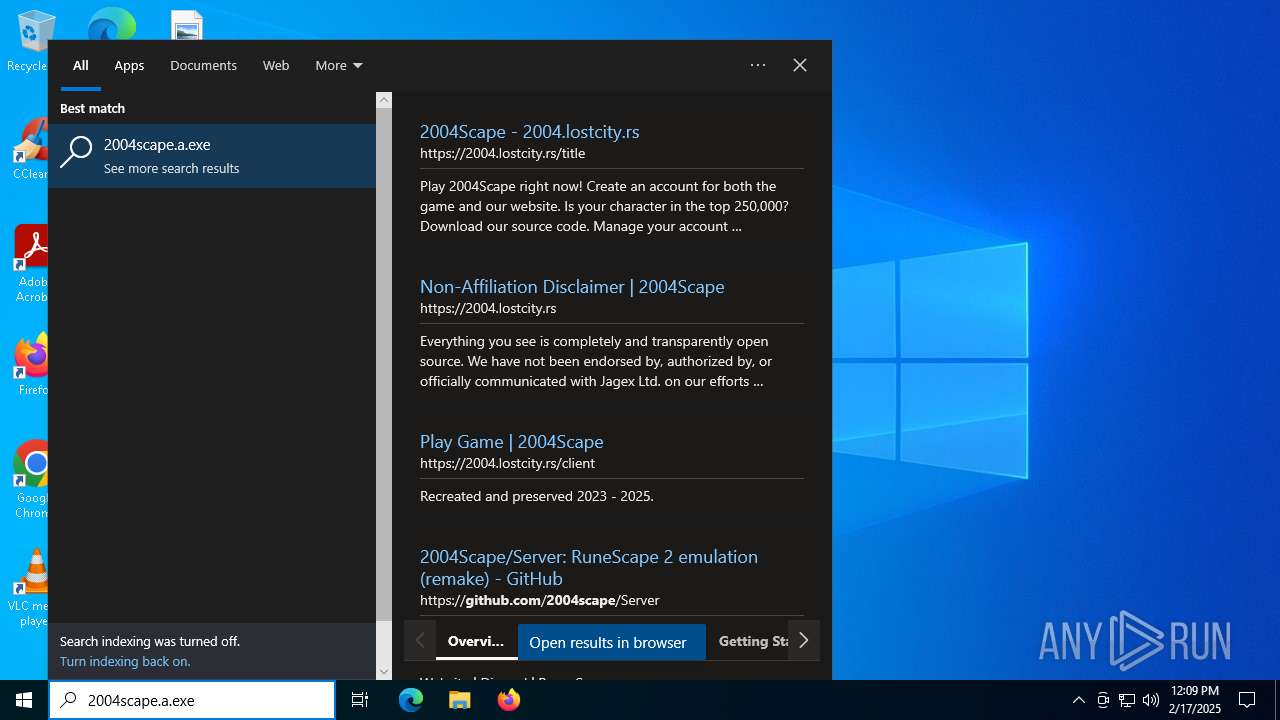
| File name: | 2004Scape.a.exe |
| Full analysis: | https://app.any.run/tasks/36efe9ce-e8d1-49e1-9e96-f80b86281ad4 |
| Verdict: | Malicious activity |
| Analysis date: | February 17, 2025, 12:07:10 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive, with extra data prepended |
| MD5: | 100640058440F586688DC2F1E94B8984 |
| SHA1: | 3684BFF8C72EA79E0D433EEBE39B5C1543807667 |
| SHA256: | 70C76421B140F947524D5D586B2B0E44E701D2D69FCBAF7FA0C76C6BE1FA1B29 |
| SSDEEP: | 98304:kY1gCzWlfOJ8Iv6jePOj7g7luUToNcuzxOjum6cdOVIBjBFGcub4qt6JFDFilBAF:c6YkHTfNL |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- jre-8u441-windows-i586-iftw.exe (PID: 7312)
- jre-8u441-windows-i586-iftw.exe (PID: 7456)
- LZMA_EXE (PID: 5560)
- installer.exe (PID: 7184)
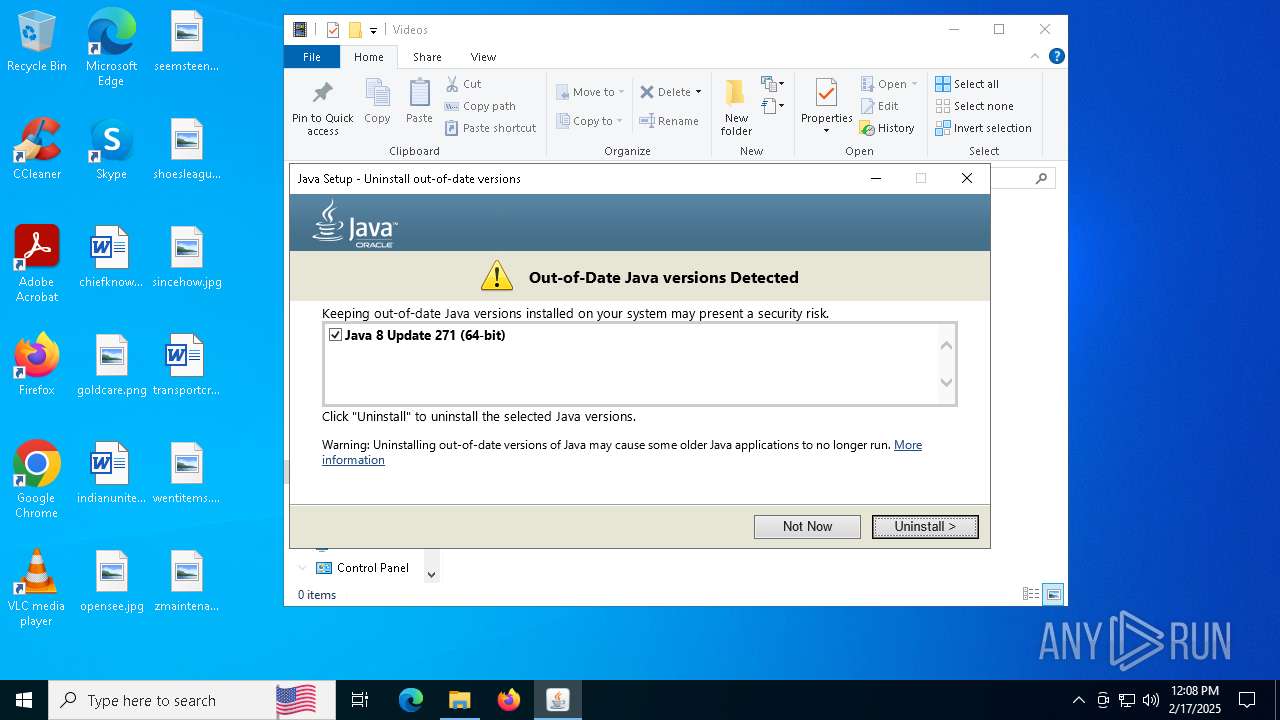
Checks for Java to be installed
- jre-8u441-windows-i586-iftw.exe (PID: 7456)
- msiexec.exe (PID: 7760)
- installer.exe (PID: 7184)
- ssvagent.exe (PID: 7404)
- jp2launcher.exe (PID: 8100)
- msiexec.exe (PID: 7772)
- jp2launcher.exe (PID: 6488)
- msiexec.exe (PID: 8132)
- javaw.exe (PID: 7400)
Reads Microsoft Outlook installation path
- jre-8u441-windows-i586-iftw.exe (PID: 7456)
Reads security settings of Internet Explorer
- jre-8u441-windows-i586-iftw.exe (PID: 7456)
- installer.exe (PID: 7184)
- jp2launcher.exe (PID: 8100)
- jp2launcher.exe (PID: 6488)
Reads Internet Explorer settings
- jre-8u441-windows-i586-iftw.exe (PID: 7456)
Starts application with an unusual extension
- jre-8u441-windows-i586-iftw.exe (PID: 7456)
Process drops legitimate windows executable
- msiexec.exe (PID: 7760)
The process drops C-runtime libraries
- msiexec.exe (PID: 7760)
Checks Windows Trust Settings
- jre-8u441-windows-i586-iftw.exe (PID: 7456)
- msiexec.exe (PID: 7760)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7760)
Creates/Modifies COM task schedule object
- installer.exe (PID: 7184)
- ssvagent.exe (PID: 7404)
INFO
Checks supported languages
- 2004Scape.a.exe (PID: 4724)
- jre-8u441-windows-i586-iftw.exe (PID: 7456)
- jre-8u441-windows-i586-iftw.exe (PID: 7312)
- LZMA_EXE (PID: 5560)
- LZMA_EXE (PID: 4872)
- msiexec.exe (PID: 6824)
- msiexec.exe (PID: 7760)
- installer.exe (PID: 7184)
- ssvagent.exe (PID: 7404)
- javaws.exe (PID: 6452)
- jp2launcher.exe (PID: 6488)
- javaw.exe (PID: 7248)
- jp2launcher.exe (PID: 8100)
- javaws.exe (PID: 6364)
- msiexec.exe (PID: 7772)
- msiexec.exe (PID: 8132)
- msiexec.exe (PID: 7544)
- javaw.exe (PID: 3260)
- msiexec.exe (PID: 6600)
- javaw.exe (PID: 7400)
- msiexec.exe (PID: 6876)
- javaw.exe (PID: 7788)
Java executable
- jre-8u441-windows-i586-iftw.exe (PID: 7472)
- jre-8u441-windows-i586-iftw.exe (PID: 7312)
- jre-8u441-windows-i586-iftw.exe (PID: 7456)
- installer.exe (PID: 7184)
The sample compiled with english language support
- firefox.exe (PID: 5432)
- jre-8u441-windows-i586-iftw.exe (PID: 7312)
- LZMA_EXE (PID: 5560)
- msiexec.exe (PID: 7760)
- jre-8u441-windows-i586-iftw.exe (PID: 7456)
- installer.exe (PID: 7184)
Manual execution by a user
- firefox.exe (PID: 3732)
Executable content was dropped or overwritten
- firefox.exe (PID: 5432)
- msiexec.exe (PID: 7760)
Application launched itself
- firefox.exe (PID: 3732)
- firefox.exe (PID: 5432)
Reads the computer name
- 2004Scape.a.exe (PID: 4724)
- jre-8u441-windows-i586-iftw.exe (PID: 7312)
- jre-8u441-windows-i586-iftw.exe (PID: 7456)
- msiexec.exe (PID: 6824)
- msiexec.exe (PID: 7760)
- installer.exe (PID: 7184)
- jp2launcher.exe (PID: 6488)
- javaws.exe (PID: 6452)
- javaws.exe (PID: 6364)
- msiexec.exe (PID: 7772)
- jp2launcher.exe (PID: 8100)
- msiexec.exe (PID: 7544)
- msiexec.exe (PID: 6876)
- msiexec.exe (PID: 6600)
- javaw.exe (PID: 3260)
- javaw.exe (PID: 7400)
- msiexec.exe (PID: 8132)
- javaw.exe (PID: 7788)
Create files in a temporary directory
- jre-8u441-windows-i586-iftw.exe (PID: 7312)
- javaw.exe (PID: 7248)
- installer.exe (PID: 7184)
- jp2launcher.exe (PID: 8100)
- javaw.exe (PID: 3260)
- javaw.exe (PID: 7400)
- javaw.exe (PID: 7788)
Checks proxy server information
- jre-8u441-windows-i586-iftw.exe (PID: 7456)
Creates files or folders in the user directory
- jre-8u441-windows-i586-iftw.exe (PID: 7456)
- LZMA_EXE (PID: 5560)
- LZMA_EXE (PID: 4872)
Reads the software policy settings
- jre-8u441-windows-i586-iftw.exe (PID: 7456)
- msiexec.exe (PID: 7760)
Reads the machine GUID from the registry
- jre-8u441-windows-i586-iftw.exe (PID: 7456)
- msiexec.exe (PID: 7760)
Reads CPU info
- msiexec.exe (PID: 7760)
Creates a software uninstall entry
- msiexec.exe (PID: 7760)
Creates files in the program directory
- javaw.exe (PID: 7248)
- installer.exe (PID: 7184)
Local mutex for internet shortcut management
- installer.exe (PID: 7184)
JAVA mutex has been found
- jp2launcher.exe (PID: 8100)
- msiexec.exe (PID: 7544)
- msiexec.exe (PID: 6876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:05:29 16:13:54+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 2.22 |
| CodeSize: | 44032 |
| InitializedDataSize: | 103936 |
| UninitializedDataSize: | 38912 |
| EntryPoint: | 0x1590 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
179
Monitored processes
43
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1412 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | LZMA_EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2084 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{06622D85-6856-4460-8DE1-A81921B41C4B} | C:\Windows\SysWOW64\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3260 | -Djdk.disableLastUsageTracking -cp "C:\Program Files (x86)\Java\jre1.8.0_441\bin\..\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -systemConfig deployment.expiration.check.enabled false | C:\Program Files (x86)\Java\jre1.8.0_441\bin\javaw.exe | — | jre-8u441-windows-i586-iftw.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.4410.7 Modules
| |||||||||||||||
| 3640 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1912 -parentBuildID 20240213221259 -prefsHandle 1844 -prefMapHandle 1832 -prefsLen 31031 -prefMapSize 244583 -appDir "C:\Program Files\Mozilla Firefox\browser" - {ba07dbff-7195-4ace-a39a-35218679c29a} 5432 "\\.\pipe\gecko-crash-server-pipe.5432" 2b939fed810 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 1 Version: 123.0 Modules
| |||||||||||||||
| 3664 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | LZMA_EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3732 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 3876 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4724 | "C:\Users\admin\AppData\Local\Temp\2004Scape.a.exe" | C:\Users\admin\AppData\Local\Temp\2004Scape.a.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 4872 | "C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_441\LZMA_EXE" d "C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_441\jre1.8.0_441.msi" "C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_441\msi.tmp" | C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_441\LZMA_EXE | — | jre-8u441-windows-i586-iftw.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 5432 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
Total events
55 085
Read events
33 847
Write events
12 893
Delete events
8 345
Modification events
| (PID) Process: | (5432) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (5432) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (7456) jre-8u441-windows-i586-iftw.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\JavaSoft |
| Operation: | delete value | Name: | InstallStatus |
Value: | |||
| (PID) Process: | (7456) jre-8u441-windows-i586-iftw.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7456) jre-8u441-windows-i586-iftw.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7456) jre-8u441-windows-i586-iftw.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7456) jre-8u441-windows-i586-iftw.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFavoritesInitialSelection |
Value: | |||
| (PID) Process: | (7456) jre-8u441-windows-i586-iftw.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFeedsInitialSelection |
Value: | |||
| (PID) Process: | (7456) jre-8u441-windows-i586-iftw.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\JavaSoft\Java Update\Policy |
| Operation: | write | Name: | Country |
Value: NL | |||
| (PID) Process: | (7456) jre-8u441-windows-i586-iftw.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\JavaSoft\Java Update\Policy |
| Operation: | write | Name: | Method |
Value: jother | |||
Executable files
207
Suspicious files
280
Text files
136
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5432 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 5432 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 5432 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:6FAEC95F36DFDDE92F12A7AB381A7073 | SHA256:3F7C70351500137CA4C25C1CD47FE5EA5B48A2B1BFADC29CB3C146F28894D708 | |||
| 5432 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5432 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.bin | binary | |
MD5:D30F5B10F3D4B3992E4D666F622163F4 | SHA256:2585819A7401A308DA879FA416278E473CEA5F6D0D24C59F514C5A698C61D03A | |||
| 5432 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 5432 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5432 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5432 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 5432 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
61
TCP/UDP connections
188
DNS requests
206
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5432 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5432 | firefox.exe | POST | 200 | 2.16.168.113:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
5432 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
5432 | firefox.exe | POST | 200 | 2.16.168.113:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
5432 | firefox.exe | POST | 200 | 2.16.168.113:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
5432 | firefox.exe | POST | 200 | 142.250.186.99:80 | http://o.pki.goog/s/wr3/jLM | unknown | — | — | whitelisted |
5432 | firefox.exe | POST | 200 | 142.250.186.99:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
5432 | firefox.exe | POST | 200 | 142.250.186.99:80 | http://o.pki.goog/s/wr3/3cs | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5064 | SearchApp.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
440 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2160 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.31.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
1076 | svchost.exe | 92.123.18.10:443 | go.microsoft.com | AKAMAI-AS | AT | whitelisted |
5432 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
spocs.getpocket.com |
| whitelisted |