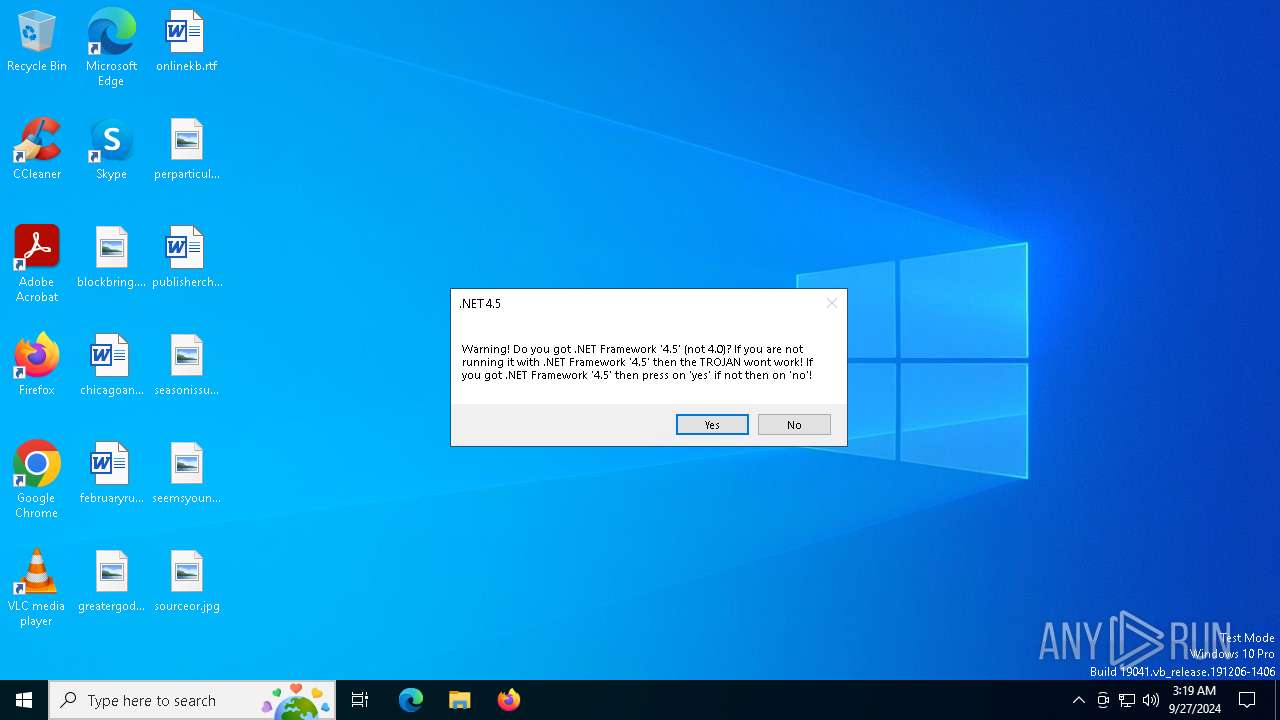
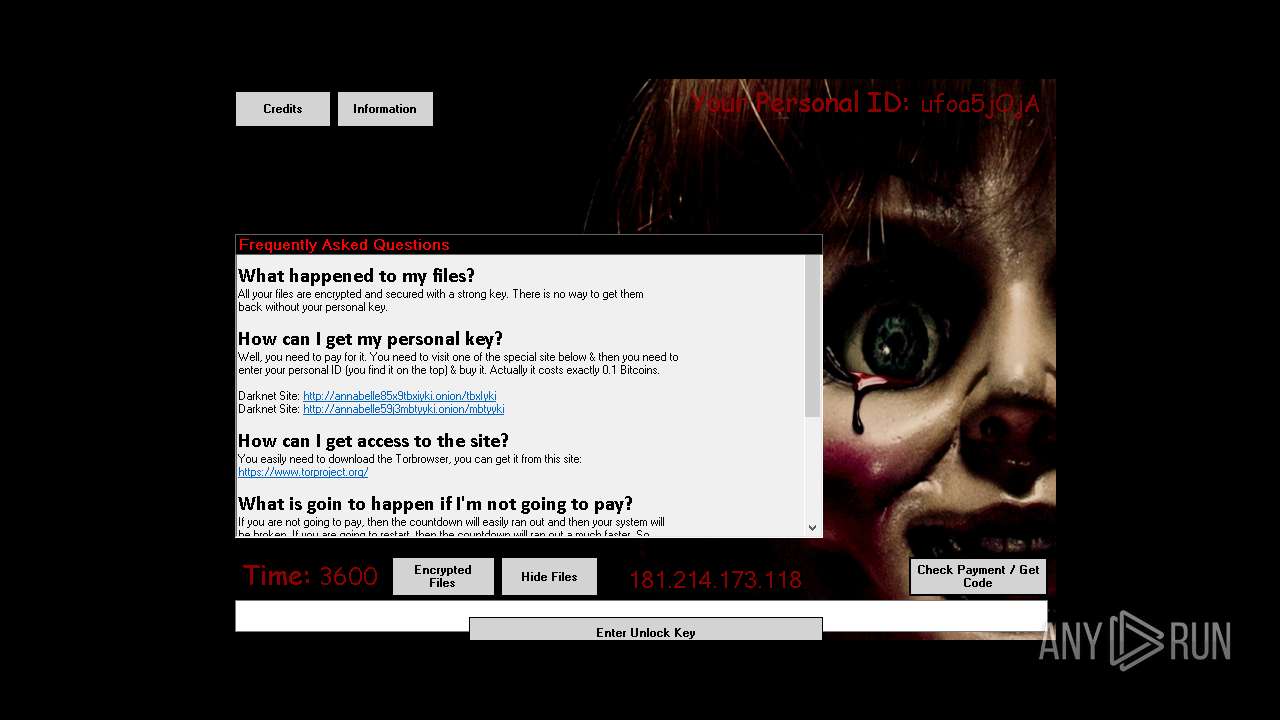
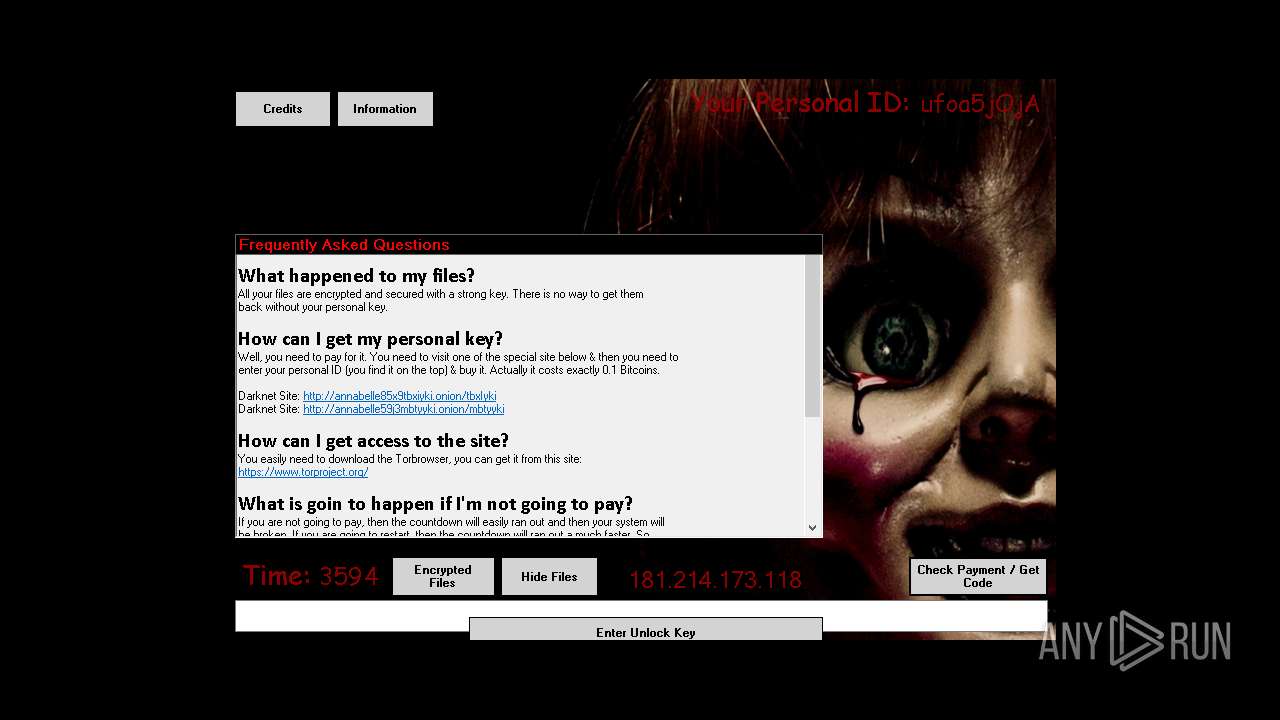
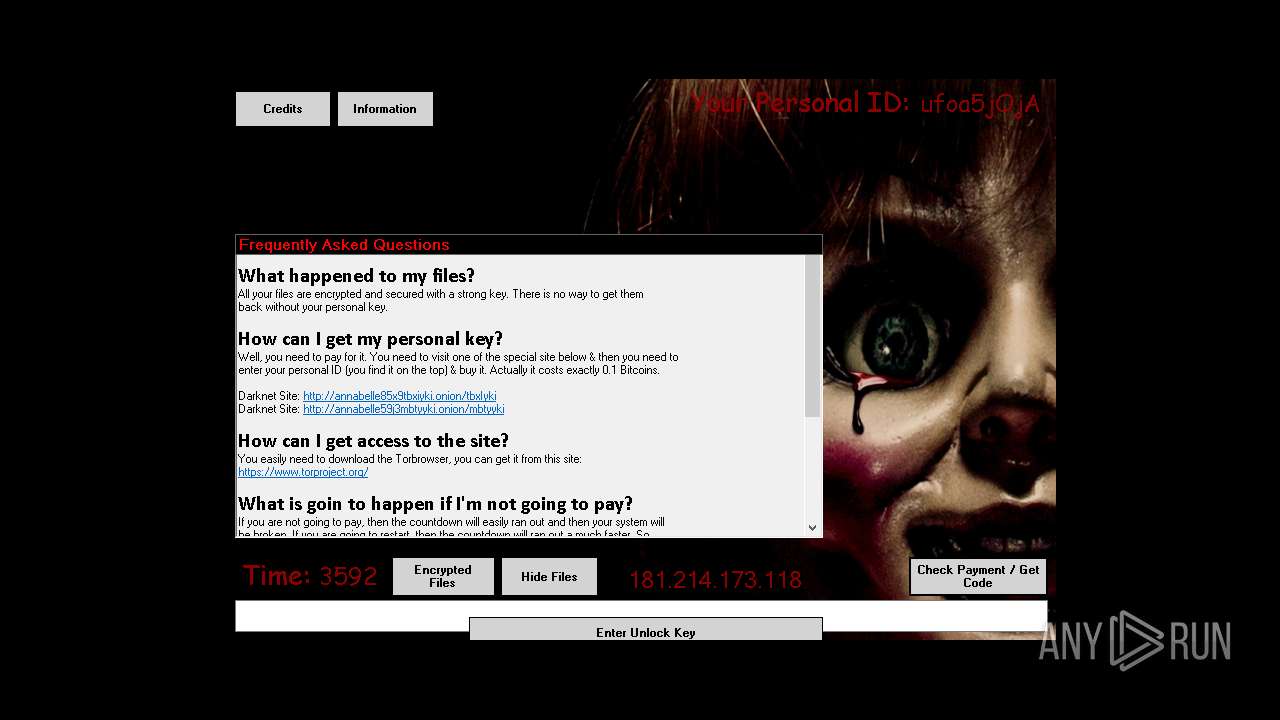
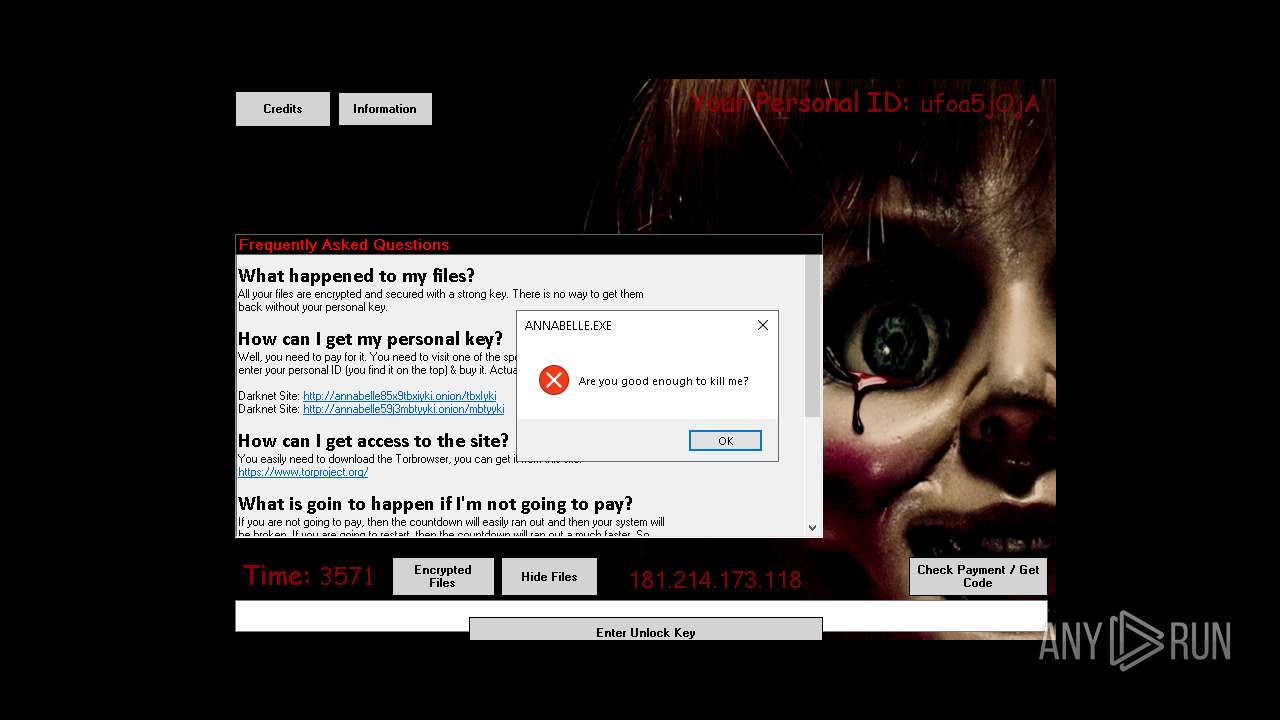
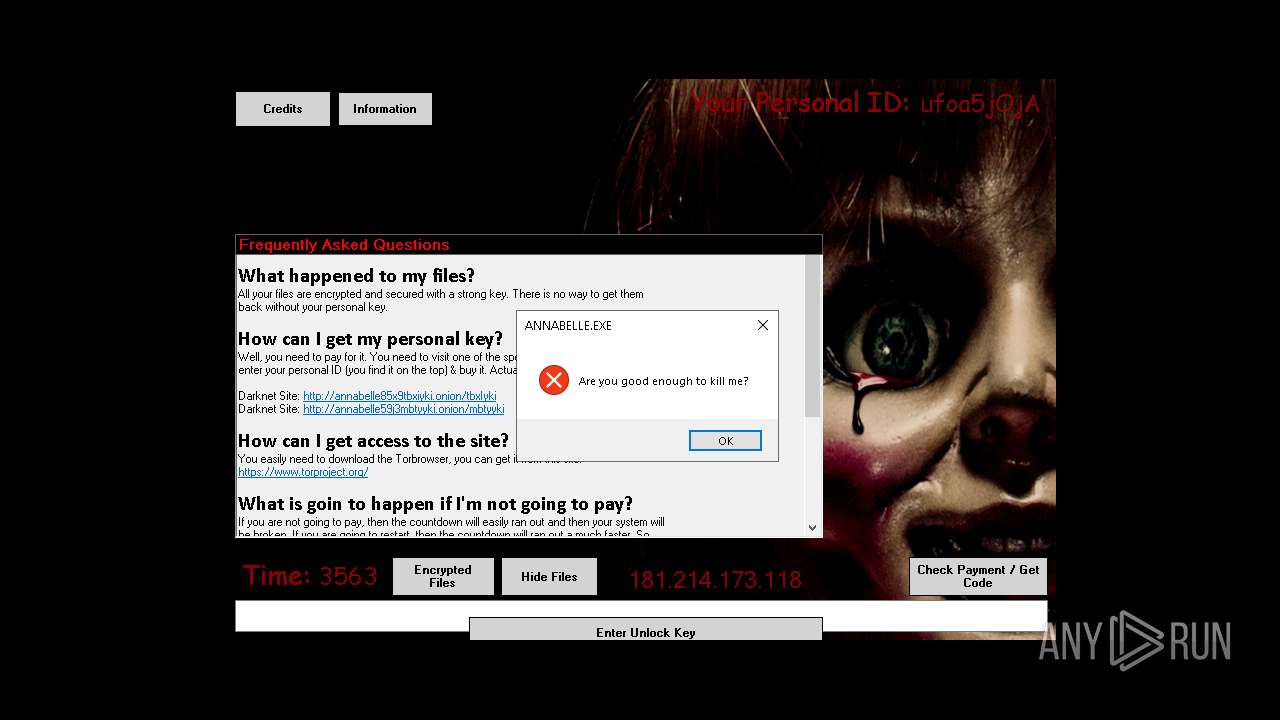
| File name: | Annabelle.exe |
| Full analysis: | https://app.any.run/tasks/b9c48297-d152-4d80-a2de-2d2df1bb733a |
| Verdict: | Malicious activity |
| Analysis date: | September 27, 2024, 03:19:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64 Mono/.Net assembly, for MS Windows |
| MD5: | 0F743287C9911B4B1C726C7C7EDCAF7D |
| SHA1: | 9760579E73095455FCBADDFE1E7E98A2BB28BFE0 |
| SHA256: | 716335BA5CD1E7186C40295B199190E2B6655E48F1C1CBE12139BA67FAA5E1AC |
| SSDEEP: | 393216:UMwm0qBknxdEX+LbMUgoSZmWSmh4aaRN22ChHCMNku1y4:UMcKX+Lbjgd7W1RNVC9ku1x |
MALICIOUS
Deletes shadow copies
- Annabelle.exe (PID: 4688)
UAC/LUA settings modification
- Annabelle.exe (PID: 4688)
Disables Windows Defender
- Annabelle.exe (PID: 4688)
Changes the login/logoff helper path in the registry
- Annabelle.exe (PID: 4688)
Disables the Run the Start menu
- Annabelle.exe (PID: 4688)
Changes the autorun value in the registry
- Annabelle.exe (PID: 4688)
Changes image file execution options
- Annabelle.exe (PID: 4688)
SUSPICIOUS
Uses NETSH.EXE to change the status of the firewall
- Annabelle.exe (PID: 4688)
Executes as Windows Service
- VSSVC.exe (PID: 6960)
The system shut down or reboot
- Annabelle.exe (PID: 4688)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 2380)
Checks for external IP
- Annabelle.exe (PID: 4184)
INFO
Checks supported languages
- Annabelle.exe (PID: 4688)
Reads the computer name
- Annabelle.exe (PID: 4688)
Reads the machine GUID from the registry
- Annabelle.exe (PID: 4688)
Confuser has been detected (YARA)
- Annabelle.exe (PID: 4688)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2018:02:18 17:54:24+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 80 |
| CodeSize: | 16437248 |
| InitializedDataSize: | 274432 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x0000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.1.0.0 |
| ProductVersionNumber: | 2.1.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Annabelle |
| FileVersion: | 2.1.0.0 |
| InternalName: | Annabelle.exe |
| LegalCopyright: | Copyright © 2018 |
| LegalTrademarks: | - |
| OriginalFileName: | Annabelle.exe |
| ProductName: | UpdateBackup |
| ProductVersion: | 2.1.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
233
Monitored processes
18
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | vssadmin delete shadows /all /quiet | C:\Windows\System32\vssadmin.exe | — | Annabelle.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | shutdown.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1940 | "C:\Users\admin\AppData\Local\Temp\Annabelle.exe" | C:\Users\admin\AppData\Local\Temp\Annabelle.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Annabelle Exit code: 3221226540 Version: 2.1.0.0 Modules
| |||||||||||||||
| 2272 | vssadmin delete shadows /all /quiet | C:\Windows\System32\vssadmin.exe | — | Annabelle.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2380 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2660 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3288 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | vssadmin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3588 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | vssadmin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4112 | %ProgramFiles%\RUXIM\RUXIMICS.EXE /onlyloadcampaigns | C:\Program Files\RUXIM\RUXIMICS.exe | PLUGScheduler.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Reusable UX Interaction Manager Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4156 | "C:\Windows\System32\shutdown.exe" -r -t 00 -f | C:\Windows\System32\shutdown.exe | — | Annabelle.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Shutdown and Annotation Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 787
Read events
4 666
Write events
121
Delete events
0
Modification events
| (PID) Process: | (4688) Annabelle.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | UpdateBackup |
Value: C:\Users\admin\AppData\Local\Temp\Annabelle.exe | |||
| (PID) Process: | (4688) Annabelle.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | UpdateBackup |
Value: C:\Users\admin\AppData\Local\Temp\Annabelle.exe | |||
| (PID) Process: | (4688) Annabelle.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | UpdateBackup |
Value: C:\Users\admin\AppData\Local\Temp\Annabelle.exe | |||
| (PID) Process: | (4688) Annabelle.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender |
| Operation: | write | Name: | DisableAntiSpyware |
Value: 1 | |||
| (PID) Process: | (4688) Annabelle.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender |
| Operation: | write | Name: | DisableRoutinelyTakingAction |
Value: 1 | |||
| (PID) Process: | (4688) Annabelle.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | WindowsDefenderMAJ |
Value: 1 | |||
| (PID) Process: | (4688) Annabelle.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | WindowsDefenderMAJ |
Value: 1 | |||
| (PID) Process: | (4688) Annabelle.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script Host\Settings |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
| (PID) Process: | (4688) Annabelle.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Script Host\Settings |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
| (PID) Process: | (4688) Annabelle.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Windows NT\SystemRestore |
| Operation: | write | Name: | DisableSR |
Value: 1 | |||
Executable files
0
Suspicious files
55
Text files
2
Unknown types
61
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4688 | Annabelle.exe | C:\Users\admin\Pictures\msnworth.png.ANNABELLE | binary | |
MD5:F29A3ACA819461E8FE91FFC6B136F160 | SHA256:59F50125A98F20D43CC1FF9394A640C832CFD0EF6F2A39905132367B127943B7 | |||
| 4688 | Annabelle.exe | C:\Users\admin\Documents\benefitscreen.rtf.ANNABELLE | binary | |
MD5:1E87E561E614FF87F9376B654E586A6D | SHA256:AEC2CDBFAA737FB79E69D2C80AD6E0383B717B8324701CDDF0C23F3FCCC970D8 | |||
| 4688 | Annabelle.exe | C:\Users\admin\Documents\focushard.rtf.ANNABELLE | binary | |
MD5:F4CD2B9E75491E8E2DA98B5D43B425F7 | SHA256:BF84D716B016C0397A72DC5BC179D8B1EFF17B1E1070E4E8A45123E88D5DE2D2 | |||
| 4688 | Annabelle.exe | C:\Users\admin\Documents\Database1.accdb.ANNABELLE | binary | |
MD5:6923415A237011EFB8D48C0981D40E42 | SHA256:66C65F8208725E985A2DE2E56200173FC3F91FBDB64EFDE9DF799945BF0E9E1C | |||
| 4688 | Annabelle.exe | C:\Users\admin\Pictures\surewashington.jpg.ANNABELLE | binary | |
MD5:DF82D5D2F5A8D5B47992FE35AFB1F4D3 | SHA256:830C803C4719B055787553568A9275EF60AC409C6794FAAFEA2F2919BB3B4FBF | |||
| 4688 | Annabelle.exe | C:\Users\admin\Pictures\greatertrue.jpg.ANNABELLE | binary | |
MD5:8DF0341627E50405932A705483C98333 | SHA256:25C1B07D83733173018EB9C218C4E76885F4F913E97A701CF22547A75DB74081 | |||
| 4688 | Annabelle.exe | C:\Users\admin\Documents\lastllc.rtf.ANNABELLE | binary | |
MD5:1D25C5ED3A3BF25D0C255B179B3E430E | SHA256:B88E1E75276137BB2EF77E4E4EB592D73C87E847686CB67232F0B1EDD52FD726 | |||
| 4688 | Annabelle.exe | C:\Users\admin\Pictures\titlesxxx.png.ANNABELLE | binary | |
MD5:72678D55F132FB1624CFFC6F63A62229 | SHA256:E28543CBD212063E52D4C1EF7218F57A1DF351B92659F51B37A95DA925967780 | |||
| 4688 | Annabelle.exe | C:\Users\admin\Downloads\beingconsider.jpg.ANNABELLE | binary | |
MD5:6E272EA6322E4CA6B65A9B0FBFC6D086 | SHA256:354FB41127A98F2C0C8B26076A5230D1BE72172B7FED5864649DDDCBF03DE492 | |||
| 4688 | Annabelle.exe | C:\Users\admin\Downloads\selectionbrowse.jpg.ANNABELLE | binary | |
MD5:E4719D1D4C2703AD574D4F24AE6CB9FA | SHA256:34FCB6328776525DB30BB549BB24525C3B1067B60DE15568655B8B33CC98E5C3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
53
DNS requests
25
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4256 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2292 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4800 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4184 | Annabelle.exe | GET | 200 | 146.112.255.205:80 | http://myip.dnsomatic.com/ | unknown | — | — | unknown |
4800 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3648 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5336 | SearchApp.exe | 104.208.16.91:443 | browser.pipe.aria.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4004 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4184 | Annabelle.exe | Device Retrieving External IP Address Detected | ET POLICY Internal Host Retrieving External IP via myip.dnsomatic.com |
4184 | Annabelle.exe | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |