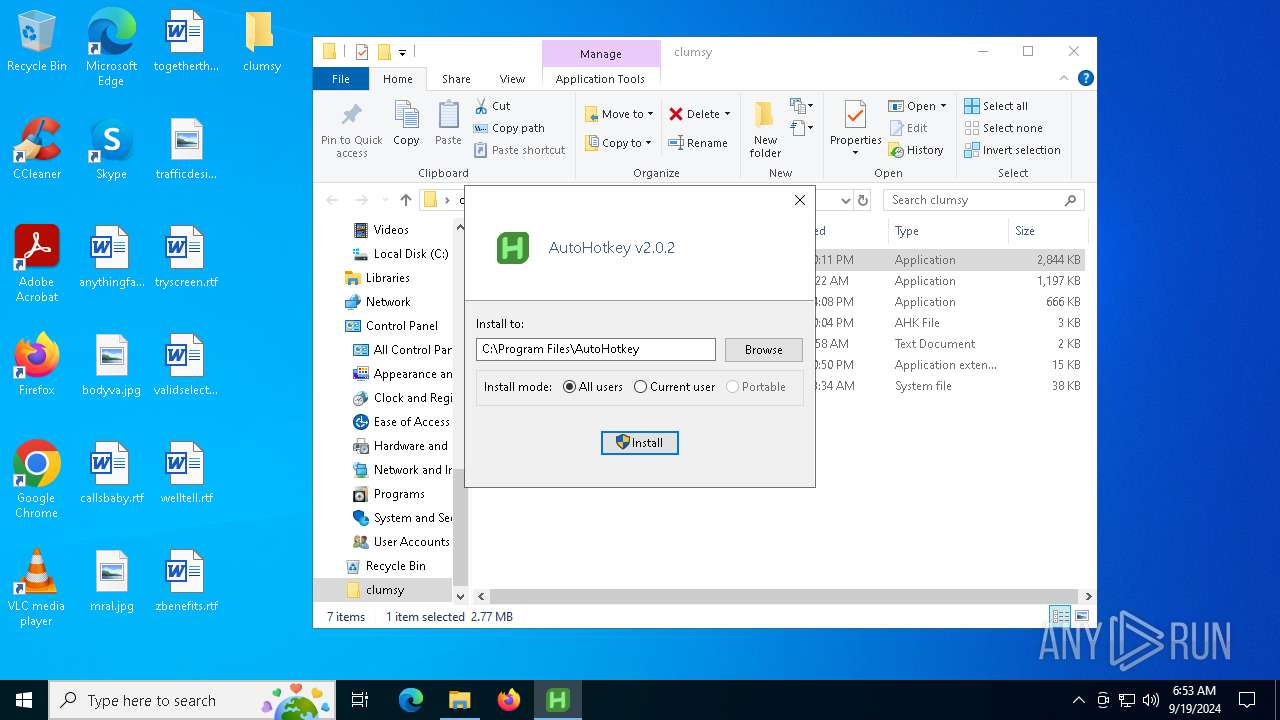
- AutoHotkey_2.0.2_setup.exe (PID: 5388)
- binder.exe (PID: 2960)
- AutoHotkeyUX.exe (PID: 7016)
- AutoHotkeyUX.exe (PID: 6308)
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 6500)
Executable content was dropped or overwritten
- AutoHotkey_2.0.2_setup.exe (PID: 6424)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6500)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:02:26 22:11:28 |
| ZipCRC: | 0x09dfb7f3 |
| ZipCompressedSize: | 2889093 |
| ZipUncompressedSize: | 2912256 |
| ZipFileName: | clumsy/AutoHotkey_2.0.2_setup.exe |
Total processes
160
Monitored processes
20
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1680 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2660 | "C:\Users\admin\Desktop\clumsy\binder.exe" | C:\Users\admin\Desktop\clumsy\binder.exe | binder.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.1.34.03 Modules
| |||||||||||||||
| 2960 | "C:\Users\admin\Desktop\clumsy\binder.exe" | C:\Users\admin\Desktop\clumsy\binder.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.1.34.03 Modules
| |||||||||||||||
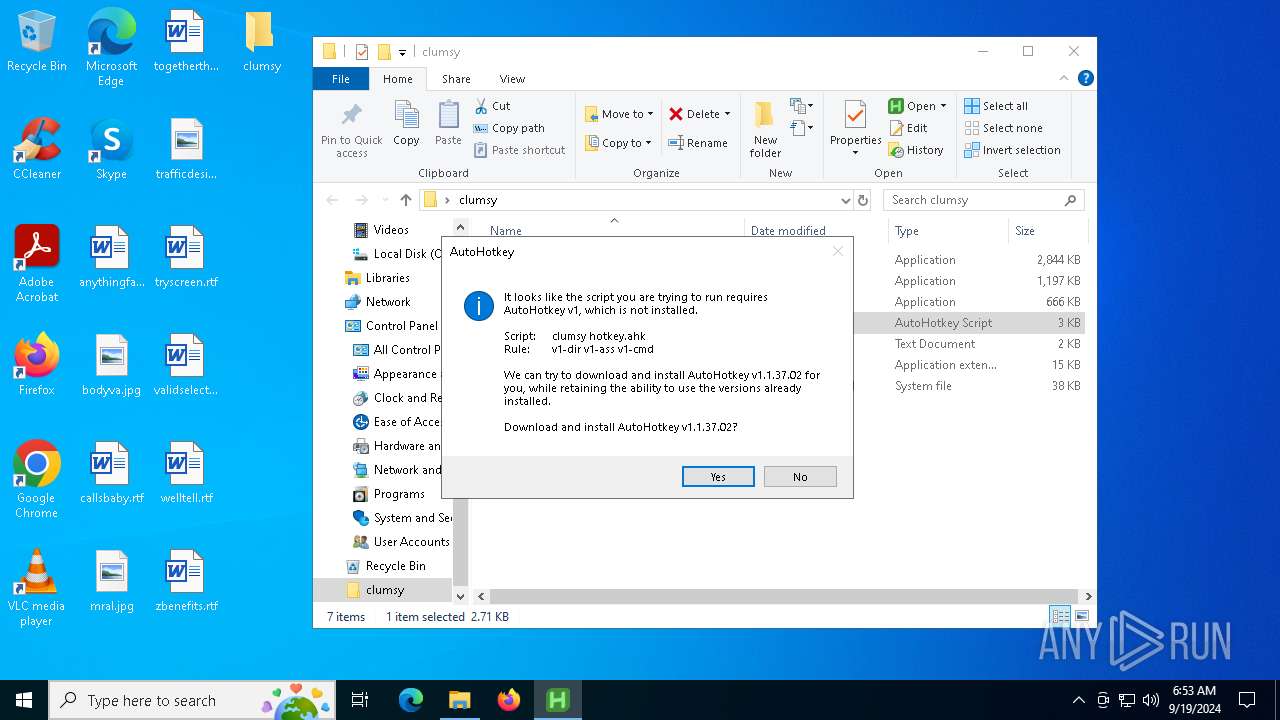
| 3076 | "C:\Program Files\AutoHotkey\UX\AutoHotkeyUX.exe" /force /script "C:\Program Files\AutoHotkey\UX\install-version.ahk" 1.1.37.02 /Y | C:\Program Files\AutoHotkey\UX\AutoHotkeyUX.exe | AutoHotkeyUX.exe | ||||||||||||
User: admin Company: AutoHotkey Foundation LLC Integrity Level: HIGH Description: AutoHotkey 64-bit Exit code: 0 Version: 2.0.2 Modules
| |||||||||||||||
| 5160 | "C:\Users\admin\Desktop\clumsy\clumsy 0.2 v6.exe" | C:\Users\admin\Desktop\clumsy\clumsy 0.2 v6.exe | explorer.exe | ||||||||||||
User: admin Company: Nishant Sivakumar Integrity Level: HIGH Description: TypeDescriptionProviderDemo Exit code: 3762504530 Version: 5.66.0.7716 Modules
| |||||||||||||||
| 5388 | "C:\Users\admin\Desktop\clumsy\AutoHotkey_2.0.2_setup.exe" | C:\Users\admin\Desktop\clumsy\AutoHotkey_2.0.2_setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: AutoHotkey installer Exit code: 0 Version: 2.0.2 Modules
| |||||||||||||||
| 5768 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6188 -s 1004 | C:\Windows\SysWOW64\WerFault.exe | clumsy 0.2 v6.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6188 | "C:\Users\admin\Desktop\clumsy\clumsy 0.2 v6.exe" | C:\Users\admin\Desktop\clumsy\clumsy 0.2 v6.exe | explorer.exe | ||||||||||||
User: admin Company: Nishant Sivakumar Integrity Level: MEDIUM Description: TypeDescriptionProviderDemo Exit code: 3762504530 Version: 5.66.0.7716 Modules
| |||||||||||||||
| 6308 | "C:\Program Files\AutoHotkey\UX\AutoHotkeyUX.exe" "C:\Program Files\AutoHotkey\UX\launcher.ahk" "C:\Users\admin\Desktop\clumsy\clumsy hotkey.ahk" | C:\Program Files\AutoHotkey\UX\AutoHotkeyUX.exe | explorer.exe | ||||||||||||
User: admin Company: AutoHotkey Foundation LLC Integrity Level: MEDIUM Description: AutoHotkey 64-bit Exit code: 2 Version: 2.0.2 Modules
| |||||||||||||||
| 6424 | "C:\Users\admin\Desktop\clumsy\AutoHotkey_2.0.2_setup.exe" /to "C:\Program Files\AutoHotkey" | C:\Users\admin\Desktop\clumsy\AutoHotkey_2.0.2_setup.exe | AutoHotkey_2.0.2_setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: AutoHotkey installer Exit code: 0 Version: 2.0.2 Modules
| |||||||||||||||
Total events
21 521
Read events
21 455
Write events
56
Delete events
10
Modification events
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\clumsy.zip | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
16
Suspicious files
10
Text files
72
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6928 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_clumsy 0.2 v6.ex_d0c622f89c48c7d52807d6830e2541dc492808_7c56091b_bbdb934b-2eca-4ece-9424-d65c5c782c7c\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6928 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\clumsy 0.2 v6.exe.7000.dmp | — | |
MD5:— | SHA256:— | |||
| 6928 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERE9DC.tmp.dmp | dmp | |
MD5:6771D69015DED911228BFDCCF18692AB | SHA256:3D3C5F5DAA6EF252373662836C2FEC3E56BFD7B55F2BD8345ABBBB7CE752A3EF | |||
| 6500 | WinRAR.exe | C:\Users\admin\Desktop\clumsy\WinDivert64.sys | executable | |
MD5:3BD5AC2E9D96E680F5DBDD183A58C47D | SHA256:208C092FE77F161C5A313B916D73FA7F6D10DD289BAB8BB5DFB3D59AACB27F25 | |||
| 6500 | WinRAR.exe | C:\Users\admin\Desktop\clumsy\clumsy hotkey.ahk | text | |
MD5:76E8A1857CF727EC994B44ADF506F916 | SHA256:F185BF19DC42B6306FD9E591CFE69AD5C5FDE719144A04291BE2756B6CFA8698 | |||
| 6500 | WinRAR.exe | C:\Users\admin\Desktop\clumsy\clumsy 0.2 v6.exe | executable | |
MD5:FA80399205E0CF1DABD46A1DFD5A66DD | SHA256:C9417BF78D6D3DB7915EC9FCFD5770FD6D3C86A8A86B1EE1D5775E3F72890C1A | |||
| 6928 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WEREB26.tmp.xml | xml | |
MD5:FD87A9709269C0028C90C7DA3F55BA07 | SHA256:D351866E452316087EE390AC961C0074F6F72C6C329AC2C67041A95FD99CB409 | |||
| 6500 | WinRAR.exe | C:\Users\admin\Desktop\clumsy\WinDivert.dll | executable | |
MD5:1B1284100327D972E017F565DBECF80E | SHA256:9444A6E6B66F13F666F9C60D1935824F61C7256E35A8CF0440E29BAA7FBE42C7 | |||
| 6928 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WEREAE7.tmp.WERInternalMetadata.xml | xml | |
MD5:CBD22707996C817CD50832FE225500E2 | SHA256:8AE8A0F68BC94E579428BF0207B43AF67F1F8965B7964541A16696D50B268A04 | |||
| 6928 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:FB64A9EBEDF48D3895381D5B7D80743D | SHA256:EA21D495930AD76F267A33A0F593DBF0C7EA75E457FCAE49A29DAAD8BD920F42 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
49
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
32 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6928 | WerFault.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6204 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6352 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6308 | AutoHotkeyUX.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6352 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
32 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1776 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.79.141.152:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | FR | unknown |
— | — | 104.126.37.147:443 | — | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
32 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
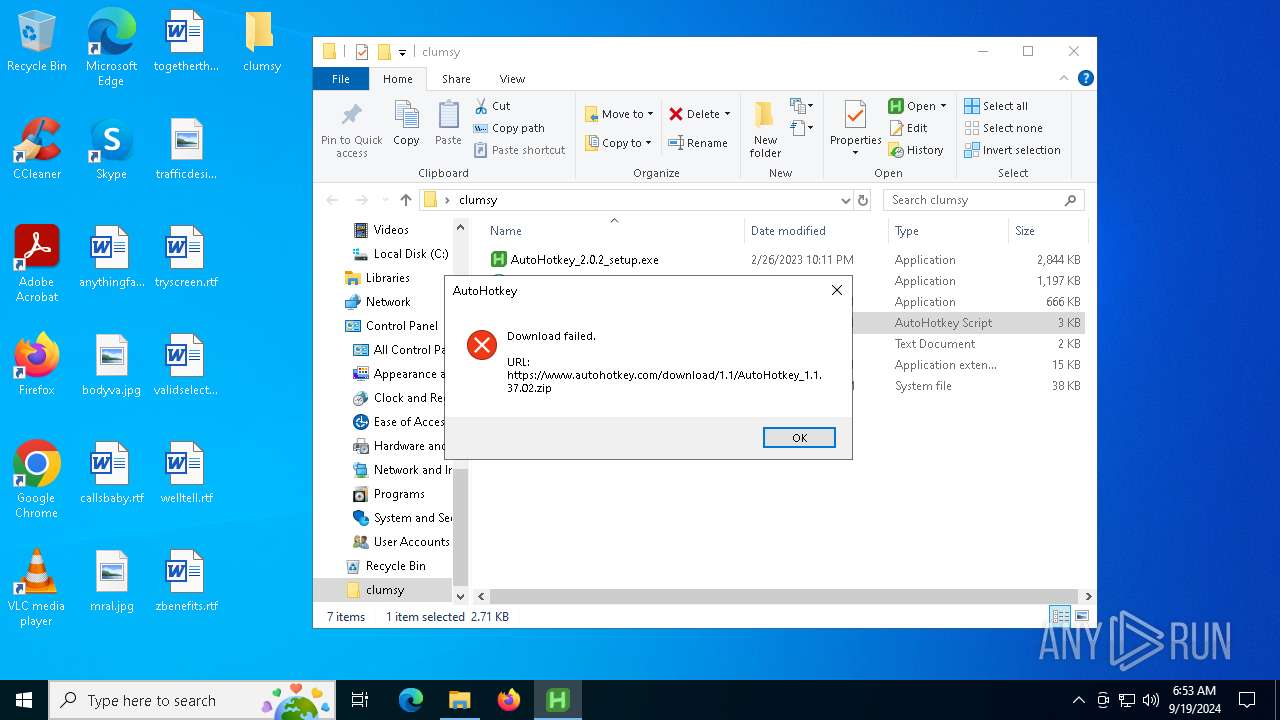
www.autohotkey.com |
| whitelisted |