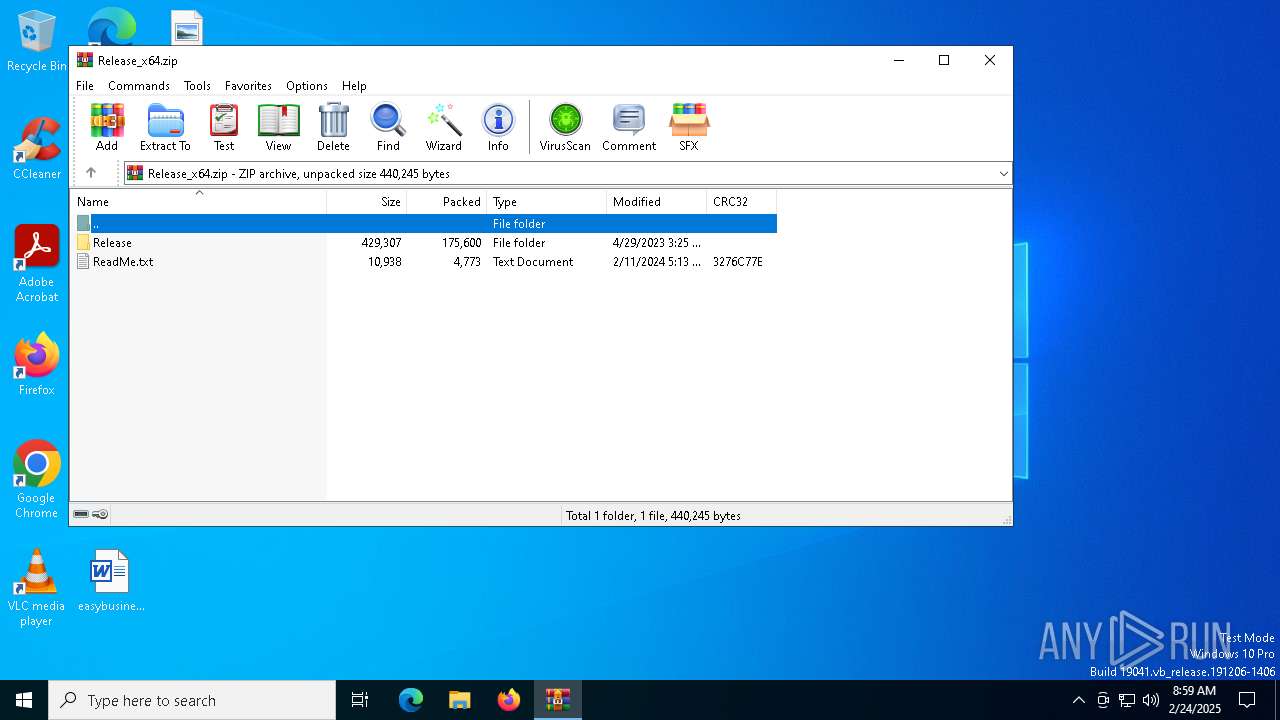
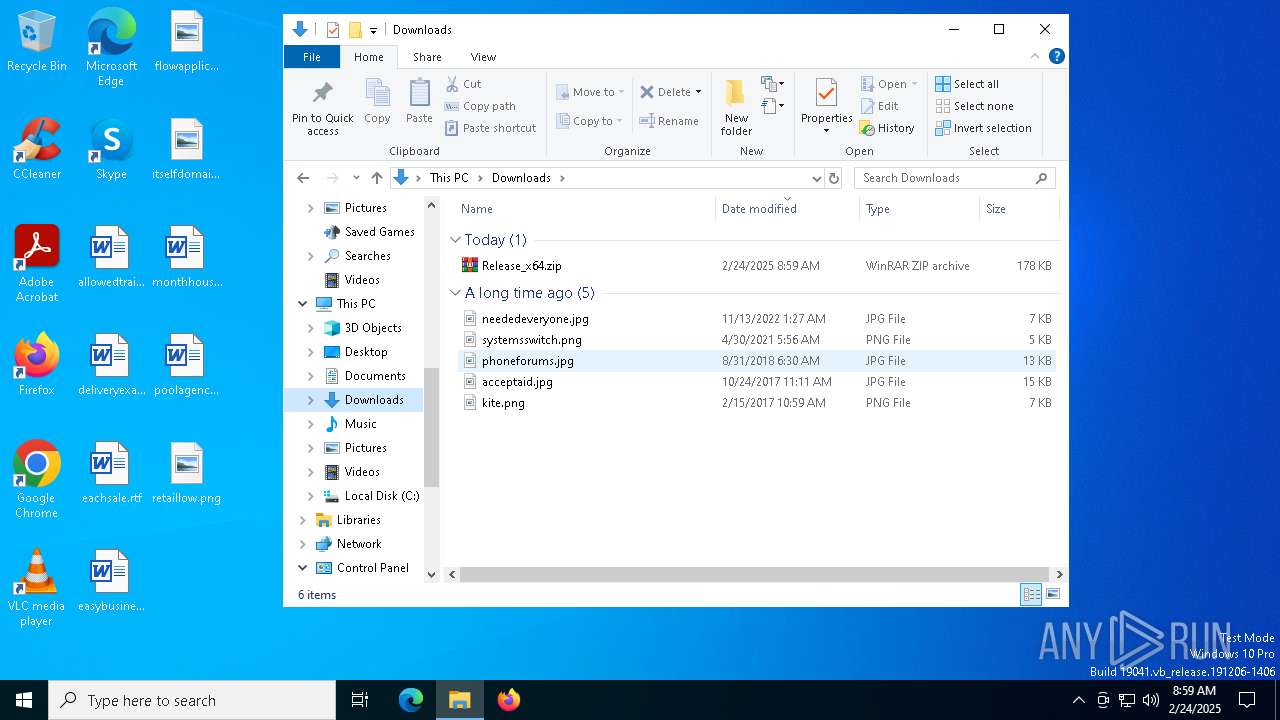
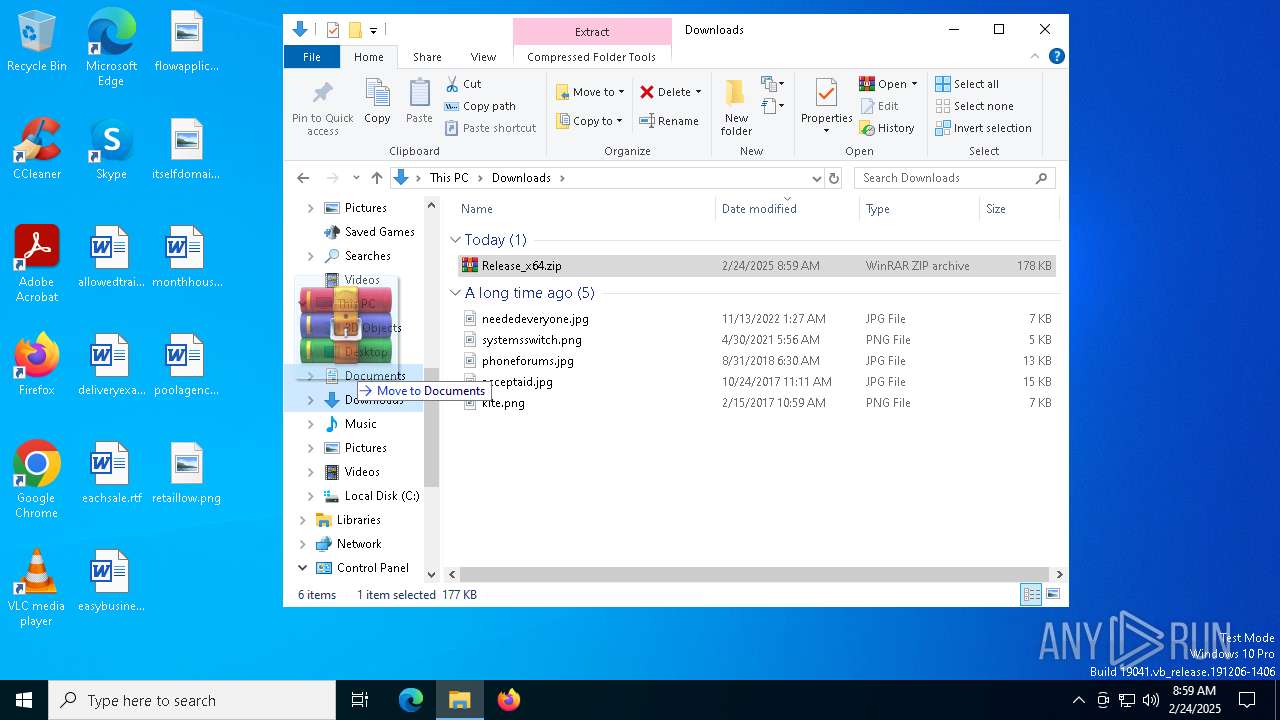
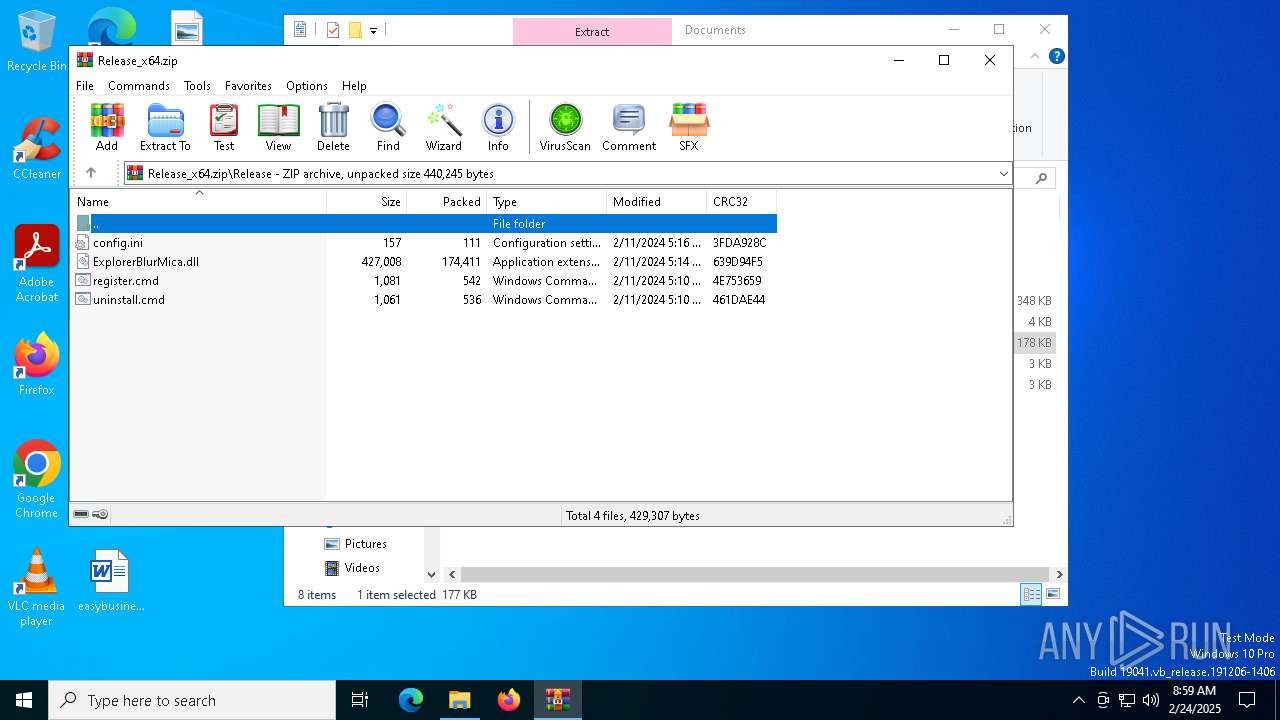
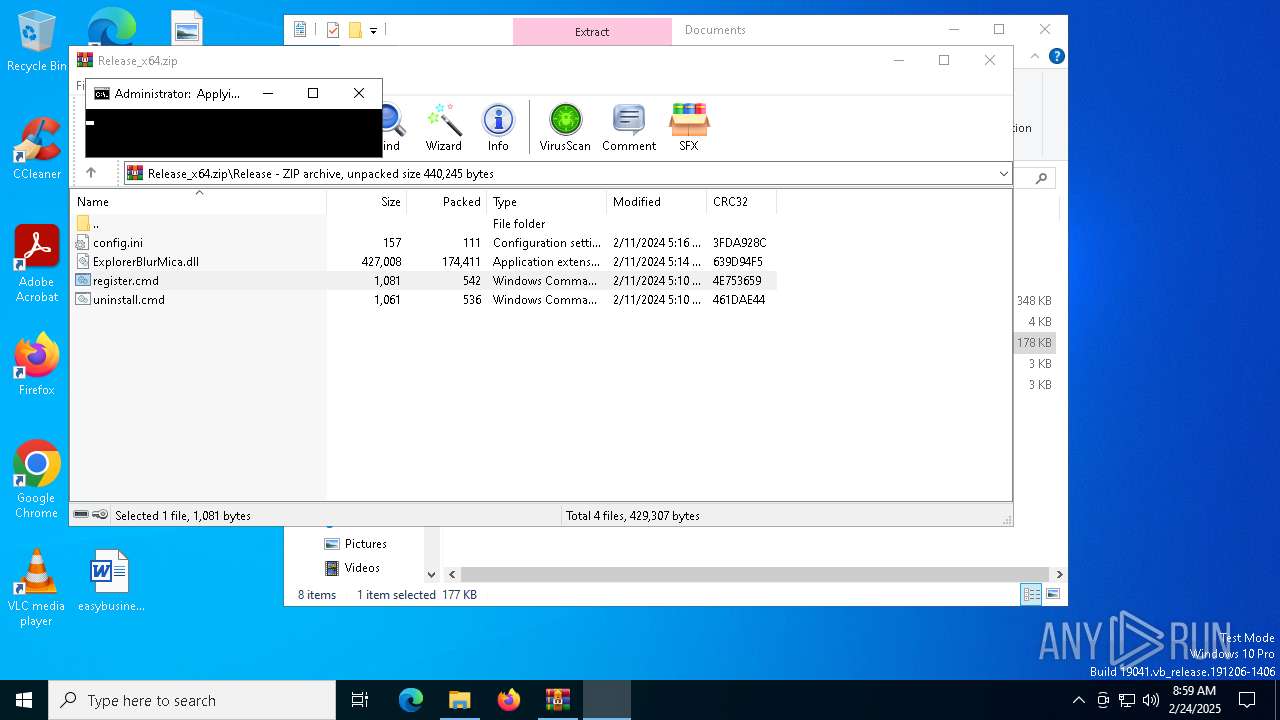
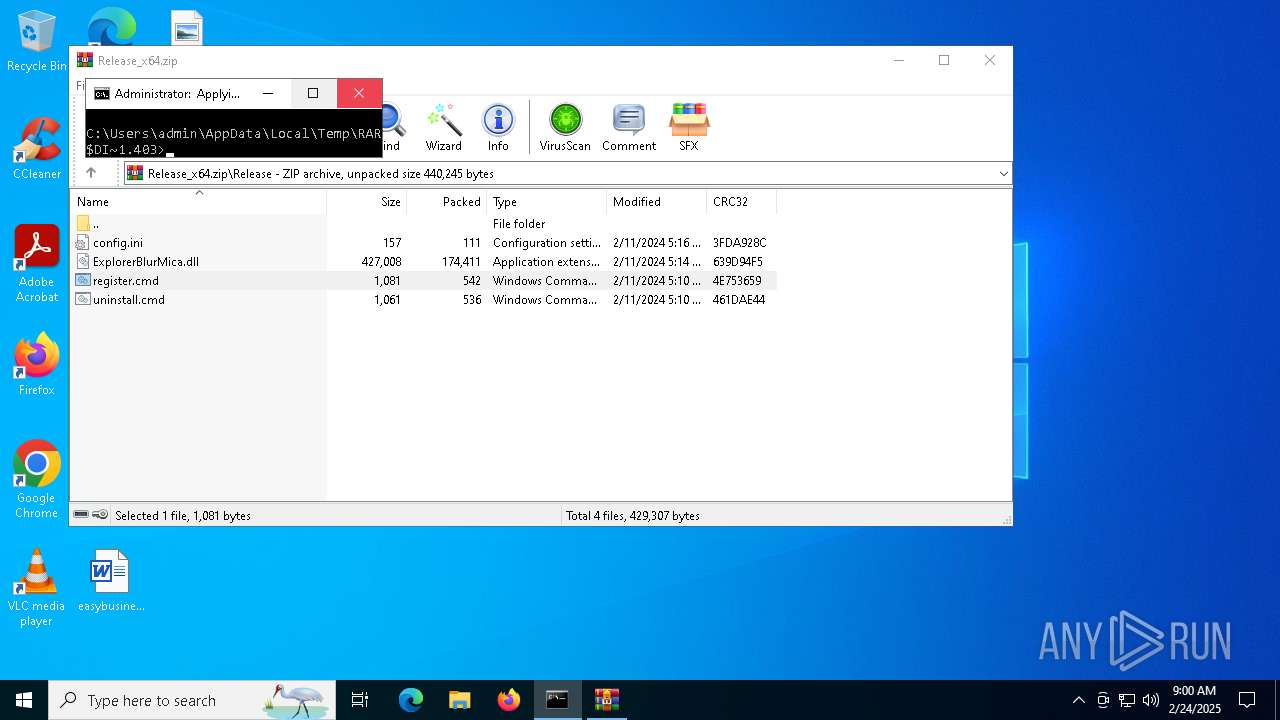
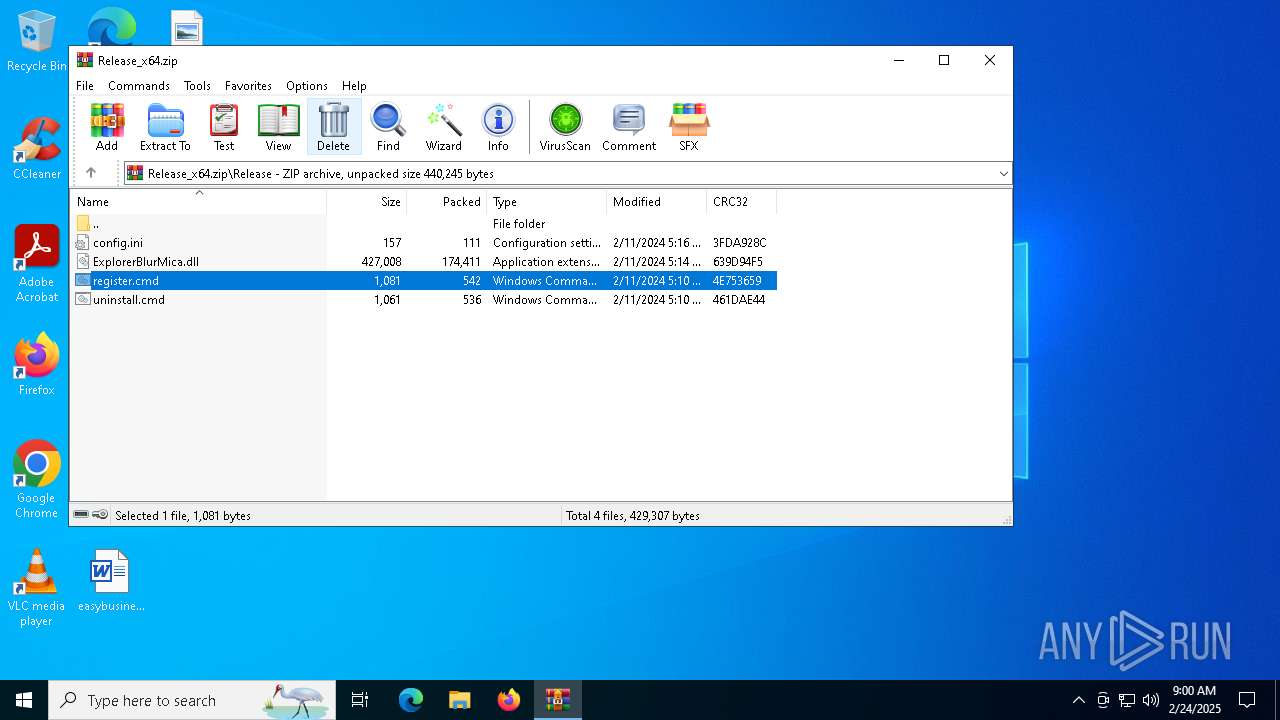
| File name: | Release_x64.zip |
| Full analysis: | https://app.any.run/tasks/f1a0db28-f227-4d65-8b45-c958a0f2c813 |
| Verdict: | Malicious activity |
| Analysis date: | February 24, 2025, 08:58:58 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | EB07E464101A8E02298B79A71086837B |
| SHA1: | 8DA823868381F2F20B4E095BE065433A4E625AC1 |
| SHA256: | 70E982BBFEDCA5F1DF51F7B2F7713CEDAF3124053074737B3D77E460894D2FC7 |
| SSDEEP: | 6144:zmef50C0pqkwOweXzJzjcEKNX++NKNVFUSqp:y050C0pqkwbSo+he |
MALICIOUS
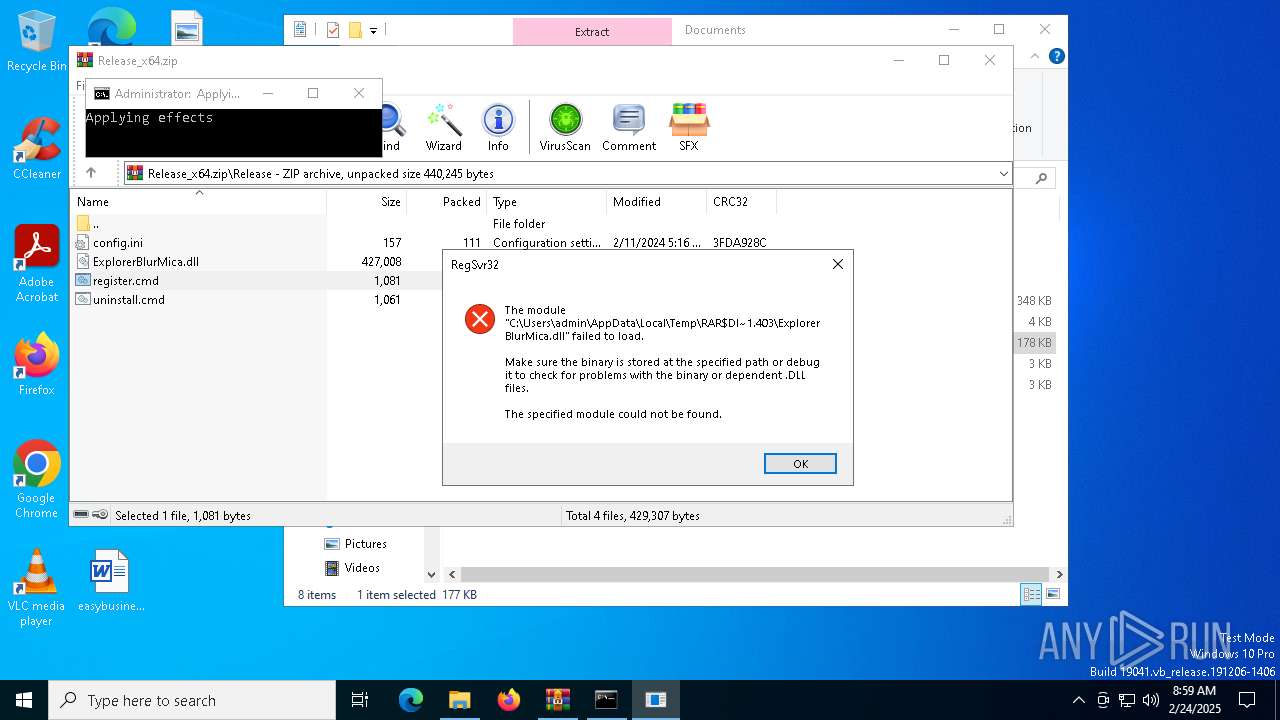
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 5696)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6164)
- StartMenuExperienceHost.exe (PID: 6076)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 5488)
- WinRAR.exe (PID: 6164)
- wscript.exe (PID: 1944)
Application launched itself
- cmd.exe (PID: 5488)
Executing commands from ".cmd" file
- WinRAR.exe (PID: 6164)
- wscript.exe (PID: 1944)
- cmd.exe (PID: 5488)
The process executes VB scripts
- cmd.exe (PID: 5488)
Runs shell command (SCRIPT)
- wscript.exe (PID: 1944)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 5696)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 5696)
The process executes via Task Scheduler
- explorer.exe (PID: 2992)
Reads the date of Windows installation
- StartMenuExperienceHost.exe (PID: 6076)
INFO
Manual execution by a user
- WinRAR.exe (PID: 6164)
Starts MODE.COM to configure console settings
- mode.com (PID: 2092)
- mode.com (PID: 1512)
Checks supported languages
- mode.com (PID: 2092)
- mode.com (PID: 1512)
- TextInputHost.exe (PID: 1520)
- SearchApp.exe (PID: 5192)
- StartMenuExperienceHost.exe (PID: 6076)
Reads security settings of Internet Explorer
- explorer.exe (PID: 2992)
Reads the computer name
- TextInputHost.exe (PID: 1520)
- StartMenuExperienceHost.exe (PID: 6076)
- SearchApp.exe (PID: 5192)
Process checks computer location settings
- StartMenuExperienceHost.exe (PID: 6076)
- SearchApp.exe (PID: 5192)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 4208)
- explorer.exe (PID: 2992)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 5192)
Checks proxy server information
- SearchApp.exe (PID: 5192)
- explorer.exe (PID: 2992)
Reads the software policy settings
- SearchApp.exe (PID: 5192)
Reads Environment values
- SearchApp.exe (PID: 5192)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:02:12 01:13:58 |
| ZipCRC: | 0x3276c77e |
| ZipCompressedSize: | 4773 |
| ZipUncompressedSize: | 10938 |
| ZipFileName: | ReadMe.txt |
Total processes
159
Monitored processes
29
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 556 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 624 | fsutil dirty query C: | C:\Windows\System32\fsutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: fsutil.exe Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 624 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1512 | mode CON COLS=37 LINES=3 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1520 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 1944 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\getadmin.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2092 | mode CON COLS=37 LINES=3 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2456 | explorer.exe | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 2 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2992 | "C:\WINDOWS\explorer.exe" /NoUACCheck | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3688 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
29 460
Read events
29 184
Write events
255
Delete events
21
Modification events
| (PID) Process: | (6416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\Release_x64.zip | |||
| (PID) Process: | (6416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
2
Suspicious files
56
Text files
104
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5192 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\AptopUBu7_oVDubJxwvaIprW-lI[1].css | text | |
MD5:4E0E75684C84C0102CED12948B95609B | SHA256:4D18E491B2DE4DA34F6C15F0574911613E902F791FE72501E4404802760D1BCA | |||
| 5192 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\dA5C-RUNdfz70qQQUNOSPqSPraE[1].js | binary | |
MD5:7F503C331FDA0B17D382157723BF2770 | SHA256:C9A57CFEE6238DE9C26C9E5F3C3E03686499F84B36F3B988D566987423BEA183 | |||
| 5192 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\TokenBroker\Cache\95d9a2a97a42f02325559b453ba7f8fe839baa18.tbres | binary | |
MD5:8329E55D45C940EF0C73E64B22AE7E20 | SHA256:A63B7615C432A3714A4B35E6868630943BC219AB652BF55E91DB08BD9F7EC878 | |||
| 5192 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\Init[1].htm | html | |
MD5:BDE53FCF0C72557B43F9B666F57E8DB9 | SHA256:C81C33F2BDCCAC8EEE171B80BF029E6EE4EA5709548E950FB0A527C88E2A85AF | |||
| 5192 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\vOJNaIfAXvJzmnBm845ss-M9YR8[1].css | text | |
MD5:87BBB1A289EDC24C9F06B88229765467 | SHA256:85B291C46F9D1EEEC71DB839F649D748F48B203EA836F3ACE3B9B761947D960C | |||
| 5192 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\fvNdnrKxhhxDQUEi09cCaSWpzzE[1].css | text | |
MD5:15DC838A1A66277F9F4D915124DFFBBC | SHA256:9C947D5F732431197DA9DB1F159CB3D4CDC5DBFE55FDC0A9513E571FF31236A1 | |||
| 5192 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\-iNIzuEypRdgRJ6xnyVHizZ3bpM.br[1].js | binary | |
MD5:E86ABEFE45E62F7E2F865D8A344D0B6F | SHA256:5D54790C856CE13811590E18AC3B0ACEEFEFB61258852490F4C5C60748365E89 | |||
| 5192 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\-F7bYnjk9S0ADBYML9L8EdympNE.br[1].js | binary | |
MD5:4AB990A76783365262550A7F0BD63627 | SHA256:DE10DD0F9F06597A855DCB3D3517830CA8D599BA340DE2814250A42AEAD4FCBD | |||
| 5192 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\2u1i5bXJCKdk4jOb70d5CjAHxg4[1].css | text | |
MD5:FB0A7FB447B21BFD27B771B689DD9E12 | SHA256:D1C023C91717180C42EDCB702C6D2EDDD5813CA7A7BD255F537EDD613369C539 | |||
| 6164 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6164.40332\register.cmd | text | |
MD5:69D7C77DA0C817B911E7FCBFEB1DD271 | SHA256:A171D3AE6B224D7C2AB8B778AA66311E2A91C91540DAB6606623B36C02F548CA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
45
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.194:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6656 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1216 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4208 | BackgroundTransferHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4444 | SIHClient.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4444 | SIHClient.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.194:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2736 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.16.204.133:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |