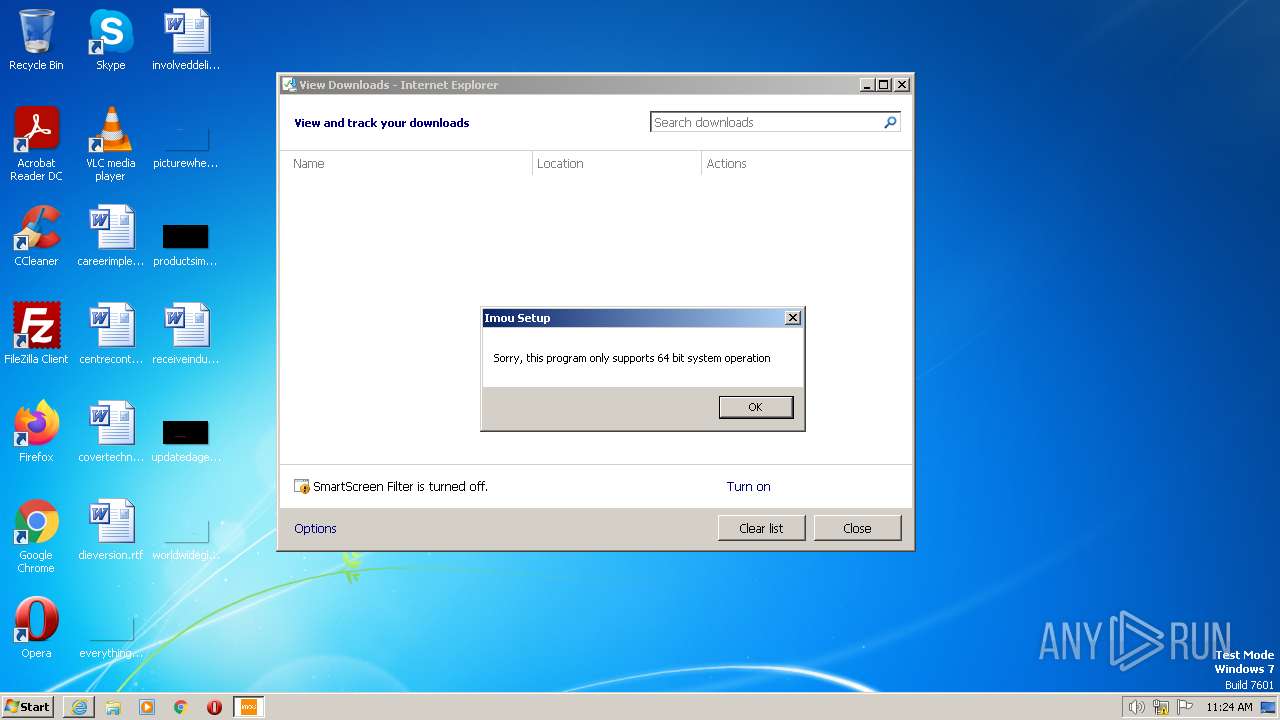
| URL: | https://file-proxy.imoulife.com/easy4ip-oms-sg/file_transfer/dubhe/fde5cef54b80449ea2b75818550e7296/b8266e30d.exe |
| Full analysis: | https://app.any.run/tasks/fabc5b7b-f26b-4408-95f2-17443ecef3c6 |
| Verdict: | Malicious activity |
| Analysis date: | June 19, 2023, 10:22:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | BCAB04385BFD5540B679AF94AE18B8AB |
| SHA1: | 0185AB818D2AE419C3DF6E640956D92A58EC8615 |
| SHA256: | 70728BF34046F64FCB6AE55560EDE3412640315790F8F6D4ED157E5A7E19287F |
| SSDEEP: | 3:N8oXKeLEMGKwUHKaRULWDnKbDudVRRcA++FVnD5+An:2ofGXu9mSB6OD5/n |
MALICIOUS
Application was dropped or rewritten from another process
- b8266e30d.exe (PID: 2508)
- b8266e30d.exe (PID: 572)
SUSPICIOUS
Executable content was dropped or overwritten
- b8266e30d.exe (PID: 2508)
The process creates files with name similar to system file names
- b8266e30d.exe (PID: 2508)
INFO
Checks supported languages
- b8266e30d.exe (PID: 2508)
The process checks LSA protection
- b8266e30d.exe (PID: 2508)
Reads the computer name
- b8266e30d.exe (PID: 2508)
Application launched itself
- iexplore.exe (PID: 1008)
The process uses the downloaded file
- iexplore.exe (PID: 1008)
Executable content was dropped or overwritten
- iexplore.exe (PID: 3036)
Create files in a temporary directory
- b8266e30d.exe (PID: 2508)
Loads dropped or rewritten executable
- b8266e30d.exe (PID: 2508)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
43
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 572 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\b8266e30d.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\b8266e30d.exe | — | iexplore.exe | |||||||||||
User: admin Company: 杭州华橙网络科技有限公司 Integrity Level: MEDIUM Description: 乐橙客户端安装程序 Exit code: 3221226540 Version: 2.6.0 Modules
| |||||||||||||||
| 1008 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://file-proxy.imoulife.com/easy4ip-oms-sg/file_transfer/dubhe/fde5cef54b80449ea2b75818550e7296/b8266e30d.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2508 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\b8266e30d.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\b8266e30d.exe | iexplore.exe | ||||||||||||
User: admin Company: 杭州华橙网络科技有限公司 Integrity Level: HIGH Description: 乐橙客户端安装程序 Exit code: 2 Version: 2.6.0 Modules
| |||||||||||||||
| 3036 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1008 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
18 963
Read events
18 868
Write events
89
Delete events
6
Modification events
| (PID) Process: | (1008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (1008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (1008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (1008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
2
Suspicious files
16
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3036 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:ED9D5703AF532B952592AD79B72B4751 | SHA256:D79B19493343BBEFE324427C63D2BDF68257227459495291C9599EE89A0A4318 | |||
| 3036 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\FA0A17BC17FF10008872A7205D0D43E2_608DEF97DFACECDA8E97C6F270153A4F | binary | |
MD5:60ECD294B0E457EC459F74898D3A7898 | SHA256:8B71463161A171B625A9E65CD763D36E53775C9468FD75E02A2EAC93A7C41B6C | |||
| 1008 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\versionlist.xml | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
| 3036 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\b8266e30d.exe.3bd4wkf.partial | — | |
MD5:— | SHA256:— | |||
| 3036 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\FA0A17BC17FF10008872A7205D0D43E2_608DEF97DFACECDA8E97C6F270153A4F | binary | |
MD5:6E112F7E8F82B30ED9F6B91ABA1F8300 | SHA256:659BA8ADAFDE0F0DB335DFD989B45982140E1D14D7C2EB9B72EDEE28E67CF0A2 | |||
| 3036 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8F8712BCE78D28F9C5E3E950CD93EADA_7778759470DAF8CCC2D6FE253408594E | binary | |
MD5:3A06C9C5EDB592B83523A3324DBE59FA | SHA256:8B528B4835CAE50D494BA42D03400A96C256BED2EC9787502AEB0E06BEF0F0E4 | |||
| 3036 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\b8266e30d[1].exe | executable | |
MD5:BF4CC4CBB87A74C179F4701D3CA9C6B9 | SHA256:4DAF87CB315697BCDFB063A8D2F94B5655F0004810AA225B814290545BC0EA1F | |||
| 1008 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\b8266e30d.exe | — | |
MD5:— | SHA256:— | |||
| 1008 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\verEBE4.tmp | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
| 1008 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\J4PHHJ4I.txt | text | |
MD5:555FDEB3310EB527992E2671F62FAC37 | SHA256:B209EF8305359F54EFF40D49A18C85F67DE13C1FC3394F9D105E2A18FD4FD925 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
27
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1008 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | der | 471 b | whitelisted |
3036 | iexplore.exe | GET | 200 | 163.181.56.169:80 | http://ocsp.dcocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSmVYFXwi%2FRq9wx3PKhB8lC%2FFYUyAQUkZ9eMRWuEJ%2BtYMH3wcyqSDQvDCYCEAPOTKMbiejjYQwsI3iUHhE%3D | US | der | 471 b | whitelisted |
3036 | iexplore.exe | GET | 200 | 163.181.56.169:80 | http://ocsp.dcocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAoEcNCWvIoSyJCm34Ju7Es%3D | US | binary | 471 b | whitelisted |
1008 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
1008 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
1008 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3036 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ea3c704d59272f21 | US | compressed | 4.70 Kb | whitelisted |
3036 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?009888d0b2fe5ccb | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1008 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1008 | iexplore.exe | 204.79.197.200:443 | ieonline.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1008 | iexplore.exe | 204.79.197.203:443 | www.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | malicious |
4004 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3036 | iexplore.exe | 8.209.118.186:443 | file-proxy.imoulife.com | Alibaba US Technology Co., Ltd. | DE | suspicious |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3036 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1008 | iexplore.exe | 104.80.243.160:443 | go.microsoft.com | Akamai International B.V. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
file-proxy.imoulife.com |
| suspicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.dcocsp.cn |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.msn.com |
| whitelisted |
query.prod.cms.msn.com |
| whitelisted |