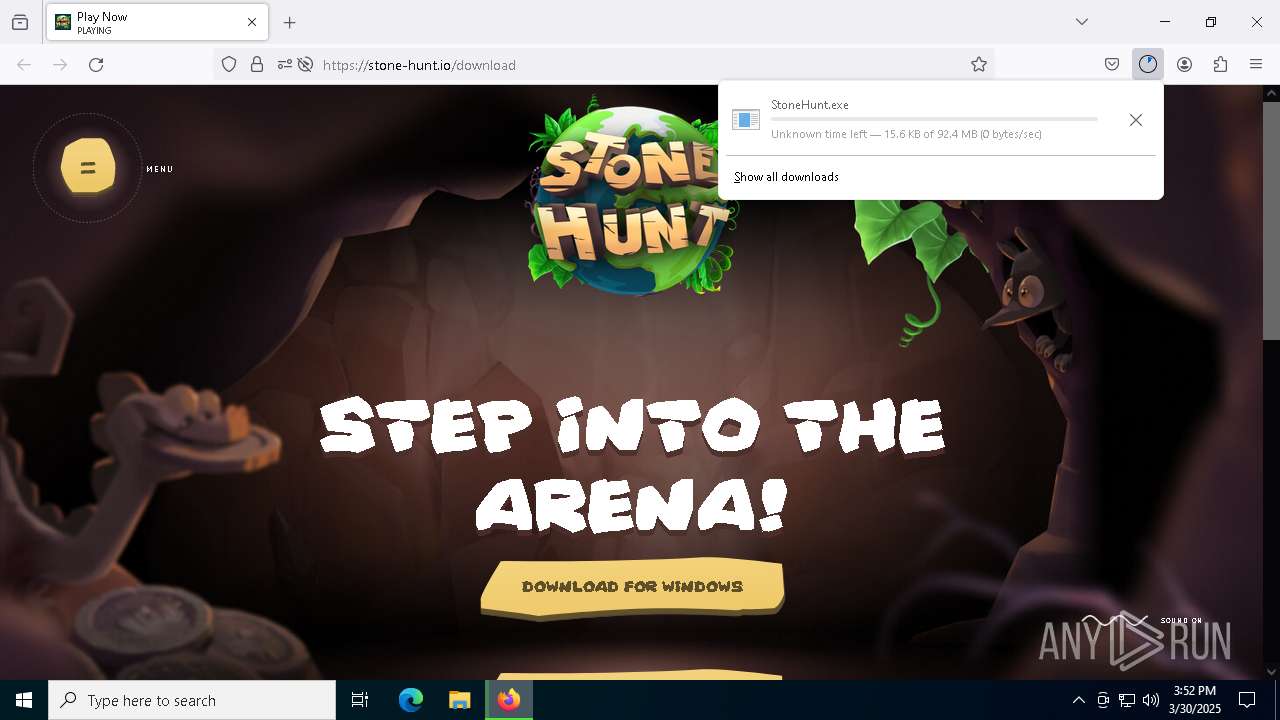
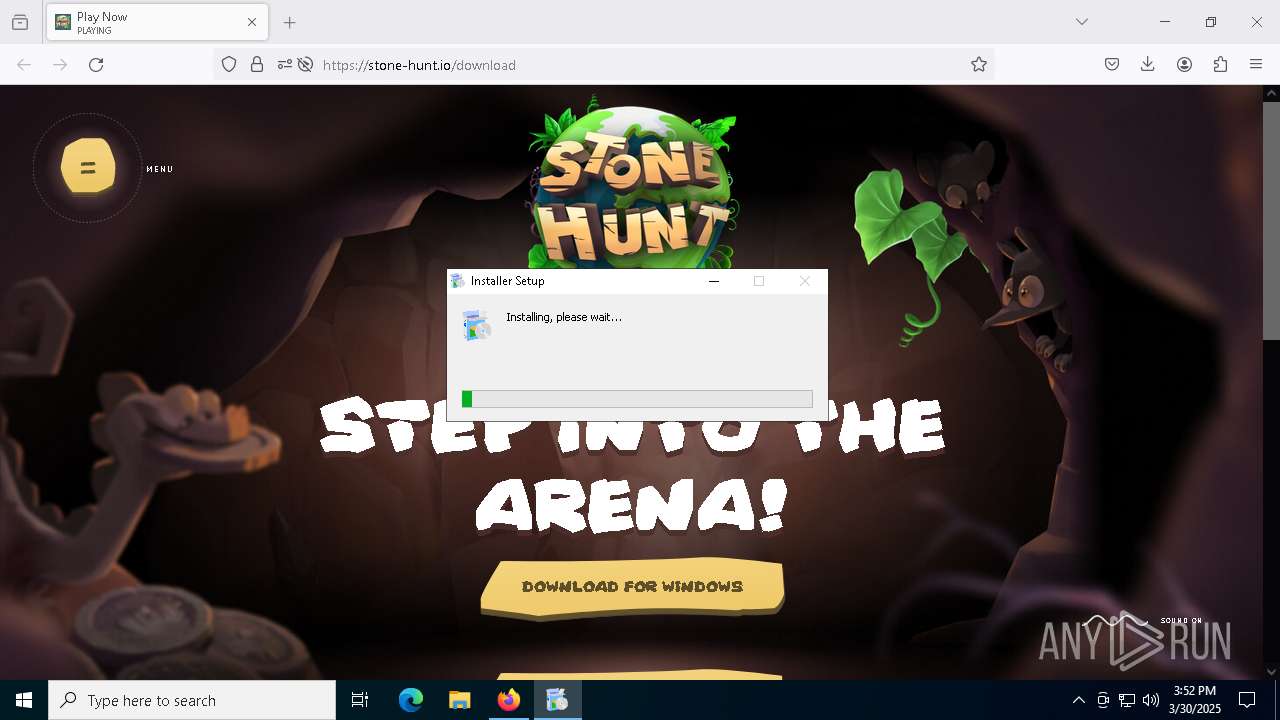
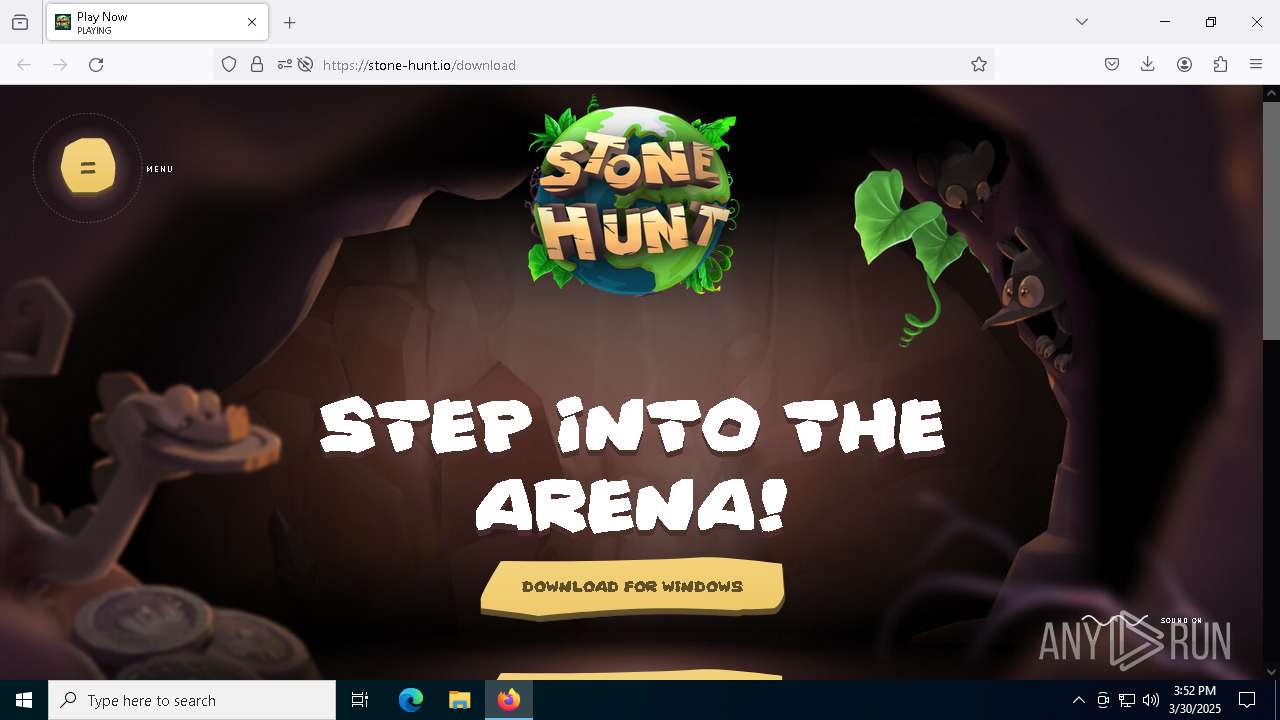
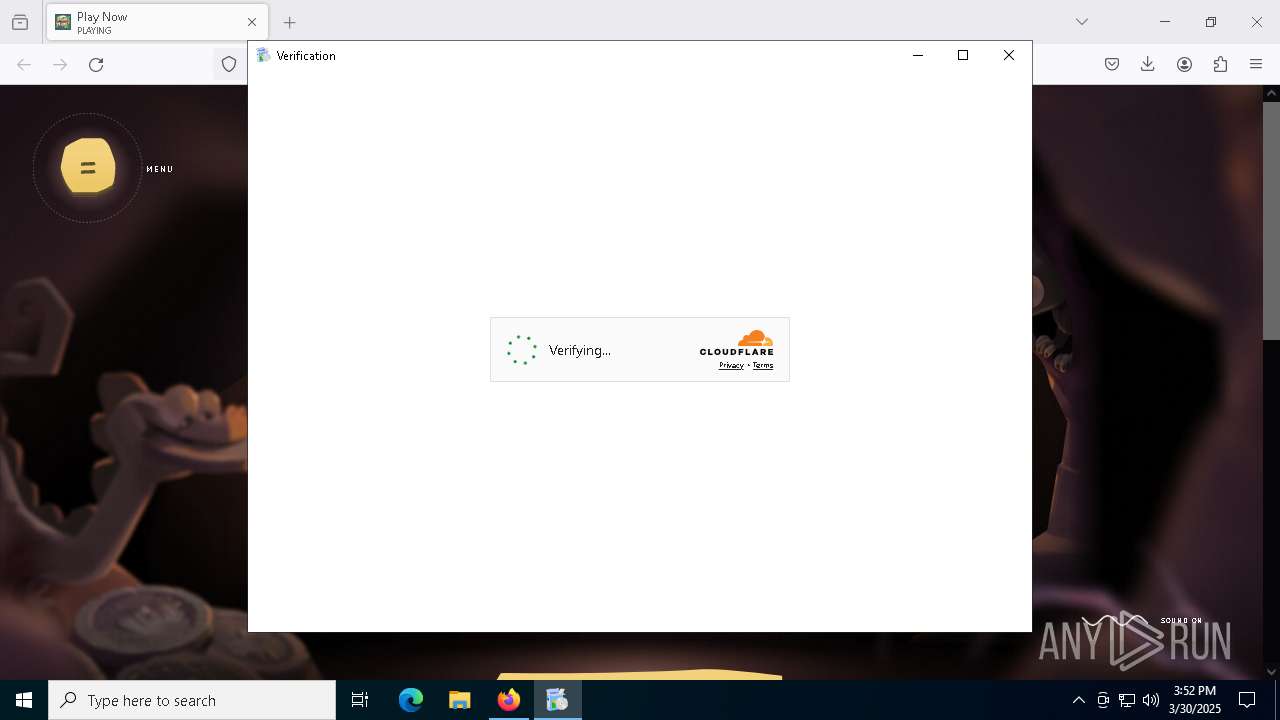
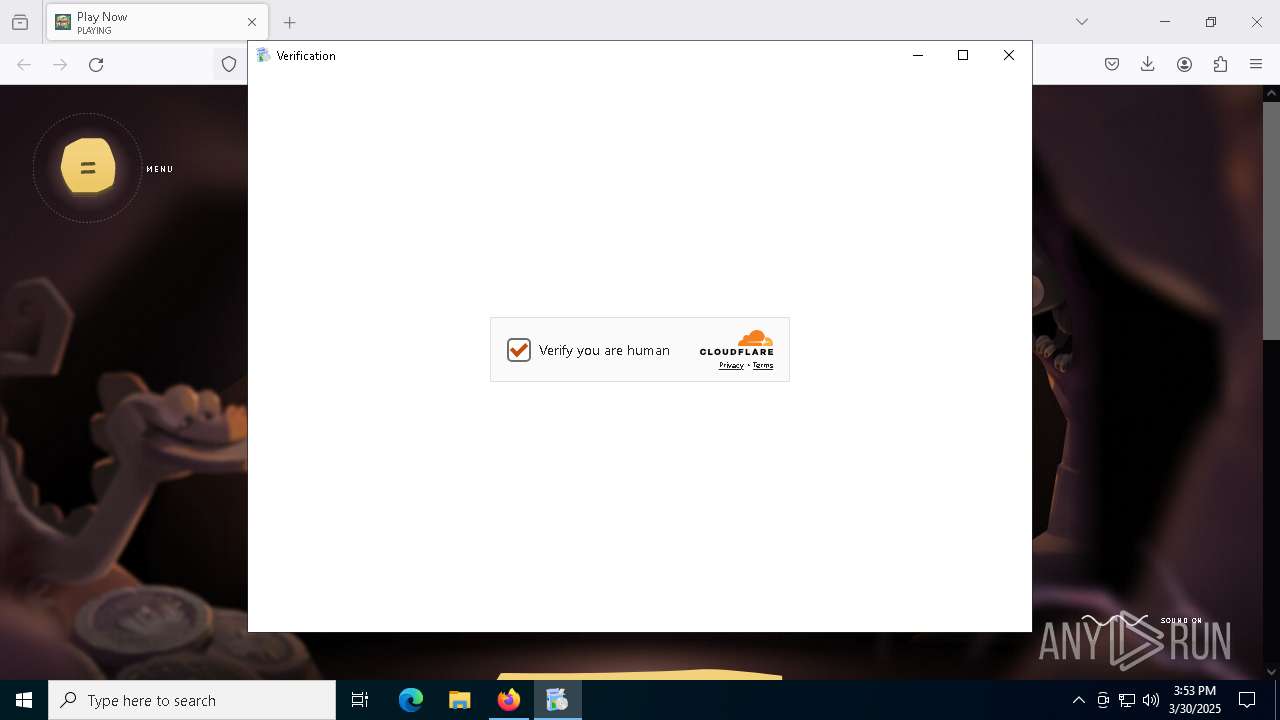
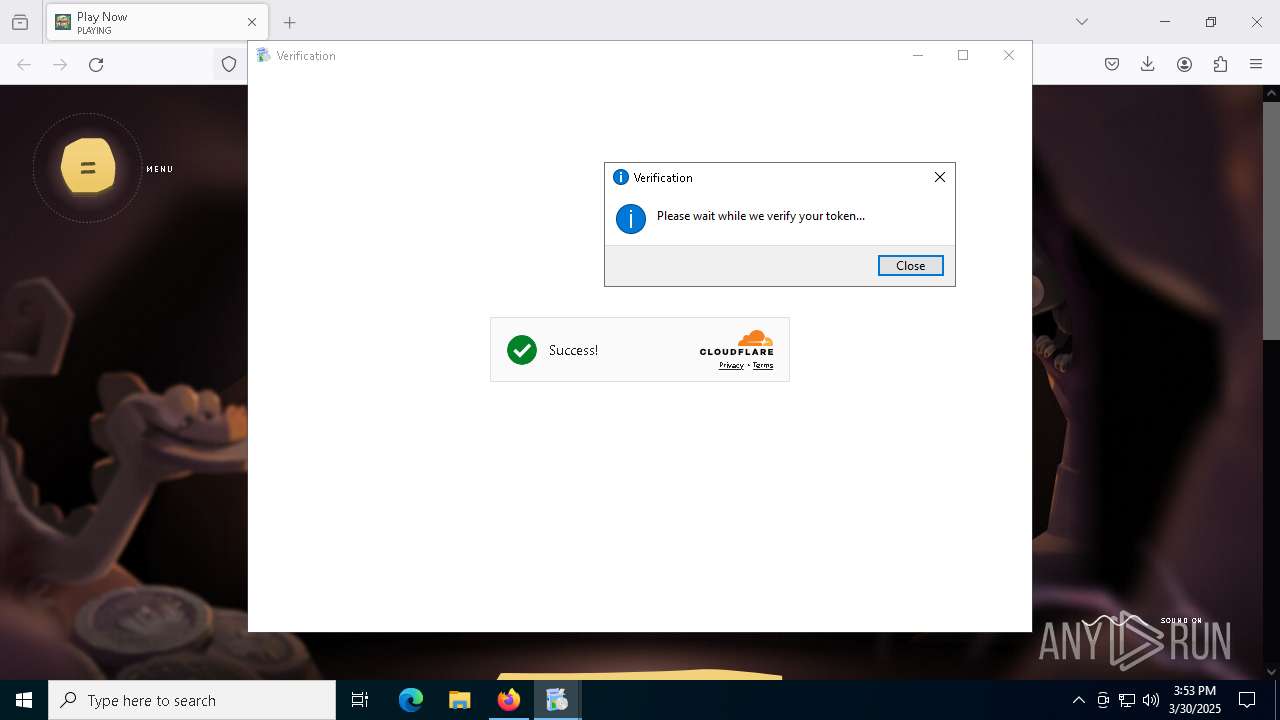
| URL: | https://stone-hunt.io/download |
| Full analysis: | https://app.any.run/tasks/aaf08294-f208-4a9b-bd38-c1fb104cbef5 |
| Verdict: | Malicious activity |
| Analysis date: | March 30, 2025, 15:51:39 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 9FC4061DFE951446E3866EB6BD7616E9 |
| SHA1: | C2F2355C9D09DB1DC00785384D5053D932ECD44A |
| SHA256: | 70B9E8C2A423073E1BF72DB7B2157E457F905F9739441BEEAE8D22AE943FA445 |
| SSDEEP: | 3:N8cQAw7:2cQ/7 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- StoneHunt.exe (PID: 8200)
Process drops legitimate windows executable
- StoneHunt.exe (PID: 8200)
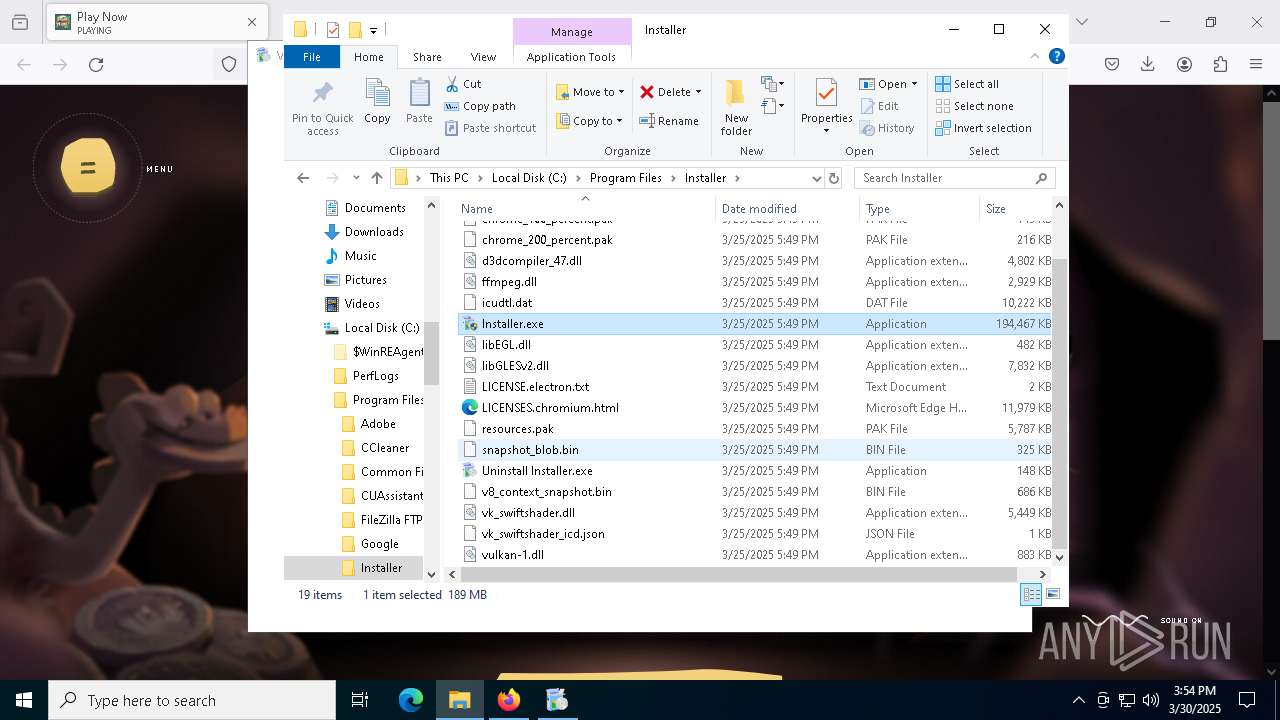
- Installer.exe (PID: 6744)
Creates a software uninstall entry
- StoneHunt.exe (PID: 8200)
Executable content was dropped or overwritten
- StoneHunt.exe (PID: 8200)
- Installer.exe (PID: 6744)
Drops 7-zip archiver for unpacking
- StoneHunt.exe (PID: 8200)
Reads security settings of Internet Explorer
- StoneHunt.exe (PID: 8200)
- Installer.exe (PID: 6744)
There is functionality for taking screenshot (YARA)
- StoneHunt.exe (PID: 8200)
Application launched itself
- Installer.exe (PID: 6744)
- Installer.exe (PID: 8748)
- Installer.exe (PID: 7556)
The process drops C-runtime libraries
- Installer.exe (PID: 6744)
The process creates files with name similar to system file names
- StoneHunt.exe (PID: 8200)
Reads the date of Windows installation
- Installer.exe (PID: 6744)
Starts CMD.EXE for commands execution
- Installer.exe (PID: 6744)
Process drops python dynamic module
- Installer.exe (PID: 6744)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2344)
- cmd.exe (PID: 4268)
- cmd.exe (PID: 208)
- cmd.exe (PID: 8768)
- cmd.exe (PID: 7084)
- cmd.exe (PID: 8276)
- cmd.exe (PID: 4108)
- cmd.exe (PID: 8912)
- cmd.exe (PID: 516)
- cmd.exe (PID: 8232)
- cmd.exe (PID: 3028)
- cmd.exe (PID: 6268)
- cmd.exe (PID: 1040)
- cmd.exe (PID: 496)
- cmd.exe (PID: 776)
- cmd.exe (PID: 6564)
- cmd.exe (PID: 3760)
- cmd.exe (PID: 632)
INFO
Executable content was dropped or overwritten
- firefox.exe (PID: 7376)
Application launched itself
- firefox.exe (PID: 7352)
- firefox.exe (PID: 7376)
Checks supported languages
- StoneHunt.exe (PID: 8200)
- Installer.exe (PID: 8608)
- Installer.exe (PID: 6744)
- Installer.exe (PID: 4244)
- Installer.exe (PID: 8088)
- Installer.exe (PID: 9040)
- Installer.exe (PID: 8840)
- Installer.exe (PID: 8748)
- Installer.exe (PID: 3176)
- Installer.exe (PID: 5364)
- Installer.exe (PID: 1128)
- Installer.exe (PID: 7556)
- Installer.exe (PID: 8224)
- Installer.exe (PID: 8976)
- Installer.exe (PID: 1748)
Reads the computer name
- StoneHunt.exe (PID: 8200)
- Installer.exe (PID: 6744)
- Installer.exe (PID: 4244)
- Installer.exe (PID: 8748)
- Installer.exe (PID: 3176)
- Installer.exe (PID: 5364)
- Installer.exe (PID: 8608)
- Installer.exe (PID: 7556)
- Installer.exe (PID: 8224)
- Installer.exe (PID: 1748)
Autorun file from Downloads
- firefox.exe (PID: 7376)
The sample compiled with english language support
- StoneHunt.exe (PID: 8200)
- Installer.exe (PID: 6744)
Manual execution by a user
- Installer.exe (PID: 2984)
- Installer.exe (PID: 6744)
- Installer.exe (PID: 3888)
- Installer.exe (PID: 7556)
Create files in a temporary directory
- StoneHunt.exe (PID: 8200)
- Installer.exe (PID: 6744)
- Installer.exe (PID: 8748)
- Installer.exe (PID: 7556)
Creates files in the program directory
- StoneHunt.exe (PID: 8200)
Creates files or folders in the user directory
- StoneHunt.exe (PID: 8200)
- Installer.exe (PID: 6744)
- Installer.exe (PID: 8608)
- Installer.exe (PID: 5364)
- Installer.exe (PID: 1748)
- Installer.exe (PID: 7556)
- Installer.exe (PID: 8748)
Reads the software policy settings
- slui.exe (PID: 5596)
- slui.exe (PID: 7812)
Reads Environment values
- Installer.exe (PID: 6744)
- Installer.exe (PID: 8748)
- Installer.exe (PID: 7556)
Process checks computer location settings
- Installer.exe (PID: 6744)
- Installer.exe (PID: 8840)
- Installer.exe (PID: 9040)
- Installer.exe (PID: 8088)
- Installer.exe (PID: 8748)
- Installer.exe (PID: 1128)
- Installer.exe (PID: 7556)
- Installer.exe (PID: 8976)
Checks proxy server information
- Installer.exe (PID: 6744)
- Installer.exe (PID: 8748)
- slui.exe (PID: 7812)
- Installer.exe (PID: 7556)
Reads product name
- Installer.exe (PID: 6744)
- Installer.exe (PID: 8748)
- Installer.exe (PID: 7556)
Reads the machine GUID from the registry
- Installer.exe (PID: 6744)
- Installer.exe (PID: 8748)
- Installer.exe (PID: 7556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
227
Monitored processes
91
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | C:\WINDOWS\system32\cmd.exe /d /s /c "powershell.exe -Command "(Get-CimInstance Win32_ComputerSystemProduct).UUID"" | C:\Windows\System32\cmd.exe | — | Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 496 | C:\WINDOWS\system32\cmd.exe /d /s /c "powershell.exe -Command "(Get-CimInstance Win32_ComputerSystemProduct).UUID"" | C:\Windows\System32\cmd.exe | — | Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | C:\WINDOWS\system32\cmd.exe /d /s /c "powershell.exe -Command "(Get-CimInstance Win32_ComputerSystemProduct).UUID"" | C:\Windows\System32\cmd.exe | — | Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | C:\WINDOWS\system32\cmd.exe /d /s /c "powershell.exe -Command "(Get-CimInstance Win32_ComputerSystemProduct).UUID"" | C:\Windows\System32\cmd.exe | — | Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 776 | C:\WINDOWS\system32\cmd.exe /d /s /c "powershell.exe -Command "(Get-CimInstance Win32_ComputerSystemProduct).UUID"" | C:\Windows\System32\cmd.exe | — | Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 780 | powershell.exe -Command "(Get-CimInstance Win32_ComputerSystemProduct).UUID" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 924 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | C:\WINDOWS\system32\cmd.exe /d /s /c "powershell.exe -Command "(Get-CimInstance Win32_ComputerSystemProduct).UUID"" | C:\Windows\System32\cmd.exe | — | Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | "C:\Program Files\Installer\Installer.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Roaming\Installer" --app-path="C:\Program Files\Installer\resources\app.asar" --no-sandbox --no-zygote --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --field-trial-handle=1800,i,8224431826895847488,12693104994576288256,262144 --enable-features=PdfUseShowSaveFilePicker --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit --variations-seed-version --mojo-platform-channel-handle=2512 /prefetch:1 | C:\Program Files\Installer\Installer.exe | — | Installer.exe | |||||||||||
User: admin Company: GitHub, Inc. Integrity Level: HIGH Description: This is an innovative application developed to the highest security standards, ensuring reliable protection of your data. Exit code: 0 Version: 7.13.25 Modules
| |||||||||||||||
| 1128 | powershell.exe -Command "(Get-CimInstance Win32_ComputerSystemProduct).UUID" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
100 047
Read events
99 937
Write events
20
Delete events
90
Modification events
| (PID) Process: | (7376) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (8200) StoneHunt.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\c4f5041e-7e61-54a5-883d-d6f55efb1083 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\Installer | |||
| (PID) Process: | (8200) StoneHunt.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\c4f5041e-7e61-54a5-883d-d6f55efb1083 |
| Operation: | write | Name: | KeepShortcuts |
Value: true | |||
| (PID) Process: | (8200) StoneHunt.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\c4f5041e-7e61-54a5-883d-d6f55efb1083 |
| Operation: | write | Name: | ShortcutName |
Value: Installer | |||
| (PID) Process: | (8200) StoneHunt.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\c4f5041e-7e61-54a5-883d-d6f55efb1083 |
| Operation: | write | Name: | DisplayName |
Value: Installer 7.13.25 | |||
| (PID) Process: | (8200) StoneHunt.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\c4f5041e-7e61-54a5-883d-d6f55efb1083 |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\Installer\Uninstall Installer.exe" /allusers | |||
| (PID) Process: | (8200) StoneHunt.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\c4f5041e-7e61-54a5-883d-d6f55efb1083 |
| Operation: | write | Name: | QuietUninstallString |
Value: "C:\Program Files\Installer\Uninstall Installer.exe" /allusers /S | |||
| (PID) Process: | (8200) StoneHunt.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\c4f5041e-7e61-54a5-883d-d6f55efb1083 |
| Operation: | write | Name: | DisplayVersion |
Value: 7.13.25 | |||
| (PID) Process: | (8200) StoneHunt.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\c4f5041e-7e61-54a5-883d-d6f55efb1083 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\Installer\Installer.exe,0 | |||
| (PID) Process: | (8200) StoneHunt.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\c4f5041e-7e61-54a5-883d-d6f55efb1083 |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
Executable files
51
Suspicious files
532
Text files
176
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7376 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 7376 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:59C23014570CC8BFDCA02E00B1243A23 | SHA256:FF4DABFE2C11D3720144382EB373B81B070FD4EBEC2D9A62F85C0DA252E57288 | |||
| 7376 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 7376 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7376 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 7376 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7376 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cert9.db-journal | binary | |
MD5:61F8F3E553FD240381EE996FD0B1CDAF | SHA256:1F6E7B47DCBD3CAA75B07231898A43F01B1954AFB6F333AE554685F1EA5EC12D | |||
| 7376 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
| 7376 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\protections.sqlite-journal | binary | |
MD5:EB41BE9CB8B518BC920F12813D7FF638 | SHA256:9C2B63816119CAA13E86DBA292616005148A3BB8F6B5C1FD19B3F69DA196B7E6 | |||
| 7376 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\AlternateServices.bin | binary | |
MD5:225425AC2DFE5E54D3893EA1647EB3CA | SHA256:9197C9ECECB4CB2B44A67564C033FDC7FFFB5581C2431D3323E26EBFCDBB142A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
91
DNS requests
134
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.31:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7376 | firefox.exe | POST | 200 | 142.250.184.227:80 | http://o.pki.goog/s/wr3/cgo | unknown | — | — | whitelisted |
7376 | firefox.exe | POST | 200 | 184.24.77.59:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
7376 | firefox.exe | POST | 200 | 142.250.184.227:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.31:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7376 | firefox.exe | POST | 200 | 142.250.184.227:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
7376 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
7376 | firefox.exe | POST | 200 | 18.245.65.219:80 | http://ocsp.r2m02.amazontrust.com/ | unknown | — | — | whitelisted |
7376 | firefox.exe | POST | 200 | 184.24.77.59:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
7376 | firefox.exe | POST | 200 | 18.245.65.219:80 | http://ocsp.r2m02.amazontrust.com/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.216.77.31:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.31:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
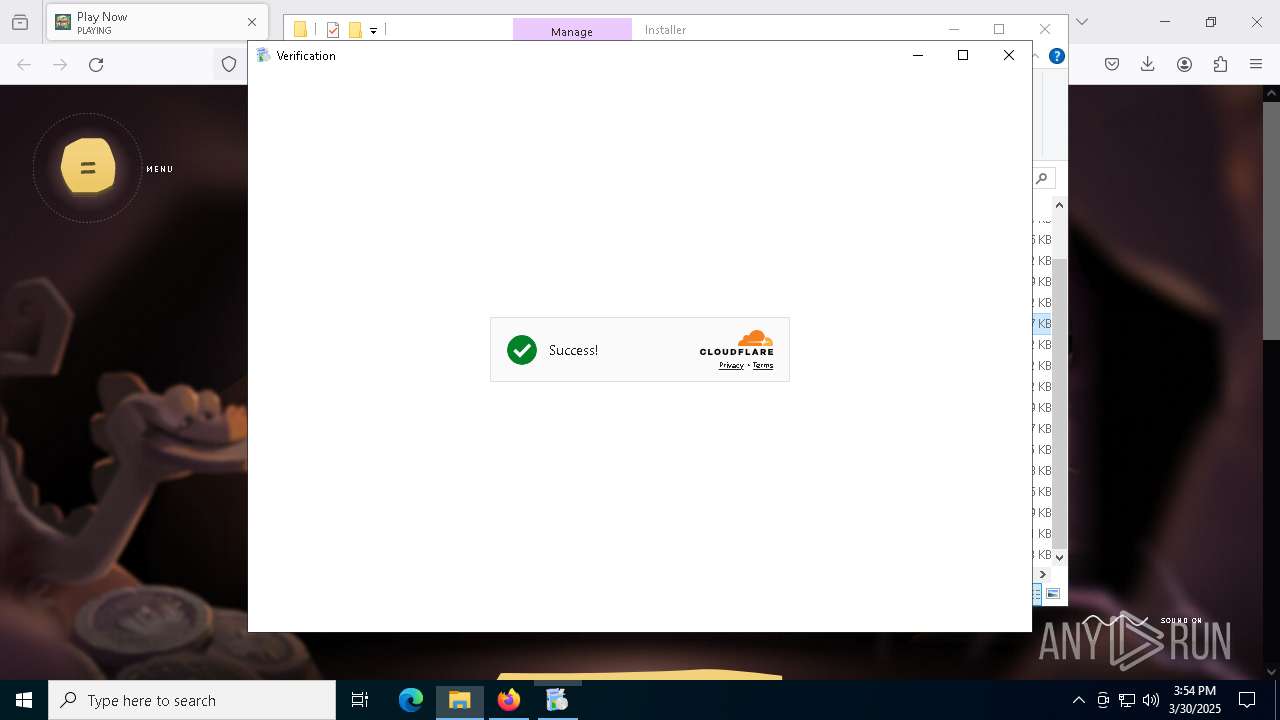
7376 | firefox.exe | 104.21.11.60:443 | stone-hunt.io | CLOUDFLARENET | — | malicious |
7376 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
7376 | firefox.exe | 34.117.188.166:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
7376 | firefox.exe | 34.160.144.191:443 | content-signature-2.cdn.mozilla.net | GOOGLE | US | whitelisted |
7376 | firefox.exe | 142.250.184.227:80 | o.pki.goog | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
stone-hunt.io |
| malicious |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
prod.ads.prod.webservices.mozgcp.net |
| whitelisted |
content-signature-2.cdn.mozilla.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
8608 | Installer.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
8608 | Installer.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
8608 | Installer.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
8608 | Installer.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
8608 | Installer.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
8608 | Installer.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
8608 | Installer.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
8608 | Installer.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |