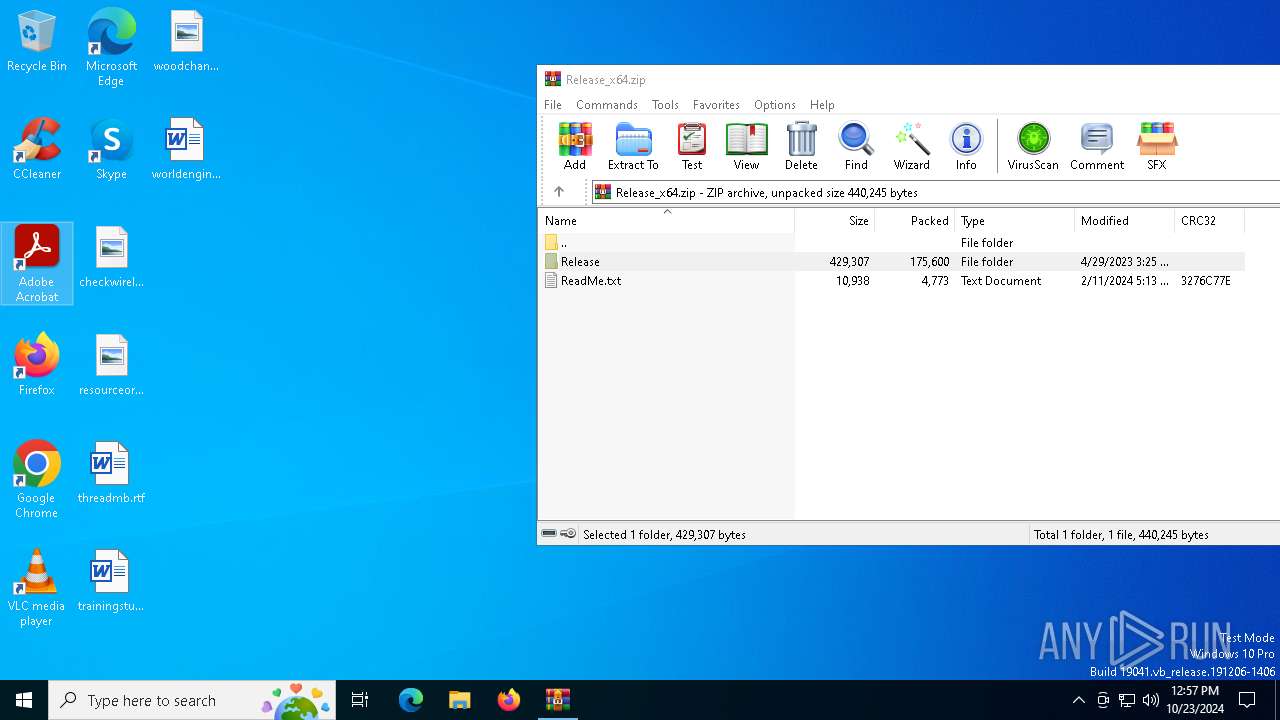
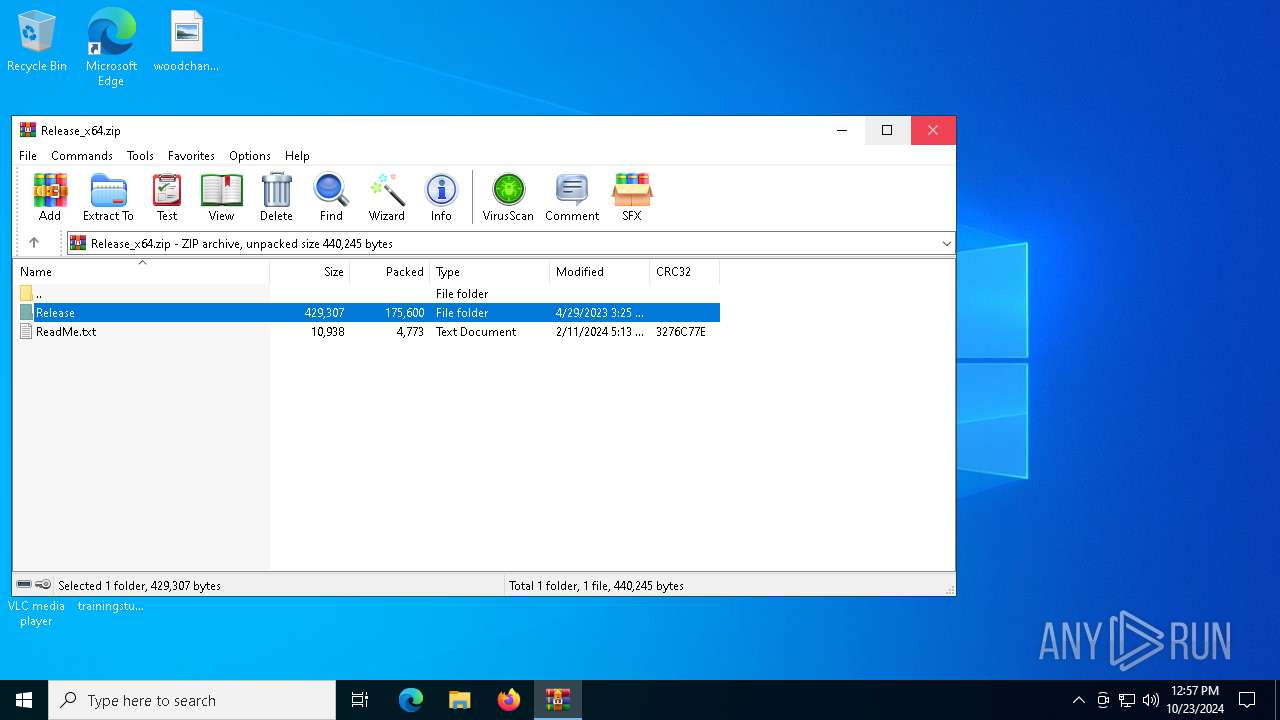
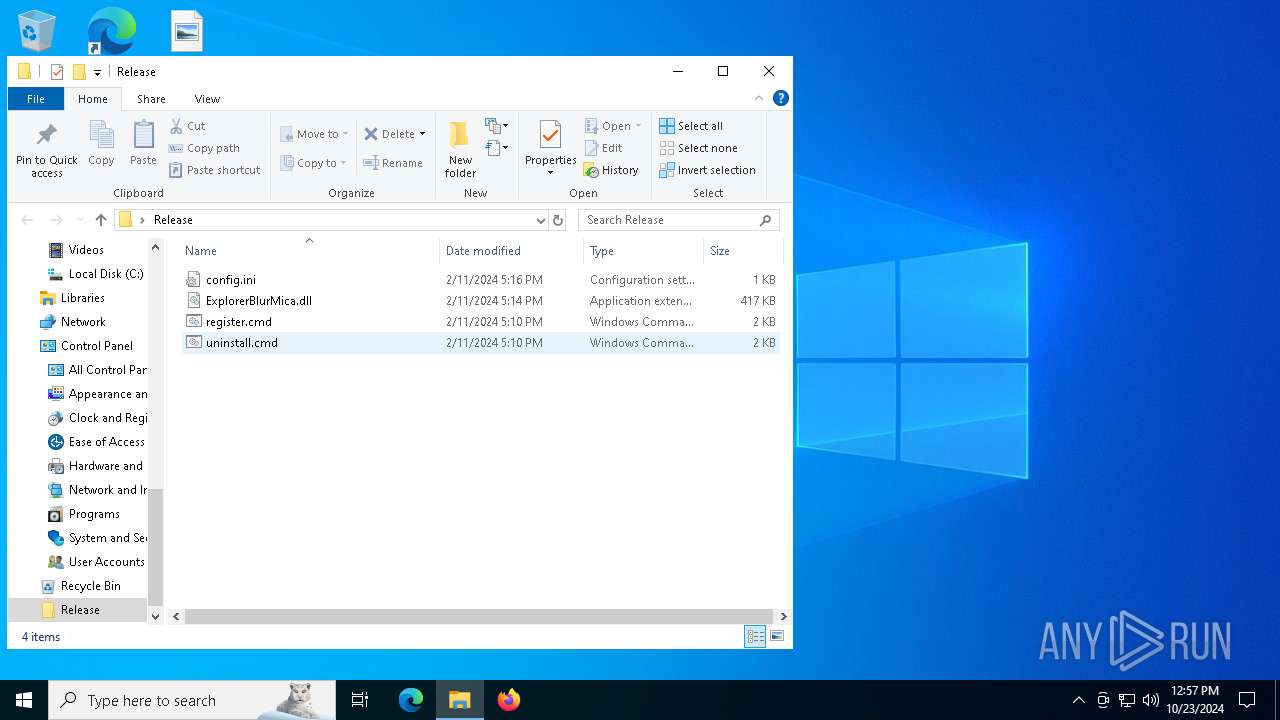
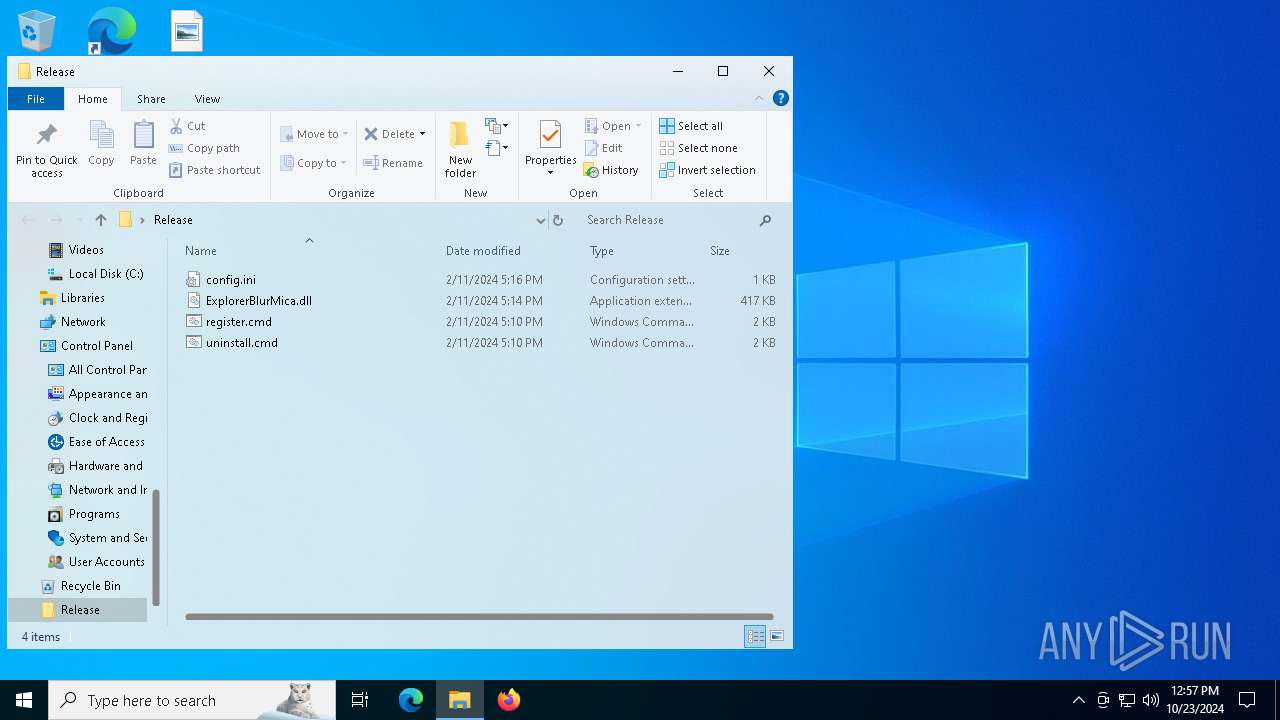
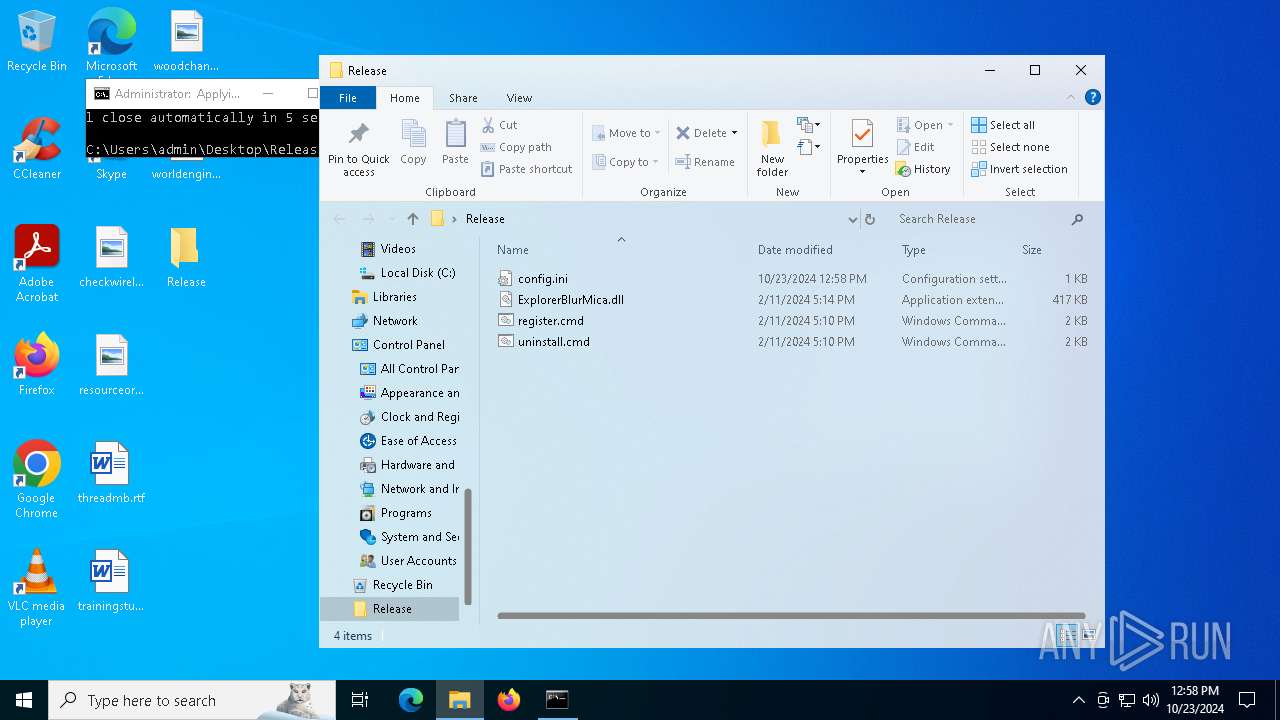
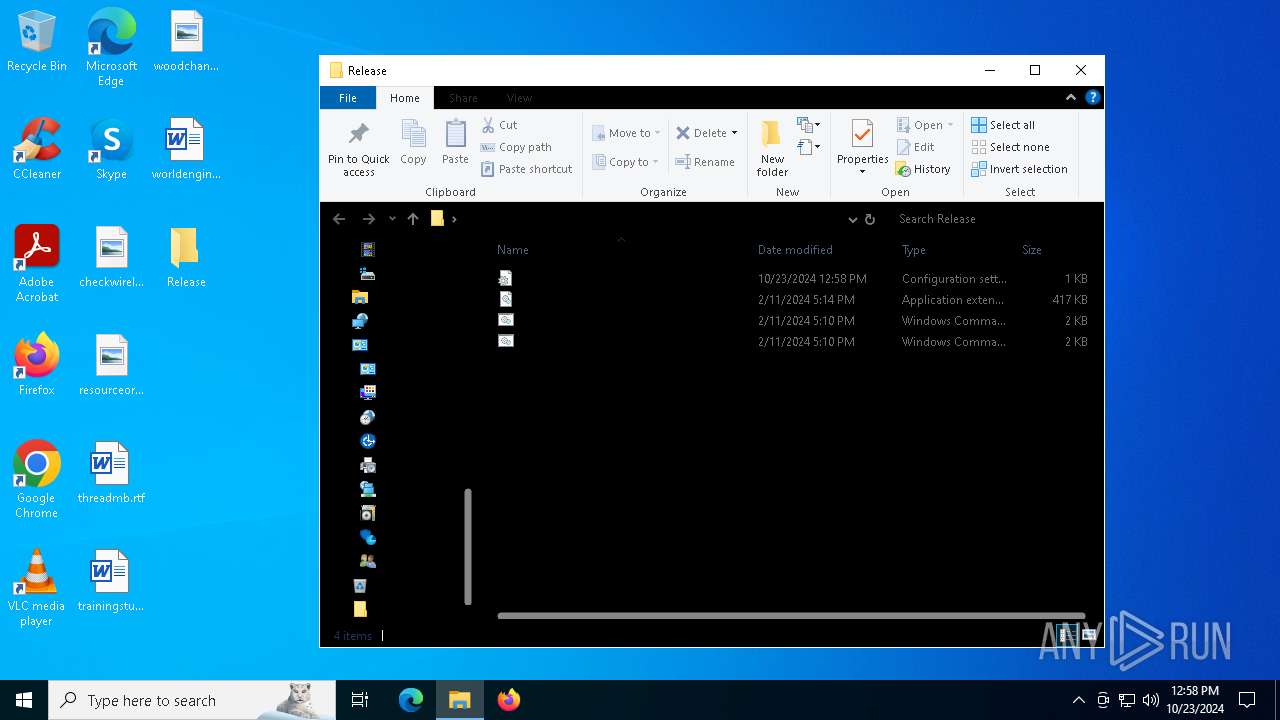
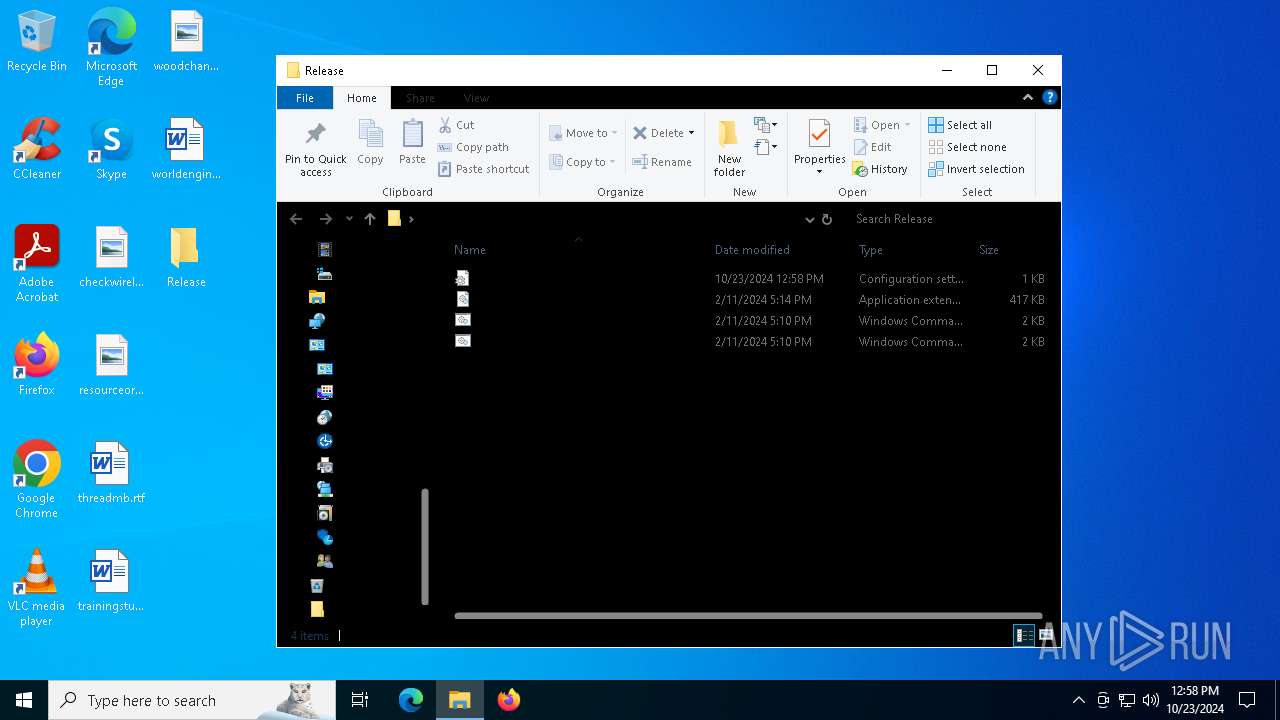
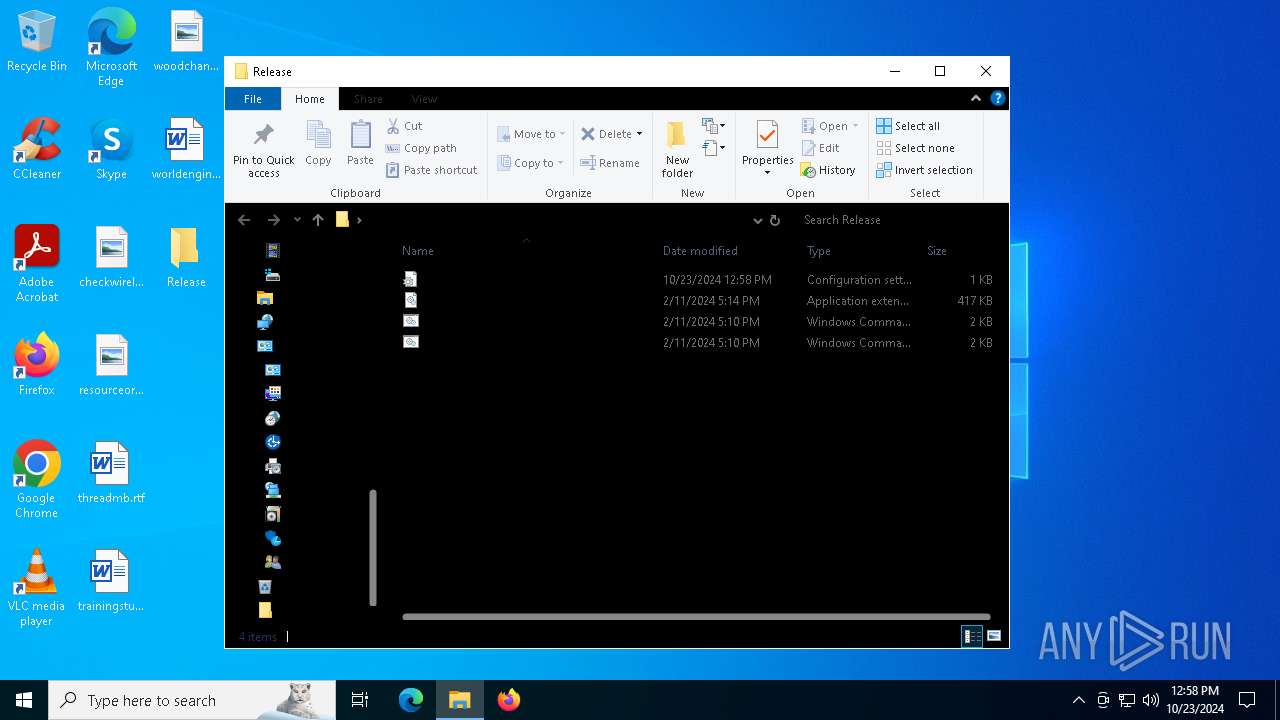
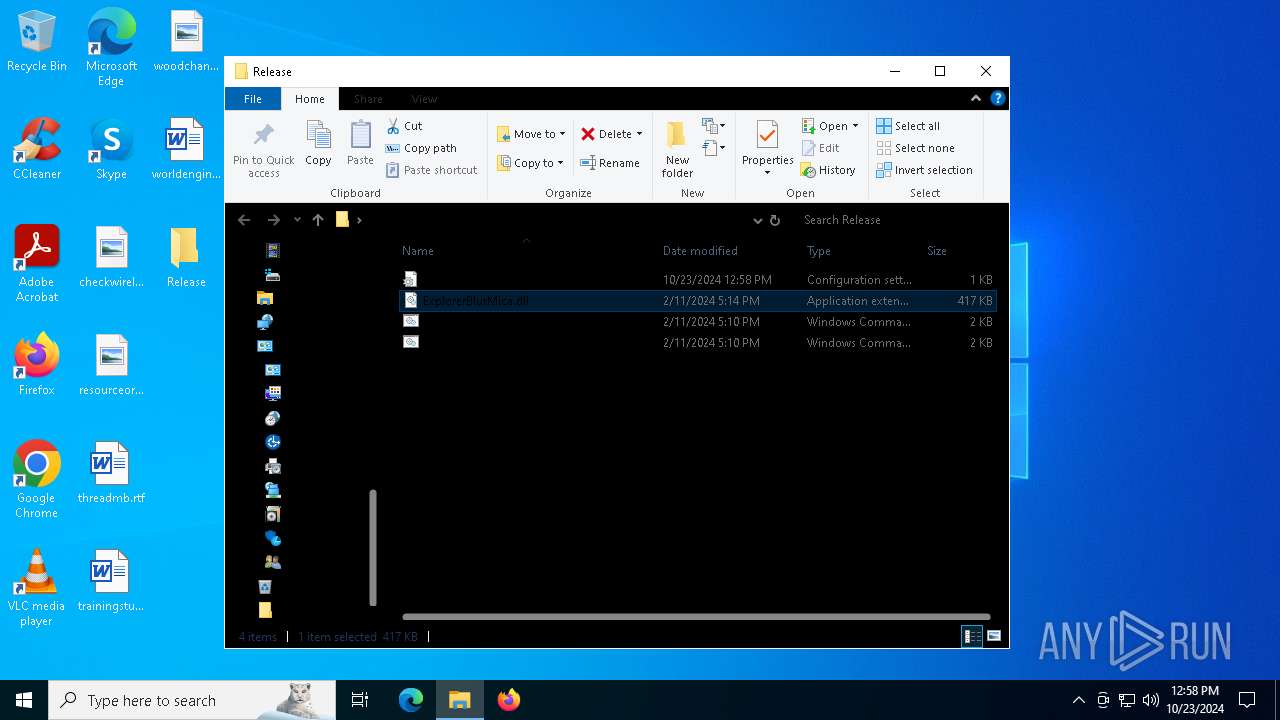
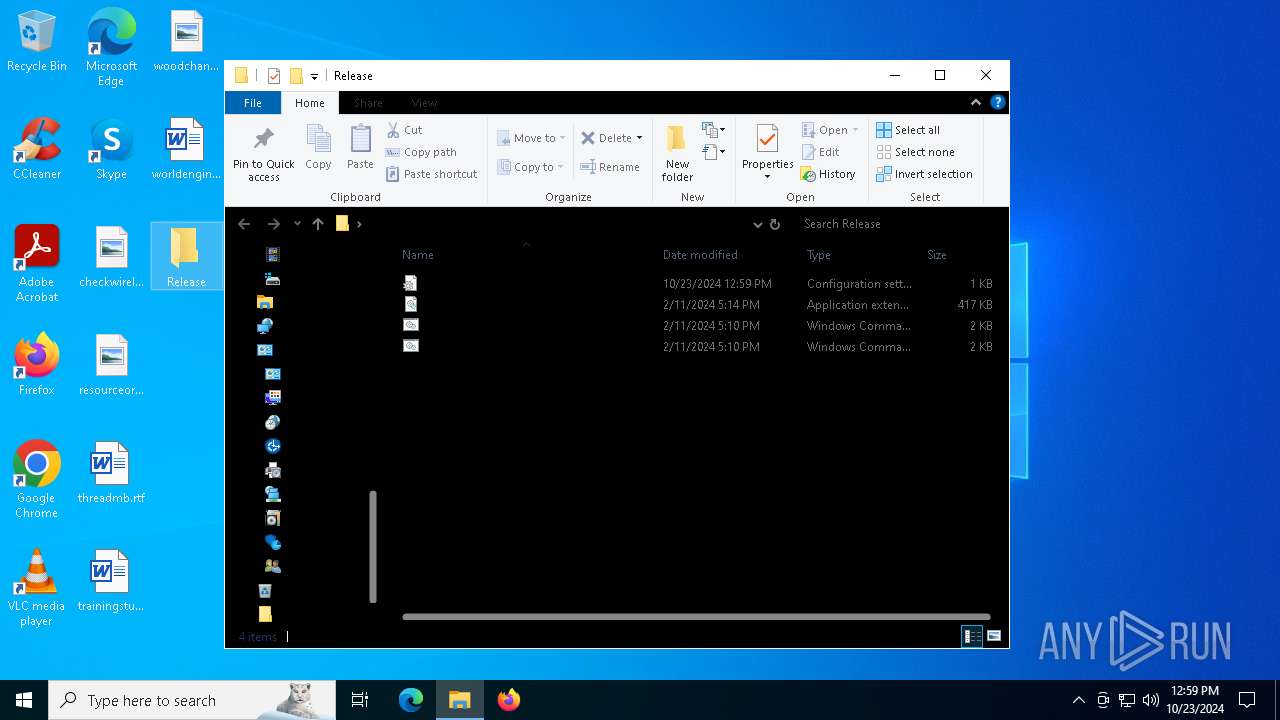
| File name: | Release_x64.zip |
| Full analysis: | https://app.any.run/tasks/6049f1fb-06ec-4b5f-be24-5f1c129ca021 |
| Verdict: | Malicious activity |
| Analysis date: | October 23, 2024, 12:57:05 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | EB07E464101A8E02298B79A71086837B |
| SHA1: | 8DA823868381F2F20B4E095BE065433A4E625AC1 |
| SHA256: | 70E982BBFEDCA5F1DF51F7B2F7713CEDAF3124053074737B3D77E460894D2FC7 |
| SSDEEP: | 6144:zmef50C0pqkwOweXzJzjcEKNX++NKNVFUSqp:y050C0pqkwbSo+he |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 1196)
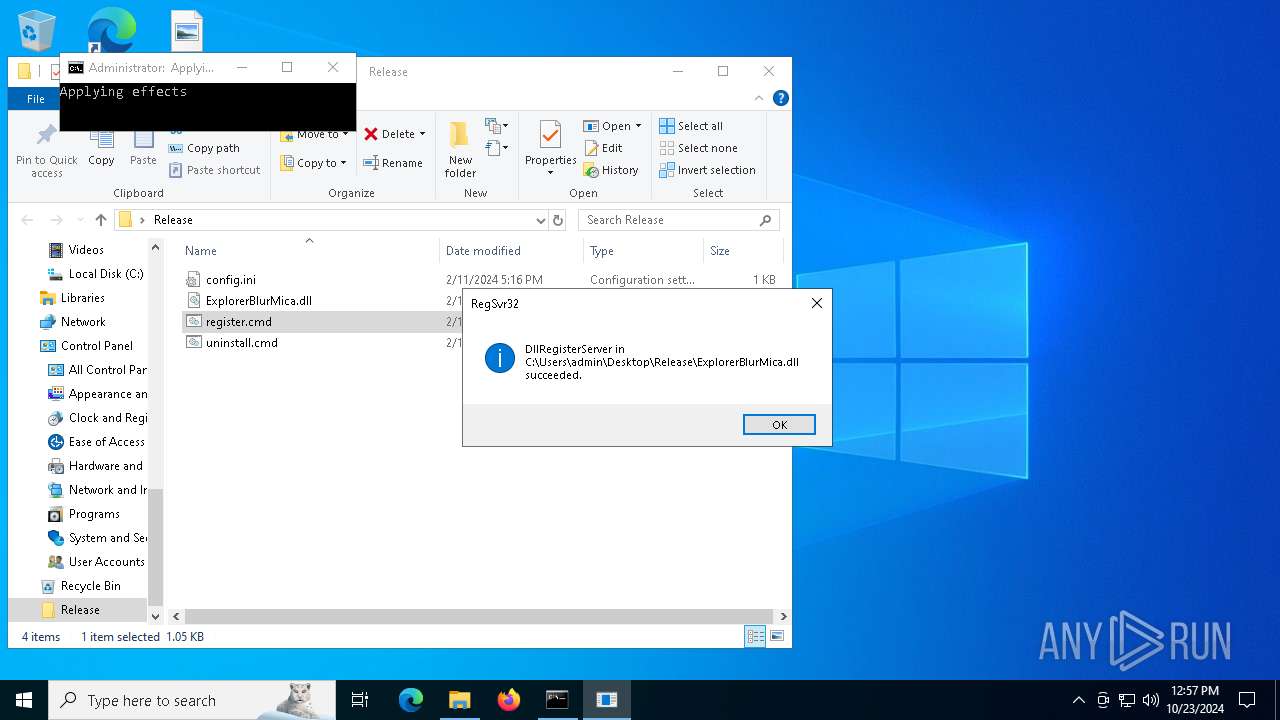
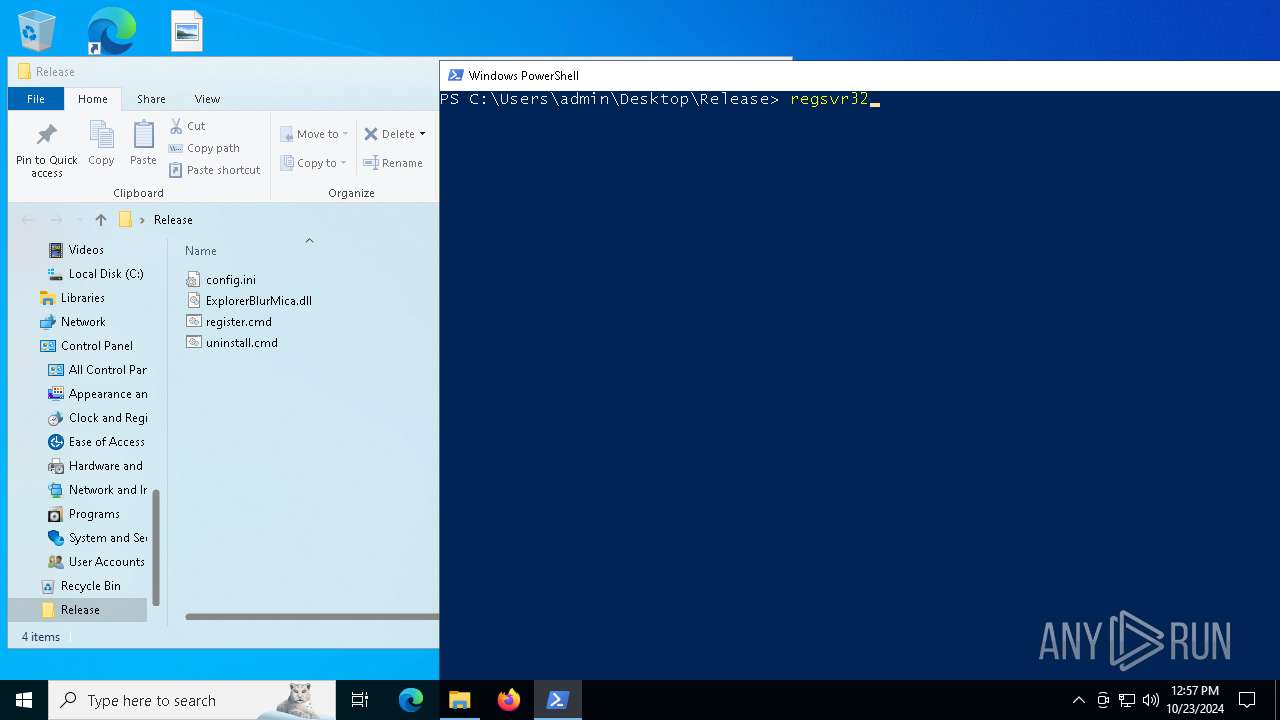
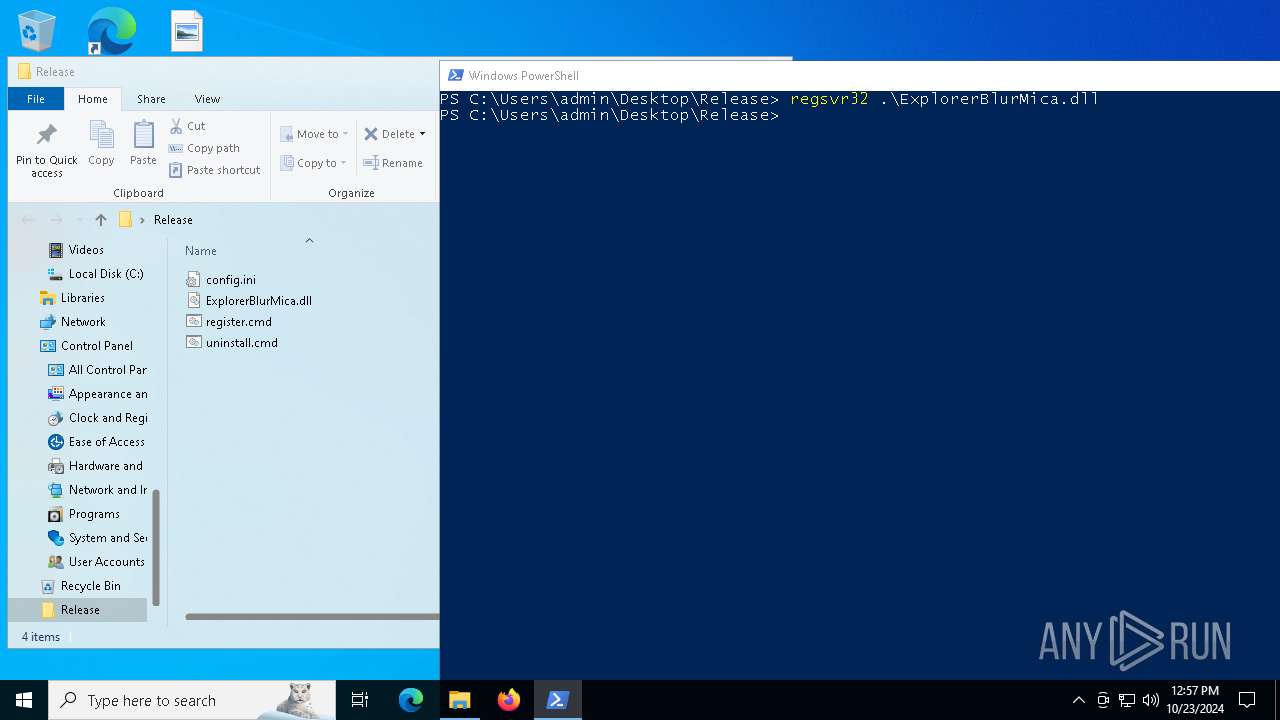
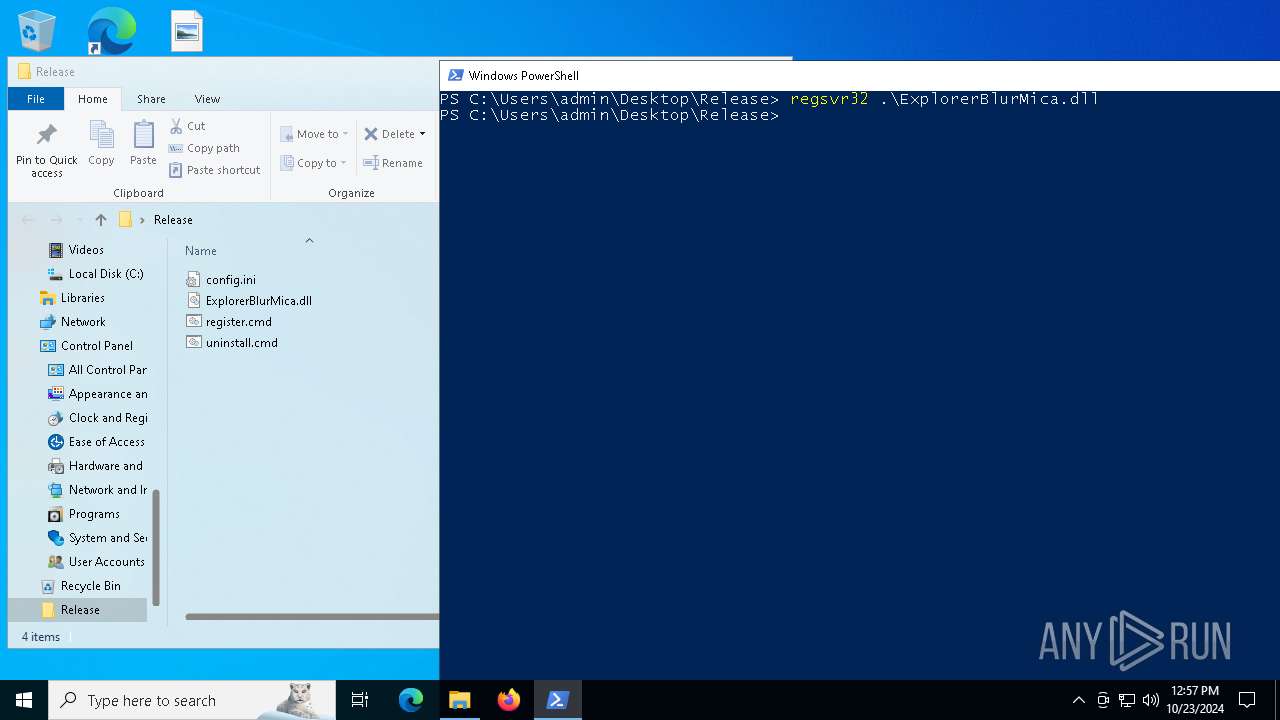
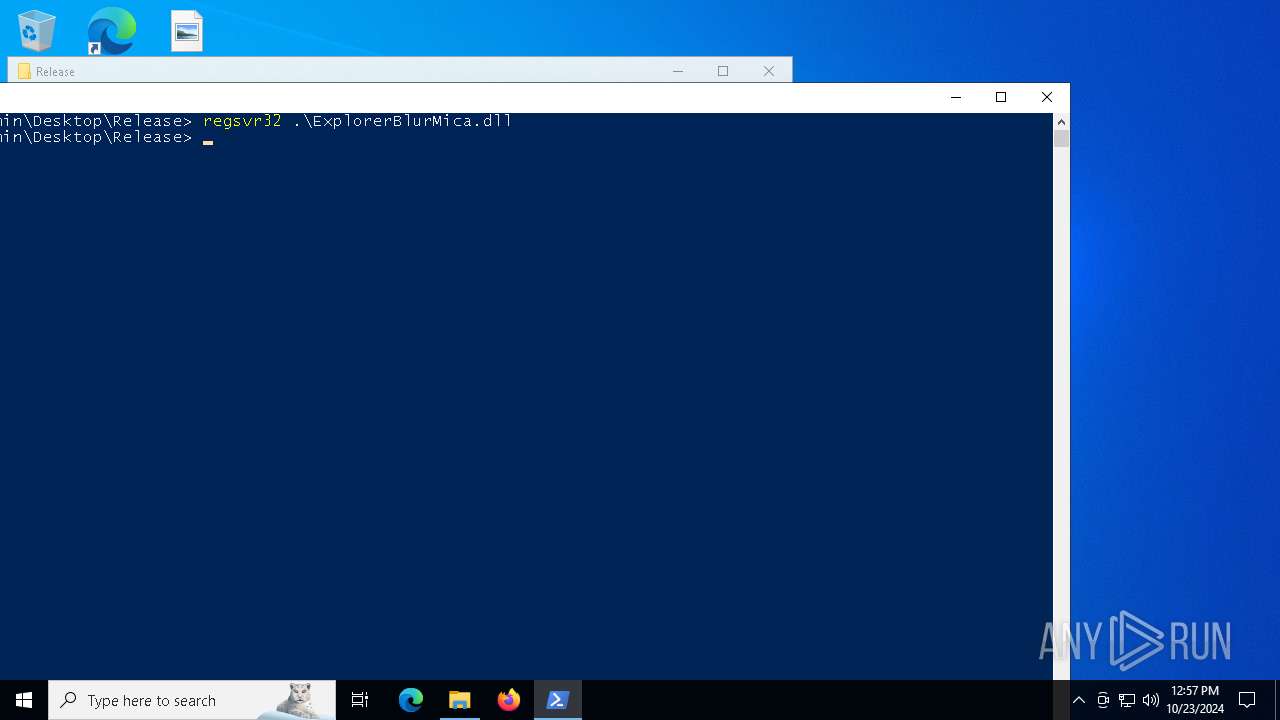
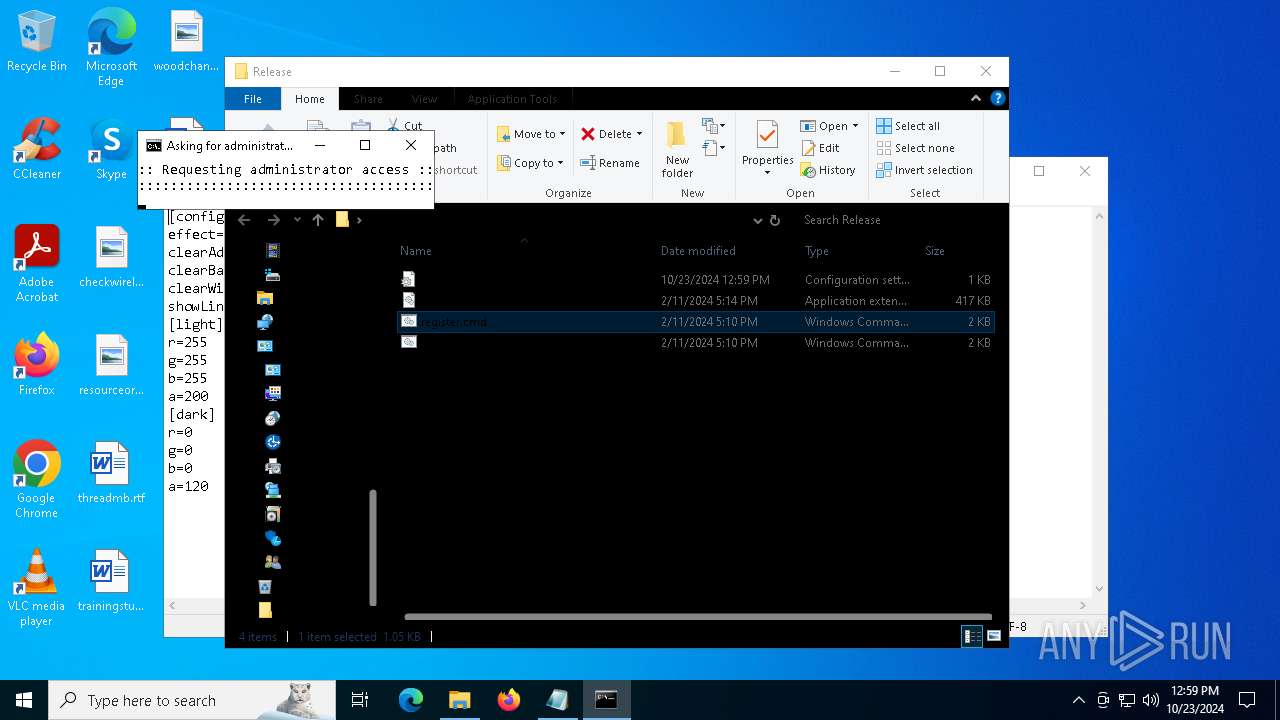
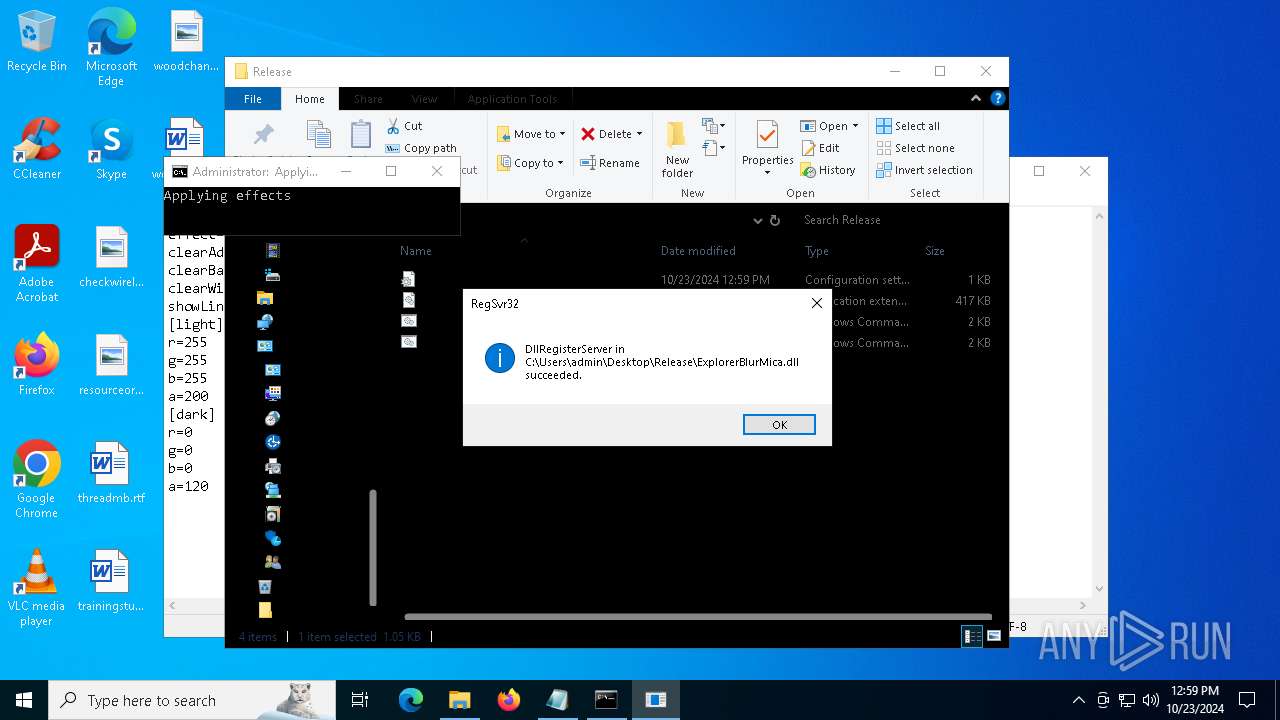
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 7680)
- powershell.exe (PID: 7976)
- cmd.exe (PID: 4668)
- cmd.exe (PID: 7608)
- cmd.exe (PID: 5892)
- cmd.exe (PID: 7756)
- cmd.exe (PID: 992)
SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 7436)
- wscript.exe (PID: 7588)
- explorer.exe (PID: 8044)
- cmd.exe (PID: 5300)
- wscript.exe (PID: 5008)
- explorer.exe (PID: 5448)
- cmd.exe (PID: 7656)
- cmd.exe (PID: 4376)
- wscript.exe (PID: 8124)
- wscript.exe (PID: 5724)
- explorer.exe (PID: 616)
- cmd.exe (PID: 7636)
- wscript.exe (PID: 5460)
- explorer.exe (PID: 1588)
- cmd.exe (PID: 5640)
- wscript.exe (PID: 7480)
Executing commands from ".cmd" file
- cmd.exe (PID: 7436)
- wscript.exe (PID: 7588)
- wscript.exe (PID: 5008)
- cmd.exe (PID: 5300)
- explorer.exe (PID: 5448)
- cmd.exe (PID: 7656)
- cmd.exe (PID: 4376)
- wscript.exe (PID: 5724)
- wscript.exe (PID: 8124)
- explorer.exe (PID: 616)
- explorer.exe (PID: 1588)
- cmd.exe (PID: 5640)
- wscript.exe (PID: 7480)
- explorer.exe (PID: 8044)
- wscript.exe (PID: 5460)
- cmd.exe (PID: 7636)
Application launched itself
- cmd.exe (PID: 7436)
- cmd.exe (PID: 5300)
- cmd.exe (PID: 7656)
- cmd.exe (PID: 4376)
- cmd.exe (PID: 7636)
- cmd.exe (PID: 5640)
The process executes VB scripts
- cmd.exe (PID: 7436)
- cmd.exe (PID: 5300)
- cmd.exe (PID: 7656)
- cmd.exe (PID: 4376)
- cmd.exe (PID: 7636)
- cmd.exe (PID: 5640)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7680)
- cmd.exe (PID: 4668)
- cmd.exe (PID: 5892)
- cmd.exe (PID: 7608)
- cmd.exe (PID: 7756)
- cmd.exe (PID: 992)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7680)
- cmd.exe (PID: 4668)
- cmd.exe (PID: 5892)
- cmd.exe (PID: 7608)
- cmd.exe (PID: 7756)
- cmd.exe (PID: 992)
The process executes via Task Scheduler
- explorer.exe (PID: 8044)
- explorer.exe (PID: 5448)
- explorer.exe (PID: 616)
- explorer.exe (PID: 2776)
- explorer.exe (PID: 1588)
- explorer.exe (PID: 5280)
Starts POWERSHELL.EXE for commands execution
- explorer.exe (PID: 8044)
INFO
Manual execution by a user
- cmd.exe (PID: 7436)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1196)
Starts MODE.COM to configure console settings
- mode.com (PID: 7496)
- mode.com (PID: 7752)
- mode.com (PID: 4812)
- mode.com (PID: 5444)
- mode.com (PID: 5304)
- mode.com (PID: 5480)
- mode.com (PID: 3744)
- mode.com (PID: 4808)
- mode.com (PID: 6568)
- mode.com (PID: 6624)
- mode.com (PID: 7636)
- mode.com (PID: 4516)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:02:12 01:13:58 |
| ZipCRC: | 0x3276c77e |
| ZipCompressedSize: | 4773 |
| ZipUncompressedSize: | 10938 |
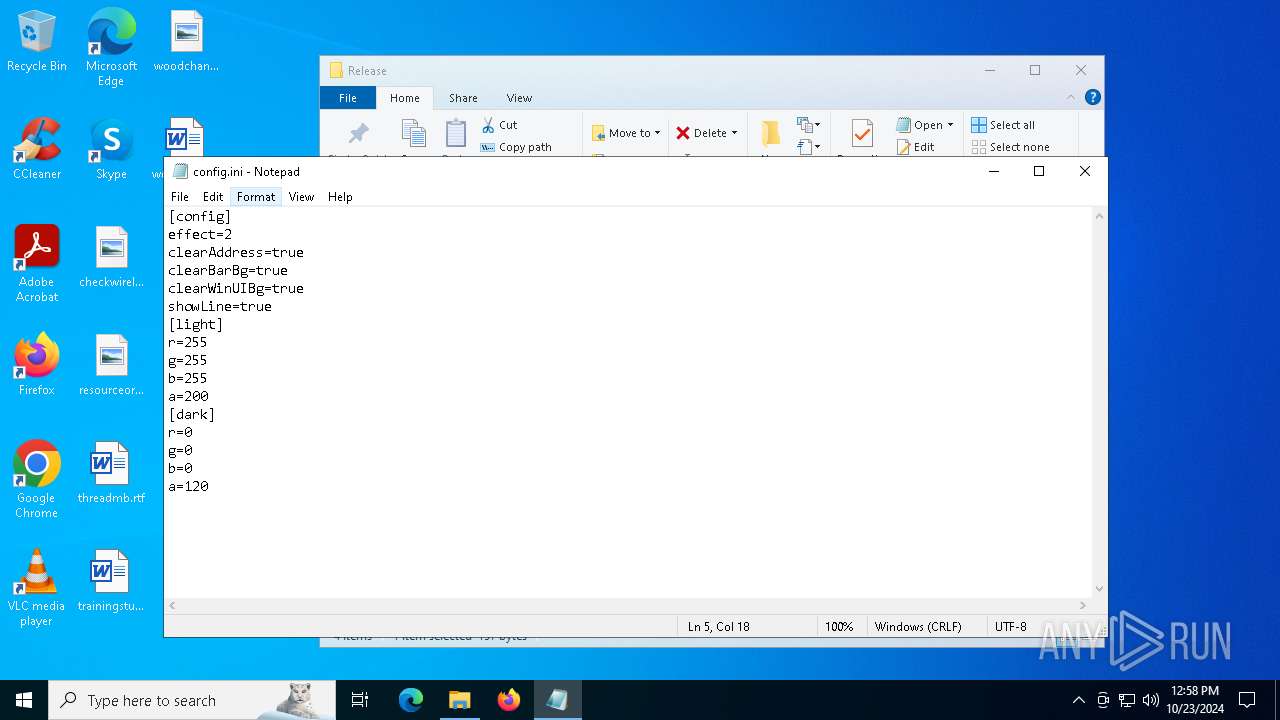
| ZipFileName: | ReadMe.txt |
Total processes
273
Monitored processes
131
Malicious processes
2
Suspicious processes
19
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 204 | timeout /t 5 | C:\Windows\System32\timeout.exe | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 528 | explorer.exe | C:\Windows\explorer.exe | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 2 Version: 10.0.19041.3758 (WinBuild.160101.0800) | ||||
| 616 | "C:\WINDOWS\explorer.exe" /NoUACCheck | C:\Windows\explorer.exe | — | svchost.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) | ||||
| 784 | fsutil dirty query C: | C:\Windows\System32\fsutil.exe | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: fsutil.exe Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
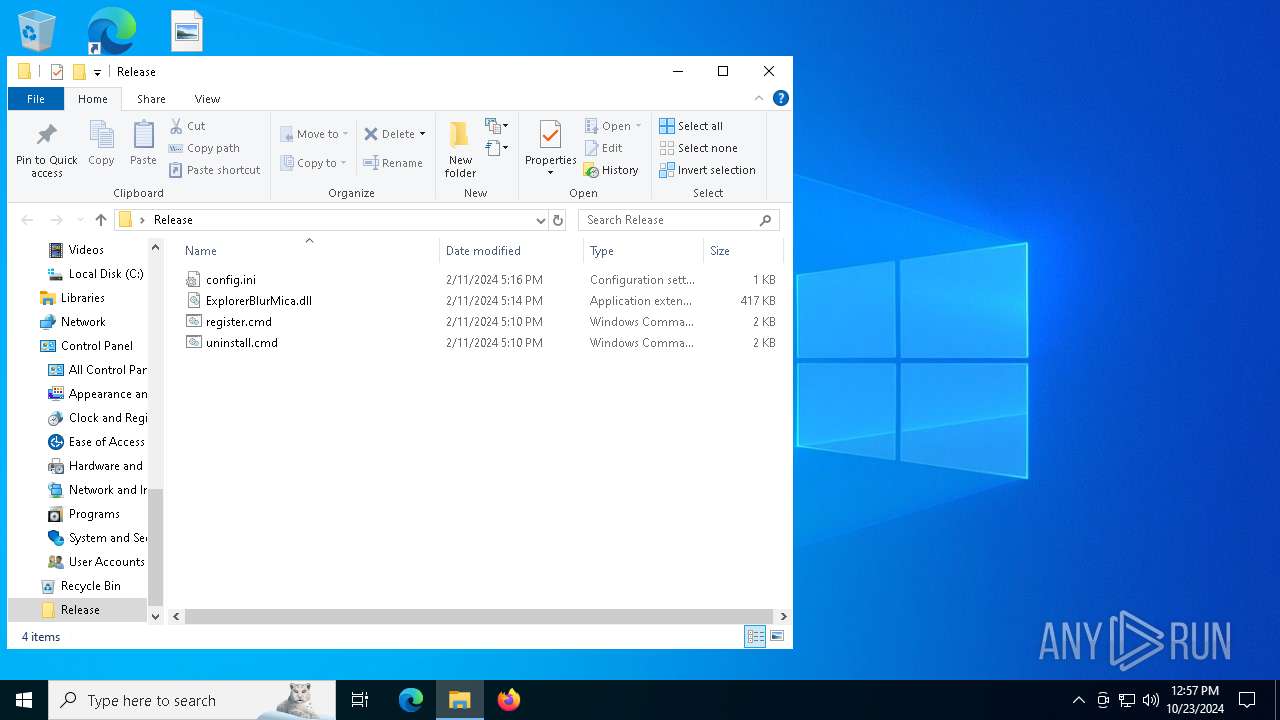
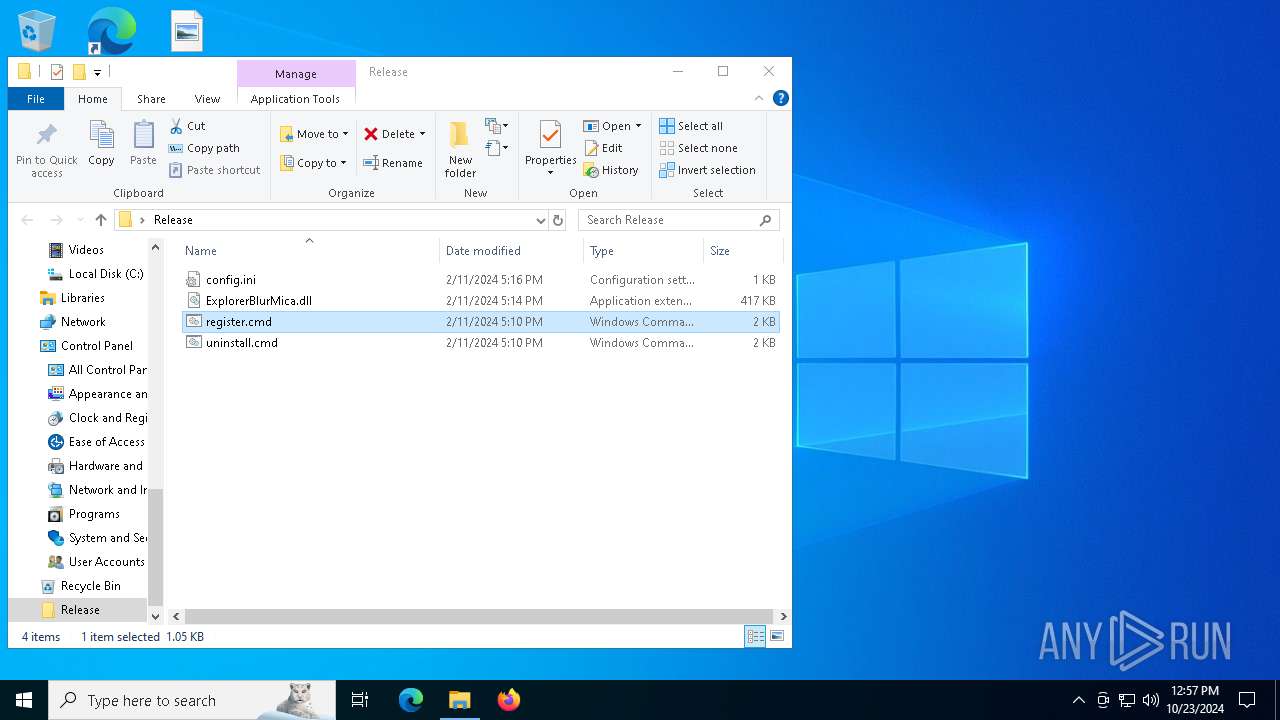
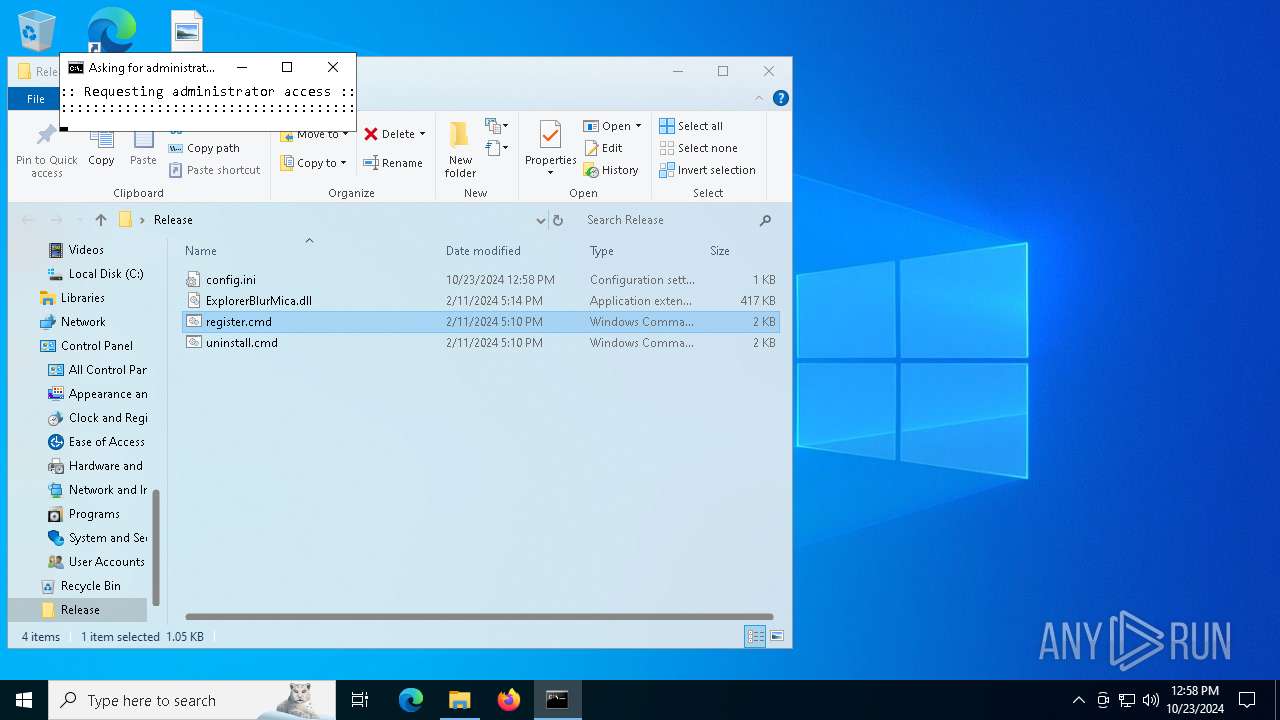
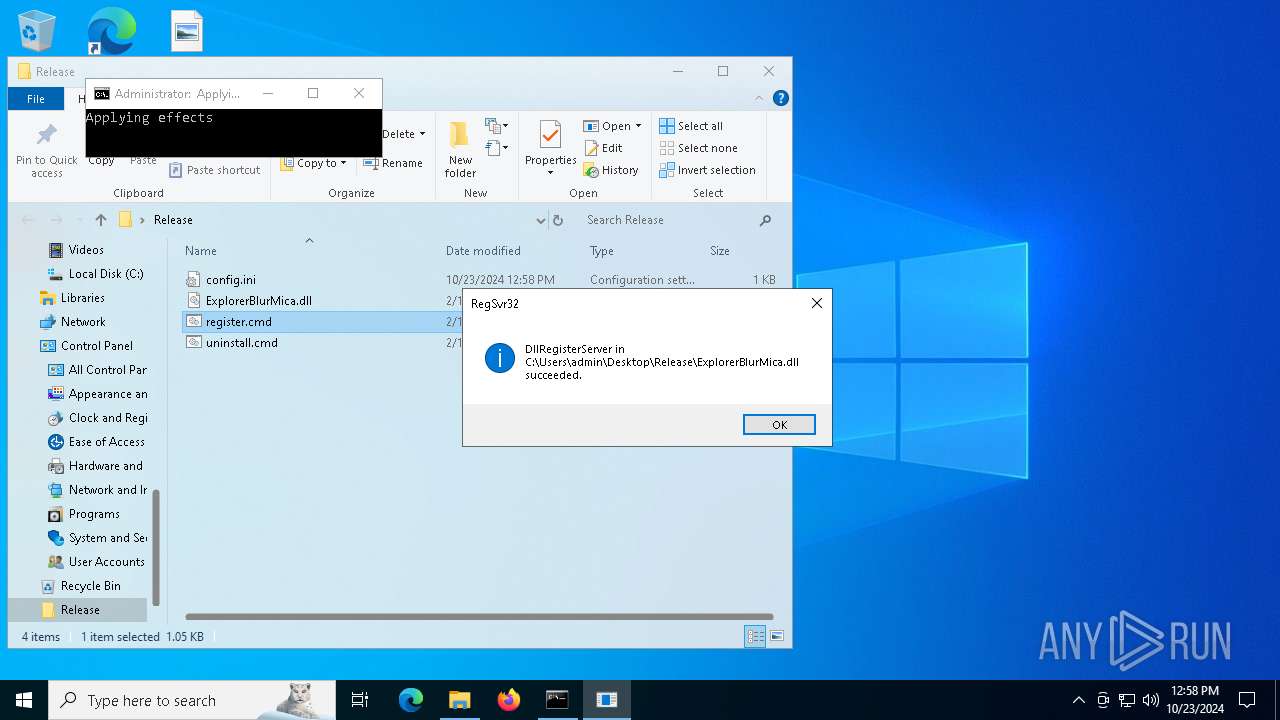
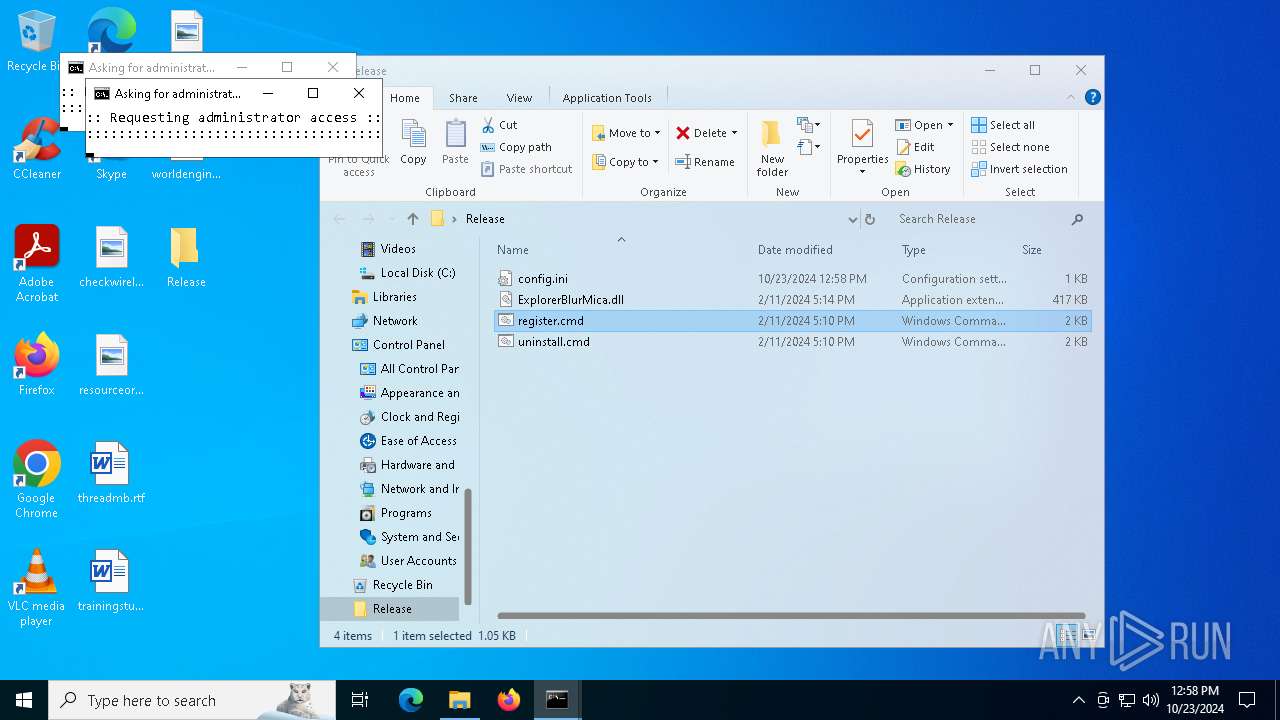
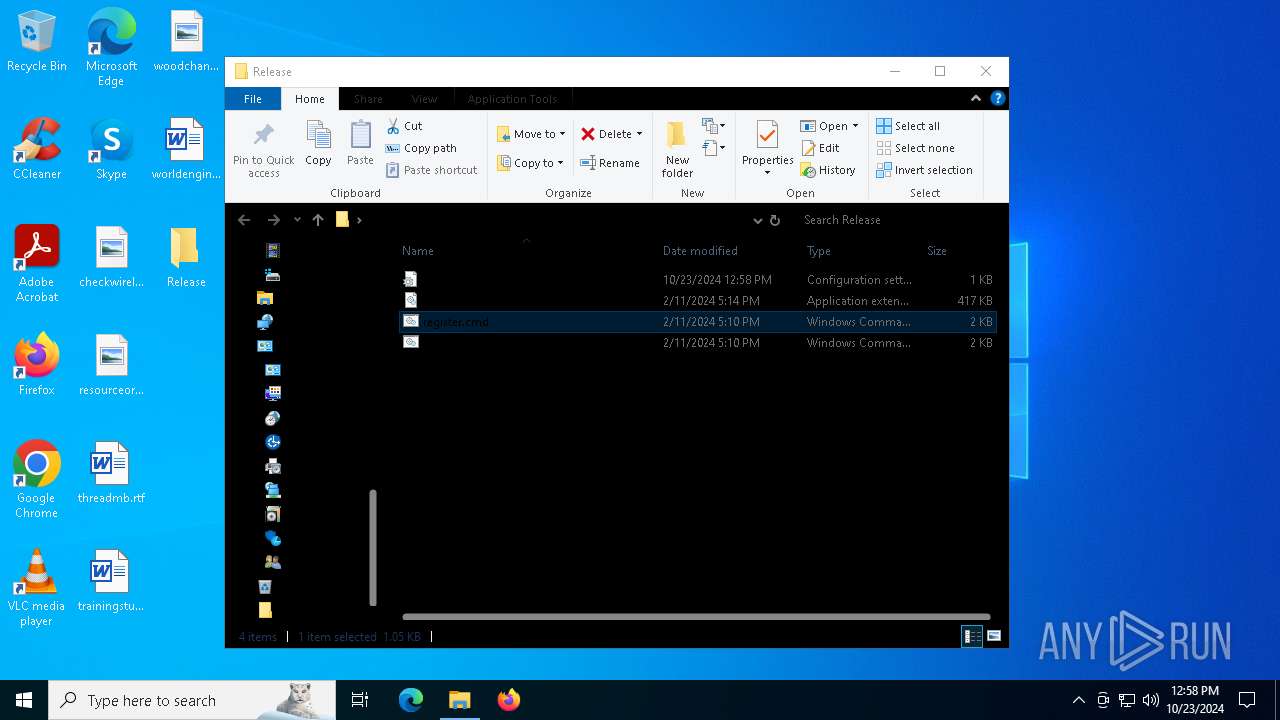
| 992 | "C:\Windows\System32\cmd.exe" /k cd "C:\Users\admin\Desktop\Release\" && "C:\Users\admin\Desktop\Release\register.cmd" | C:\Windows\System32\cmd.exe | wscript.exe | |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 1172 | cmd /u /c echo Set UAC = CreateObject("Shell.Application") : UAC.ShellExecute "cmd.exe", "/k cd ""C:\Users\admin\Desktop\Release\"" && ""C:\Users\admin\Desktop\Release\register.cmd"" ", "", "runas", 1 | C:\Windows\System32\cmd.exe | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 1196 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Release_x64.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | |
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 | ||||
| 1432 | explorer.exe | C:\Windows\explorer.exe | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 2 Version: 10.0.19041.3758 (WinBuild.160101.0800) | ||||
| 1452 | fsutil dirty query C: | C:\Windows\System32\fsutil.exe | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: fsutil.exe Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 1584 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | — | svchost.exe |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
3
Suspicious files
206
Text files
337
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1788 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\DeviceSearchCache\AppCache133741618502986674.txt~RF904f5.TMP | — | |
MD5:— | SHA256:— | |||
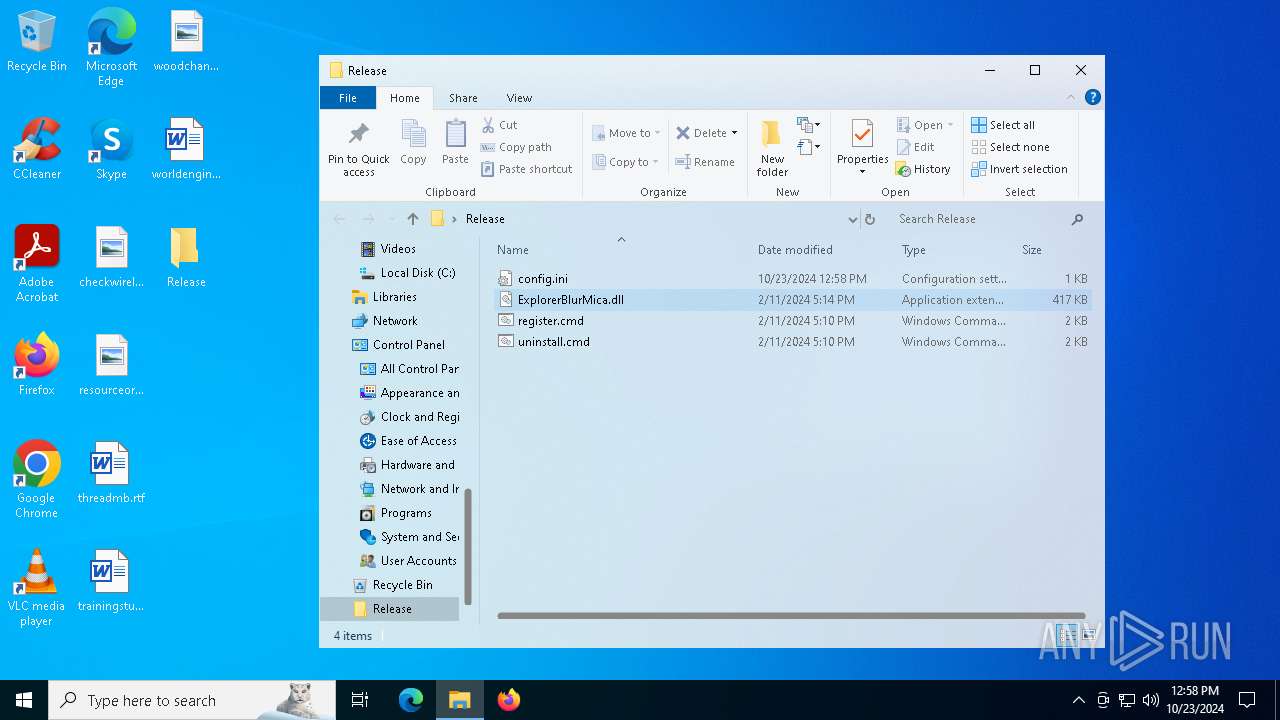
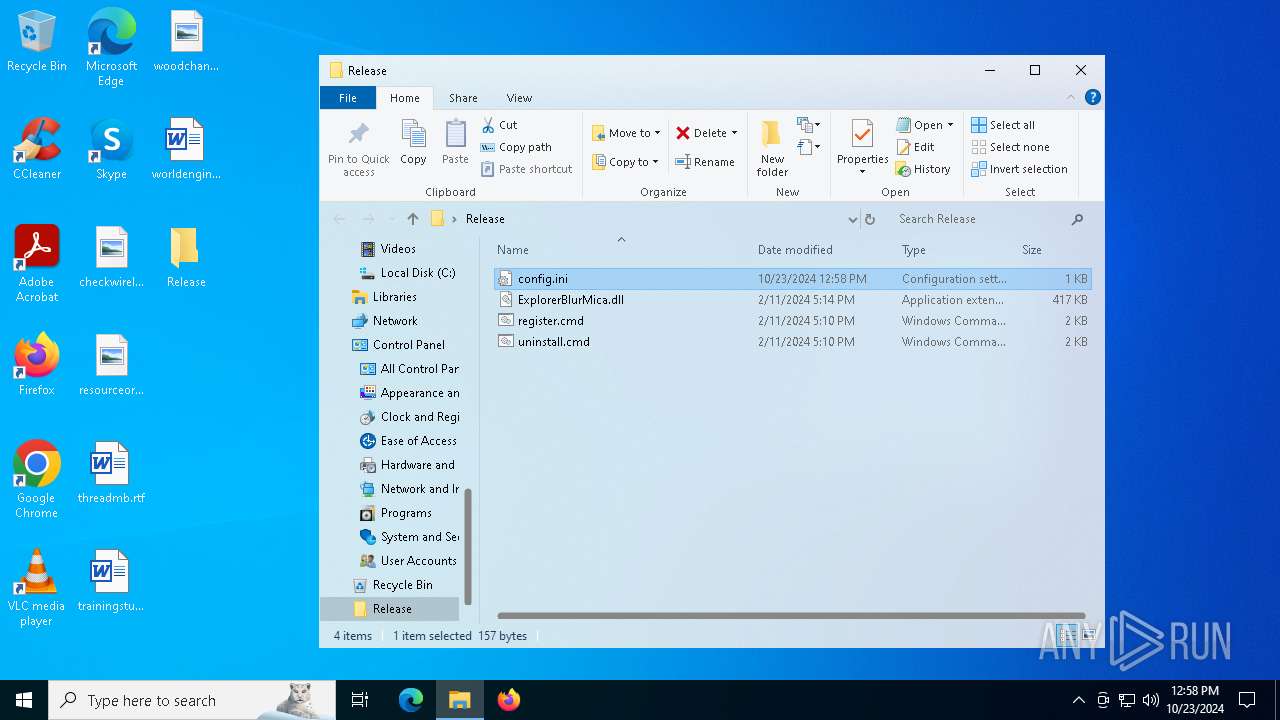
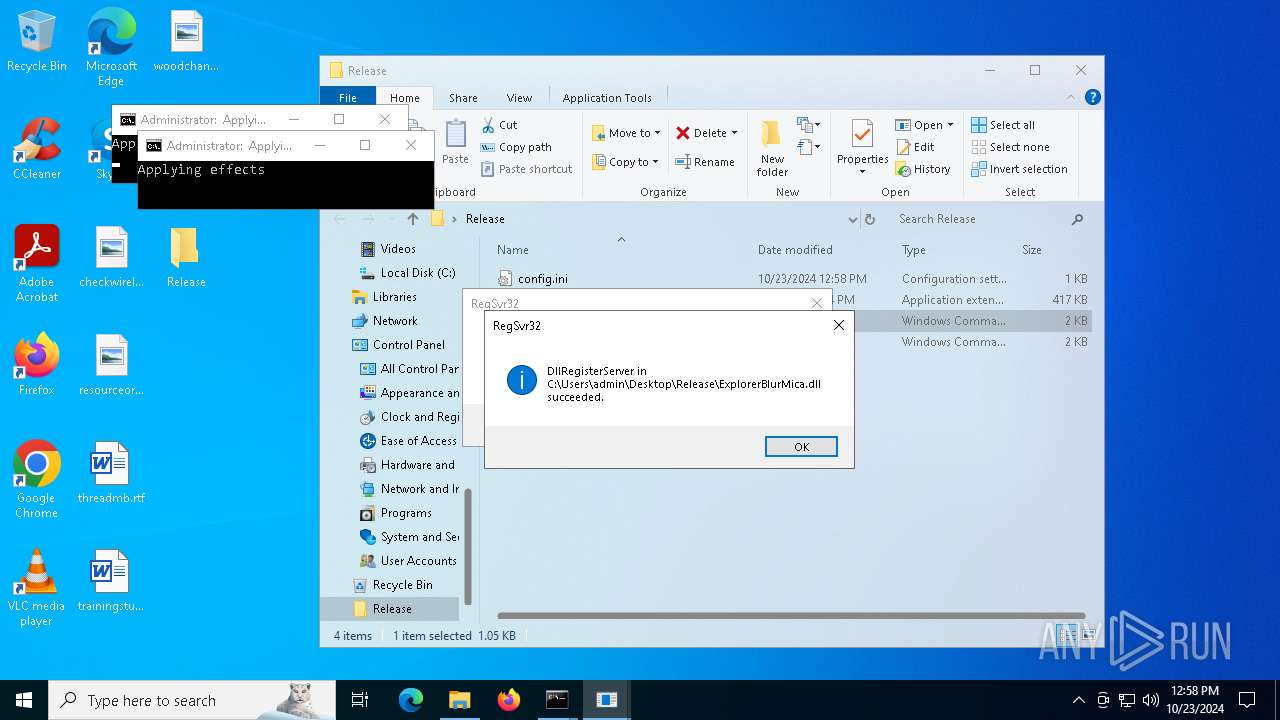
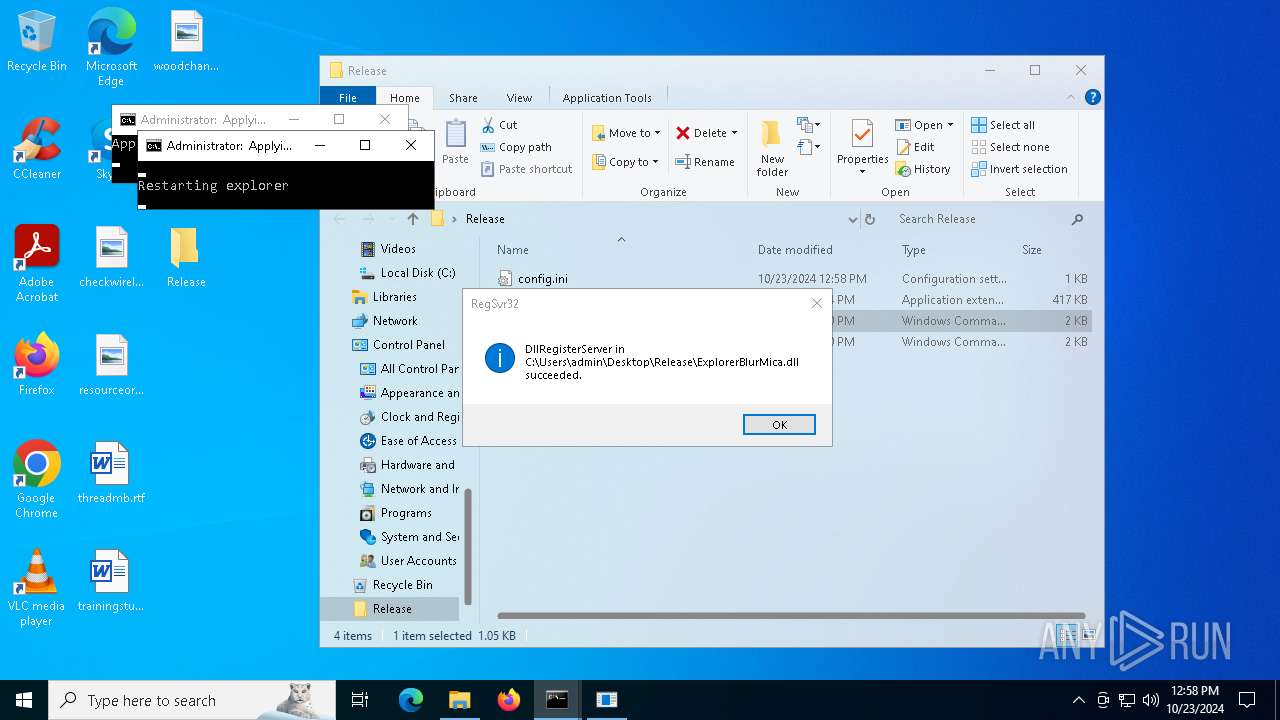
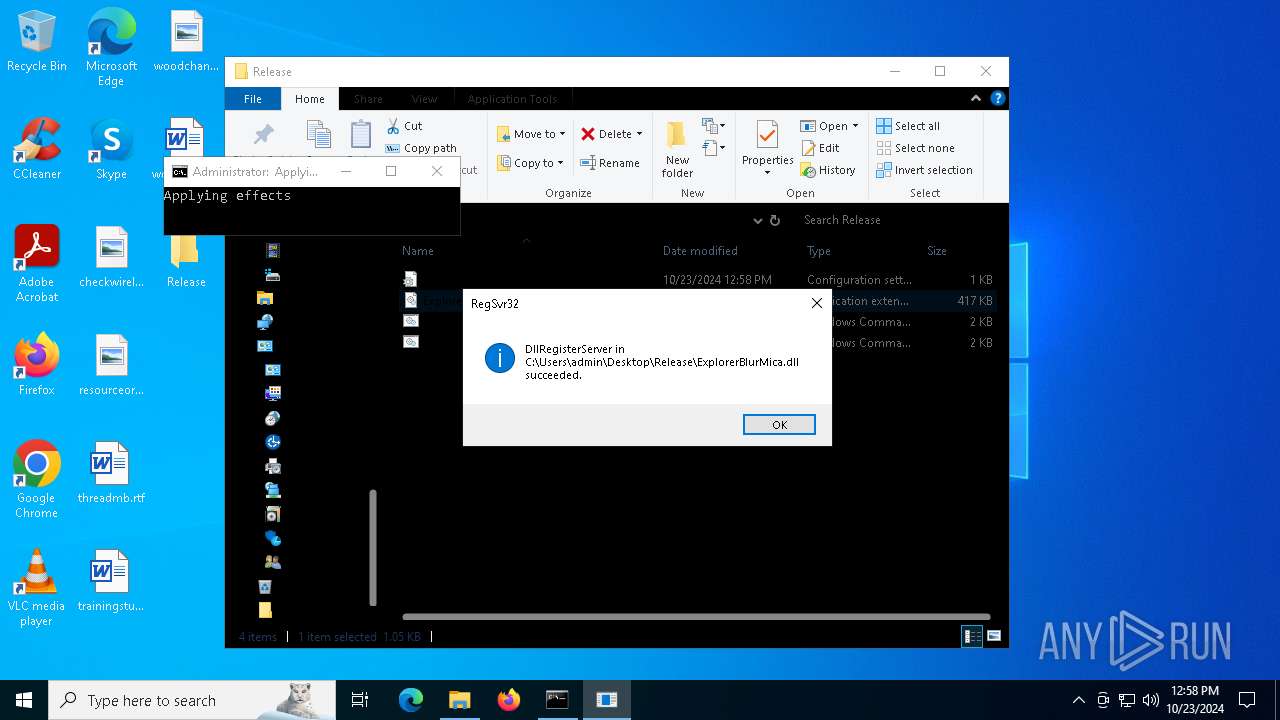
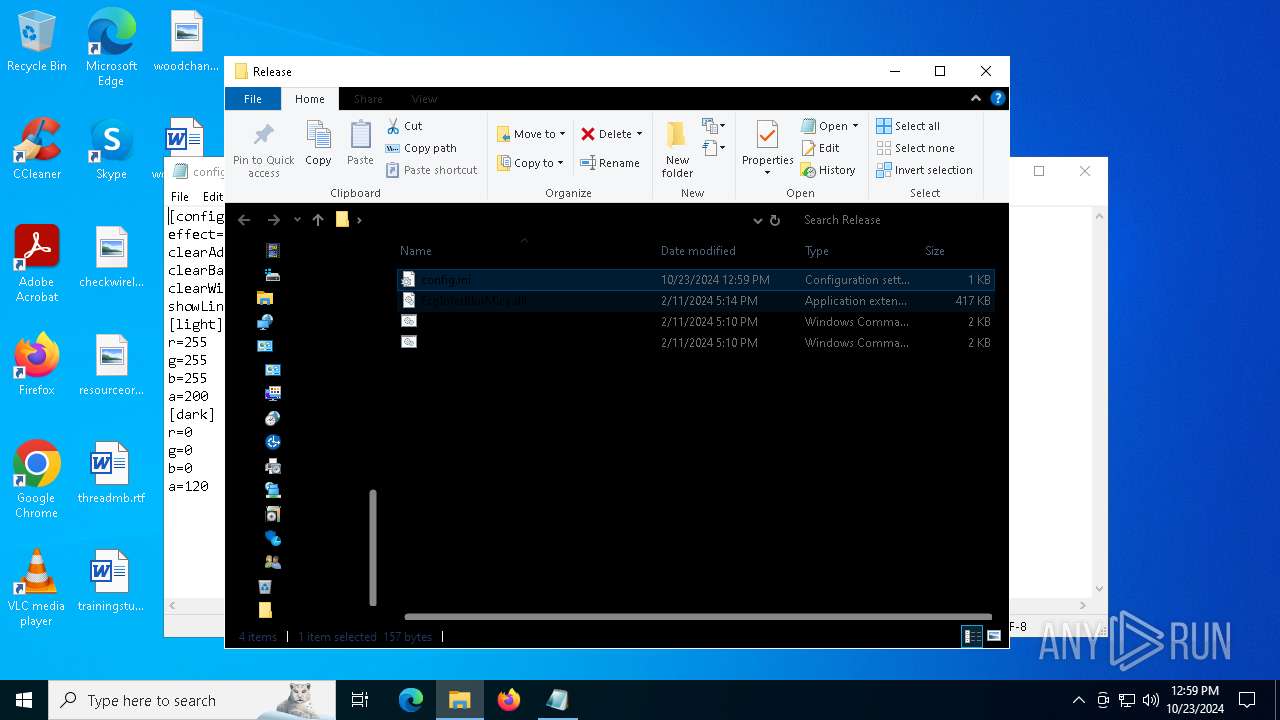
| 1196 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1196.4614\Release\ExplorerBlurMica.dll | executable | |
MD5:B10D1151419C25E1E7F62FAF643026A2 | SHA256:F0FB61E3ABD19EEE67BA486045DA823A62F6B7E99FF4C51375BC280246FA49A5 | |||
| 1788 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\63\f4st08wpuYBQ5KWRJ3MqAsJB8zg[1].css | text | |
MD5:3D24779C6014BCFEFB3D9A80B8F3567B | SHA256:A7EF8FAA37710D7E90C9C8950C203C8DA82410780F872E4F217EE636250D831F | |||
| 1788 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\DeviceSearchCache\AppCache133741618502986674.txt.~tmp | text | |
MD5:180FD11F475B69869DD05B3B9272888A | SHA256:A75EAD11F270D925773B7203D5C1CBB11D8D85B91CFCC31A7EB1B367917F7AE0 | |||
| 1788 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\INetCache\P26HLZ9S\-UAIppANYxiGpRWJy2NDph4qOEw.gz[1].js | s | |
MD5:9E527B91C2D8B31B0017B76049B5E4E3 | SHA256:38EDF0F961C1CCB287880B88F12F370775FC65B2E28227EEE215E849CDBE9BBC | |||
| 1788 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\63\_BjeFNPDJ-N9umMValublyrbq4Y[1].css | text | |
MD5:15DC838A1A66277F9F4D915124DFFBBC | SHA256:9C947D5F732431197DA9DB1F159CB3D4CDC5DBFE55FDC0A9513E571FF31236A1 | |||
| 1788 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\63\4-xJy3tX6bM2BGl5zKioiEcQ1TU[1].css | text | |
MD5:94D8383805B336E533D1D234AAA98A21 | SHA256:699D6C87C646D3875C45FAB214BFE2E385B54F325F25818C72C2C45C1A5F6897 | |||
| 1584 | TiWorker.exe | C:\Windows\Logs\CBS\CBS.log | text | |
MD5:E04B5ED5607D219C8ACC6FF982C73871 | SHA256:0A194EE3998A1222BB47769D1AF8FEB5E3D08B9E7C2B54C77D70DCBCF35D33B8 | |||
| 1788 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\DeviceSearchCache\AppCache133741618502986674.txt | text | |
MD5:180FD11F475B69869DD05B3B9272888A | SHA256:A75EAD11F270D925773B7203D5C1CBB11D8D85B91CFCC31A7EB1B367917F7AE0 | |||
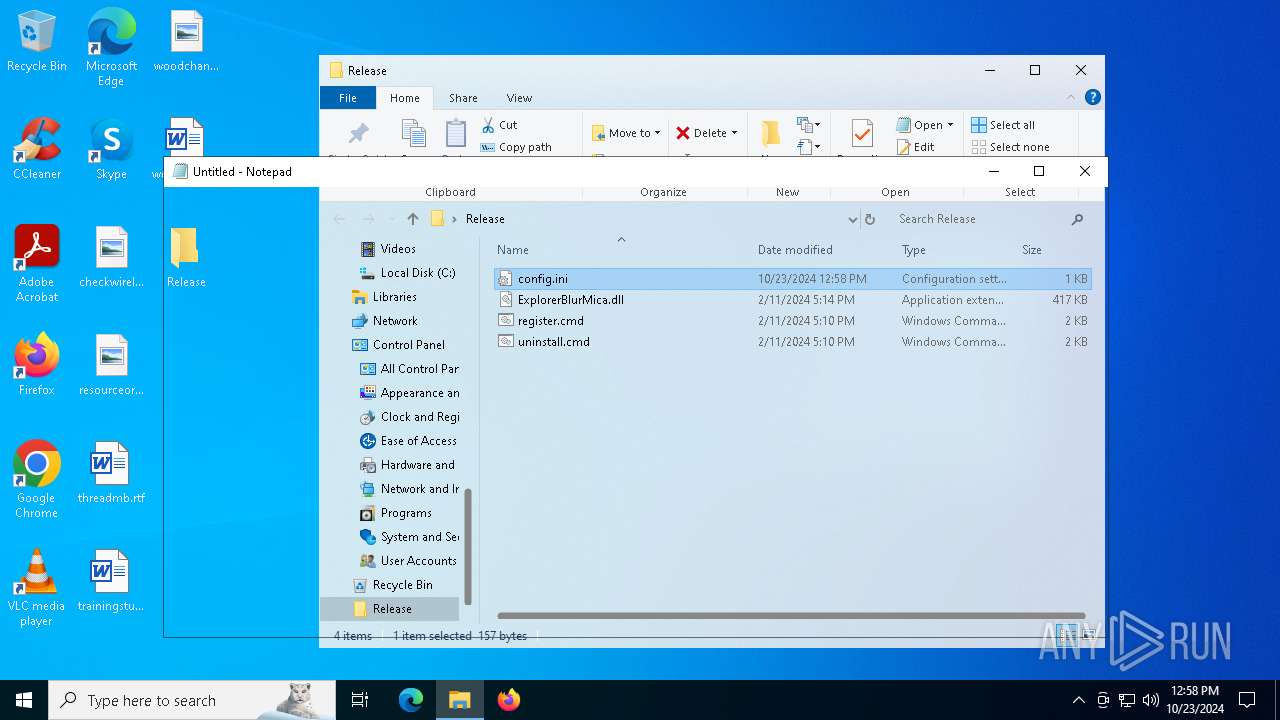
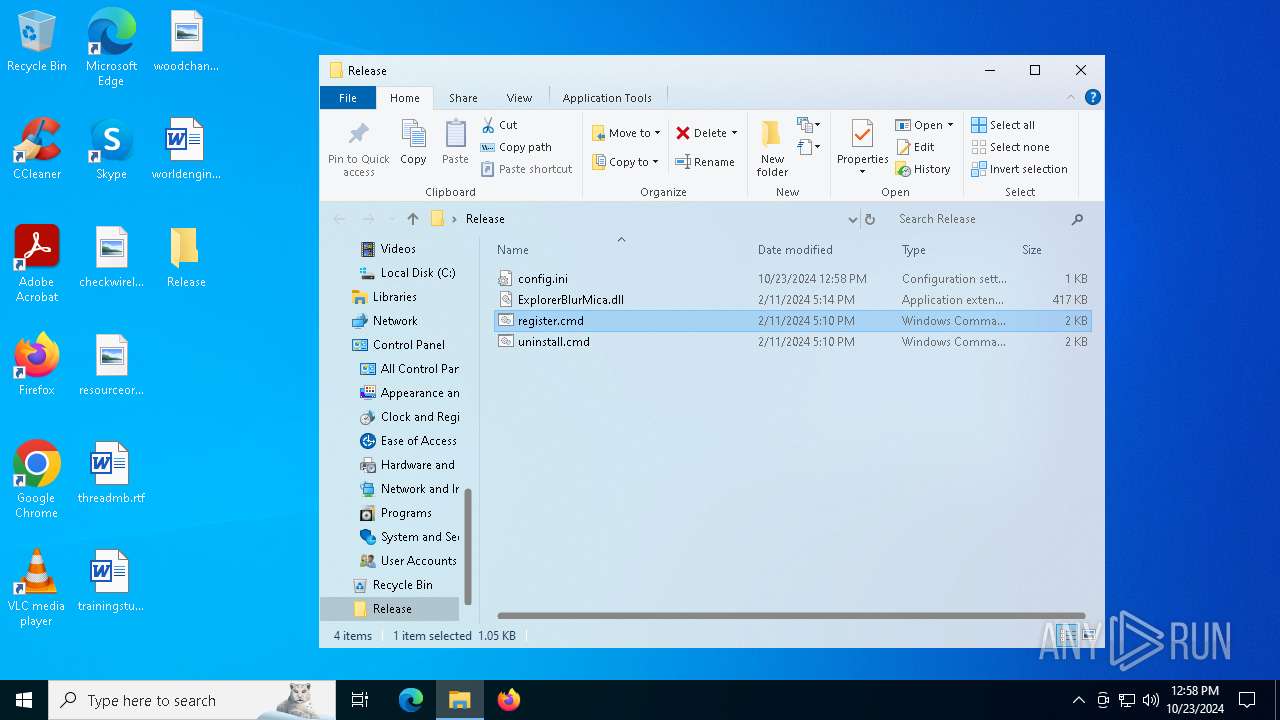
| 1196 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1196.4614\Release\register.cmd | text | |
MD5:69D7C77DA0C817B911E7FCBFEB1DD271 | SHA256:A171D3AE6B224D7C2AB8B778AA66311E2A91C91540DAB6606623B36C02F548CA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
69
DNS requests
31
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.51:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.72.205.209:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 2.16.164.51:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.23.209.179:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
r.bing.com |
| whitelisted |