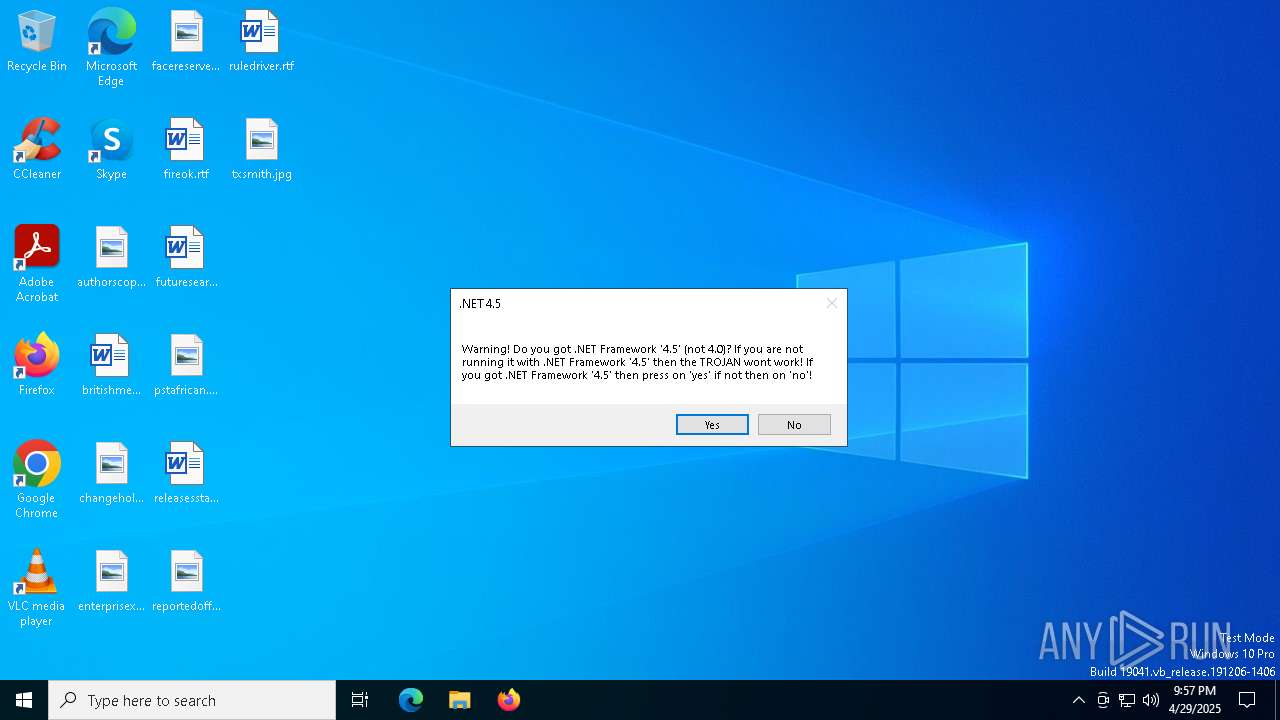
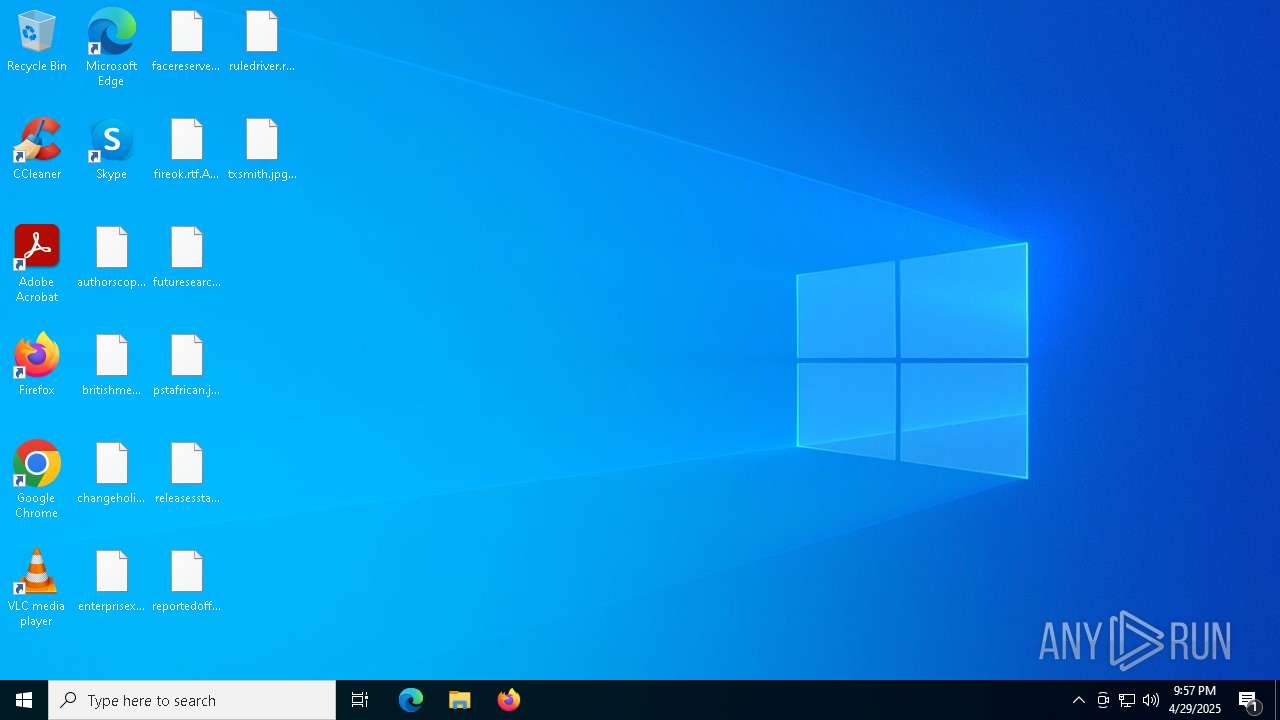
| File name: | Annabelle.exe |
| Full analysis: | https://app.any.run/tasks/357f9ca2-889d-4472-91f6-b35f069fc2a7 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 21:57:21 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64 Mono/.Net assembly, for MS Windows, 2 sections |
| MD5: | 0F743287C9911B4B1C726C7C7EDCAF7D |
| SHA1: | 9760579E73095455FCBADDFE1E7E98A2BB28BFE0 |
| SHA256: | 716335BA5CD1E7186C40295B199190E2B6655E48F1C1CBE12139BA67FAA5E1AC |
| SSDEEP: | 393216:UMwm0qBknxdEX+LbMUgoSZmWSmh4aaRN22ChHCMNku1y4:UMcKX+Lbjgd7W1RNVC9ku1x |
MALICIOUS
Deletes shadow copies
- Annabelle.exe (PID: 7704)
Changes the autorun value in the registry
- Annabelle.exe (PID: 7704)
Disables task manager
- Annabelle.exe (PID: 7704)
Disables Windows Defender
- Annabelle.exe (PID: 7704)
Changes the login/logoff helper path in the registry
- Annabelle.exe (PID: 7704)
Disables the Run the Start menu
- Annabelle.exe (PID: 7704)
UAC/LUA settings modification
- Annabelle.exe (PID: 7704)
Changes image file execution options
- Annabelle.exe (PID: 7704)
SUSPICIOUS
Uses NETSH.EXE to change the status of the firewall
- Annabelle.exe (PID: 7704)
Executes as Windows Service
- VSSVC.exe (PID: 8060)
Creates file in the systems drive root
- Annabelle.exe (PID: 7704)
Reads security settings of Internet Explorer
- Annabelle.exe (PID: 7704)
- ShellExperienceHost.exe (PID: 7196)
Reads the date of Windows installation
- Annabelle.exe (PID: 7704)
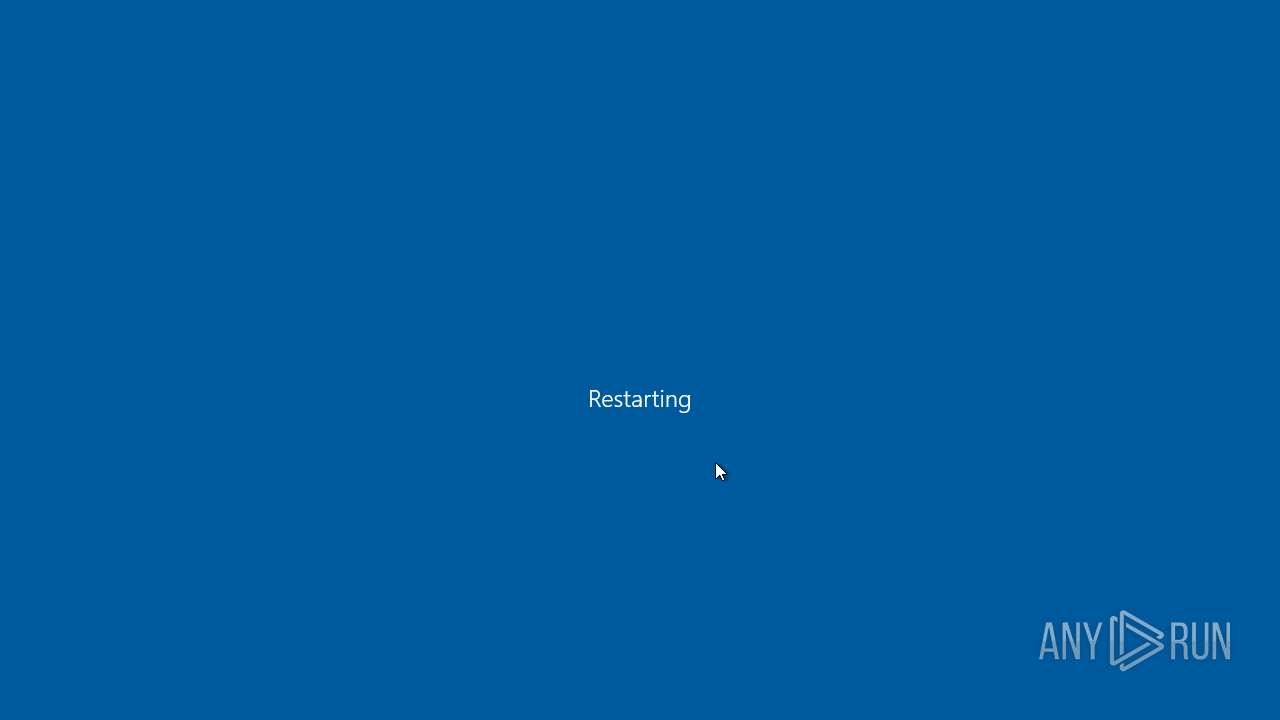
The system shut down or reboot
- Annabelle.exe (PID: 7704)
INFO
Reads the computer name
- Annabelle.exe (PID: 7704)
- ShellExperienceHost.exe (PID: 7196)
Checks supported languages
- Annabelle.exe (PID: 7704)
- ShellExperienceHost.exe (PID: 7196)
Reads the machine GUID from the registry
- Annabelle.exe (PID: 7704)
Process checks computer location settings
- Annabelle.exe (PID: 7704)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2018:02:18 17:54:24+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 80 |
| CodeSize: | 16437248 |
| InitializedDataSize: | 274432 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x0000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.1.0.0 |
| ProductVersionNumber: | 2.1.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Annabelle |
| FileVersion: | 2.1.0.0 |
| InternalName: | Annabelle.exe |
| LegalCopyright: | Copyright © 2018 |
| LegalTrademarks: | - |
| OriginalFileName: | Annabelle.exe |
| ProductName: | UpdateBackup |
| ProductVersion: | 2.1.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
137
Monitored processes
14
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7196 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7248 | "C:\Windows\System32\shutdown.exe" -r -t 00 -f | C:\Windows\System32\shutdown.exe | — | Annabelle.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Shutdown and Annotation Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7272 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | shutdown.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7620 | "C:\Users\admin\AppData\Local\Temp\Annabelle.exe" | C:\Users\admin\AppData\Local\Temp\Annabelle.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Annabelle Exit code: 3221226540 Version: 2.1.0.0 Modules
| |||||||||||||||
| 7704 | "C:\Users\admin\AppData\Local\Temp\Annabelle.exe" | C:\Users\admin\AppData\Local\Temp\Annabelle.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Annabelle Version: 2.1.0.0 Modules
| |||||||||||||||
| 7804 | vssadmin delete shadows /all /quiet | C:\Windows\System32\vssadmin.exe | — | Annabelle.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7812 | vssadmin delete shadows /all /quiet | C:\Windows\System32\vssadmin.exe | — | Annabelle.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7820 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | vssadmin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7828 | vssadmin delete shadows /all /quiet | C:\Windows\System32\vssadmin.exe | — | Annabelle.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7840 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | vssadmin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 644
Read events
1 557
Write events
87
Delete events
0
Modification events
| (PID) Process: | (7704) Annabelle.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | UpdateBackup |
Value: C:\Users\admin\AppData\Local\Temp\Annabelle.exe | |||
| (PID) Process: | (7704) Annabelle.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | UpdateBackup |
Value: C:\Users\admin\AppData\Local\Temp\Annabelle.exe | |||
| (PID) Process: | (7704) Annabelle.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | UpdateBackup |
Value: C:\Users\admin\AppData\Local\Temp\Annabelle.exe | |||
| (PID) Process: | (7704) Annabelle.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msconfig.exe |
| Operation: | write | Name: | Debugger |
Value: RIP | |||
| (PID) Process: | (7704) Annabelle.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\taskmgr.exe |
| Operation: | write | Name: | Debugger |
Value: RIP | |||
| (PID) Process: | (7704) Annabelle.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cmd.exe |
| Operation: | write | Name: | Debugger |
Value: RIP | |||
| (PID) Process: | (7704) Annabelle.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\chrome.exe |
| Operation: | write | Name: | Debugger |
Value: RIP | |||
| (PID) Process: | (7704) Annabelle.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\firefox.exe |
| Operation: | write | Name: | Debugger |
Value: RIP | |||
| (PID) Process: | (7704) Annabelle.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\opera.exe |
| Operation: | write | Name: | Debugger |
Value: RIP | |||
| (PID) Process: | (7704) Annabelle.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\microsoftedge.exe |
| Operation: | write | Name: | Debugger |
Value: RIP | |||
Executable files
0
Suspicious files
23
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7704 | Annabelle.exe | C:\Users\admin\Documents\Database1.accdb.ANNABELLE | binary | |
MD5:6923415A237011EFB8D48C0981D40E42 | SHA256:66C65F8208725E985A2DE2E56200173FC3F91FBDB64EFDE9DF799945BF0E9E1C | |||
| 7704 | Annabelle.exe | C:\Users\admin\Documents\providesconsumer.rtf.ANNABELLE | binary | |
MD5:190A3F82F517DCA092FB293F678C54AF | SHA256:31378659928FC2C437171A15616B1142B7641C4F85A7DA0C93B2202CC677C687 | |||
| 7704 | Annabelle.exe | C:\Users\admin\Pictures\isbnnight.png.ANNABELLE | binary | |
MD5:28038C252A419E23A0110F788A5B3D89 | SHA256:A8AE53798B20FAE048C2EDCBCF7936C0DEF54C2543BB6B9305C878D63576F8E1 | |||
| 7704 | Annabelle.exe | C:\Users\admin\Downloads\telephonetaken.jpg.ANNABELLE | binary | |
MD5:8C4BE2BB706EDE30D98DB12D312BAB10 | SHA256:5C5CA854ACF15CE74175BB51E43E3B7D0AF1036DE4161C1625C39DC72BAED625 | |||
| 7704 | Annabelle.exe | C:\Users\admin\Pictures\oncescience.jpg.ANNABELLE | binary | |
MD5:6864A96EE1F058888CBF84C583DC4F50 | SHA256:61A9820CDD99CC9DECDCCD2088605A6B2533ECF68AB1E160CF0431F7E8602D7D | |||
| 7704 | Annabelle.exe | C:\Users\admin\Pictures\imagesyear.png.ANNABELLE | binary | |
MD5:32728D21AB6FE7B5EF49900D13427696 | SHA256:FFC7B7190F76629113BCECE282F16CAEAFA5DB456F91E435816D443A6C25B497 | |||
| 7704 | Annabelle.exe | C:\Users\admin\Downloads\htoo.png.ANNABELLE | binary | |
MD5:50D2EC180E8E8D7BEDAFC33B16D568FE | SHA256:A89CEB41EC737B4D3378CA3AAA022D27BD085B7D6DB35923E5DA66CAD163CD26 | |||
| 7704 | Annabelle.exe | C:\Users\admin\Pictures\williamboth.png.ANNABELLE | binary | |
MD5:D125114B5B40B220D3E0CE1BBD8425DE | SHA256:465CF51B0483E62203211E1763FB40F05C33AB2665580D7A0E6FBA6CC29517C1 | |||
| 7704 | Annabelle.exe | C:\Users\admin\Desktop\britishmembers.rtf.ANNABELLE | binary | |
MD5:4C88EDC441475A4B18500E35FC6AEC61 | SHA256:B135AF931735B2D2DF2689B94AD6AACD9B15DA8F05AD99AE59E5D805F1A763E3 | |||
| 7704 | Annabelle.exe | C:\Users\admin\Desktop\changeholiday.jpg.ANNABELLE | binary | |
MD5:4FBBD8A55494E4071F728110AC1AA9AE | SHA256:EE9483F4C41542CCE36E1DBCE1A876C90644C912437BF35C5342DFED2A711231 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
31
DNS requests
6
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3812 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2292 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
— | — | 20.189.173.12:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |