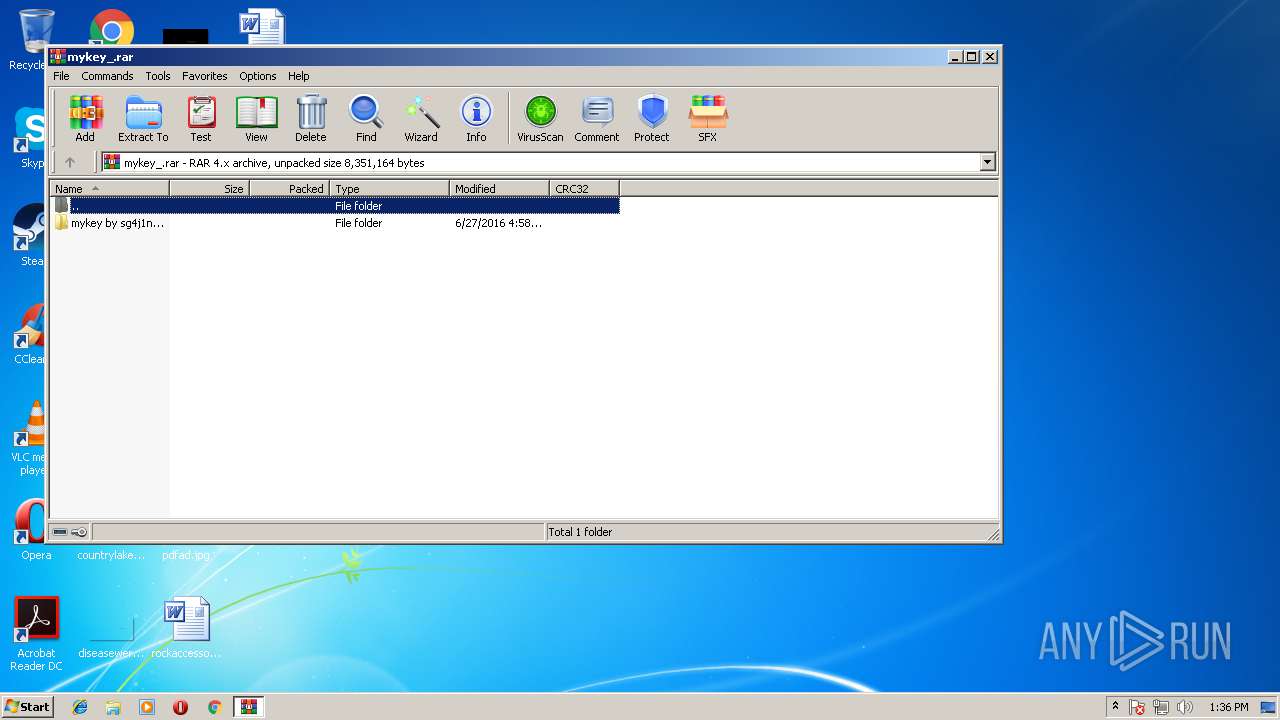
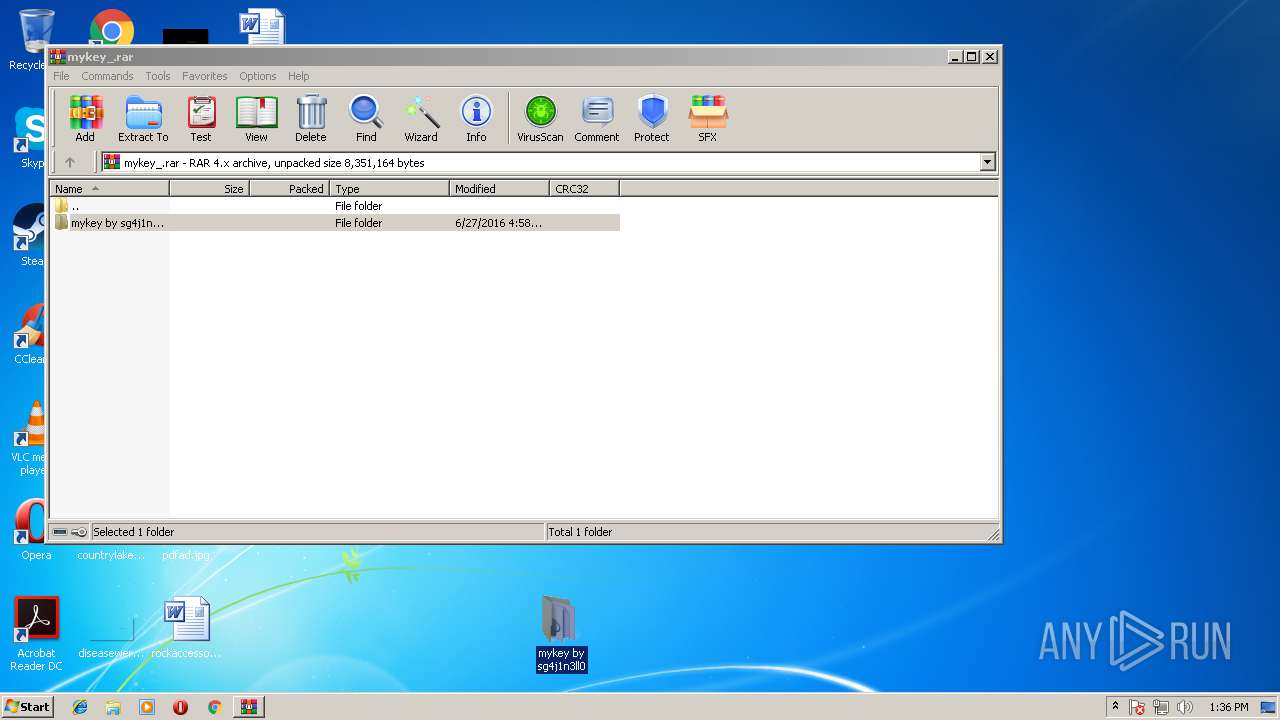
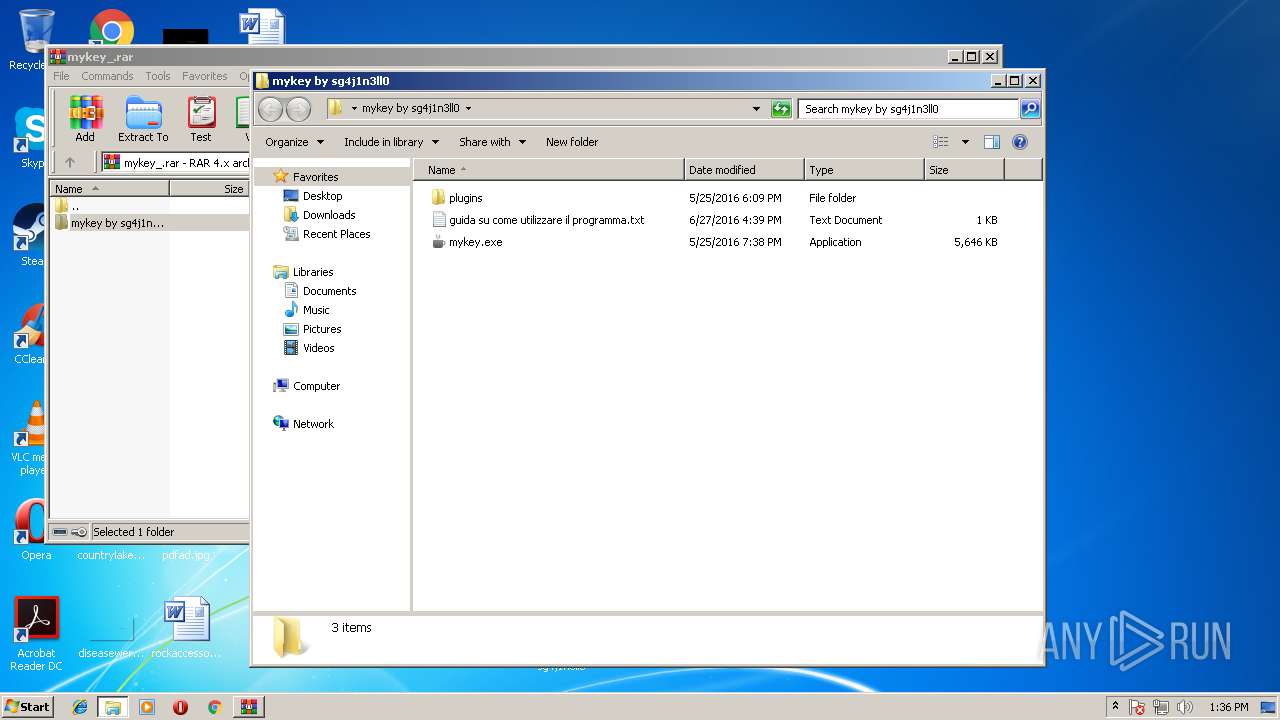
| File name: | mykey_.rar |
| Full analysis: | https://app.any.run/tasks/9e56710e-dd8e-4df8-97c1-bf783cc93c58 |
| Verdict: | Malicious activity |
| Analysis date: | August 22, 2018, 12:35:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 460F98C7960444845BE0F1710D92ED1D |
| SHA1: | FA3F6CE892A1888D720B513A12EEEB61E443F5BA |
| SHA256: | 7136CFB4343CAE6D67A7E7A7572C5E2EDB36F1ECA4B7EB24B202E632071EAE8F |
| SSDEEP: | 196608:PbwKK/IldXbJis+MIrBiOI/N/U9NcjY9FYMCFl:VK/IlddqMIrMOI/NMgjBBl |
MALICIOUS
Loads dropped or rewritten executable
- sl500f.exe (PID: 2648)
- acr122u.exe (PID: 4020)
- SearchProtocolHost.exe (PID: 1640)
Application was dropped or rewritten from another process
- mykey.exe (PID: 2264)
- acr122u.exe (PID: 4020)
- sl500f.exe (PID: 2648)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3368)
INFO
Dropped object may contain URL's
- WinRAR.exe (PID: 3368)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 656 |
|---|---|
| UncompressedSize: | 910 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2016:06:27 16:39:05 |
| PackingMethod: | Normal |
| ArchivedFileName: | mykey by sg4j1n3ll0\guida su come utilizzare il programma.txt |
Total processes
38
Monitored processes
5
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1640 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe12_ Global\UsGthrCtrlFltPipeMssGthrPipe12 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
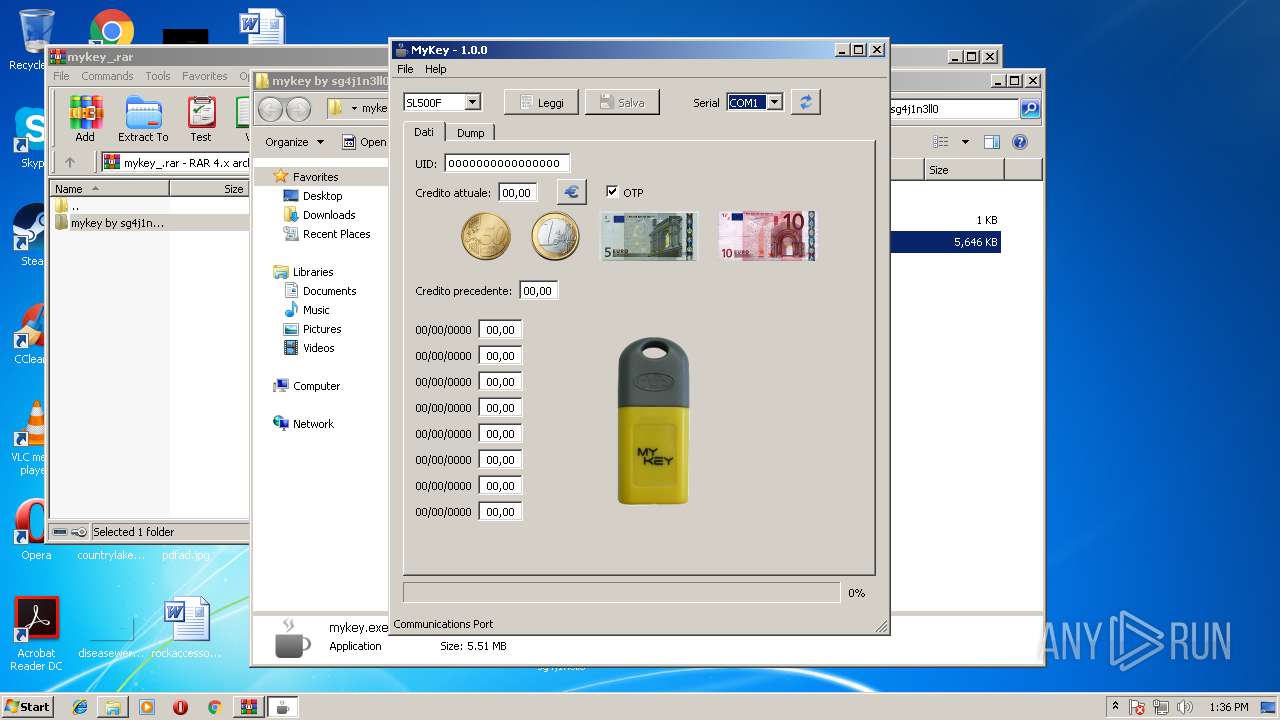
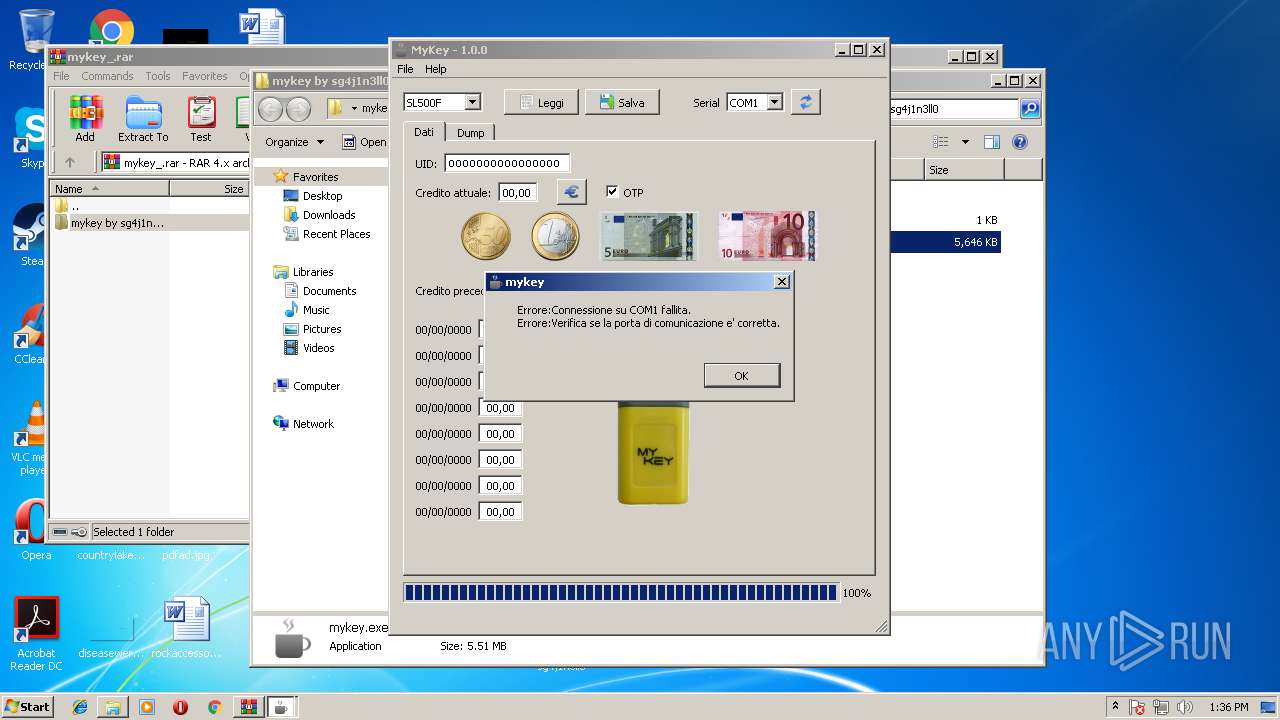
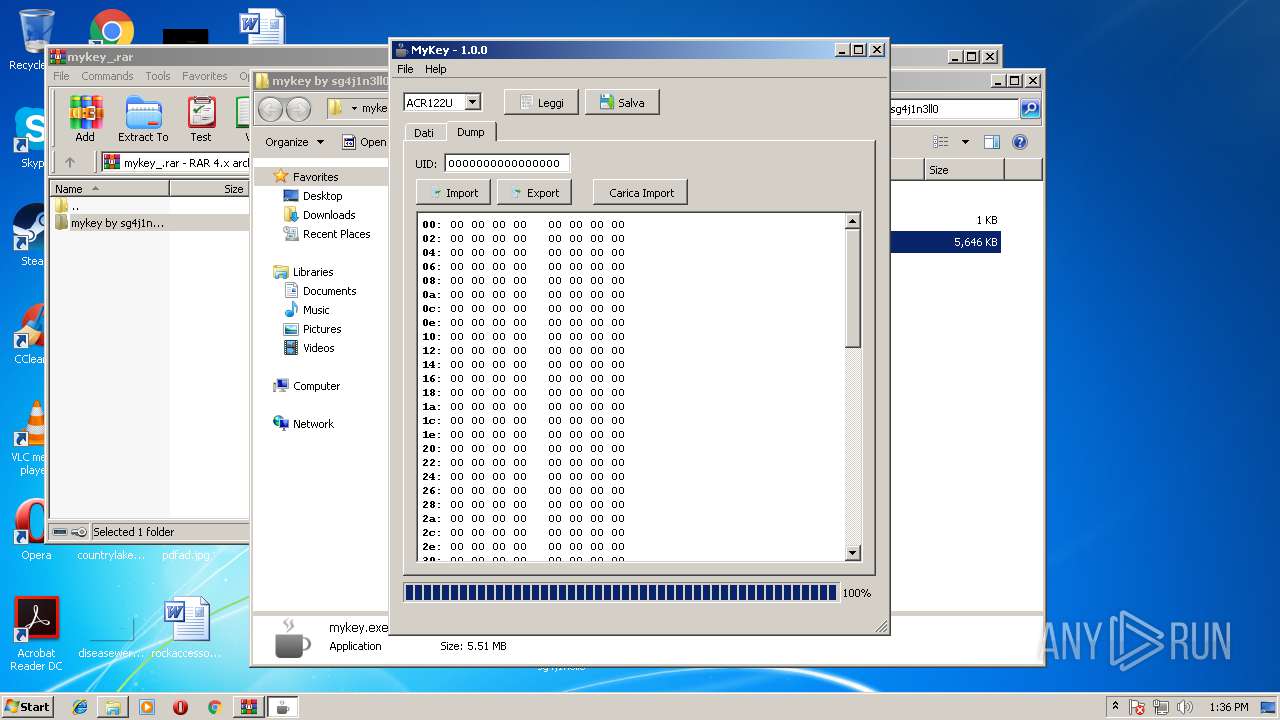
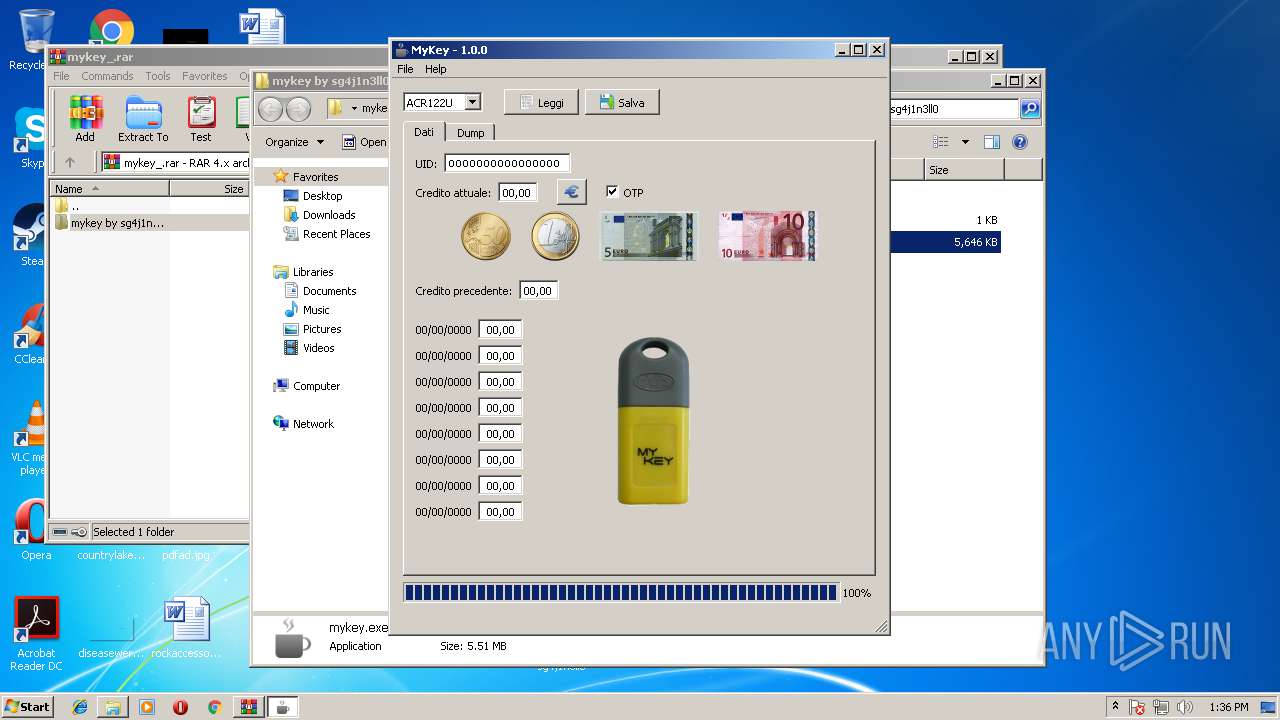
| 2264 | "C:\Users\admin\Desktop\mykey by sg4j1n3ll0\mykey.exe" | C:\Users\admin\Desktop\mykey by sg4j1n3ll0\mykey.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
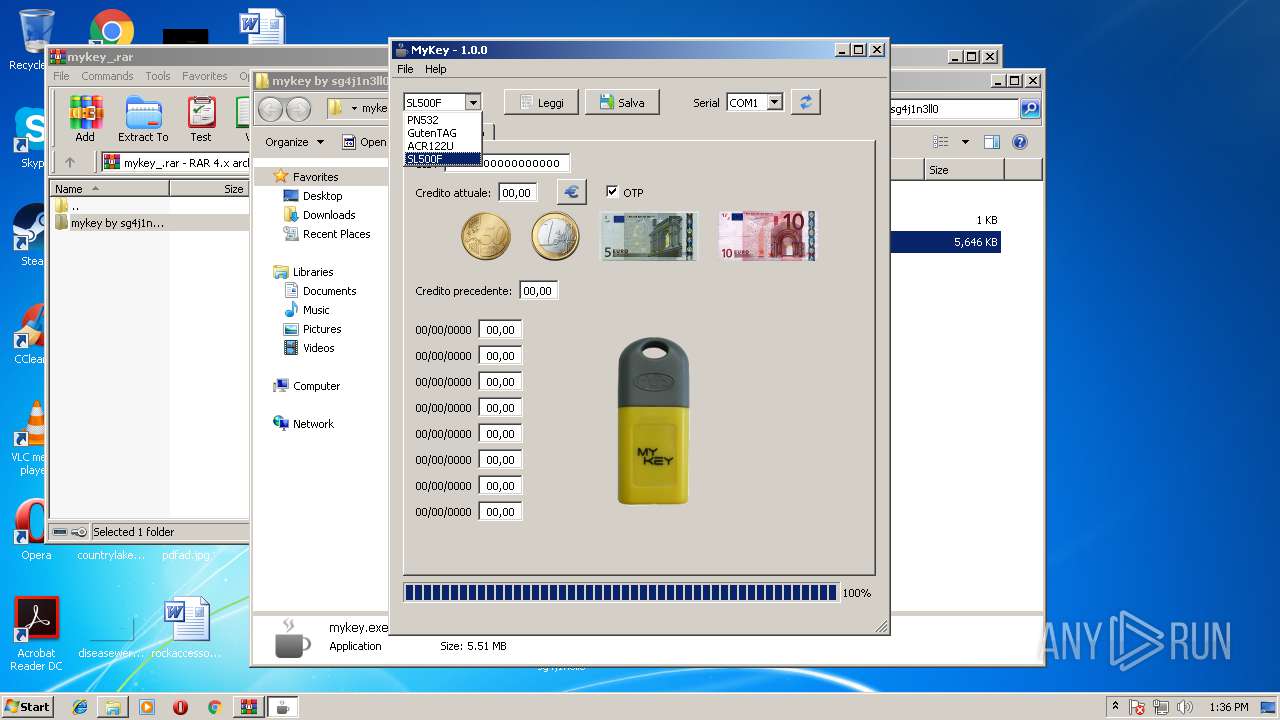
| 2648 | sl500f.exe -v 9940220 -b -o 1 -p SL500F | C:\Users\admin\Desktop\mykey by sg4j1n3ll0\plugins\SL500F\sl500f.exe | — | mykey.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3368 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\mykey_.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
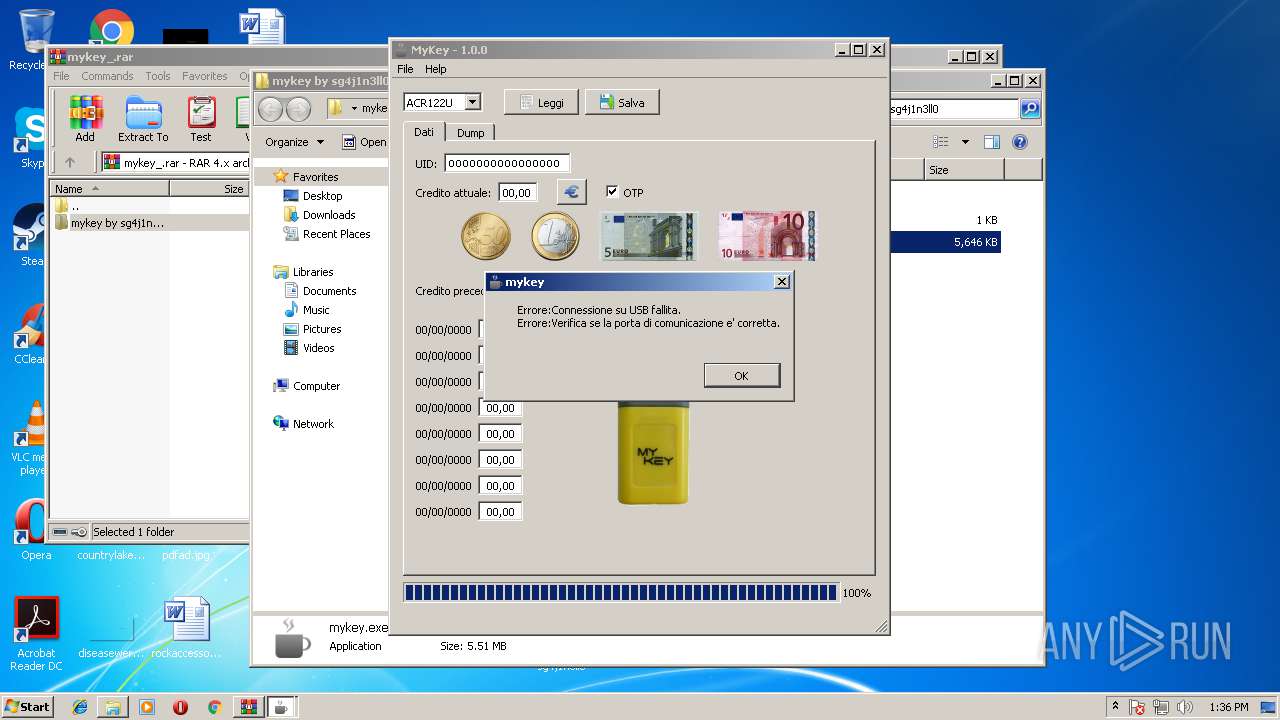
| 4020 | acr122u.exe -v 9940220 -b -p ACR122U | C:\Users\admin\Desktop\mykey by sg4j1n3ll0\plugins\ACR122U\acr122u.exe | — | mykey.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
785
Read events
771
Write events
14
Delete events
0
Modification events
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\59\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\mykey_.rar | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1640) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\59\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1640) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\59\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\msxml3r.dll,-1 |
Value: XML Document | |||
Executable files
17
Suspicious files
0
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3368 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3368.5508\mykey by sg4j1n3ll0\guida su come utilizzare il programma.txt | text | |
MD5:— | SHA256:— | |||
| 3368 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3368.5508\mykey by sg4j1n3ll0\plugins\ACR122U\acr122u.exe | executable | |
MD5:6F637F74E24B666058DF22DAF0843F6F | SHA256:41815BB79FDE882ADA92B050C5AFCFE9336D015BA7E36AF272F438F76B6E5A4D | |||
| 3368 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3368.5508\mykey by sg4j1n3ll0\plugins\ACR122U\pcre3.dll | executable | |
MD5:57CAC848FA14AE38F14F9441F8933282 | SHA256:8861AAAF4C65EB975B927292F7283BF1AEACDAE8428700E81DDFD0FA2C379D62 | |||
| 3368 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3368.5508\mykey by sg4j1n3ll0\plugins\ACR122U\libusb0.dll | executable | |
MD5:535779909A40B42F4F3E48598F5778A5 | SHA256:00CACA07869B19D10B370552AC7CC2F6F2EE246FC15DB11650F6CD3F4EF9B666 | |||
| 3368 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3368.5508\mykey by sg4j1n3ll0\plugins\ACR122U\libnfc.dll | executable | |
MD5:46670E4C1CD1DC0F3B33328D6C0B4990 | SHA256:ABF2CD53E1430D86AD3A252F17EBE6E7E2B0B0C6ECC8C76A97C1BB61D24374ED | |||
| 3368 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3368.5508\mykey by sg4j1n3ll0\plugins\SL500F\MasterCom.dll | executable | |
MD5:ACCAF687146081A35C249E7B17A3E49B | SHA256:11976024701F38C32609D8CA94B678C33227A3AD2EADD3B3138AE6F8498554FF | |||
| 3368 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3368.5508\mykey by sg4j1n3ll0\plugins\pn532\libnfc.dll | executable | |
MD5:46670E4C1CD1DC0F3B33328D6C0B4990 | SHA256:ABF2CD53E1430D86AD3A252F17EBE6E7E2B0B0C6ECC8C76A97C1BB61D24374ED | |||
| 3368 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3368.5508\mykey by sg4j1n3ll0\plugins\GutenTAG\LibUsbDotNet.dll | executable | |
MD5:E2F6B564CB161A24FBD82E93352D1C9B | SHA256:B589AF12FE5E014A73051DF1C84124282FF7F63230B26B07B879BC9F47726EA2 | |||
| 3368 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3368.5508\mykey by sg4j1n3ll0\plugins\GutenTAG\LibUsbDotNet.xml | xml | |
MD5:97C442B9A4830661736AEE13794FA5EE | SHA256:0C0C357BEA31A90D7313BC156B565813537DC7F71BD49735ECFF21D680D0095F | |||
| 3368 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3368.5508\mykey by sg4j1n3ll0\plugins\SL500F\libnfc.dll | executable | |
MD5:46670E4C1CD1DC0F3B33328D6C0B4990 | SHA256:ABF2CD53E1430D86AD3A252F17EBE6E7E2B0B0C6ECC8C76A97C1BB61D24374ED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
mykey.exe | Could not parse application stylesheet
|
mykey.exe | libpng warning: iCCP: known incorrect sRGB profile
|
mykey.exe | "Find 1 Serial Port(s):"
|
mykey.exe | Name : "COM1"
|
mykey.exe | Description : "Communications Port"
|
mykey.exe | Manufacturer: "(Standard port types)"
|
mykey.exe | SystemLocation: "\\\\.\\COM1"
|
mykey.exe | "COM1\t----\t(Standard port types) Communications Port"
|
mykey.exe | "C:/Users/admin/Desktop/mykey by sg4j1n3ll0"
|
mykey.exe | "C:/Users/admin/Desktop/mykey by sg4j1n3ll0"
|