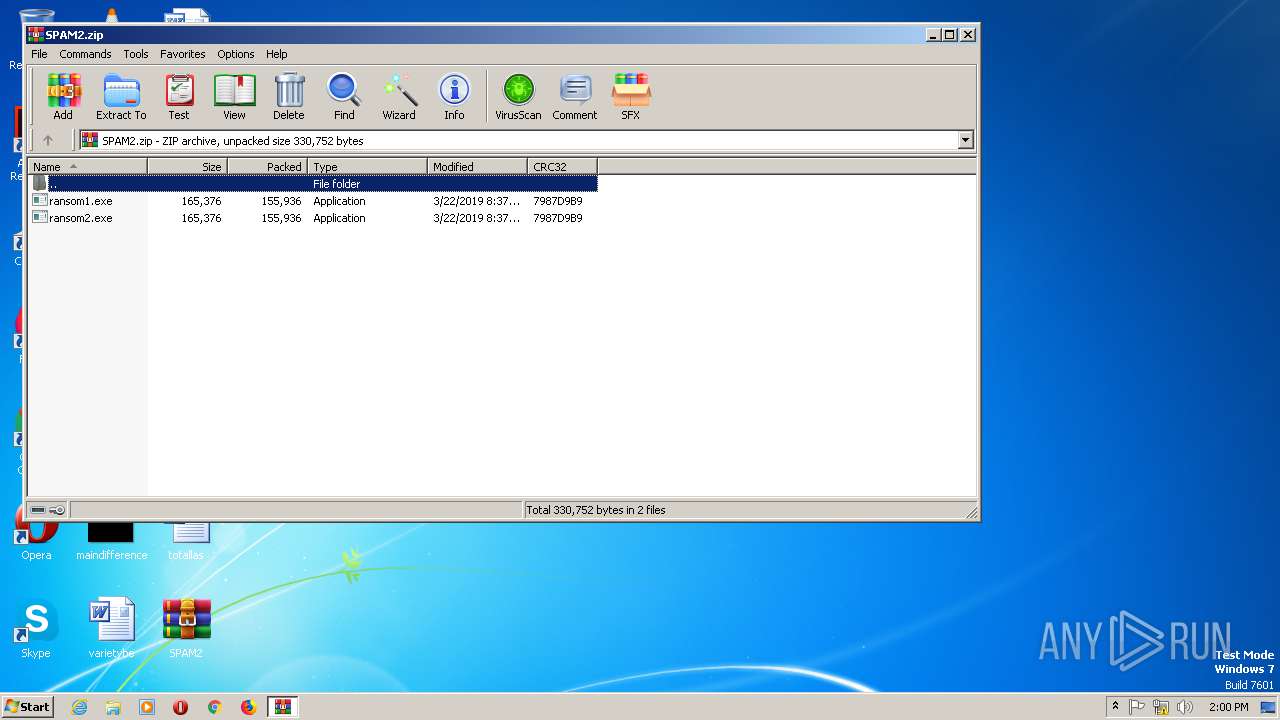
| File name: | SPAM2.zip |
| Full analysis: | https://app.any.run/tasks/c0ef9114-89f1-41b6-b4f3-aefc20464183 |
| Verdict: | Malicious activity |
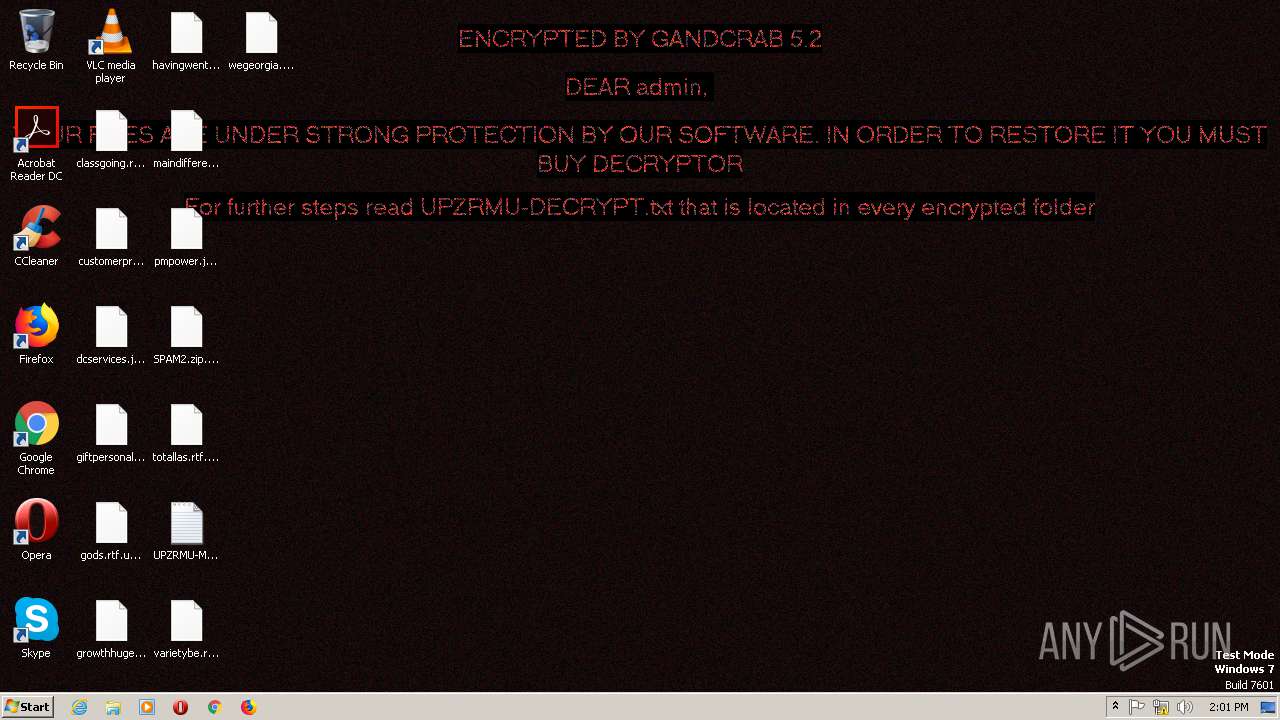
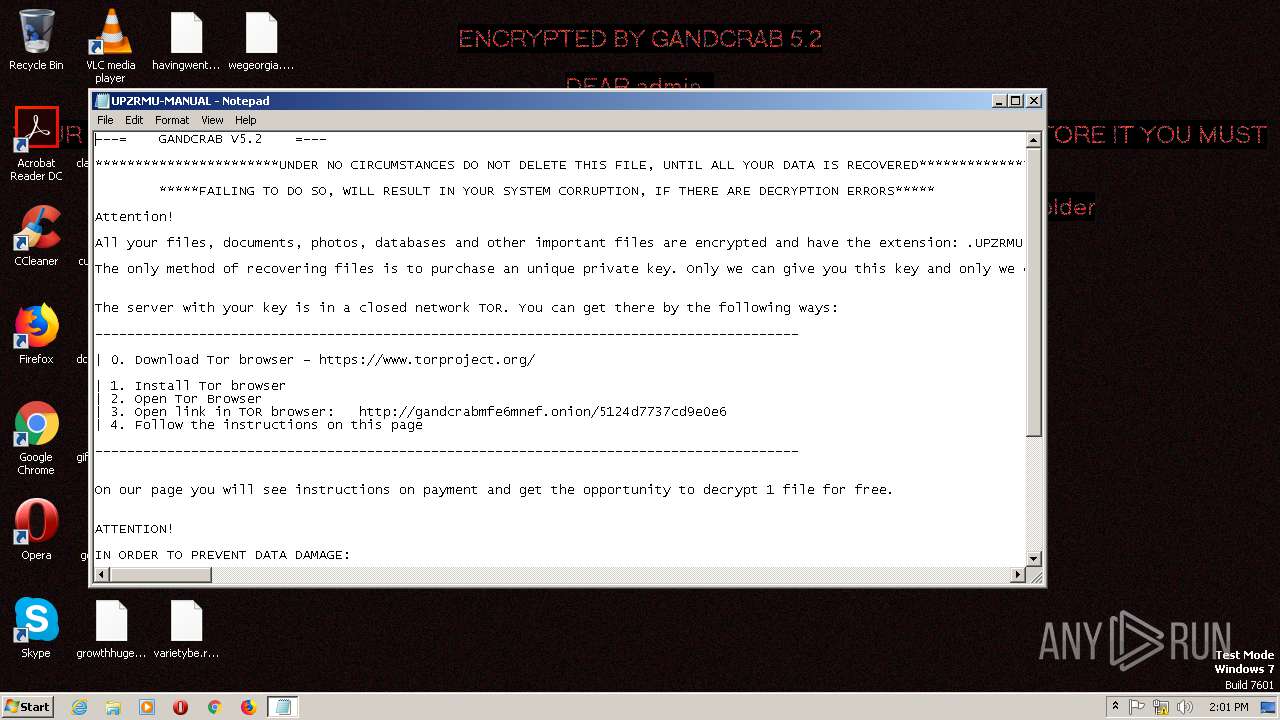
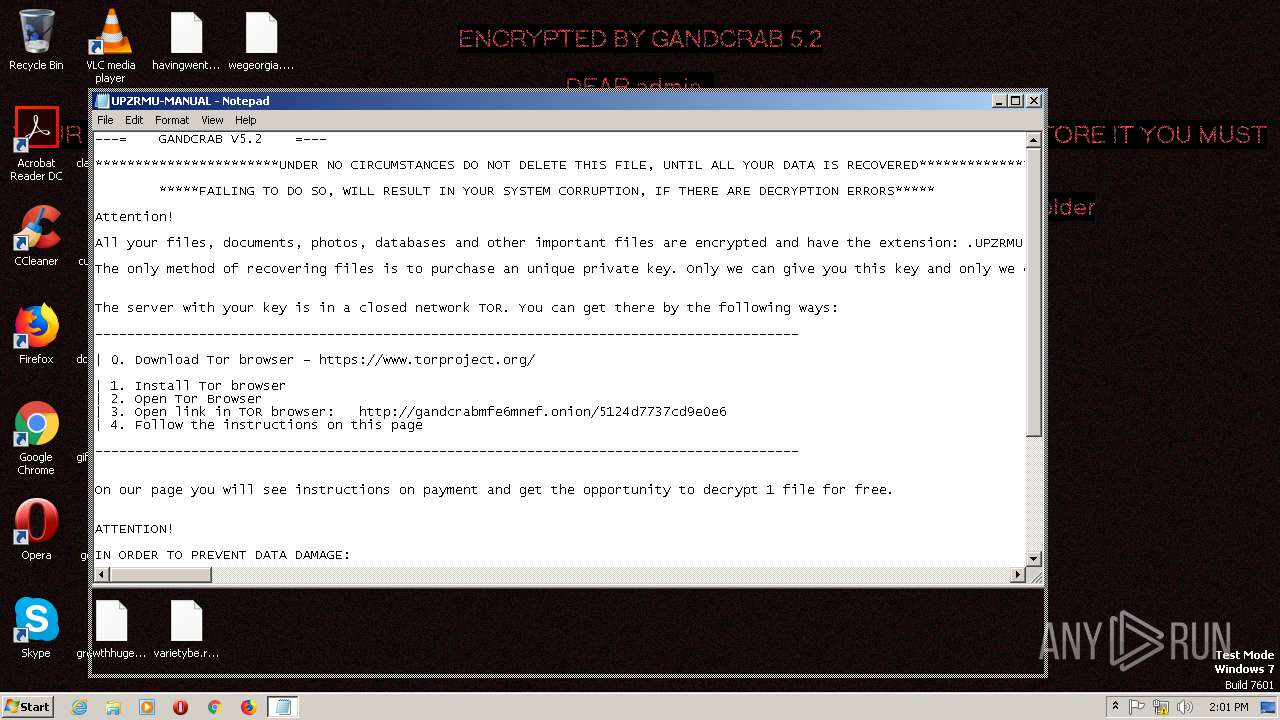
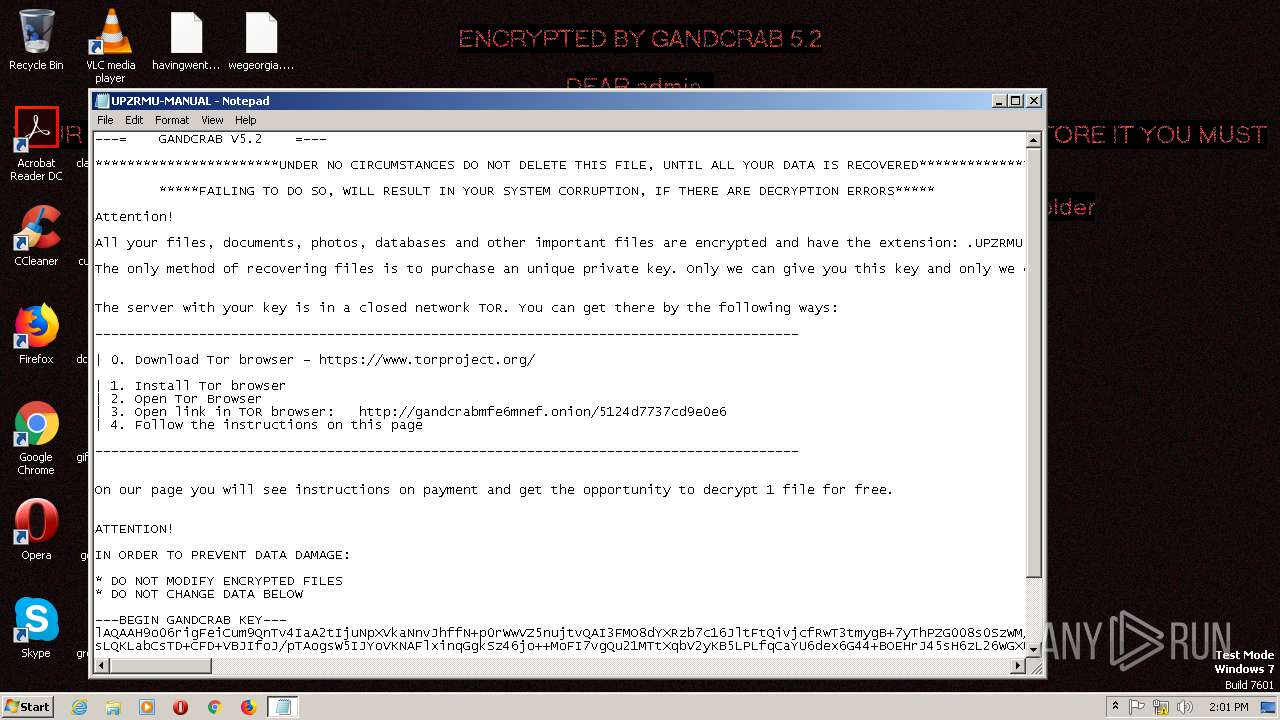
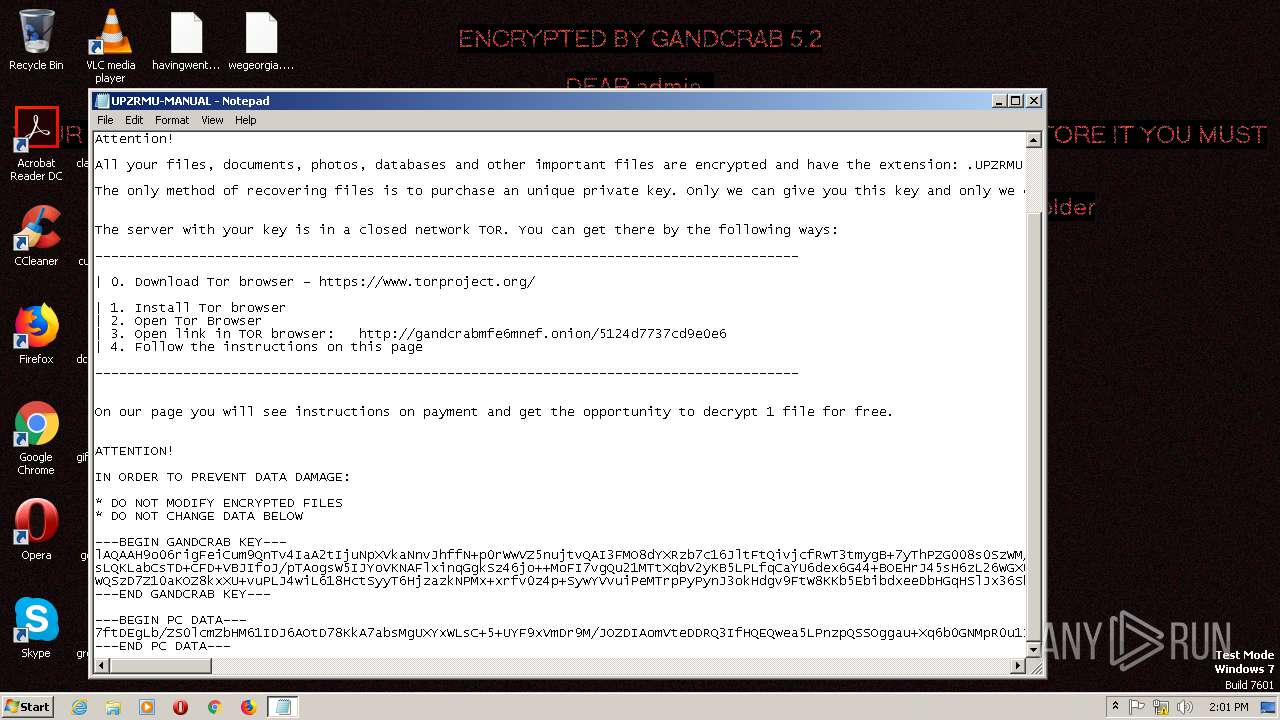
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | March 22, 2019, 13:59:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 8B0A34A4E85C7BF0FEA3CA339D7A947E |
| SHA1: | CB08899315BB2272807D2F6D28037D28145B6673 |
| SHA256: | 71148F8DBE96D81653029E6AF3CBEFDC72FE8702CEB9590C1313617C23D57FEA |
| SSDEEP: | 6144:RHaNlc0yOzcXx/MS67uiTcSiHaNlc0yOzcXx/MS67uiTcSL:4yO6BiYStyO6BiYSL |
MALICIOUS
Application was dropped or rewritten from another process
- ransom1.exe (PID: 1216)
Writes file to Word startup folder
- ransom1.exe (PID: 1216)
Renames files like Ransomware
- ransom1.exe (PID: 1216)
Dropped file may contain instructions of ransomware
- ransom1.exe (PID: 1216)
Deletes shadow copies
- cmd.exe (PID: 2116)
Changes settings of System certificates
- ransom1.exe (PID: 1216)
GANDCRAB detected
- ransom1.exe (PID: 1216)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1844)
Creates files in the program directory
- ransom1.exe (PID: 1216)
Reads the machine GUID from the registry
- WinRAR.exe (PID: 1844)
Starts CMD.EXE for commands execution
- ransom1.exe (PID: 1216)
Creates files in the user directory
- ransom1.exe (PID: 1216)
INFO
Dropped object may contain TOR URL's
- ransom1.exe (PID: 1216)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:03:22 09:37:14 |
| ZipCRC: | 0x7987d9b9 |
| ZipCompressedSize: | 155936 |
| ZipUncompressedSize: | 165376 |
| ZipFileName: | ransom1.exe |
Total processes
37
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1216 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1844.23574\ransom1.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1844.23574\ransom1.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1844 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\SPAM2.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2116 | "C:\Windows\system32\cmd.exe" /c vssadmin delete shadows /all /quiet | C:\Windows\SysWOW64\cmd.exe | — | ransom1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2436 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\UPZRMU-MANUAL.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2624 | vssadmin delete shadows /all /quiet | C:\Windows\SysWOW64\vssadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
597
Read events
541
Write events
55
Delete events
1
Modification events
| (PID) Process: | (1844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1844) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\65\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\SPAM2.zip | |||
| (PID) Process: | (1844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
2
Suspicious files
2 208
Text files
218
Unknown types
66
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1216 | ransom1.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | — | |
MD5:— | SHA256:— | |||
| 1216 | ransom1.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\GlobData | — | |
MD5:— | SHA256:— | |||
| 1216 | ransom1.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\GlobSettings | — | |
MD5:— | SHA256:— | |||
| 1844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1844.23574\ransom1.exe | executable | |
MD5:— | SHA256:— | |||
| 1216 | ransom1.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\addressbook.acrodata | — | |
MD5:— | SHA256:— | |||
| 1844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1844.23574\ransom2.exe | executable | |
MD5:— | SHA256:— | |||
| 1216 | ransom1.exe | C:\$Recycle.Bin\S-1-5-21-3896776584-4254864009-862391680-1000\UPZRMU-MANUAL.txt | text | |
MD5:— | SHA256:— | |||
| 1216 | ransom1.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\CRLCache\0FDED5CEB68C302B1CDB2BDDD9D0000E76539CB0.crl | — | |
MD5:— | SHA256:— | |||
| 1216 | ransom1.exe | C:\Users\admin\AppData\Local\VirtualStore\UPZRMU-MANUAL.txt | text | |
MD5:— | SHA256:— | |||
| 1216 | ransom1.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\CRLCache\CE338828149963DCEA4CD26BB86F0363B4CA0BA5.crl | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
1
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1216 | ransom1.exe | GET | 301 | 107.173.49.208:80 | http://www.kakaocorp.link/ | US | html | 162 b | malicious |
1216 | ransom1.exe | POST | 404 | 107.173.49.208:443 | https://www.kakaocorp.link/content/graphic/kathzu.bmp | US | html | 603 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1216 | ransom1.exe | 107.173.49.208:80 | www.kakaocorp.link | ColoCrossing | US | malicious |
1216 | ransom1.exe | 107.173.49.208:443 | www.kakaocorp.link | ColoCrossing | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.kakaocorp.link |
| malicious |
Threats
1 ETPRO signatures available at the full report