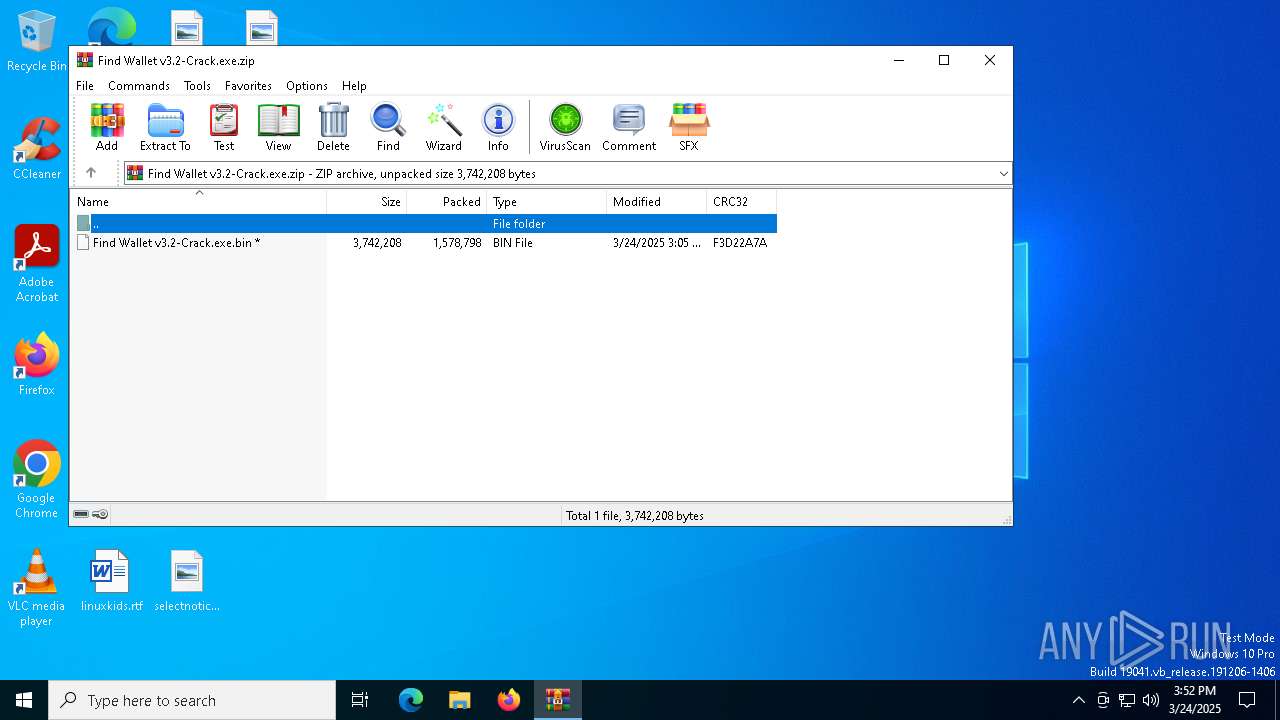
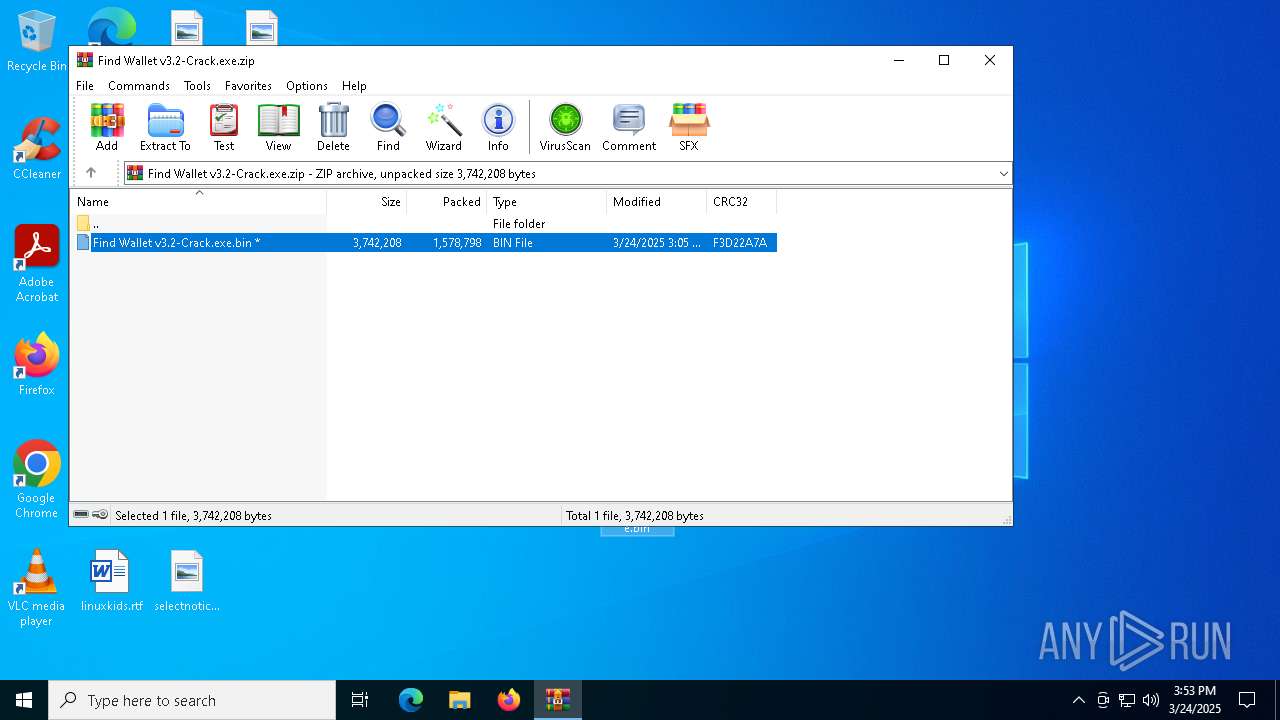
| File name: | Find Wallet v3.2-Crack.exe.zip |
| Full analysis: | https://app.any.run/tasks/396fbfc4-506f-4598-9e5f-123df5815ccc |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 15:52:31 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
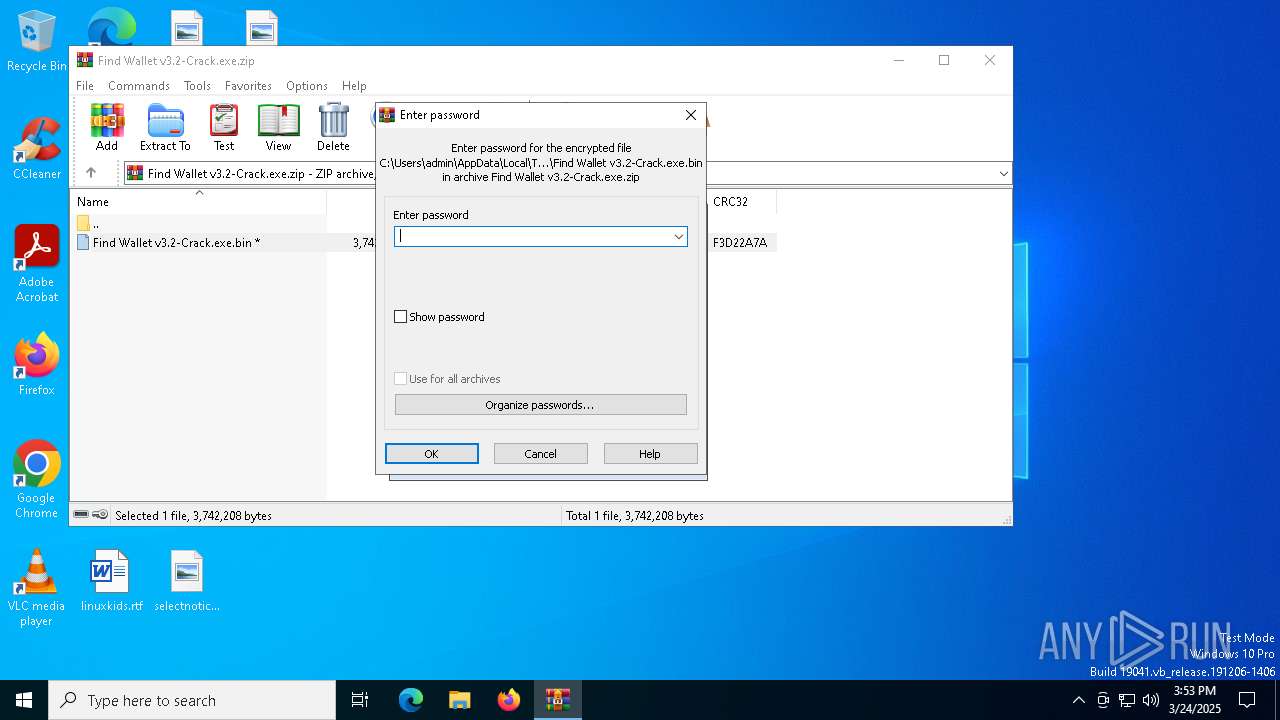
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | CC6BAF54F3D6AD7463F272D0781CE753 |
| SHA1: | 83B411038A5DE605CB299D69C7B1252859932C22 |
| SHA256: | 7087799FC34BF8538C11CE734E3CD2D31290915D49AF765A1C889E847C0264F4 |
| SSDEEP: | 49152:OuL5792r556LDhdVKXGAcu9oZ8p+c5KVRZ0DptiCHmAge4H9WnO3lsDgP7sOLuHI:L57906LlyXJl9oapL5M0D3iCOH9Wncll |
MALICIOUS
NESHTA mutex has been found
- Find Wallet v3.2-Crack.exe (PID: 5176)
- Find Wallet v3.2-Crack.exe (PID: 2568)
Actions looks like stealing of personal data
- Find Wallet v3.2-Crack.exe (PID: 5176)
SUSPICIOUS
Executable content was dropped or overwritten
- Find Wallet v3.2-Crack.exe (PID: 5176)
- Find Wallet v3.2-Crack.exe (PID: 2568)
- Find Wallet v3.2-Crack.exe (PID: 4336)
Mutex name with non-standard characters
- Find Wallet v3.2-Crack.exe (PID: 5176)
- Find Wallet v3.2-Crack.exe (PID: 2568)
Checks for external IP
- svchost.exe (PID: 2196)
- Client.exe (PID: 4300)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2148)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 2772)
- dw20.exe (PID: 2960)
Manual execution by a user
- Find Wallet v3.2-Crack.exe (PID: 5176)
- Find Wallet v3.2-Crack.exe (PID: 2568)
Create files in a temporary directory
- Find Wallet v3.2-Crack.exe (PID: 5176)
- Find Wallet v3.2-Crack.exe (PID: 2568)
- Client.exe (PID: 4300)
Checks supported languages
- Find Wallet v3.2-Crack.exe (PID: 4336)
Reads the computer name
- Find Wallet v3.2-Crack.exe (PID: 4336)
Creates files in the program directory
- dw20.exe (PID: 2960)
- Client.exe (PID: 4300)
Reads the machine GUID from the registry
- Client.exe (PID: 4300)
Reads the software policy settings
- dw20.exe (PID: 2960)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:03:24 15:05:10 |
| ZipCRC: | 0xf3d22a7a |
| ZipCompressedSize: | 1578798 |
| ZipUncompressedSize: | 3742208 |
| ZipFileName: | Find Wallet v3.2-Crack.exe.bin |
Total processes
148
Monitored processes
16
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 960 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1196 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1240 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Find Wallet v3.2-Crack.exe.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2504 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2568 | "C:\Users\admin\Desktop\Find Wallet v3.2-Crack.exe" | C:\Users\admin\Desktop\Find Wallet v3.2-Crack.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2772 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2960 | dw20.exe -x -s 320 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\dw20.exe | Find Wallet v3.2-Crack.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Error Reporting Shim Exit code: 0 Version: 2.0.50727.9149 (WinRelRS6.050727-9100) Modules
| |||||||||||||||
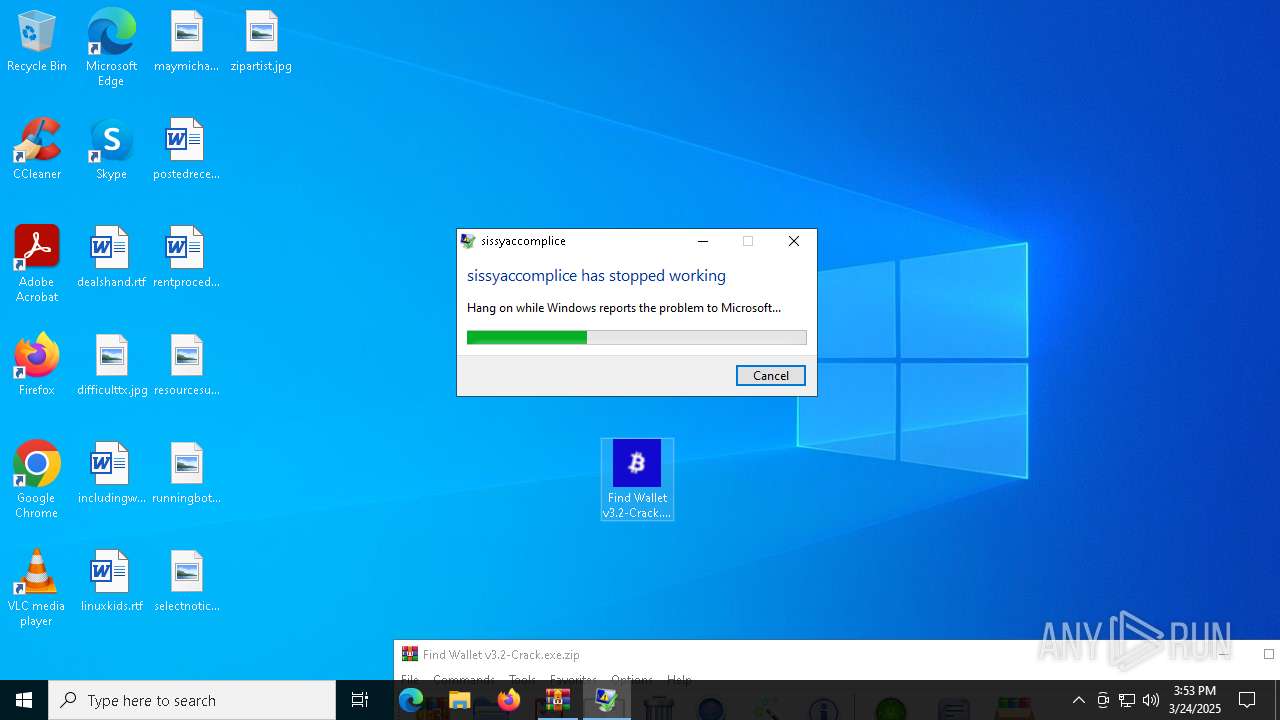
| 3300 | "C:\Users\admin\AppData\Local\Temp\3582-490\Find Wallet v3.2-Crack.exe" | C:\Users\admin\AppData\Local\Temp\3582-490\Find Wallet v3.2-Crack.exe | Find Wallet v3.2-Crack.exe | ||||||||||||
User: admin Company: bitter Integrity Level: MEDIUM Description: sissyaccomplice Exit code: 3762507597 Version: 4.6.11.32 Modules
| |||||||||||||||
Total events
8 856
Read events
8 815
Write events
41
Delete events
0
Modification events
| (PID) Process: | (2148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Find Wallet v3.2-Crack.exe.zip | |||
| (PID) Process: | (2148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2772) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2772) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
9
Suspicious files
37
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2772 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\438277b4-6137-4b6c-a510-cfe8178df5ae.down_data | — | |
MD5:— | SHA256:— | |||
| 4300 | Client.exe | C:\Users\admin\AppData\Local\Temp\places.raw | — | |
MD5:— | SHA256:— | |||
| 2772 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:B942480202B2AC3DB84E75249008AAE4 | SHA256:C70876FACDECCC0E1731F9DD0880CA65C2C12A27D4B3B61944F33A4A88BDF583 | |||
| 2772 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:4872BABAF39AA62B8D32695EBB7E9173 | SHA256:2EE85DF86EE29BBEB3DCA81AA29B6DE204F605A2769B84C728A329178A2D0999 | |||
| 4300 | Client.exe | C:\ProgramData\DESKTOP-JGLLJLD\Browsers\Outlook\Outlook.txt | text | |
MD5:81051BCC2CF1BEDF378224B0A93E2877 | SHA256:7EB70257593DA06F682A3DDDA54A9D260D4FC514F645237F5CA74B08F8DA61A6 | |||
| 2772 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\f0227c23-1e0c-44cf-be64-fcca4ded9b1c.up_meta_secure | binary | |
MD5:5DA2040F503F4DA87C4674864F3D4ADD | SHA256:B4C259644BB776953FC31583123FACB855D9B8A6786DAF21CA9848A0992588A8 | |||
| 4336 | Find Wallet v3.2-Crack.exe | C:\Users\admin\AppData\Roaming\Find Wallet v3.2-Crack.exe | executable | |
MD5:C309CB9865DFC6DBB7F977F4C0F722C0 | SHA256:51472E512316807270D85560BF6E3030355007C36A4F74D59A286411BB5378B5 | |||
| 2772 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\438277b4-6137-4b6c-a510-cfe8178df5ae.dfaea1c8-d983-4be2-90d1-69f8261215bb.down_meta | binary | |
MD5:D2BABCC2BAEE0677F18F74F74CB521CD | SHA256:2A31BD3BC4FC2D4A9C7DCED9727023DB7C2D30CD7EC86899A3C2ACD6481E5143 | |||
| 2568 | Find Wallet v3.2-Crack.exe | C:\Users\admin\AppData\Local\Temp\3582-490\Find Wallet v3.2-Crack.exe | executable | |
MD5:68F929DC1286BF7AF65BF056845F9B42 | SHA256:0D20648267D3004BA95B04F9EF01F3F6E40644B46773990807C2741ADBDD3D82 | |||
| 2148 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2148.41054\Find Wallet v3.2-Crack.exe.bin | executable | |
MD5:A5AAD19F2467992040DCE284A1D34016 | SHA256:6131F59ADE95F5AAF4F78C1CBD31F033AE508BAE3418D30AD9B7E35E3F96BEB6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
32
DNS requests
20
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.168:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.63.118.230:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1452 | backgroundTaskHost.exe | GET | 200 | 23.63.118.230:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.168:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2772 | BackgroundTransferHost.exe | GET | 200 | 23.63.118.230:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6132 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6132 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2960 | dw20.exe | GET | 200 | 23.48.23.185:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2960 | dw20.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.168:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.168:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 23.63.118.230:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Checker Domain (freegeoip .app) |
4300 | Client.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] SNI External IP Domain Lookup (freegeoip .app) |
4300 | Client.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
4300 | Client.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
4300 | Client.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
2196 | svchost.exe | Potentially Bad Traffic | ET INFO External IP Lookup Domain Domain in DNS Lookup (ipbase .com) |
4300 | Client.exe | Potentially Bad Traffic | ET INFO Observed External IP Lookup Domain (ipbase .com in TLS SNI) |
4300 | Client.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
4300 | Client.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
4300 | Client.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |