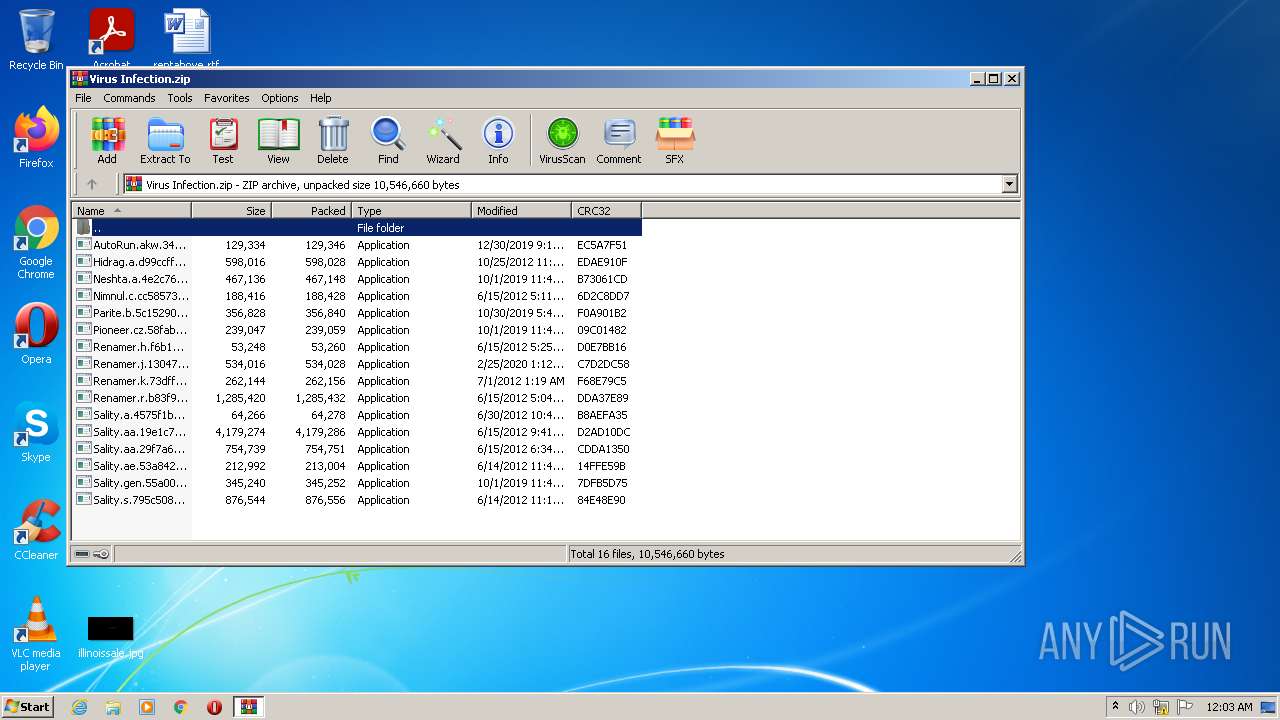
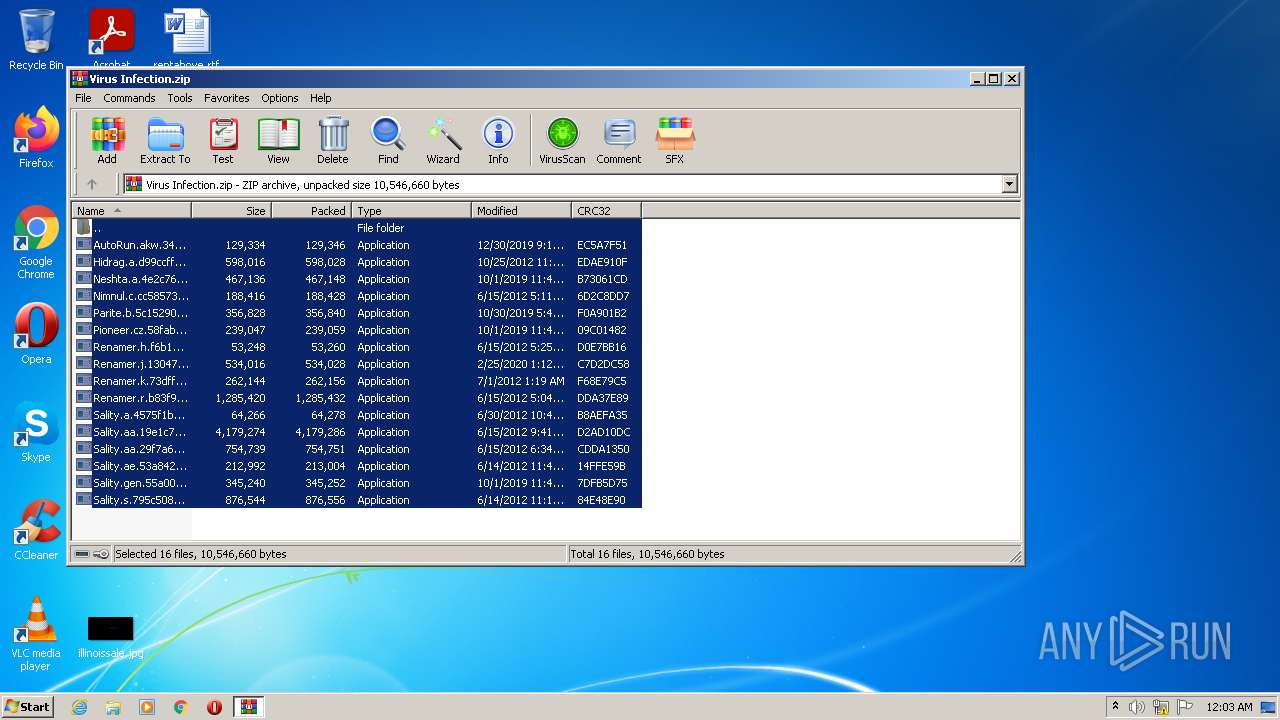
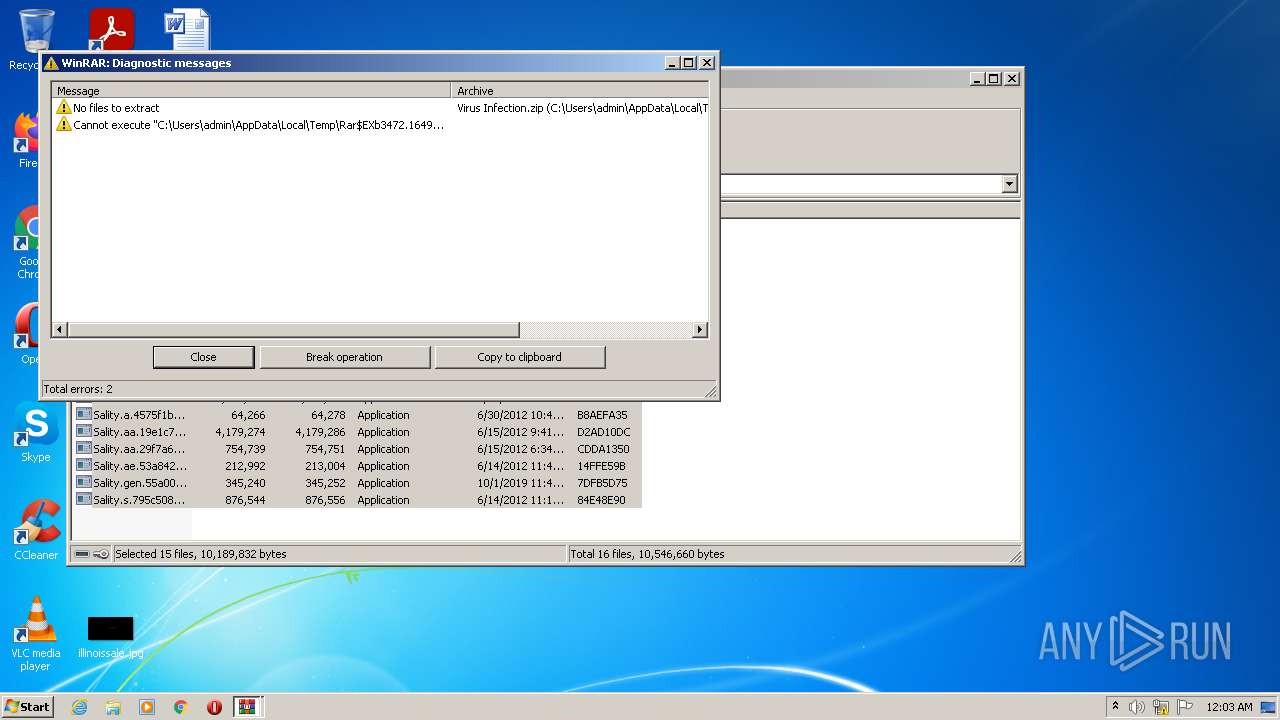
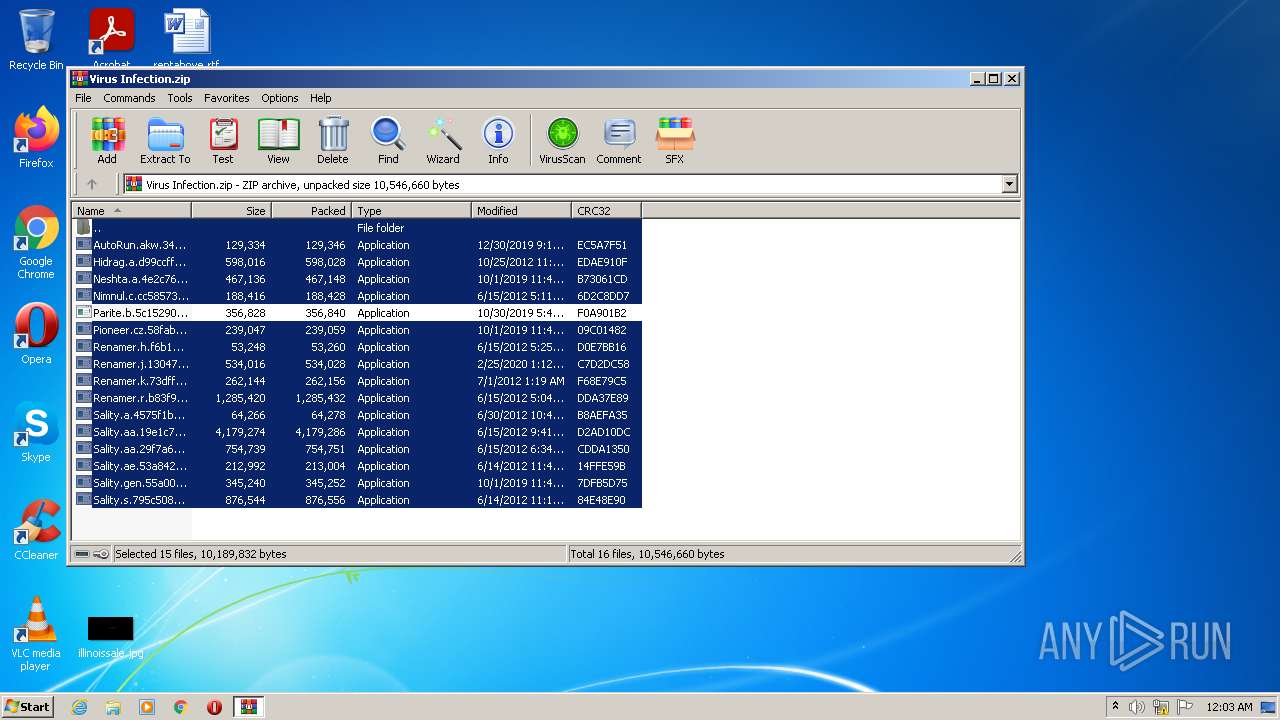
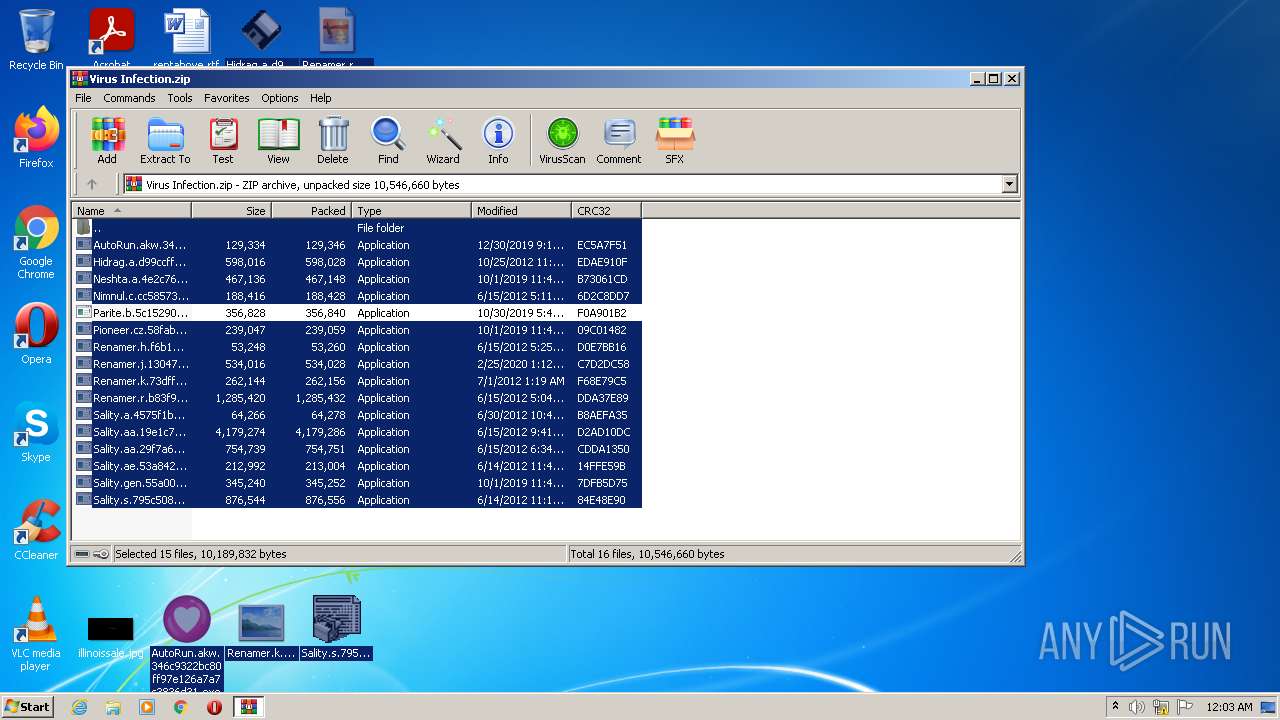
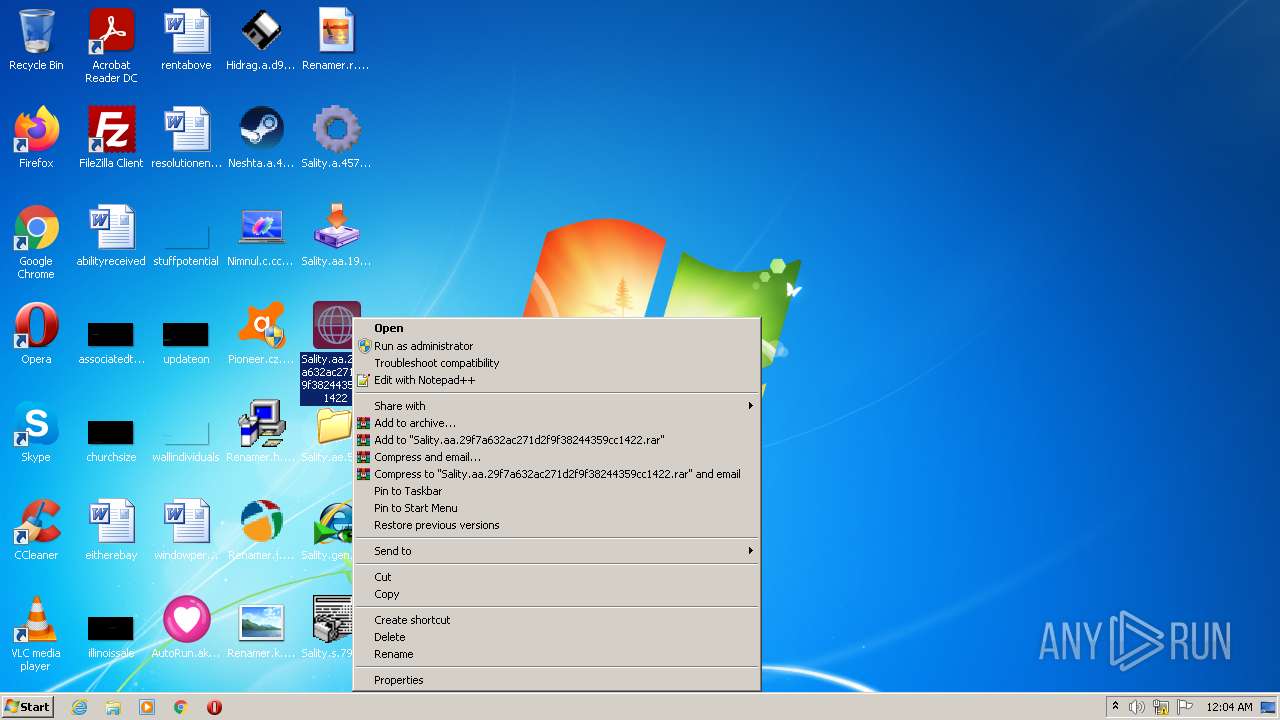
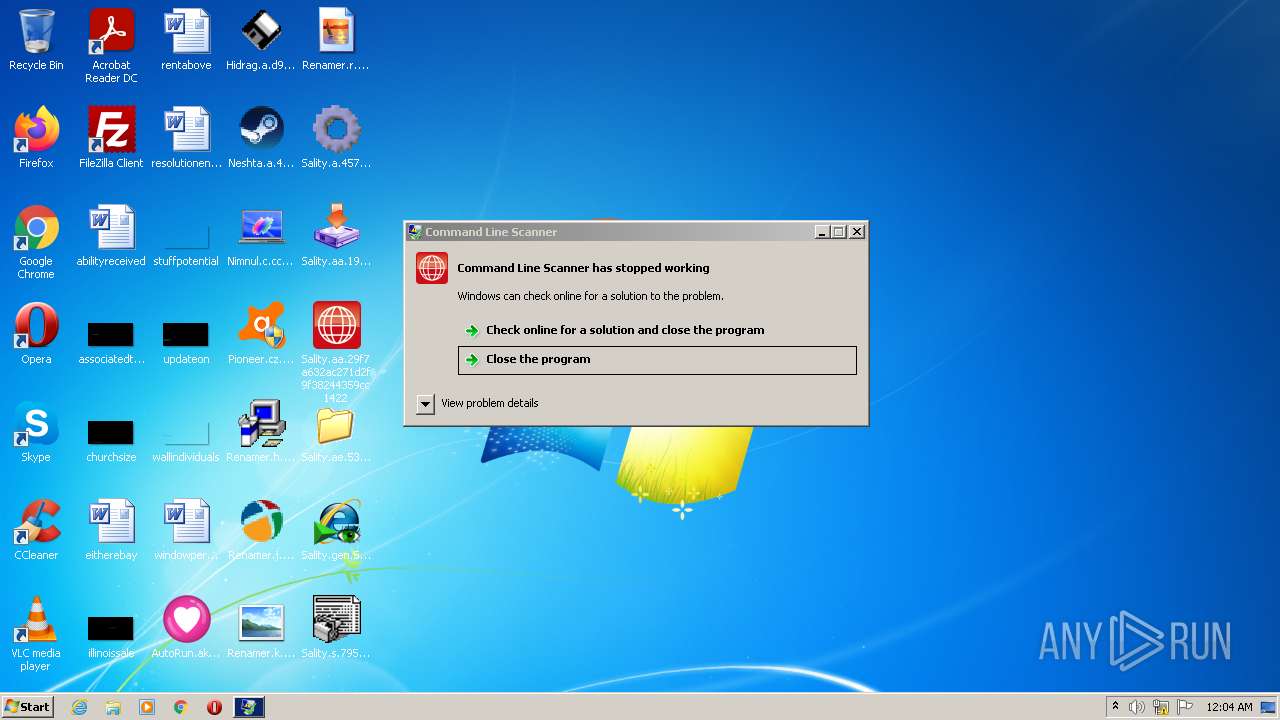
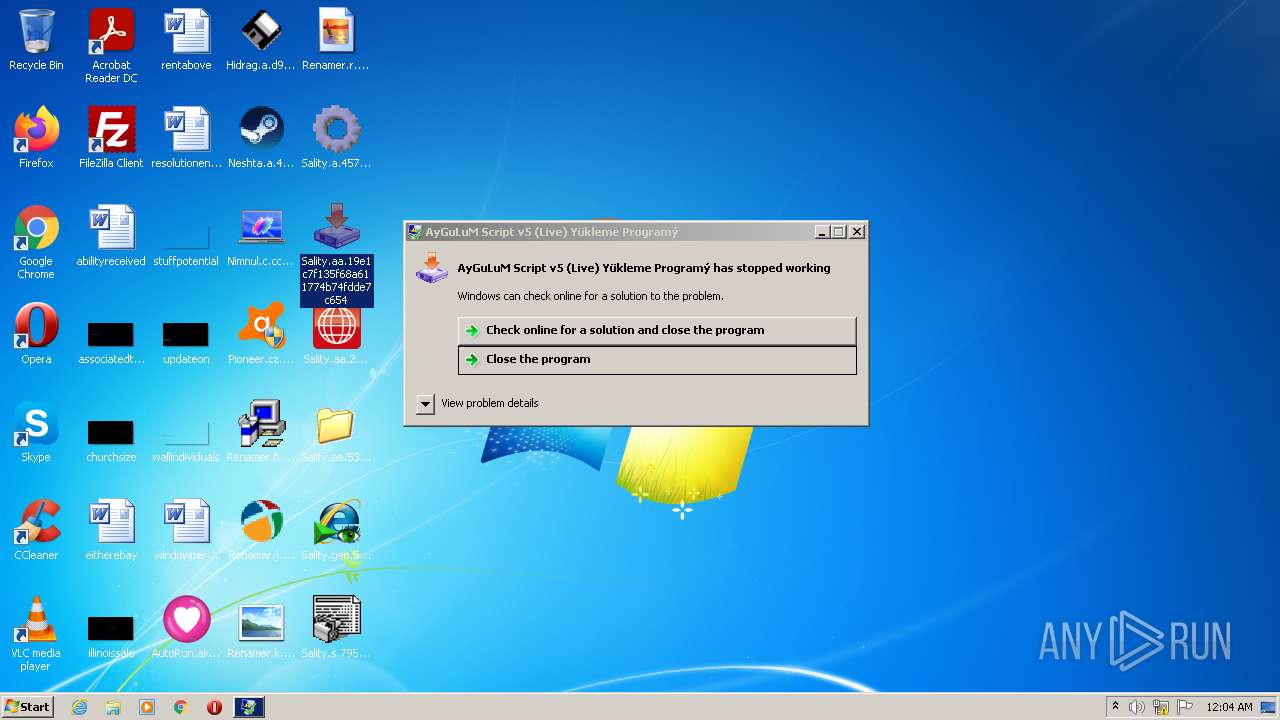
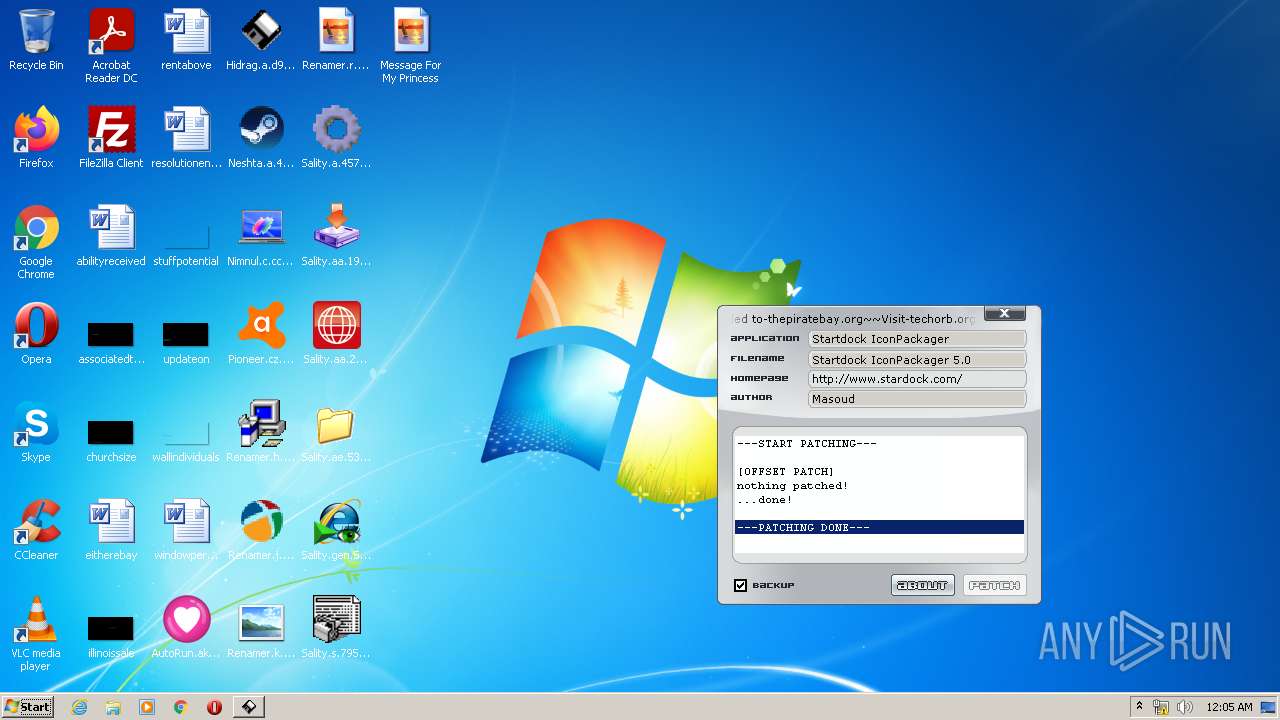
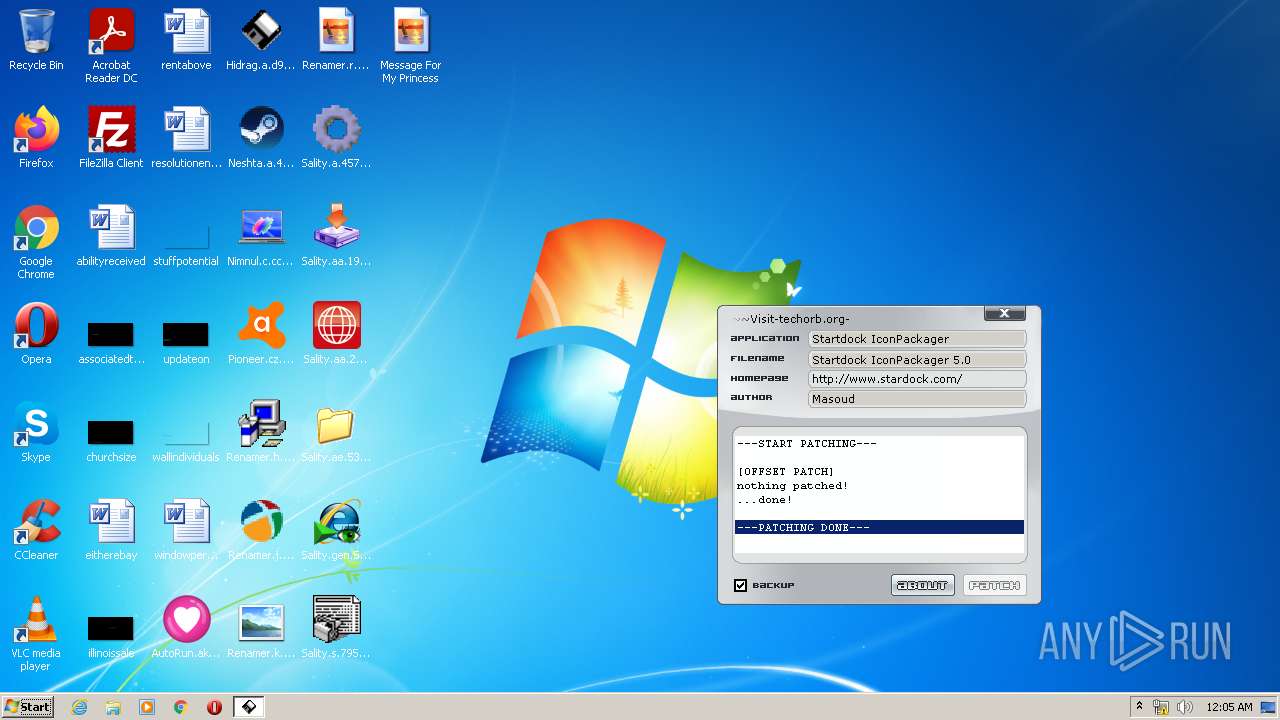
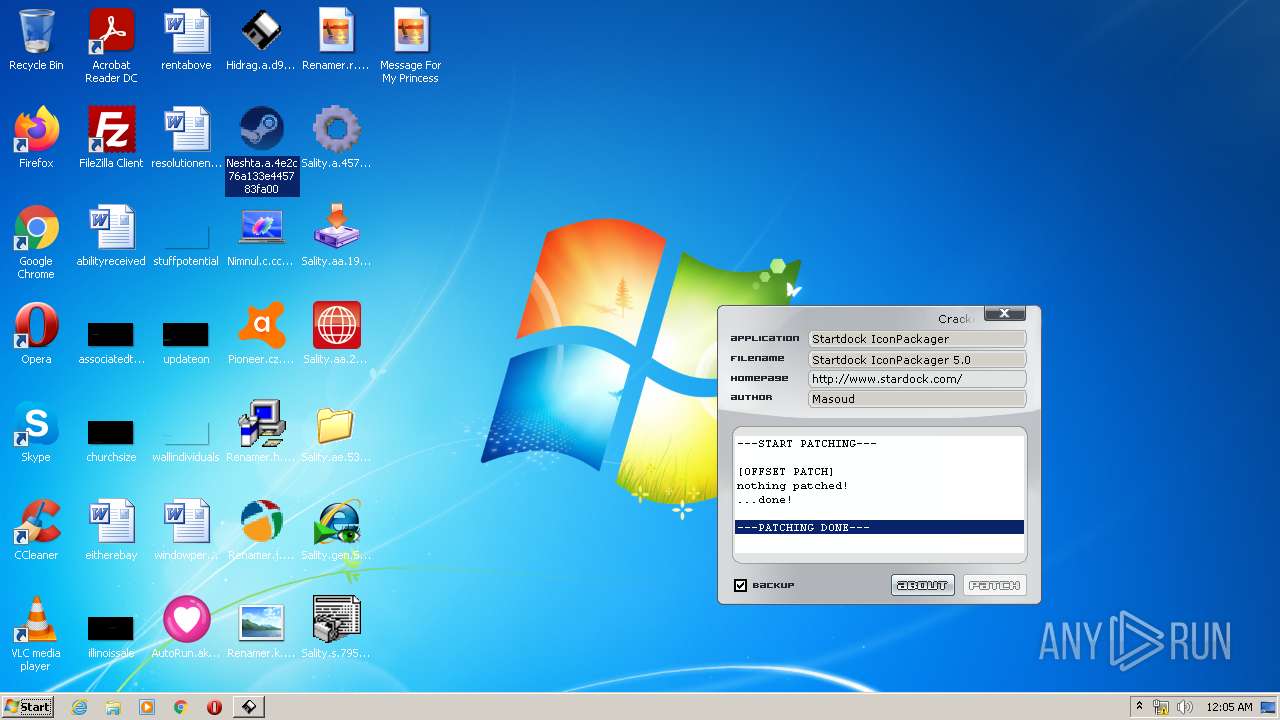
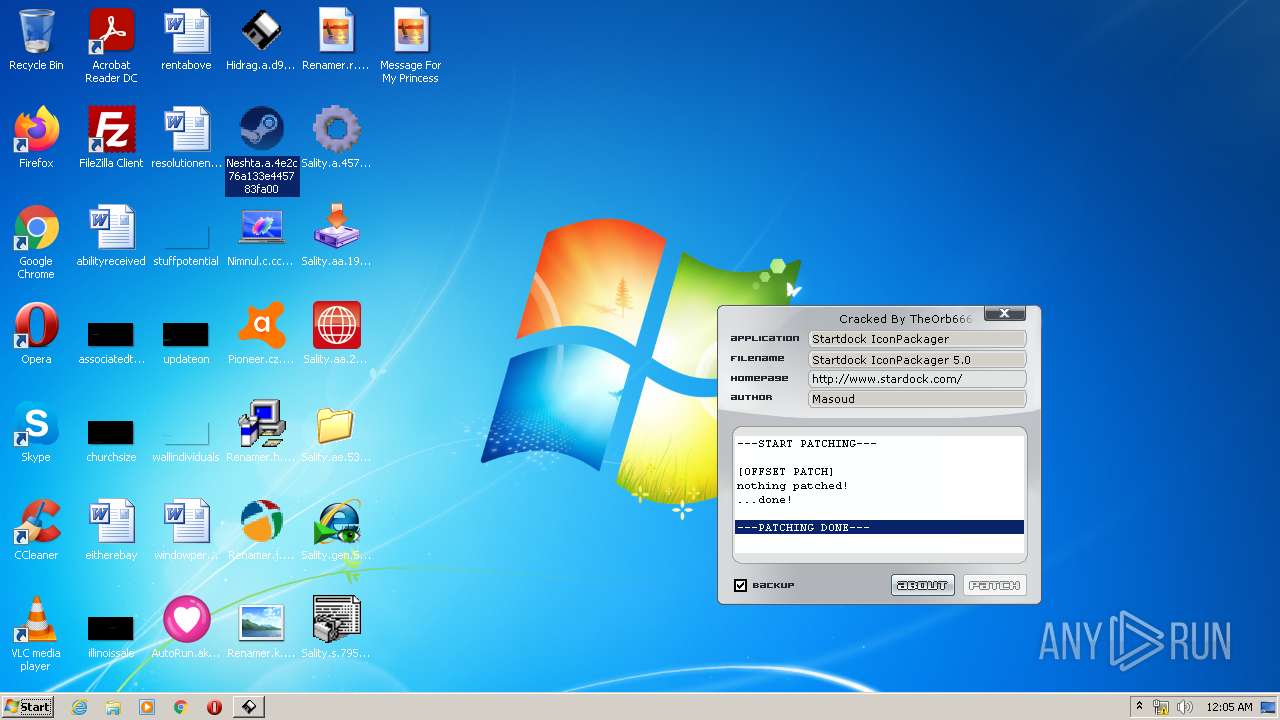
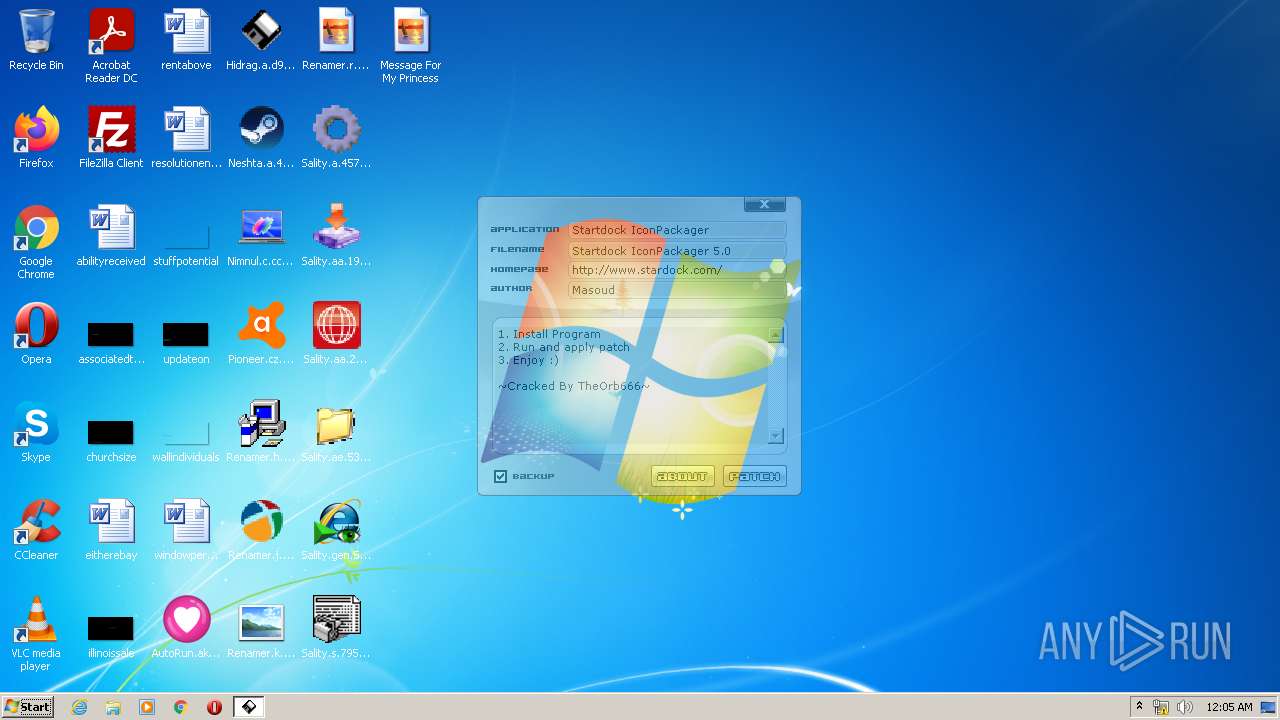
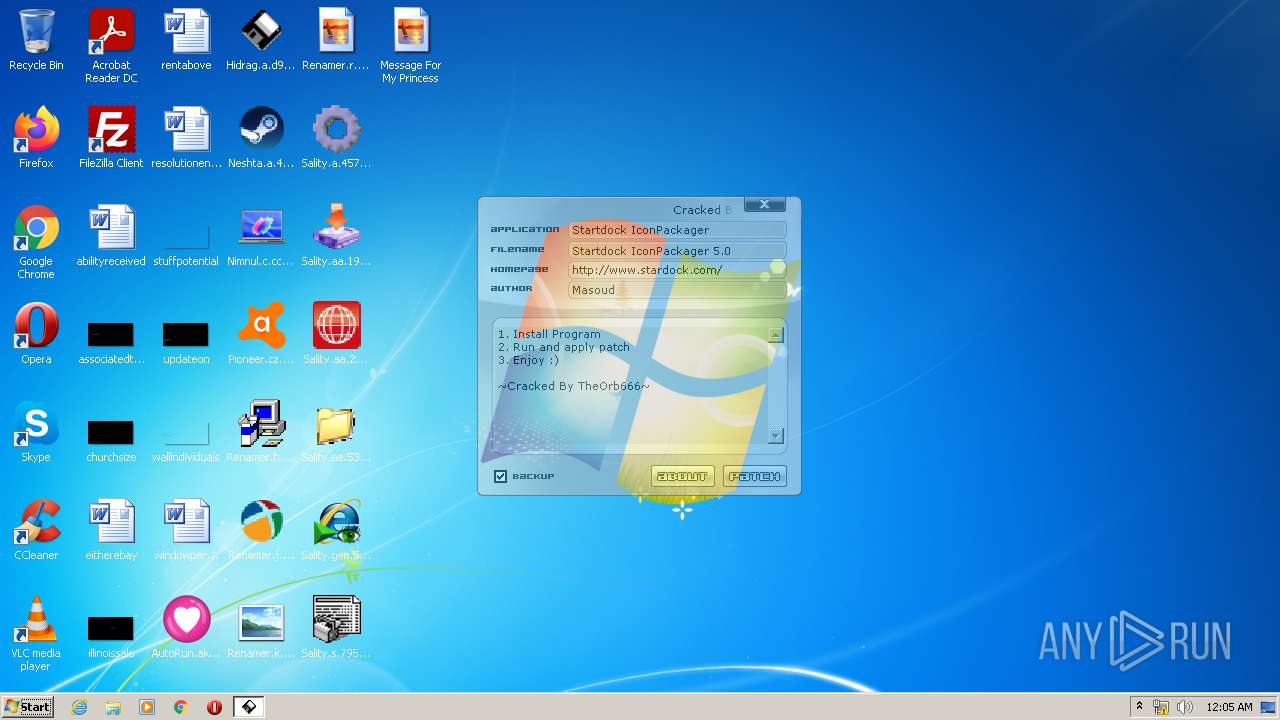
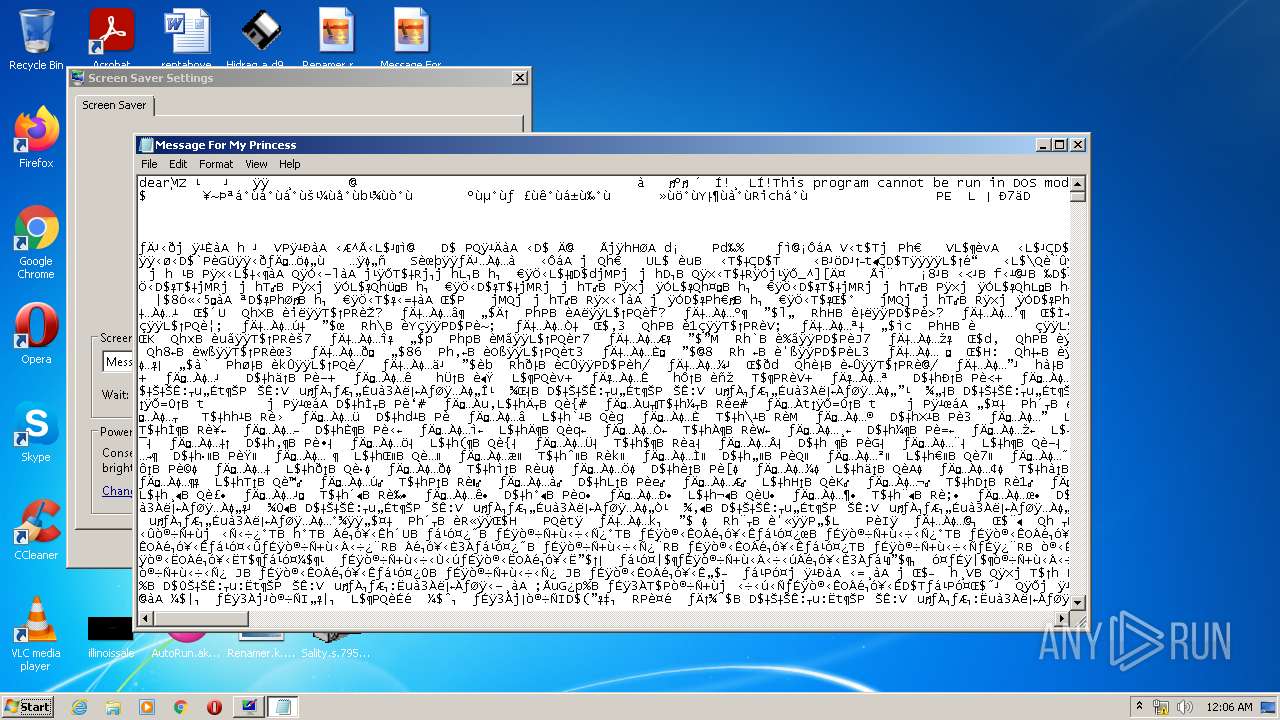
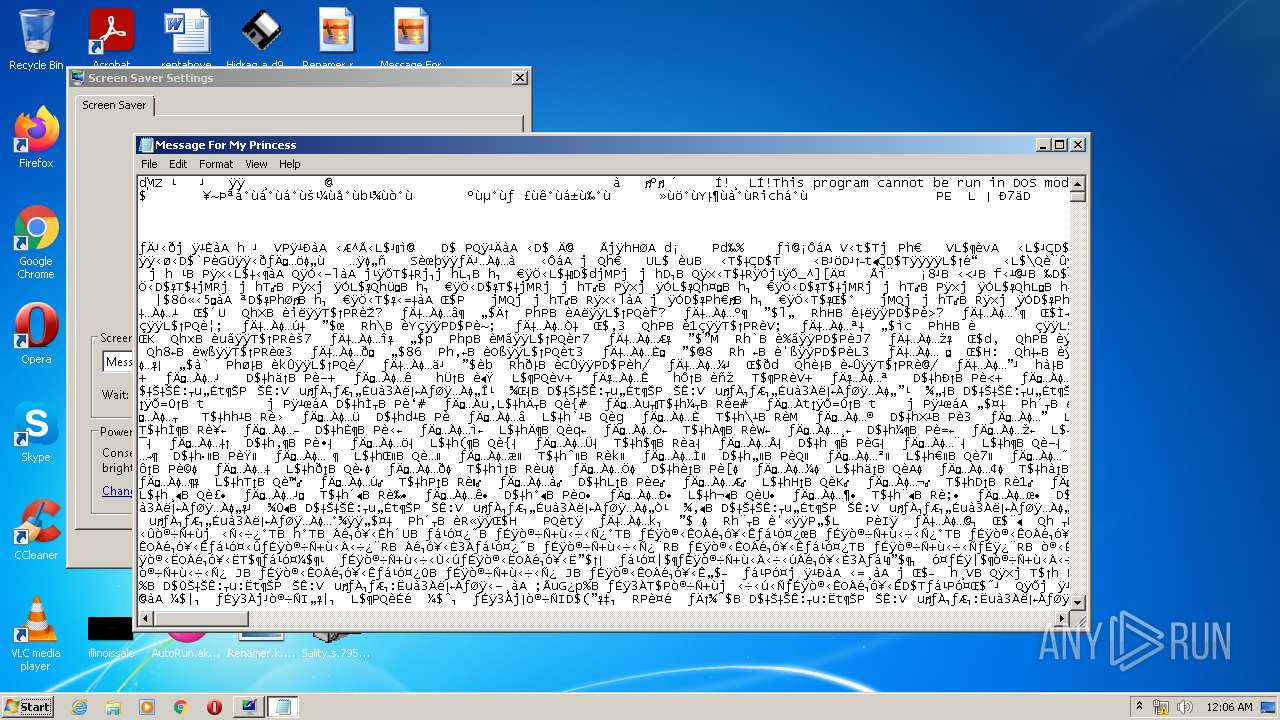
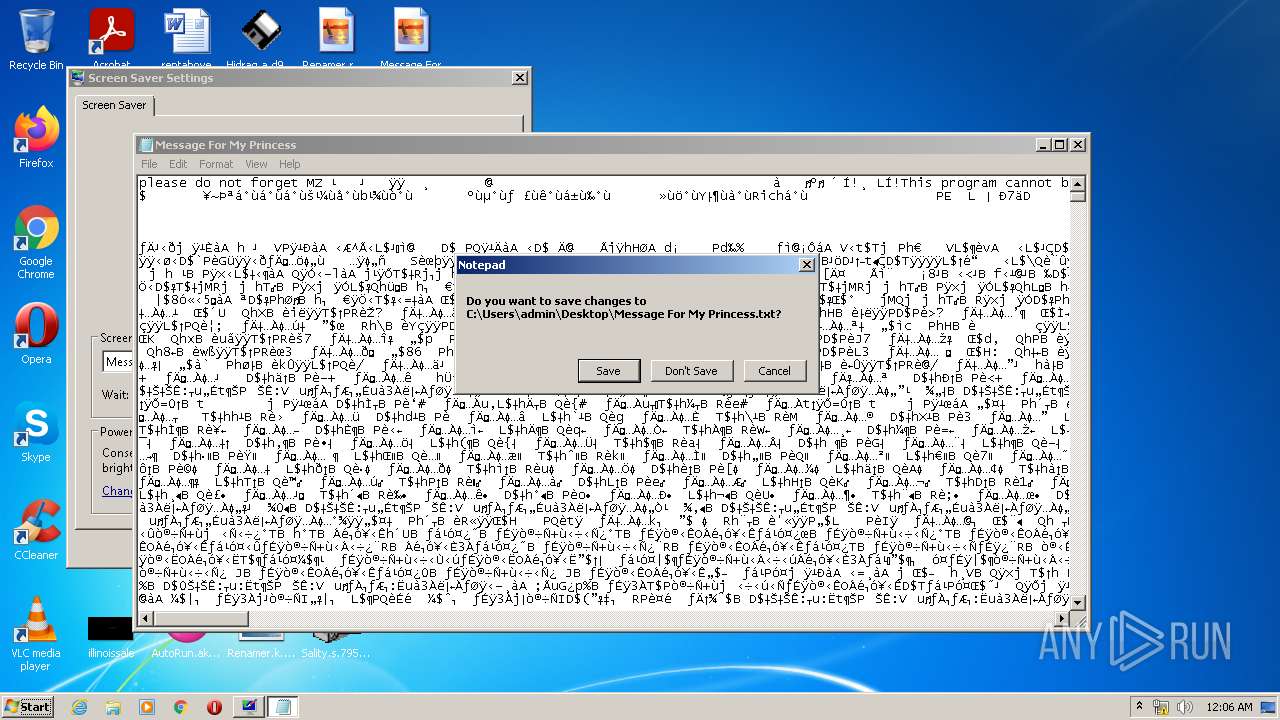
| File name: | Virus Infection.zip |
| Full analysis: | https://app.any.run/tasks/e1de9731-5a7f-49f8-81ec-44a8bacb1645 |
| Verdict: | Malicious activity |
| Threats: | Sality is a highly sophisticated malware known for infecting executable files and rapidly spreading across networks. It primarily creates a peer-to-peer botnet that is used for malicious activities such as spamming, data theft, and downloading additional malware. Sality has strong persistence mechanisms, including disabling security software, making it difficult to remove. Its ability to spread quickly and silently, along with its polymorphic nature, allows it to evade detection by traditional antivirus solutions. |
| Analysis date: | January 15, 2022, 00:03:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 563328B7A1439A567E7B87C8232F5F44 |
| SHA1: | 93D7E9C693364A359F535A4DCA250E61C7429D59 |
| SHA256: | 70AD044E9AE1BEAAA97CD9C5478278A765ECC42628C3B1BD13710619821FDF5A |
| SSDEEP: | 196608:8Njv+NYQf47AGyT4qreHeoX5icSVHnSHGrVYl7QS9kDkt4G/79Ss5RsQMCA:avOf47CTxe+oX5jSVHSu8QS9kD4J/0Y+ |
MALICIOUS
Drops executable file immediately after starts
- Explorer.EXE (PID: 740)
- AutoRun.akw.346c9322bc80ff97e126a7a7c3836d31.exe (PID: 784)
- Sality.ae.53a84290774665e9fcfc1576680c25c0.exe (PID: 988)
- Pioneer.cz.58fab99607afc5da878c0.exe (PID: 4060)
- Sality.a.4575f1b529a64524ea52b160bb8fc08f.exe (PID: 2596)
- Hidrag.a.d99ccff80df6a7f290fdeeed1b341ae5.exe (PID: 1752)
- Hidrag.a.d99ccff80df6a7f290fdeeed1b341ae5.exe (PID: 2340)
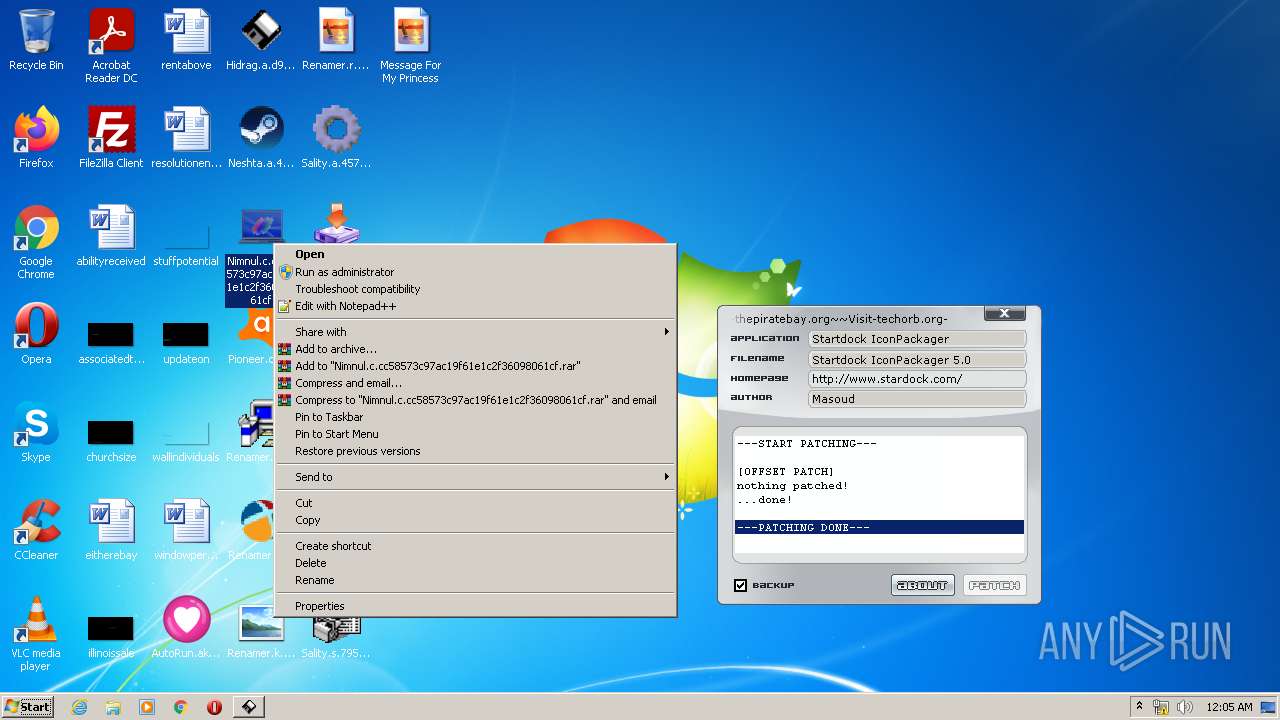
- Nimnul.c.cc58573c97ac19f61e1c2f36098061cf.exe (PID: 1400)
- Neshta.a.4e2c76a133e445783fa00.exe (PID: 856)
Application was dropped or rewritten from another process
- AutoRun.akw.346c9322bc80ff97e126a7a7c3836d31.exe (PID: 784)
- red_conapi.exe (PID: 1780)
- Renamer.k.73dff1c450ac7df11c7b3f7f3d261569.exe (PID: 2052)
- Sality.gen.55a00c72391b2e89c4500.exe (PID: 376)
- Sality.s.795c5088f67de4bfbf81fcbf8b0fea1f.exe (PID: 1144)
- Sality.ae.53a84290774665e9fcfc1576680c25c0.exe (PID: 988)
- Fun.exe (PID: 3972)
- dc.exe (PID: 3696)
- SVIQ.EXE (PID: 380)
- Pioneer.cz.58fab99607afc5da878c0.exe (PID: 4060)
- Pioneer.cz.58fab99607afc5da878c0.exe (PID: 472)
- Sality.aa.29f7a632ac271d2f9f38244359cc1422.exe (PID: 3992)
- Sality.aa.19e1c7f135f68a611774b74fdde7c654.exe (PID: 840)
- Renamer.r.b83f9d710264a26cbe2cd36a3de05088.exe (PID: 3496)
- Hidrag.a.d99ccff80df6a7f290fdeeed1b341ae5.exe (PID: 1752)
- svchost.exe (PID: 2480)
- svchost.exe (PID: 2888)
- WinSit.exe (PID: 1564)
- Sality.a.4575f1b529a64524ea52b160bb8fc08f.exe (PID: 2596)
- Nimnul.c.cc58573c97ac19f61e1c2f36098061cf.exe (PID: 1400)
- Neshta.a.4e2c76a133e445783fa00.exe (PID: 856)
- Neshta.a.4e2c76a133e445783fa00.exe (PID: 3748)
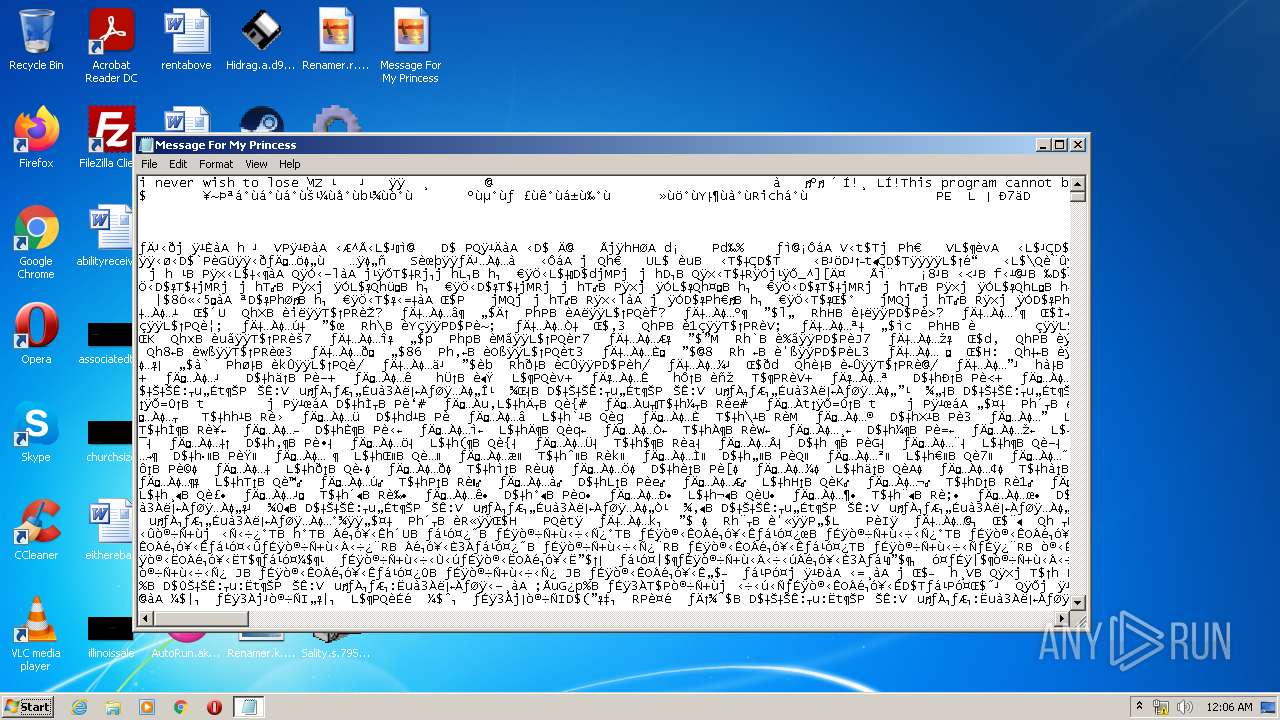
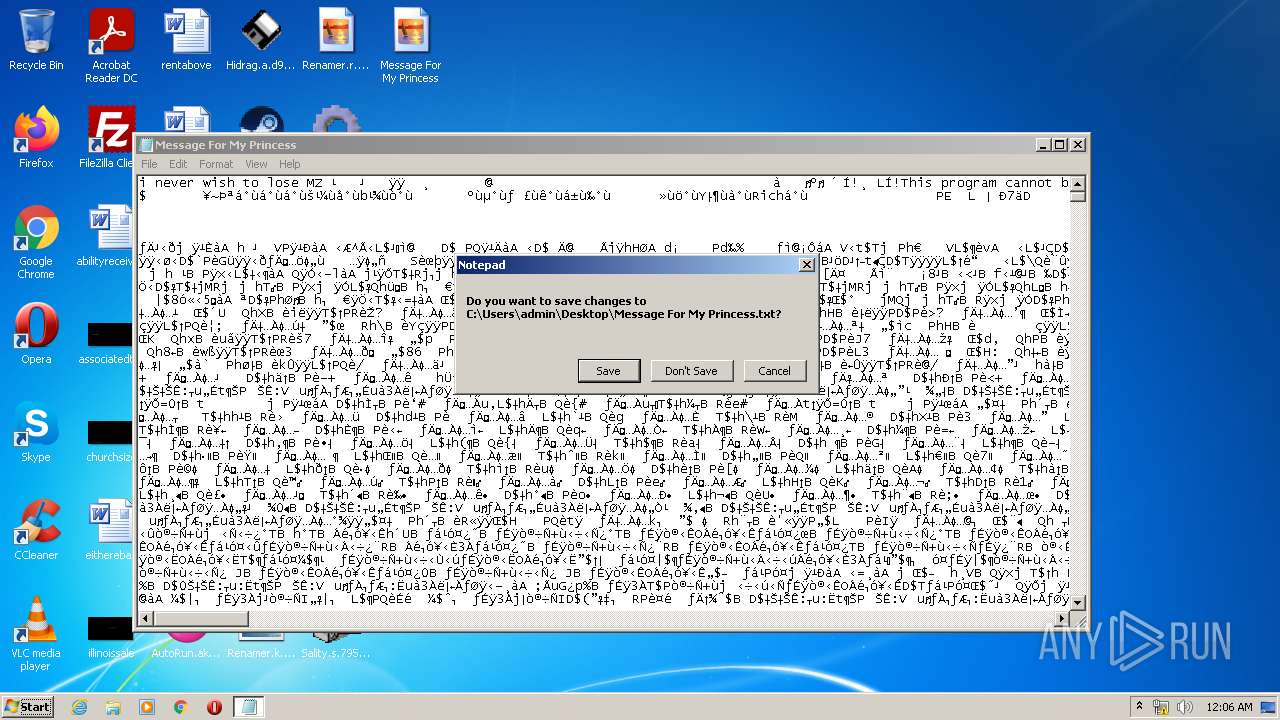
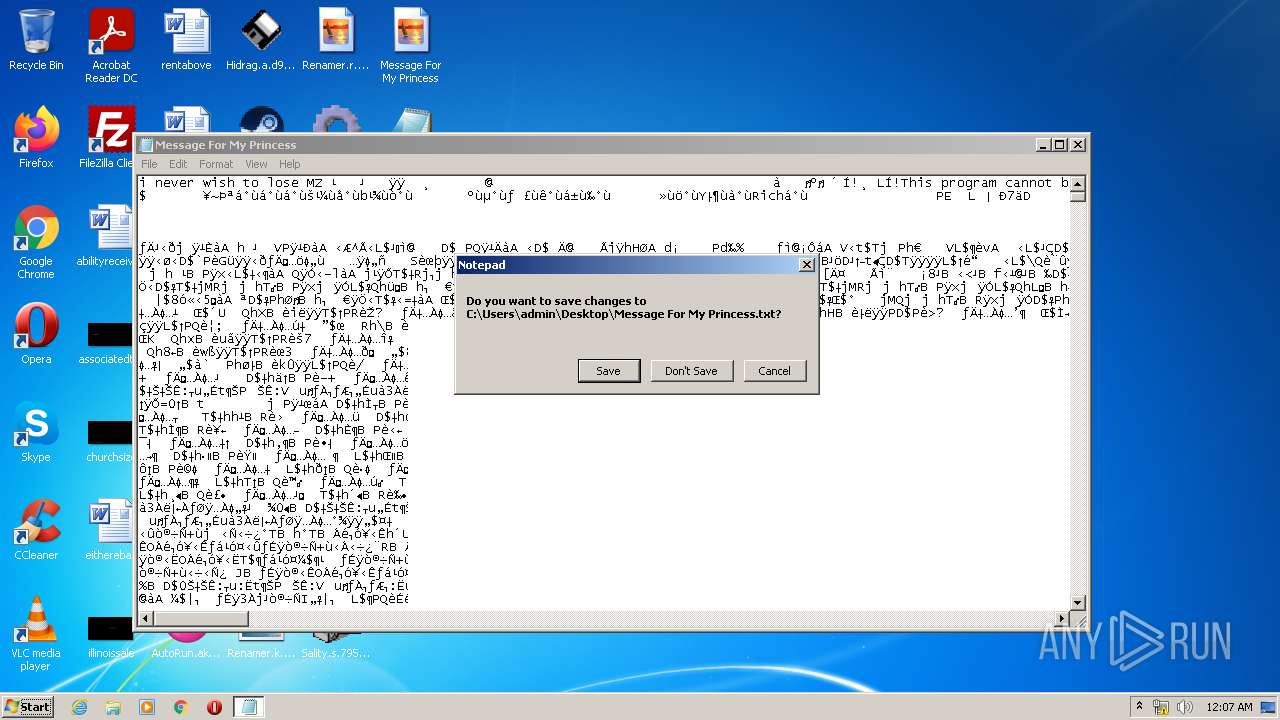
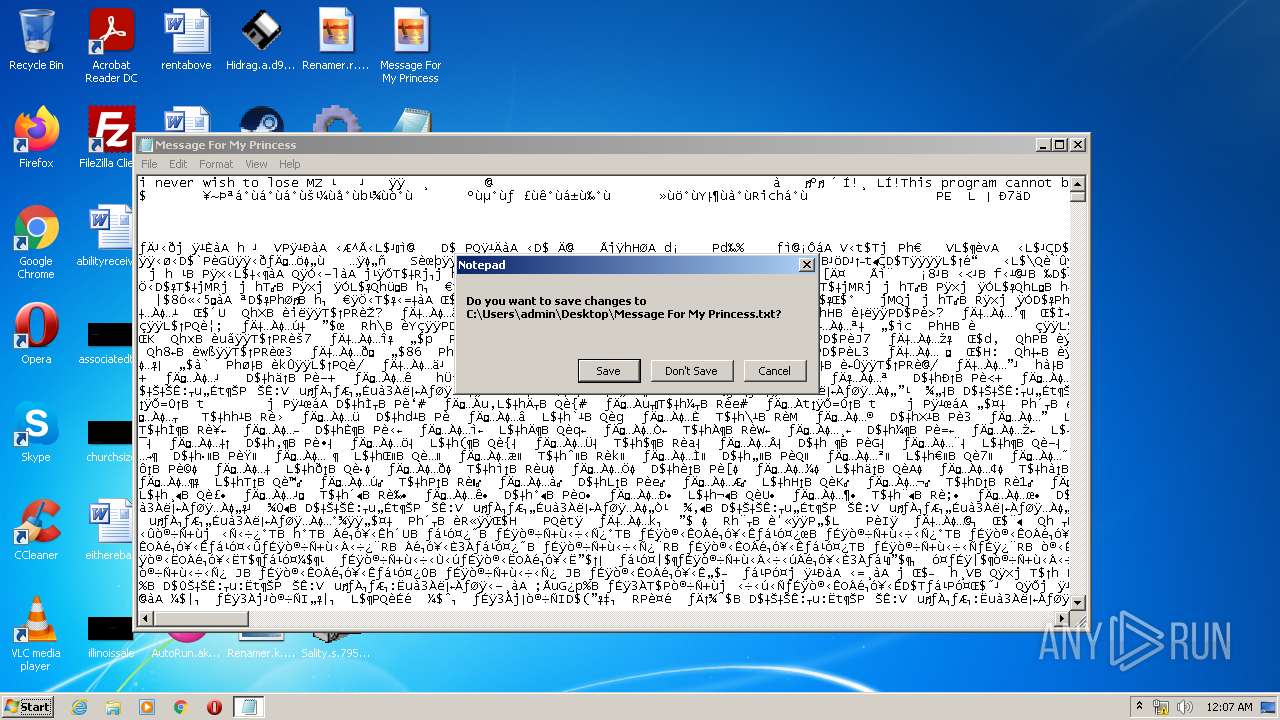
- Message For My Princess.scr (PID: 2528)
- Message For My Princess.scr (PID: 1284)
- svchost.com (PID: 1996)
- NOTEPAD.EXE (PID: 3328)
- NOTEPAD.EXE (PID: 2868)
- notepad.exe (PID: 516)
- notepad.exe (PID: 3592)
- svchost.com (PID: 3248)
- svchost.com (PID: 128)
Tries to delete the host file
- red_conapi.exe (PID: 1780)
Changes the autorun value in the registry
- red_conapi.exe (PID: 1780)
- Sality.ae.53a84290774665e9fcfc1576680c25c0.exe (PID: 988)
- Renamer.k.73dff1c450ac7df11c7b3f7f3d261569.exe (PID: 2052)
- Fun.exe (PID: 3972)
- dc.exe (PID: 3696)
- WinSit.exe (PID: 1564)
- Renamer.r.b83f9d710264a26cbe2cd36a3de05088.exe (PID: 3496)
- SVIQ.EXE (PID: 380)
- Message For My Princess.scr (PID: 2528)
- Message For My Princess.scr (PID: 1284)
Writes to the hosts file
- red_conapi.exe (PID: 1780)
UAC/LUA settings modification
- Sality.gen.55a00c72391b2e89c4500.exe (PID: 376)
Changes Security Center notification settings
- Sality.gen.55a00c72391b2e89c4500.exe (PID: 376)
Changes firewall settings
- Sality.gen.55a00c72391b2e89c4500.exe (PID: 376)
Application was injected by another process
- Explorer.EXE (PID: 740)
- ctfmon.exe (PID: 1404)
- taskeng.exe (PID: 632)
- Dwm.exe (PID: 928)
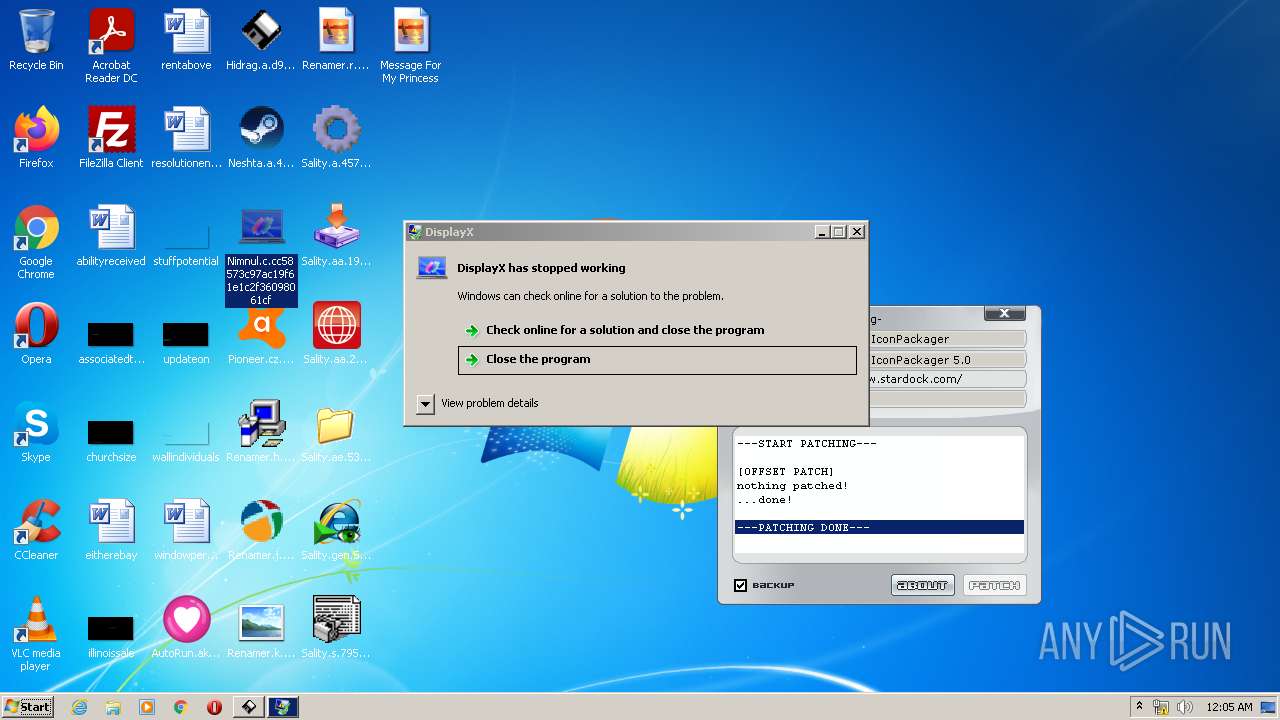
- WerFault.exe (PID: 3564)
- SearchProtocolHost.exe (PID: 3684)
Runs injected code in another process
- Sality.gen.55a00c72391b2e89c4500.exe (PID: 376)
Changes the login/logoff helper path in the registry
- Sality.ae.53a84290774665e9fcfc1576680c25c0.exe (PID: 988)
- Fun.exe (PID: 3972)
- SVIQ.EXE (PID: 380)
- dc.exe (PID: 3696)
- WinSit.exe (PID: 1564)
Loads dropped or rewritten executable
- Pioneer.cz.58fab99607afc5da878c0.exe (PID: 4060)
- Fun.exe (PID: 3972)
- dc.exe (PID: 3696)
- Renamer.r.b83f9d710264a26cbe2cd36a3de05088.exe (PID: 3496)
- Explorer.EXE (PID: 740)
- Sality.a.4575f1b529a64524ea52b160bb8fc08f.exe (PID: 2596)
- Sality.a.4575f1b529a64524ea52b160bb8fc08f.~01 (PID: 320)
- SVIQ.EXE (PID: 380)
- DllHost.exe (PID: 308)
- Explorer.exe (PID: 3852)
- explorer.exe (PID: 636)
- WinSit.exe (PID: 1564)
- DllHost.exe (PID: 3832)
- conhost.exe (PID: 3392)
- explorer.exe (PID: 2760)
- ctfmon.exe (PID: 1404)
- taskeng.exe (PID: 632)
- Dwm.exe (PID: 928)
- Renamer.k.73dff1c450ac7df11c7b3f7f3d261569.exe (PID: 2052)
- red_conapi.exe (PID: 1780)
- taskhost.exe (PID: 1280)
- Sality.gen.55a00c72391b2e89c4500.exe (PID: 376)
- WerFault.exe (PID: 2944)
- Neshta.a.4e2c76a133e445783fa00.exe (PID: 856)
- DllHost.exe (PID: 2076)
- Hidrag.a.d99ccff80df6a7f290fdeeed1b341ae5.exe (PID: 2312)
- rundll32.exe (PID: 3512)
- Hidrag.a.d99ccff80df6a7f290fdeeed1b341ae5.exe (PID: 2340)
- Message For My Princess.scr (PID: 2528)
- NOTEPAD.EXE (PID: 3328)
- Message For My Princess.scr (PID: 1284)
- NOTEPAD.EXE (PID: 2868)
- DllHost.exe (PID: 2488)
- explorer.exe (PID: 3836)
- DllHost.exe (PID: 1056)
- DllHost.exe (PID: 3948)
- DllHost.exe (PID: 2084)
- notepad.exe (PID: 516)
- notepad.exe (PID: 3592)
- conhost.exe (PID: 524)
Turns off system restore
- Renamer.r.b83f9d710264a26cbe2cd36a3de05088.exe (PID: 3496)
- Message For My Princess.scr (PID: 2528)
- Message For My Princess.scr (PID: 1284)
Changes appearance of the explorer extensions
- Renamer.r.b83f9d710264a26cbe2cd36a3de05088.exe (PID: 3496)
- Message For My Princess.scr (PID: 2528)
- Message For My Princess.scr (PID: 1284)
Runs app for hidden code execution
- Hidrag.a.d99ccff80df6a7f290fdeeed1b341ae5.exe (PID: 2340)
- svchost.com (PID: 128)
Loads the Task Scheduler COM API
- explorer.exe (PID: 2760)
SALITY was detected
- Sality.gen.55a00c72391b2e89c4500.exe (PID: 376)
Connects to CnC server
- Sality.gen.55a00c72391b2e89c4500.exe (PID: 376)
Changes settings of System certificates
- Sality.gen.55a00c72391b2e89c4500.exe (PID: 376)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 3472)
- AutoRun.akw.346c9322bc80ff97e126a7a7c3836d31.exe (PID: 784)
- red_conapi.exe (PID: 1780)
- Renamer.k.73dff1c450ac7df11c7b3f7f3d261569.exe (PID: 2052)
- Sality.gen.55a00c72391b2e89c4500.exe (PID: 376)
- Sality.s.795c5088f67de4bfbf81fcbf8b0fea1f.exe (PID: 1144)
- Sality.ae.53a84290774665e9fcfc1576680c25c0.exe (PID: 988)
- Fun.exe (PID: 3972)
- SVIQ.EXE (PID: 380)
- dc.exe (PID: 3696)
- Pioneer.cz.58fab99607afc5da878c0.exe (PID: 4060)
- Sality.aa.29f7a632ac271d2f9f38244359cc1422.exe (PID: 3992)
- Sality.aa.19e1c7f135f68a611774b74fdde7c654.exe (PID: 840)
- Sality.a.4575f1b529a64524ea52b160bb8fc08f.exe (PID: 2596)
- Renamer.r.b83f9d710264a26cbe2cd36a3de05088.exe (PID: 3496)
- Sality.a.4575f1b529a64524ea52b160bb8fc08f.~01 (PID: 320)
- Hidrag.a.d99ccff80df6a7f290fdeeed1b341ae5.exe (PID: 1752)
- svchost.exe (PID: 2480)
- Hidrag.a.d99ccff80df6a7f290fdeeed1b341ae5.exe (PID: 2340)
- svchost.exe (PID: 2888)
- WinSit.exe (PID: 1564)
- conhost.exe (PID: 3392)
- cmd.exe (PID: 1400)
- Nimnul.c.cc58573c97ac19f61e1c2f36098061cf.exe (PID: 1400)
- Neshta.a.4e2c76a133e445783fa00.exe (PID: 856)
- Neshta.a.4e2c76a133e445783fa00.exe (PID: 3748)
- Hidrag.a.d99ccff80df6a7f290fdeeed1b341ae5.exe (PID: 2312)
- Message For My Princess.scr (PID: 2528)
- Message For My Princess.scr (PID: 1284)
- svchost.com (PID: 1996)
- notepad.exe (PID: 516)
- notepad.exe (PID: 3592)
- svchost.com (PID: 3248)
- svchost.com (PID: 128)
- conhost.exe (PID: 524)
- cmd.exe (PID: 3256)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3472)
- Explorer.EXE (PID: 740)
- Sality.gen.55a00c72391b2e89c4500.exe (PID: 376)
- Nimnul.c.cc58573c97ac19f61e1c2f36098061cf.exe (PID: 1400)
- Neshta.a.4e2c76a133e445783fa00.exe (PID: 856)
- explorer.exe (PID: 2760)
- Sality.a.4575f1b529a64524ea52b160bb8fc08f.exe (PID: 2596)
Reads the computer name
- WinRAR.exe (PID: 3472)
- red_conapi.exe (PID: 1780)
- AutoRun.akw.346c9322bc80ff97e126a7a7c3836d31.exe (PID: 784)
- Sality.gen.55a00c72391b2e89c4500.exe (PID: 376)
- Fun.exe (PID: 3972)
- Pioneer.cz.58fab99607afc5da878c0.exe (PID: 4060)
- Renamer.r.b83f9d710264a26cbe2cd36a3de05088.exe (PID: 3496)
- svchost.exe (PID: 2480)
- Hidrag.a.d99ccff80df6a7f290fdeeed1b341ae5.exe (PID: 2340)
- svchost.exe (PID: 2888)
- Neshta.a.4e2c76a133e445783fa00.exe (PID: 856)
- Hidrag.a.d99ccff80df6a7f290fdeeed1b341ae5.exe (PID: 2312)
- Message For My Princess.scr (PID: 1284)
- Message For My Princess.scr (PID: 2528)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3472)
- AutoRun.akw.346c9322bc80ff97e126a7a7c3836d31.exe (PID: 784)
- Renamer.k.73dff1c450ac7df11c7b3f7f3d261569.exe (PID: 2052)
- Sality.ae.53a84290774665e9fcfc1576680c25c0.exe (PID: 988)
- Pioneer.cz.58fab99607afc5da878c0.exe (PID: 4060)
- Sality.gen.55a00c72391b2e89c4500.exe (PID: 376)
- Sality.a.4575f1b529a64524ea52b160bb8fc08f.exe (PID: 2596)
- Renamer.r.b83f9d710264a26cbe2cd36a3de05088.exe (PID: 3496)
- Hidrag.a.d99ccff80df6a7f290fdeeed1b341ae5.exe (PID: 1752)
- Hidrag.a.d99ccff80df6a7f290fdeeed1b341ae5.exe (PID: 2340)
- svchost.exe (PID: 2888)
- Nimnul.c.cc58573c97ac19f61e1c2f36098061cf.exe (PID: 1400)
- Neshta.a.4e2c76a133e445783fa00.exe (PID: 856)
- explorer.exe (PID: 2760)
Drops a file with too old compile date
- WinRAR.exe (PID: 3472)
- Explorer.EXE (PID: 740)
- AutoRun.akw.346c9322bc80ff97e126a7a7c3836d31.exe (PID: 784)
- Sality.ae.53a84290774665e9fcfc1576680c25c0.exe (PID: 988)
- Sality.gen.55a00c72391b2e89c4500.exe (PID: 376)
- Sality.a.4575f1b529a64524ea52b160bb8fc08f.exe (PID: 2596)
- Renamer.r.b83f9d710264a26cbe2cd36a3de05088.exe (PID: 3496)
- Hidrag.a.d99ccff80df6a7f290fdeeed1b341ae5.exe (PID: 2340)
- Hidrag.a.d99ccff80df6a7f290fdeeed1b341ae5.exe (PID: 1752)
- svchost.exe (PID: 2888)
- Nimnul.c.cc58573c97ac19f61e1c2f36098061cf.exe (PID: 1400)
- Neshta.a.4e2c76a133e445783fa00.exe (PID: 856)
Removes files from Windows directory
- AutoRun.akw.346c9322bc80ff97e126a7a7c3836d31.exe (PID: 784)
- red_conapi.exe (PID: 1780)
- svchost.com (PID: 1996)
- svchost.com (PID: 3248)
- svchost.com (PID: 128)
Creates files in the Windows directory
- AutoRun.akw.346c9322bc80ff97e126a7a7c3836d31.exe (PID: 784)
- red_conapi.exe (PID: 1780)
- Renamer.k.73dff1c450ac7df11c7b3f7f3d261569.exe (PID: 2052)
- Sality.ae.53a84290774665e9fcfc1576680c25c0.exe (PID: 988)
- Sality.a.4575f1b529a64524ea52b160bb8fc08f.exe (PID: 2596)
- Hidrag.a.d99ccff80df6a7f290fdeeed1b341ae5.exe (PID: 1752)
- Renamer.r.b83f9d710264a26cbe2cd36a3de05088.exe (PID: 3496)
- Neshta.a.4e2c76a133e445783fa00.exe (PID: 856)
- svchost.com (PID: 1996)
Reads Microsoft Outlook installation path
- red_conapi.exe (PID: 1780)
Reads internet explorer settings
- red_conapi.exe (PID: 1780)
Creates files in the driver directory
- red_conapi.exe (PID: 1780)
Starts itself from another location
- Sality.ae.53a84290774665e9fcfc1576680c25c0.exe (PID: 988)
- Fun.exe (PID: 3972)
Creates files in the program directory
- Pioneer.cz.58fab99607afc5da878c0.exe (PID: 4060)
- WerFault.exe (PID: 3564)
- WerFault.exe (PID: 2944)
Starts application with an unusual extension
- Sality.a.4575f1b529a64524ea52b160bb8fc08f.exe (PID: 2596)
- explorer.exe (PID: 2760)
- rundll32.exe (PID: 3512)
Creates files in the user directory
- Renamer.r.b83f9d710264a26cbe2cd36a3de05088.exe (PID: 3496)
- Sality.gen.55a00c72391b2e89c4500.exe (PID: 376)
Creates executable files which already exist in Windows
- Hidrag.a.d99ccff80df6a7f290fdeeed1b341ae5.exe (PID: 1752)
- Renamer.r.b83f9d710264a26cbe2cd36a3de05088.exe (PID: 3496)
Executed as Windows Service
- svchost.exe (PID: 2888)
Writes to a desktop.ini file (may be used to cloak folders)
- Renamer.r.b83f9d710264a26cbe2cd36a3de05088.exe (PID: 3496)
Executed via COM
- explorer.exe (PID: 636)
Starts CMD.EXE for commands execution
- Hidrag.a.d99ccff80df6a7f290fdeeed1b341ae5.exe (PID: 2340)
- svchost.com (PID: 128)
Reads the date of Windows installation
- explorer.exe (PID: 2760)
- Message For My Princess.scr (PID: 2528)
- Message For My Princess.scr (PID: 1284)
Reads default file associations for system extensions
- explorer.exe (PID: 2760)
Changes default file association
- Neshta.a.4e2c76a133e445783fa00.exe (PID: 856)
Uses RUNDLL32.EXE to load library
- explorer.exe (PID: 2760)
Adds / modifies Windows certificates
- Sality.gen.55a00c72391b2e89c4500.exe (PID: 376)
INFO
Manual execution by user
- AutoRun.akw.346c9322bc80ff97e126a7a7c3836d31.exe (PID: 784)
- Renamer.k.73dff1c450ac7df11c7b3f7f3d261569.exe (PID: 2052)
- Sality.gen.55a00c72391b2e89c4500.exe (PID: 376)
- Sality.s.795c5088f67de4bfbf81fcbf8b0fea1f.exe (PID: 1144)
- Sality.ae.53a84290774665e9fcfc1576680c25c0.exe (PID: 988)
- Pioneer.cz.58fab99607afc5da878c0.exe (PID: 472)
- Pioneer.cz.58fab99607afc5da878c0.exe (PID: 4060)
- Sality.aa.29f7a632ac271d2f9f38244359cc1422.exe (PID: 3992)
- Sality.aa.19e1c7f135f68a611774b74fdde7c654.exe (PID: 840)
- Sality.a.4575f1b529a64524ea52b160bb8fc08f.exe (PID: 2596)
- Renamer.r.b83f9d710264a26cbe2cd36a3de05088.exe (PID: 3496)
- Hidrag.a.d99ccff80df6a7f290fdeeed1b341ae5.exe (PID: 1752)
- SearchProtocolHost.exe (PID: 3324)
- SearchFilterHost.exe (PID: 2724)
Checks supported languages
- taskhost.exe (PID: 1280)
- WerFault.exe (PID: 3564)
- DllHost.exe (PID: 308)
- Explorer.exe (PID: 3852)
- explorer.exe (PID: 636)
- DllHost.exe (PID: 3832)
- explorer.exe (PID: 2760)
- SearchProtocolHost.exe (PID: 3684)
- WerFault.exe (PID: 2944)
- DllHost.exe (PID: 2076)
- rundll32.exe (PID: 3512)
- SearchFilterHost.exe (PID: 3472)
- NOTEPAD.EXE (PID: 3328)
- NOTEPAD.EXE (PID: 2868)
- explorer.exe (PID: 3836)
- DllHost.exe (PID: 2488)
- DllHost.exe (PID: 2084)
- DllHost.exe (PID: 1056)
- SearchProtocolHost.exe (PID: 3324)
- DllHost.exe (PID: 3948)
- SearchFilterHost.exe (PID: 2724)
Reads the computer name
- WerFault.exe (PID: 3564)
- DllHost.exe (PID: 308)
- explorer.exe (PID: 636)
- Explorer.exe (PID: 3852)
- DllHost.exe (PID: 3832)
- SearchProtocolHost.exe (PID: 3684)
- WerFault.exe (PID: 2944)
- DllHost.exe (PID: 2076)
- rundll32.exe (PID: 3512)
- SearchFilterHost.exe (PID: 3472)
- explorer.exe (PID: 3836)
- DllHost.exe (PID: 2488)
- DllHost.exe (PID: 1056)
- DllHost.exe (PID: 3948)
- SearchFilterHost.exe (PID: 2724)
- explorer.exe (PID: 2760)
- SearchProtocolHost.exe (PID: 3324)
- DllHost.exe (PID: 2084)
Dropped object may contain Bitcoin addresses
- WerFault.exe (PID: 3564)
Reads Microsoft Office registry keys
- Hidrag.a.d99ccff80df6a7f290fdeeed1b341ae5.exe (PID: 2340)
- explorer.exe (PID: 2760)
Reads settings of System Certificates
- Sality.gen.55a00c72391b2e89c4500.exe (PID: 376)
Checks Windows Trust Settings
- Sality.gen.55a00c72391b2e89c4500.exe (PID: 376)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | AutoRun.akw.346c9322bc80ff97e126a7a7c3836d31.exe |
|---|---|
| ZipUncompressedSize: | 129346 |
| ZipCompressedSize: | 129346 |
| ZipCRC: | 0xec5a7f51 |
| ZipModifyDate: | 2019:12:30 01:13:19 |
| ZipCompression: | None |
| ZipBitFlag: | 0x0001 |
| ZipRequiredVersion: | 20 |
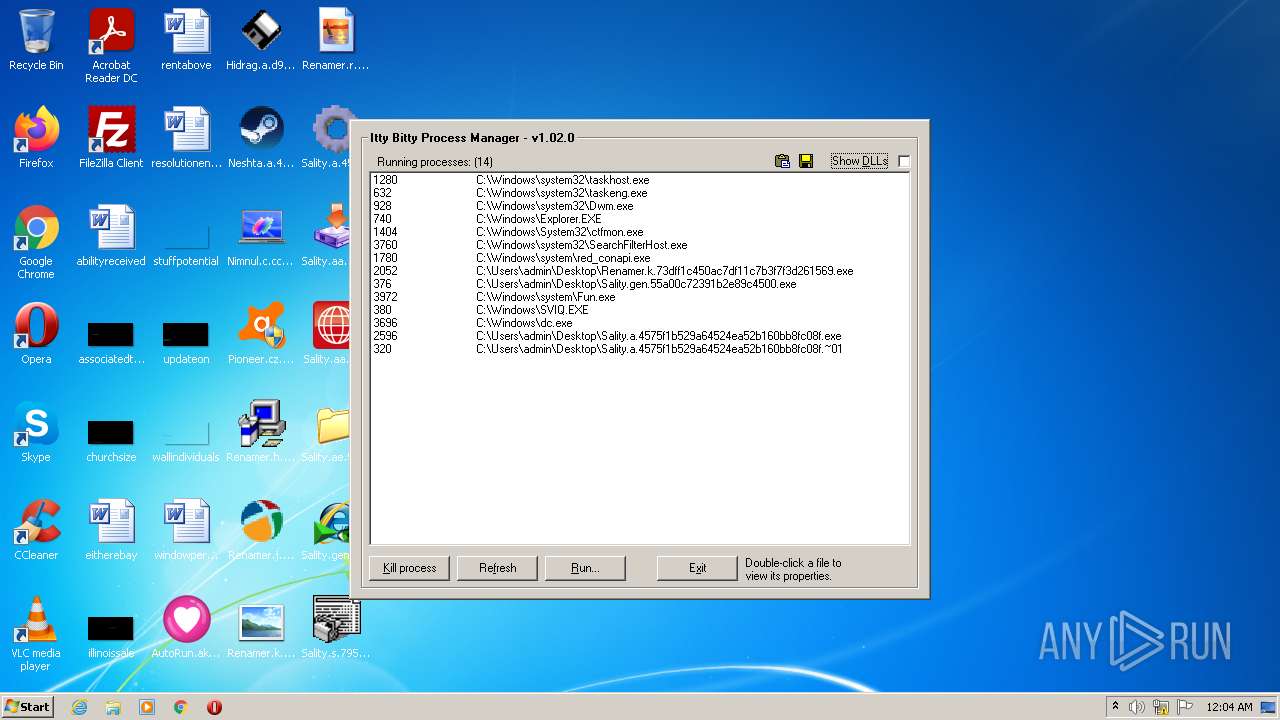
Total processes
117
Monitored processes
62
Malicious processes
27
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Windows\svchost.com" "C:\Windows\system32\cmd.exe" | C:\Windows\svchost.com | — | explorer.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 308 | C:\Windows\system32\DllHost.exe /Processid:{AB8902B4-09CA-4BB6-B78D-A8F59079A8D5} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 320 | C:\Users\admin\Desktop\Sality.a.4575f1b529a64524ea52b160bb8fc08f.~01 | C:\Users\admin\Desktop\Sality.a.4575f1b529a64524ea52b160bb8fc08f.~01 | — | Sality.a.4575f1b529a64524ea52b160bb8fc08f.exe | |||||||||||
User: admin Company: Soeperman Enterprises Ltd. Integrity Level: HIGH Description: Itty Bitty Process Manager Exit code: 0 Version: 1.02 Modules
| |||||||||||||||
| 376 | "C:\Users\admin\Desktop\Sality.gen.55a00c72391b2e89c4500.exe" | C:\Users\admin\Desktop\Sality.gen.55a00c72391b2e89c4500.exe | Explorer.EXE | ||||||||||||
User: admin Company: Tonec Inc. Integrity Level: HIGH Description: Internet Download Manager agent for click monitoring in IE-based browsers Exit code: 0 Version: 6, 22, 1, 1 Modules
| |||||||||||||||
| 380 | C:\Windows\SVIQ.EXE | C:\Windows\SVIQ.EXE | Fun.exe | ||||||||||||
User: admin Company: Test Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 472 | "C:\Users\admin\Desktop\Pioneer.cz.58fab99607afc5da878c0.exe" | C:\Users\admin\Desktop\Pioneer.cz.58fab99607afc5da878c0.exe | — | Explorer.EXE | |||||||||||
User: admin Company: AVAST Software Integrity Level: MEDIUM Description: Avast Antivirus Installer Exit code: 3221226540 Version: 18.3.260.0 Modules
| |||||||||||||||
| 516 | C:\Users\admin\Desktop\notepad.exe | C:\Users\admin\Desktop\notepad.exe | — | svchost.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 6.1.7601.18917 (win7sp1_gdr.150709-0600) Modules
| |||||||||||||||
| 524 | \??\C:\Windows\system32\conhost.exe "-660699828-20218964047218129051797443944-9962150-17267900771531557757-841024380" | \??\C:\Windows\system32\conhost.exe | — | csrss.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 632 | taskeng.exe {54738773-C509-4DB9-AC49-6F558536DDDE} | C:\Windows\system32\taskeng.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Engine Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 636 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
41 033
Read events
35 662
Write events
5 366
Delete events
5
Modification events
| (PID) Process: | (3472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3472) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Virus Infection.zip | |||
| (PID) Process: | (3472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
93
Suspicious files
10
Text files
46
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3472 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3472.16976\AutoRun.akw.346c9322bc80ff97e126a7a7c3836d31.exe | executable | |
MD5:— | SHA256:— | |||
| 3472 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3472.16976\Pioneer.cz.58fab99607afc5da878c0.exe | executable | |
MD5:— | SHA256:— | |||
| 3472 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3472.16976\Renamer.k.73dff1c450ac7df11c7b3f7f3d261569.exe | executable | |
MD5:— | SHA256:— | |||
| 3472 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3472.16976\Neshta.a.4e2c76a133e445783fa00.exe | executable | |
MD5:— | SHA256:— | |||
| 3472 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3472.16976\Renamer.h.f6b1d9829e787805d5f4c096350e8cfc.exe | executable | |
MD5:— | SHA256:— | |||
| 3472 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3472.16976\Sality.aa.19e1c7f135f68a611774b74fdde7c654.exe | executable | |
MD5:— | SHA256:— | |||
| 3472 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3472.16976\Sality.a.4575f1b529a64524ea52b160bb8fc08f.exe | executable | |
MD5:— | SHA256:— | |||
| 3472 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3472.16976\Renamer.r.b83f9d710264a26cbe2cd36a3de05088.exe | executable | |
MD5:— | SHA256:— | |||
| 3472 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3472.16976\Renamer.j.13047ece5b2000329b0ef36f5d45b70a.exe | executable | |
MD5:— | SHA256:— | |||
| 740 | Explorer.EXE | C:\Users\admin\Desktop\Neshta.a.4e2c76a133e445783fa00.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
228
DNS requests
30
Threats
31
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
376 | Sality.gen.55a00c72391b2e89c4500.exe | GET | 200 | 173.231.189.15:80 | http://ksandrafashion.com/logo.gif?150e90=5519936 | US | — | — | malicious |
376 | Sality.gen.55a00c72391b2e89c4500.exe | GET | — | 94.101.91.137:80 | http://www.ledyazilim.com/logo.gif?149912=5399624 | TR | — | — | malicious |
376 | Sality.gen.55a00c72391b2e89c4500.exe | GET | 301 | 68.66.226.85:80 | http://toalladepapel.com.ar/images/logo.gif?15117e=11045872 | US | — | — | malicious |
376 | Sality.gen.55a00c72391b2e89c4500.exe | GET | 200 | 63.251.106.25:80 | http://www.ecole-saint-simon.net/index_top/logo.gif?151edc=9689092 | US | — | — | malicious |
376 | Sality.gen.55a00c72391b2e89c4500.exe | GET | 200 | 206.189.61.126:80 | http://kulppasur.com/logo.gif?1510d2=4141686 | US | — | — | malicious |
376 | Sality.gen.55a00c72391b2e89c4500.exe | GET | 200 | 63.251.106.25:80 | http://koonadance2.com/images/logo.gif?15219b=13848590 | US | — | — | malicious |
1780 | red_conapi.exe | GET | 200 | 97.74.42.79:80 | http://artistlegion.com/modules/readme_NT.txt | US | html | 1.54 Kb | malicious |
1780 | red_conapi.exe | GET | 200 | 97.74.42.79:80 | http://artistlegion.com/modules/readme_NT.txt | US | html | 1.54 Kb | malicious |
376 | Sality.gen.55a00c72391b2e89c4500.exe | GET | 200 | 104.18.30.182:80 | http://ocsp.comodoca.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBReAhtobFzTvhaRmVeJ38QUchY9AwQUu69%2BAj36pvE8hI6t7jiY7NkyMtQCEQDwHUvue3yjezwFZqwFlyRY | US | der | 728 b | whitelisted |
376 | Sality.gen.55a00c72391b2e89c4500.exe | GET | 200 | 104.18.30.182:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEGfe9D7xe9riT%2FWUBgbSwIQ%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1780 | red_conapi.exe | 142.250.186.132:80 | www.google.com | Google Inc. | US | whitelisted |
1780 | red_conapi.exe | 97.74.42.79:80 | artistlegion.com | GoDaddy.com, LLC | US | malicious |
— | — | 142.250.186.132:80 | www.google.com | Google Inc. | US | whitelisted |
376 | Sality.gen.55a00c72391b2e89c4500.exe | 94.101.91.137:80 | www.ledyazilim.com | Radore Veri Merkezi Hizmetleri A.S. | TR | malicious |
376 | Sality.gen.55a00c72391b2e89c4500.exe | 173.231.189.15:80 | ksandrafashion.com | Voxel Dot Net, Inc. | US | malicious |
376 | Sality.gen.55a00c72391b2e89c4500.exe | 199.59.243.200:80 | www.lafyeri.com | — | US | malicious |
376 | Sality.gen.55a00c72391b2e89c4500.exe | 206.189.61.126:80 | kulppasur.com | — | US | malicious |
376 | Sality.gen.55a00c72391b2e89c4500.exe | 68.66.226.85:443 | toalladepapel.com.ar | A2 Hosting, Inc. | US | malicious |
376 | Sality.gen.55a00c72391b2e89c4500.exe | 68.66.226.85:80 | toalladepapel.com.ar | A2 Hosting, Inc. | US | malicious |
376 | Sality.gen.55a00c72391b2e89c4500.exe | 104.18.30.182:80 | ocsp.comodoca.com | Cloudflare Inc | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| malicious |
www.industriaboston.com |
| unknown |
artistlegion.com |
| malicious |
www.interneland.com |
| suspicious |
pagansoftheworld.com |
| unknown |
www.beetzy.net |
| unknown |
www.google-analytics.com |
| whitelisted |
dns.msftncsi.com |
| shared |
www.ledyazilim.com |
| malicious |
ksandrafashion.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1780 | red_conapi.exe | A Network Trojan was detected | AV USER_AGENTS Suspicious User-Agent (vb wininet) |
1780 | red_conapi.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
1780 | red_conapi.exe | A Network Trojan was detected | AV USER_AGENTS Suspicious User-Agent (vb wininet) |
1780 | red_conapi.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
1780 | red_conapi.exe | A Network Trojan was detected | AV USER_AGENTS Suspicious User-Agent (vb wininet) |
1780 | red_conapi.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
1780 | red_conapi.exe | A Network Trojan was detected | AV USER_AGENTS Suspicious User-Agent (vb wininet) |
1780 | red_conapi.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
1780 | red_conapi.exe | A Network Trojan was detected | AV USER_AGENTS Suspicious User-Agent (vb wininet) |
1780 | red_conapi.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |