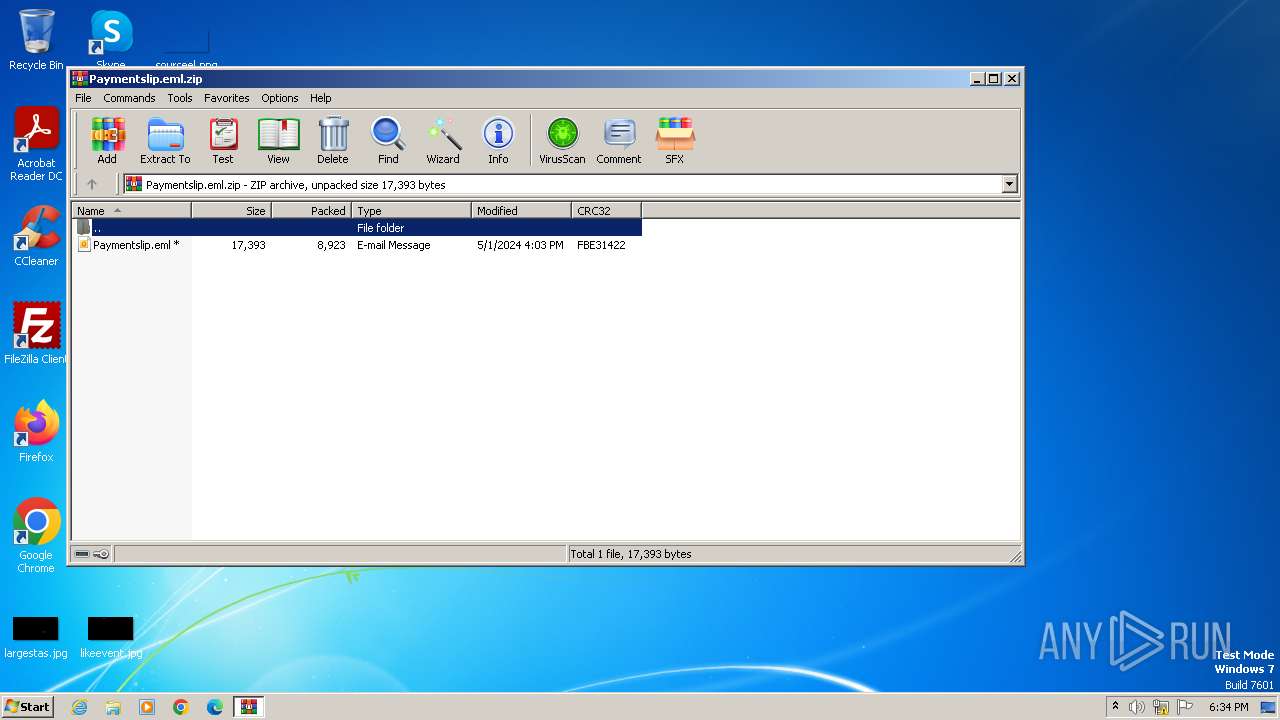
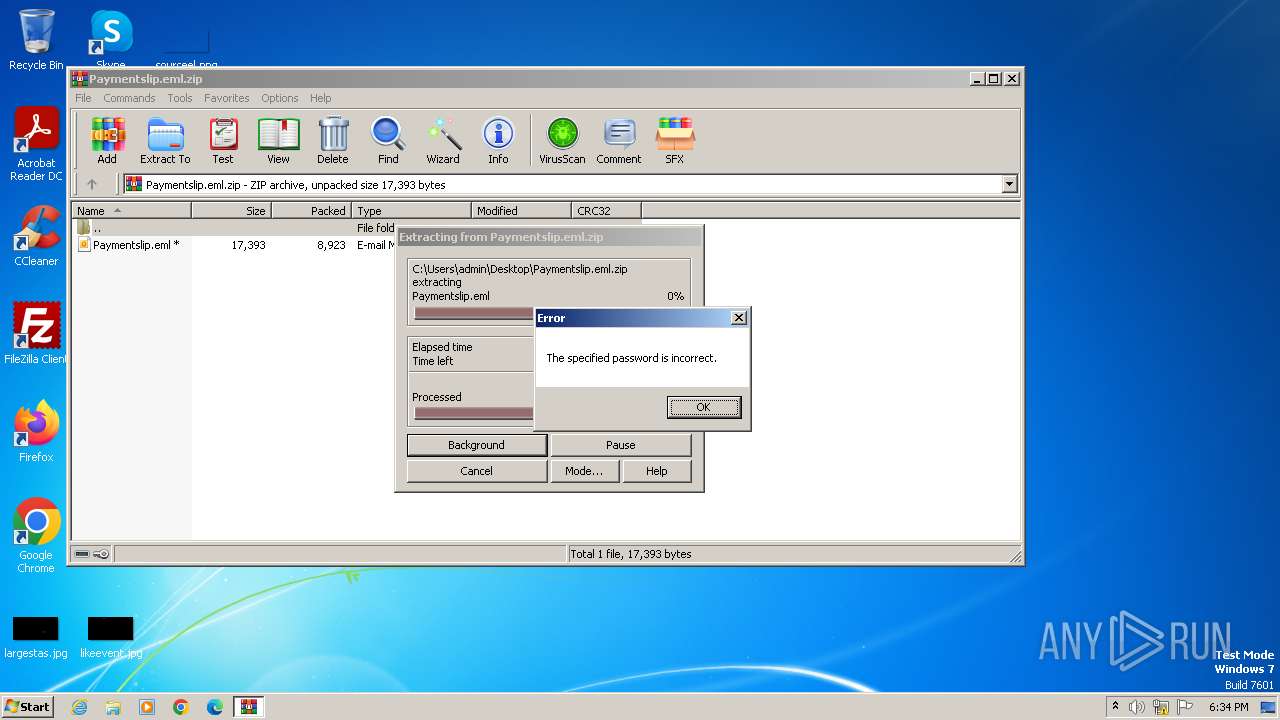
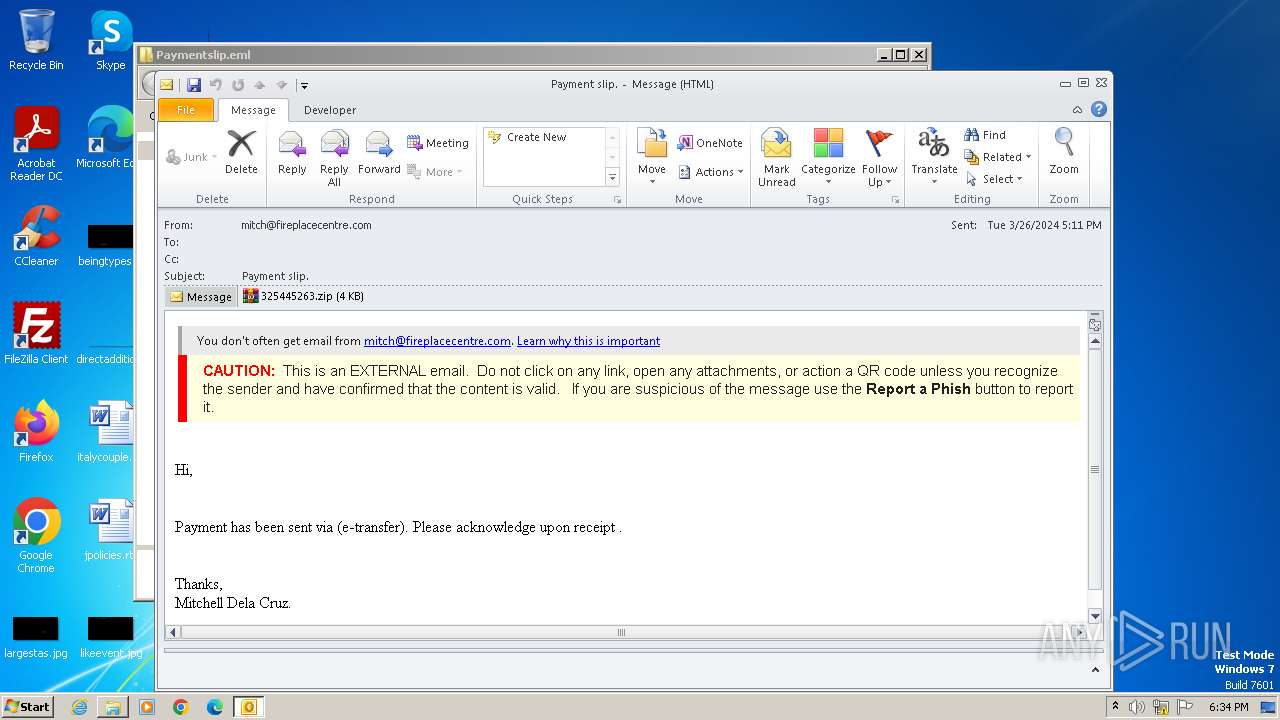
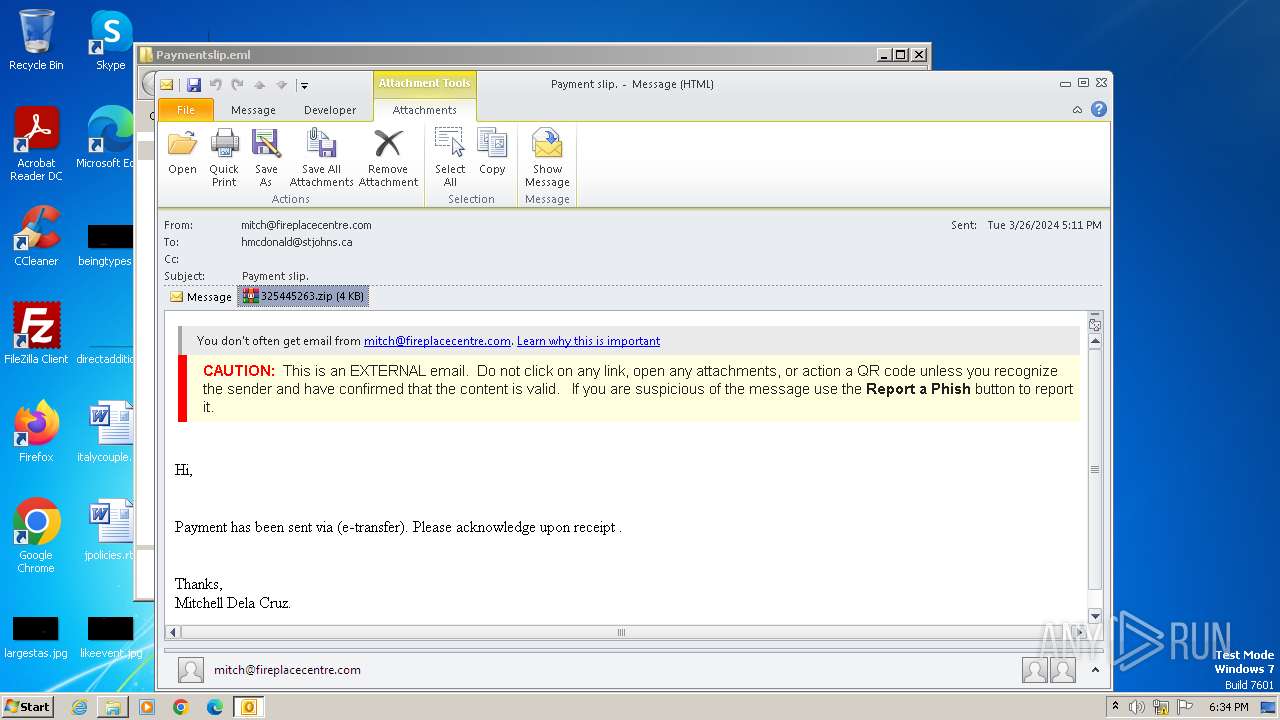
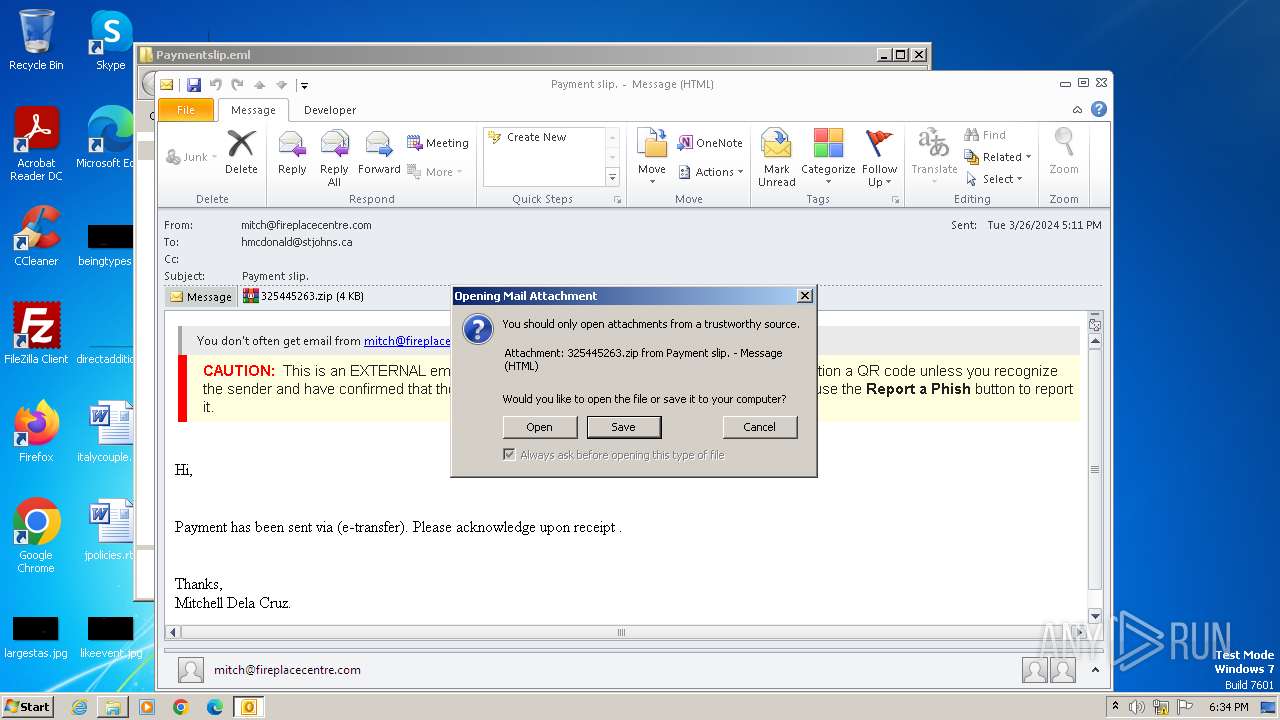
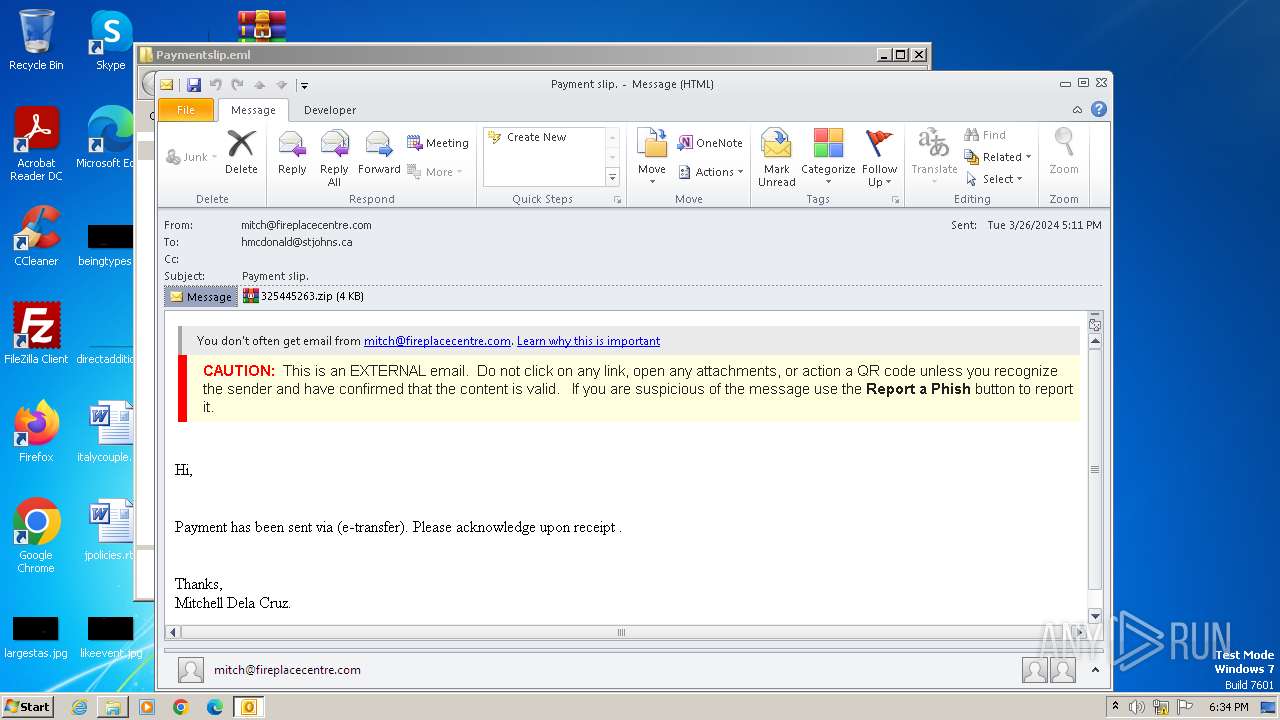
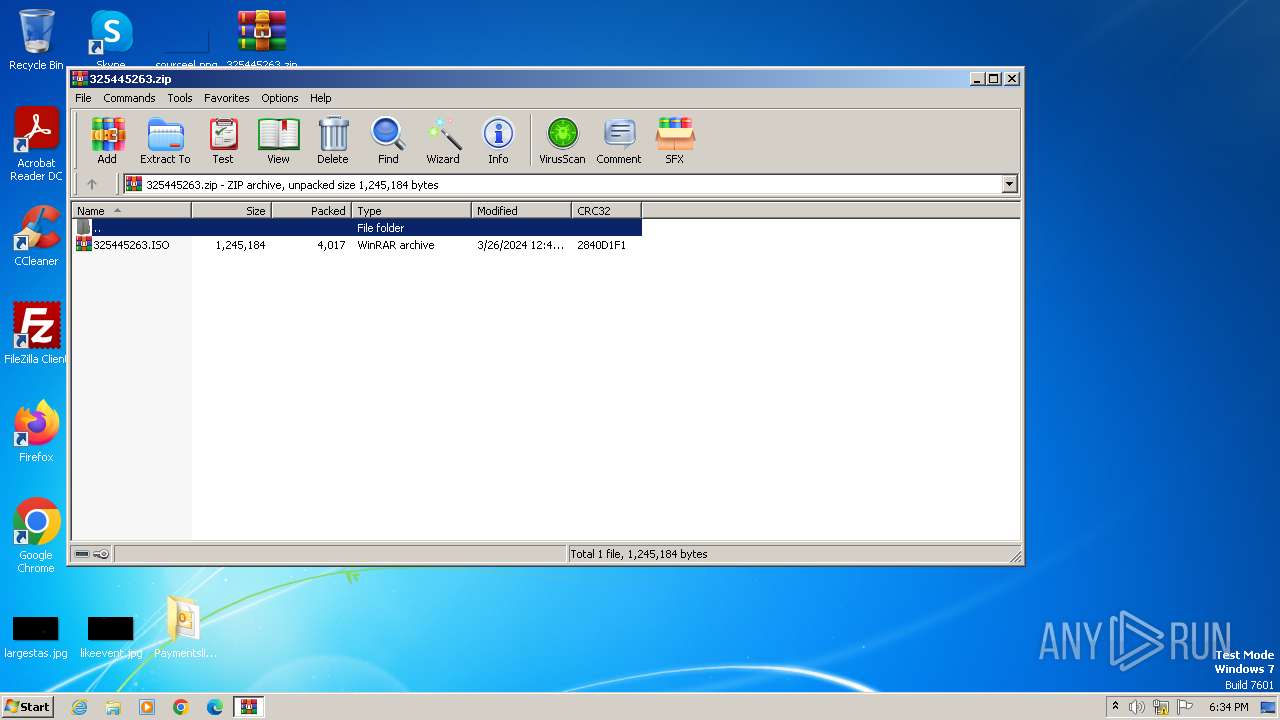
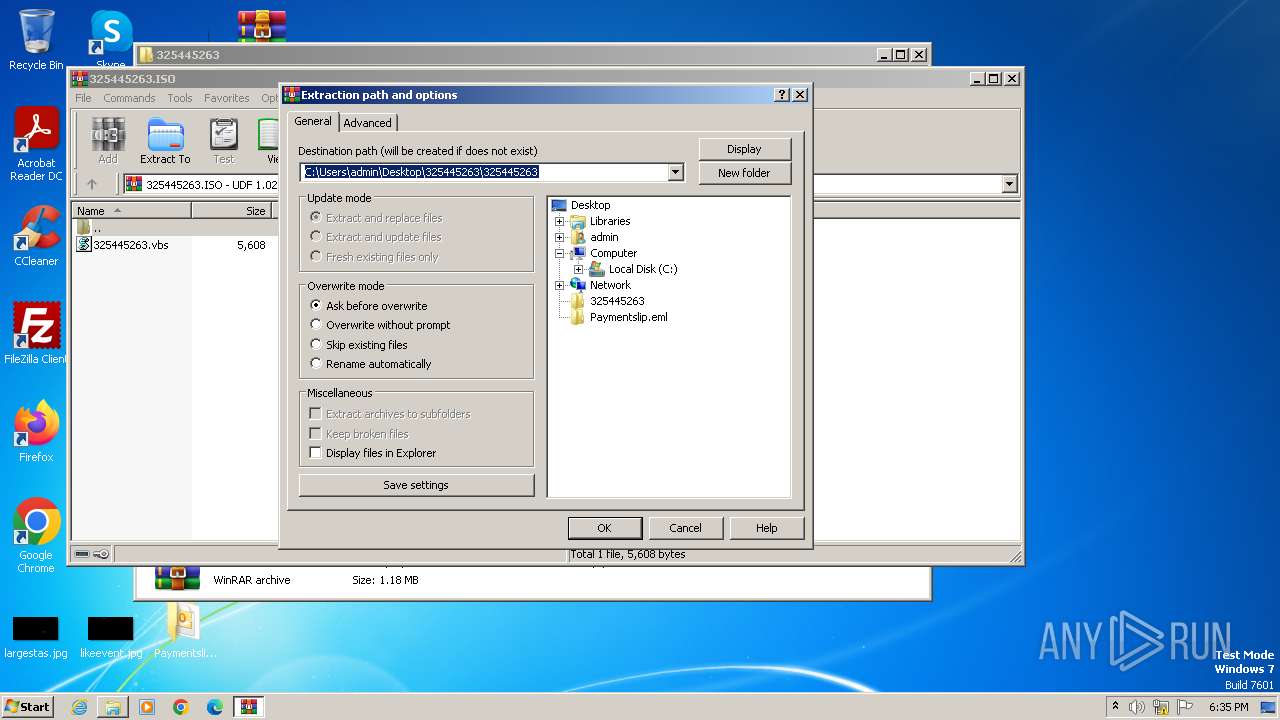
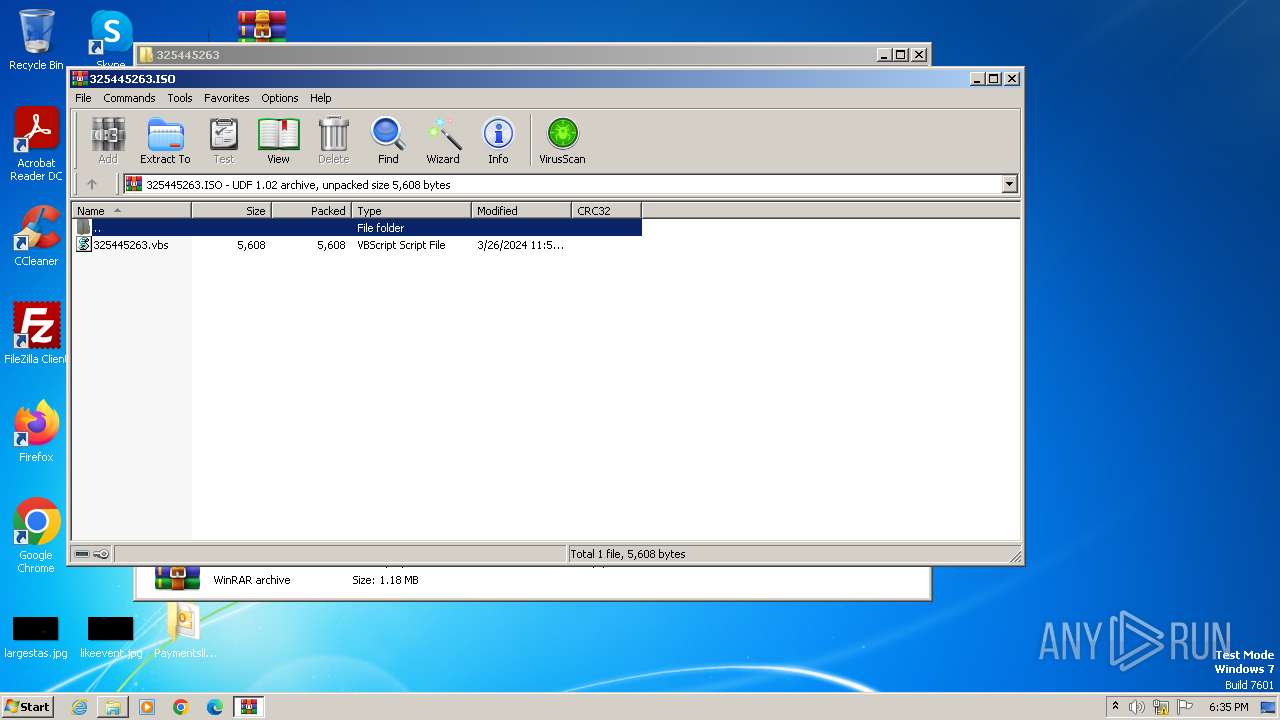
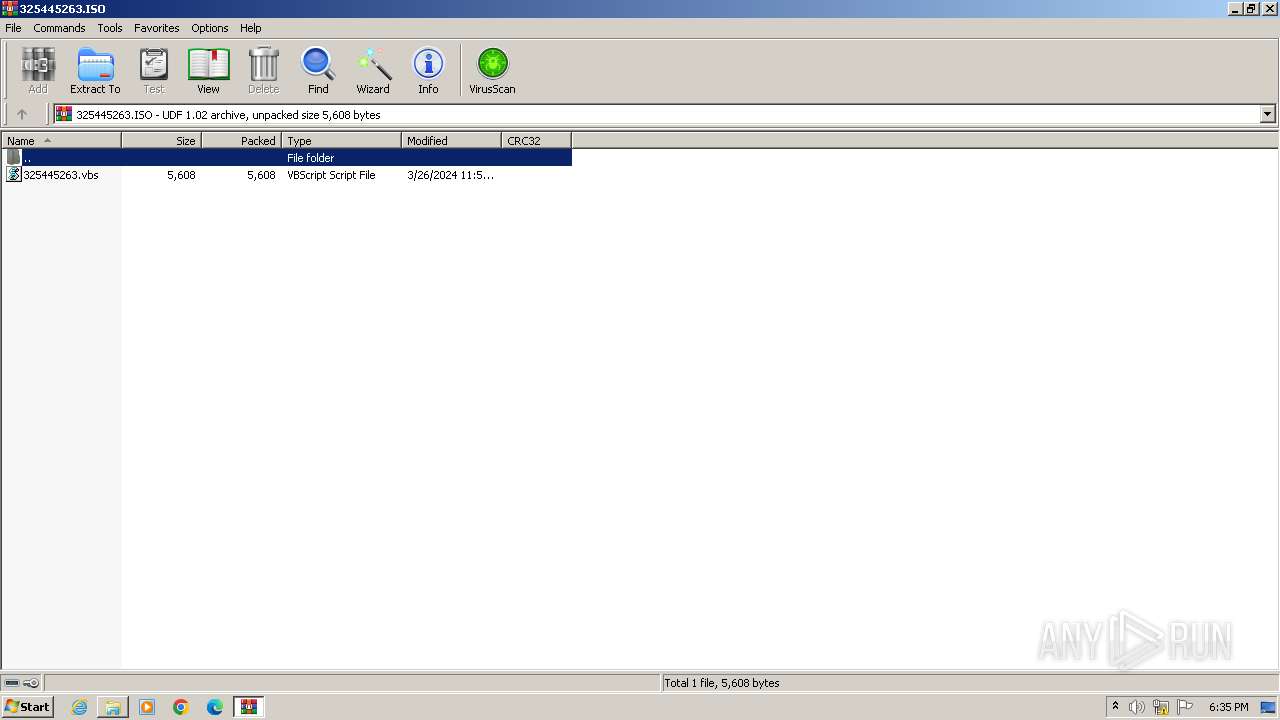
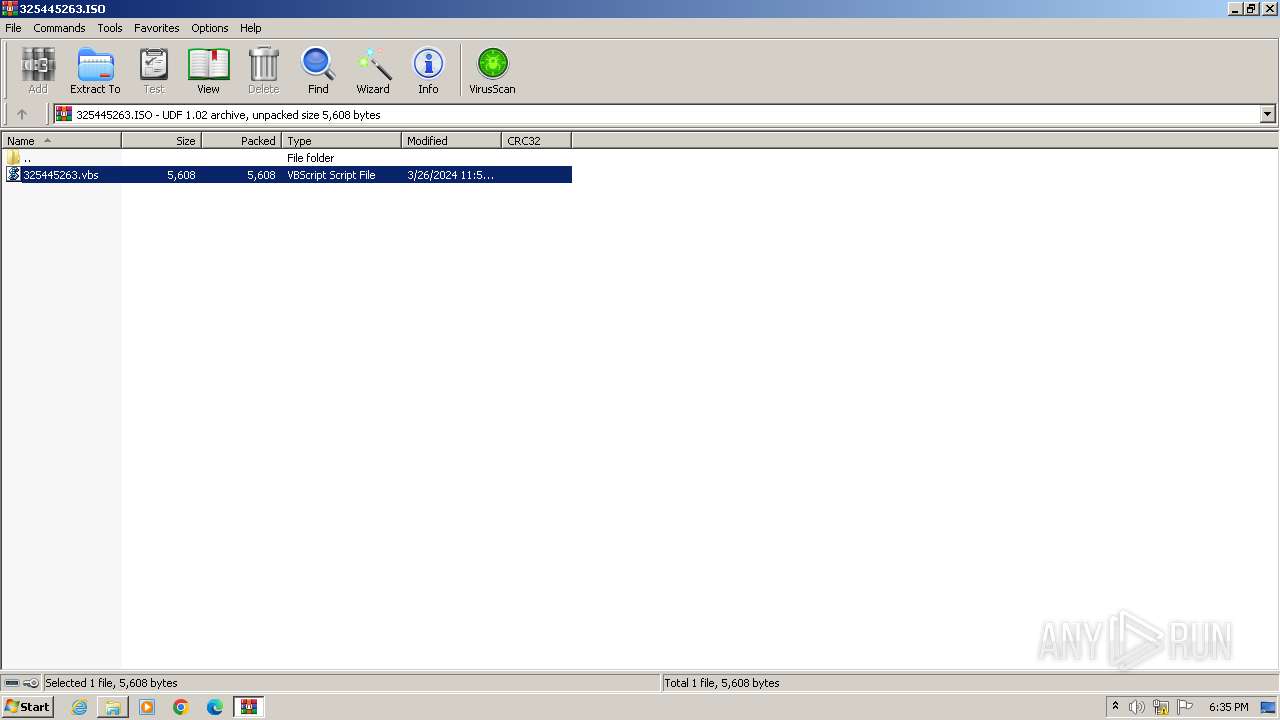
| File name: | Paymentslip.eml.zip |
| Full analysis: | https://app.any.run/tasks/63e13171-640e-4434-8275-f470018e6089 |
| Verdict: | Malicious activity |
| Analysis date: | May 01, 2024, 17:34:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | A7FAED114181120108696F23769C49FF |
| SHA1: | 75AAC097BE2C3284178D3EB7DD181B1CBF2FE840 |
| SHA256: | 70927C41FDED908B635858D5C25AA82503077EE0E54F2B91E74D17A279128572 |
| SSDEEP: | 192:LKOLcHD4aGIlvhFOpPnUJDx3hqJW7bPoJ/rgwe+5Dei7Oi35h8o6tgJwfxrfX:L+D2gWpPnEtR6Wukweme3e5hmpFX |
MALICIOUS
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 2336)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 2336)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 2336)
Unusual connection from system programs
- wscript.exe (PID: 2336)
SUSPICIOUS
The process executes VB scripts
- WinRAR.exe (PID: 1072)
Reads the Internet Settings
- wscript.exe (PID: 2336)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1072)
Potential Corporate Privacy Violation
- wscript.exe (PID: 2336)
INFO
Manual execution by a user
- OUTLOOK.EXE (PID: 1036)
- WinRAR.exe (PID: 2280)
- WinRAR.exe (PID: 1072)
- wmpnscfg.exe (PID: 1012)
The process uses the downloaded file
- OUTLOOK.EXE (PID: 1036)
Checks proxy server information
- wscript.exe (PID: 2336)
Checks supported languages
- wmpnscfg.exe (PID: 1012)
Reads the computer name
- wmpnscfg.exe (PID: 1012)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:05:01 16:03:36 |
| ZipCRC: | 0xfbe31422 |
| ZipCompressedSize: | 8923 |
| ZipUncompressedSize: | 17393 |
| ZipFileName: | Paymentslip.eml |
Total processes
45
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1012 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1036 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\Desktop\Paymentslip.eml\Paymentslip.eml" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 1072 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\325445263\325445263.ISO" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2280 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\325445263.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2336 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa1072.21650\325445263.vbs" | C:\Windows\System32\wscript.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3960 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Paymentslip.eml.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
26 505
Read events
25 708
Write events
714
Delete events
83
Modification events
| (PID) Process: | (3960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3960) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Paymentslip.eml.zip | |||
| (PID) Process: | (3960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
0
Suspicious files
11
Text files
6
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1036 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR8C44.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1036 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 1036 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~WRD0000.tmp | — | |
MD5:— | SHA256:— | |||
| 3960 | WinRAR.exe | C:\Users\admin\Desktop\Paymentslip.eml\Paymentslip.eml | binary | |
MD5:D91FE31CE08EF8AE3A9FF9A92E3BE234 | SHA256:3CEF49E5A180B23993F79CB2F039D5675B795DC11BF0268024CBC43D4B3AEEF3 | |||
| 1036 | OUTLOOK.EXE | C:\Users\admin\Desktop\325445263.zip | compressed | |
MD5:F800094C828A775D8B5CB8D9F77AF988 | SHA256:681F9EB257B075171815114AF624C40B034567D0260E246ECA216DE1DF186FF0 | |||
| 1036 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\LJWTV350\325445263.zip:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 1036 | OUTLOOK.EXE | C:\Users\admin\Desktop\325445263.zip:Zone.Identifier:$DATA | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 1036 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\~Outlook Data File - NoMail.pst.tmp | binary | |
MD5:33DB42B7A175C9065ECA31F03EABBFB6 | SHA256:1886CB9BD4304B3D43F114E517C2FEE1740EB5F4C7708874345F2AB772C8FDB4 | |||
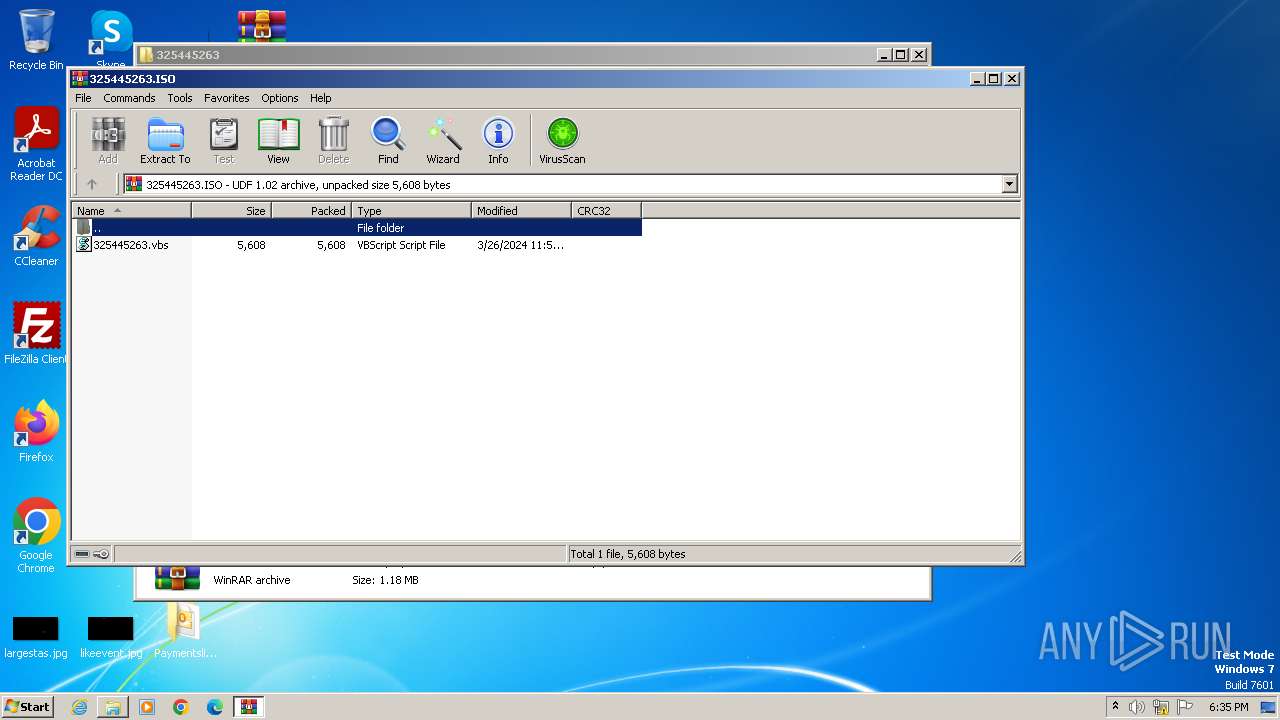
| 1072 | WinRAR.exe | C:\Users\admin\Desktop\325445263\325445263\325445263.vbs | text | |
MD5:8860415C7F6F62563E6A83F38F5E9C9E | SHA256:A27BEFDA630CF94FA78551C737D99B4A370B4CF03FA30CC66ECDB25ABE7FFABF | |||
| 1036 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\LJWTV350\325445263.zip | compressed | |
MD5:F800094C828A775D8B5CB8D9F77AF988 | SHA256:681F9EB257B075171815114AF624C40B034567D0260E246ECA216DE1DF186FF0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
7
DNS requests
5
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2336 | wscript.exe | GET | 304 | 80.239.138.97:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e15277e2dedc708d | unknown | — | — | unknown |
2336 | wscript.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | unknown |
2336 | wscript.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1036 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2336 | wscript.exe | 188.114.97.3:443 | paste.ee | CLOUDFLARENET | NL | unknown |
2336 | wscript.exe | 80.239.138.97:80 | ctldl.windowsupdate.com | Telia Company AB | DE | unknown |
2336 | wscript.exe | 142.250.181.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
dns.msftncsi.com |
| shared |
paste.ee |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2336 | wscript.exe | Potential Corporate Privacy Violation | ET POLICY Pastebin-style Service (paste .ee) in TLS SNI |