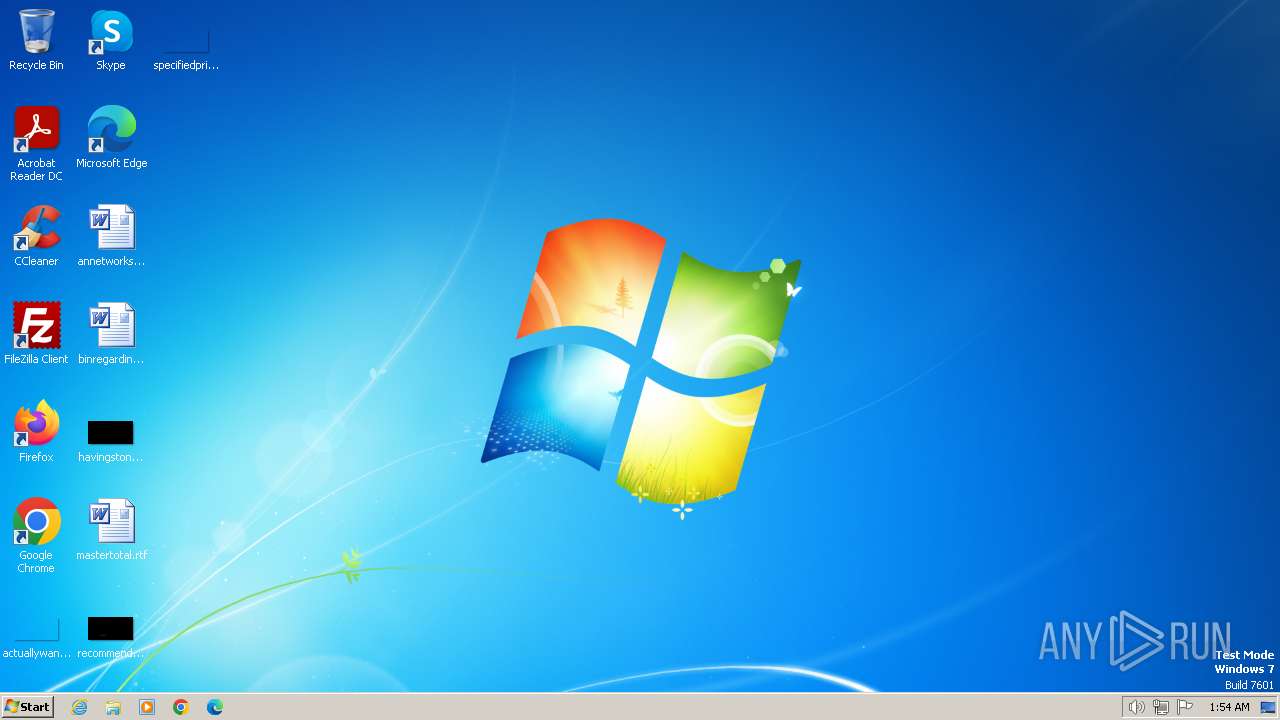
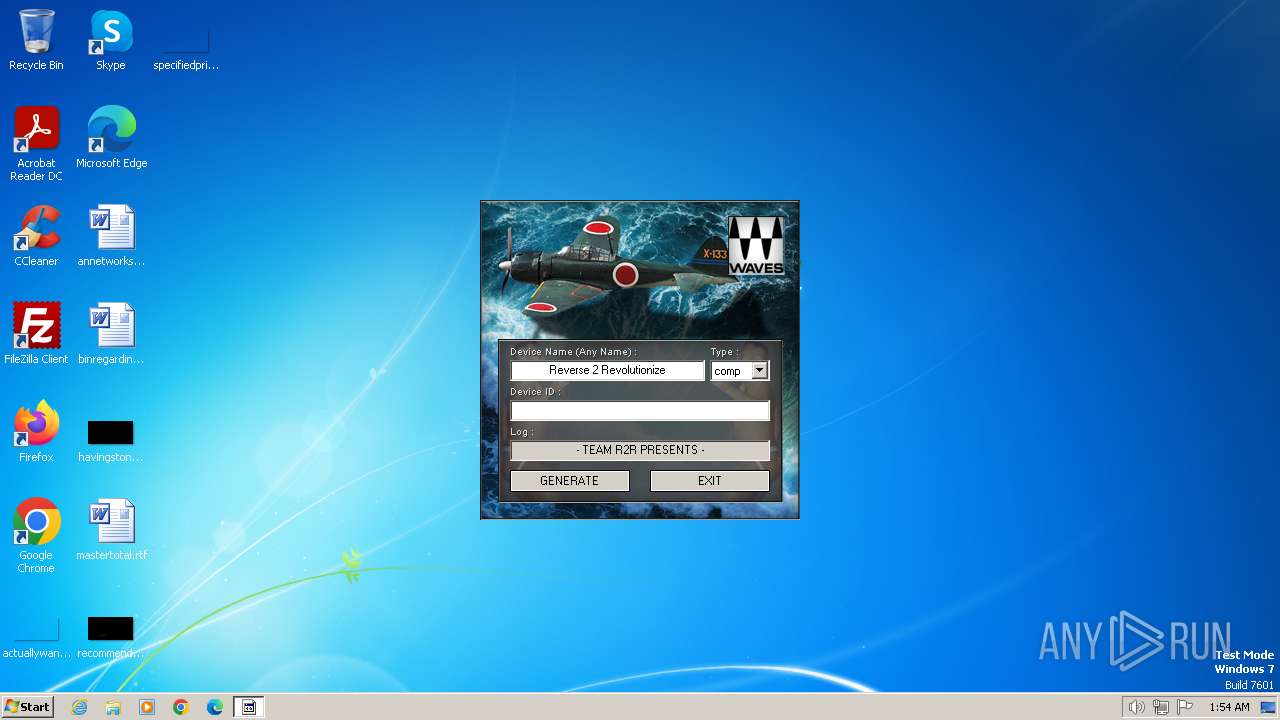
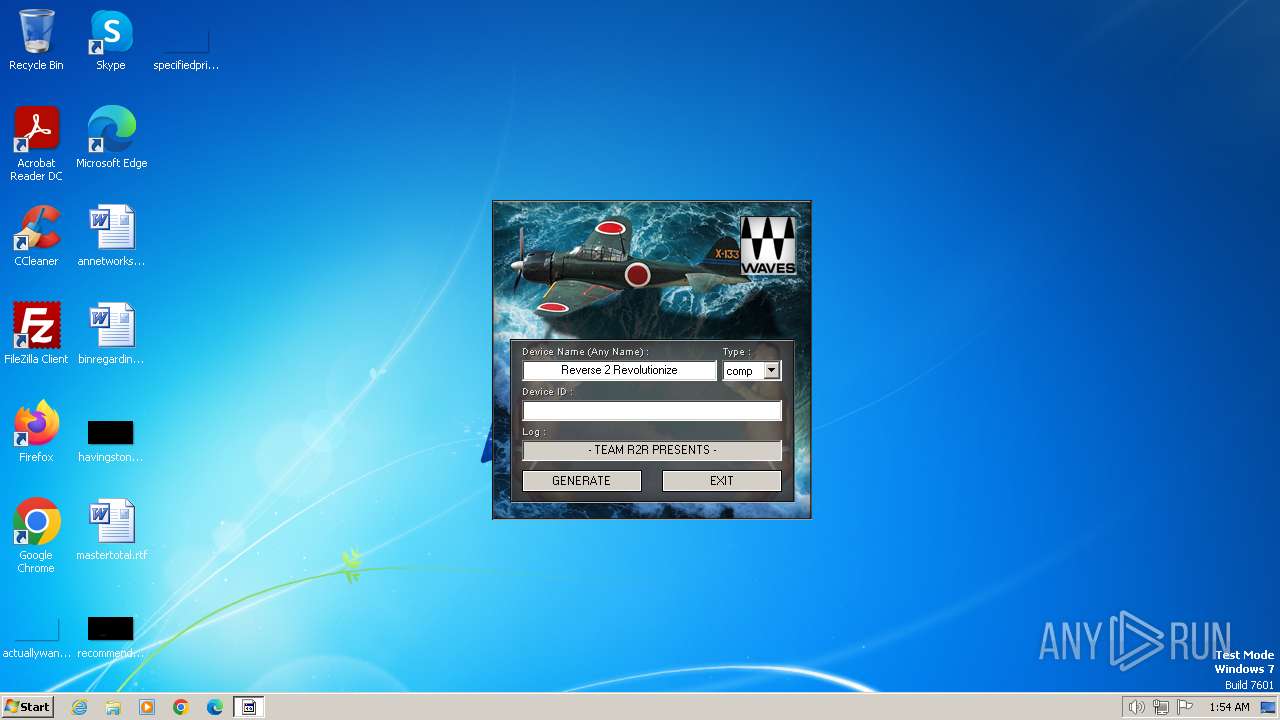
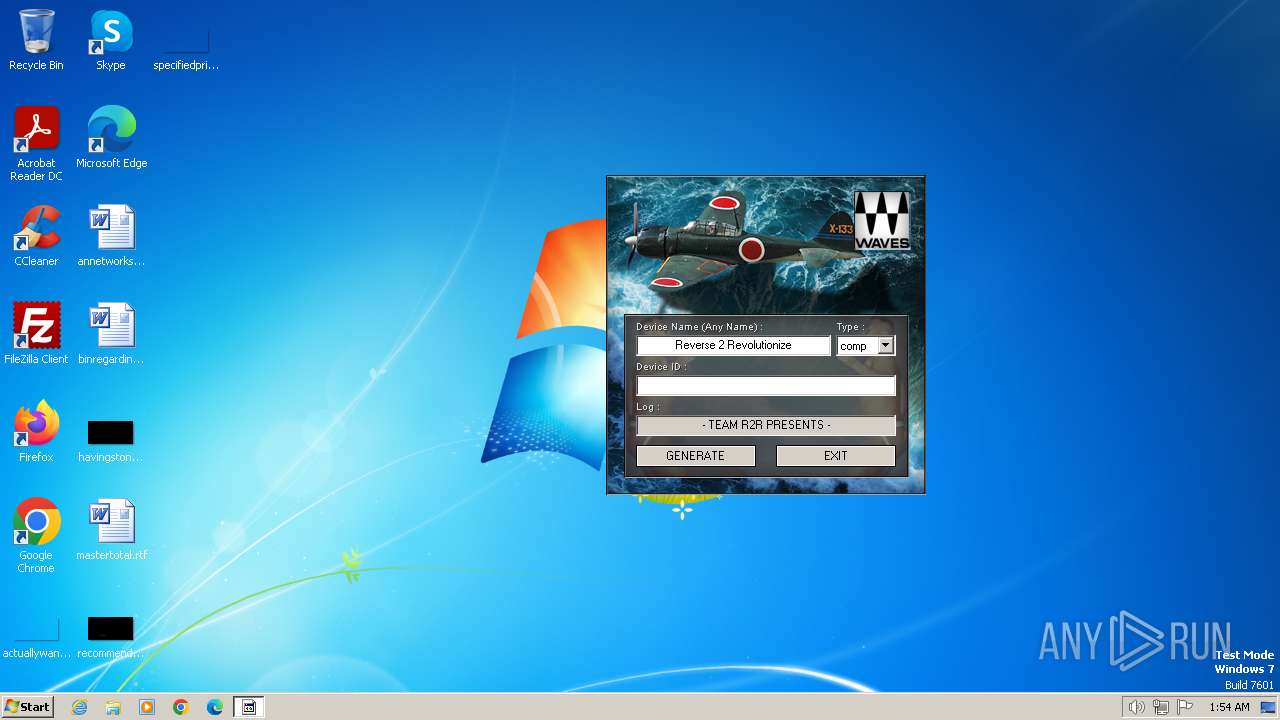
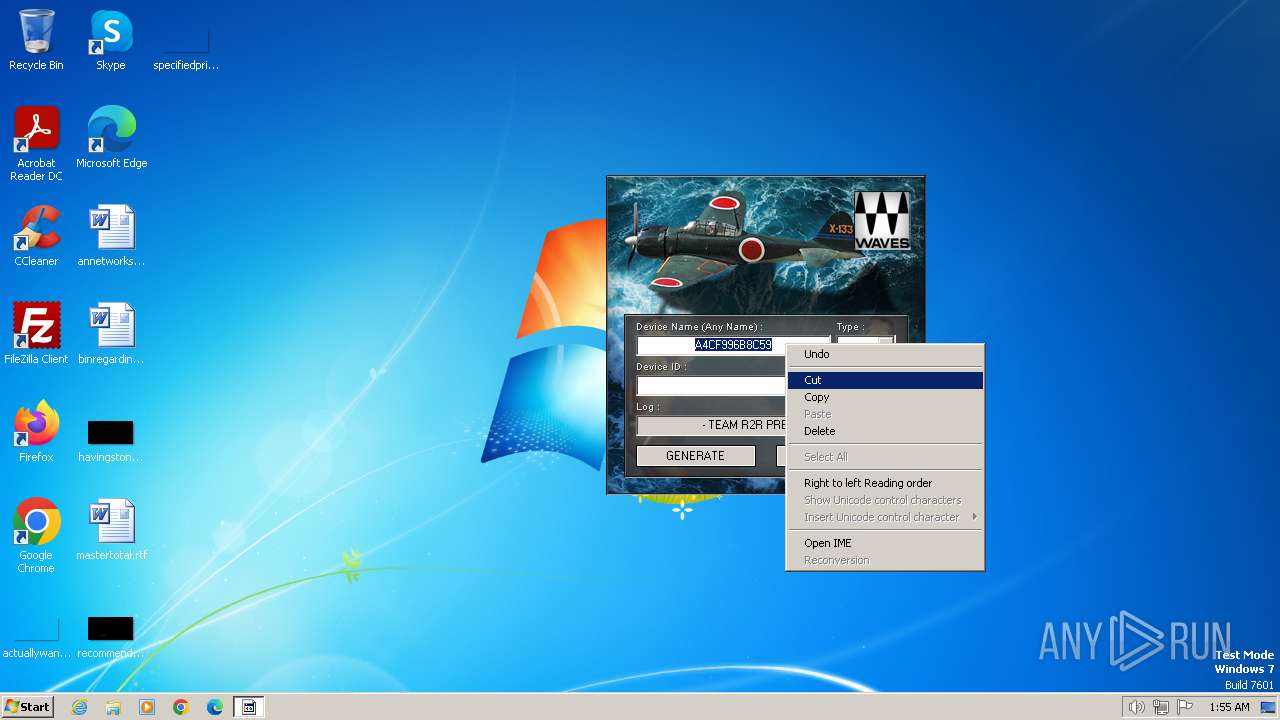
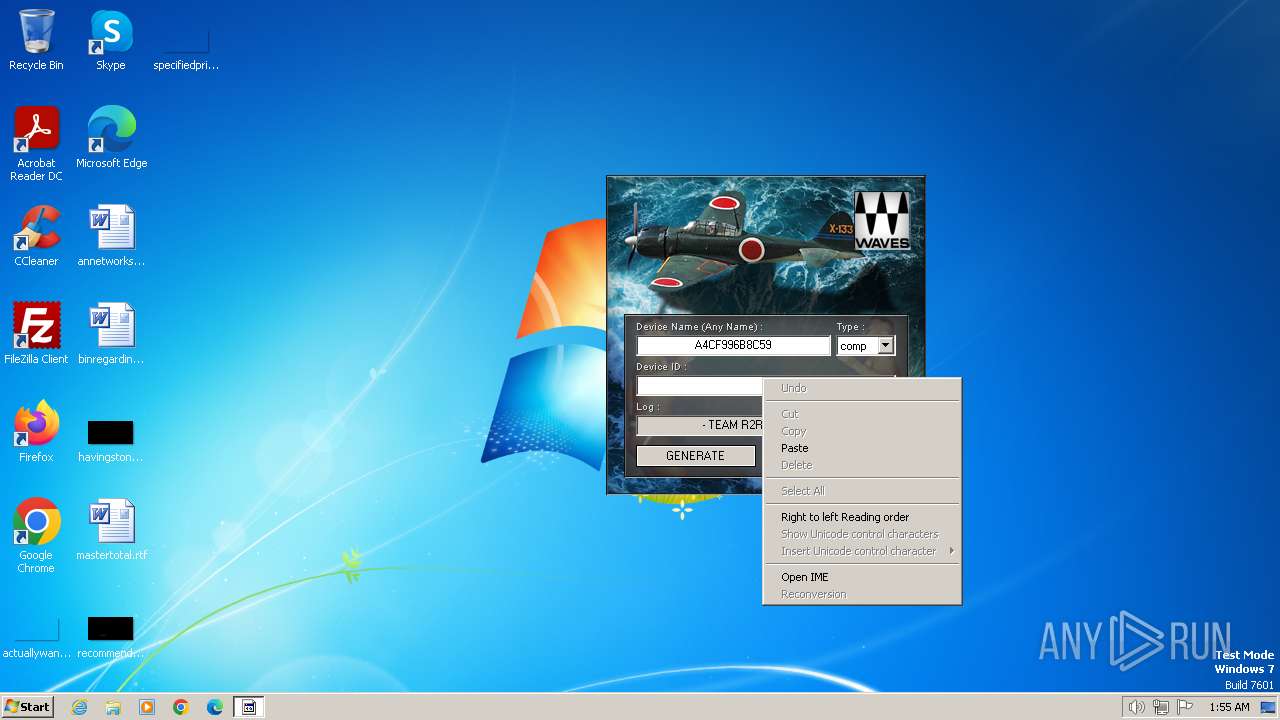
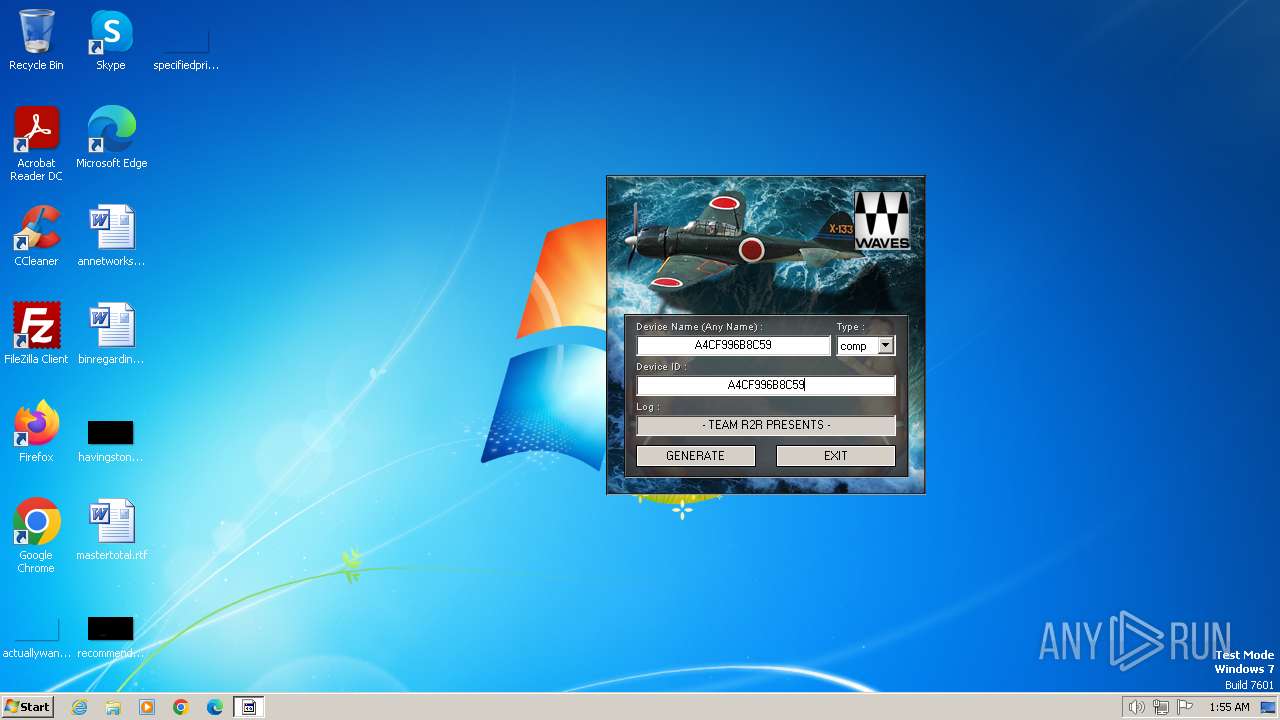
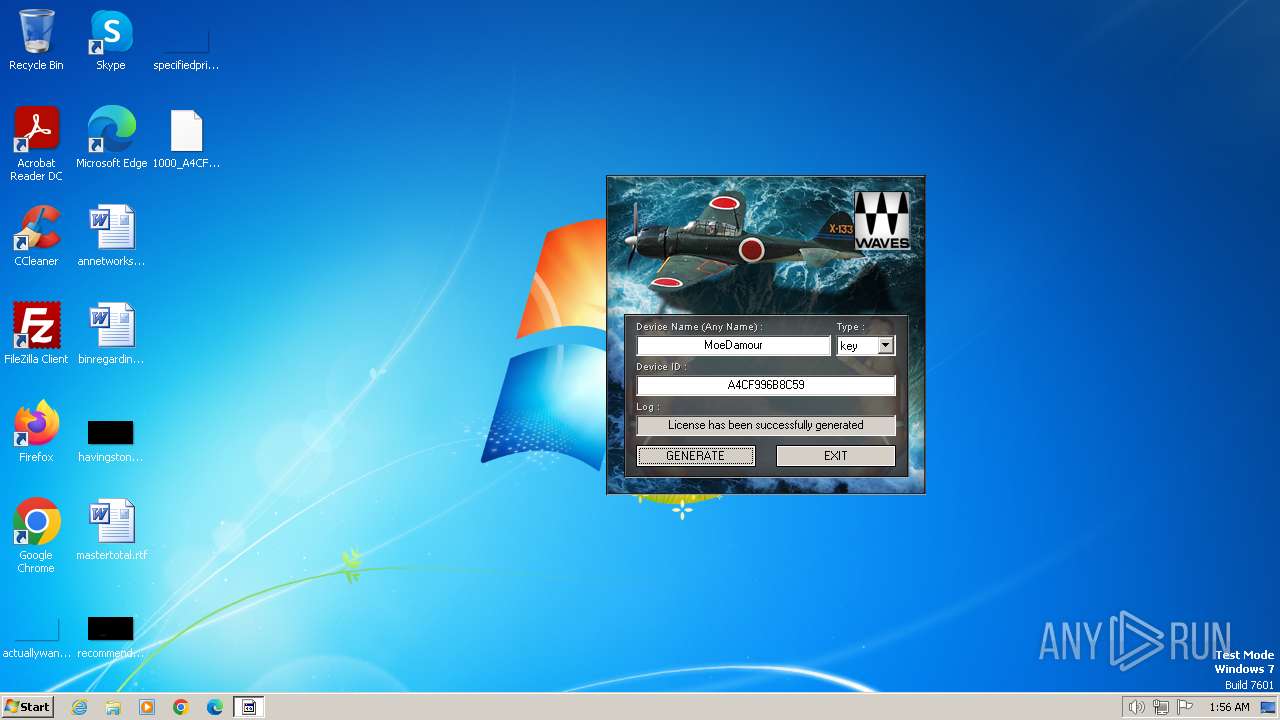
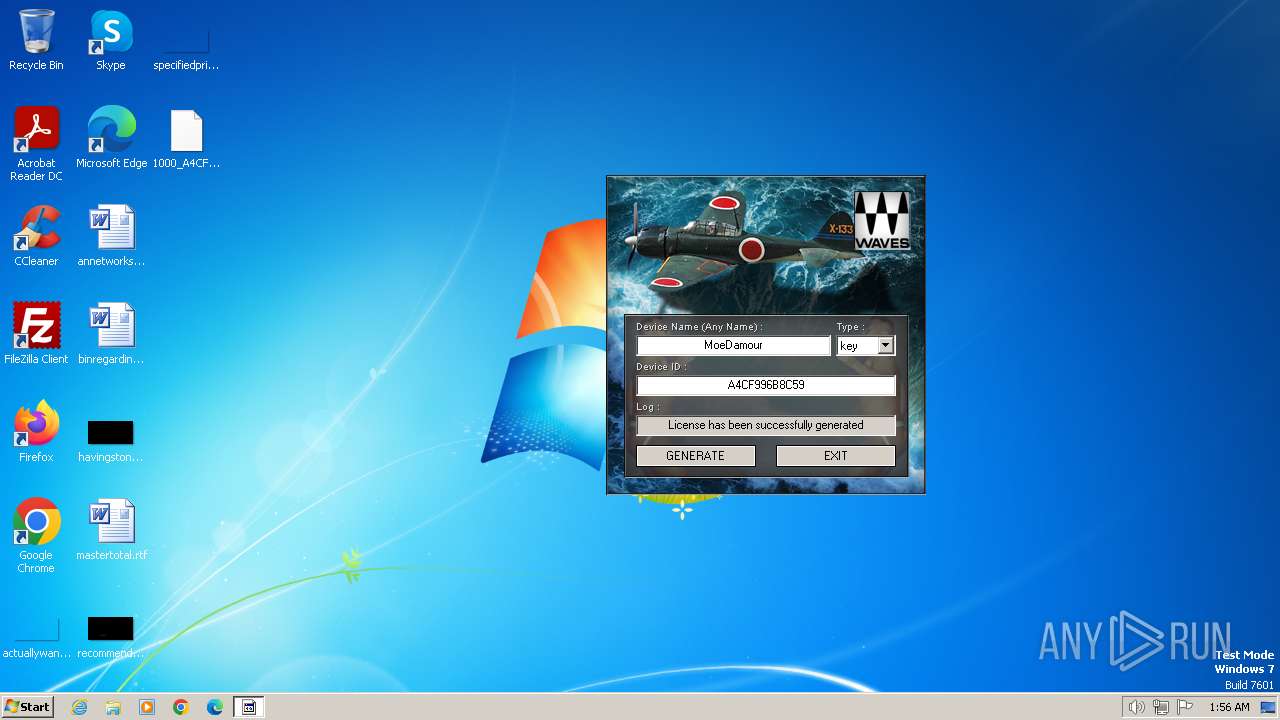
| File name: | Waves_Keygen.exe |
| Full analysis: | https://app.any.run/tasks/bbb0840a-a204-4bce-9f29-ab24065c4105 |
| Verdict: | Malicious activity |
| Analysis date: | July 10, 2024, 00:54:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | E927148AF4298E8D1CA02D175218B9BC |
| SHA1: | 18224FD3B2108160E3905F6EBCE75D0B88529B42 |
| SHA256: | 7175D0071E3FEFE19009A280A0CD3E43ECF3936FF5A06D0A2CA616F5D0D6A3CF |
| SSDEEP: | 49152:ZJ898deEVoa2swq7vLGkZvRRIAyu+2pYYJRt+zP0CjdTqYEKvkLg2h8iMfiti3x2:ZJ8yoa2sD7vLzRn9yH2pYvDdCmkM2hPF |
MALICIOUS
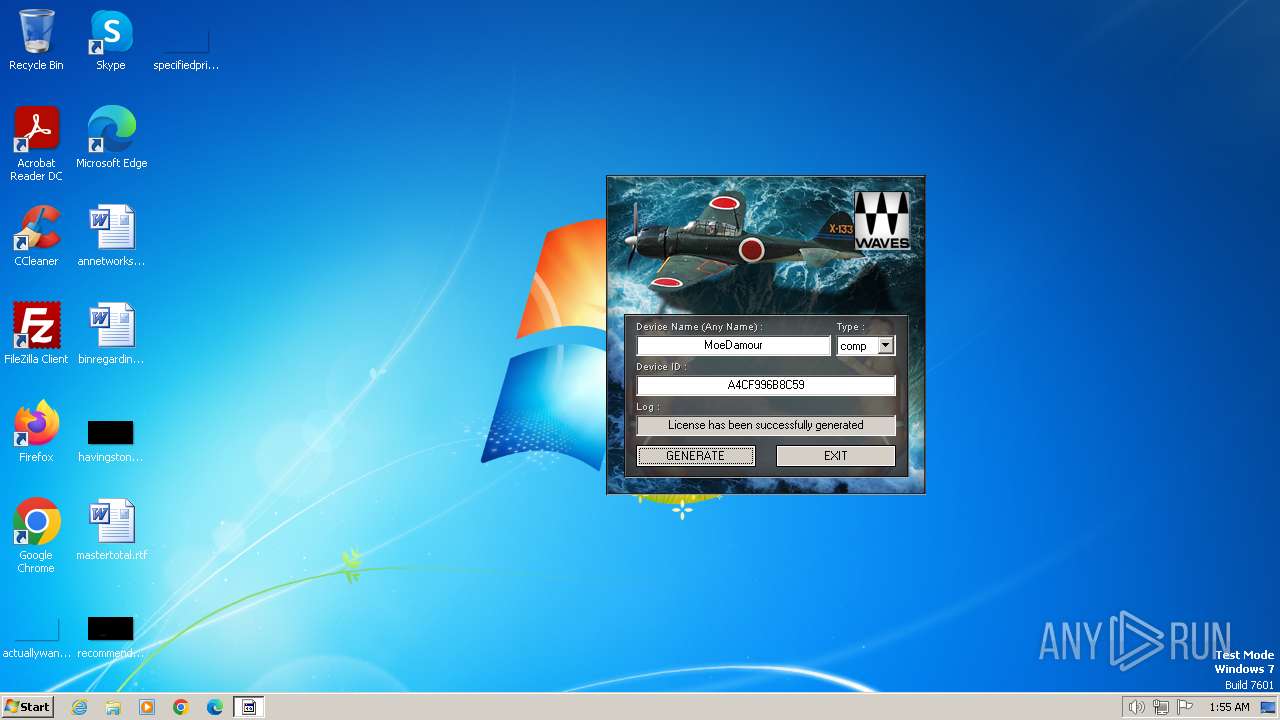
Drops the executable file immediately after the start
- Waves_Keygen.exe (PID: 3708)
SUSPICIOUS
Executable content was dropped or overwritten
- Waves_Keygen.exe (PID: 3708)
Reads the Internet Settings
- keygen.exe (PID: 3192)
INFO
Create files in a temporary directory
- Waves_Keygen.exe (PID: 3708)
- keygen.exe (PID: 3192)
Checks supported languages
- Waves_Keygen.exe (PID: 3708)
- keygen.exe (PID: 3192)
Reads the computer name
- Waves_Keygen.exe (PID: 3708)
- keygen.exe (PID: 3192)
Reads the machine GUID from the registry
- keygen.exe (PID: 3192)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:25 21:56:47+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 141824 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3640 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
46
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3192 | C:\Users\admin\AppData\Local\Temp\keygen.exe | C:\Users\admin\AppData\Local\Temp\keygen.exe | — | Waves_Keygen.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225547 Modules
| |||||||||||||||
| 3380 | "C:\Users\admin\AppData\Local\Temp\Waves_Keygen.exe" | C:\Users\admin\AppData\Local\Temp\Waves_Keygen.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3708 | "C:\Users\admin\AppData\Local\Temp\Waves_Keygen.exe" | C:\Users\admin\AppData\Local\Temp\Waves_Keygen.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
11 971
Read events
11 790
Write events
166
Delete events
15
Modification events
| (PID) Process: | (3192) keygen.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | delete value | Name: | MRUList |
Value: | |||
| (PID) Process: | (3192) keygen.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | write | Name: | 0 |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C006B0065007900670065006E002E00650078006500000043003A005C00550073006500720073005C00610064006D0069006E005C004400650073006B0074006F0070000000 | |||
| (PID) Process: | (3192) keygen.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | write | Name: | MRUListEx |
Value: 00000000FFFFFFFF | |||
| (PID) Process: | (3192) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3192) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 07000000000000000100000002000000060000000B0000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3192) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3192) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\82\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | Mode |
Value: 6 | |||
| (PID) Process: | (3192) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\82\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | LogicalViewMode |
Value: 2 | |||
| (PID) Process: | (3192) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\82\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | FFlags |
Value: | |||
| (PID) Process: | (3192) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\82\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | IconSize |
Value: 48 | |||
Executable files
3
Suspicious files
3
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3708 | Waves_Keygen.exe | C:\Users\admin\AppData\Local\Temp\bgm.it | binary | |
MD5:E5F0FB9378B3438C07D7501BBDDC364C | SHA256:EDD5692A6CFD7CC7499989A92B52690311162920375688C86CCAEBFB82E214AB | |||
| 3708 | Waves_Keygen.exe | C:\Users\admin\AppData\Local\Temp\R2ROPENSSL.dll | executable | |
MD5:FC931742500771148D7309413218F50D | SHA256:A03C381DF4A4366CCB4ADFB16905DDB1F21ACD02B325A2C56670428994904B84 | |||
| 3708 | Waves_Keygen.exe | C:\Users\admin\AppData\Local\Temp\BASSMOD.dll | executable | |
MD5:E4EC57E8508C5C4040383EBE6D367928 | SHA256:8AD9E47693E292F381DA42DDC13724A3063040E51C26F4CA8E1F8E2F1DDD547F | |||
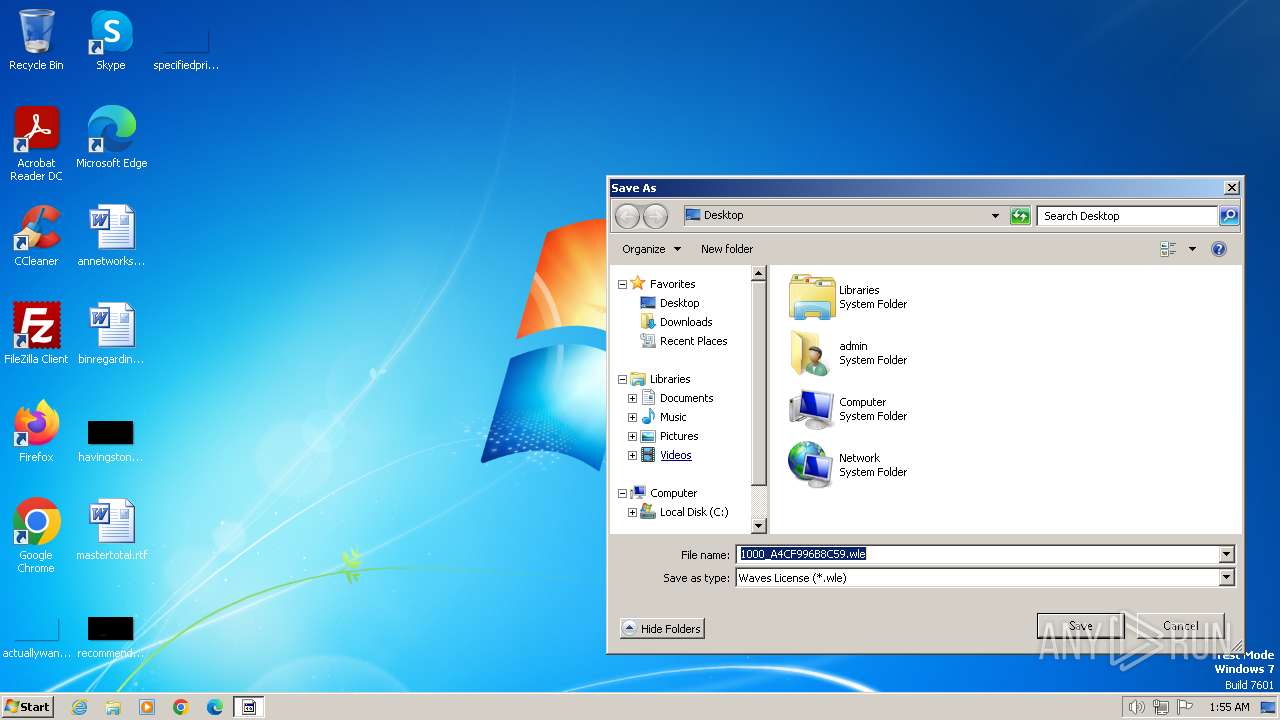
| 3192 | keygen.exe | C:\Users\admin\Downloads\1000_A4CF996B8C59.wle | text | |
MD5:93222E47EDF9F52570B459E6AA091D6E | SHA256:5DA57EDF869326FC74A7B1C0669751B5181DF6780CA05F2D7A8EF423E108295D | |||
| 3708 | Waves_Keygen.exe | C:\Users\admin\AppData\Local\Temp\nssE387.tmp | binary | |
MD5:2185B85C407B3D401B40773577FF4F9A | SHA256:B9837B7EC407BF531068F062E8F743E74EEA9E7E8FDDE9C4183EDA63D0D31173 | |||
| 3192 | keygen.exe | C:\Users\admin\AppData\Local\Temp\~DF42DC66B759AB644A.TMP | binary | |
MD5:3DB5E72EE4B9F66952E6932742808CEA | SHA256:ADB5EC4A470282DBBD262F19F76B984BF559E51624DF58C54B7522FBC579BFCC | |||
| 3708 | Waves_Keygen.exe | C:\Users\admin\AppData\Local\Temp\keygen.exe | executable | |
MD5:C559DDA89F22443229AC0B45C7F0CE42 | SHA256:E1D1021B2E1966E2224C6E3388ABD9612D2E93C81F743873235B99BBB22351B0 | |||
| 3192 | keygen.exe | C:\Users\admin\Desktop\1000_A4CF996B8C59.wle | text | |
MD5:ED7203AF82311D96C833D6D087B1AD64 | SHA256:4123704B8957E598C0221B136434AD67A8D049477E5F9463F79904545BC18BFE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
12
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a9f83325acc8ca75 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1372 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1372 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1372 | svchost.exe | 2.16.164.72:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
1372 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
1060 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |