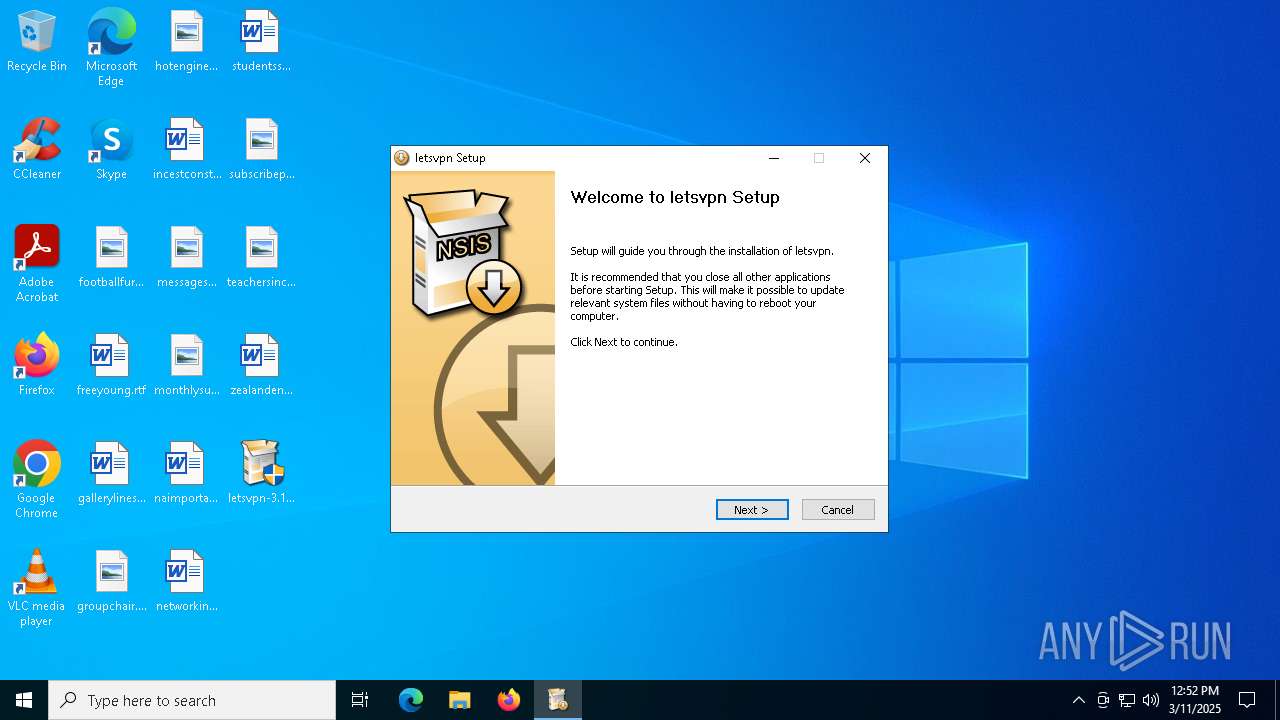
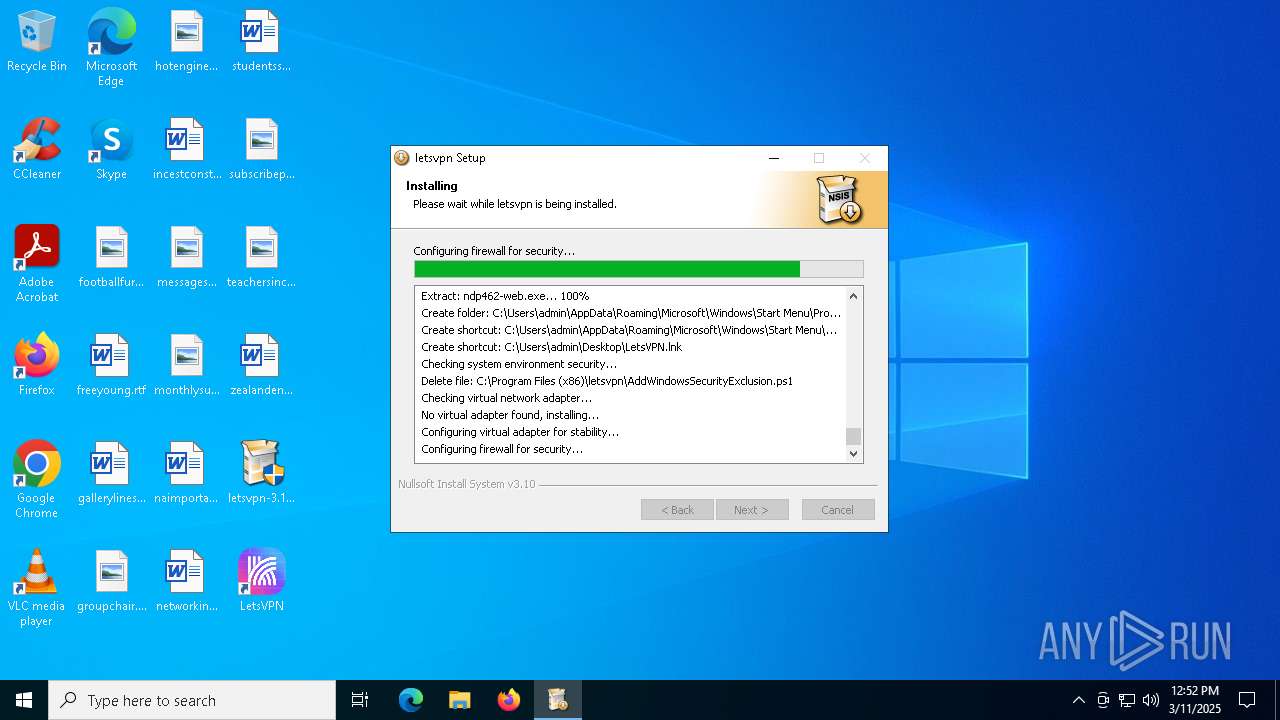
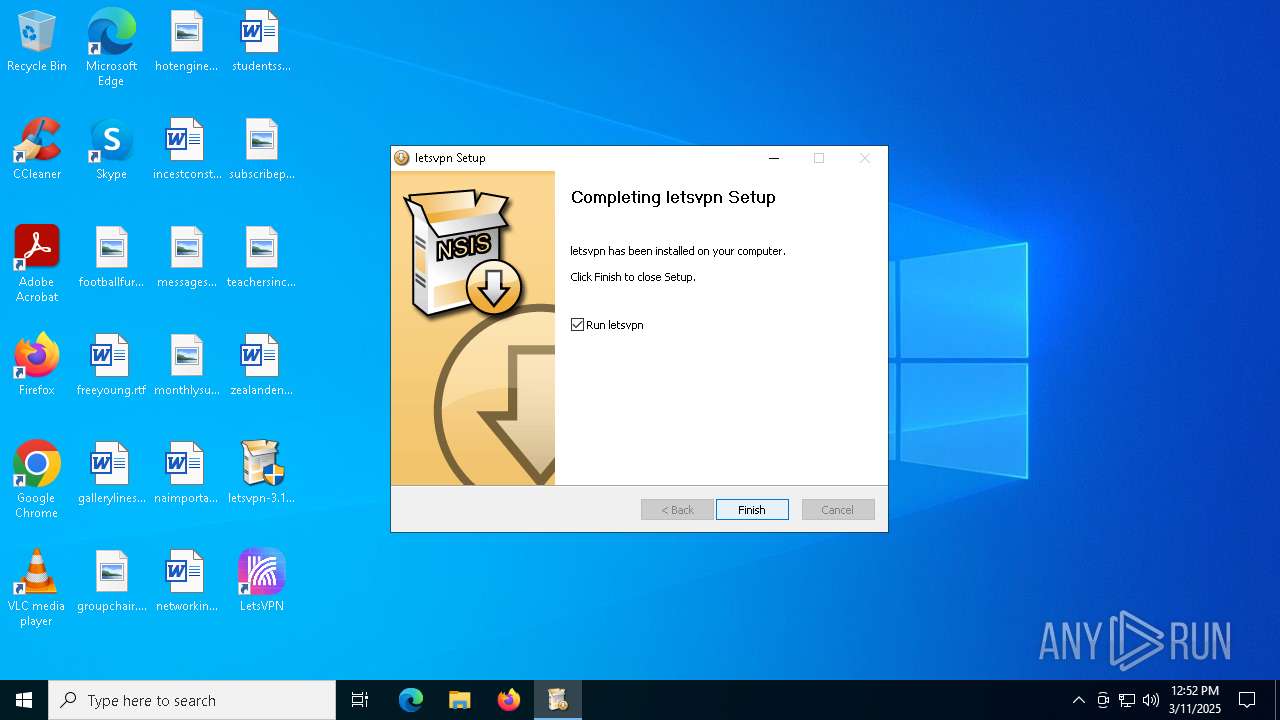
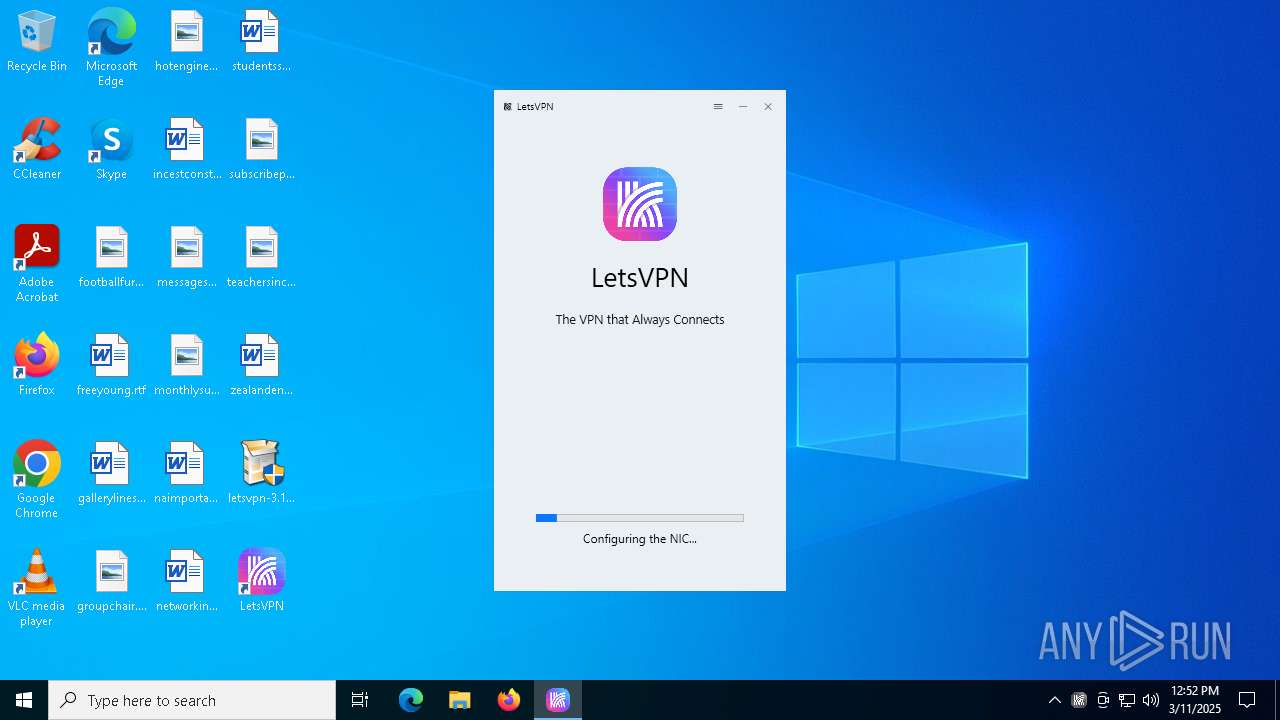
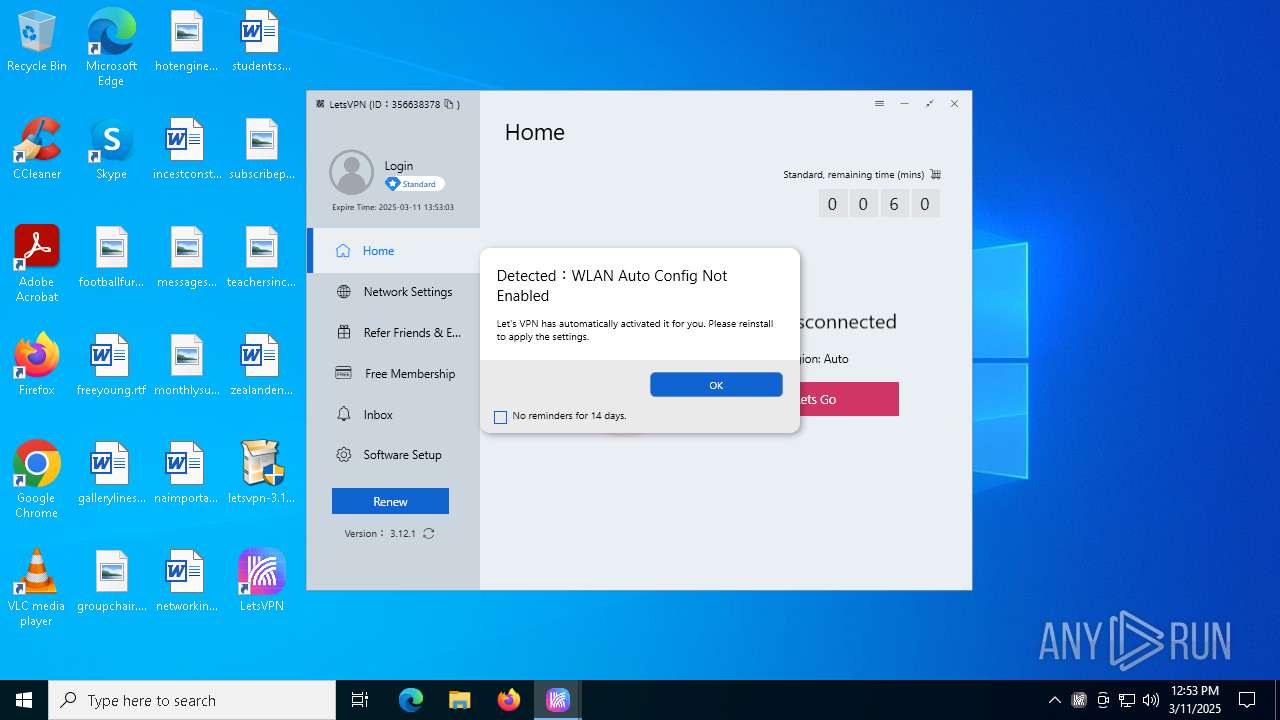
| File name: | letsvpn-3.12.1.exe |
| Full analysis: | https://app.any.run/tasks/8914872e-bb2f-44ca-b926-ef9e555246a3 |
| Verdict: | Malicious activity |
| Analysis date: | March 11, 2025, 12:52:11 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 24CDFD07594672A081A669D65DE0676B |
| SHA1: | C881A264C7550858F4893710BDCE4B96BEC79C1C |
| SHA256: | 711ACEF8D29ECECE360D6454F82E5C42BBE12F26C0CE260EC0F643750534FAEF |
| SSDEEP: | 196608:RBVmKbekOisgbxI1VfVOuWIzU1K2zZawE:RBtbekOPgb6dOXSUFZDE |
MALICIOUS
Changes powershell execution policy (Bypass)
- letsvpn-3.12.1.exe (PID: 7608)
Bypass execution policy to execute commands
- powershell.exe (PID: 6264)
SUSPICIOUS
Executable content was dropped or overwritten
- letsvpn-3.12.1.exe (PID: 7608)
- tapinstall.exe (PID: 4428)
- drvinst.exe (PID: 7360)
- drvinst.exe (PID: 7836)
Malware-specific behavior (creating "System.dll" in Temp)
- letsvpn-3.12.1.exe (PID: 7608)
Drops a system driver (possible attempt to evade defenses)
- letsvpn-3.12.1.exe (PID: 7608)
- tapinstall.exe (PID: 4428)
- drvinst.exe (PID: 7836)
- drvinst.exe (PID: 7360)
There is functionality for taking screenshot (YARA)
- letsvpn-3.12.1.exe (PID: 7608)
The process creates files with name similar to system file names
- letsvpn-3.12.1.exe (PID: 7608)
Process drops legitimate windows executable
- letsvpn-3.12.1.exe (PID: 7608)
The process executes Powershell scripts
- letsvpn-3.12.1.exe (PID: 7608)
Starts POWERSHELL.EXE for commands execution
- letsvpn-3.12.1.exe (PID: 7608)
Process uses IPCONFIG to discover network configuration
- cmd.exe (PID: 7488)
Starts CMD.EXE for commands execution
- LetsPRO.exe (PID: 3884)
- letsvpn-3.12.1.exe (PID: 7608)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 7916)
- cmd.exe (PID: 8144)
- cmd.exe (PID: 5384)
- cmd.exe (PID: 4188)
- cmd.exe (PID: 1764)
Suspicious use of NETSH.EXE
- LetsPRO.exe (PID: 3884)
Executes as Windows Service
- WmiApSrv.exe (PID: 8108)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 6808)
Process uses ARP to discover network configuration
- cmd.exe (PID: 2284)
INFO
The sample compiled with english language support
- letsvpn-3.12.1.exe (PID: 7608)
- tapinstall.exe (PID: 4428)
- drvinst.exe (PID: 7836)
- drvinst.exe (PID: 7360)
Checks supported languages
- letsvpn-3.12.1.exe (PID: 7608)
Reads the computer name
- letsvpn-3.12.1.exe (PID: 7608)
Create files in a temporary directory
- letsvpn-3.12.1.exe (PID: 7608)
Creates files in the program directory
- letsvpn-3.12.1.exe (PID: 7608)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6264)
- LetsPRO.exe (PID: 3884)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6264)
Prints a route via ROUTE.EXE
- ROUTE.EXE (PID: 8152)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:30 16:55:15+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26112 |
| InitializedDataSize: | 139776 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x351c |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.12.1.0 |
| ProductVersionNumber: | 3.12.1.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Letsgo Network Incorporated |
| FileDescription: | LetsVPN Setup EXE |
| FileVersion: | 3.12.1.0 |
| LegalCopyright: | Copyright (c) 2024 |
| ProductName: | LetsVPN |
| ProductVersion: | 3.12.1.0 |
Total processes
188
Monitored processes
46
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | netsh advfirewall firewall Delete rule name=LetsPRO | C:\Windows\SysWOW64\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1764 | cmd /c netsh advfirewall firewall Delete rule name=LetsVPN | C:\Windows\SysWOW64\cmd.exe | — | letsvpn-3.12.1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2096 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | tapinstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2284 | "cmd.exe" /C arp -a | C:\Windows\SysWOW64\cmd.exe | — | LetsPRO.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2320 | netsh advfirewall firewall Delete rule name=LetsPRO.exe | C:\Windows\SysWOW64\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2320 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3884 | "C:\Program Files (x86)\letsvpn\app-3.12.1\LetsPRO.exe" | C:\Program Files (x86)\letsvpn\app-3.12.1\LetsPRO.exe | LetsPRO.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: LetsVPN Version: 3.12.0 Modules
| |||||||||||||||
| 3896 | arp -a | C:\Windows\SysWOW64\ARP.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Arp Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
47 108
Read events
46 920
Write events
164
Delete events
24
Modification events
| (PID) Process: | (7608) letsvpn-3.12.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\lets |
| Operation: | write | Name: | InstallTimeStamp |
Value: 20250311125235.105 | |||
| (PID) Process: | (7608) letsvpn-3.12.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\lets |
| Operation: | write | Name: | InstallNewVersion |
Value: 3.12.1 | |||
| (PID) Process: | (4428) tapinstall.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\Setup\SetupapiLogStatus |
| Operation: | write | Name: | setupapi.dev.log |
Value: 4096 | |||
| (PID) Process: | (7360) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\tap0901 |
| Operation: | write | Name: | Owners |
Value: oem1.inf | |||
| (PID) Process: | (7360) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Setup\PnpLockdownFiles\%SystemRoot%/System32/drivers/tap0901.sys |
| Operation: | write | Name: | Owners |
Value: oem1.inf | |||
| (PID) Process: | (7360) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\oemvista.inf_amd64_662fd96dfdced4ae\Descriptors\tap0901 |
| Operation: | write | Name: | Configuration |
Value: tap0901.ndi | |||
| (PID) Process: | (7360) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\oemvista.inf_amd64_662fd96dfdced4ae\Descriptors\tap0901 |
| Operation: | write | Name: | Manufacturer |
Value: %provider% | |||
| (PID) Process: | (7360) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\oemvista.inf_amd64_662fd96dfdced4ae\Descriptors\tap0901 |
| Operation: | write | Name: | Description |
Value: %devicedescription% | |||
| (PID) Process: | (7360) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\oemvista.inf_amd64_662fd96dfdced4ae\Configurations\tap0901.ndi |
| Operation: | write | Name: | Service |
Value: tap0901 | |||
| (PID) Process: | (7360) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\oemvista.inf_amd64_662fd96dfdced4ae\Configurations\tap0901.ndi |
| Operation: | write | Name: | ConfigScope |
Value: 5 | |||
Executable files
227
Suspicious files
43
Text files
18
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7608 | letsvpn-3.12.1.exe | C:\Users\admin\AppData\Local\Temp\nsxBC4E.tmp\modern-header.bmp | image | |
MD5:5ACF495828FEAE7F85E006B7774AF497 | SHA256:6CFEBB59F0BA1B9F1E8D7AA6387F223A468EB2FF74A9ED3C3F4BB688C2B6455E | |||
| 7608 | letsvpn-3.12.1.exe | C:\Program Files (x86)\letsvpn\driver\tap0901.sys | executable | |
MD5:C10CCDEC5D7AF458E726A51BB3CDC732 | SHA256:589C5667B1602837205DA8EA8E92FE13F8C36048B293DF931C99B39641052253 | |||
| 7608 | letsvpn-3.12.1.exe | C:\Program Files (x86)\letsvpn\app-3.12.1\DeltaCompressionDotNet.PatchApi.dll | executable | |
MD5:839E774D3E0B80A9C407A1269D66D11A | SHA256:ABB8794A52C85A16A4CAD28C99FEA73AE4730ED7B2F708EF58894CC1791217C9 | |||
| 7608 | letsvpn-3.12.1.exe | C:\Program Files (x86)\letsvpn\driver\OemVista.inf | binary | |
MD5:26009F092BA352C1A64322268B47E0E3 | SHA256:150EF8EB07532146F833DC020C02238161043260B8A565C3CFCB2365BAD980D9 | |||
| 7608 | letsvpn-3.12.1.exe | C:\Program Files (x86)\letsvpn\driver\tapinstall.exe | executable | |
MD5:1E3CF83B17891AEE98C3E30012F0B034 | SHA256:9F45A39015774EEAA2A6218793EDC8E6273EB9F764F3AEDEE5CF9E9CCACDB53F | |||
| 7608 | letsvpn-3.12.1.exe | C:\Users\admin\AppData\Local\Temp\nsxBC4E.tmp\nsDialogs.dll | executable | |
MD5:B7D61F3F56ABF7B7FF0D4E7DA3AD783D | SHA256:89A82C4849C21DFE765052681E1FAD02D2D7B13C8B5075880C52423DCA72A912 | |||
| 7608 | letsvpn-3.12.1.exe | C:\Program Files (x86)\letsvpn\Update.exe | executable | |
MD5:A26437B62A28EF9F216BE2CC7035D2DF | SHA256:14776718CBF032A64A3312DACE8A87E06DA8FDC06CB7C067707674B8E68DC7F9 | |||
| 7608 | letsvpn-3.12.1.exe | C:\Program Files (x86)\letsvpn\app-3.12.1\CommunityToolkit.Mvvm.dll | executable | |
MD5:C5485166B86B4CD6DE97C4DC8D0FBEFB | SHA256:21678620BF5E7B4C8481270594B0A36615BE6152CA7A9396487364712236A3D5 | |||
| 7608 | letsvpn-3.12.1.exe | C:\Program Files (x86)\letsvpn\app-3.12.1\DeltaCompressionDotNet.dll | executable | |
MD5:B6634DCB0B38617B4345A4346DA620C7 | SHA256:8A397246E984B4FD51A15C5E71BD217A92061F9AEC3CB6CFCB938834E9DD4B65 | |||
| 7608 | letsvpn-3.12.1.exe | C:\Users\admin\AppData\Local\Temp\nsxBC4E.tmp\modern-wizard.bmp | image | |
MD5:7F8E1969B0874C8FB9AB44FC36575380 | SHA256:076221B4527FF13C3E1557ABBBD48B0CB8E5F7D724C6B9171C6AADADB80561DD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
68
DNS requests
26
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7940 | backgroundTaskHost.exe | GET | — | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | unknown |
7940 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://crl3.digicert.com/DigiCertGlobalRootG2.crl | unknown | — | — | unknown |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
1280 | SIHClient.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
1280 | SIHClient.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3884 | LetsPRO.exe | GET | 101 | 47.130.76.214:80 | http://ws-ap1.pusher.com/app/4fc436ef36f4026102d7?protocol=5&client=pusher-dotnet-client&version=1.1.2 | unknown | — | — | whitelisted |
3884 | LetsPRO.exe | GET | 200 | 151.101.194.133:80 | http://ocsp.globalsign.com/gsgccr45codesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBTLuA3ygnKW%2F7xuSx%2F09F%2BhHVuEUQQU2rONwCSQo2t30wygWd0hZ2R2C3gCDFxLOsCV0WoYXJJrOQ%3D%3D | unknown | — | — | unknown |
3884 | LetsPRO.exe | GET | 200 | 151.101.194.133:80 | http://ocsp.globalsign.com/codesigningrootr45/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEQCBTkIXoSl%2F7VrM1Bf4ka11 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
— | — | 192.168.100.255:137 | — | — | — | unknown |
5496 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
5496 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6544 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | unknown |
3216 | svchost.exe | 20.198.162.78:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
7940 | backgroundTaskHost.exe | 20.31.169.57:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| unknown |
settings-win.data.microsoft.com |
| unknown |
login.live.com |
| unknown |
ocsp.digicert.com |
| unknown |
client.wns.windows.com |
| unknown |
arc.msn.com |
| unknown |
crl3.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| unknown |
www.microsoft.com |
| unknown |
fe3cr.delivery.mp.microsoft.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3884 | LetsPRO.exe | Not Suspicious Traffic | INFO [ANY.RUN] Websocket Upgrade Request |