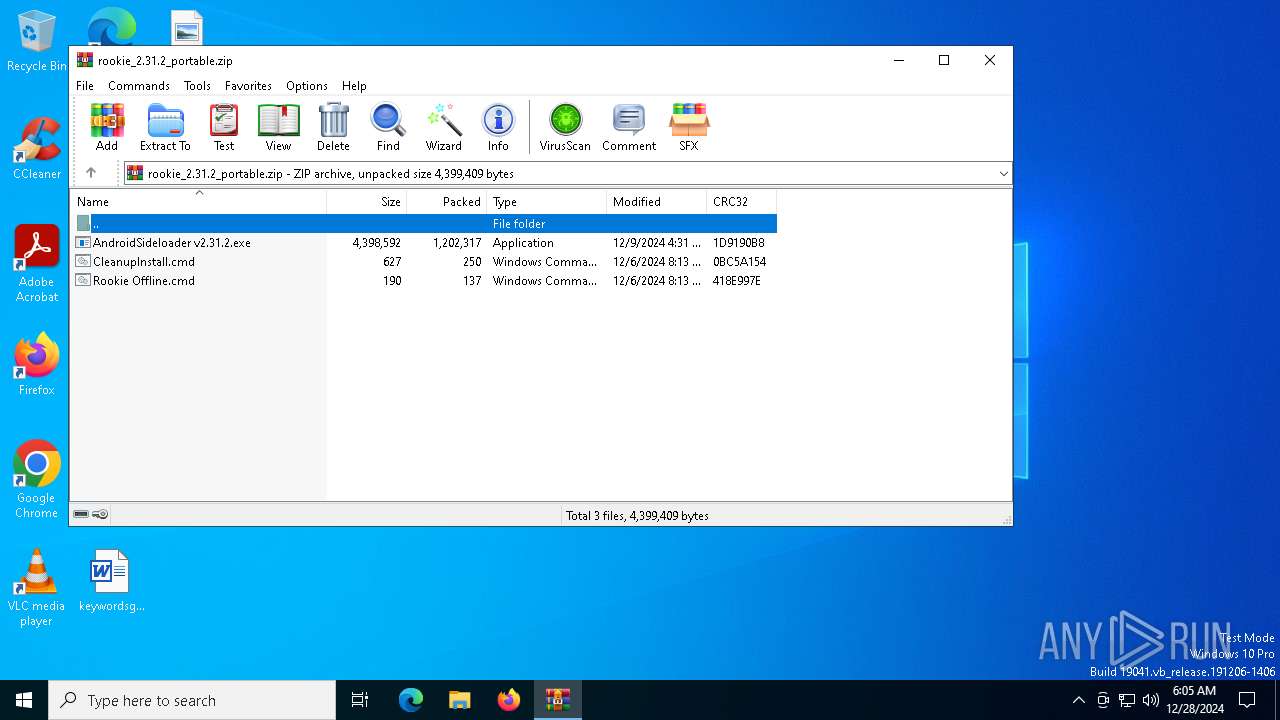
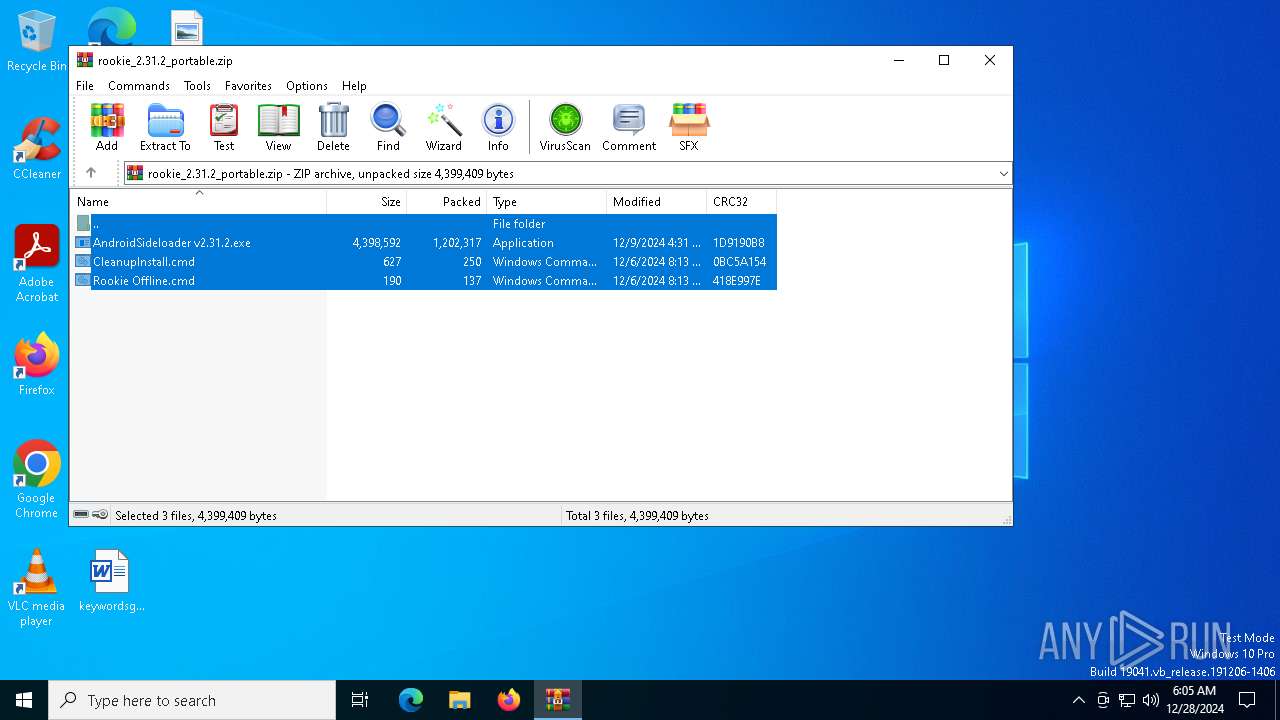
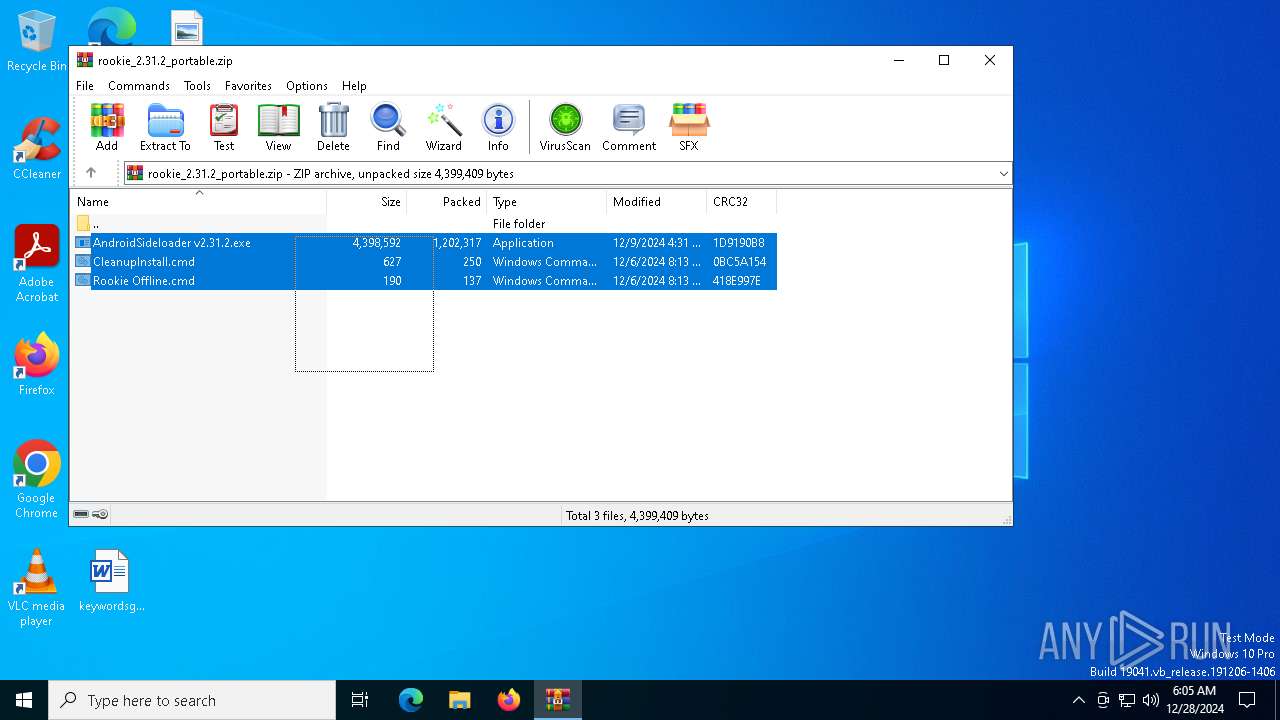
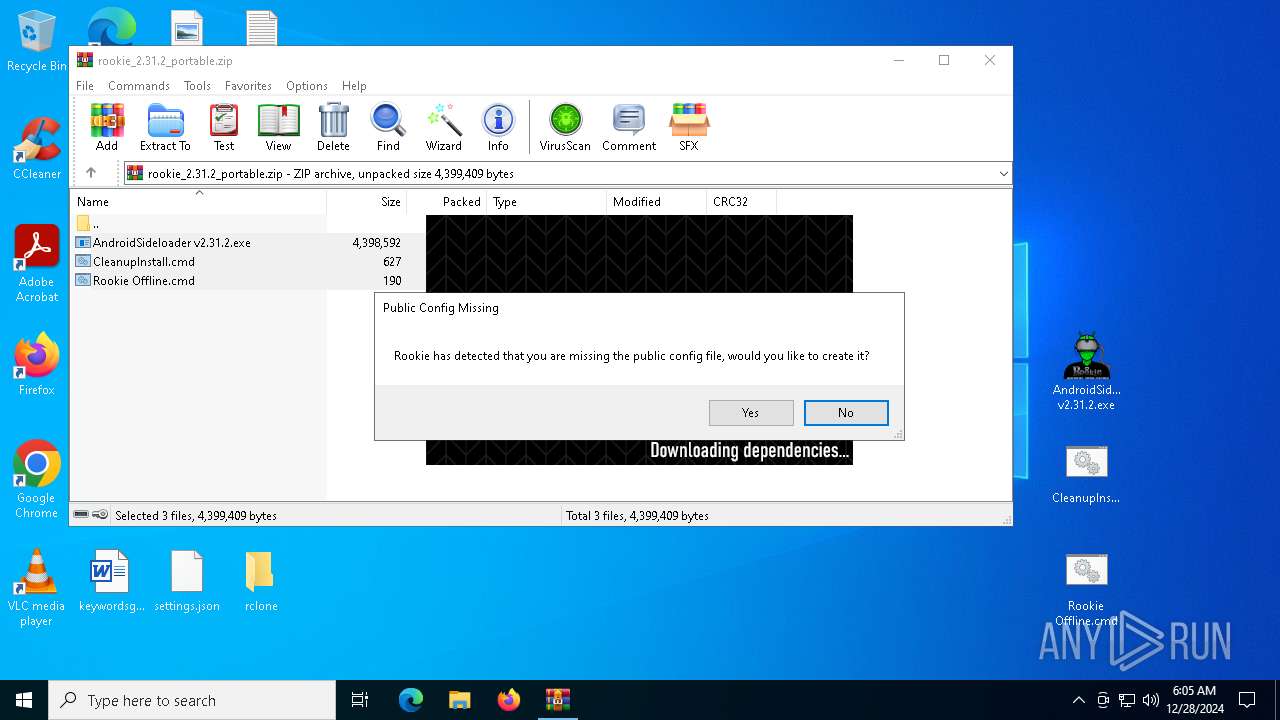
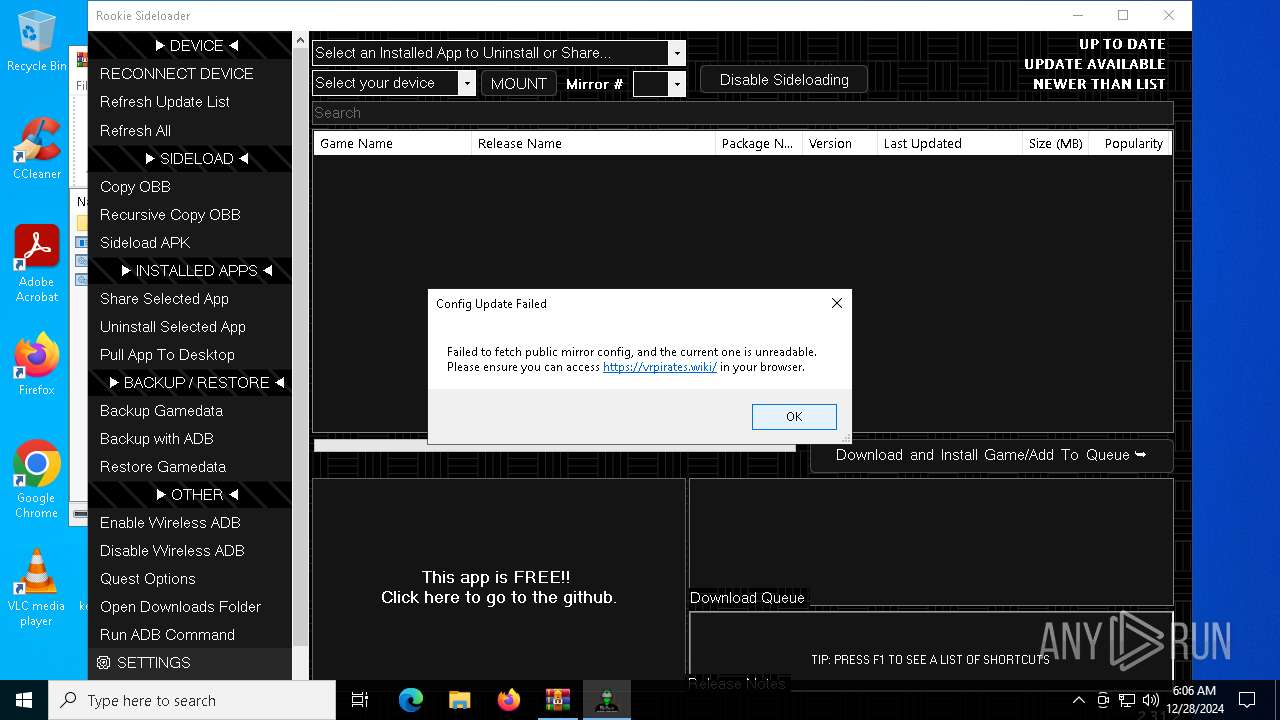
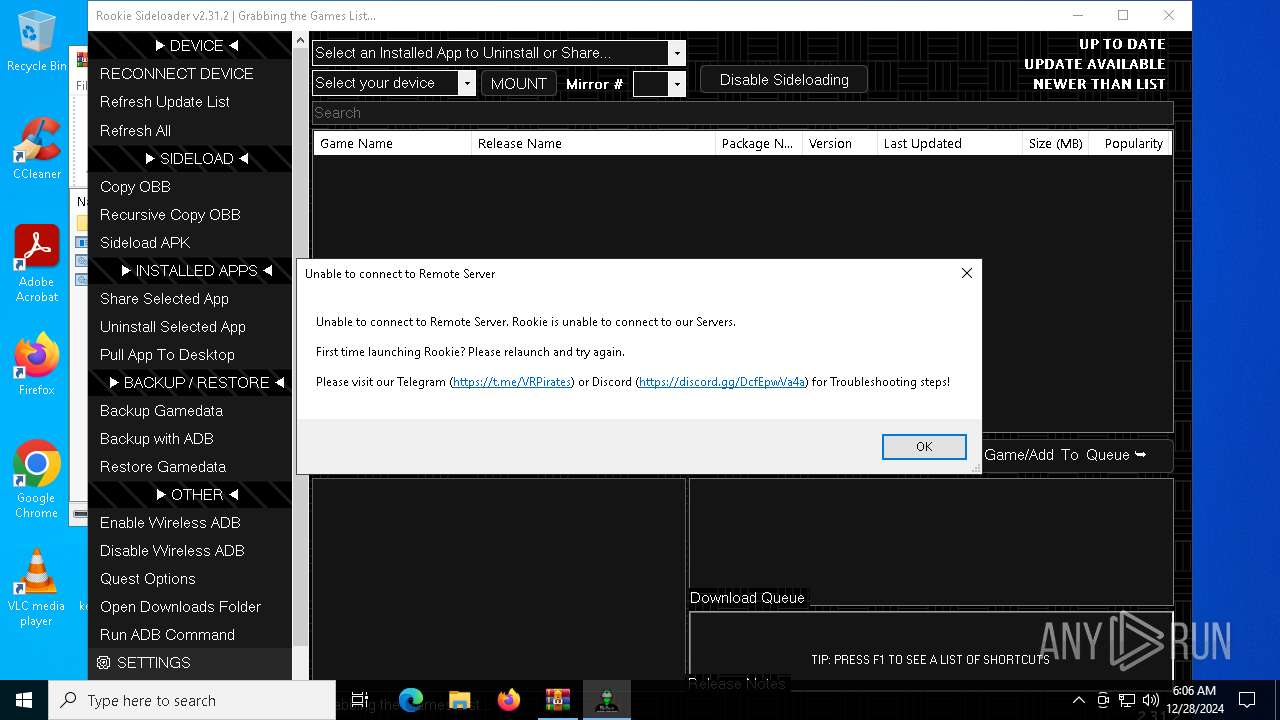
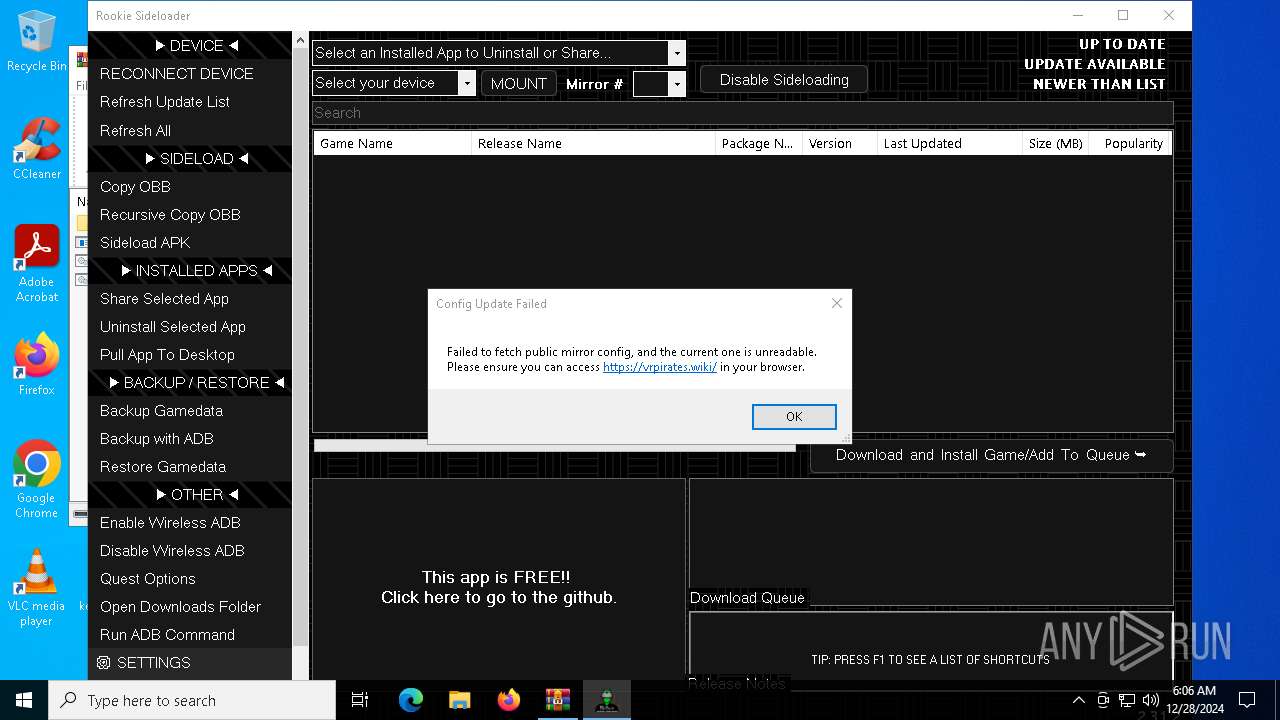
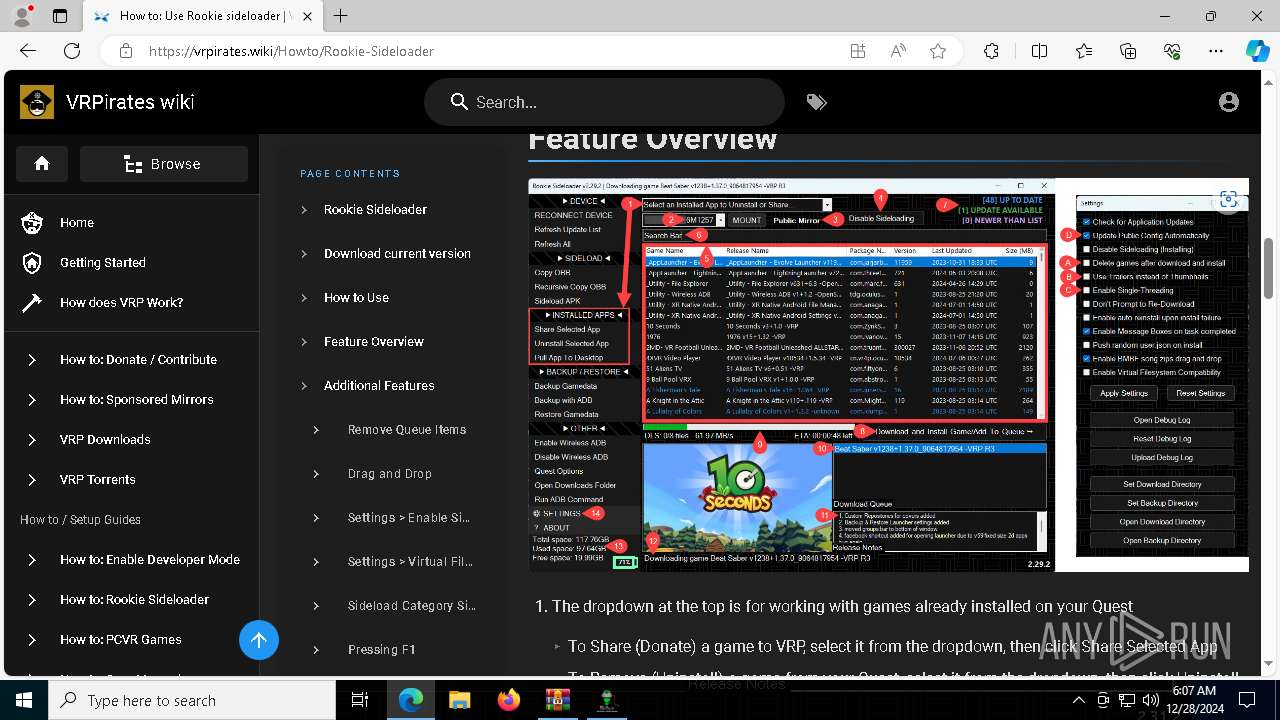
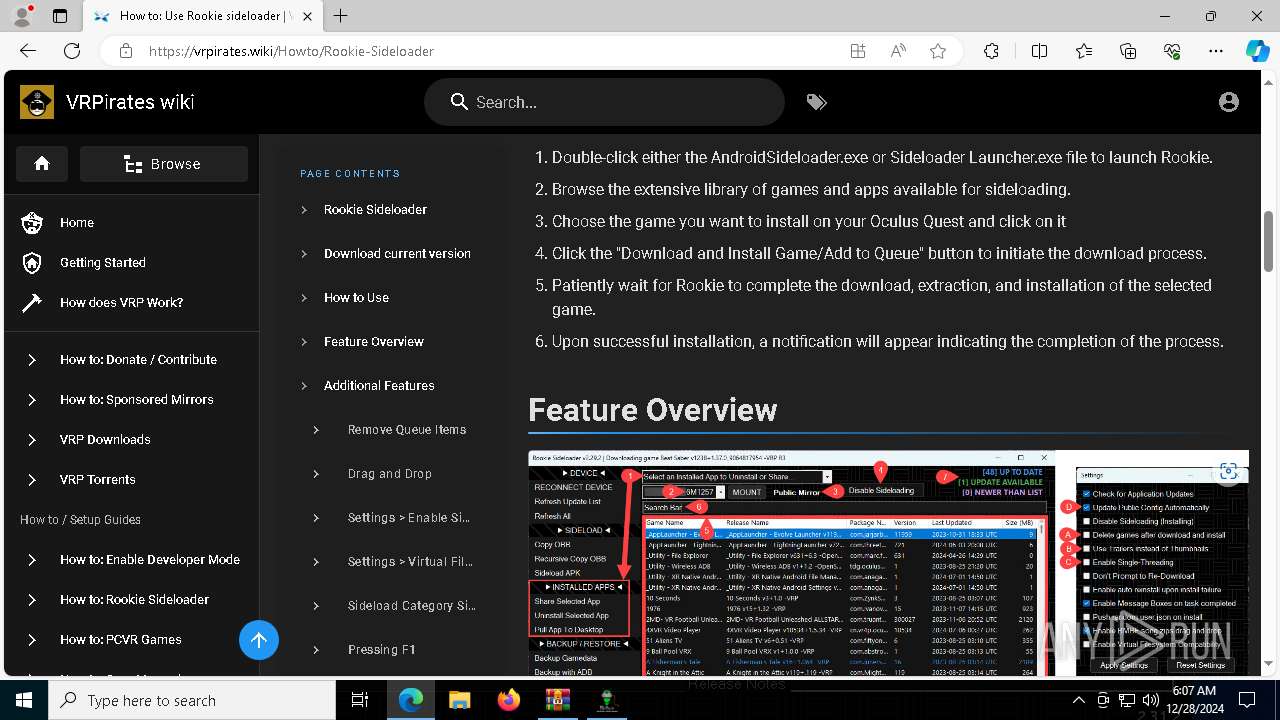
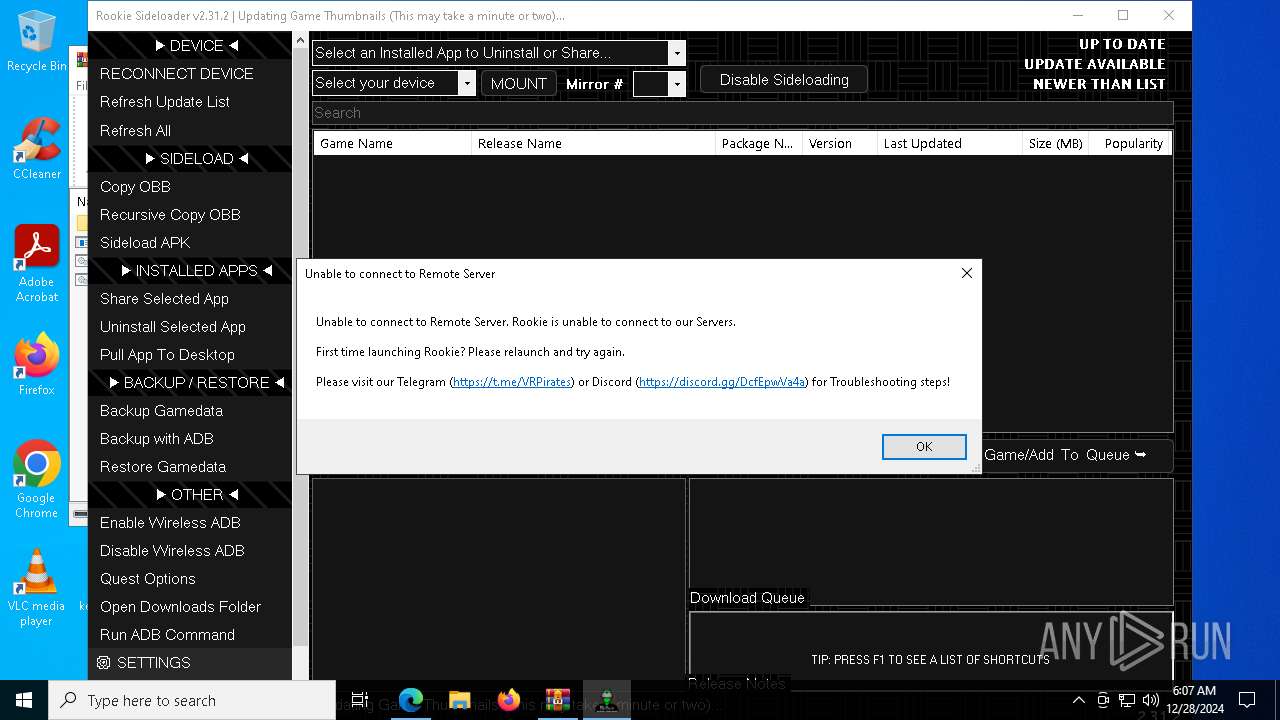
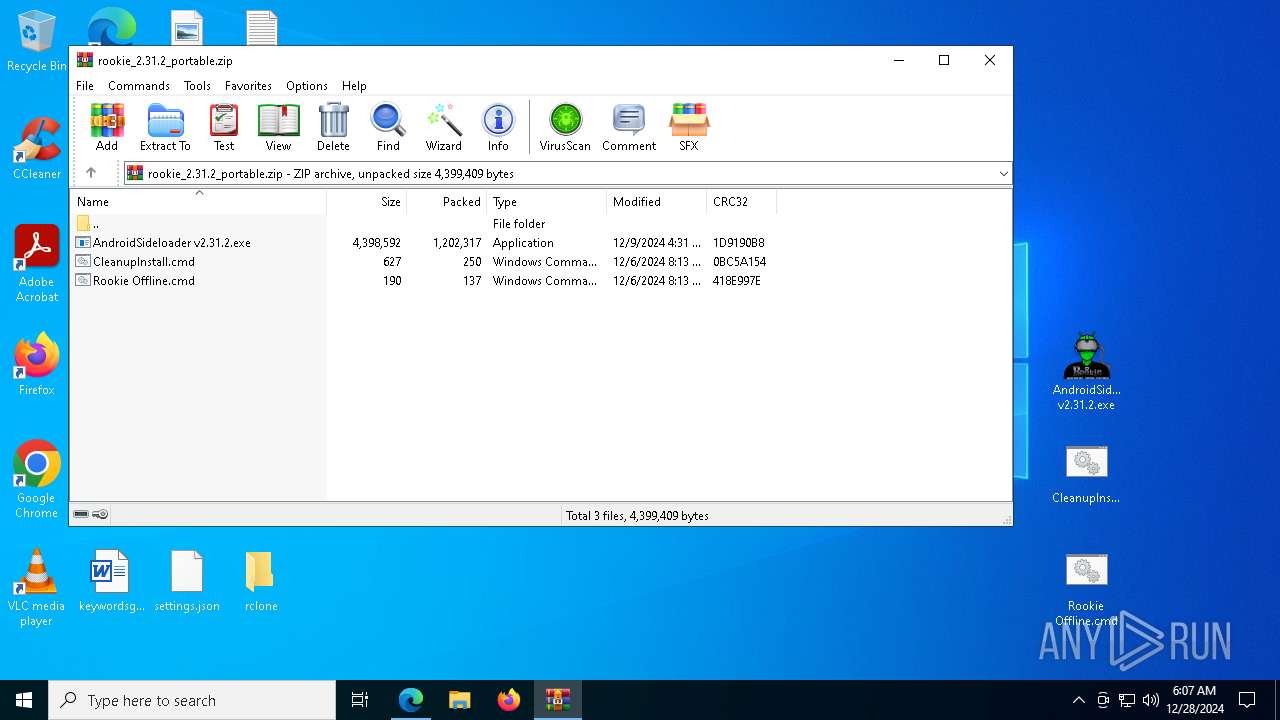
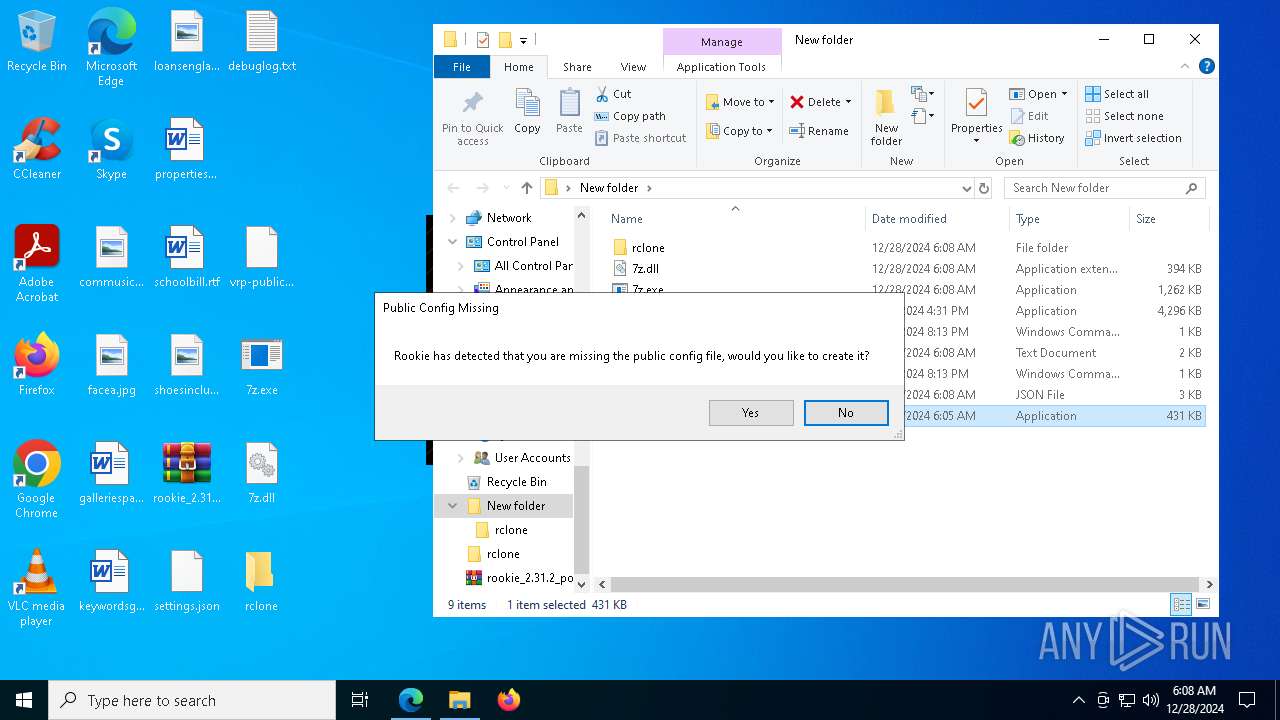
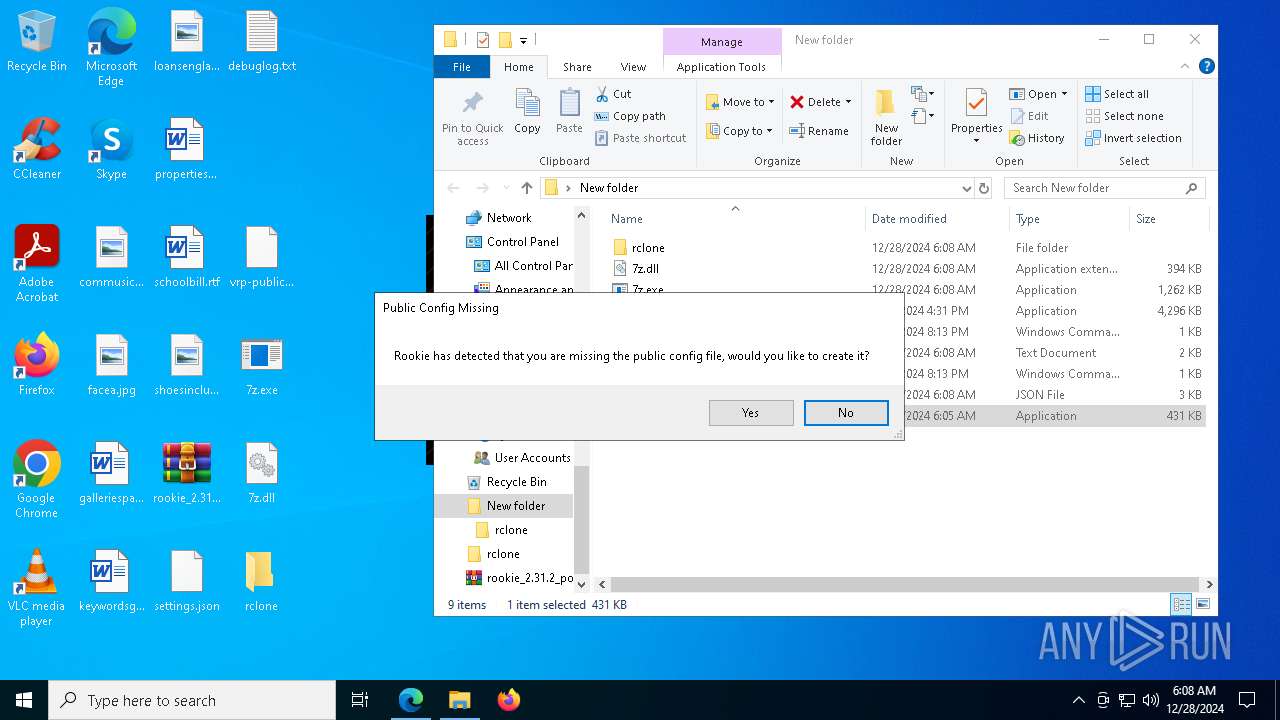
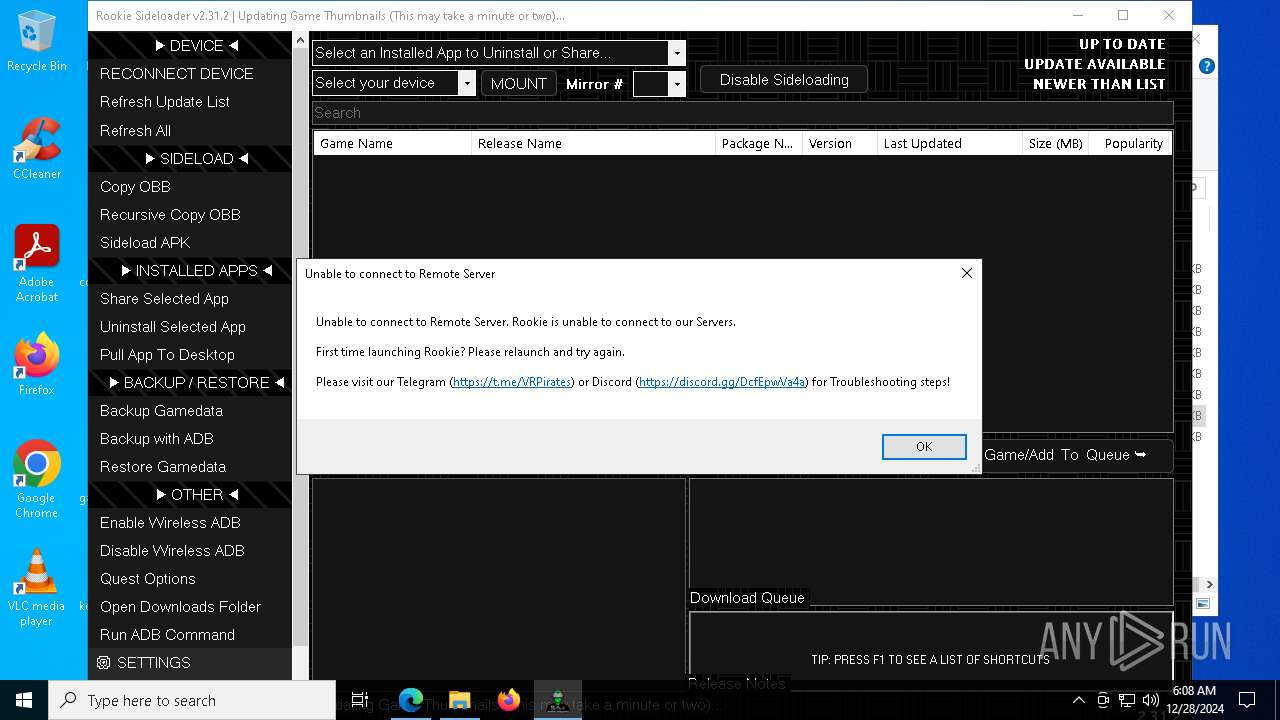
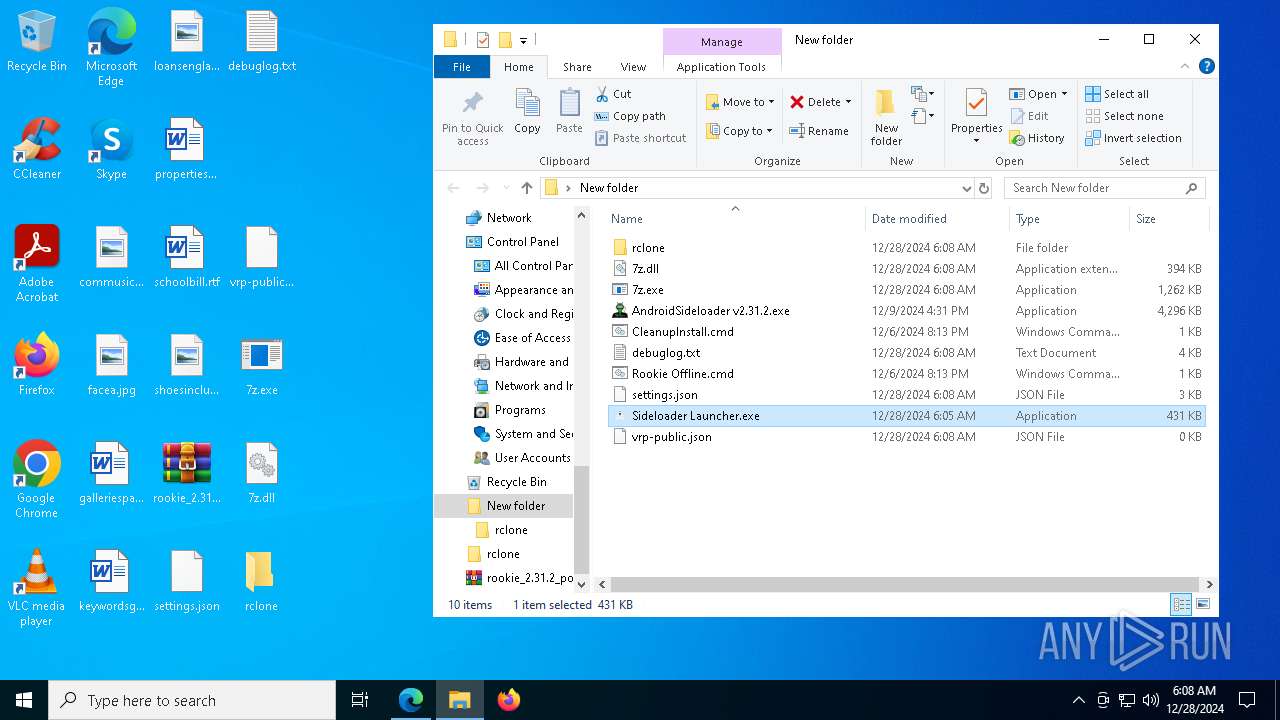
| File name: | rookie_2.31.2_portable.zip |
| Full analysis: | https://app.any.run/tasks/18f8dc58-f452-4dae-ba0a-092d02d491ea |
| Verdict: | Malicious activity |
| Analysis date: | December 28, 2024, 06:05:18 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 4D0E0C17AE3E170AC7927817BBECE847 |
| SHA1: | 43D69EF6631911004BE3E42CB20DEA89B6C4BF7A |
| SHA256: | 7164657D7743F17151304A67A00672C78433C5B520F89764373C93CF4E2505E4 |
| SSDEEP: | 49152:6lF/ucAwAlyENlLOskdPnuN8j1IsUSR7OoSSABr4oODP7Rs5jcjR6upw5EmMmVxy:yucCyENlL+dGIcEaoSNBr4lDP7Rs5kMS |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4592)
SUSPICIOUS
Drops 7-zip archiver for unpacking
- AndroidSideloader v2.31.2.exe (PID: 7008)
- AndroidSideloader v2.31.2.exe (PID: 6720)
Executable content was dropped or overwritten
- AndroidSideloader v2.31.2.exe (PID: 7008)
- 7z.exe (PID: 7116)
- AndroidSideloader v2.31.2.exe (PID: 6720)
Application launched itself
- adb.exe (PID: 5788)
- adb.exe (PID: 1468)
- adb.exe (PID: 1540)
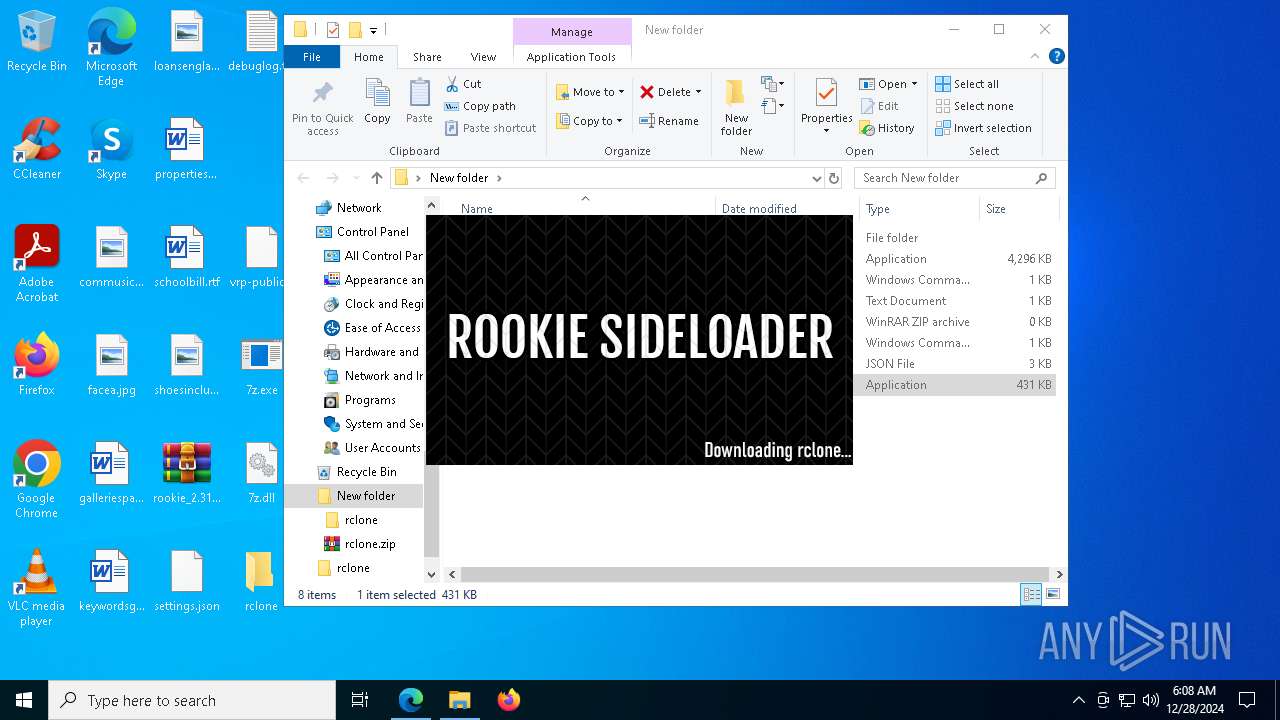
RCLONE has been detected
- rclone.exe (PID: 6524)
- rclone.exe (PID: 6508)
- rclone.exe (PID: 3224)
- rclone.exe (PID: 1988)
- rclone.exe (PID: 3812)
- rclone.exe (PID: 4972)
- rclone.exe (PID: 7052)
- rclone.exe (PID: 6524)
- rclone.exe (PID: 1348)
Reads security settings of Internet Explorer
- AndroidSideloader v2.31.2.exe (PID: 6724)
- AndroidSideloader v2.31.2.exe (PID: 7008)
- Sideloader Launcher.exe (PID: 1080)
- AndroidSideloader v2.31.2.exe (PID: 6720)
- ShellExperienceHost.exe (PID: 2008)
INFO
Checks supported languages
- 7z.exe (PID: 7116)
- AndroidSideloader v2.31.2.exe (PID: 7008)
- 7z.exe (PID: 2776)
- adb.exe (PID: 4724)
- adb.exe (PID: 5788)
- adb.exe (PID: 5916)
- rclone.exe (PID: 6508)
- rclone.exe (PID: 6524)
- rclone.exe (PID: 3224)
- AndroidSideloader v2.31.2.exe (PID: 6724)
- adb.exe (PID: 6772)
- adb.exe (PID: 1468)
- adb.exe (PID: 7052)
- identity_helper.exe (PID: 5732)
- ShellExperienceHost.exe (PID: 2008)
- rclone.exe (PID: 1988)
- rclone.exe (PID: 1348)
- rclone.exe (PID: 3812)
- Sideloader Launcher.exe (PID: 1080)
- AndroidSideloader v2.31.2.exe (PID: 6720)
- 7z.exe (PID: 7116)
- adb.exe (PID: 1460)
- adb.exe (PID: 1540)
- adb.exe (PID: 7128)
- rclone.exe (PID: 6524)
- rclone.exe (PID: 7052)
- rclone.exe (PID: 4972)
Disables trace logs
- AndroidSideloader v2.31.2.exe (PID: 7008)
- AndroidSideloader v2.31.2.exe (PID: 6724)
- AndroidSideloader v2.31.2.exe (PID: 6720)
The sample compiled with english language support
- 7z.exe (PID: 7116)
- AndroidSideloader v2.31.2.exe (PID: 7008)
- AndroidSideloader v2.31.2.exe (PID: 6720)
Reads the computer name
- 7z.exe (PID: 7116)
- AndroidSideloader v2.31.2.exe (PID: 7008)
- 7z.exe (PID: 2776)
- adb.exe (PID: 5916)
- rclone.exe (PID: 6524)
- rclone.exe (PID: 6508)
- rclone.exe (PID: 3224)
- AndroidSideloader v2.31.2.exe (PID: 6724)
- adb.exe (PID: 7052)
- identity_helper.exe (PID: 5732)
- rclone.exe (PID: 1988)
- ShellExperienceHost.exe (PID: 2008)
- rclone.exe (PID: 1348)
- rclone.exe (PID: 3812)
- AndroidSideloader v2.31.2.exe (PID: 6720)
- Sideloader Launcher.exe (PID: 1080)
- 7z.exe (PID: 7116)
- adb.exe (PID: 7128)
- rclone.exe (PID: 4972)
- rclone.exe (PID: 6524)
- rclone.exe (PID: 7052)
Manual execution by a user
- AndroidSideloader v2.31.2.exe (PID: 7008)
- AndroidSideloader v2.31.2.exe (PID: 6724)
- Sideloader Launcher.exe (PID: 1080)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4592)
The process uses the downloaded file
- WinRAR.exe (PID: 4592)
- AndroidSideloader v2.31.2.exe (PID: 6724)
- AndroidSideloader v2.31.2.exe (PID: 7008)
- Sideloader Launcher.exe (PID: 1080)
- AndroidSideloader v2.31.2.exe (PID: 6720)
Create files in a temporary directory
- adb.exe (PID: 5916)
Reads the machine GUID from the registry
- AndroidSideloader v2.31.2.exe (PID: 6724)
- AndroidSideloader v2.31.2.exe (PID: 7008)
- AndroidSideloader v2.31.2.exe (PID: 6720)
Checks proxy server information
- AndroidSideloader v2.31.2.exe (PID: 6724)
- AndroidSideloader v2.31.2.exe (PID: 7008)
- AndroidSideloader v2.31.2.exe (PID: 6720)
Reads the software policy settings
- AndroidSideloader v2.31.2.exe (PID: 6724)
- AndroidSideloader v2.31.2.exe (PID: 7008)
- AndroidSideloader v2.31.2.exe (PID: 6720)
Reads Environment values
- identity_helper.exe (PID: 5732)
Application launched itself
- msedge.exe (PID: 7144)
Sends debugging messages
- ShellExperienceHost.exe (PID: 2008)
Process checks computer location settings
- Sideloader Launcher.exe (PID: 1080)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:12:09 10:31:54 |
| ZipCRC: | 0x1d9190b8 |
| ZipCompressedSize: | 1202317 |
| ZipUncompressedSize: | 4398592 |
| ZipFileName: | AndroidSideloader v2.31.2.exe |
Total processes
221
Monitored processes
88
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 420 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 7z.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 540 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | rclone.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 836 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | adb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1080 | "C:\Users\admin\Desktop\New folder\Sideloader Launcher.exe" | C:\Users\admin\Desktop\New folder\Sideloader Launcher.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Sideloader Launcher Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1144 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=4248 --field-trial-handle=2348,i,12718062362600423490,4584139537287857217,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1220 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6572 --field-trial-handle=2348,i,12718062362600423490,4584139537287857217,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1220 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5228 --field-trial-handle=2348,i,12718062362600423490,4584139537287857217,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1344 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3704 --field-trial-handle=2348,i,12718062362600423490,4584139537287857217,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1348 | "C:\Users\admin\Desktop\rclone\rclone.exe" sync ":Quest Games/.meta/notes" "C:\Users\admin\Desktop\notes" --config vrp.download.config --inplace | C:\Users\admin\Desktop\rclone\rclone.exe | AndroidSideloader v2.31.2.exe | ||||||||||||
User: admin Company: https://rclone.org Integrity Level: MEDIUM Description: Rclone Exit code: 1 Version: 1.68.2 Modules
| |||||||||||||||
| 1400 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5960 --field-trial-handle=2348,i,12718062362600423490,4584139537287857217,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
39 550
Read events
39 468
Write events
82
Delete events
0
Modification events
| (PID) Process: | (4592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\rookie_2.31.2_portable.zip | |||
| (PID) Process: | (4592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7008) AndroidSideloader v2.31.2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\AndroidSideloader v2_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7008) AndroidSideloader v2.31.2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\AndroidSideloader v2_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
24
Suspicious files
349
Text files
81
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7008 | AndroidSideloader v2.31.2.exe | C:\Users\admin\Desktop\dependencies.7z | — | |
MD5:— | SHA256:— | |||
| 7008 | AndroidSideloader v2.31.2.exe | C:\Users\admin\Desktop\Sideloader Launcher.exe | executable | |
MD5:A53A5E70248EB3DA58DEFA74B0554704 | SHA256:98BC8CF1C6A59EF70D6431E1E92887984E5B21C8FBC85B4AD23CCC70589C4B1F | |||
| 7008 | AndroidSideloader v2.31.2.exe | C:\Users\admin\Desktop\7z.exe | executable | |
MD5:1A7EAA1DAB7867E15D7800AE0B5AF5E3 | SHA256:356BEA8B6E9EB84DFA0DD8674E7C03428C641A47789DF605C5BEA0730DE4AED2 | |||
| 7116 | 7z.exe | C:\RSL\platform-tools\aapt.exe | executable | |
MD5:A7944D392F439C722C55E2F09410D494 | SHA256:2A9BD1798D3841C7592D995C87FD1FB92397CDB700F076C51B9E9E722F9EB82C | |||
| 7116 | 7z.exe | C:\RSL\platform-tools\source.properties | text | |
MD5:EC771EFEE4A8AA924A7791F814221B02 | SHA256:E43DB3B096E922AFD7607090E626C9D0600AAAAB6E312AE441F44263E72D1328 | |||
| 7116 | 7z.exe | C:\RSL\platform-tools\NOTICE.txt | text | |
MD5:E7E8B9497810834CAB9522FE5DD80560 | SHA256:D25FAFFB58D73FEF75D10B7D9B49D8D9872CBB33018F23232D04E8C3EA9DC4DB | |||
| 4592 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4592.24694\CleanupInstall.cmd | text | |
MD5:9AE44CEBBDE4F44C27801BBF93494C1D | SHA256:57FC69317DE4E7B75A6D45C6037572738F6B48766A6C0D8A47A4F4A4CC533281 | |||
| 7008 | AndroidSideloader v2.31.2.exe | C:\Users\admin\Desktop\debuglog.txt | text | |
MD5:0498A9AE9C6FE5F418F659F484EC2D6E | SHA256:329BC810F43F54449F112A5C776B7C9C4C4D3807D2B5D71AC34205E1D6E0393B | |||
| 7008 | AndroidSideloader v2.31.2.exe | C:\Users\admin\Desktop\7z.dll | executable | |
MD5:71EBAC040D32560BB9D76A552A7CB986 | SHA256:1AA51AA9BB50B26BB652D9C442208DB76546286B0DB169C8882DE97D1117029D | |||
| 7116 | 7z.exe | C:\RSL\platform-tools\mke2fs.conf | text | |
MD5:699098CA95F87BA48BB94A3E848549B3 | SHA256:AD58A58DCDD24D85055814CA9CAC67DB89D4E67C434E96774BDCE0D0A007D067 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
101
DNS requests
84
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6076 | svchost.exe | GET | 200 | 23.216.77.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6076 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2680 | msedge.exe | GET | 200 | 172.64.149.23:80 | http://zerossl.crt.sectigo.com/ZeroSSLECCDomainSecureSiteCA.crt | unknown | — | — | whitelisted |
3848 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3848 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6664 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1735952968&P2=404&P3=2&P4=XlPZyqtlGW6DJ4FV4FnV0RUPcis4BiwuzJlL5dpj%2fsZQqmJUbL88hQIEfq8GblzvFoUXa%2fjrgTh7NmvfCfOHbQ%3d%3d | unknown | — | — | whitelisted |
6664 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1735952968&P2=404&P3=2&P4=XlPZyqtlGW6DJ4FV4FnV0RUPcis4BiwuzJlL5dpj%2fsZQqmJUbL88hQIEfq8GblzvFoUXa%2fjrgTh7NmvfCfOHbQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | unknown |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.216.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6076 | svchost.exe | 23.216.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6076 | svchost.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.21.110.146:443 | www.bing.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
github.com |
| shared |
raw.githubusercontent.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
7008 | AndroidSideloader v2.31.2.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
6724 | AndroidSideloader v2.31.2.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
6720 | AndroidSideloader v2.31.2.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |